



This CYFIRMA government & civic organization’s report offers original cybersecurity insights and statistics, presented in an engaging infographic format. It covers key trends and statistics from November 2023 to November 2024.
Welcome to the CYFIRMA infographic report, where we delve into the external threat landscape of government organizations over the past 365 days. This report provides valuable insights and data-driven statistics, delivering a concise analysis of attack campaigns and ransomware incidents targeting government, civic and non-profit organizations around the world.
We aim to present an industry-specific overview in a convenient, engaging, and informative format. Leveraging our cutting-edge platform telemetry and the expertise of our analysts, we bring you actionable intelligence to stay ahead in the cybersecurity landscape.
CYFIRMA provides cyber threat intelligence and external threat landscape management platforms, DeCYFIR and DeTCT, which utilize artificial intelligence and machine learning to ingest and process relevant data, complemented by manual CTI research.
For the purpose of these reports, we leverage the following data from our platform. These are data processed by AI and ML automation, based on both human research input and automated ingestions.
While this report contains statistics and graphs generated primarily by automation, it undergoes thorough review and enhancement for additional context by CYFIRMA CTI analysts to ensure the highest quality and provide valuable insights.
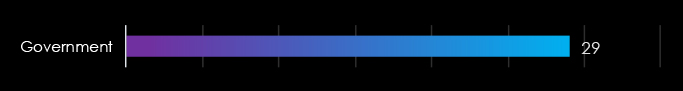
Over the past 12 months, government organizations recorded victims across 29 of the 34 Advanced Persistent Threat (APT) campaigns observed – an incidence rate of 35%.
We track only a single segment in the government category for APT campaigns as per below:
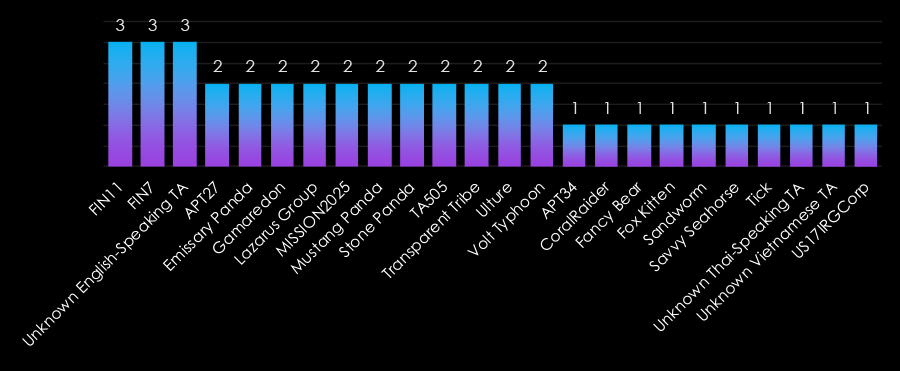
The government sector faces a diverse range of threats from both nation-state and financially motivated actors. FIN11 and FIN7 lead in targeting, reflecting financially driven motives, such as ransomware and data extortion.
Nation-state groups like Lazarus Group, MISSION2025, and Mustang Panda (China) focus on espionage and the theft of sensitive information. Russian actors, including Gamaredon, Fancy Bear, and Sandworm, prioritize geopolitical objectives and intelligence gathering. Emerging actors, such as Unknown Thai-speaking TA and Unknown Vietnamese TA, highlight the sector’s appeal to a broader range of adversaries.
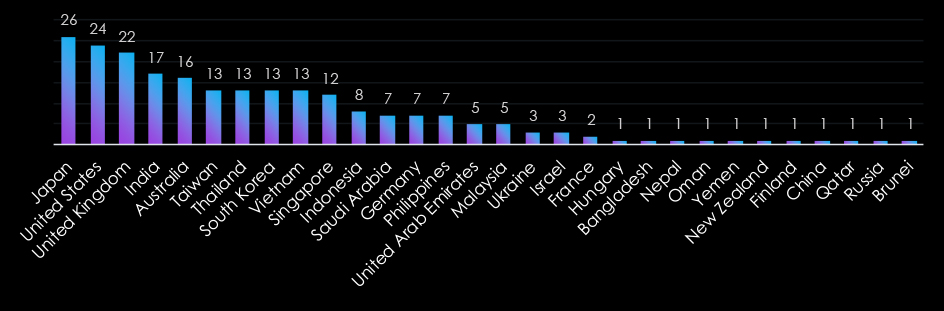
Government organizations are globally targeted, with a strong emphasis on advanced economies like Japan, the United States, and the United Kingdom, reflecting their prominence in geopolitical and global affairs. Asia-Pacific countries, including India, Taiwan, and South Korea, also feature prominently, highlighting the region’s growing strategic importance.
Emerging markets like Indonesia, the Philippines, and Malaysia further underscore attackers’ interest in developing nations. Smaller nations such as Oman, Nepal, and Brunei illustrate the sector’s appeal to a wide range of adversaries, targeting both established and less fortified government systems globally.
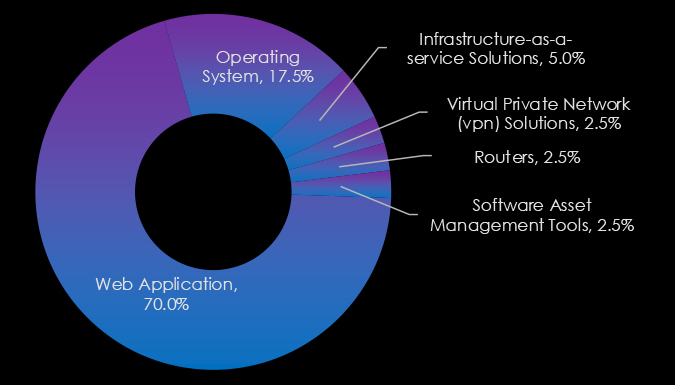
The Government & Civic Organizations sector’s most targeted technologies emphasize the attackers’ focus on foundational and internet-facing systems. Web applications dominate, reflecting their critical role in service delivery and their vulnerability to exploitation.
Operating systems also see significant targeting, highlighting their importance in maintaining governmental infrastructure. Additionally, technologies like infrastructure-as-a-service solutions, VPN solutions, and routers are targeted, underscoring the sector’s reliance on secure and resilient IT systems to protect sensitive operations and data.
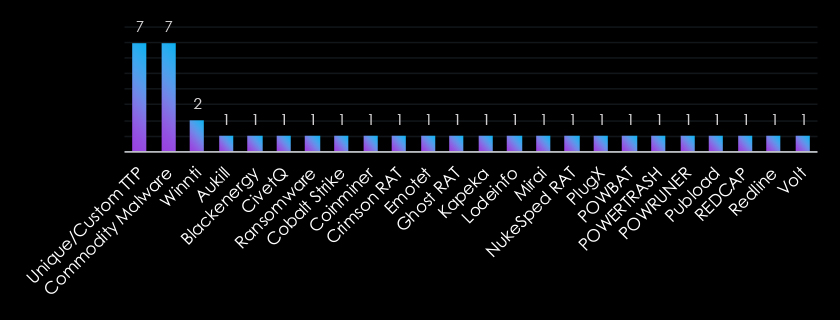
The Government & Civic Organizations sector is targeted with a diverse range of malware, reflecting both tailored and scalable approaches. Unique/Custom TTPs and Commodity Malware dominate, highlighting the balance between sophisticated, targeted attacks and accessible, off-the-shelf tools.
Winnti and tools like NukeSped RAT, PlugX, and Cobalt Strike underscore a focus on espionage and long-term infiltration. Financially motivated malware, such as ransomware and Emotet, emphasizes data theft and extortion, while niche tools like Mirai and Redline demonstrate opportunistic campaigns.
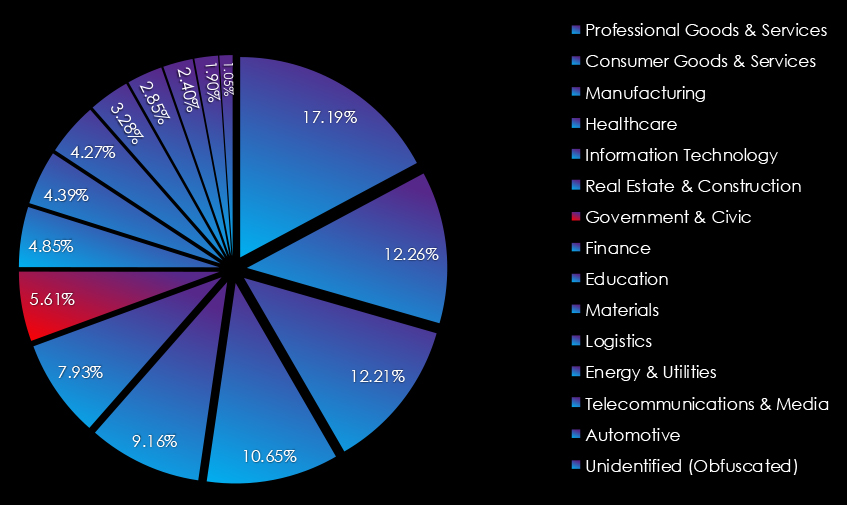
In the past 12 months, CYFIRMA has identified 293 verified government & civic sector ransomware victims. This accounts for 5.61% of the overall total of 5,219 ransomware victims during the same period.
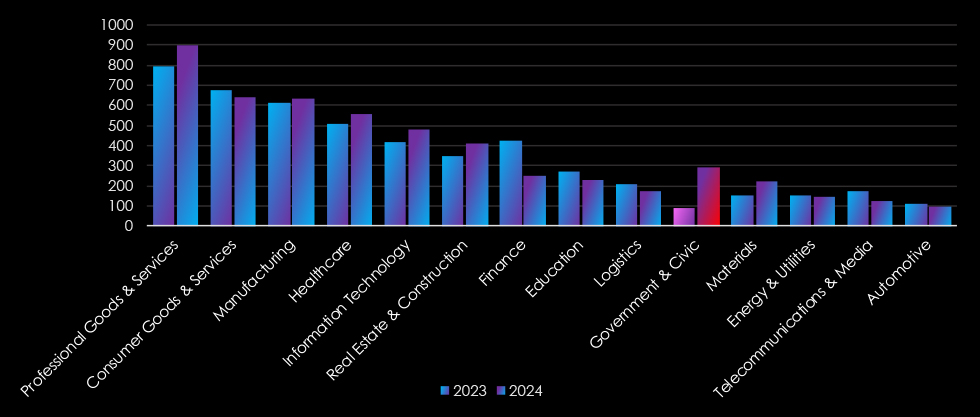
The government and civic organizations recorded the highest year-to-year growth of recorded victims, with 229.21%, more than triple from the previous year. It ranked at the 10th place for both years combined. However, it moved up from the last 13th in 2023 to the 7th place as the sixth most frequent victim of ransomware in 2024.
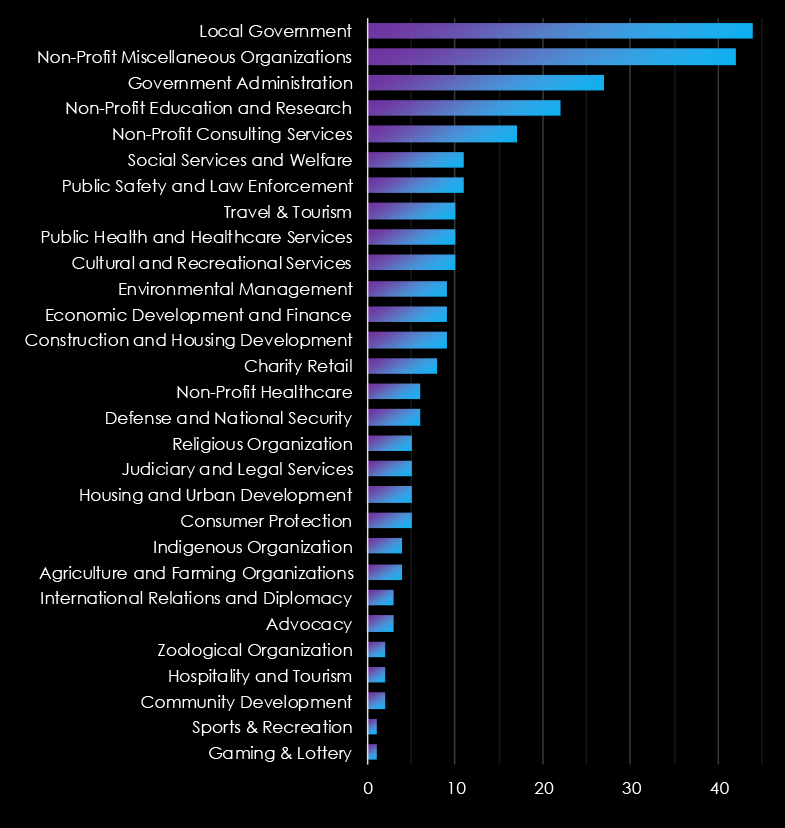
Ransomware attacks in 2024 highlight vulnerabilities across diverse government, civic, and non-profit sectors.
Local Government faces the highest incidents (44), followed by Non-Profit Miscellaneous Organizations (42) and Government Administration (27).
Non-Profit Education and Research (22) and Public Health Services (10) also stand out, reflecting threats to critical services and sensitive data.
Notably, Social Services (11) and Environmental Management (9) indicate expanding targets beyond traditional sectors.
While some sectors like Gaming and Recreation report minimal cases, the overall trend underscores widespread susceptibility, with community-serving entities like Housing Development and Judiciary Services also affected.
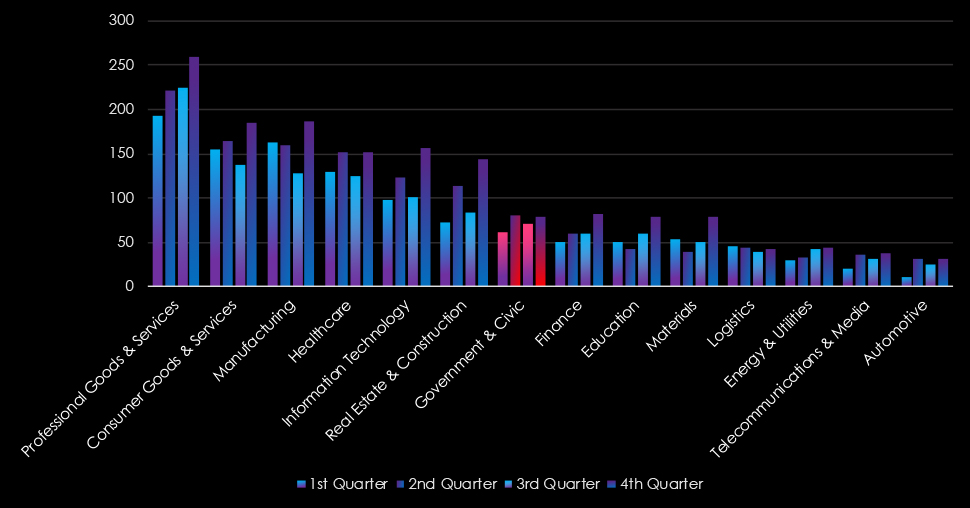
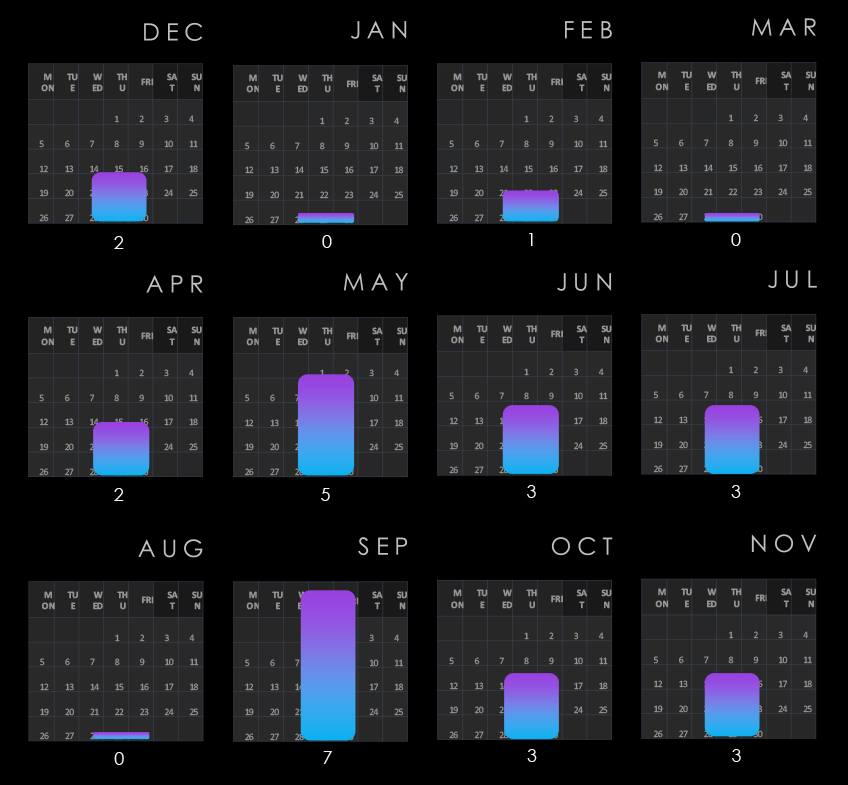
Government & civic organizations experienced sustained activity with moderate and alternate growth from quarter to quarter, second and fourth quarters show mild spikes.
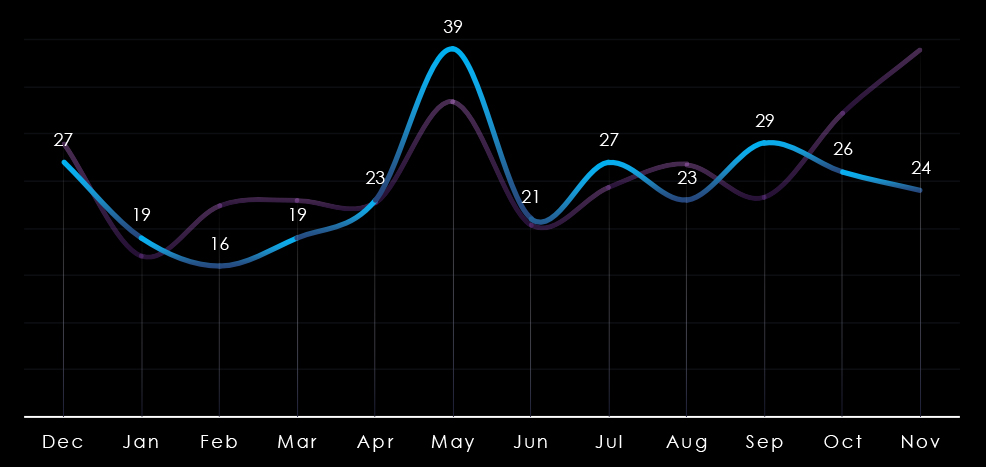
Monthly activity follows the scaled-down global trendline with mostly minor divergences. February, March, and August recorded mild dips. The global spike in May was moderately amplified for government & civic organizations. Despite a small spike in September, this sector diverged from the strong global upswing in October and November, suggesting a calmer start to 2025 relative to other industries.
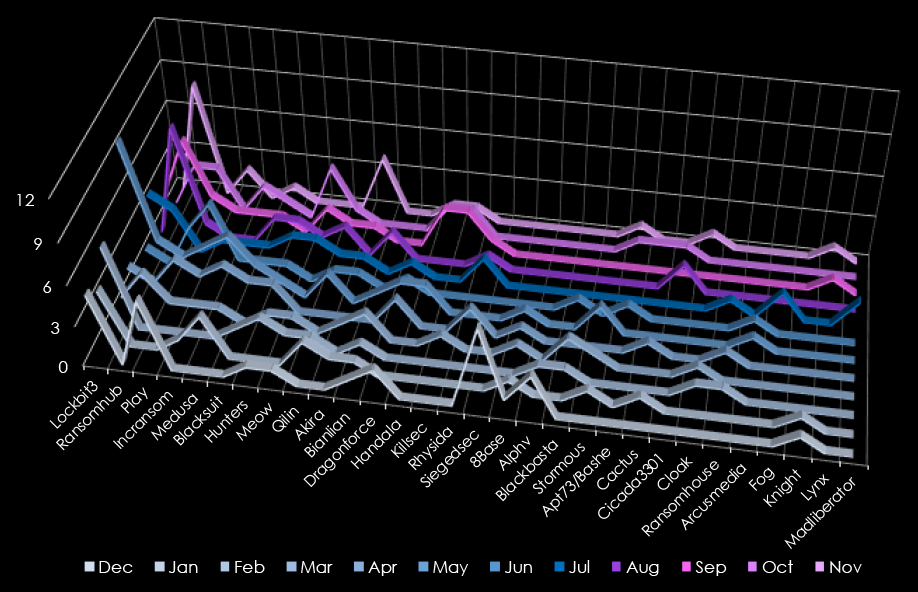
In total 54 out of 97 gangs recorded victims in government & civic organizations industry, with a 56% participation.
LockBit3 and RansomHub led ransomware activity, each targeting 35 victims. RansomHub saw a late-year surge, peaking in November (8 victims), and consistent operations from July onward.
Play targeted 20 victims, with steady activity across the year and peaks in December, April, and October. Incransom and Medusa followed with 16 victims each. Incransom peaked in June and showed sporadic activity, while Medusa had its strongest months in May and October.
Blacksuit, Hunters, and Meow each accounted for 12 victims. Meow peaked in October with four victims, while Hunters and Blacksuit maintained steady but lower levels of activity throughout the year. Qilin (11 victims) was active sporadically, with peaks in February and August.
Less active groups like Akira (9 victims) and Bianlian, Dragonforce, and Handala (8 victims each) showed scattered activity, with Handala focusing on late-year operations. Emerging actors such as Killsec (7 victims) and Rhysida (6 victims) demonstrated limited campaigns, with peaks in October.
Siegedsec had a focused campaign in December, targeting six victims. Large gangs like 8Base (5 victims), Alphv (4 victims), and Blackbasta (4 victims) reported isolated victims. Stormous (4 victims) and groups like Cactus and Cicada3301 (3 victims each) reflected sporadic operations.
Overall, LockBit3 and RansomHub dominated with year-round campaigns, while Play and other mid-tier actors maintained steady operations. Smaller and emerging groups contributed sporadic but impactful campaigns, emphasizing a diverse ransomware ecosystem.
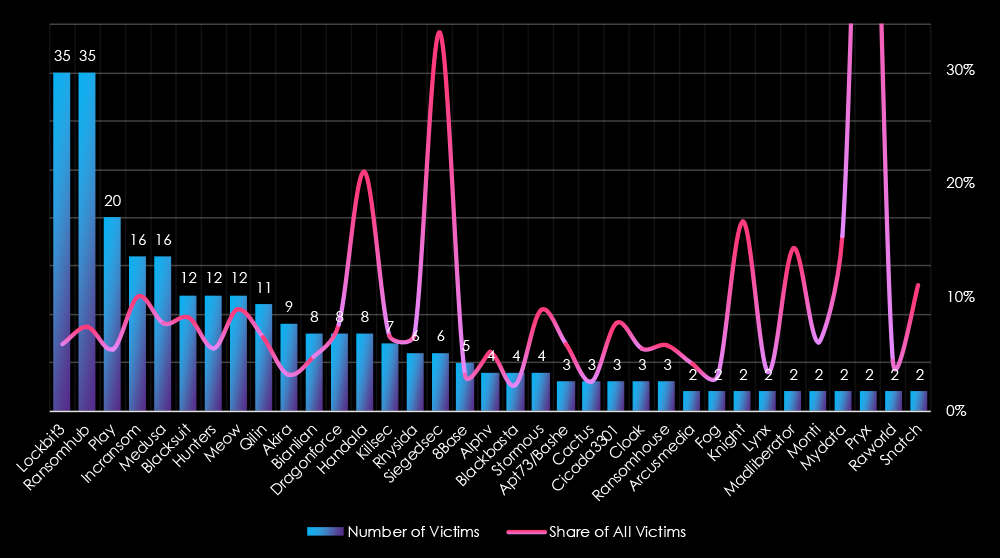
Looking at the top 35 gangs, LockBit3 and RansomHub lead in activity within this sector, with 35 victims each (5.84% and 7.37%, respectively), indicating significant activity but distributed targeting. Play (20 victims, 5.43%) also shows moderate activity. Other notable actors include Incransom (16 victims, 10.13%) and Medusa (16 victims, 7.73%), both showing stronger focus.
Several gangs demonstrate a notable focus on government and civic organizations:
Some gangs exhibit disproportionately high percentages due to low victim counts:
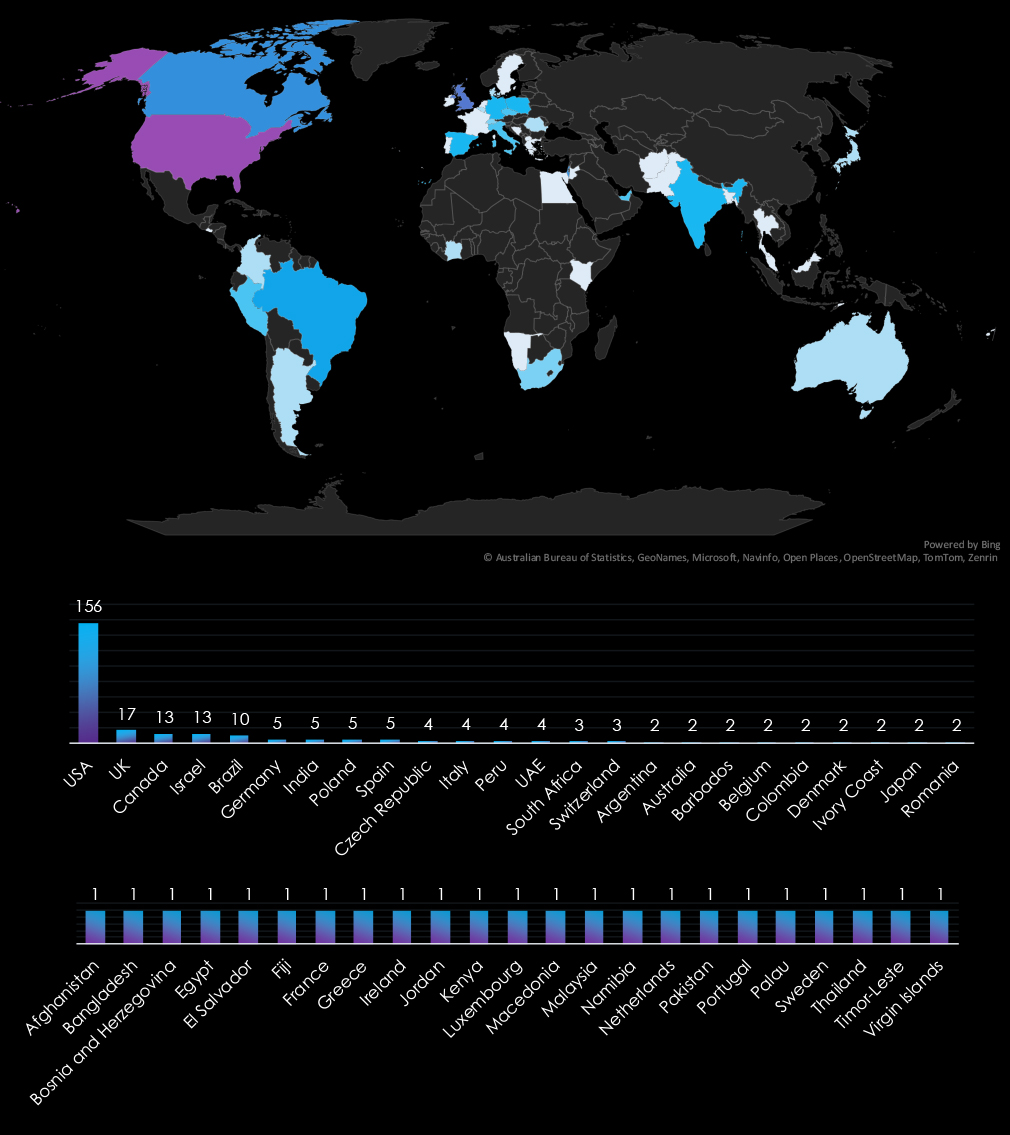
The USA accounts for 53.2% of ransomware victims in the Government & Civic Organizations industry in 2024. The next most affected countries are the UK with 17 victims, Canada with 13, Israel with 13, and Brazil with 10.
A total of 48 countries reported victims, with 24 of them having only one victim each.
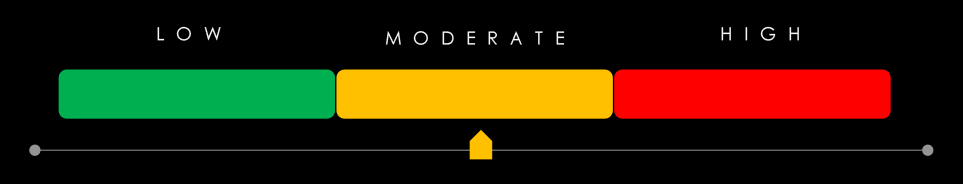
Risk Level Indicator: Moderate
APT Campaigns
Government organizations experienced a 35% incidence rate across APT campaigns, driven by nation-state and financially motivated actors. Groups like Lazarus and MISSION2025 focus on espionage and intelligence gathering, while financially driven actors like FIN11 and FIN7 pursue ransomware and extortion. Emerging groups like Handala and Siegedsec reflect diverse motivations, including political and social agendas.
Actors: FIN11, FIN7, Lazarus, MISSION2025, Mustang Panda, Gamaredon, Fancy Bear, emerging groups like Handala and Siegedsec.
Geographic Focus: U.S., Japan, U.K.; Asia-Pacific nations (India, Taiwan, South Korea); emerging markets (Indonesia, Philippines, Malaysia).
Targets: Web applications, operating systems, IaaS solutions, VPNs, and routers.
Malware: Winnti, NukeSped RAT, PlugX, Cobalt Strike; ransomware, and tools like Mirai and Emotet.
Ransomware
The government & civic sector recorded 293 ransomware victims (5.61% of the global total), reflecting the highest year-over-year growth (+69.62%) among industries. Activity was consistent with peaks in Q2 and Q4, though the sector diverged from the global trend with a calmer October and November, suggesting a slower start to 2025.
Victim Trends: Peaks in May and November; minor dips in February, March, and August.
Key Actors: The most active were LockBit3 (35 victims, steady activity) and RansomHub (35 victims, peak in November).
Other notable gangs were Play (20 victims, peaks in December, April, October); Incransom, and Medusa (16 each).
Geography: The U.S. accounted for 53% of all victims; activity was recorded in 47 countries.
Ranking: Government & civic organizations ranked as the 7th most frequent victim of ransomware.