



The CYFIRMA industry Report delivers original cybersecurity insights and telemetry-driven statistics of global industries, covering one sector each week for a quarter. This report focuses on the Finance industry, presenting key trends and statistics in an engaging infographic format.
Welcome to the CYFIRMA infographic industry report, where we delve into the external threat landscape of the Finance industry over the past three months. This report provides valuable insights and data-driven statistics, delivering a concise analysis of attack campaigns, phishing telemetry, and ransomware incidents targeting the Finance industry.
We aim to present an industry-specific overview in a convenient, engaging, and informative format. Leveraging our cutting-edge platform telemetry and the expertise of our analysts, we bring you actionable intelligence to stay ahead in the cybersecurity landscape.
CYFIRMA provides cyber threat intelligence and external threat landscape management platforms, DeCYFIR and DeTCT, which utilize artificial intelligence and machine learning to ingest and process relevant data, complemented by manual CTI research.
For the purpose of these reports, we leverage the following data from our platform. These are data processed by AI and ML automation based on both human research input and automated ingestions.
While this report contains statistics and graphs generated primarily by automation, it undergoes thorough review and enhancement for additional context by CYFIRMA CTI analysts to ensure the highest quality and provide valuable insights.
Finance organizations featured in 6 out of the 8 observed campaigns, which is a presence in 75% of campaigns.
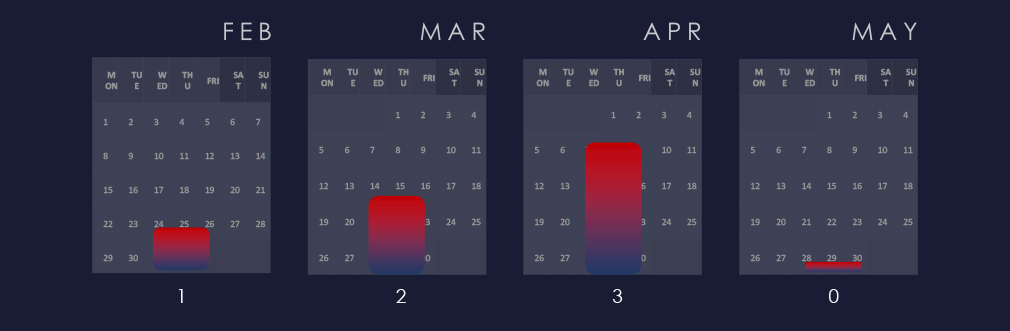
We observed a mild growth trend from mid-February to April, followed by no detections until mid-May.

We observed varied mix of suspected threat actors. Most active were Lazarus Group from DPKR, Chinese Mustang Panda, MISSION2025 and Hafnium as well as Iranian US17IRGCorp.
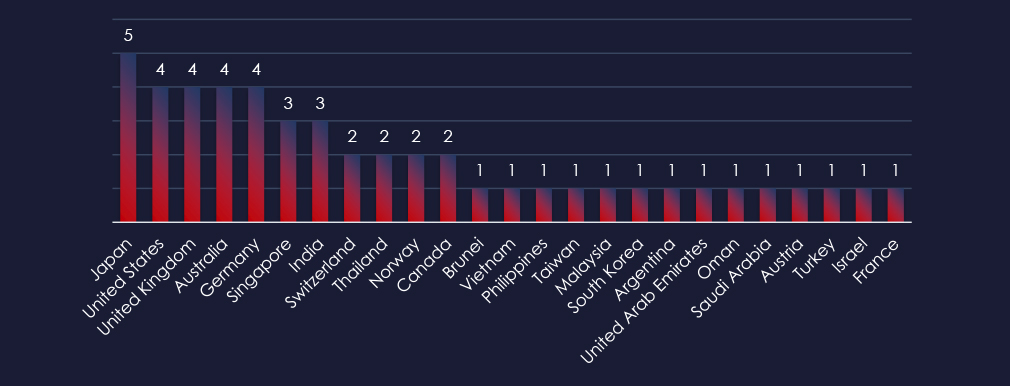
Recorded victims of observed attack campaigns span 25 different countries across continents. Japan being the hardest hit country.
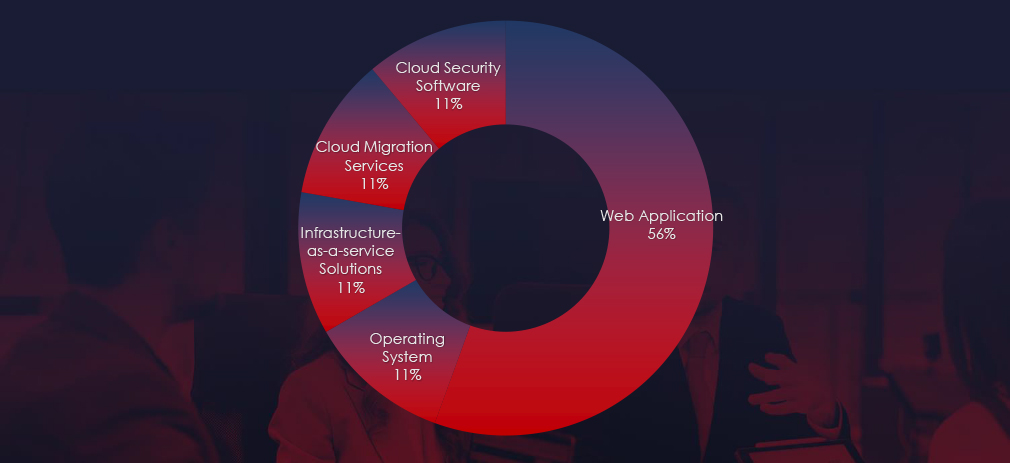
Web applications continue to rank as the most targeted technology across industries. Additionally, compromises were observed in operating systems, IaaS solutions, and cloud technologies.
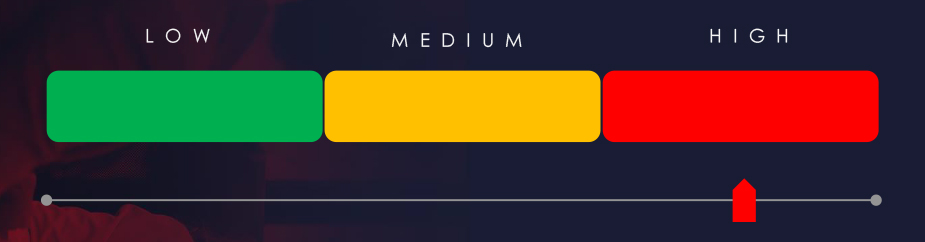
Risk Level Indicator: High
In the past 90 days, finance organizations have been significantly impacted by advanced persistent threat (APT) campaigns. Notably, 75% of observed APT campaigns targeted the finance sector, with 6 out of 8 total campaigns affecting this industry.
Monthly Trends
An analysis of monthly trends revealed a mild growth in APT activity from mid-February to April. However, this was followed by a period of no detections until mid-May, indicating a temporary lull in attacks.
Key Threat Actors
The most active threat actors identified were the Lazarus Group from North Korea and the Chinese APT Mustang Panda. Additional detections came from MISSION2025, Hafnium, and the Iranian US17IRGCorp. Lazarus Group in particular have been strategically focusing on financially motivated attacks, with an emphasis on targets in Japan.
Geographical Impact
The campaigns impacted a total of 25 countries, with Japan being the hardest hit. Other significantly affected countries included the United States, the United Kingdom, Australia, and Germany. This geographical spread correlates with the broad strategic interests of involved nation-states sponsoring these threat actors.
Targeted Technologies
Web applications emerged as the most targeted technology within these campaigns. Additionally, operating systems, IaaS solutions, and cloud technologies were also compromised, reflecting a diverse range of attack vectors employed by the threat actors.
Over the past 3 months, CYFIRMA’s telemetry detected 45,232 phishing campaigns themed around finance out of a total of 333,500.
The chart below illustrates the global distribution of observed themes. Financial and Payment Services account for 13.56% of all captured phishing attempts.
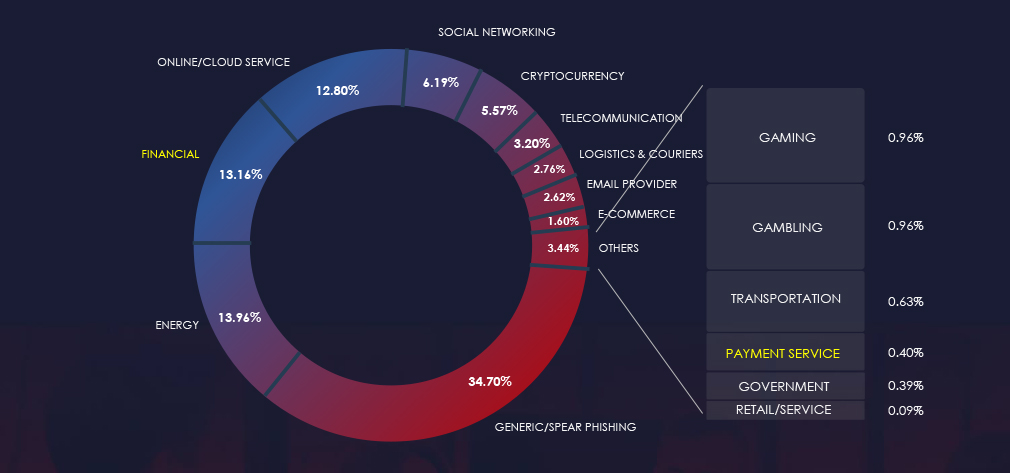
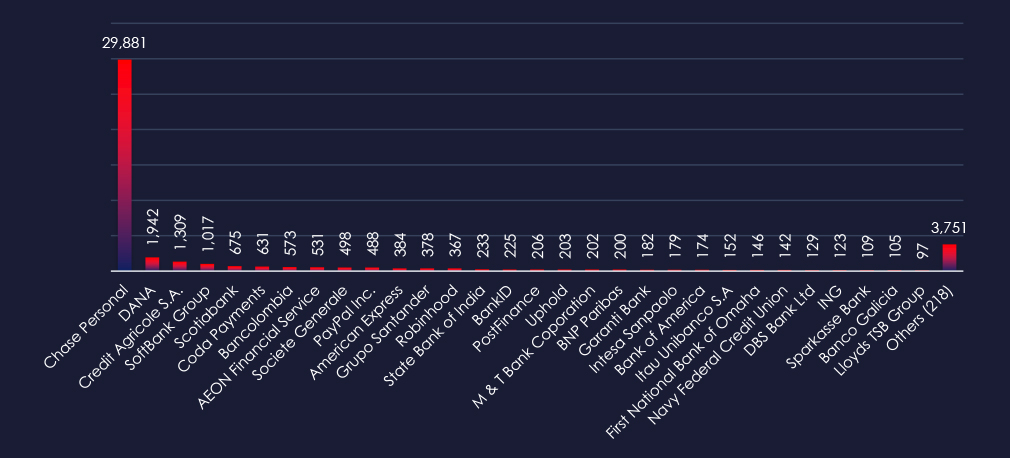
While American Chase Personal Banking faced a high-volume impersonation campaign in the past 90 days, the remaining observed brands show high geographical diversity and variety of services from traditional banks to fintech platforms.

The geographical sources of observed phishing campaigns closely correlate with the impersonated brands. Additionally, the United States serves as a significant source for many international campaigns, owing to the large number of compromised devices utilized in botnets, which are then used to distribute phishing attacks.
Risk Level Indicator: High
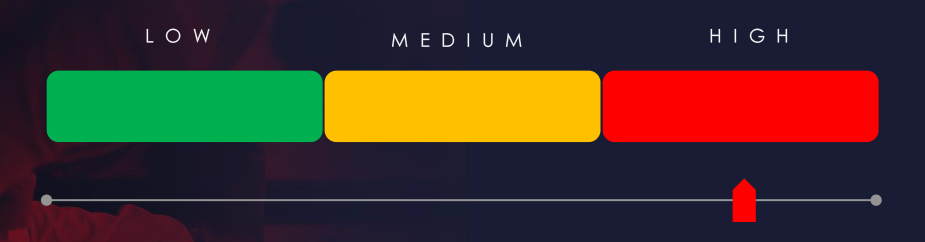
The financial sector remains a highly popular phishing theme due to the direct monetization avenue for threat actors, retaining a high-risk indicator.
Chase Personal Banking stands out as the most impersonated brand, indicating a large U.S. phishing campaign in the last 90 days. Following this, DANA (Indonesia), Credit Agricole (France), and AEON Financial Service (Japan) are also significantly targeted.
Overall, the list includes 248 organizations from 67 countries, such as Grupo Santander (Spain), State Bank of India (India), and Garanti Bank (Turkey), underscoring the worldwide nature of these threats. Notably, besides traditional banks, payment services, and newer financial platforms highlight the broad scope of phishing activities.
ASN-origin data reveals that the United States is the leading source of phishing emails impersonating financial organizations, reflecting the extensive financial sector in the U.S. and the vast number of compromised devices used in botnets to send phishing emails. Significant activity is also observed in Germany, Canada, and the Netherlands for similar reasons. Southeast Asia and Latin America are steadily growing as sources and targets of global finance-themed phishing. Additionally, we are observing an increasing number of African nations such as Angola, Mozambique, and Gabon becoming sources of phishing beyond the top 30 listed.
The presence in both developed and developing nations highlights that phishing campaigns are opportunistic and globally pervasive. Regional variations suggest more sophisticated attacks in high-count countries, while lesser-known regions like Turkmenistan show expanding attacker reach.
In the past 90 days, CYFIRMA has identified 65 verified ransomware victims in the finance industry. This accounts for 5.3% of the overall total of 1,216 ransomware victims during the same period.
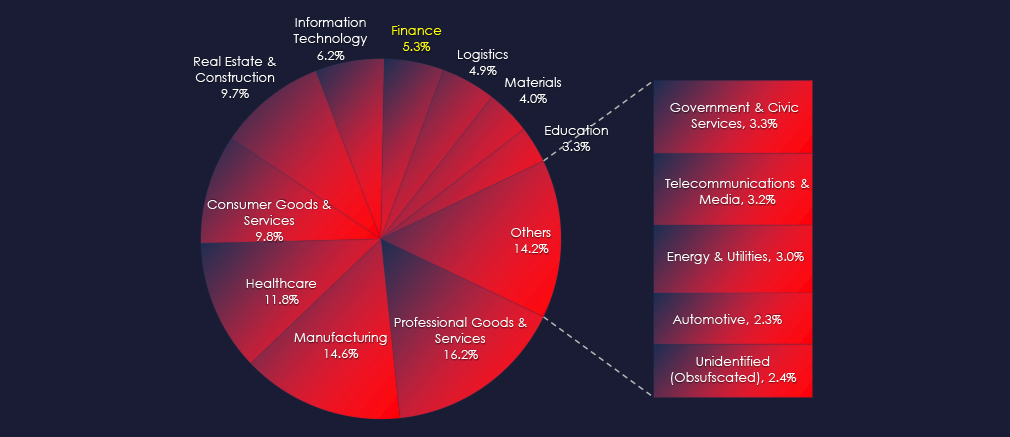
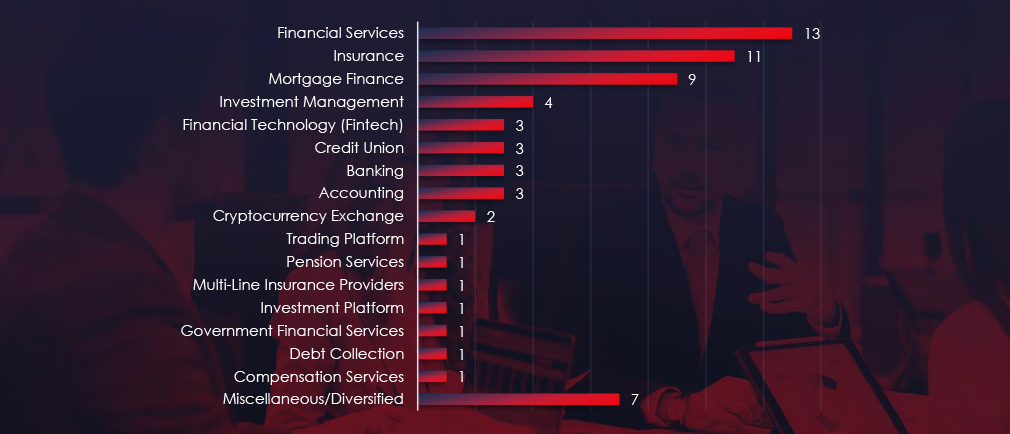
Financial services, Insurance and Mortgage finance are the most frequent victims of ransomware in finance industry.
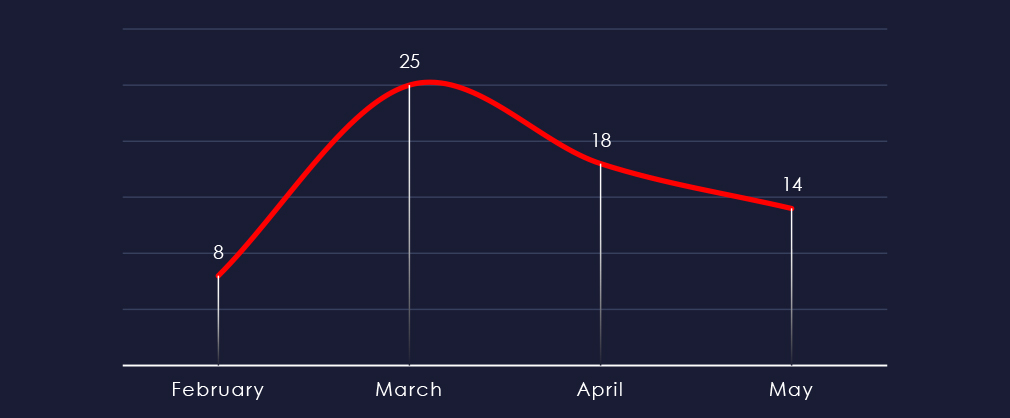
Considering partial months of February and May, we can see relatively consistent numbers of victims with uptick in March.
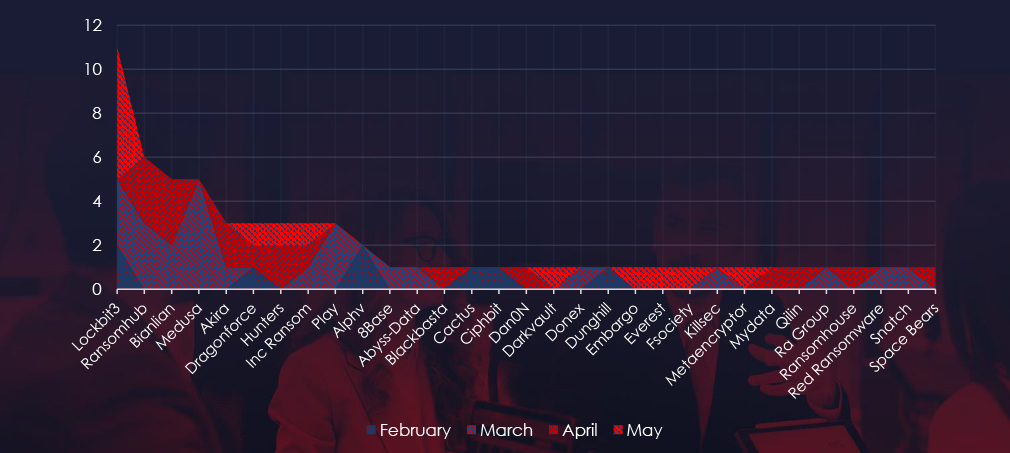
A breakdown of the monthly activity provides insights into which gangs were active each month. For example, Medusa and Play gangs recorded all their victims in March and contributed to March uptick.
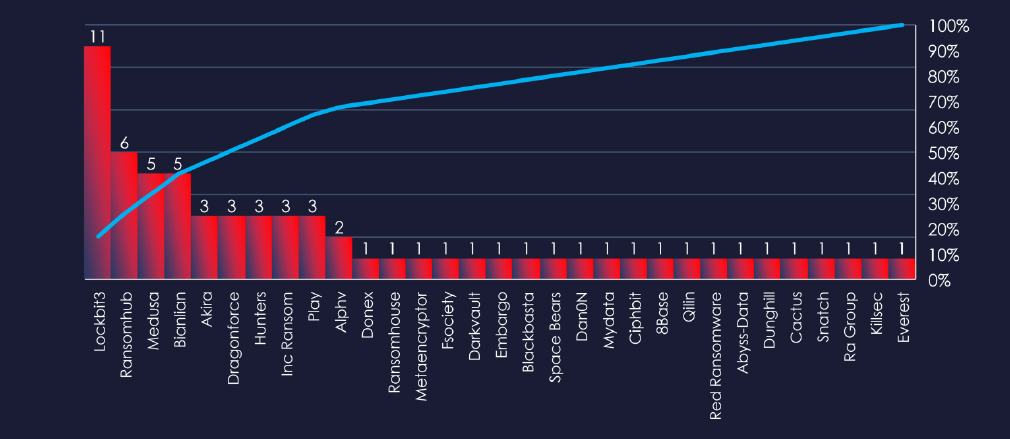
In total 31 out of 54 active groups recorded finance organization victims in the past 90 days. Notable is high distribution among large number of groups in this period.
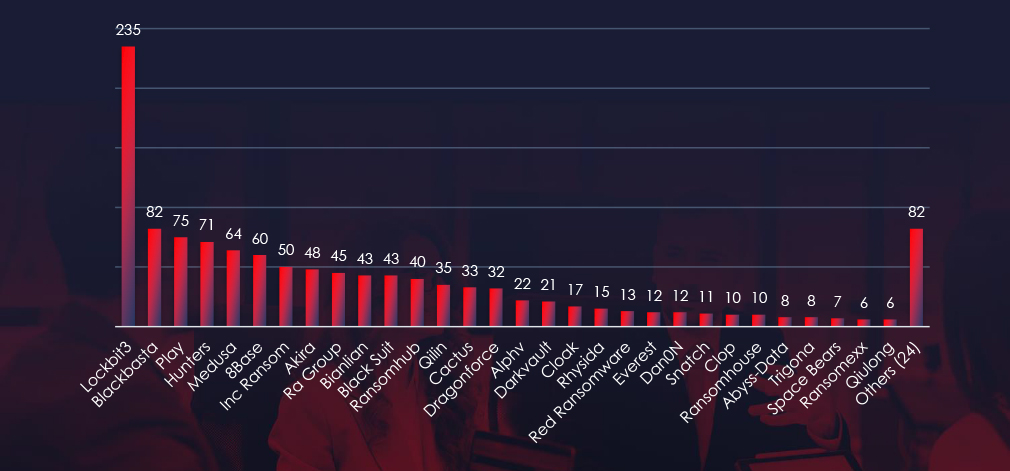
Comparing the finance industry to all recorded victims, none of the gangs particularly stands out with high percentage of victims in this industry. Highest are Ransomhub with 6 out of 40 (15%) and Bianlian with 8 out of 72 (11.6%).
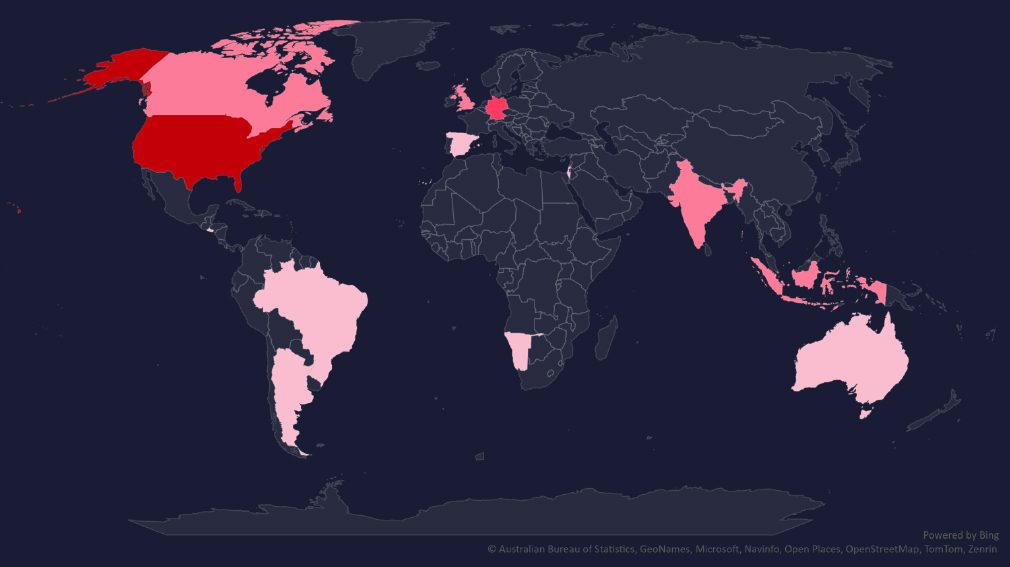
The geographic distribution heatmap underscores the widespread impact of ransomware, highlighting the countries where victims in this industry have been recorded.
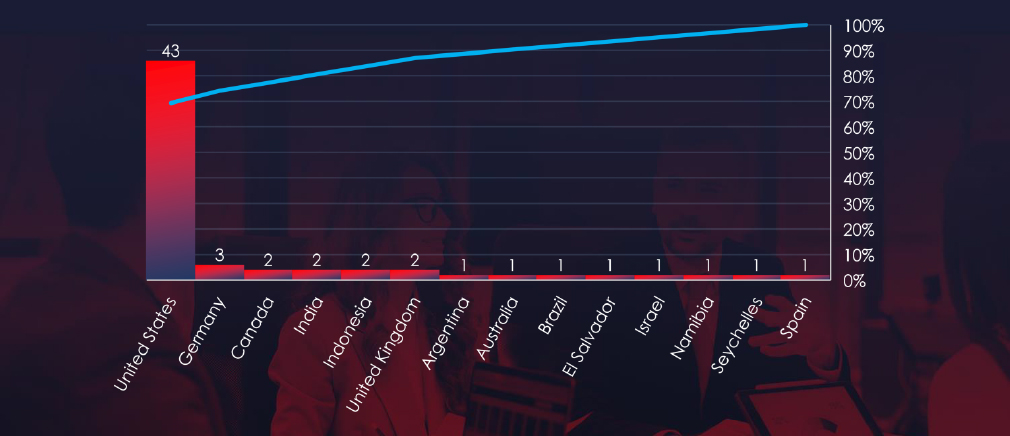
In total 14 countries recorded ransomware victims with the US alone accounting for ~69% of all victims with identified geography.
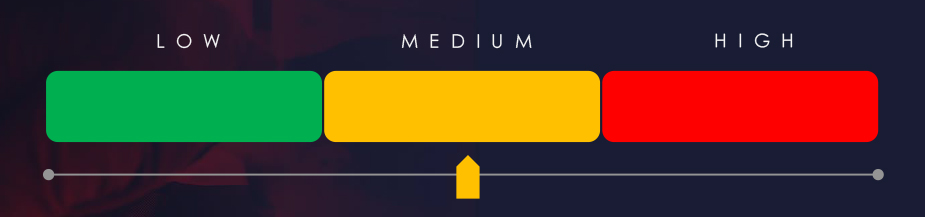
Risk Level Indicator: Moderate
The finance industry placed with 7th most victims. It faces a significant ransomware threat, with attacks affecting a wide range of sub-sectors and a broad geographic distribution. The steady monthly activity, coupled with the involvement of numerous ransomware groups, highlights the pervasive and ongoing risk.
Monthly Activity Trends
Ransomware activity in the finance industry has shown relatively consistent numbers of victims each month. However, there was a noticeable uptick in March:
Medusa and Play gangs recorded all their victims in March, contributing to the spike in activity during this month.
Ransomware Gangs
A total of 31 out of 54 active ransomware groups targeted the finance industry in the past 90 days:
Ransomhub: 15% of their victims were from the finance industry (6 out of 40 victims).
Bianlian: 11.6% of their victims were from the finance industry (8 out of 72 victims).
The distribution of attacks among many groups indicates no single gang dominated the ransomware landscape in the finance sector.
Geographic Distribution
The geographic distribution of ransomware victims in the finance industry highlights the widespread nature of these attacks:
69% of all victims with identified geography are located in the US.
In total, 14 countries reported ransomware victims in the finance industry
For a comprehensive, up-to-date global ransomware tracking report, please refer to our new monthly “Tracking Ransomware” series here.
In the past 90 days, finance organizations have faced medium to high risk across monitored categories.
APT campaigns targeted the finance sector extensively, with 75% of observed campaigns impacting this industry, particularly affecting countries like Japan and the United States. Monthly trends showed a mild growth in APT activities from mid-February to April, followed by a temporary lull until mid-May. The Lazarus Group and Chinese APT Mustang Panda were the most active threat actors.
Phishing remains a prevalent impersonation threat, with the financial sector being a prime target due to its direct monetization potential. Chase Personal Banking was the most impersonated brand, indicating a large U.S.-based campaign. Regional financial platforms such as DANA (ID), AEON (JP) or Robinhood (US)are now on par with traditional banks. The phishing threat is globally pervasive, impacting 248 organizations across 67 countries, with significant activity originating from the United States, Germany, Canada, and growing regions like Southeast Asia, Latin America, and even Africa.
Ransomware attacks also pose a significant risk, placing the finance industry as the 7th most targeted sector. The industry experienced consistent monthly activity with a noticeable spike in March due to the Medusa and Play gangs. Out of 54 active ransomware groups, 31 targeted the finance sector, with attacks being geographically widespread, notably affecting the United States. This diverse and persistent threat landscape underscores the ongoing and multifaceted ransomware risks facing the finance sector.