



The CYFIRMA Industry Report delivers original cybersecurity insights and telemetry- driven statistics of global industries, covering one sector each week for a quarter. This report focuses on the automotive industry, presenting key trends and statistics in an engaging infographic format.
Welcome to CYFIRMA infographic industry report, where we delve into the external threat landscape of the automotive industry over the past three months. This report provides valuable insights and data-driven statistics, delivering a concise analysis of attack campaigns, phishing telemetry, and ransomware incidents targeting automotive technology and manufacturing organizations.
We aim to present an industry-specific overview in a convenient, engaging, and informative format. Leveraging our cutting-edge platform telemetry and the expertise of our analysts, we bring you actionable intelligence to stay ahead in the cybersecurity landscape.
The automotive industry witnessed 11 campaigns, a seemingly modest count, yet remarkable given its specific focus. The notable spike in observed campaigns during July can be attributed to heightened activity from the Lazarus Group, along with financially motivated attacks by TA505 and FIN7.
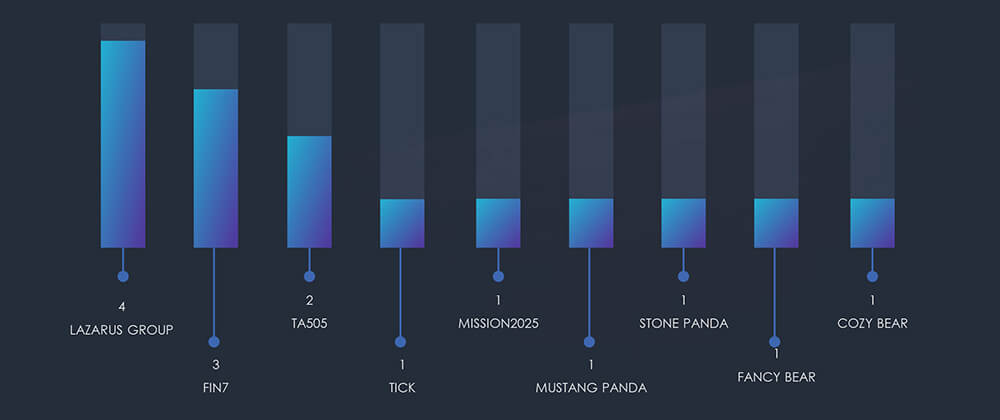
Lazarus Group, FIN7, and TA505 remain the prime suspected threat actors, reinforcing the trend observed in the previous logistics and transportation industry report. Notably, financially motivated APTs show a significantly higher level of interest in this sector compared to nation-state APTs.
It is important to highlight that MISSION2025 serves as a focal point for Chinese APT activity, with several Pandas suspected to overlap as part of the TA threat group.
The attack campaigns targeting organizations in the automotive industry align with economies renowned for their developed automotive sectors. Moreover, Southeast Asia and India are steadily emerging as prominently targeted regions by sophisticated APTs.
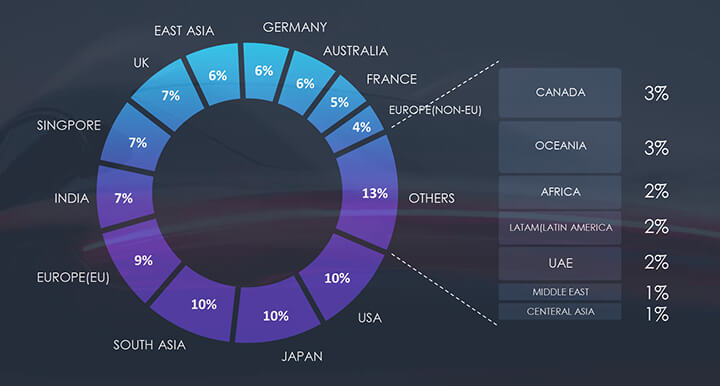
Due to the overlapping nature of monitoring telemetry, further breakdown beyond the top 10 countries is calculated for regions rather than individual countries to maintain clarity.
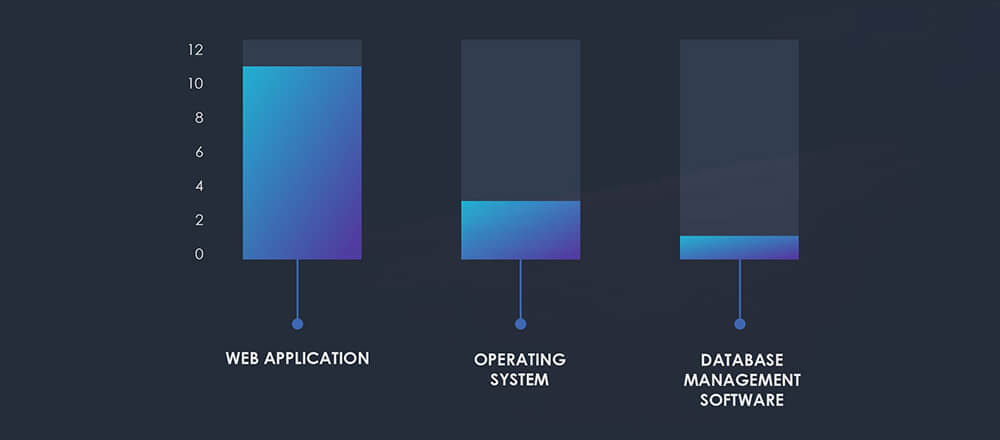
Analyzing the technologies targeted by APTs affirms a continued prominence of exploiting vulnerabilities within web applications, overshadowing other technologies. Following are operating systems and database management software.
Phishing attacks explicitly targeting or impersonating the automotive industry are sporadic. Over the past 3 months, CYFIRMA’s telemetry recorded 191 phishing attacks out of a total of 206,410, making up only 0.09% of the share.
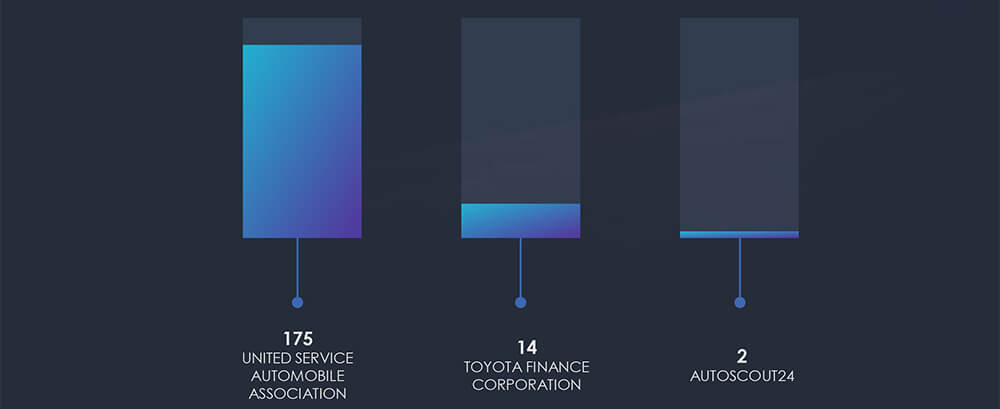
Our observations yielded only 3 organizations in the automotive industry, with two of them being financial services and one being a German car marketplace.
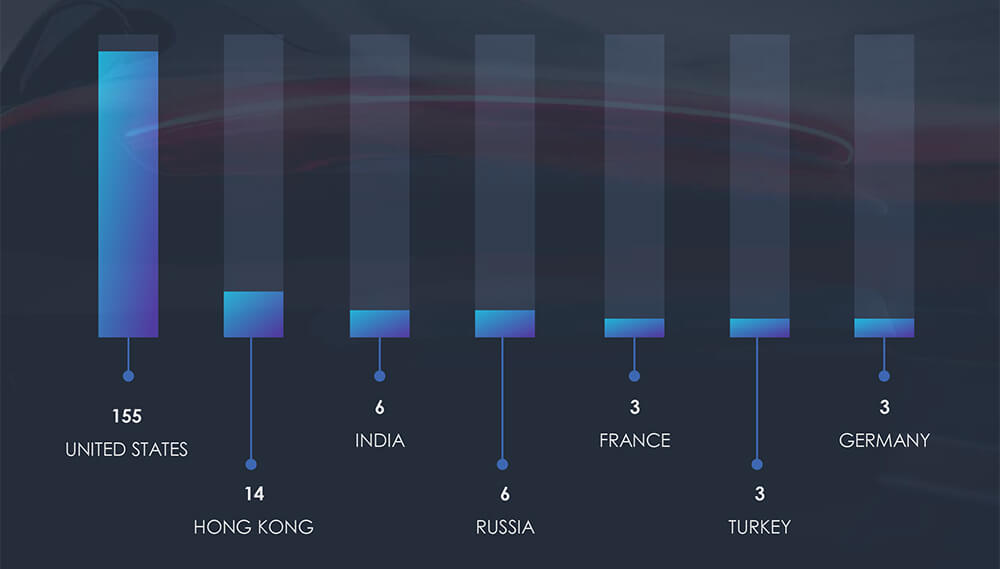
Given the limited number of known organizations, the respective geographies of origin are quite straightforward. For the German car marketplace; AutoScount24, the origin is Germany. All Toyota Finance phishing incidents originate from Hong Kong, while USAA phishing largely originates from the United States, with a few instances bouncing through different countries, as indicated below.
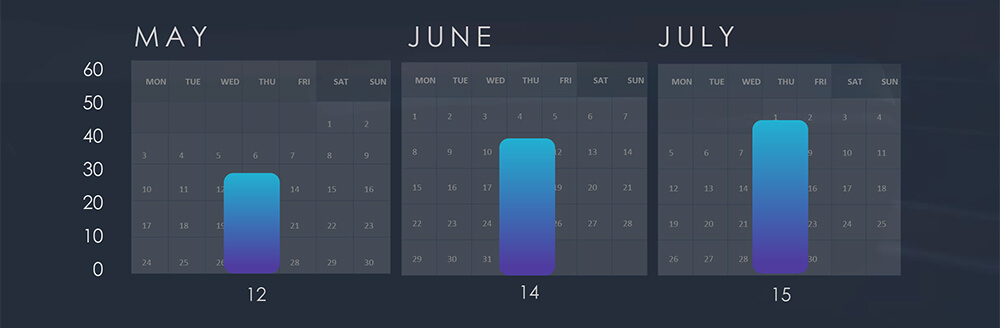
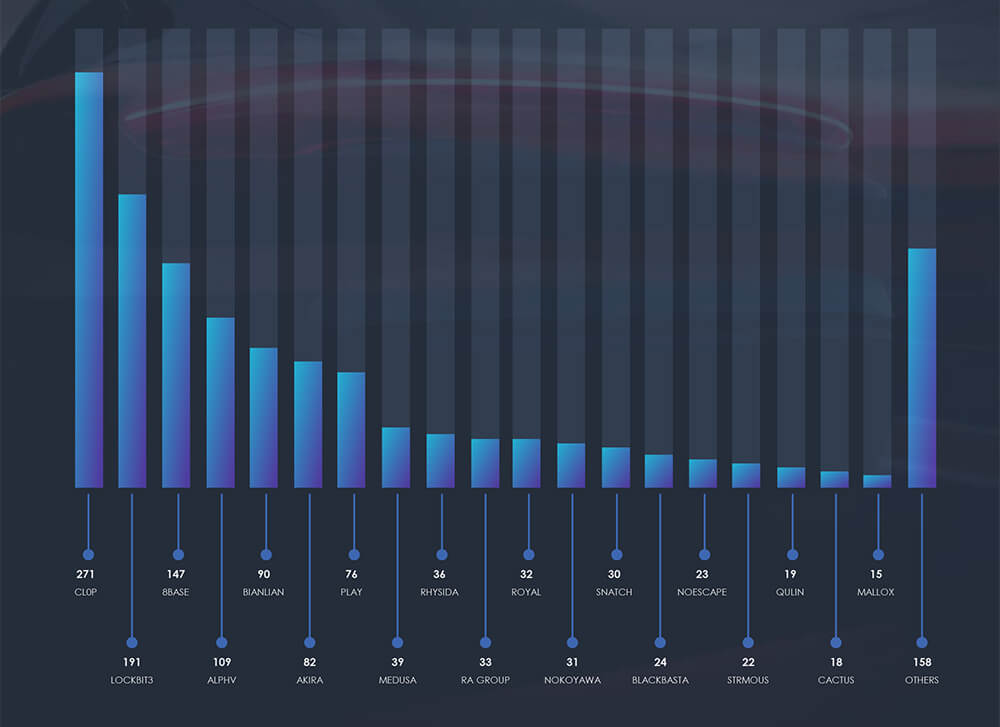
Over the last 90 days, CYFIRMA observed verified 41 ransomware victims in automotive industry. That is out of the overall total of 1,446 incidents, accounting for 2,8% of all ransomware victims during the same period, a noteworthy figure considering the industry’s specific focus.
While the number of incidents per month show a slight increase of one and two, respectively, it is not sufficient to project a definitive trend. Nonetheless, a point of interest worth monitoring.
Examining the monthly activity breakdown of each group reveals that significant players such as Lockbit3, Blackbasta, and Banlian reported the majority of their victims during June, exhibiting lower volumes in other months. Similarly, Akira, ALPHV, and Black Suit also reported a considerable number of victims in June.
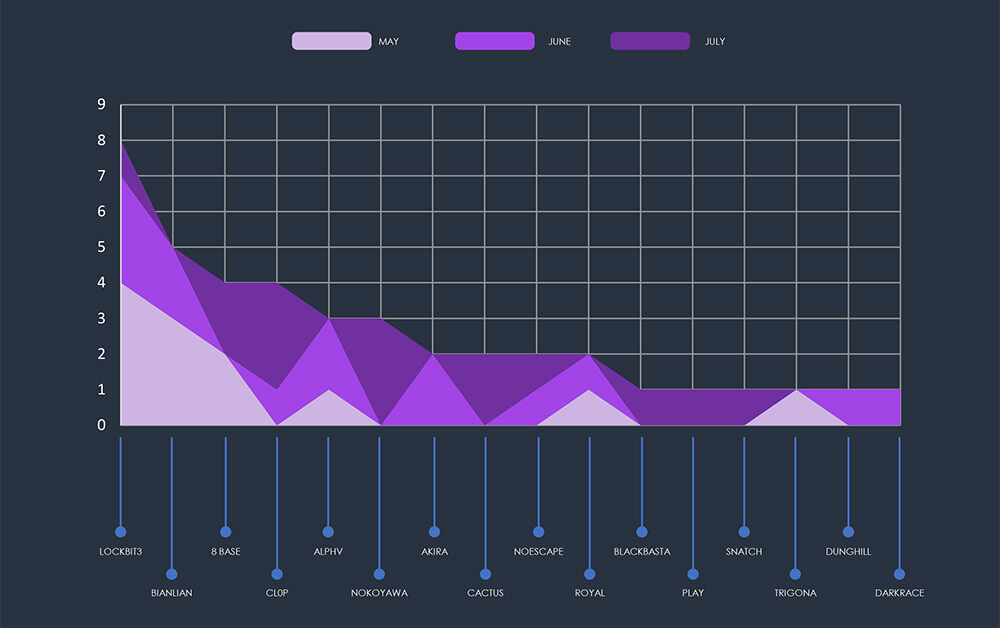
The distribution of incidents per group, indicates varying levels of interest in automotive victims, amongst different threat actor groups.
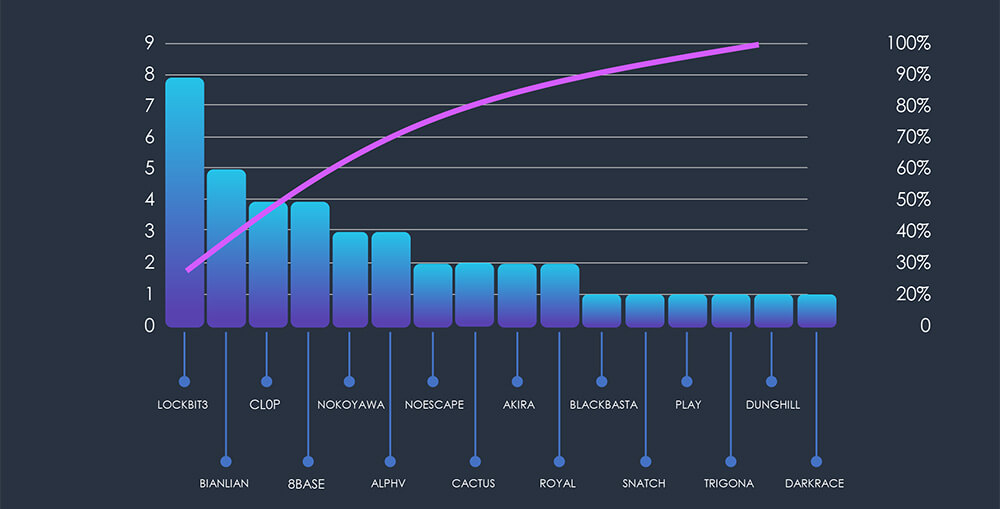
In most cases, the respective automotive victim count per group aligns with the total counts. However, Cl0p stands out with remarkably fewer automotive victims, while Play reports only a single victim. Furthermore, Medusa, RA Group, and Rhysida gangs did not record any automotive victims.
Among the 41 known victims, the United States emerges as the most affected by ransomware attacks in the automotive industry, comprising of 22 cases. This reinforces the US’s status as a prominent target across industries, owing to its economic significance and robust digital infrastructure.
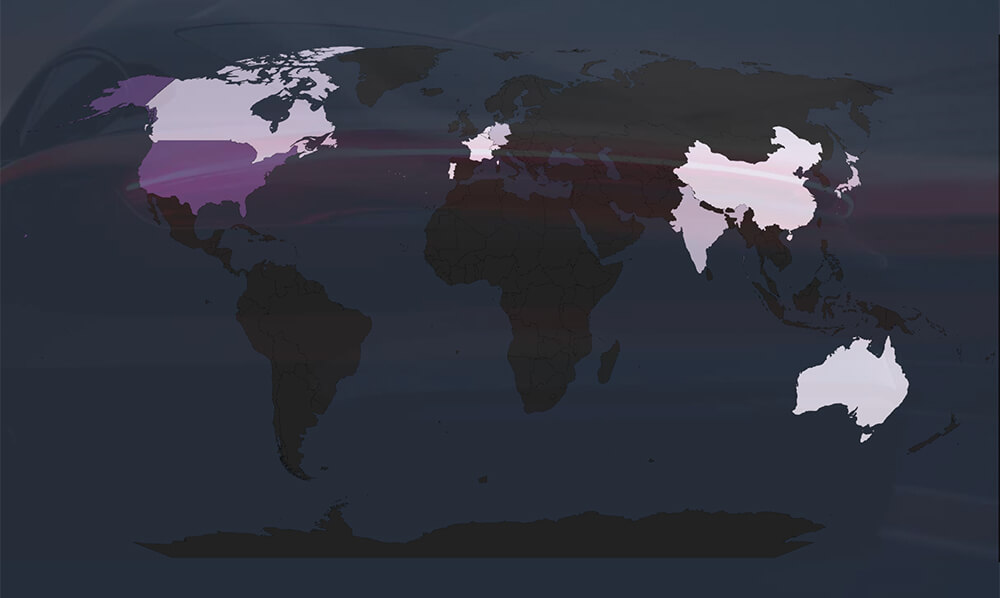
Global Spread – The remaining known incidents with identified victim countries include Japan, Germany, India, and Canada, each having 2 victims.
Together with the USA, these countries collectively account for 81% of all victims.
In contrast to the previous report on the logistics and transportation industry, where ransomware incidents were spread globally, the automotive industry’s victims show a notable correlation with countries renowned for their automotive sectors.
The distribution of ransomware incidents in the past 90 days observed a wide variety of sectors within the automotive industry.
Victims are broadly divided between dedicated automotive (Automotive / *) and Manufacturing with notable automotive clients (Manufacturing / *).
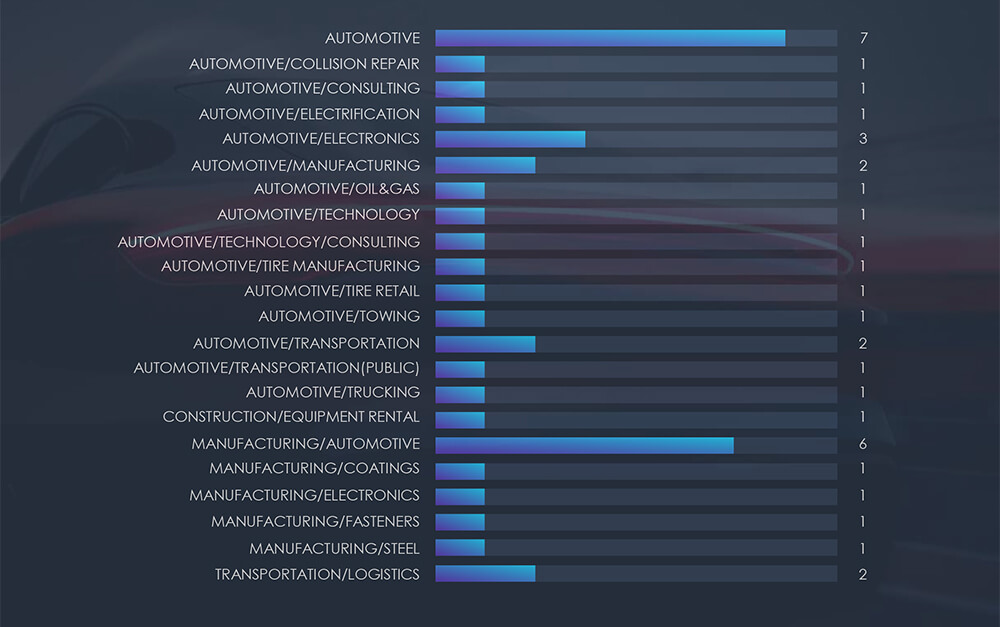
The data reinforces that manufacturing, including the automotive sector, remains among the hardest-hit industries. These sectors share a common vulnerability, where even a brief service disruption incurs high costs, providing cybercriminals with significant leverage to enforce ransom demands.
Furthermore, the ransomware’s broad targeting reveals a diverse range of victims, ranging from towing and collision repair to tire and coating manufacturing. This underscores the opportunistic nature of ransomware attacks, where organizations seemingly unrelated to cyberspace become unsuspecting victims.
The automotive industry stands out as one of the most targeted sectors in the already hard-hit manufacturing industry when it comes to cyberattacks. Its susceptibility to financially motivated threat actors, particularly those employing ransomware, is a major concern due to the high cost of outages.
Additionally, the automotive industry’s specialized supply-chain, concentrated in developed economies, further increases its allure to potential attackers.
As for phishing campaigns, statistics indicate that brand impersonation is not as prevalent as in other industries. Instead, these campaigns appear to be primarily focused on finance and marketplace-related schemes, leveraging the “spray and pray” approach to quickly monetize their efforts.