


Between May and August 2025, CYFIRMA observed sustained cyber operations against the global defence sector, driven by both state-aligned groups and criminal actors. Campaigns linked to the People’s Republic of China (PRC) concentrated on exploiting telecommunications and network infrastructure to secure long-term access, while Russian operations targeted logistics and transport contractors with the intent of disrupting defence supply chains. North Korean actors pursued both financial gains and intellectual property theft, while Iranian groups focused on politically motivated intrusions tied to regional tensions, and cybercriminal groups continued to exploit cloud misconfigurations and subcontractor access as pathways for extortion.
Monitoring of underground forums and Telegram channels revealed a surge in data breach and leak activity, accompanied by a sharp decline in ransomware chatter. This indicates a broader shift away from encryption-based attacks toward direct data theft and leak-driven extortion. Hacktivist groups, though less sophisticated, carried out disruptive operations that aligned with ongoing geopolitical narratives.
CYFIRMA assesses that the defence sector now faces a convergence of espionage and monetization threats, with cloud environments and supply-chain dependencies consistently emerging as the most exploited vulnerabilities.
Cyber campaigns against defence organizations are directly influenced by ongoing conflicts, rivalries, and political objectives.
Together, these campaigns underline the convergence of geopolitical ambitions and cyber intrusion capabilities.
May 2025 — Allied advisory and operational warnings
May 21, 2025: The UK and allied partners published a public advisory warning of Russian state-aligned campaigns targeting organizations involved in the delivery of support to Ukraine (logistics, transport, air/sea, and defence suppliers). This advisory emphasized espionage and disruptive operations against defence-adjacent targets.
June ? July 2025 — Scaling cloud abuse and ransomware activity
June and July observed a higher frequency of cloud scanning, credential stuffing, and initial access brokering focused on misconfigured cloud endpoints and leaked credentials. Ransomware groups refined cloud-native techniques for directly encrypting cloud storage and disabling backups.
August 2025 — High-visibility advisories
CISA, FBI, NSA, and international partners released a joint advisory describing widespread Chinese-state-aligned compromises affecting telecommunications, government, infrastructure, and military support networks. The advisory documented long-term persistent access and detailed network-device-focused TTPs (router compromise, SNMP/TACACS abuse, and on-box container use for staging/exfiltration).
PRC State-Aligned Clusters remained the most consistent in their activity. By exploiting network devices and leveraging built-in management functions, such as SNMP and TACACS+, they avoided detection and entrenched themselves within telecommunications backbones. Their overarching goal remained theft of defence-related technologies and intellectual property. PRC-aligned actors continue exploiting network device vulnerabilities to maintain persistence within telecommunications service providers. Despite extensive public exposure of these tactics, such operations almost certainly remain active.
Russian operations are very likely focused on disrupting defence supply chains, as indicated in the May 2025 UK–allied advisory. Instead of striking prime contractors directly, they infiltrated logistics providers and IT service firms, undermining resilience by disrupting the flow of material and operational data.
North Korean Campaigns likely combined espionage with monetization. Intellectual property theft frequently accompanies extortion attempts, indicating that Pyongyang views cybercrime as both a strategic instrument and a source of revenue.
Iranian Threat Actors followed politically motivated attacks in alignment with regional developments. Their campaigns were less global in scale but carried symbolic weight in targeting Western-linked entities.
Cybercriminal Enterprises exploited the same vulnerabilities as states, especially cloud misconfigurations and subcontractor access. Their campaigns were dominated by data theft and leak-based extortion, marking a decline in encryption-focused ransomware.
Hacktivist Groups, while technically limited, amplified propaganda and sought visibility by claiming credit for brief disruptions. Pro-Russian groups frequently boasted of Distributed Denial-of-Service attacks against Western defence portals, leveraging short-lived disruptions for outsized media attention.
CYFIRMA monitored closed Underground and dark web forums between May and August 2025. Chatter volume across key categories provides insight into threat actor focus areas against the defence and law enforcement sectors.
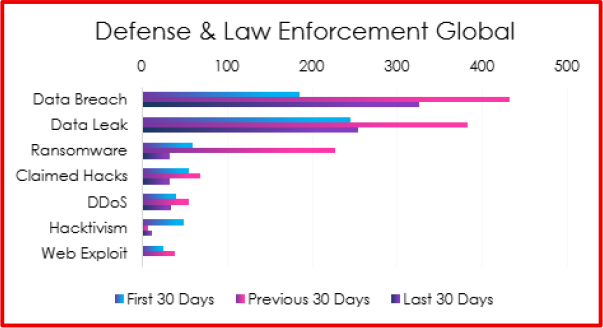
The data shows that data breaches and leaks dominate underground discourse, with 326 and 254 posts, respectively, in the last 30 days. While both categories have dropped from their May–June peak (432 and 383, respectively), the consistently high volume underscores the continued monetization of stolen defence-sector data. Several of these breach and leak claims aligned with indicators we validated in subcontractor incidents, strengthening confidence that at least a subset of the chatter corresponds to real compromises.
In sum, underground and dark web intelligence confirms the telemetry-based findings: data exfiltration and extortion remain the dominant threat, while ransomware encryption, web exploitation, and traditional DDoS are secondary tactics.

On August 31, 2025, a threat actor claimed to have leaked data associated with the Defence Research and Development Organization (DRDO) of India. The actor advertised the package for sale at a price of $5,000 USD. However, the threat actor did not disclose the source of the breach or how the data was obtained.

On August 21, 2025, a threat actor claimed responsibility for launching a Distributed Denial-of-Service (DDoS) attack against multiple government entities in Saudi Arabia.
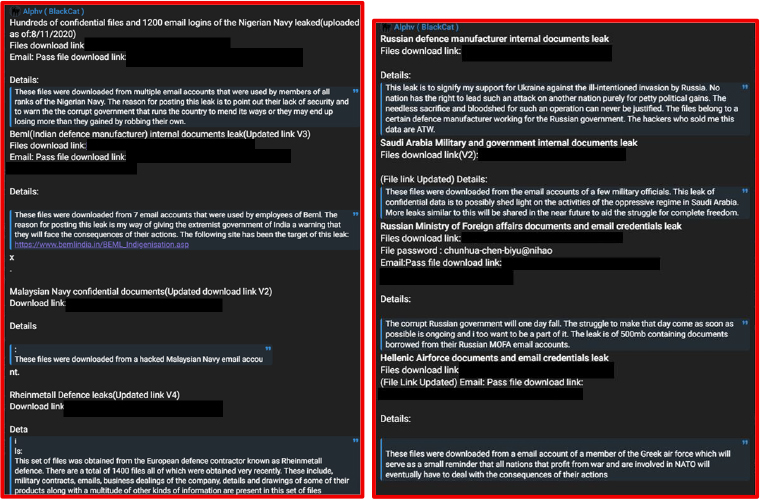
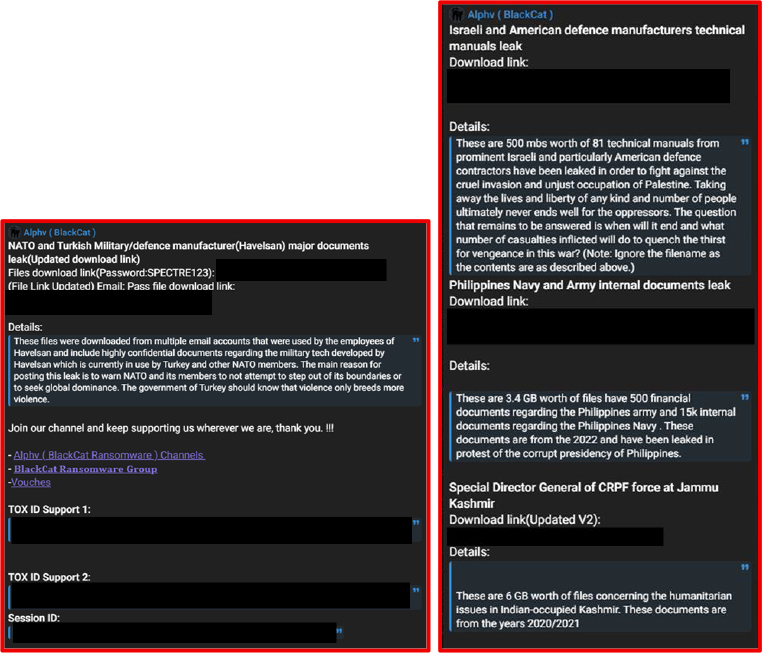
On August 8, 2025, a threat actor claimed to have leaked data allegedly linked to multiple defence agencies worldwide, including those in India, Bangladesh, Israel, the United States, Malaysia, Turkey, and NATO. The dataset appears to be a combination of both previously exposed (old) and newly obtained information. The source of the breach and the exploitation method were not disclosed.
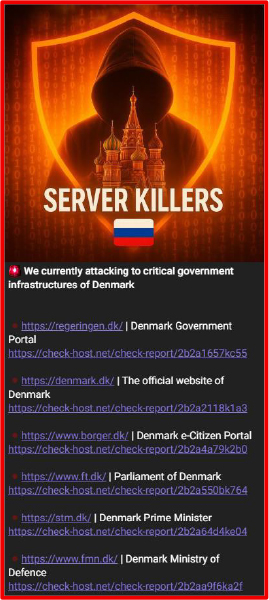
On August 5, 2025, a threat actor claimed responsibility for launching a Distributed Denial-of-Service (DDoS) attack against multiple government entities in Denmark.
On August 5, 2025, a threat actor claimed responsibility for launching a Distributed Denial-of-Service (DDoS) attack against the Ministry of Defence of Thailand.
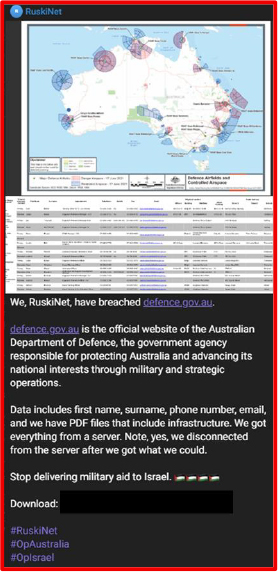
On August 3, 2025, a threat actor claimed to have leaked data allegedly associated with the Australian Department of Defence. The dataset reportedly includes first names, surnames, phone numbers, and email addresses, along with PDF files that appear to contain infrastructure-related information. The threat actor did not disclose the source of the breach or the method of exploitation.
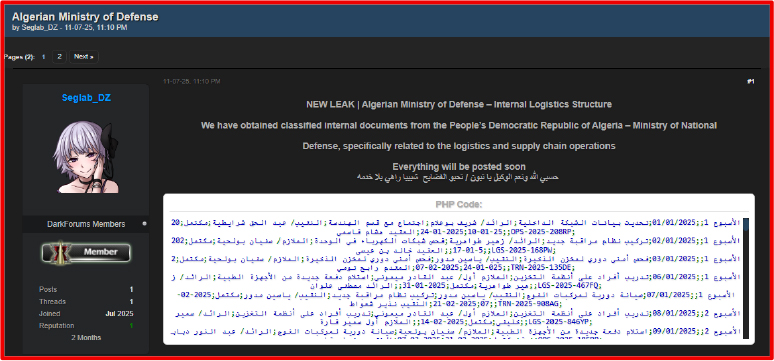
On July 11, 2025, a threat actor “Seglab_DZ” claimed to have leaked data allegedly belonging to the Ministry of Defence of Algeria. The actor did not disclose the source of the breach or the method of exploitation.
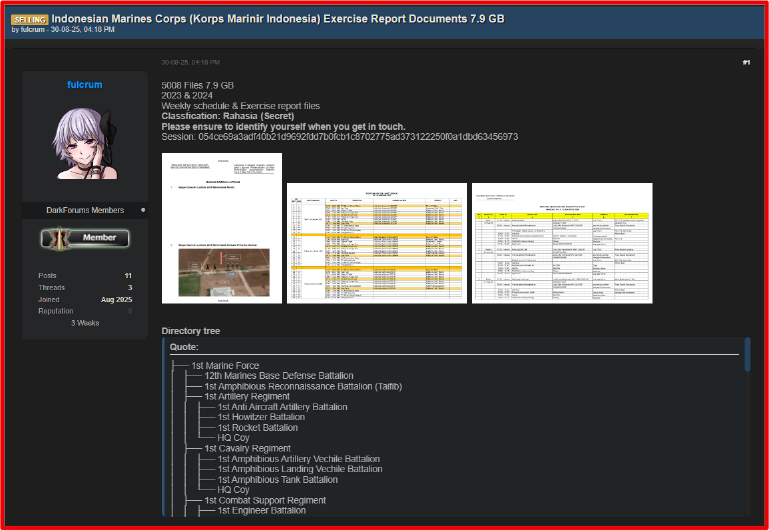
On August 30, 2025, a threat actor using the alias “fulcrum” claimed to have leaked data allegedly associated with the Indonesian Marine Corps. The actor did not disclose the source of the breach or the method of exploitation.
On June 9, 2025, a threat actor “zabanian” claimed to have leaked data allegedly associated with the Nigerian Navy. The actor did not disclose the source of the breach or the method of exploitation.
This section describes the most consequential and frequently observed tactics, techniques, and procedures affecting the defence organizations.
1) Cloud account compromise & misconfiguration abuse (highest frequency & impact)
Attackers now frequently deploy their own cloud infrastructure for command-and-control and data exfiltration, complicating attribution efforts.
2) Supply-chain & third-party compromise (highest leverage)
Third-party incidents often result in delayed detection because victims of initial compromises are not the primary defence organizations.
3) Spear-phishing & Enhanced social engineering
4) Network device compromise & data capture (router/ISP targeting)
5) Living-off-the-land & stealth persistence
6) Cloud-native ransomware & extortion
The investigation over the past 90 days confirms that the defence sector remains a high-value target for both state-aligned and criminal actors. PRC clusters demonstrated persistence in telecom and enterprise network infrastructure, exploiting device features to maintain covert access and harvest credentials. Russian activity focused on logistics and transport contractors, aiming to disrupt supply chains and collect operational data. DPRK groups combined intellectual property theft with aggressive financial intrusions, while Iranian actors maintained politically motivated targeting during periods of heightened tension. Cybercriminal groups amplified risk by adopting cloud-native techniques and abusing subcontractor and MSP access, with extortion and data-leak monetization as their core objective.
Dark web and Telegram intelligence reinforced these findings: data breaches and leaks dominate underground discussions, while ransomware chatter has declined as extortion pivots toward direct data theft and leak operations. Hacktivist and DDoS campaigns, although less technically advanced, contributed to disruptive activity aligned with geopolitical narratives. Overall, the defence sector faces a threat environment where espionage and financial crime converge, with supply chains and cloud environments repeatedly exploited as the weakest links.