Published On : 2024-07-22
CRYSTAL BALL SERIES
What cyber-related areas will evolve over 2024?
What new challenges will we face?
IN THIS INSTALMENT WE EXPLORE
ARTIFICAL INTELLIGENCE
GENERATIVE AI FOR DISINFORMATION

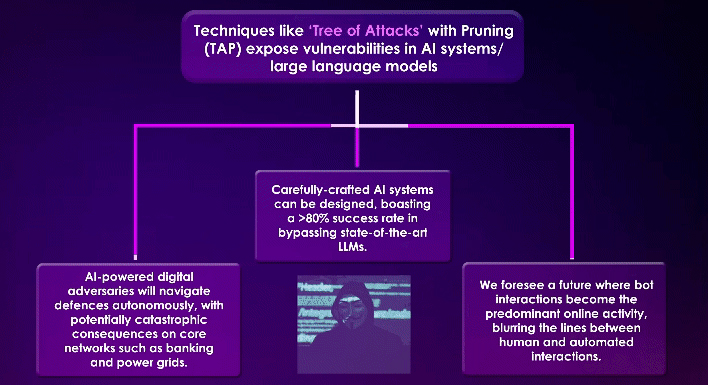
AI-POWERED CYBERSECURITY THREATS
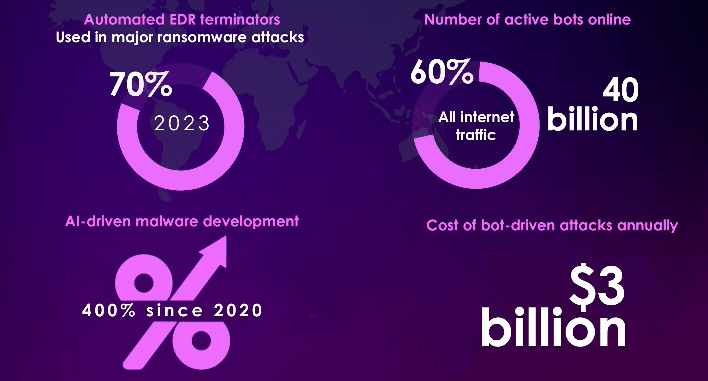
Al ADVANCEMENT IS PAVING THE WAY FOR DIGITAL ADVERSARIES

Al-powered adversaries’ infiltration of societal, political, and cultural spheres through tailored deceitful content signifies the rise of threat actors with capabilities to undermine trust and deepen societal rifts.
What we see in the future for LLMs
The cybersecurity market is valued at $250 billion. Adding up costs of lost revenue, reputational damage, etc. estimates predict cost of cybercrime to reach up to $1 trillion
CRYSTAL BALL SERIES
IN THIS INSTALMENT WE EXPLORE
PROTECTIONIST ECONOMIC POLICIES

Impact of Cybercrime Incidents
Damage & destruction of data | Financial Loss | Decreased productivity | Theft of intellectual property Personal & financial data | Embezzlement | Fraud | Operational Interruption
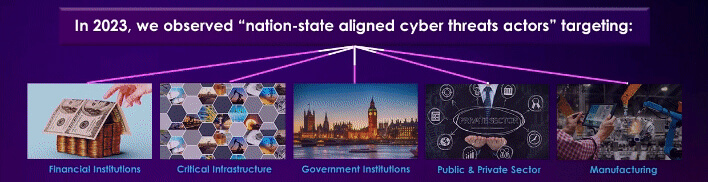
SURGE IN STATE-SPONSORED CYBER ATTACKS AMID PROTECTIONIST ECONOMIC POLICIES


CRYSTAL BALL SERIES
IN THIS INSTALMENT WE EXPLORE
Deceptive Manipulation: The rise of DEEPFAKES
This technology, powered by Al, is fictitious media compiled of known sounds (i.e. voices) and images (facial expressions and movements) with malicious
Global increase in deepfake fraud cases

% Increase in deepfake usage between 2022-2023

- North America- approx. 1700% increase.
- APAC Region- approx. 1500% increase.
- MEA Region- approx. 450% increase.
- Latin America- approx. 400% increase.

Implications of Deepfakes
- Identity Theft
- Risks of Reputational Damage
- Increase in Cyber Crime
- Disinformation
Deepfakes will become influential social engineering tools

More than 1600% increase
Global Deepfake Al Market rise from approx. $7B (2023) to $120B (2033)


Cybercriminals are actively seeking creators capable of producing flawless videos with perfect sound and seamless integration. This trend indicates a forthcoming increase in incidents.
CRYSTAL BALL SERIES
IN THIS INSTALMENT WE EXPLORE
RANSOMWARE ATTACK TRENDS
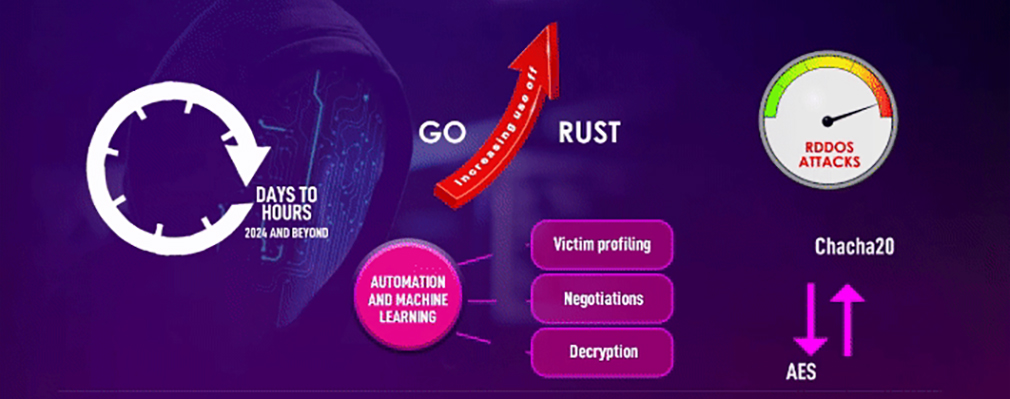
OPERATIONAL DWELL TIMES

TOP INITIAL ACCESS VECTORS
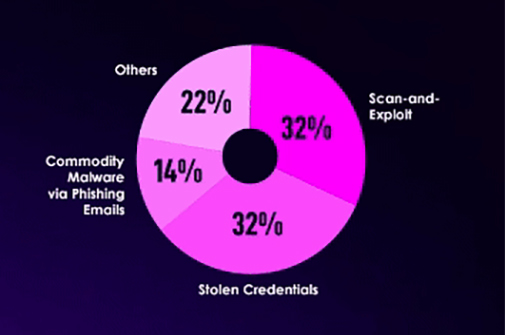
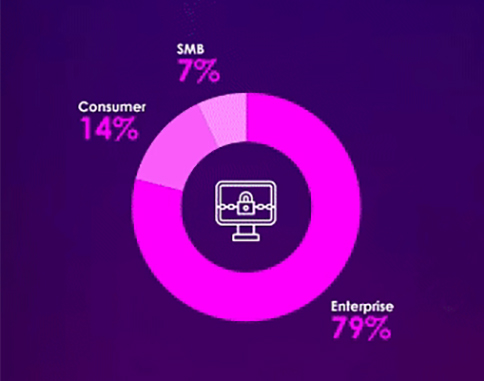
FILE DETECTIONS BY BUSINESS SEGMENT IN Q1 2024
MOST ACTIVE RANSOMWARE LANGUAGES

Ransomware Attacks Will Embrace Speed Over Stealth
| Asset Type |
Targeted Technologies |
Interested RaaS groups |
| Network Devices |
Cisco | Citrix | Fortinet | F5 |
Lockbit, Akira, Medusa |
| File Transfer Software |
GoAnywhere MovelT |
clOp |
| Pinters |
PaperCut |
Lockbit |
| Remote Access and Services |
Screenconnect
Microsoft (RDP)
Microsoft (Netlogon) |
Lockbit, Akira, Blackbasta |
| Email Gateways |
Microsoft (Exchange) |
Play, Bianlian |
ENCRYPTION ALGORITHMS OF PROMINENT GROUPS
- RSA-AES hybrid crypto system
- ChaCha20-Poly 1305
- AES-RSA
- ChaCha20 and RSA
- AES 256
- Salsa20
CRYSTAL BALL SERIES
IN THIS INSTALMENT WE EXPLORE
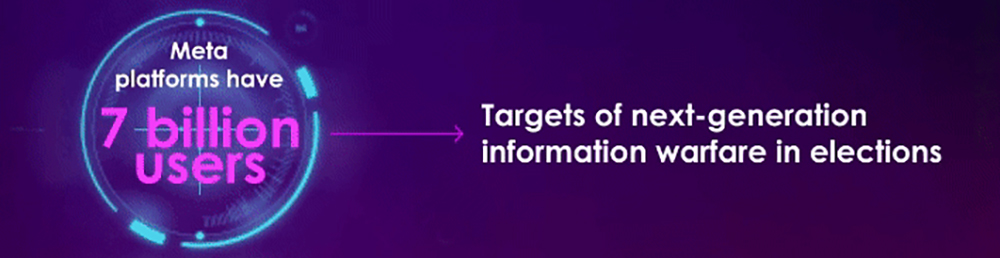
2024:THE YEAR OF ELECTIONS

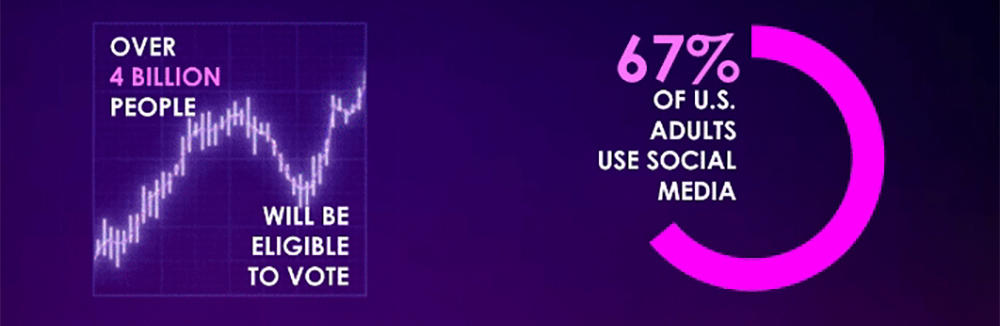
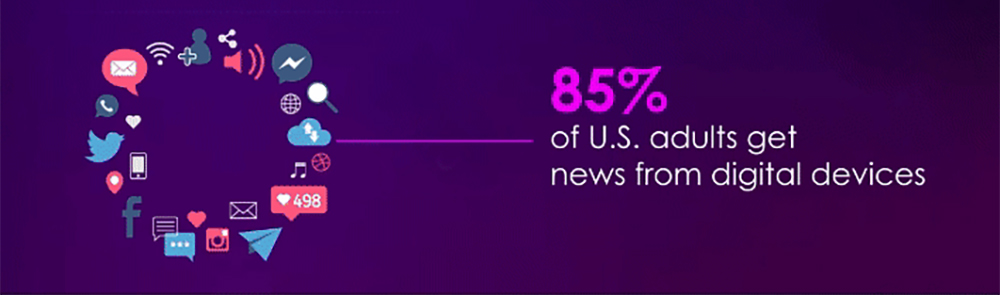
Election year will give rise to misinformation, and disinformation tradecraft
Digital publishing and Al enabled malicious actors will push their agendas widely and inexpensively.

The Future of Disinformation

CRYSTAL BALL SERIES
IN THIS INSTALMENT WE EXPLORE
SUPPLY CHAIN DEPENDENCIES : AN ESCALATING CYBERSECURITY CONCERN
Impact of Supply Chain Attacks
- Data Loss
- Disruption of Critical Operations
- Financial losses
- Reputational Damage

Prominent Supply Chain Attacks.
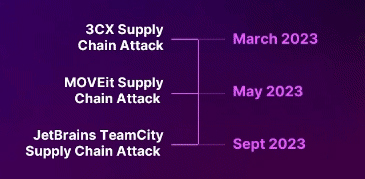
THREAT ACTORS WILL CONTINUE TO CAPITALIZE ON THIRD PARTIES AND SUPPLY CHAINS
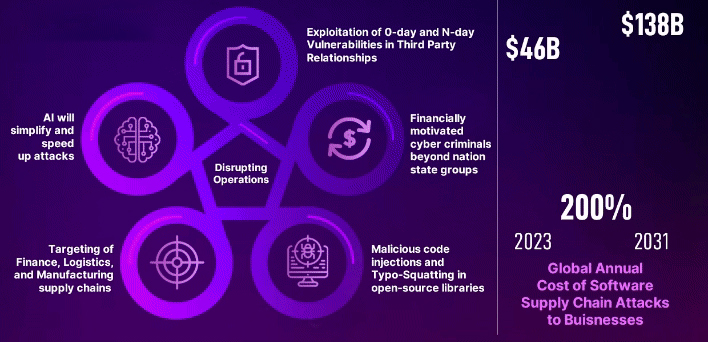
Global Supply Chain Attacks to Spike in 2024 and Beyond

Surge in Threats
CRYSTAL BALL SERIES
IN THIS INSTALMENT WE EXPLORE
THE GROWING THREAT OF CYBERCRIME IN THE ELECTRIC VEHICLE INDUSTRY
Strong security measures and regulations are critical to protect EVs from cyber threats.
EV Cybersecurity Incidents


China: 45% of all cars sold
Europe: 25% of all cars sold
United States: 11% of all cars sold
Reported EV charging vulnerabilities are expected to double by 2024

Dark Web Observations
EV company customer information currently on sale for $4000
- User IDs
- Names
- Emails
- CPFs
- Phone numbers
- Additional personal details
PERCENTAGE OF ATTACKS
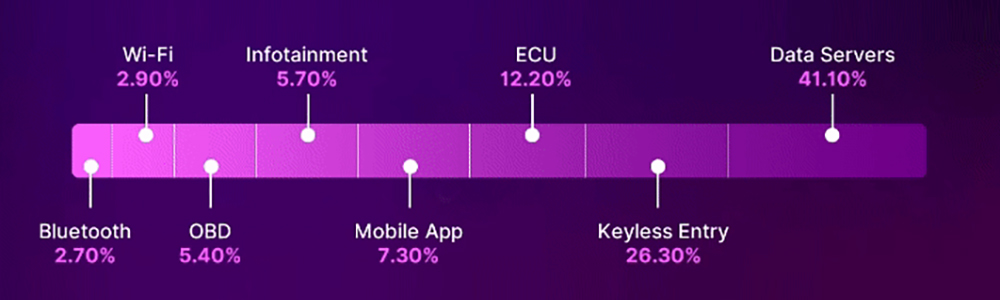
RISING VULNERABILITIES IN ELECTRIC VEHICLES
Surge in cyber incidents targeting electric vehicle components.


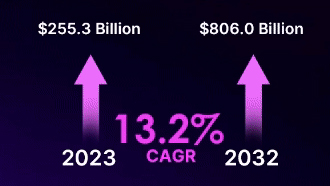
Global automotive cybersecurity market


CRYSTAL BALL SERIES
IN THIS INSTALMENT WE EXPLORE
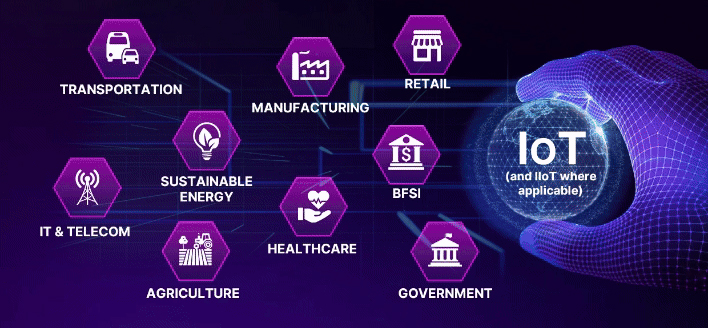
CLOUD, IOT, AND IIOT
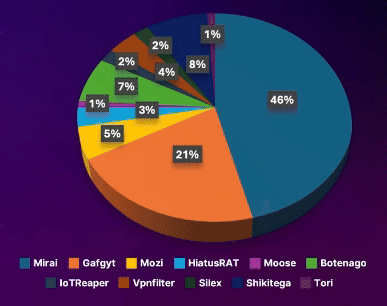
IOT MALWARE ATTACKS IN 2023
Information on loT Malware Attacks
- loT infrastructure
- Backdoors : 66% of malware facilitating botnet creation
MOST MALWARES USED
The Role of Cloud, IOT, and IloT as New Intermediaries for Adversaries
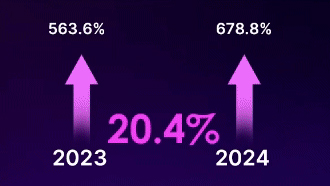
End-user spending on public cloud services
Global Industrial Internet of things (lol)
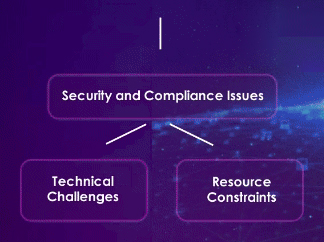
Cloud Security Main challenges in 2024
loT industry main challenges in 2024
CRYSTAL BALL SERIES
IN THIS INSTALMENT WE EXPLORE
DDOS HACKTIVISM TO RDDOS TRAJECTORY
Geopolitical conflicts are the main reason for the increase in DDoS attacks
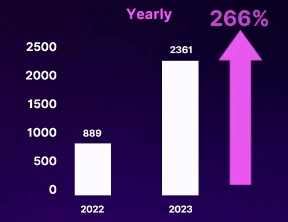
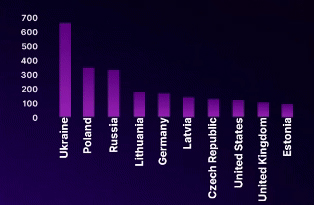
NATO and Pro NATO countries are most attacked by DDoS attackers
Top 10 Victim Countries of DDoS Attacks
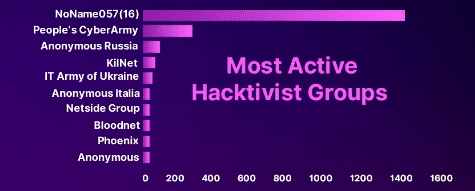
Critical Infrastructure organizations are the most targeted by DDoS attackers
Most Targeted Industries
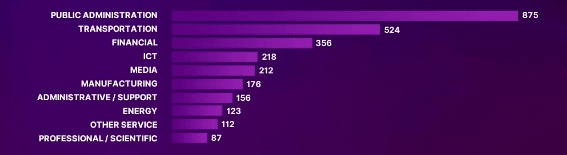
BE READY FOR A NEW CYBERCRIME ARMORY WITH NEXT-GEN RDDOS
A growing number of RDDoS campaigners will emerge with origins in DDoS hacktivism
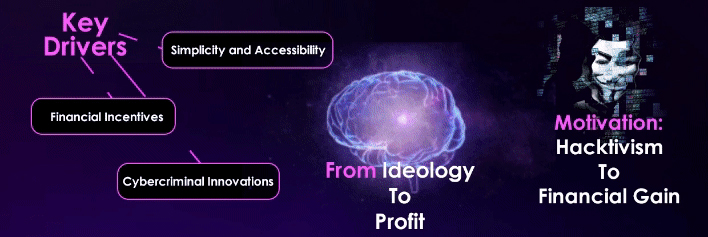
Increased Risk in 2024 and Beyond
RDDoS Top Targeted Industries

The DDos threat actors space will be dominated by Russian threat actors against NATO and Anti-Russian countries

CRYSTAL BALL SERIES
IN THIS INSTALMENT WE EXPLORE
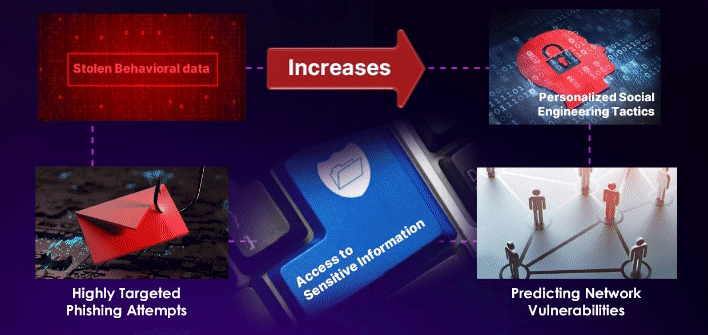
BEHAVIORAL DATA
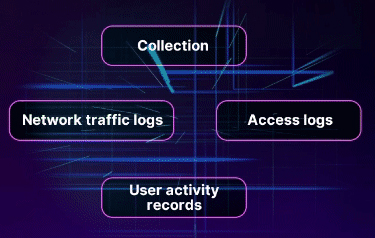

2023 saw an increase in threat intelligence sharing that integrated behavioral attributes
Distribution of social engineering attacks on individuals this time last year

BEHAVIORAL DATA WILL BECOME MORE VALUABLE