



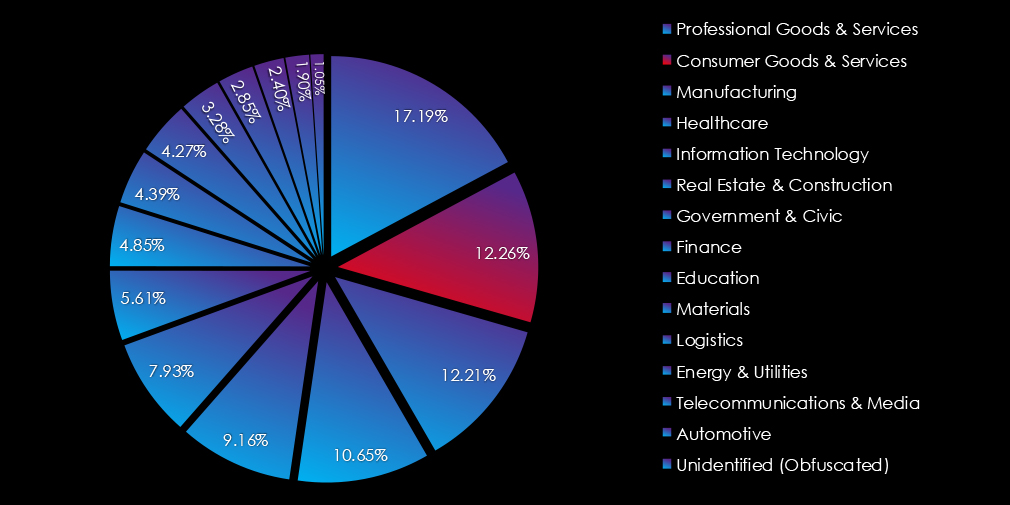
The CYFIRMA Industries Report provides cutting-edge cybersecurity insights and telemetry-driven statistics on global industries. Spanning the last 365 days and highlighting year-over-year changes between 2023 and 2024, this report covers 13 key industries and presents critical trends and data in a compelling infographic format.
This is Part 3 of the report covers only the second half of individual industry breakdowns. If you would like to access the full report, it is available exclusively on our website.
Welcome to the CYFIRMA Infographic Industry Report, where we examine the external threat landscape across 13 industries over the past year. Through clear, data-driven visuals and expert insights, we present concise analyses of attack campaigns, phishing telemetry, and ransomware incidents affecting organizations worldwide.
Leveraging our cutting-edge platform telemetry and the deep expertise of our analysts, this report covers detailed industry-specific breakdowns along with cross-industry trends and year-over-year changes published in Part 1.
Our goal is to equip you with actionable intelligence that helps you stay ahead in the ever-evolving cybersecurity landscape.
CYFIRMA provides cyber threat intelligence and external threat landscape management platforms, DeCYFIR and DeTCT, which utilize artificial intelligence and machine learning to ingest and process relevant data, complemented by hands-on CTI research.
For the purpose of these reports, we leverage the following data from our platform. These are data processed by AI and ML automation based on both human research input and automated ingestions.
Leveraging our Early Warning platform data set, we present known attack campaigns conducted by known advanced persistent threat actors, both nation-state and financially motivated.
Each attack campaign may target multiple organizations across various countries.
Campaign durations can vary from weeks to months or even years. They are sorted by the “last seen” date of activity to include the most relevant ones. Note that this may result in campaigns stacking up on later dates, affecting time-based trends.
Attribution to specific threat actors can be murky due to increasingly overlapping TTPs and commodity tools used. While suspected threat actors in this report are attributed with high confidence, we acknowledge the potential for inaccuracy.
Our data focuses on phishing campaigns rather than individual phishing or spear-phishing emails, which may limit visibility into more advanced single-target attacks.
Our primary focus is on detecting brand impersonation over intended targets. Due to our collection methodology and automation, we may not present comprehensive victimology for phishing campaigns across all industries as some are simply not good phishing lures.
Our data on victims in this report is directly collected from respective ransomware blogs, though some blogs may lack detailed victim information beyond names or domains, impacting victimology accuracy during bulk data processing.
In some cases, there are multiple companies that share the same name but are located in different countries, which may lead to discrepancies in geography and industry. Similar discrepancies occur with multinational organizations where we are not able to identify which branch in which country was actually compromised. In such a case, we count the country of the company’s HQ.
During the training of our processing algorithms, we manually verified results for industry and geography statistics at an accuracy rate of 85% with a deviation of ±5%. We continuously fine-tune and update the process.
Data related to counts of victims per ransomware group and respective dates are 100% accurate at the time of ingestion, as per their publishing on the respective group’s blog sites.
Finally, we acknowledge that many victims are never listed as they are able to make a deal with the attackers to avoid being published on their blogs. While this report contains statistics and graphs generated primarily by automation, it undergoes thorough review and enhancement for additional context by CYFIRMA CTI analysts to ensure the highest quality and provide valuable insights.
The following section delves into the Advanced Persistent Threat (APT) campaigns and ransomware victimology of 2024, offering an in-depth analysis of 13 industry categories. Each industry’s unique characteristics, vulnerabilities, and operational priorities have shaped how threat actors target and exploit them, providing valuable insights into the evolving cyber threat landscape.
This comprehensive overview highlights key trends, shifts in attacker focus, and the tactics, techniques, and procedures (TTPs) observed across sectors. The industries covered include:
(The above were covered in Part 2)
By examining the APT campaigns and ransomware victimology, this section delivers a granular view of the threats impacting these industries. It highlights both the overarching trends influencing the global threat landscape and the distinct challenges faced by each industry, providing stakeholders with critical insights to navigate the evolving cyber threat landscape heading into 2025.
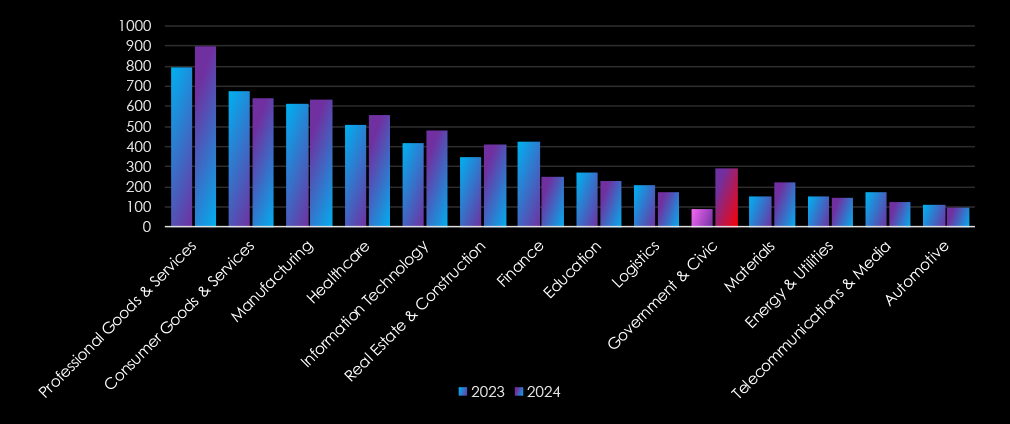
Year-to-Year Elevation: Moderate
In 2023, our DeCYFIR platform recorded a total of 27 campaigns. During 2024, it recorded 31, representing a 14.8% increase year-over-year.

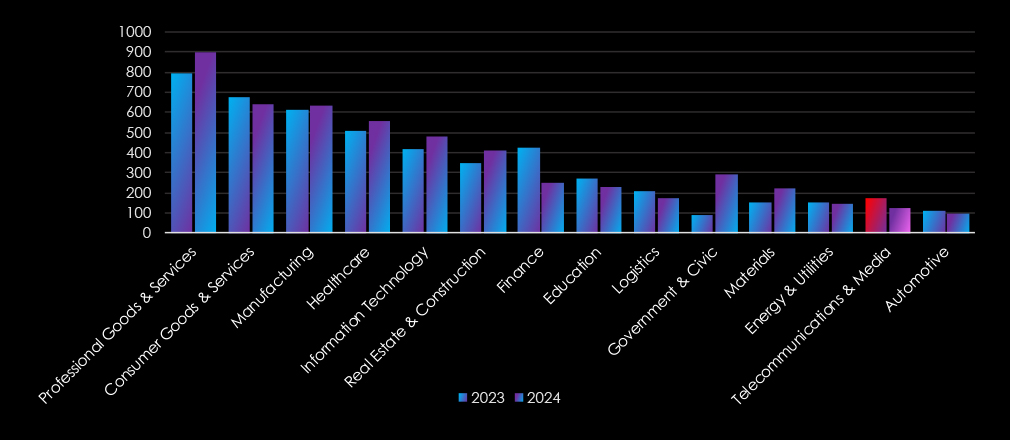
The threat landscape shifted in 2024, with IT, Finance, and Manufacturing becoming the most targeted industries, likely due to increasing global tensions and armed conflicts.
In total, 9 out of the 13 industries recorded fewer APT campaigns.
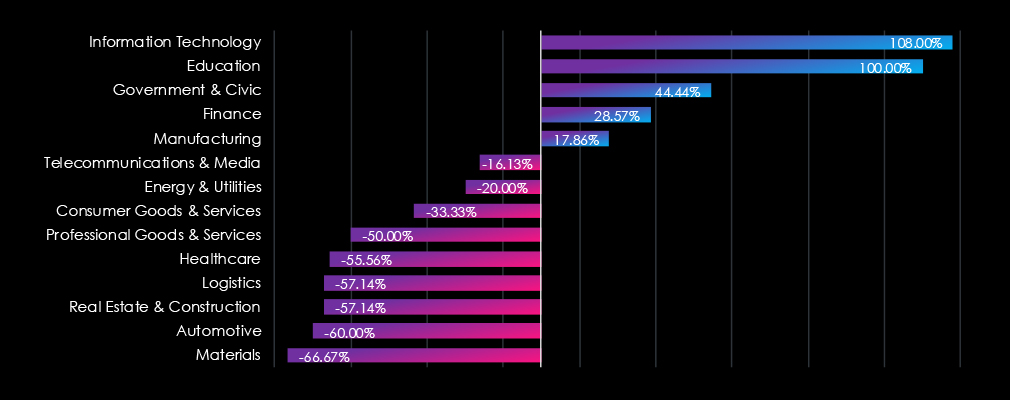
20 countries saw an increase in recorded APT campaigns, while 13 countries saw a decrease.
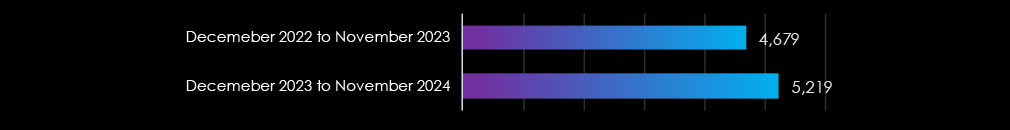
Year-to-Year Elevation: High
In 2023, CYFIRMA recorded 4,679 verified ransomware victims, while in 2024, the number increased to 5,219, representing an 11.5% year-over-year growth across all industries.
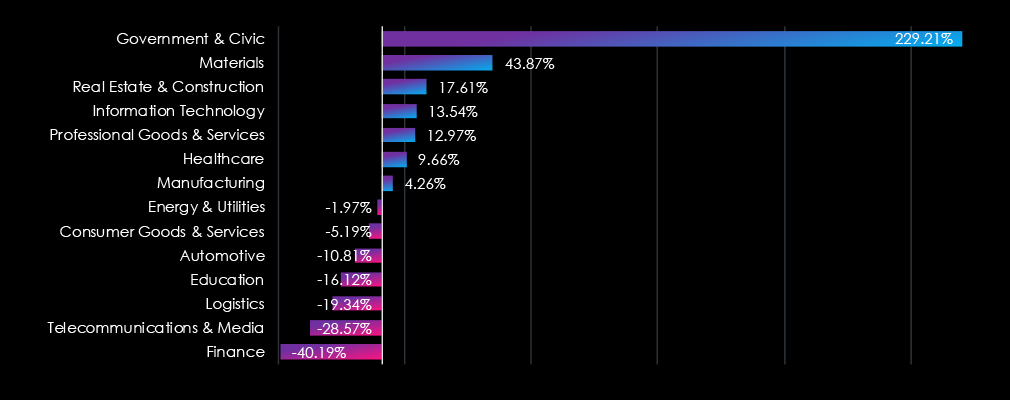
The Finance industry experienced the most notable decline, while Government & Civic saw a dramatic increase, indicating a sharp rise in targeting, correlated with heating geopolitical tension across the globe. Healthcare and Real Estate & Construction also witnessed increases. On the other hand, Logistics, and Telecommunications & Media saw significant decreases.
In total, half, 7 out of the 14, industries recorded more ransomware victims.
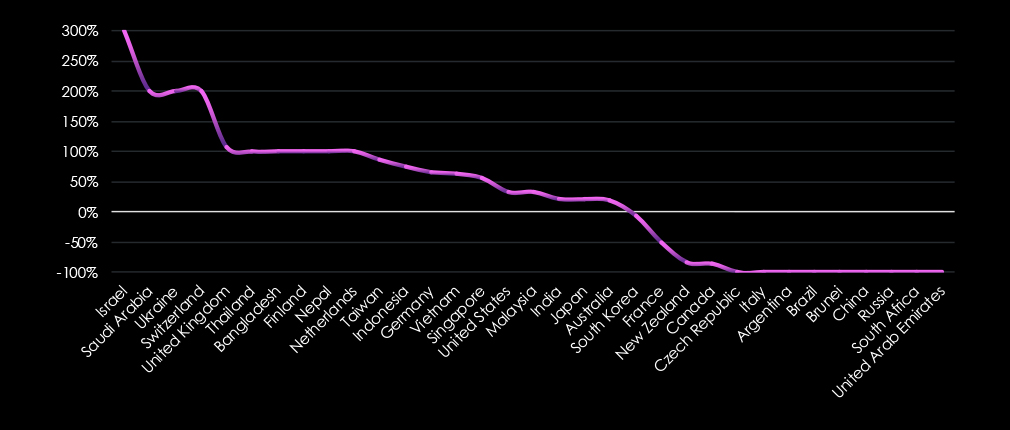
125 countries recorded ransomware victims in 2024. Below are the top 35 and their respective elevations.
Over the past 12 months, telecommunications & media organizations recorded victims across 16 of the 34 Advanced Persistent Threat (APT) campaigns observed – an incidence rate of 47%.
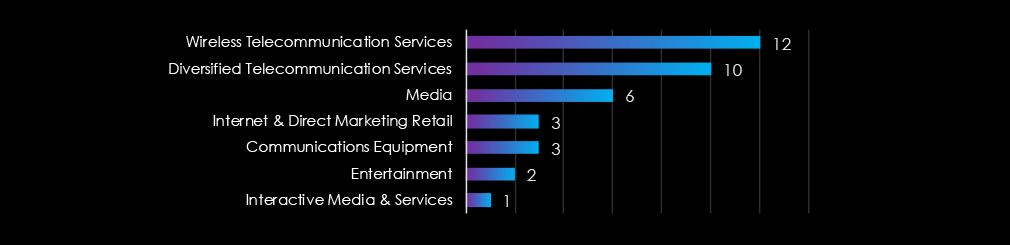
These victims spanned multiple segments within the telecommunications & media industry as per below:
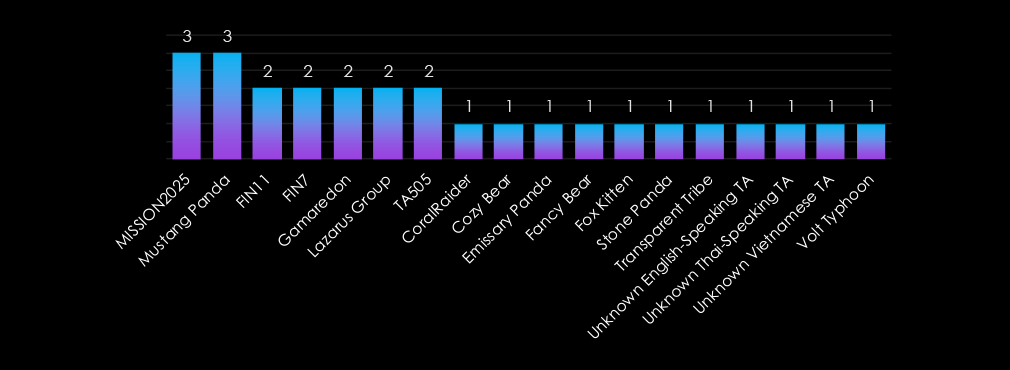
The industry faces threats from both nation state and financially motivated actors. MISSION2025 and Mustang Panda (China) lead, focusing on espionage and infrastructure exploitation, while Lazarus Group, FIN11, and FIN7 target the sector for financial gain.
Russian groups like Gamaredon, Cozy Bear, and Fancy Bear prioritize intelligence gathering and geopolitical objectives. Emerging actors, including Unknown Thai- and Vietnamese-speaking TAs, reflect an expanding threat landscape, underscoring the sector’s critical role in global communications and information control.
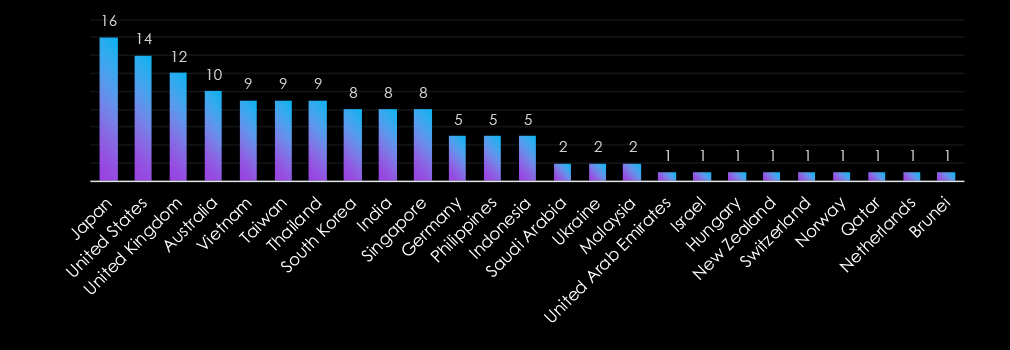
The telecommunications and media industry is targeted globally, with a strong focus on advanced economies and key hubs. Countries like Japan, the United States, and the United Kingdom lead, reflecting their prominence in global communications infrastructure. Asia-Pacific nations, including Vietnam, Taiwan, and Thailand, are heavily targeted, underscoring the region’s strategic importance.
Emerging markets such as the Philippines, Indonesia, and Malaysia also feature, highlighting attackers’ expanding reach. The inclusion of smaller nations like Brunei, Norway, and Qatar illustrates the diverse scope of threats to this critical sector.
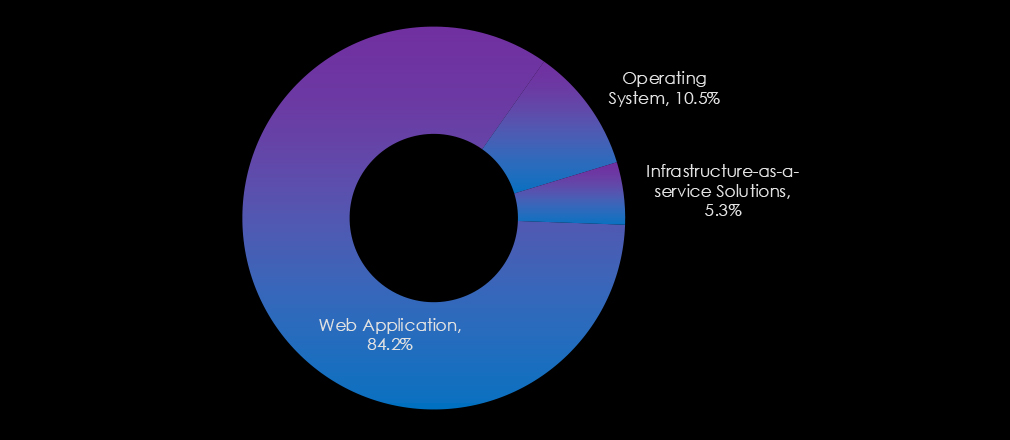
Web applications dominate, reflecting their vulnerability as internet-facing systems integral to communication platforms. Operating systems also see significant targeting, emphasizing their foundational role in infrastructure. Additionally, infrastructure-as-a-service solutions also appear as a target.
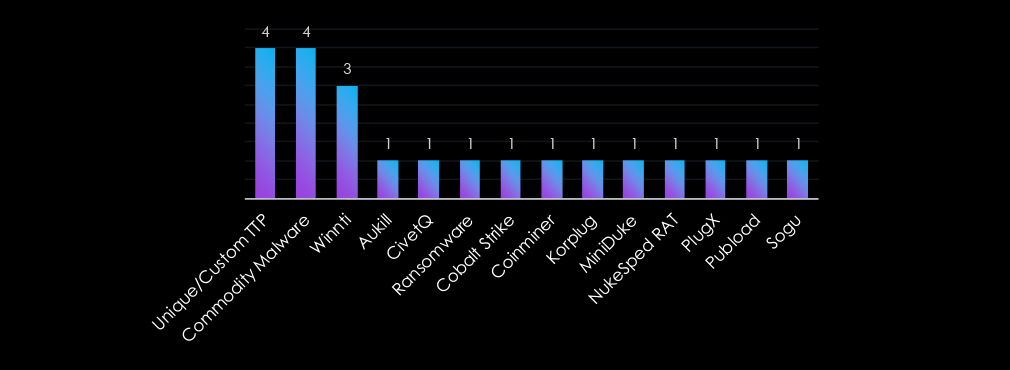
The telecommunications and media industry faces a diverse array of malware threats, with Unique/Custom TTPs and Commodity Malware leading in usage, reflecting both tailored attacks and the accessibility of widely available tools.
Winnti highlights its role in long-term infiltration and data theft, aligning with espionage objectives. Other notable tools like ransomware, Cobalt Strike, and PlugX emphasize versatility, supporting operations ranging from financial extortion to system exploitation.
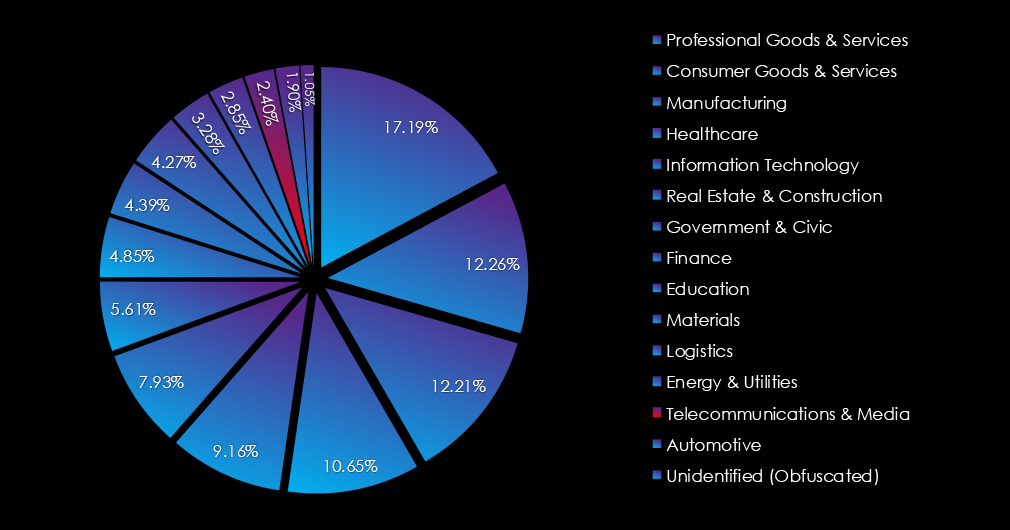
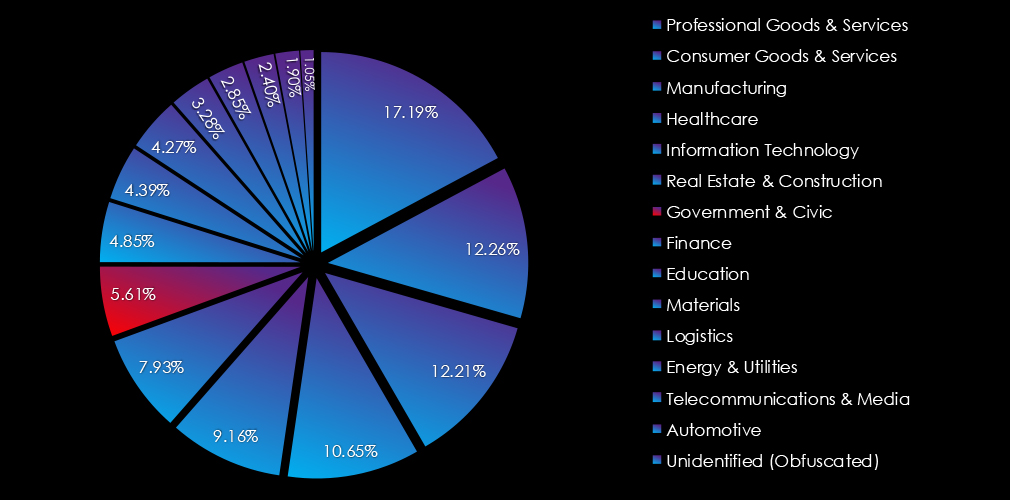
In the past 12 months, CYFIRMA has identified 125 verified telecommunications & media industry ransomware victims. This accounts for 2.40% of the overall total of 5,219 ransomware victims during the same period.
The industry recorded a remarkably consistent number of recorded victims, with a major decrease of -28.57% from the previous year. It ranked at 13th place for both years combined. The industry moved down from 10th to 13th place during 2024 as the second least frequent victim.
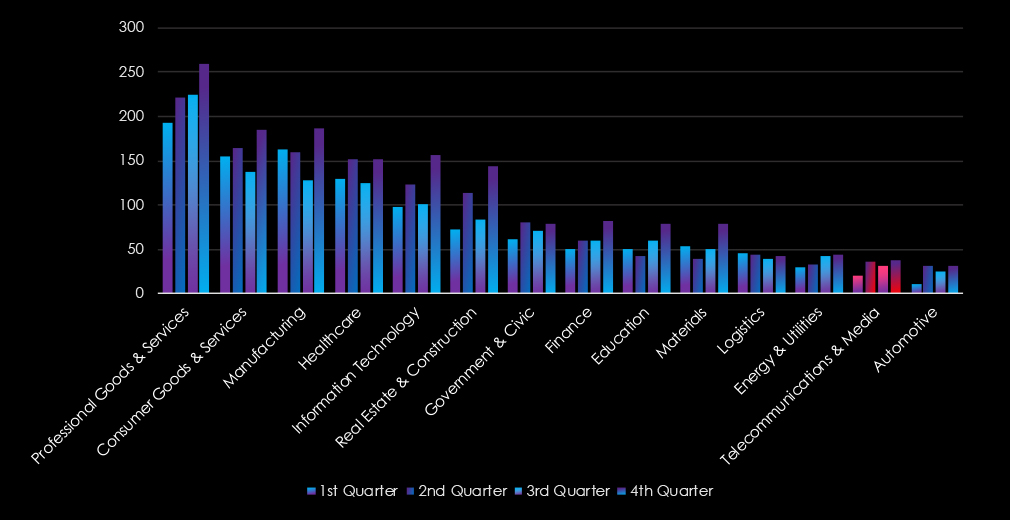
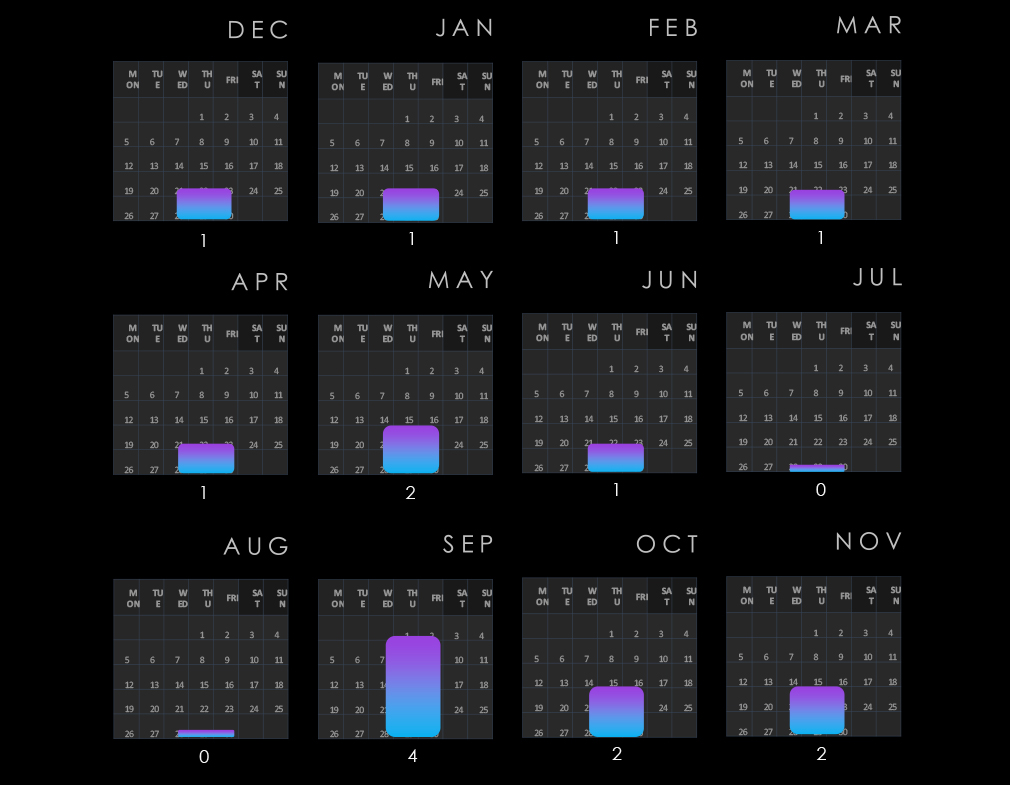
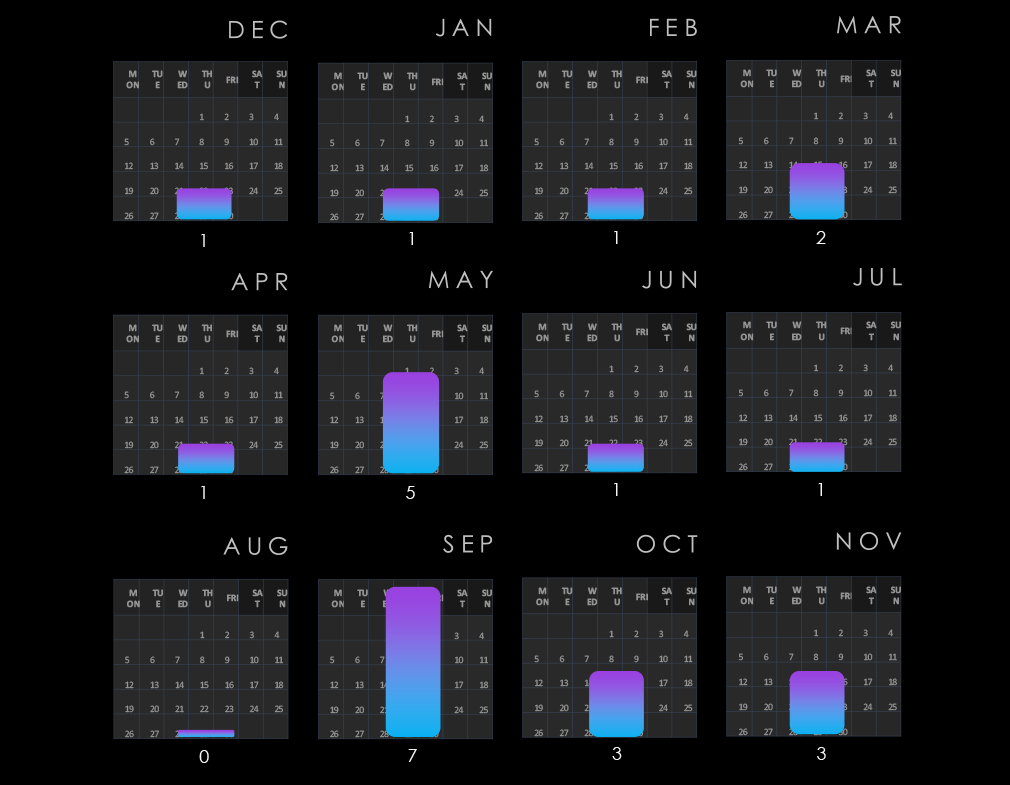
The telecommunication & media industry had a very calm start to the year in the first quarter but from the second quarter onward recorded sustained elevation until the end of the year.
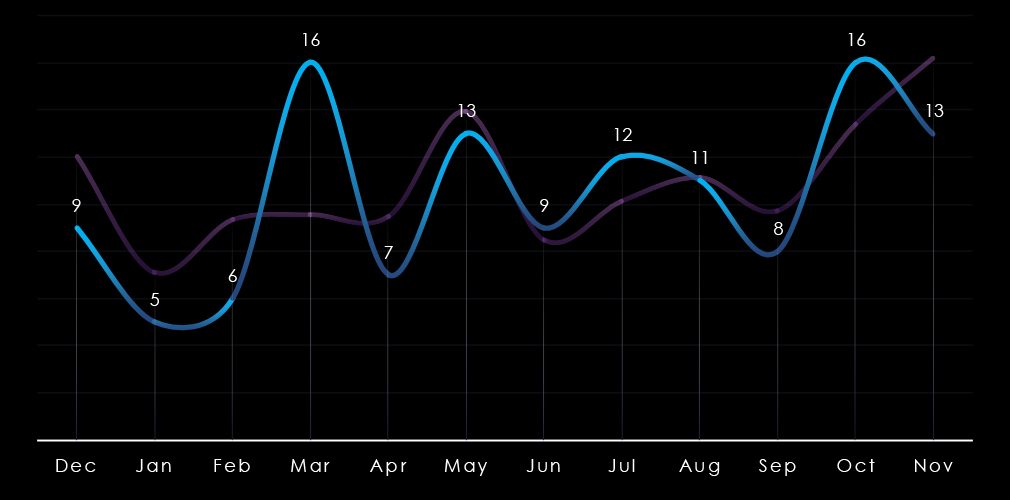
Monthly activity at large follows the scaled-down global trendline. The start of the year was mildly below average, then during March, this industry experienced a major spike in activity.
During October, the industry followed the global elevation. However, in November, it diverged and experienced a tapering off.
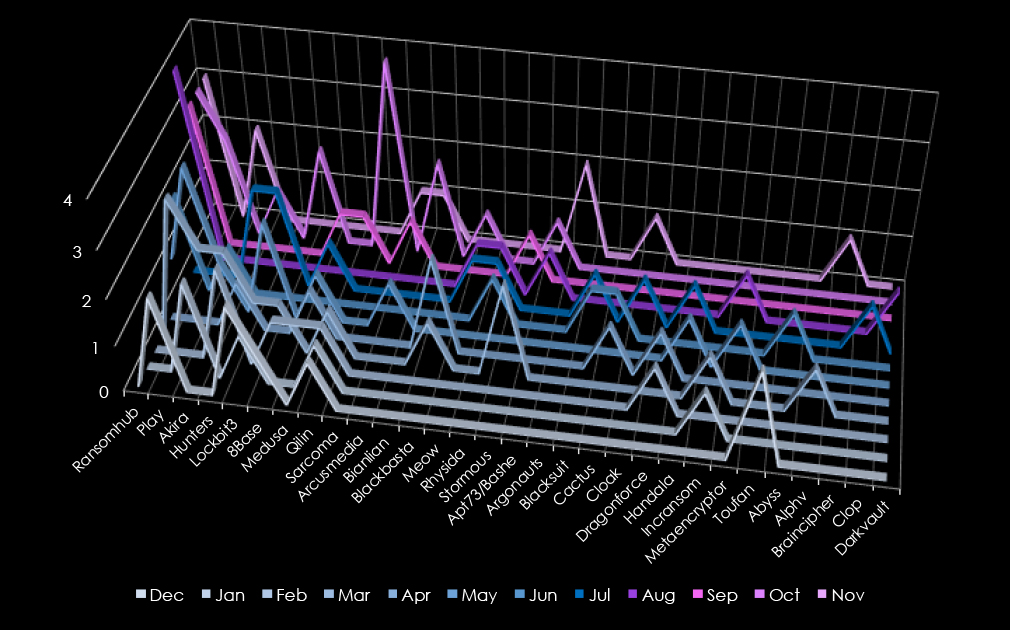
In total 43 out of 97 gangs recorded victims in the telecommunications & media technology industry, with 44% participation.
A breakdown of the top 30 gang’s monthly activity provides insights into which gangs were active each month.
RansomHub led the activity with 16 victims, focusing on late-year operations, particularly in August through November. Play followed with 10 victims, peaking in March and May. Akira, Hunters, and LockBit3 each accounted for 8 victims. Akira and Hunters showed consistent activity in the early months, while LockBit3 had scattered campaigns throughout the year.
8Base, Medusa, and Qilin each targeted 5 victims, with 8Base and Medusa showing early-year activity and Qilin spreading attacks more evenly. Sarcoma targeted 4 victims exclusively in October, reflecting a late-year focus.
Smaller actors such as Arcusmedia, Bianlian, Blackbasta, and Meow (3 victims each) had isolated campaigns, with Bianlian and Blackbasta active mid-year and Meow showing late-year spikes. Emerging groups like Rhysida and Stormous also targeted 3 victims, concentrated in the mid-to-late months.
Lesser groups, including Apt73/Bashe, Argonauts, and Blacksuit (2 victims each), displayed minimal activity. Single-incident actors like Abyss, Alphv, and Braincipher (1 victim each) had isolated operations, primarily late in the year.
Overall, RansomHub dominated with a late-year surge, while Play and Akira showed consistent mid-year activity.
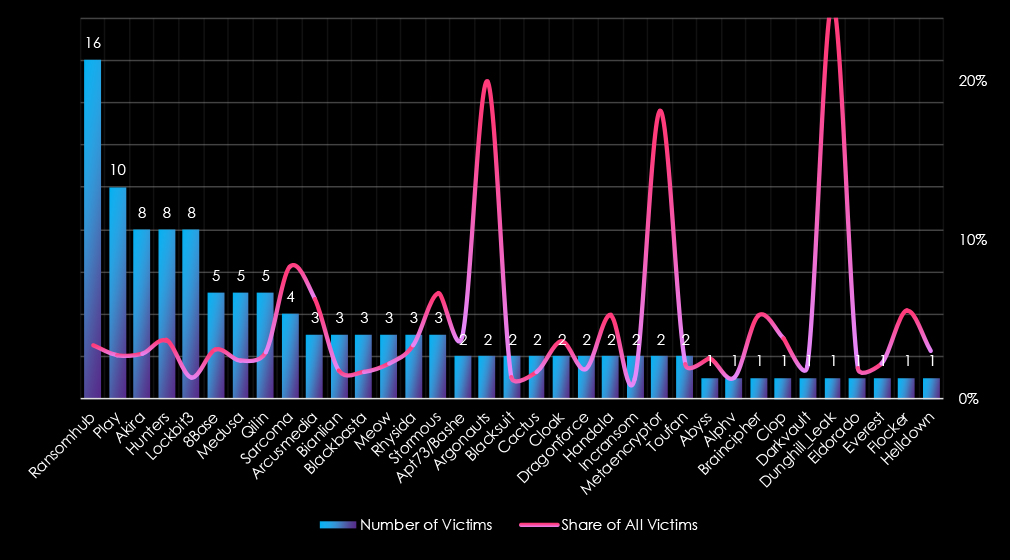
Breaking down the top 35 gangs’ victimology, the trendline of the share of all victims for the most active gangs is low, implying no targeted focus on this industry.
RansomHub leads in activity within the telecommunications and media sector, with 16 victims (3.37%), showing moderate activity but a distributed targeting strategy. Play follows with 10 victims (2.72%), while Akira and Hunters each have 8 victims (2.85% and 3.69%, respectively). LockBit3 (8 victims, 1.34%) also shows some presence in this sector, although its focus appears broader.
Several gangs demonstrate meaningful focus within the telecommunications and media industry:
Certain gangs exhibit disproportionately high percentages due to low victim counts:
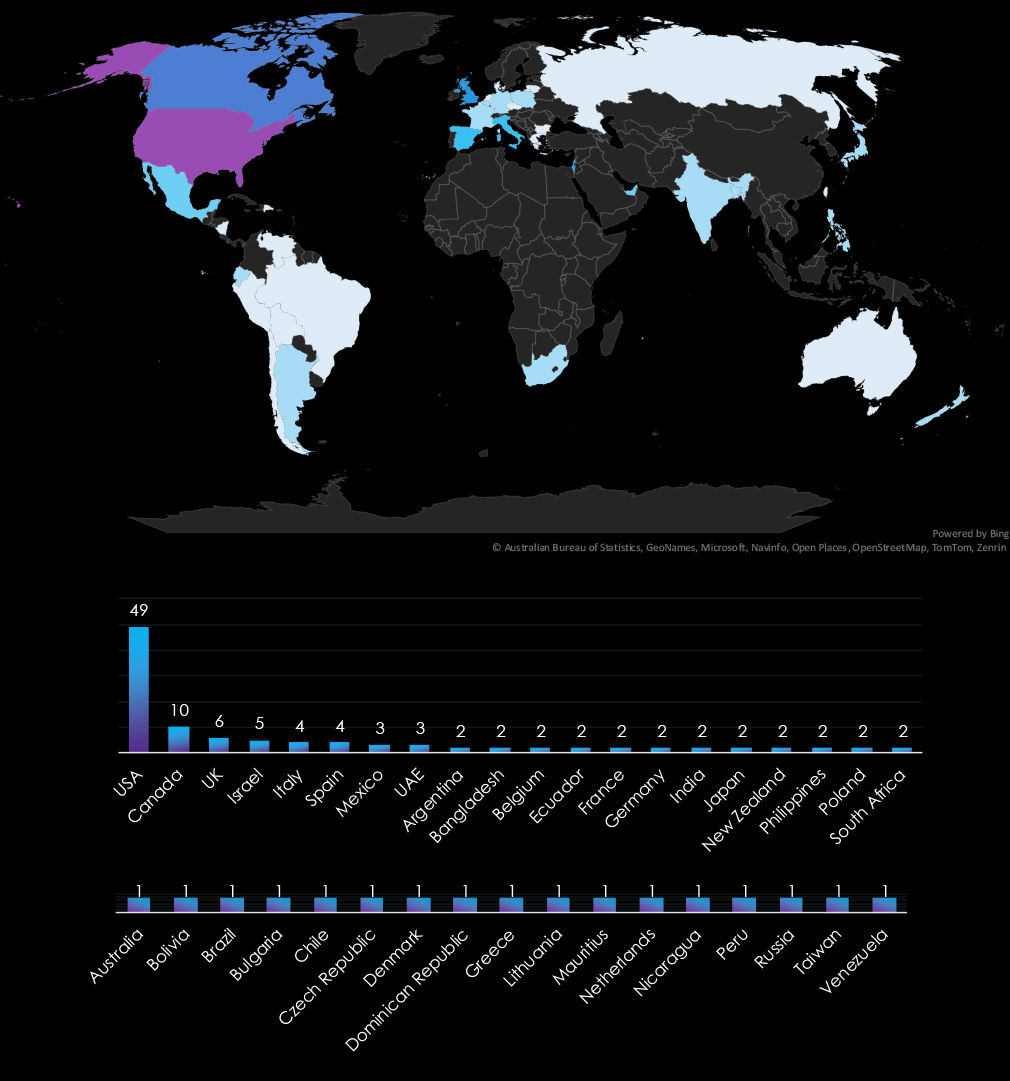
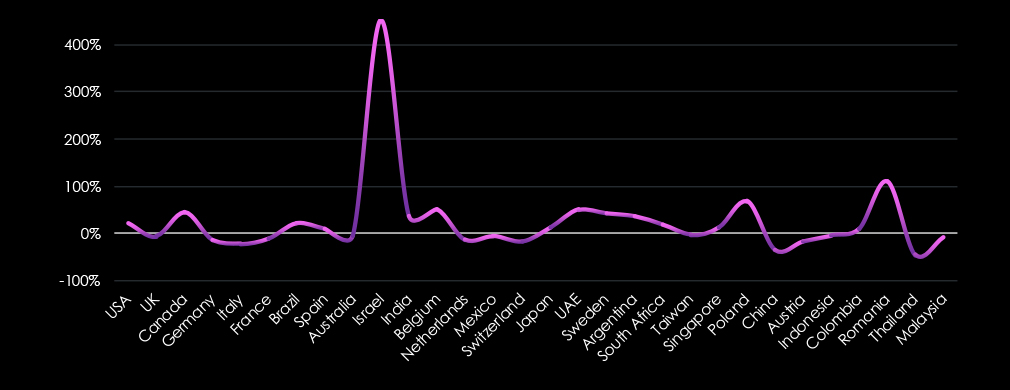
The USA accounts for 39.2% of ransomware victims in the Telecommunication & Media industry in 2024. The next most affected countries are Canada with 10 victims, the UK with 6, Israel with 5, and Italy with 4.
A total of 37 countries reported victims, with 17 of them having only one victim each.
Risk Level Indicator: High/Low

APT Campaigns
The telecommunications and media industry experienced a 47% incidence rate across observed APT campaigns, driven by nation-state and financially motivated actors. Groups like MISSION2025 and Mustang Panda target espionage and infrastructure, while FIN7 and FIN11 pursue financial gain. Emerging threats from Southeast Asian actors highlight the sector’s critical role in global communications and information control.
Actors: MISSION2025, Mustang Panda, Cozy Bear, FIN7, FIN11; emerging Thai- and Vietnamese-speaking TAs.
Geographic Focus: U.S., Japan, U.K.; heavy targeting in Asia-Pacific (Vietnam, Taiwan, Thailand); emerging economies like Indonesia, Philippines, and Malaysia.
Targets: Web applications, operating systems, and infrastructure-as-a-service solutions.
Malware: Winnti, Cobalt Strike, PlugX; a mix of tailored and commodity malware.
Ransomware
The telecommunications and media sector accounted for 125 ransomware victims (2.40% of the global total), showing a major -28.57% year-over-year decrease. After a calm start in Q1, activity surged in March and remained elevated through Q4. RansomHub led with late-year spikes, while other groups like Play, Akira, and LockBit3 maintained steady mid-year activity.
Victim Trends: Calm Q1; spikes in March and sustained activity through Q4, tapering in November.
Key Actors: RansomHub (16 victims), Play (10 victims), Akira, Hunters, LockBit3 (8 each).
Geography: The U.S. accounted for 39% of victims; activity recorded in 27 countries.
Insight: Ransomware activity was dispersed, with no group showing a sustained focus on this industry.
Ranking: It ranked 13th as the second least frequent target of ransomware.
Over the past 12 months, information technology organizations recorded victims across 26 of the 34 Advanced Persistent Threat (APT) campaigns observed – an incidence rate of 76%.
These victims spanned multiple segments within the information technology industry as per below:
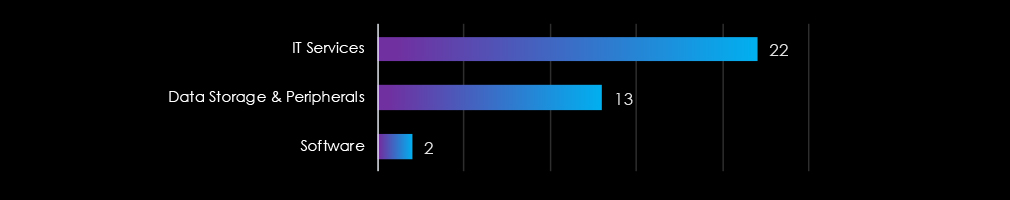
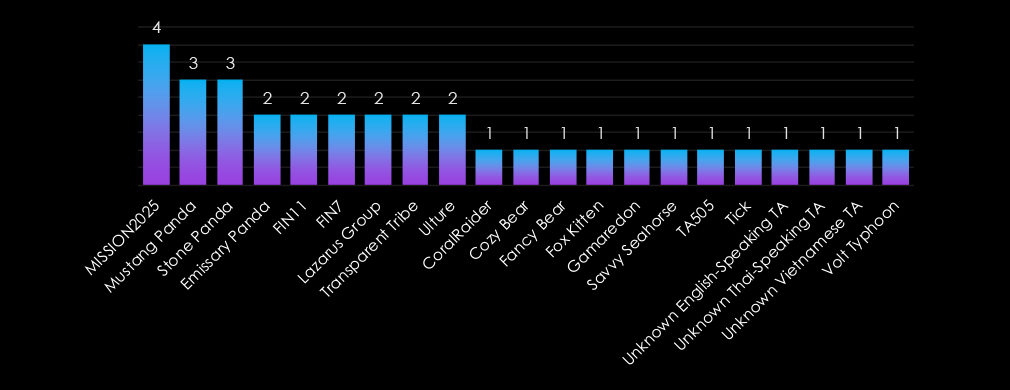
The information technology industry is heavily targeted by both nation-state and financially motivated actors. MISSION2025, Mustang Panda, and Stone Panda (China) lead, focusing on espionage and intellectual property theft to support geopolitical goals.
Financially driven groups such as FIN11, FIN7, and Lazarus Group exploit the industry for ransomware and data extortion. Russian groups, including Cozy Bear, Fancy Bear, and Gamaredon, prioritize intelligence gathering and strategic disruption. Emerging actors, such as Unknown Thai and Vietnamese-Speaking TAs, and Ulture, highlight the industry’s expanding threat landscape.
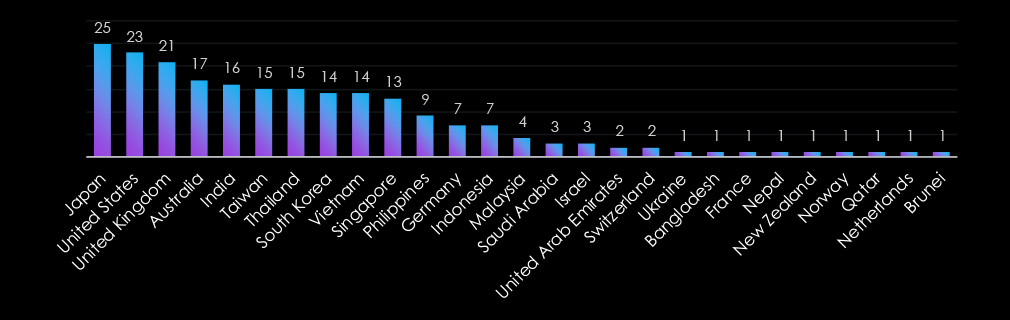
The information technology industry faces global targeting, with Japan, the United States, and the United Kingdom leading due to their prominence in innovation. Asia-Pacific nations like India, Taiwan, and South Korea are also heavily targeted, reflecting the region’s growing IT significance.
Emerging markets such as Bangladesh and Indonesia, alongside smaller nations like Brunei and Nepal, illustrate the sector’s expanding threat landscape across both established and developing regions.
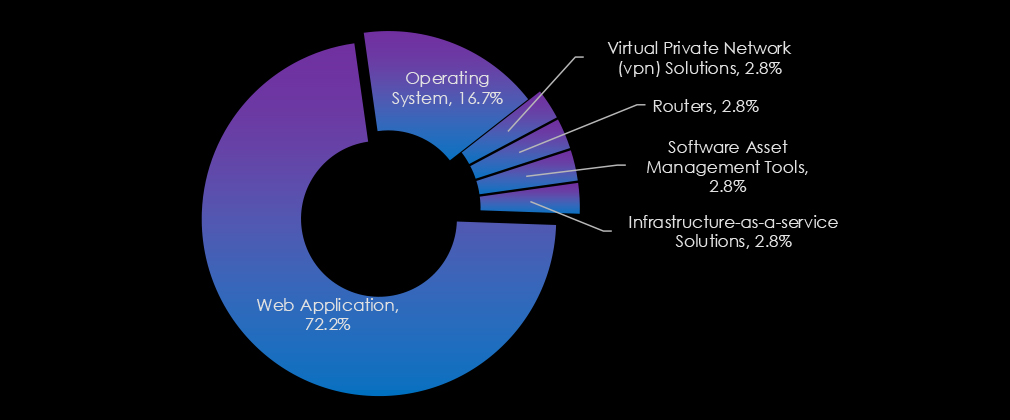
The information technology industry’s most targeted technologies highlight attackers’ focus on foundational and internet-facing systems. Web applications dominate, emphasizing their critical role and vulnerability. Operating systems also see significant targeting due to their centrality in IT infrastructure. Additional technologies like VPN solutions, routers, and infrastructure-as-a-service solutions reflect attackers’ interest in exploiting essential tools that support modern IT environments.
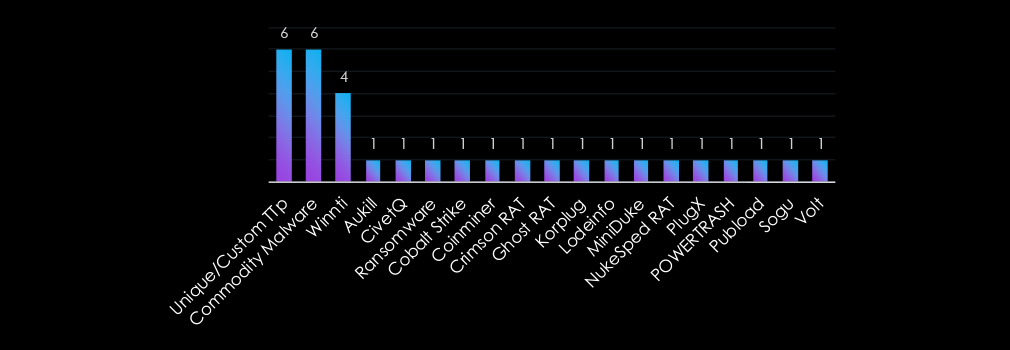
The malware targeting the information technology industry reflects a blend of tailored and widely available tools. Unique/Custom TTPs and Commodity Malware lead, emphasizing the balance between targeted sophistication and accessibility.
Winnti highlights its persistent use for espionage and data theft, while tools like Cobalt Strike, Ransomware, and PlugX showcase versatility for financial extortion and infiltration. Lesser-used malware such as Coinminer and Crimson RAT indicate niche but impactful operations, underscoring the sector’s exposure to both advanced and opportunistic threats.
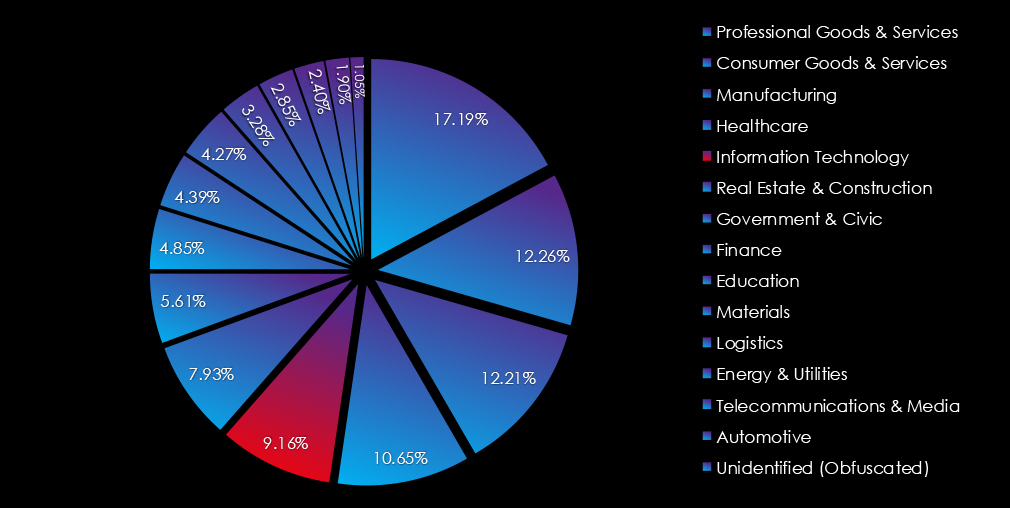
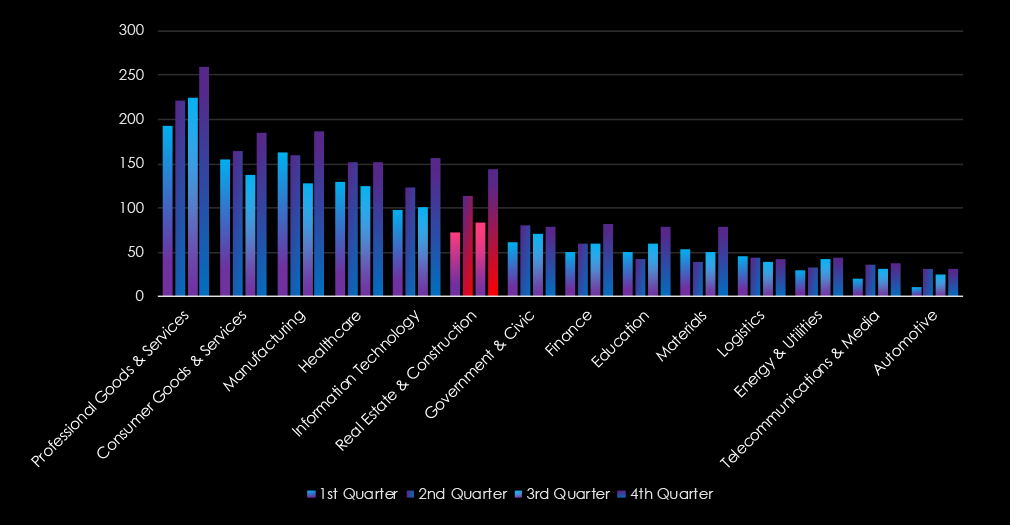
In the past 12 months, CYFIRMA has identified 478 verified information technology industry ransomware victims. This accounts for 9.16% of the overall total of 5,219 ransomware victims during the same period.
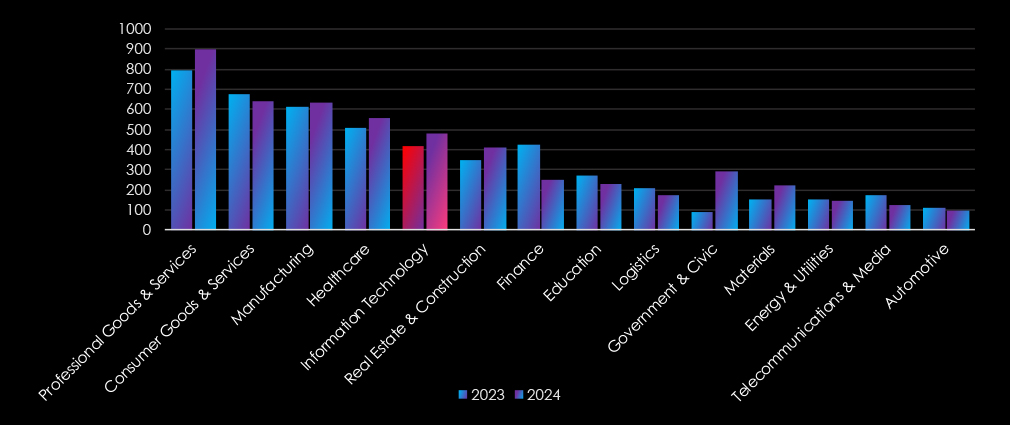
The industry recorded a remarkably consistent number of recorded victims, a major 13.54% increase from the previous year. It ranked at 5th place for both years combined. The industry moved up from 6th to 5th place during 2024 as the fifth most frequent victim.
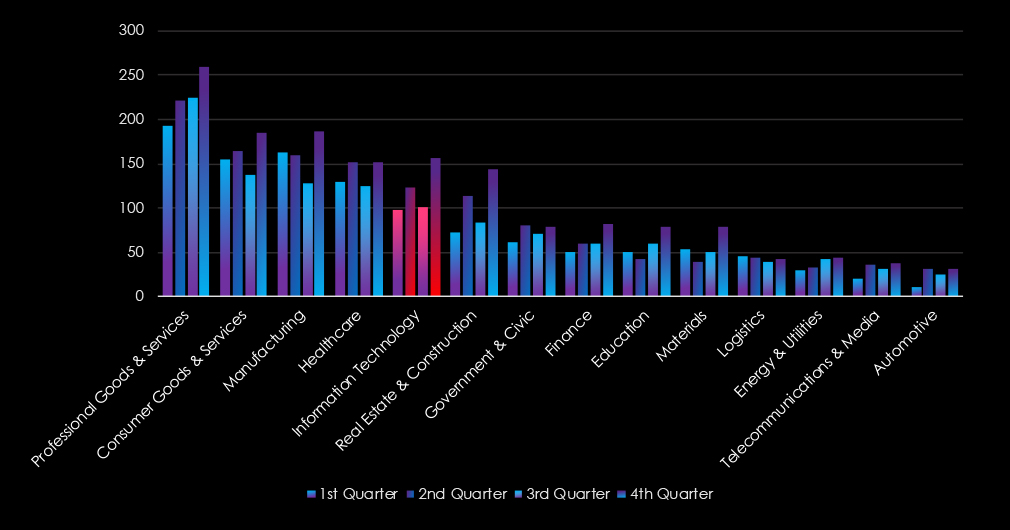
The information technology industry experienced alternating activity. The first and second quarters were relatively calmer. Third and especially fourth quarters recorded elevated numbers.
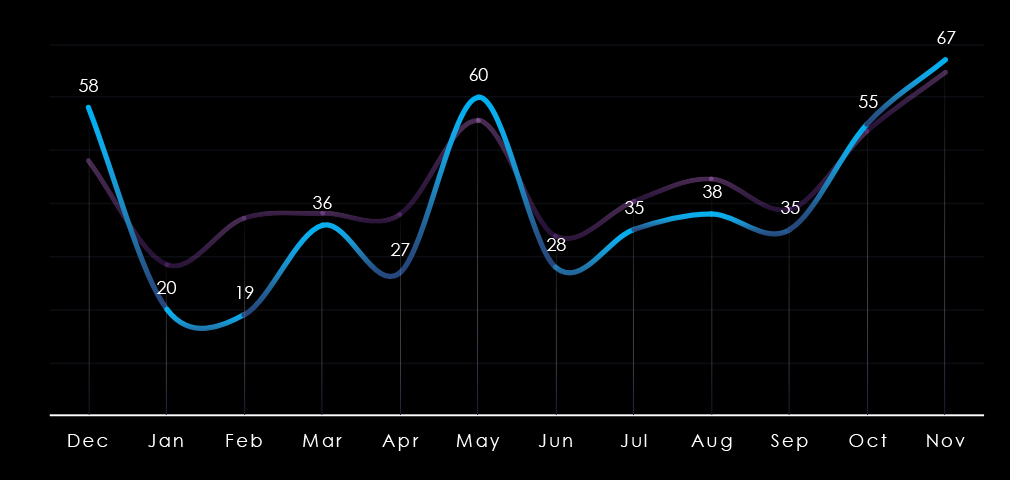
Monthly activity nearly perfectly follows the scaled-down global trendline. There is only a minor below-average dip in January and February. By the end of the year, during October and November, the number of victims sharply rose, which suggests elevation into 2025.
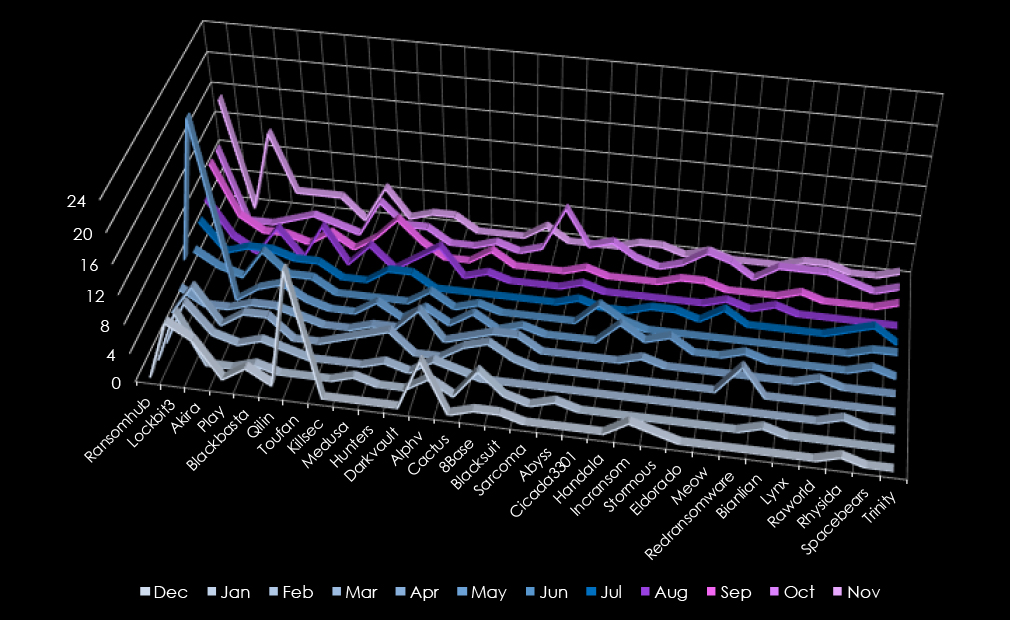
In total 67 out of 97 gangs recorded victims in the information technology industry, 69% participation.
RansomHub led ransomware activity with 62 victims, showing a sharp increase from August onward and peaking in November (15 victims). LockBit3 closely followed with 61 victims, maintaining steady activity throughout the year, with a significant spike in May (24 victims).
Akira and Play each targeted 26 victims. Akira was most active in November (11 victims), while Play had consistent activity across the year, peaking in July (5 victims). Blackbasta (23 victims) demonstrated steady activity, with notable spikes in May and November.
Qilin targeted 19 victims, with activity intensifying in August and November. Toufan published 17 victims in December. Killsec and Medusa each accounted for 16 victims, with Killsec peaking in September and October, while Medusa saw consistent activity late in the year.
Hunters and Darkvault (15 and 14 victims, respectively) maintained steady but lower activity, with Darkvault peaking in April and Hunters spreading its efforts across multiple months. Alphv and Cactus each targeted 11 victims, with Alphv active early in the year and Cactus peaking in May and September.
Large groups like 8Base (10 victims) and Blacksuit (9 victims) showed limited campaigns, with activity scattered throughout the year. Sarcoma (7 victims) conducted its operations exclusively in October. Other groups, such as Abyss, Cicada3301, and Handala (6 victims each), demonstrated sporadic, concentrated campaigns.
Emerging actors like Eldorado, Meow, and Redransomware targeted 5 victims each, while smaller gangs such as Lynx and Rhysida (4 victims each) had isolated operations.
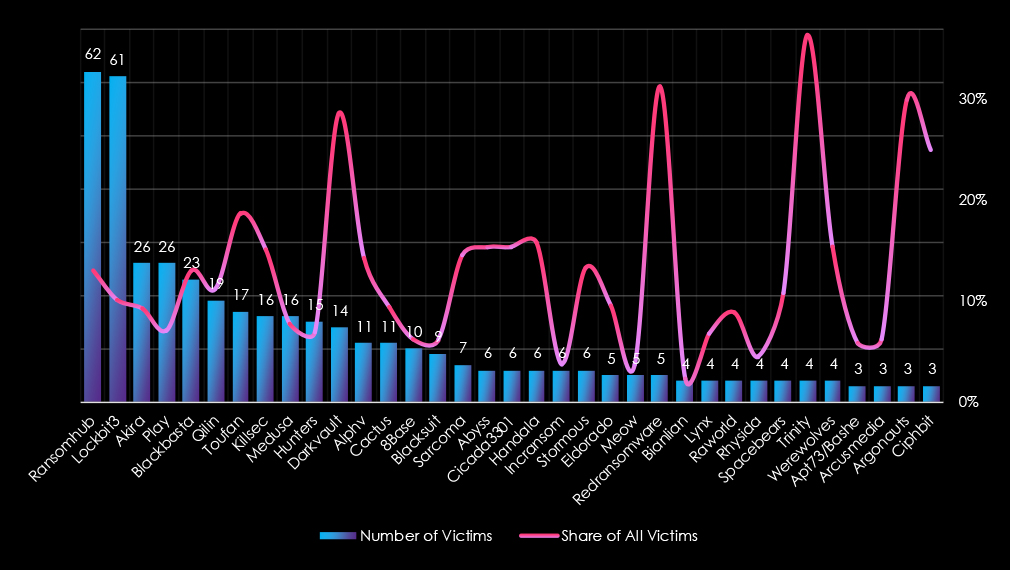
Reviewing the top 35 gangs, RansomHub and LockBit3 dominate ransomware activity within the IT sector, with 62 victims (13.05%) and 61 victims (10.18%), respectively. Their substantial victim counts highlight significant targeting efforts in this industry. Akira and Play, each with 26 victims (9.25% and 7.07%, respectively), also exhibit notable activity, though with less focus than the leading gangs.
Several gangs demonstrate concentrated targeting efforts within IT:
Some gangs exhibit disproportionately high percentages due to low victim counts:
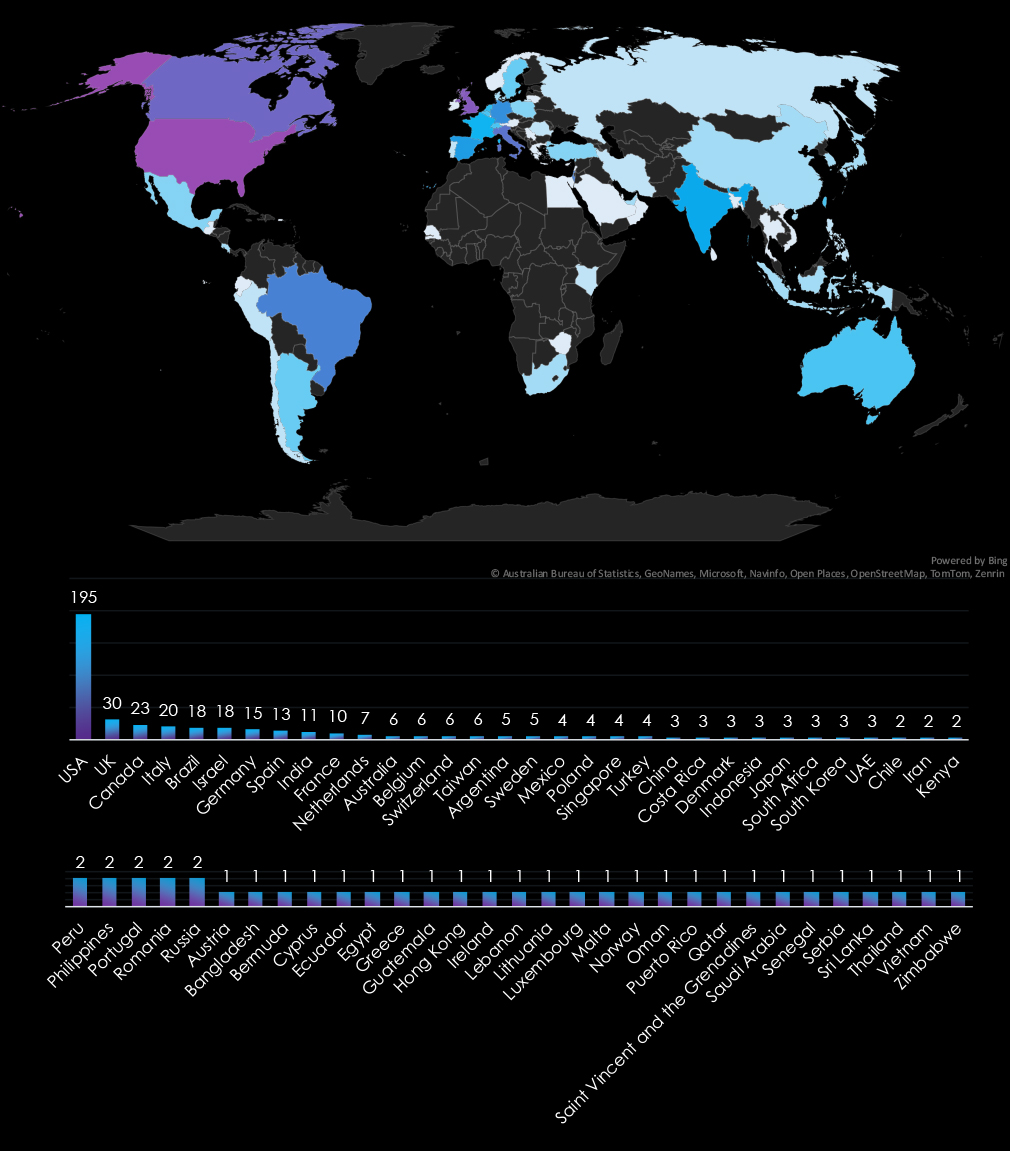
The USA accounts for 41% of ransomware victims in the Information Technology industry in 2024. The next most affected countries are the UK with 30 victims, Canada with 23, Italy with 20, and Brazil with 18.
A total of 63 countries reported victims, with 26 of them having only one victim each.
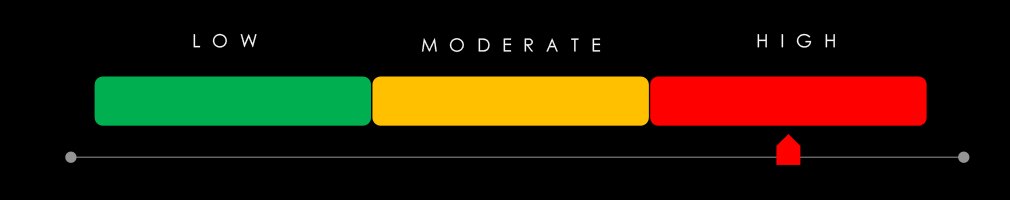
Risk Level Indicator: High
APT Campaigns
The information technology industry recorded a 76% incidence rate across observed APT campaigns, with threats driven by both nation-state and financially motivated actors. Groups like MISSION2025 and Stone Panda target intellectual property and geopolitical objectives, while FIN7 and FIN11 focus on ransomware and data extortion. Emerging threats from Southeast Asian actors highlight the industry’s growing vulnerability.
Actors: MISSION2025, Mustang Panda, Stone Panda, FIN7, Cozy Bear, emerging Southeast Asian TAs.
Geographic Focus: U.S., Japan, U.K.; heavy targeting in Asia-Pacific (India, Taiwan, South Korea); emerging markets like Philippines and Indonesia.
Targets: Web applications, operating systems, VPN solutions, routers, IaaS.
Malware: Winnti, Cobalt Strike, PlugX, Coinminer, Crimson RAT.
Ransomware
The IT sector accounted for 478 ransomware victims (9.16% of the global total), showing a major 13.54% year-over-year increase and ranking 5th in targeted industries. Activity intensified in Q3 and Q4, with October and November showing sharp increases, signaling continued risks into 2025.
Victim Trends: Calm Q1/Q2; spikes in Q3/Q4, peaking in November.
Key Actors: Most active were RansomHub (62 victims, peak in November), and LockBit 3 (61 victims, peak in May). Most consistent were Akira (26 victims, peak in November), and Play (26 victims, peak in July).
Geography: The U.S. accounted for 41% of victims; activity recorded in 63 countries.
Insights: RansomHub and Blackbasta showed the highest share of victims in IT (13% each), with niche groups like Darkvault and Redransomware recording 28%-36% of their targets in IT.
Ranking: IT Industry ranked as the 5th most frequent target of ransomware.
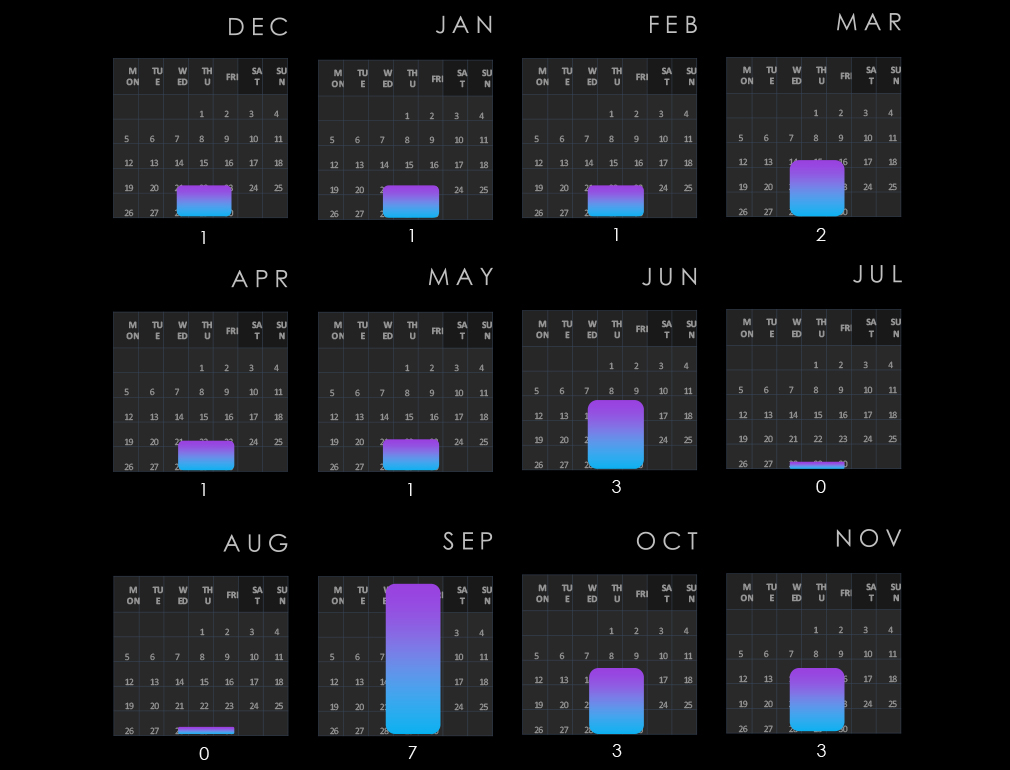
Over the past 12 months, professional goods & services organizations recorded victims across 23 of the 34 Advanced Persistent Threat (APT) campaigns observed – an incidence rate of 68%.
These victims spanned multiple segments within the professional goods & services industry as per below:
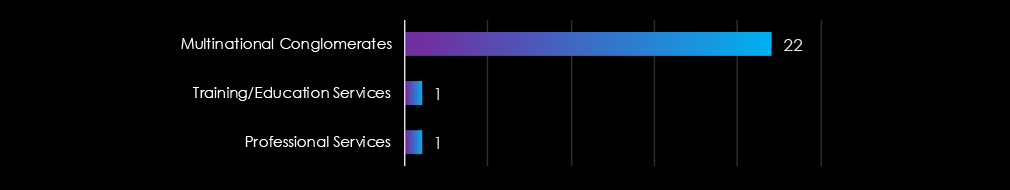
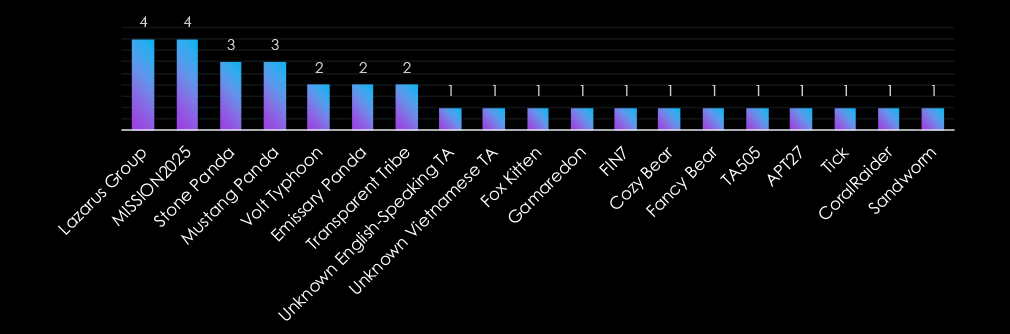
The Professional Goods & Services industry is targeted by a mix of nation-state and financially motivated actors. Chinese groups, including Lazarus Group, MISSION2025, Stone Panda, and Mustang Panda, dominate, focusing on espionage and intellectual property theft. Russian actors such as Cozy Bear, Fancy Bear, and Gamaredon prioritize intelligence gathering and strategic disruption.
Financially motivated groups like FIN7 and TA505 exploit the sector for data extortion and ransomware. Lesser-known or emerging actors, such as Unknown Vietnamese TA and Fox Kitten, reflect the industry’s appeal to a growing range of adversaries.
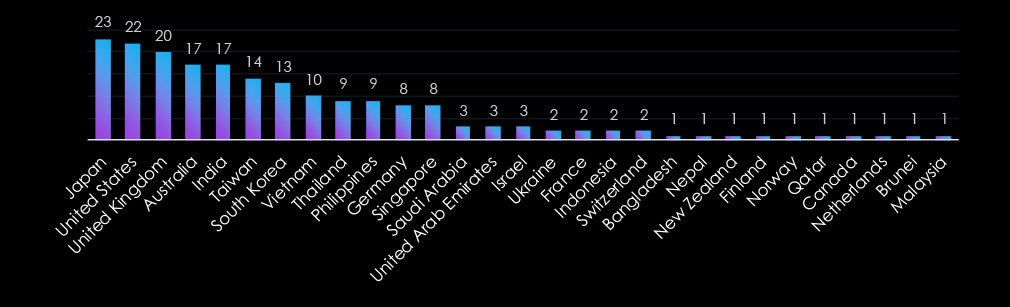
The Professional Goods & Services industry is globally targeted, with Japan, the United States, and the United Kingdom leading due to their prominence in the sector. Asia-Pacific nations, including India, Taiwan, and South Korea, also feature prominently, reflecting the region’s growing professional goods & services industry.
Emerging markets such as Vietnam, the Philippines, and Indonesia highlight the attackers’ expanding interest in developing economies. The inclusion of smaller nations like Finland, Qatar, and Brunei demonstrates the broadening scope of threats, targeting both established and emerging markets across the globe.
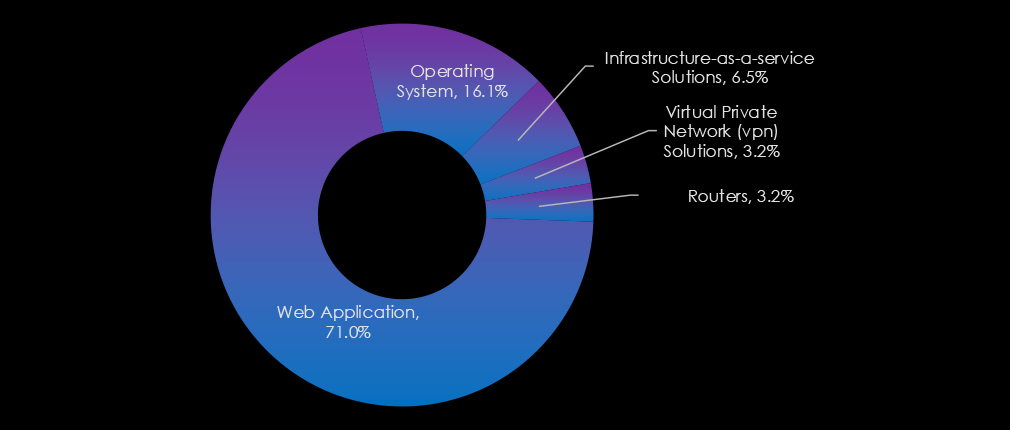
Web applications dominate, reflecting their vulnerability as internet-facing systems integral to business operations. Operating systems are also heavily targeted, underscoring their foundational role in infrastructure. Additionally, infrastructure-as-a-service solutions, VPN solutions, and routers appear as key targets.
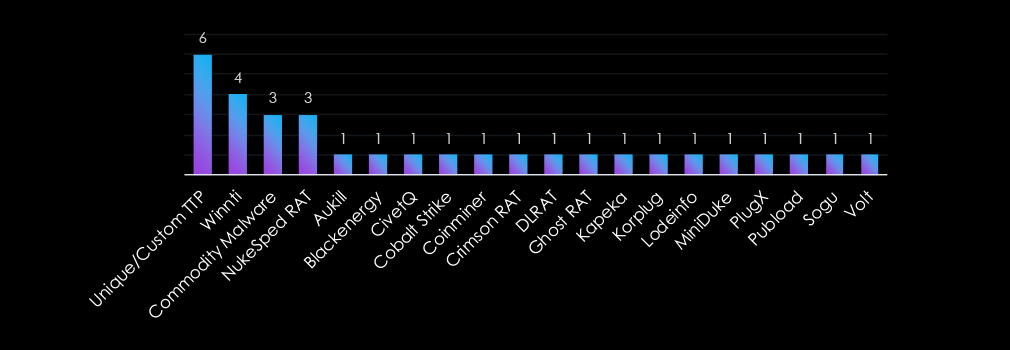
The industry faces a diverse range of malware threats, blending sophisticated custom tools with widely used strains. Unique/Custom TTPs lead, reflecting attackers’ tailored approaches to exploit vulnerabilities. Winnti and NukeSped RAT highlight their persistent use for espionage and long-term infiltration.
Tools like Cobalt Strike and PlugX underscore versatility for data theft and system compromise, while niche malware such as Coinminer and Crimson RAT indicate opportunistic campaigns.
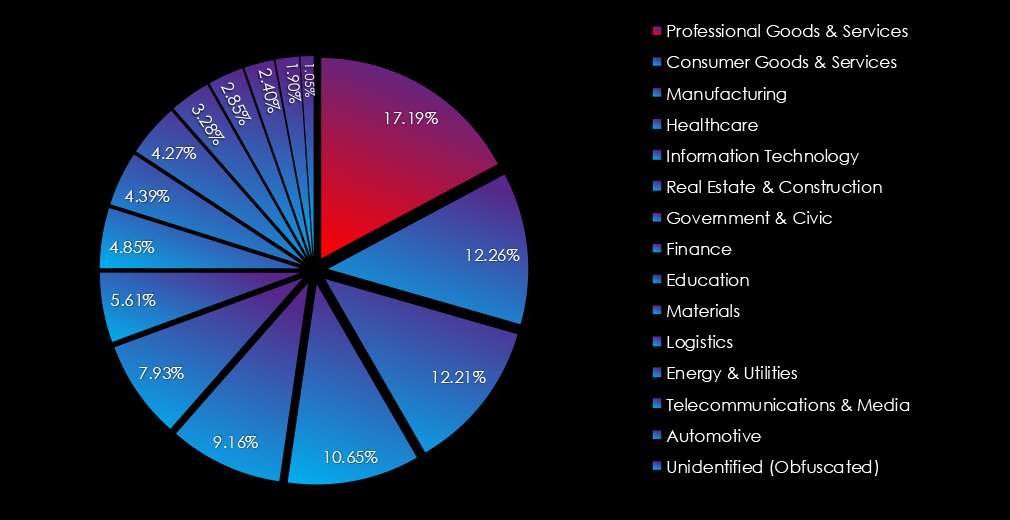
In the past 12 months, CYFIRMA has identified 897 verified professional goods & services industry ransomware victims. This accounts for 17.19% of the overall total of 5,219 ransomware victims during the same period.
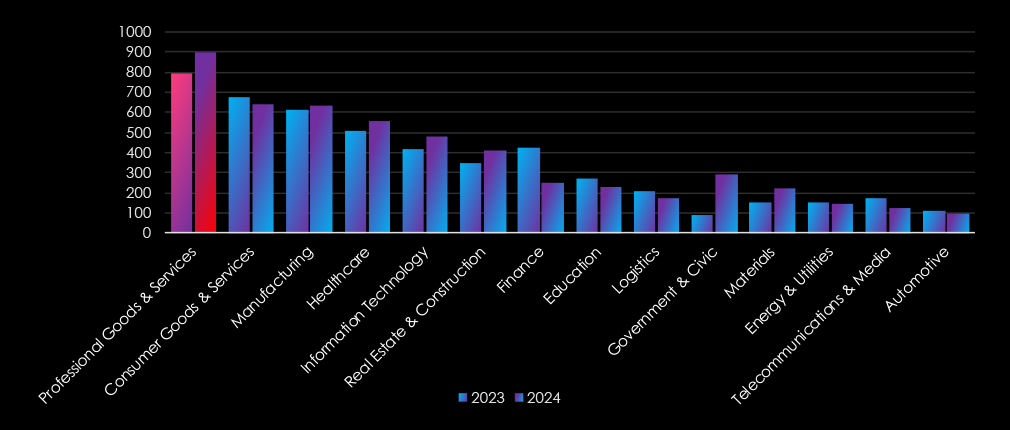
The industry recorded a consistently high and growing number of recorded victims, with a 12.97% increase from the previous year. It ranked in 1st place for both years combined as well as 1st for both consecutive years as the most frequent victims of ransomware.
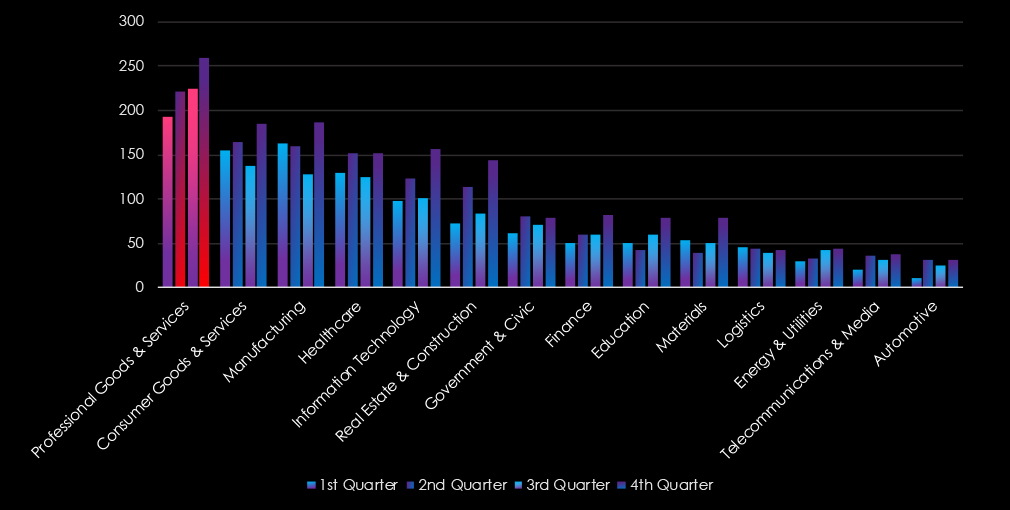
The professional goods & services industry experienced gradual growth from quarter to quarter, further cementing the industry as the most frequent target of ransomware.
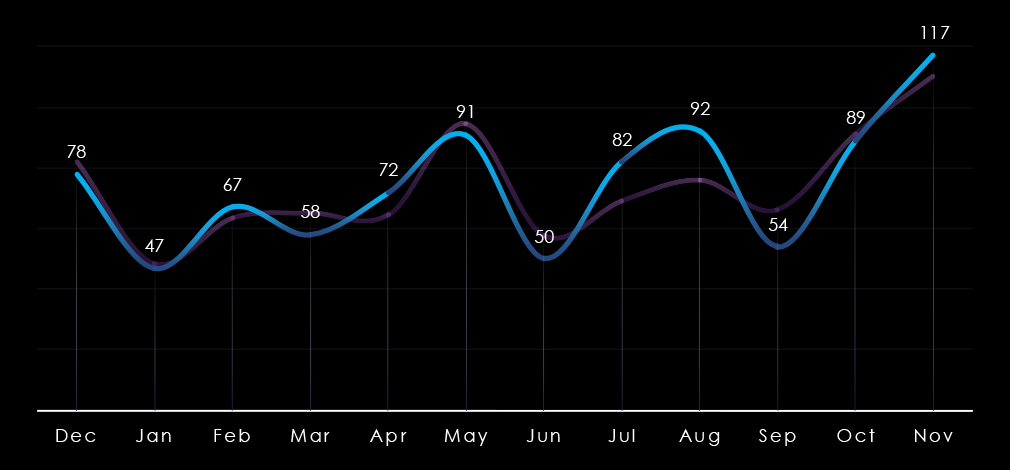
Monthly activity nearly perfectly follows the scaled-down global trendline. There is a mild above-average spike in July and August. By the end of the year, during October and November, the number of victims sharply rose in line with global activity, implying elevation into 2025.
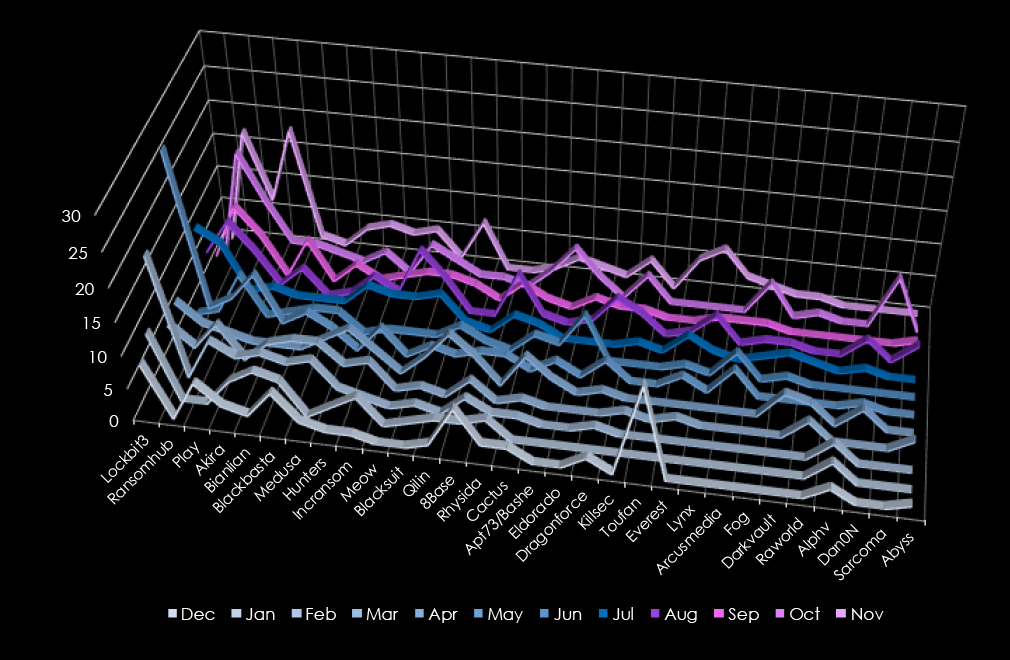
In total 74 out of 97 gangs recorded victims in the professional goods & services industry, with a 76% participation.
A breakdown of the top 30 gang’s monthly activity provides insights into which gangs were active each month.
LockBit3 dominated ransomware activity with 95 victims, peaking in February (19 victims). RansomHub followed with 75 victims, showing increasing activity from August onward, peaking in November (17 victims).
Play targeted 66 victims, maintaining steady activity with peaks in February, March, and November (7 victims each). Akira impacted 52 victims, showing a late-year surge in November (18 victims) and consistent activity in May (10 victims). Bianlian (43 victims) demonstrated moderate activity throughout the year, peaking in February and September.
Blackbasta and Medusa (37 and 35 victims, respectively) maintained steady activity, with Blackbasta active early in the year and Medusa showing consistent operations across multiple months. Hunters (32 victims) and Incransom (30 victims) exhibited scattered campaigns, with notable spikes for Hunters in July and for Incransom in January and November.
Emerging groups like Meow (27 victims) peaked in late summer and fall, particularly August and October, while Blacksuit (26 victims) maintained activity throughout the year, with a late peak in September. Qilin (25 victims) concentrated activity in April and November, while 8Base (23 victims) peaked early in the year.
Smaller groups such as Rhysida (21 victims), Cactus (20 victims), and Eldorado (15 victims) showed intermittent campaigns. Notable isolated surges include Toufan’s December victims dump and Sarcoma’s October focus (8 victims).
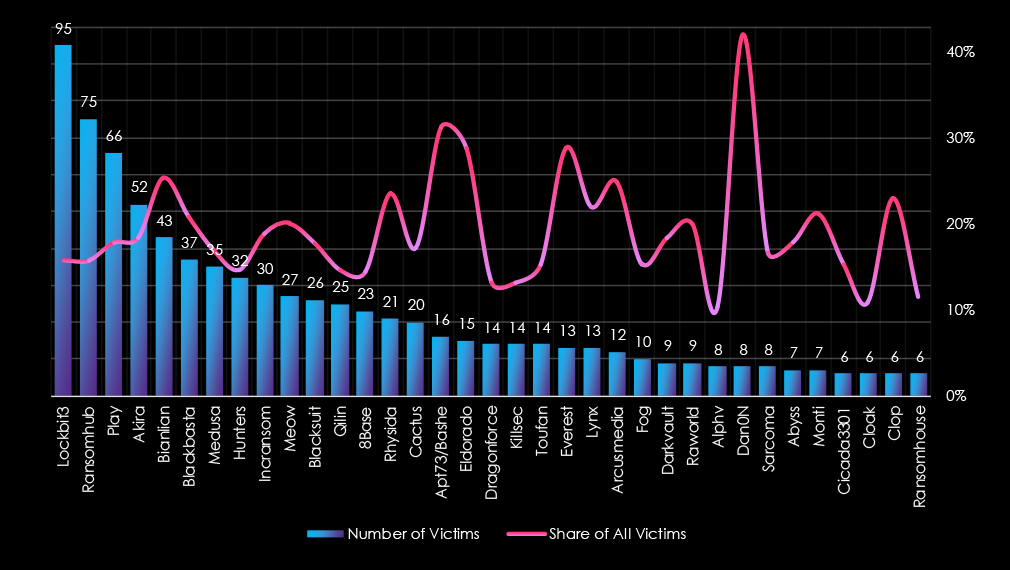
Looking at the top 35 gangs, the share of all victims in this industry is above 10% for all top 35 gangs. The top 5 trendline of the share of all victims starts at 15% and tops 25% for the Bianlian gang.
LockBit3 and RansomHub lead ransomware activity within this sector, with 95 victims (15.86%) and 75 victims (15.79%), respectively, highlighting significant targeting. Play (66 victims, 17.93%) and Akira (52 victims, 18.51%) also show substantial activity and a strong focus on the professional goods and services industry.
Several gangs demonstrate a substantial focus on this industry:
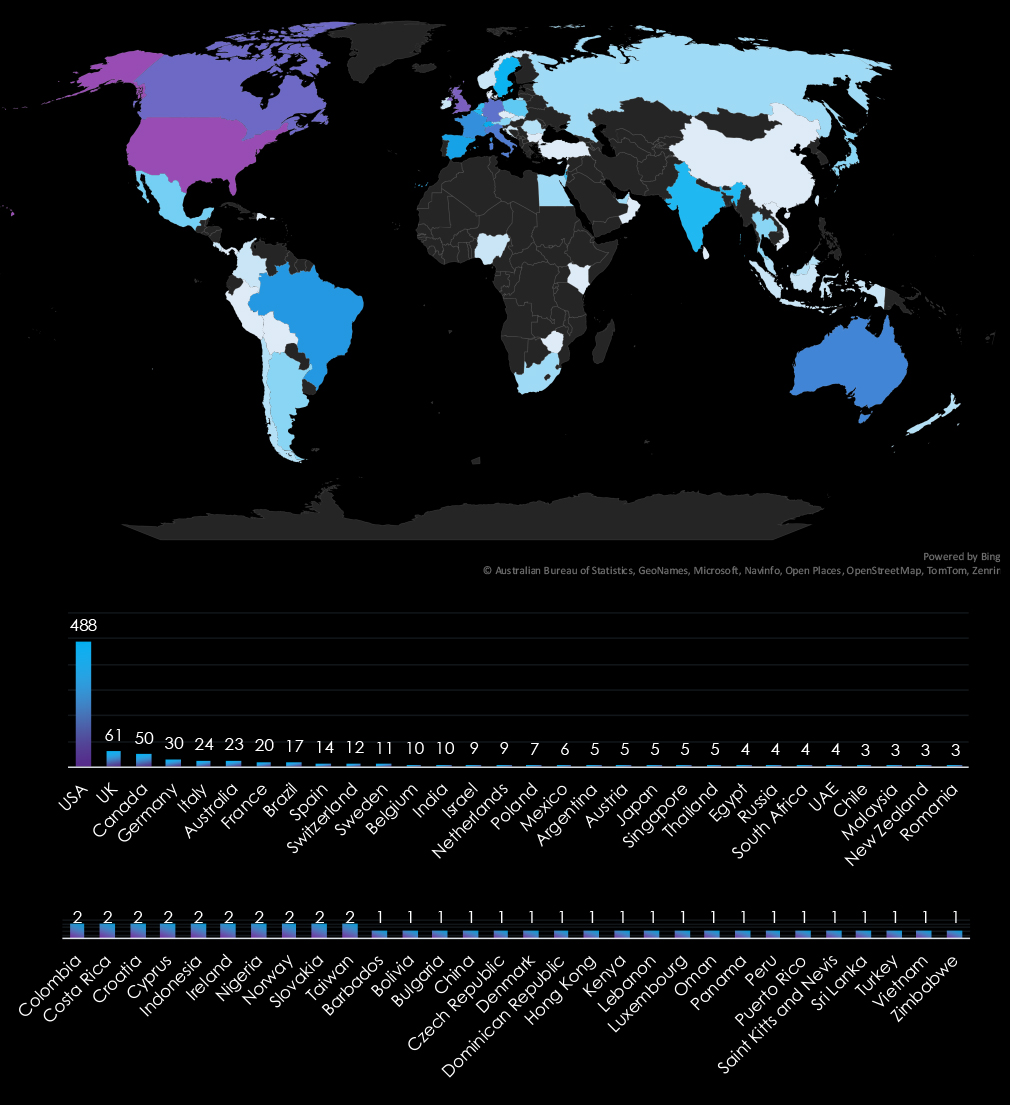
The USA accounts for 54.4% of ransomware victims in the Professional Goods & Services industry in 2024. The next most affected countries are the UK with 61 victims, Canada with 50, Germany with 30, and Italy with 24.
A total of 61 countries reported victims, with 20 of them having only one victim each.
Risk Level Indicator: High

APT Campaigns
The professional goods & services sector experienced a high 68% incidence rate across observed APT campaigns, driven by nation-state espionage and financially motivated attacks. Chinese groups, including MISSION2025 and Mustang Panda, dominate, while Russian groups like Cozy Bear and Fancy Bear focus on intelligence gathering. Emerging actors like Fox Kitten and Southeast Asian TAs add to the diverse threat landscape.
Actors: MISSION2025, Mustang Panda, Cozy Bear, FIN7, TA505; emerging actors like Fox Kitten.
Geographic Focus: U.S., Japan, U.K.; growing focus on Asia-Pacific (India, Taiwan, South Korea); emerging markets like Vietnam and the Philippines.
Targets: Web applications, operating systems, VPNs, routers, and IaaS solutions.
Malware: Winnti, NukeSped RAT, Cobalt Strike, PlugX; niche tools like Coinminer, Crimson RAT.
Ransomware
The professional goods & services industry was the most frequently targeted sector, with 897 victims (17.19% of the global total), marking a 12.97% year-over-year increase. Activity steadily grew across all quarters, peaking in Q4, and is expected to continue rising into 2025.
Victim Trends: Consistent growth; peaks in Q4 and mild spikes in July and August.
Key Actors: Most active were LockBit 3 (95 victims, peak in February), and Ransomhub (75 victims, peak in November).
Other notable gangs were Play (66 victims), Akira (52 victims, peak in November), and Bianlian (43 victims).
Geography: The U.S. accounted for 54% of victims; activity recorded in 61 countries.
Ranking: The professional goods & services industry ranked 1st as the most frequent victim of ransomware.
Over the past 12 months, consumer goods & services organizations recorded victims across 12 of the 34 Advanced Persistent Threat (APT) campaigns observed – an incidence rate of 35%.
These victims spanned multiple segments within the consumer goods & services industry as per below:
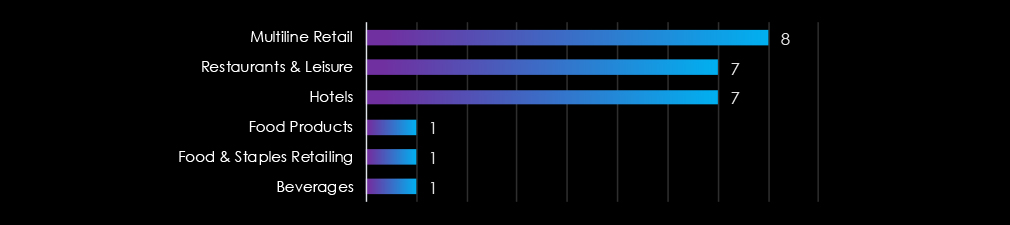
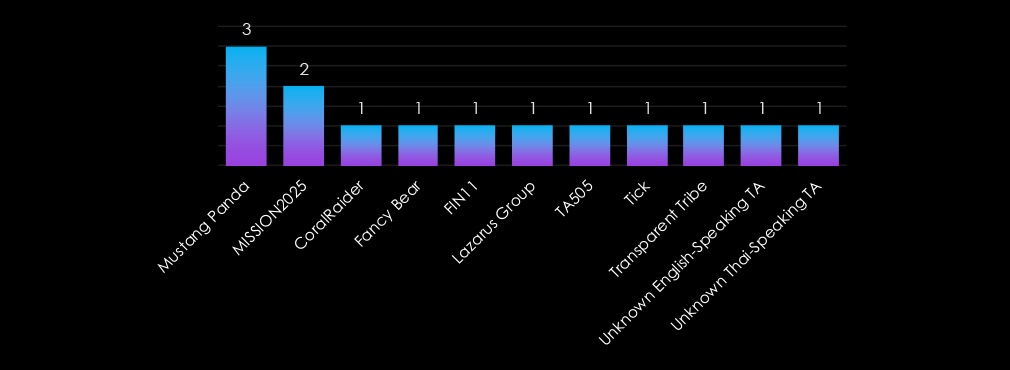
The Consumer Goods & Services industry is targeted by a mix of nation-state and financially motivated threat actors. Mustang Panda and MISSION2025 (China) focus on espionage and the theft of valuable data, likely related to supply chains or intellectual property.
Financially motivated groups like FIN11, Lazarus Group, and TA505 exploit the sector for ransomware and data extortion. Actors such as Fancy Bear (Russia) and Transparent Tribe (Pakistan) reflect geopolitical interests, while emerging groups like Unknown Thai-speaking TA and Unknown English-speaking TA suggest the industry’s appeal to a growing range of adversaries.
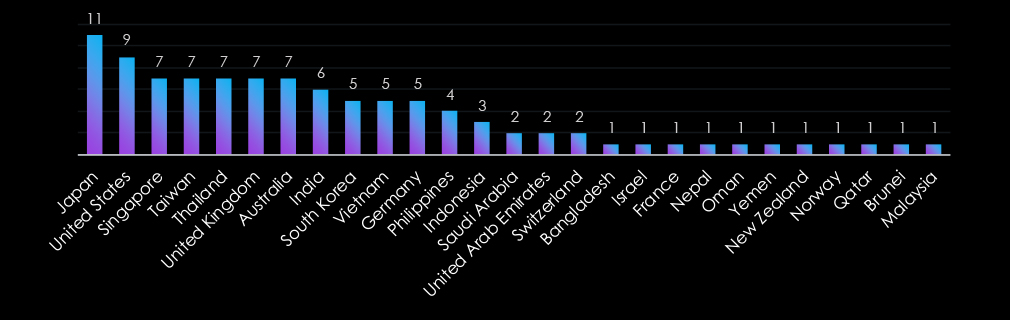
The Consumer Goods & Services industry faces global targeting, with Japan, the United States, and Singapore leading, reflecting their prominence in the sector. Asia-Pacific countries, including Taiwan, Thailand, India, and South Korea, are also heavily targeted, highlighting the region’s growing role in global consumer markets.
Emerging markets like the Philippines and Indonesia further emphasize attackers’ expanding reach. The inclusion of smaller nations such as Bangladesh, Nepal, and Brunei underscores the diverse scope of threats, targeting both established and developing markets in this industry.
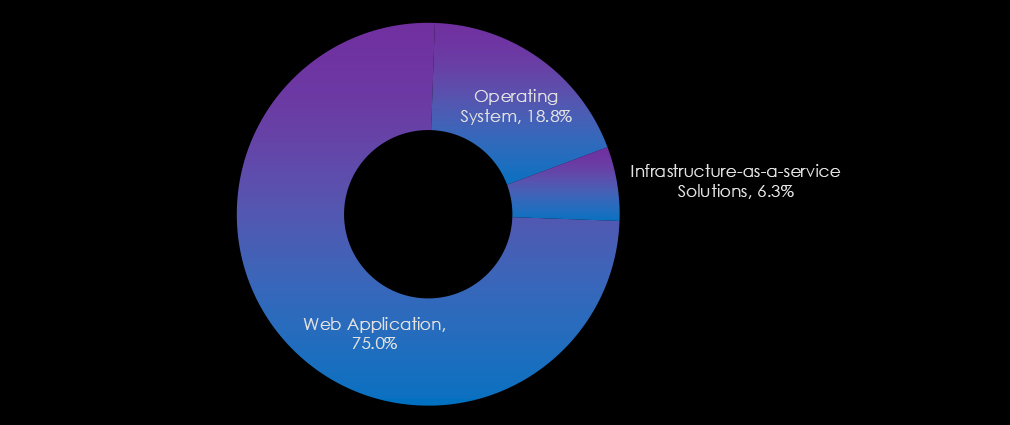
The industry’s most targeted technologies highlight a focus on critical digital infrastructure. Web applications dominate, reflecting their vulnerability as internet-facing systems essential for customer interaction and operational processes.
Operating systems are also key targets, emphasizing attackers’ interest in exploiting foundational technologies. Additionally, infrastructure-as-a-service solutions are targeted, underscoring the risks associated with cloud-based services in this sector.
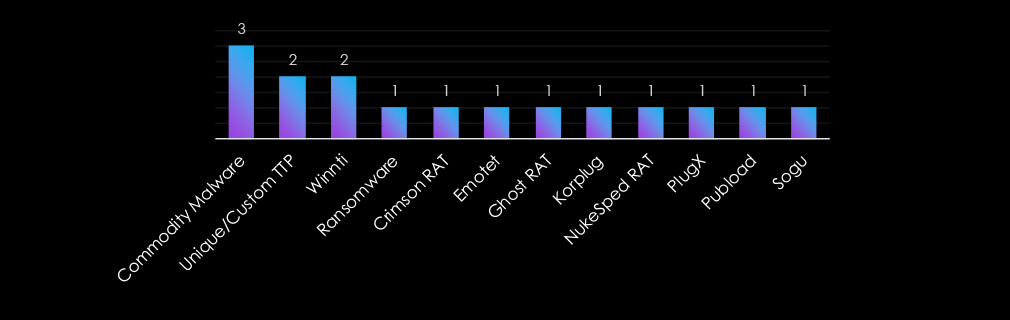
The Consumer Goods & Services industry faces a mix of sophisticated and widely available malware threats. Commodity Malware leads, reflecting its accessibility and effectiveness for broad campaigns, while Unique/Custom TTPs and Winnti emphasize tailored attacks for espionage and persistence.
Tools like ransomware and Emotet highlight financial extortion and data theft, while PlugX, Crimson RAT, and NukeSped RAT demonstrate a focus on infiltration and intelligence gathering.
In the past 12 months, CYFIRMA has identified 640 verified consumer goods & services organization ransomware victims. This accounts for 12.39% of the overall total of 5,219 ransomware victims during the same period.
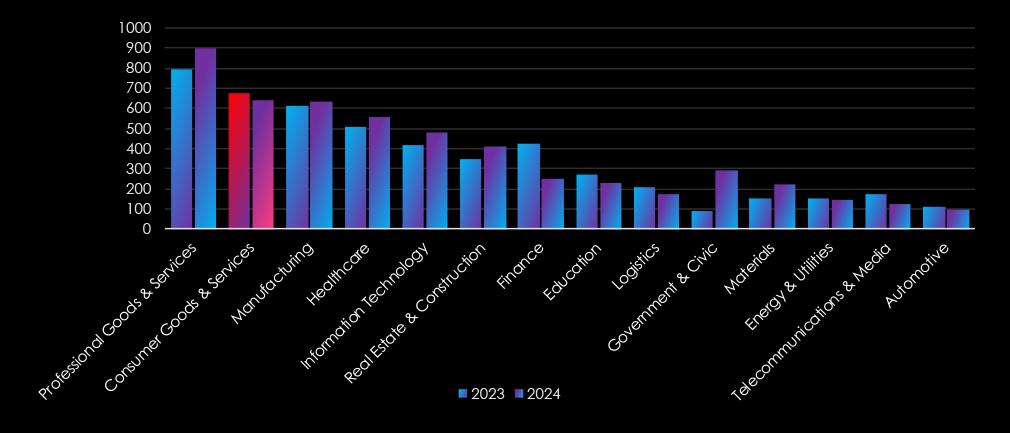
The industry recorded a minor decline of -5.19% in recorded victims from the previous year. It placed 2nd in a combined number of victims for both years, as well as retained the 2nd position as the most frequent victim each year.
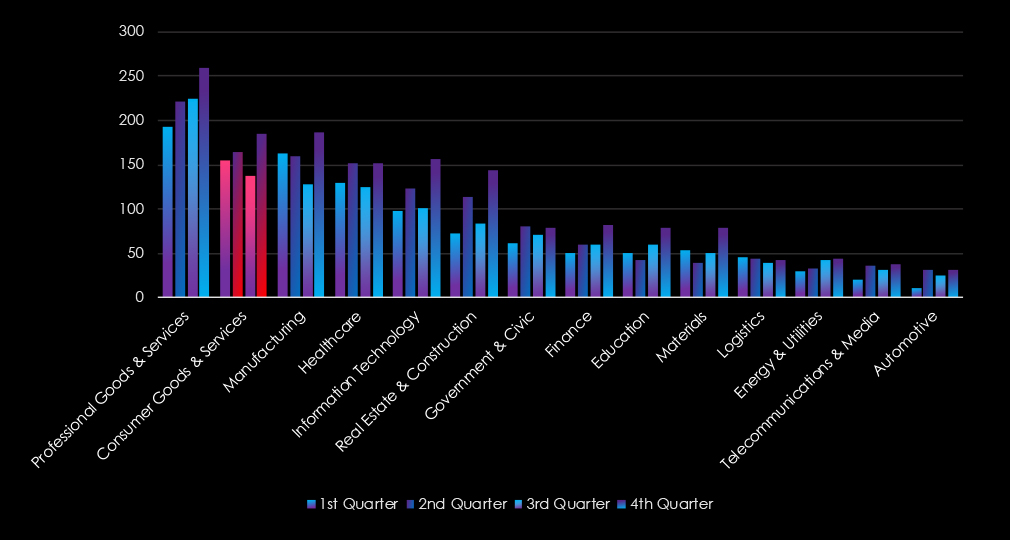
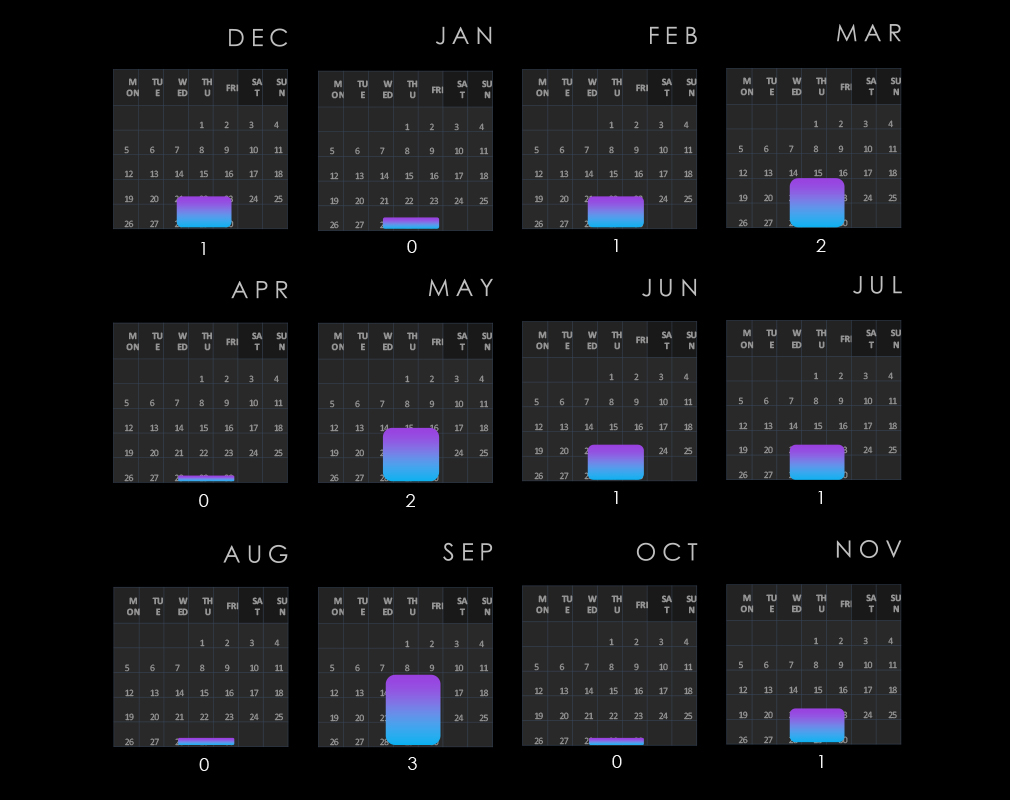
Consumer goods & services show sustained numbers of victims. A minor dip occurred during the third quarter but was followed by a mild spike in the fourth quarter.
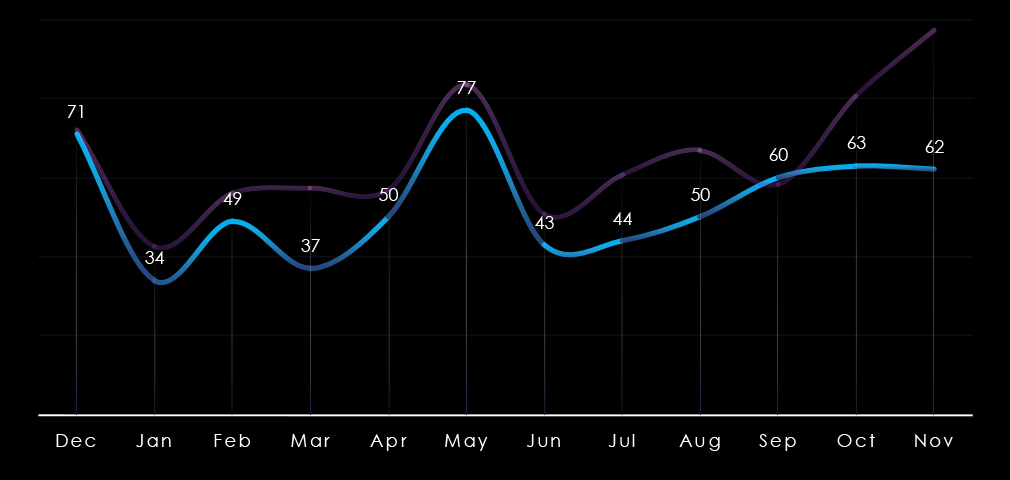
Monthly activity mostly follows the scaled-down global trendline. December 2023 and August 2024 recorded significant spikes. In October and November, we see a downward trend compared to the global line, implying a slowdown into 2025.
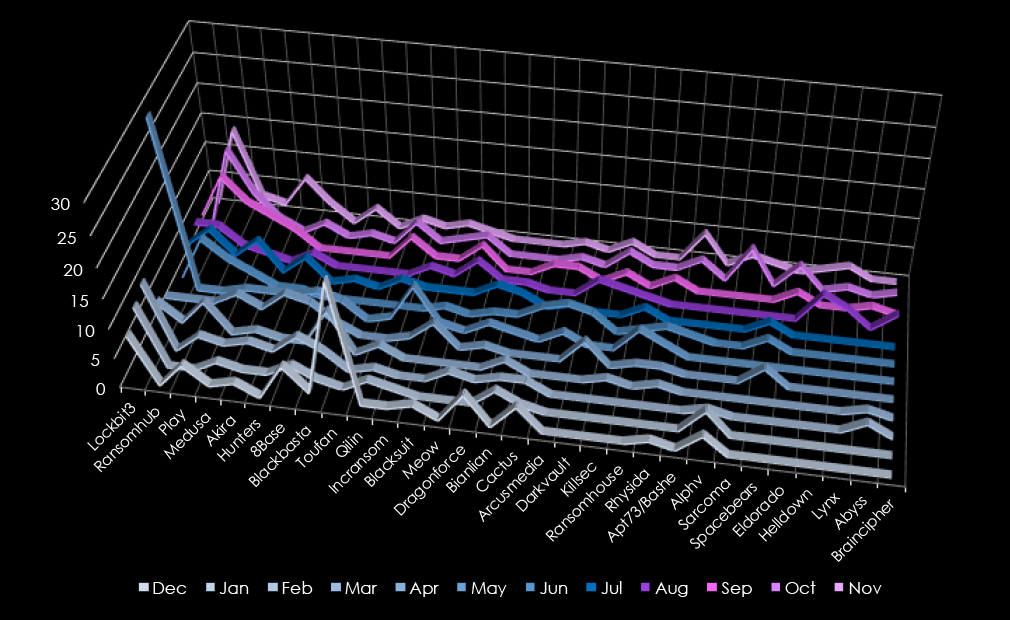
In total 73 out of 97 gangs recorded victims in the consumer goods & services industry, with 75% participation.
A breakdown of the top 30 gang’s monthly activity provides insights into which gangs were active each month.
LockbBt3 led ransomware activity with 82 victims, with notable spikes in February and January. RansomHub followed with 65 victims, surging in September through November, peaking at 14 victims in November.
Play impacted 44 victims, showing steady activity across most months. Medusa accounted for 33 victims, maintaining steady operations throughout the year and peaking in May and September. Akira and Hunters targeted 26 and 25 victims, respectively, with Akira peaking in November (7 victims) and Hunters in April (6 victims).
Emerging groups included 8Base (24 victims), active early in the year, peaking in December and February, and Blackbasta (23 victims), showing spikes in March and November. Toufan conducted a singular large campaign in December, affecting 21 victims.
Qilin (19 victims) was consistently active, with peaks in September and October. Groups like Incransom (16 victims) and Blacksuit and Meow (15 victims each) showed scattered campaigns, with Meow active primarily in late summer and fall.
Smaller actors like Dragonforce (14 victims), Bianlian and Cactus (12 each), and Arcusmedia (11 victims) demonstrated sporadic but impactful campaigns. Groups such as Darkvault, Killsec, and Ransomhouse (10 victims each) had targeted activity, often peaking mid-year.
Emerging groups like Sarcoma, Spacebears, and Alphv (8 victims each) had limited but concentrated activity, while others such as Eldorado, Helldown, and Lynx (6 victims each) contributed with isolated late-year campaigns.
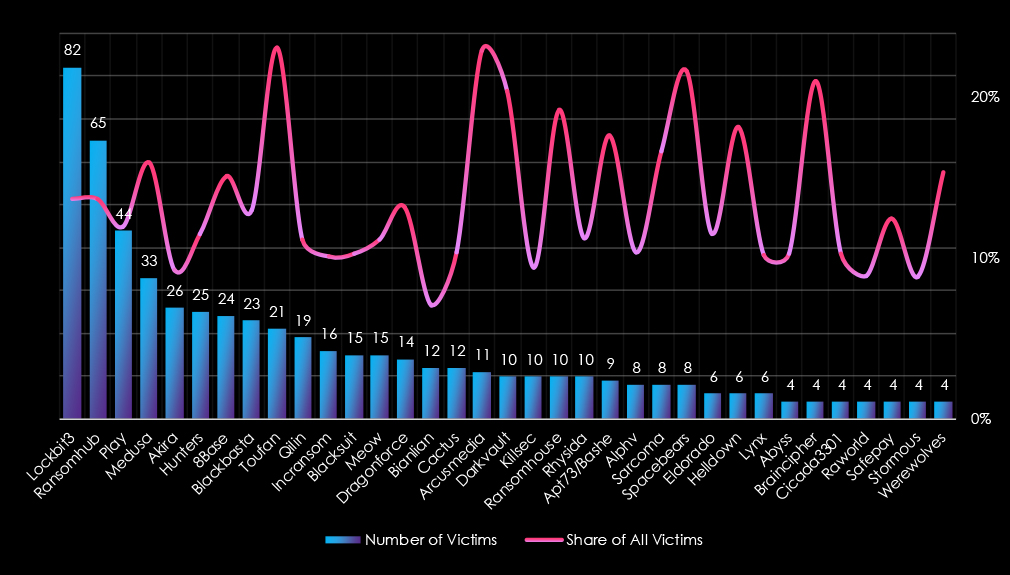
Analysis of the top 35 gangs shows LockBit3 (82 victims, 13.69%) and RansomHub (65 victims, 13.68%) leading ransomware activity in this sector, reflecting strong targeting. Play (44 victims, 11.96%), and Medusa (33 victims, 15.94%) also show significant activity and focus on consumer goods and services.
Several gangs exhibit notable focus on this industry:
It is important to note that consumer goods & services include many small to medium-sized businesses, which are easier targets for smaller gangs willing to accept relatively smaller ransoms. Therefore, the share of victims is among the highest across industries.
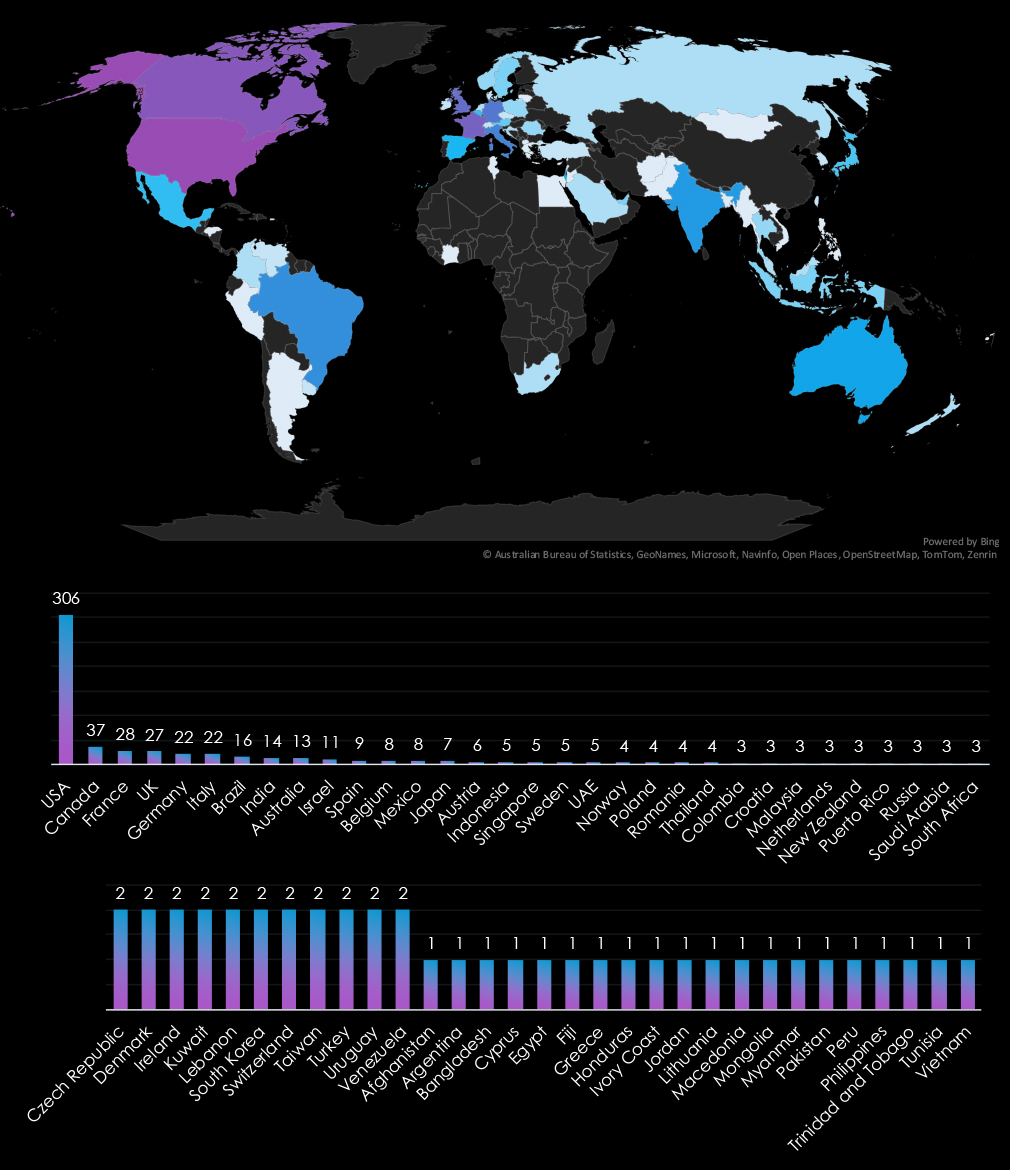
The USA accounts for 47.8% of ransomware victims in the Consumer Goods & Services industry in 2024. The next most affected countries are Canada with 37 victims, France with 28, the UK with 27, and Italy with 22.
A total of 64 countries reported victims, with 21 of them having only one victim each.
Risk Level Indicator: High

APT Campaigns
The consumer goods & services sector recorded a 35% incidence rate across observed APT campaigns, driven by a mix of nation-state espionage and financially motivated attacks. Groups like MISSION2025 and Mustang Panda target intellectual property and supply chain data, while financially driven actors such as Lazarus Group and FIN11 pursue ransomware and extortion. Emerging actors underscore the industry’s growing appeal to adversaries.
Actors: Mustang Panda, MISSION2025, FIN11, Lazarus, Fancy Bear; emerging Thai- and English-speaking TAs.
Geographic Focus: U.S., Japan, Singapore; heavy targeting in Asia-Pacific (Taiwan, Thailand, South Korea); expanding in Indonesia and the Philippines.
Targets: Web applications, operating systems, IaaS solutions.
Malware: Commodity Malware, Cl0p Ransomware, Emotet, PlugX, Crimson RAT, NukeSped RAT.
Ransomware
The consumer goods & services sector ranked as the second most targeted industry, with 640 victims (12.39% of the global total), despite a slight -5.19% year-over-year decrease. Activity remained steady across the year, with spikes in December 2023 and August 2024, and a tapering trend into late 2024.
Victim Trends: Sustained activity; peaks in December 2023 and August 2024, with a mild Q3 dip.
Key Actors: Most active were LockBit 3 (82 victims, spikes in January/February), and RansomHub (65 victims, peak in November).
Other notable gangs were Play (44 victims), Medusa (33 victims, peaks in May/September), and Akira (26 victims, peak in November).
Geography: The U.S. accounted for 48% of victims; activity recorded in 64 countries.
Ranking: The consumer goods & services industry ranked as the second most frequent victim of ransomware.
Over the past 12 months, real estate & construction organizations recorded victims across 3 of the 34 Advanced Persistent Threat (APT) campaigns observed – an incidence rate of 9%.
These victims spanned multiple segments within the real estate & construction industry as per below:
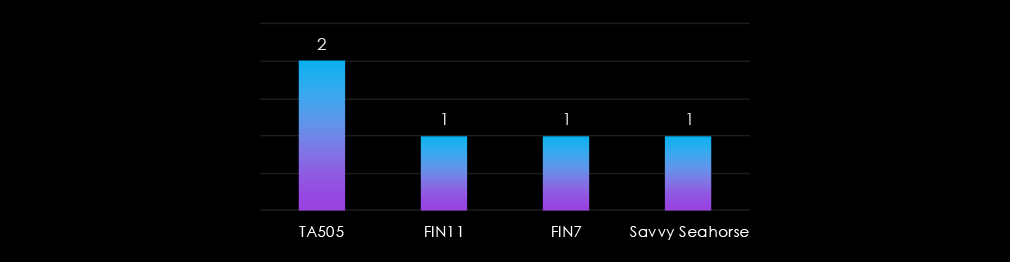
The Real Estate & Construction industry is primarily targeted by financially motivated threat actors. Groups like TA505, FIN11, and FIN7 exploit the sector for data extortion and ransomware attacks, leveraging its reliance on critical operational data.
The inclusion of Savvy Seahorse, a less well-known actor, suggests emerging threats targeting the industry. This focus on financial gain highlights the sector’s vulnerability to opportunistic and profit-driven cybercriminals.
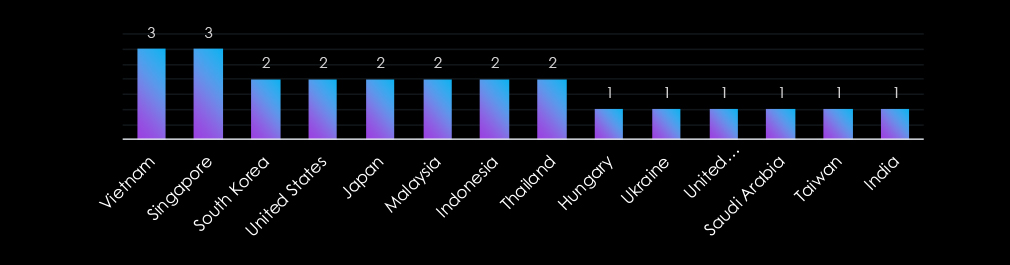
The Real Estate & Construction industry faces targeted attacks across a range of countries, with a notable focus on the Asia-Pacific region. Vietnam, Singapore, and South Korea lead, reflecting the region’s growing development and investment in real estate infrastructure.
Other heavily targeted nations, such as the United States and Japan, highlight attackers’ interest in established markets. Countries like Malaysia, Indonesia, and Thailand further emphasize the focus on emerging economies, while smaller markets such as Hungary and Ukraine illustrate the sector’s global appeal to cyber criminals.

The Real Estate & Construction industry’s primary targeted technology is web applications, reflecting their critical role in managing projects, client interactions, and operational data. As internet-facing systems, they are particularly vulnerable to exploitation.
The Real Estate & Construction industry is targeted with Unique/Custom TTPs, reflecting attackers’ tailored approaches to exploiting specific vulnerabilities within the sector.
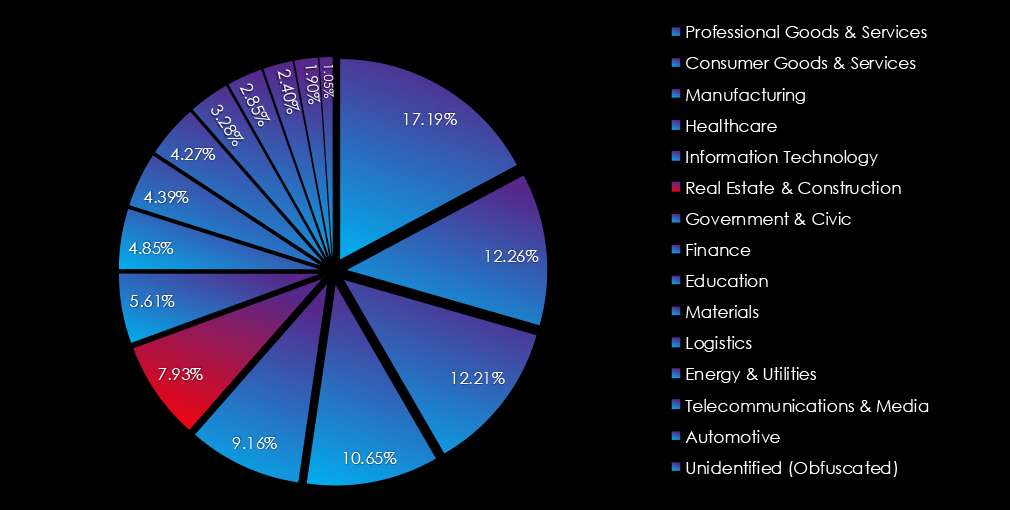
In the past 12 months, CYFIRMA has identified 414 verified real estate & construction industry ransomware victims. This accounts for 7.93% of the overall total of 5,219 ransomware victims during the same period.
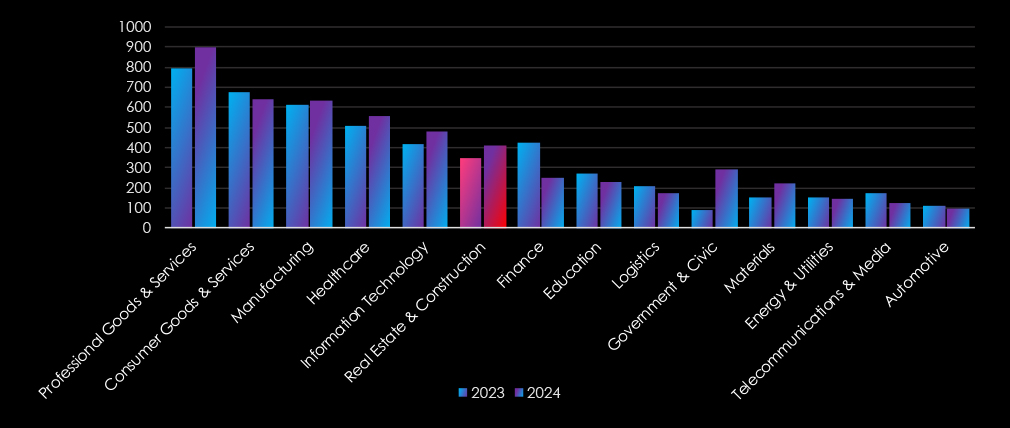
The industry recorded a moderately high and significantly growing number of recorded victims, with a 17.61% increase from the previous year. It ranked at 6th place for both years combined. It moved up from the 7th to the 6th position, securing the sixth spot as the most frequent victim of ransomware.
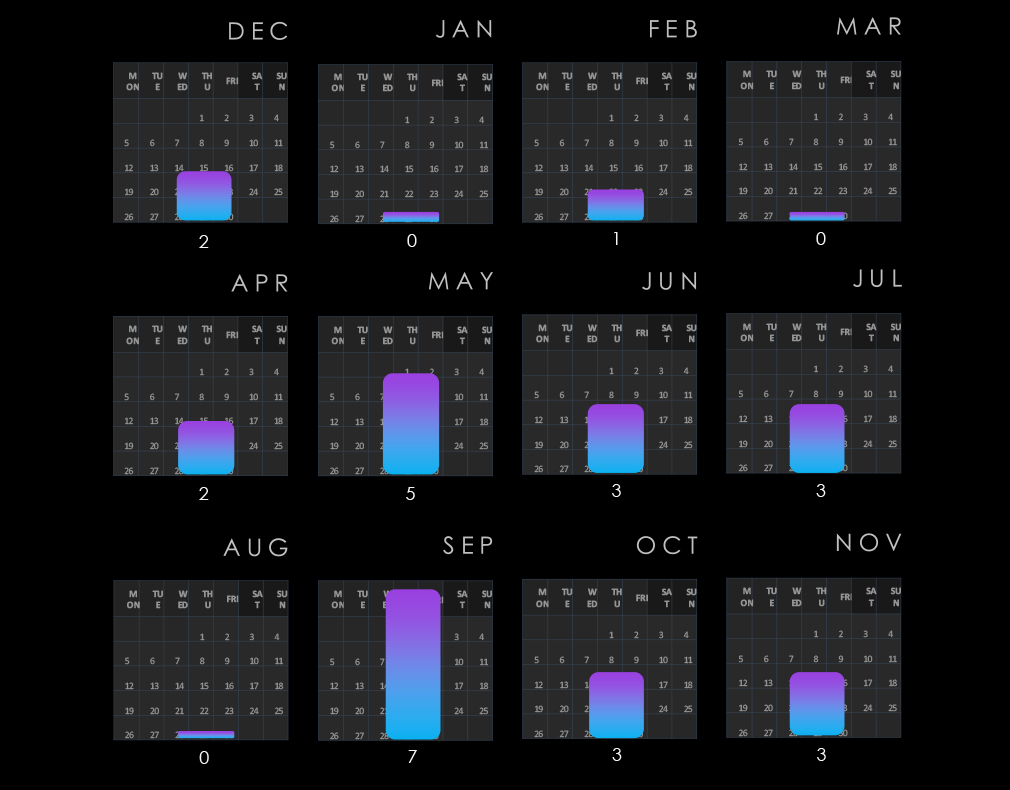
The real estate & construction industry experienced alternate growth from quarter to quarter, with spikes during the second and fourth quarters.
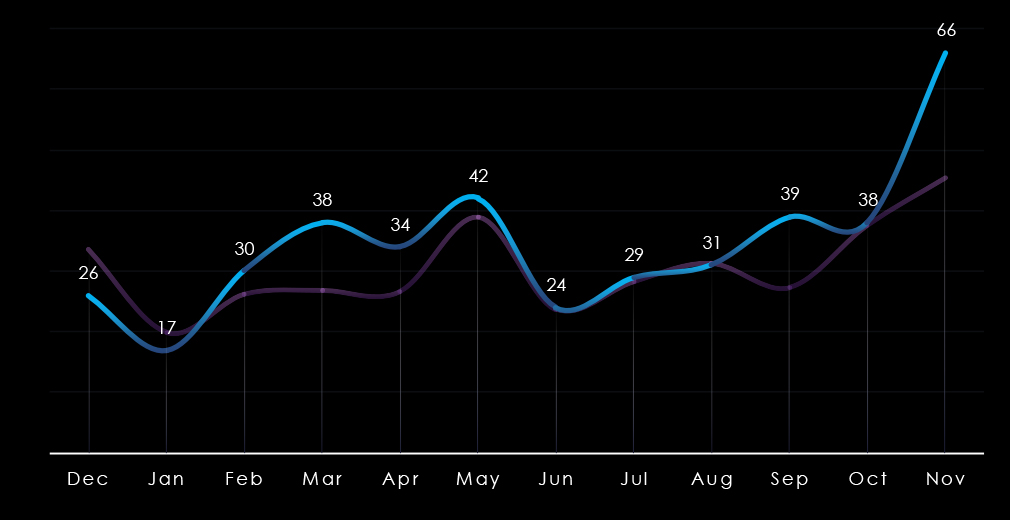
Monthly activity only roughly follows the scaled-down global trendline. There is a mild above-average spike from February to May. After a few months of alignment, activity in the industry spiked above average in September and especially in November, strongly suggesting elevation going into 2025.
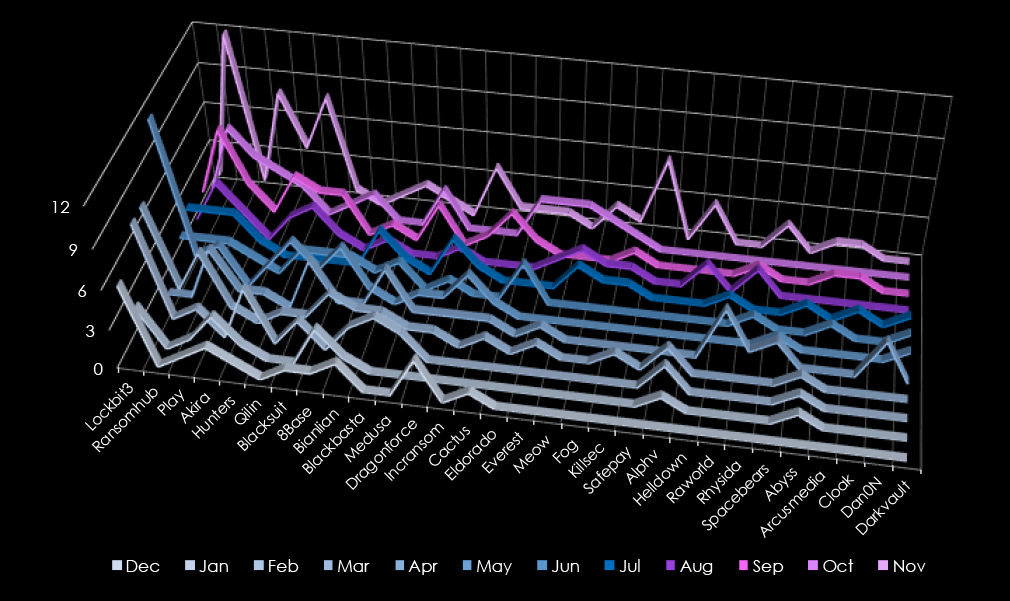
In total 59 out of 97 gangs recorded victims in the real estate & construction industry, with 61% participation.
A breakdown of the top 30 gang’s monthly activity provides insights into which gangs were active each month.
LockBit3 led ransomware activity with 47 victims. RansomHub followed with 39 victims, peaking in November (12 victims) and maintaining steady activity from July onward.
Play targeted 31 victims, with notable activity in March, April, and October. Akira, Hunters, and Qilin each accounted for 21 victims. Akira peaked in November (8 victims), Hunters in October and November, and Qilin surged in May and November.
Blacksuit (18 victims) and 8Base and Bianlian (16 each) maintained moderate activity, with Blacksuit peaking in April. Blackbasta (14 victims) was active early in the year, with peaks in March and May. Medusa (12 victims) and Dragonforce (11 victims) focused their campaigns in spring and summer, with Medusa peaking in October.
Smaller groups included Incransom (10 victims), Cactus, and Eldorado (8 each), with Eldorado showing late-year spikes. Meow and Everest (7 each) focused on fall operations, and Fog and Killsec (6 each) showed limited but steady activity.
Emerging actors such as Safepay (6 victims) concentrated all their activity in November, while Alphv, Helldown, Raworld, and Spacebears (5 victims each) demonstrated isolated campaigns. Minor actors like Abyss (4 victims), Arcusmedia, and Cloak (3 each) contributed to the fragmented landscape.
Overall, LockBit3, RansomHub, and Play dominated the landscape, while Akira and Hunters showed seasonal peaks.
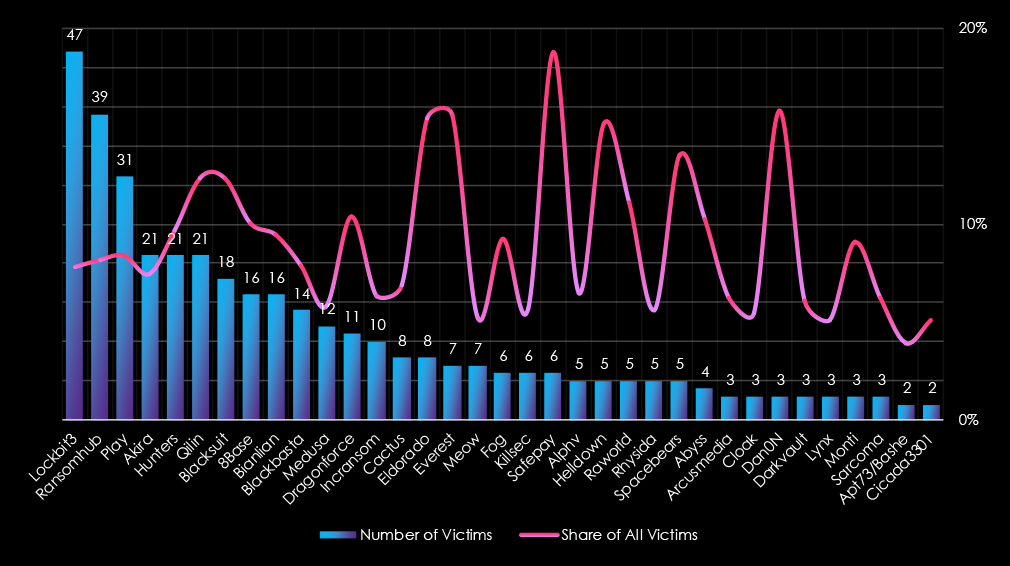
A review of the top 35 gangs shows LockBit3 leads ransomware activity in this sector, with 47 victims (7.85%), reflecting widespread activity but not a concentrated focus. RansomHub (39 victims, 8.21%) and Play (31 victims, 8.42%) also show significant activity but are distributed across multiple industries. Akira and Hunters, each with 21 victims (7.47% and 9.68%, respectively), also highlight moderate activity within this industry.
Several gangs demonstrate a meaningful focus on the real estate and construction industry:
Some gangs exhibit disproportionately high percentages due to low victim counts:
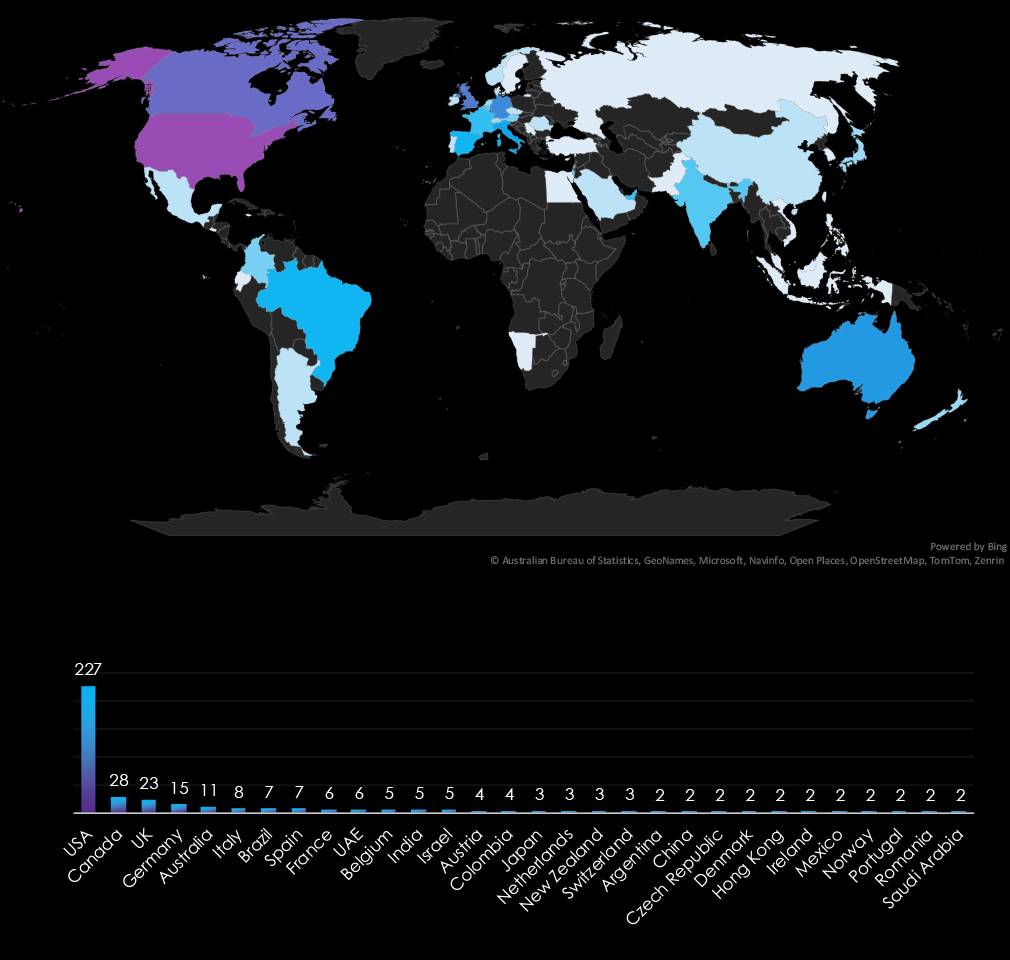
The USA accounts for 54.8% of ransomware victims in the Real Estate & Construction industry in 2024. The next most affected countries are Canada with 28 victims, the UK with 23, Germany with 15, and Australia with 11.
A total of 49 countries reported victims, with 19 of them having only one victim each.
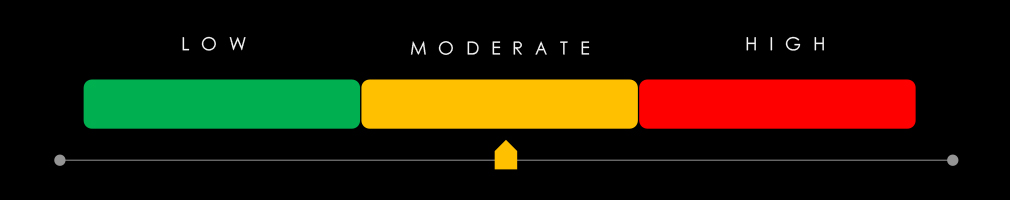
Risk Level Indicator: Low/Moderate
APT Campaigns
The real estate & construction sector recorded a low 9% incidence rate across observed APT campaigns, driven primarily by financially motivated groups such as TA505, FIN11, and FIN7. Emerging actors like Savvy Seahorse highlight the sector’s vulnerability to opportunistic threats focused on data extortion and ransomware.
Actors: TA505, FIN11, FIN7; emerging actor Savvy Seahorse.
Geographic Focus: Asia-Pacific (Vietnam, Singapore, South Korea); established markets like U.S. and Japan; emerging markets including Malaysia, Indonesia, and Thailand.
Targets: Web applications, reflecting their critical role in managing projects and operational data.
Malware: Unique/Custom TTPs targeting industry-specific vulnerabilities.
Ransomware
The real estate & construction industry accounted for 414 ransomware victims (7.93% of global total), with a 17.61% year-over-year increase. Activity alternated across quarters, with notable spikes in Q2 and Q4, especially in September and November, signaling heightened risks into 2025.
Victim Trends: Sustained activity; Peaks in Q2 (April-May) and Q4 (November).
Key Actors: the most active were LockBit 3 (47 victims), and RansomHub (39 victims, peak in November).
Other notable gangs were Play (31 victims, active in March, April, and October), and Akira (21 victims, peak in November).
Geography: The U.S. accounted for 55% of victims; activity was recorded in 49 countries.
Ranking: The real estate & construction industry ranked as the 6th most frequent victim of ransomware.
Over the past 12 months, government organizations recorded victims across 29 of the 34 Advanced Persistent Threat (APT) campaigns observed – an incidence rate of 35%.
We track only a single segment in the government category for APT campaigns as per below:

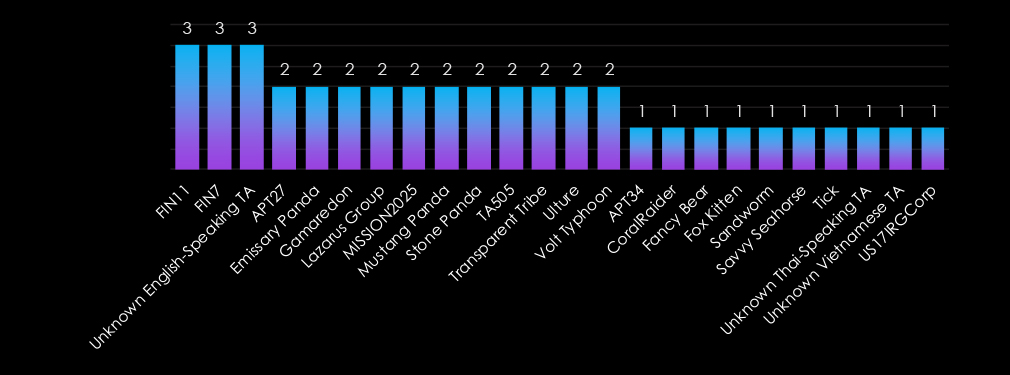
The government sector faces a diverse range of threats from both nation-state and financially motivated actors. FIN11 and FIN7 lead in targeting, reflecting financially driven motives such as ransomware and data extortion.
Nation-state groups like Lazarus Group, MISSION2025, and Mustang Panda (China) focus on espionage and the theft of sensitive information. Russian actors, including Gamaredon, Fancy Bear, and Sandworm, prioritize geopolitical objectives and intelligence gathering. Emerging actors, such as Unknown Thai-speaking TA and Unknown Vietnamese TA, highlight the sector’s appeal to a broader range of adversaries.
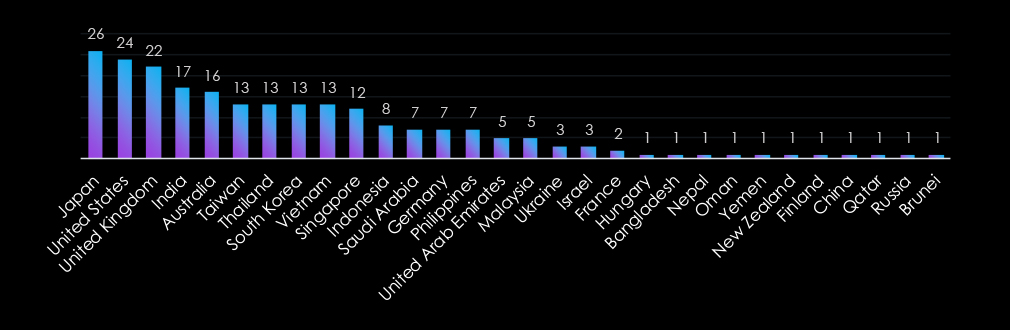
Government organizations are globally targeted, with a strong emphasis on advanced economies like Japan, the United States, and the United Kingdom, reflecting their prominence in geopolitical and global affairs. Asia-Pacific countries, including India, Taiwan, and South Korea, also feature prominently, highlighting the region’s growing strategic importance.
Emerging markets like Indonesia, the Philippines, and Malaysia further underscore attackers’ interest in developing nations. Smaller nations such as Oman, Nepal, and Brunei illustrate the sector’s appeal to a wide range of adversaries, targeting both established and less fortified government systems globally.
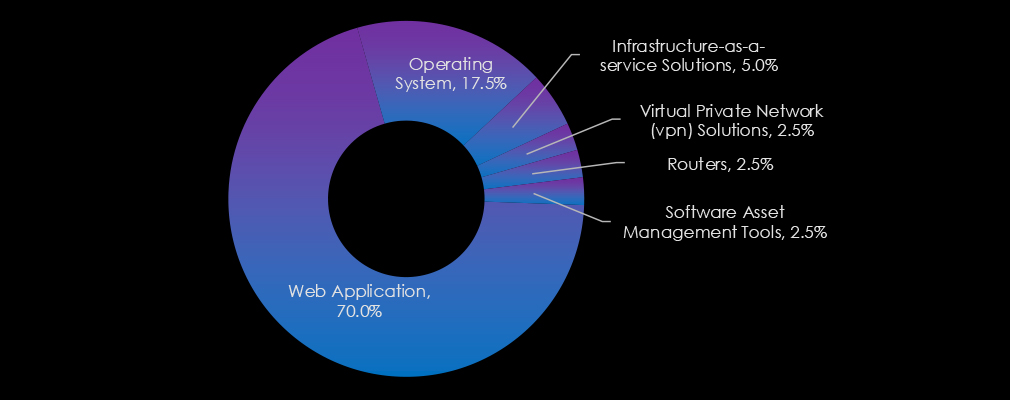
The Government & Civic Organizations sector’s most targeted technologies emphasize the attackers’ focus on foundational and internet-facing systems. Web applications dominate, reflecting their critical role in service delivery and their vulnerability to exploitation.
Operating systems also see significant targeting, highlighting their importance in maintaining governmental infrastructure. Additionally, technologies like infrastructure-as-a-service solutions, VPN solutions, and routers are targeted, underscoring the sector’s reliance on secure and resilient IT systems to protect sensitive operations and data.
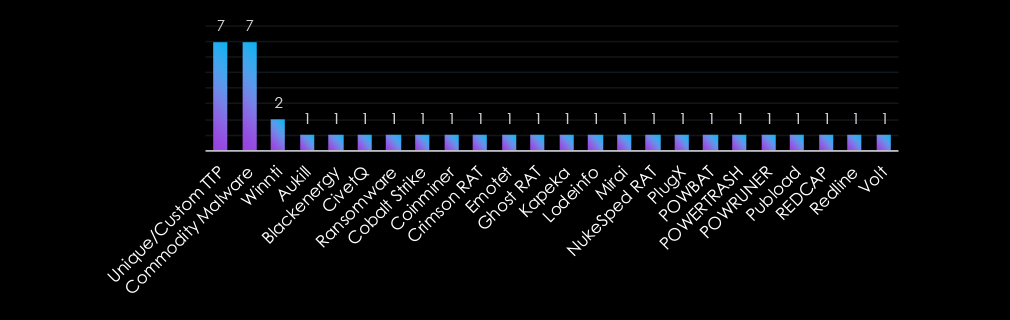
The Government & Civic Organizations sector is targeted with a diverse range of malware, reflecting both tailored and scalable approaches. Unique/Custom TTPs and Commodity Malware dominate, highlighting the balance between sophisticated, targeted attacks and accessible, off-the-shelf tools.
Winnti and tools like NukeSped RAT, PlugX, and Cobalt Strike underscore a focus on espionage and long-term infiltration. Financially motivated malware, such as ransomware and Emotet, emphasizes data theft and extortion, while niche tools like Mirai and Redline demonstrate opportunistic campaigns.
In the past 12 months, CYFIRMA has identified 293 verified government & civic sector ransomware victims. This accounts for 5.61% of the overall total of 5,219 ransomware victims during the same period.
The government and civic organizations recorded the highest year-to-year growth of recorded victims, with 229.21%, more than triple from the previous year. It ranked at 10th place for both years combined. However, it moved up from last 13th in 2023 to 7th place as the seventh most frequent victim of ransomware in 2024.
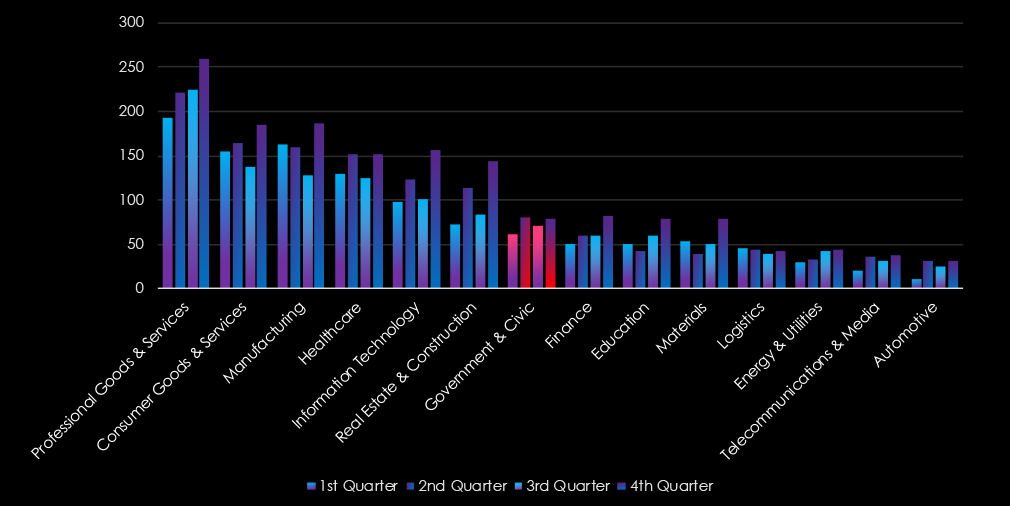
Government & civic organizations experienced sustained activity with moderate and alternate growth from quarter to quarter, with the second and fourth quarters showing mild spikes.
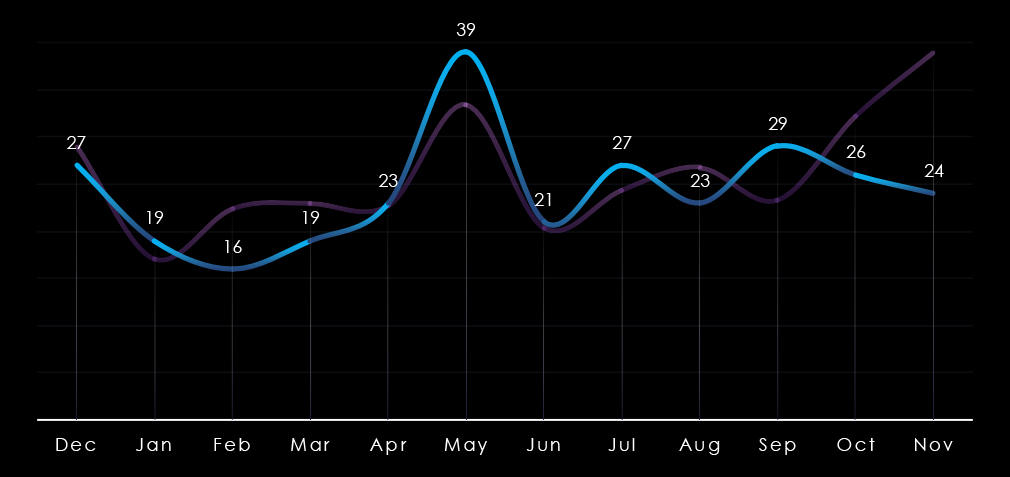
Monthly activity follows the scaled-down global trendline with mostly minor divergences. February, March, and August recorded mild dips. The global spike in May was moderately amplified for government & civic organizations. And despite a small spike in September, this sector diverged from the strong global upswing in October and November, suggesting a calmer start to 2025 relative to other industries.
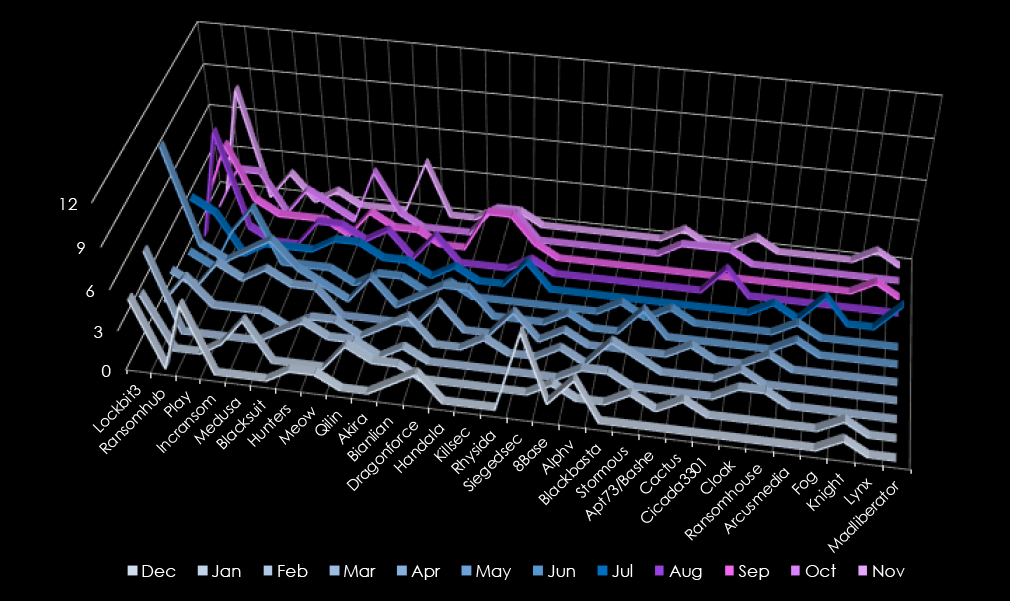
In total 54 out of 97 gangs recorded victims in government & civic organizations industry, with 56% participation.
LockBit3 and RansomHub led ransomware activity, each targeting 35 victims. RansomHub saw a late-year surge, peaking in November (8 victims), and consistent operations from July onward.
Play targeted 20 victims, with steady activity across the year and peaks in December, April, and October. Incransom and Medusa followed with 16 victims each. Incransom peaked in June and showed sporadic activity, while Medusa had its strongest months in May and October.
Blacksuit, Hunters, and Meow each accounted for 12 victims. Meow peaked in October with four victims, while Hunters and Blacksuit maintained steady but lower levels of activity throughout the year. Qilin (11 victims) was active sporadically, with peaks in February and August.
Less active groups like Akira (9 victims) and Bianlian, Dragonforce, and Handala (8 victims each) showed scattered activity, with Handala focusing on late-year operations. Emerging actors such as Killsec (7 victims) and Rhysida (6 victims) demonstrated limited campaigns, with peaks in October.
Siegedsec had a focused campaign in December, targeting six victims. Large gangs like 8Base (5 victims), Alphv (4 victims), and Blackbasta (4 victims) reported isolated victims. Stormous (4 victims) and groups like Cactus and Cicada3301 (3 victims each) reflected sporadic operations.
Overall, LockBit3 and RansomHub dominated with year-round campaigns, while Play and other mid-tier actors maintained steady operations. Smaller and emerging groups contributed sporadic but impactful campaigns, emphasizing a diverse ransomware ecosystem.
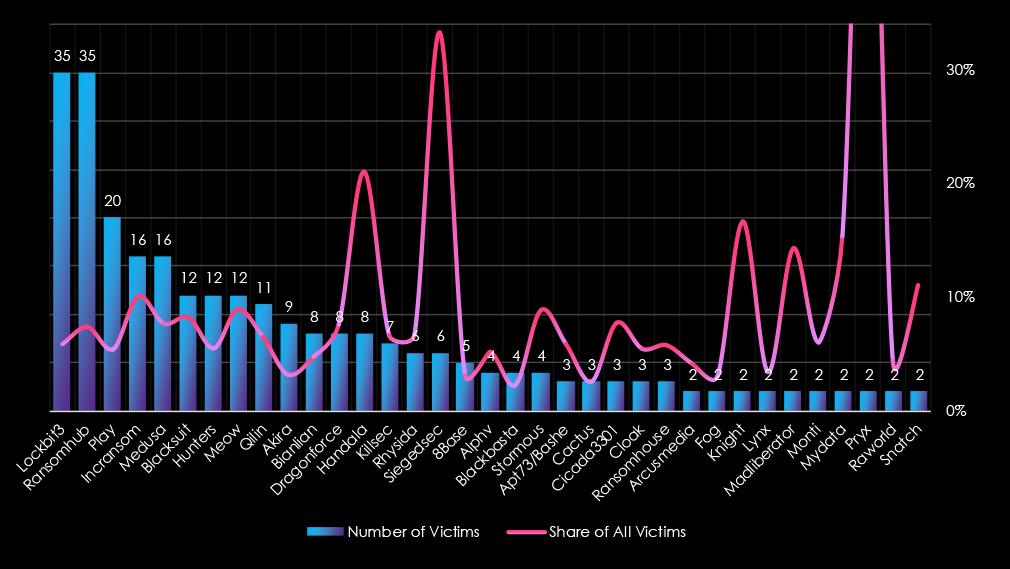
Looking at the top 35 gangs, LockBit3 and RansomHub lead in activity within this sector, with 35 victims each (5.84% and 7.37%, respectively), indicating significant activity but distributed targeting. Play (20 victims, 5.43%) also shows moderate activity. Other notable actors include Incransom (16 victims, 10.13%), and Medusa (16 victims, 7.73%), both showing stronger focus.
Several gangs demonstrate a notable focus on government and civic organizations:
Some gangs exhibit disproportionately high percentages due to low victim counts:
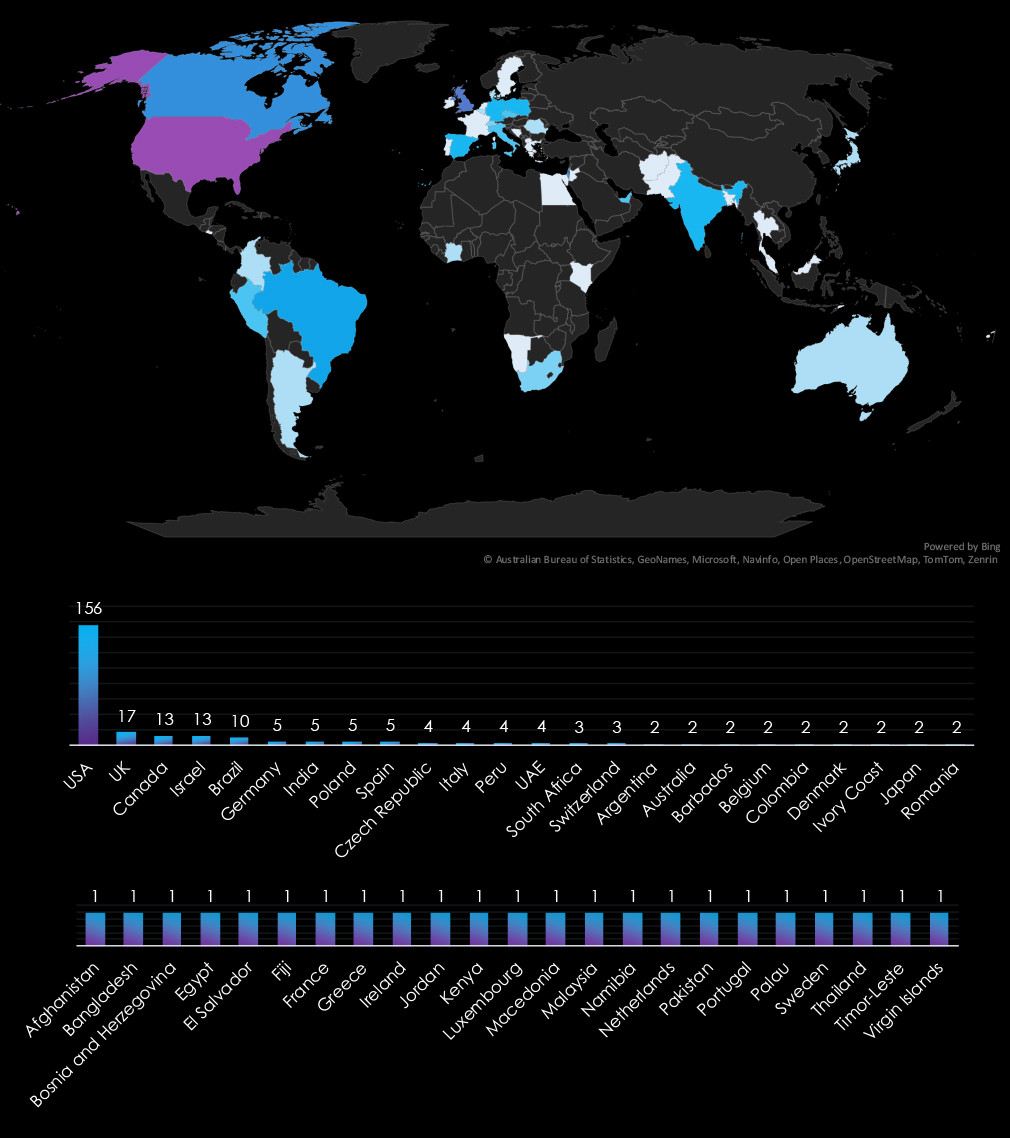
The USA accounts for 53.2% of ransomware victims in the Government & Civic Organizations industry in 2024. The next most affected countries are the UK with 17 victims, Canada with 13, Israel with 13, and Brazil with 10.
A total of 48 countries reported victims, with 24 of them having only one victim each.
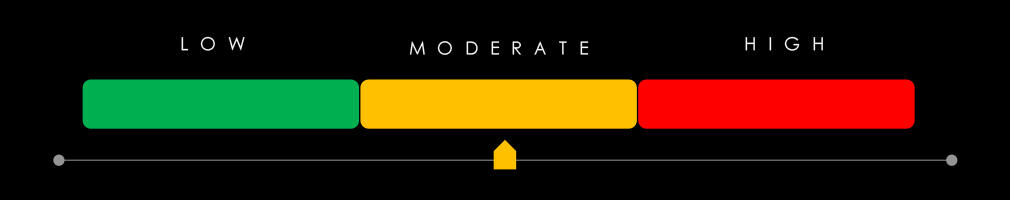
Risk Level Indicator: Moderate
APT Campaigns
Government and civic organizations experienced a 35% incidence rate across APT campaigns, driven by nation-state and financially motivated actors. Groups like Lazarus and MISSION2025 focus on espionage and intelligence gathering, while financially driven actors like FIN11 and FIN7 pursue ransomware and extortion. Emerging groups like Handala and Siegedsec reflect diverse motivations, including political and social agendas.
Actors: FIN11, FIN7, Lazarus, MISSION2025, Mustang Panda, Gamaredon, Fancy Bear, emerging groups like Handala and Siegedsec.
Geographic Focus: U.S., Japan, U.K.; Asia-Pacific nations (India, Taiwan, South Korea); emerging markets (Indonesia, Philippines, Malaysia).
Targets: Web applications, operating systems, IaaS solutions, VPNs, and routers.
Malware: Winnti, NukeSped RAT, PlugX, Cobalt Strike; ransomware, and tools like Mirai and Emotet.
Ransomware
The government & civic sector recorded 293 ransomware victims (5.61% of the global total), reflecting the highest year-over-year growth (+69.62%) among industries. Activity was consistent with peaks in Q2 and Q4, though the sector diverged from the global trend with a calmer October and November, suggesting a slower start to 2025.
Victim Trends: Peaks in May and November; minor dips in February, March, and August.
Key Actors: The most active were LockBit3 (35 victims, steady activity), and RansomHub (35 victims, peak in November).
Other notable gangs were Play (20 victims, peaks in December, April, October); Incransom, and Medusa (16 each).
Geography: The U.S. accounted for 53% of victims; activity was recorded in 47 countries.
Ranking: Government & civic organizations ranked as the 7th most frequent victim of ransomware.