


The CYFIRMA Industries Report provides cutting-edge cybersecurity insights and telemetry-driven statistics on global industries. Spanning the last 365 days and highlighting year-over-year changes between 2024 and 2025, this report covers 14 key industries and presents critical trends and data in a compelling infographic format.
This is Part 2 of the report covering only first 7 out of 14 industries. If you would like to view the complete report with global trends and all 14 industries detailed breakdown, it is available exclusively on our website.
Welcome to the CYFIRMA Infographic Industry Report, where we examine the external threat landscape across 14 industries over the past year. Through clear, data-driven visuals and expert insights, we present concise analyses of attack campaigns, underground and dark web chatter, reported vulnerabilities, and ransomware incidents affecting organizations worldwide.
Leveraging our cutting-edge platform telemetry and the deep expertise of our analysts, this report highlights detailed industry-specific breakdowns of first 7 out of 14 industries.
Our goal is to equip you with actionable intelligence that helps you stay ahead in the ever-evolving cybersecurity landscape.
CYFIRMA delivers pre-emptive cybersecurity, cyber threat intelligence, and external threat landscape management through its platforms, DeCYFIR and DeTCT. These platforms have been purpose-built over many years to continuously collect, correlate, and analyse large volumes of external threat data, combining proprietary intelligence automation with deep, hands-on cyber threat research.
For the purposes of this report, the analysis draws on intelligence generated from CYFIRMA’s platforms. The data referenced has been processed through automated correlation and enrichment mechanisms, informed and validated by human-led research and investigative expertise, and sourced from both structured and unstructured external intelligence channels.
While this report contains data collected and processed by our in-house AI and ML, all charts, statistics, and analyses are done by human CYFIRMA CTI analysts to ensure the highest quality and provide accurate insights.
Over the past 12 months, finance organizations recorded victims across 36 of the 43 Advanced Persistent Threat (APT) campaigns observed – an incidence rate of 84%. It is also an increase of 20% from 30 in the previous year.
These victims spanned multiple segments within the finance industry, as shown below:
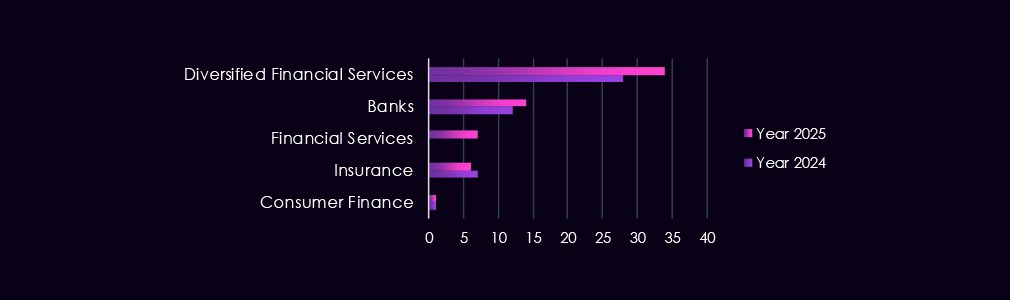
The finance industry remains a high-value target for both nation-state and financially motivated threat actors, with 2025 showing a clearer tilt toward state-linked access and persistence operations. China-aligned groups such as Volt Typhoon, Salt Typhoon, Stone Panda, Mustang Panda, and MISSION2025 increased activity in 2025.
At the same time, financially motivated groups such as FIN7, TA505, and FIN11 remain consistently active. Lazarus Group continues to operate at the intersection of state and financial motives, using attacks on financial entities to support state funding. The appearance of multiple newly tracked CC- and NS-prefixed groups in 2025 further reflects a broader and more geographically diverse threat landscape.
We observed geographic concentration of victims in the Asia-Pacific and Western economies, which remain primary targets. In 2025, Japan, the United States, the United Kingdom, Australia, India, South Korea, Thailand, and Taiwan continue to dominate, reflecting their role as major regional financial hubs and strategic targets. Compared to 2024, 2025 shows a broader regional spread, with increased activity across Southeast Asia and a steady expansion into the Middle East (e.g., Saudi Arabia, UAE) and Europe (Germany, France), indicating both opportunistic cybercrime and sustained nation-state interest in the globally connected finance industry.
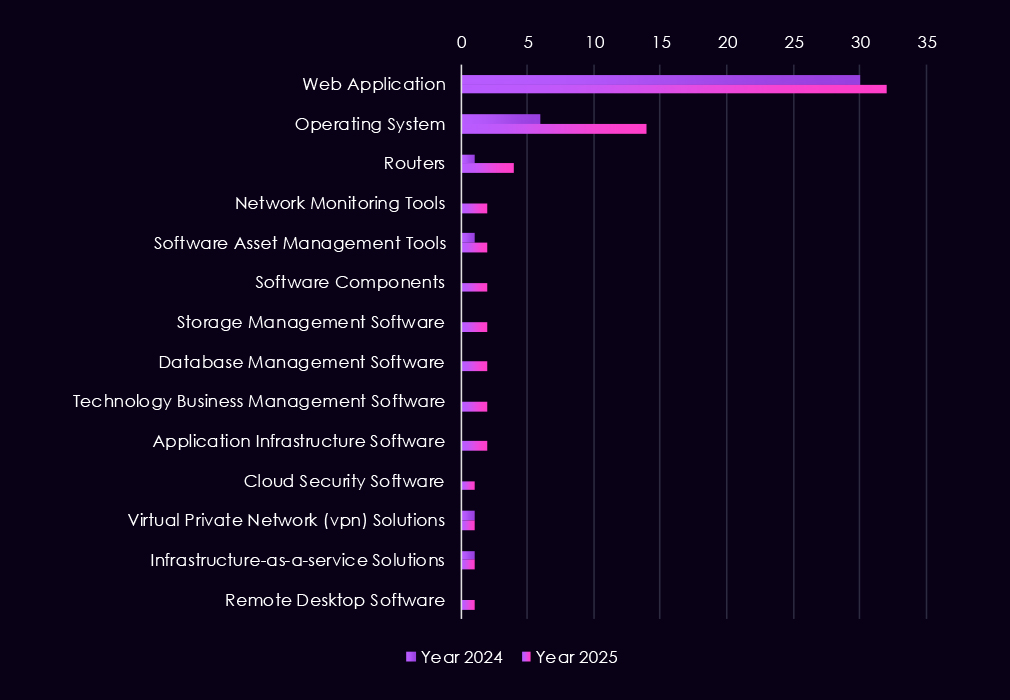
Attacks against the finance industry continue to focus on widely exposed and business-critical technologies, with activity increasing further in 2025. Web applications remain the most targeted systems, reflecting their role as the main entry point for credential theft, fraud, and initial compromise. Targeting of operating systems more than doubled, pointing to a greater focus on maintaining control after initial access, including persistence and lateral movement, rather than one-off exploits.
Compared to 2024, 2025 shows a broader range of technologies under attack. Threat activity expanded to include software management tools, application infrastructure, databases, network monitoring platforms, and cloud-related services, while VPNs and routers continue to see lower but steady attention.
Overall, this shift suggests attackers are increasingly abusing trusted internal systems, moving past perimeter defenses in line with both advanced cybercrime operations and nation-state campaigns seeking long-term, reliable access into financial environments.
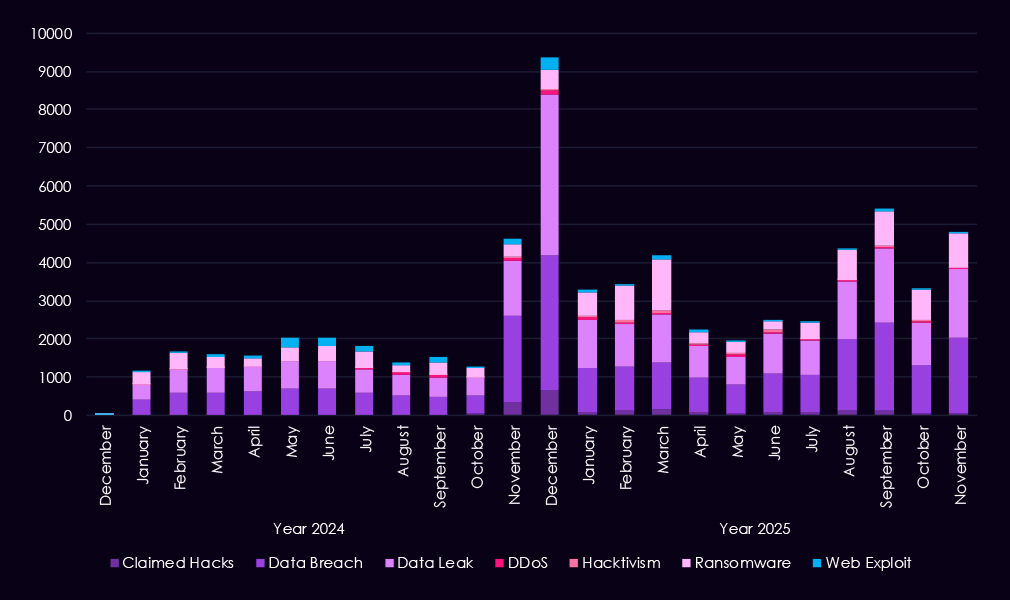
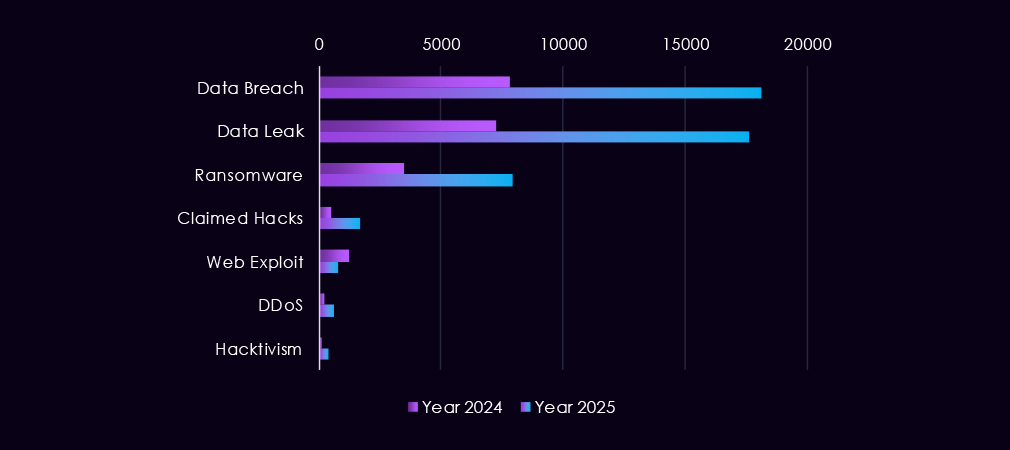
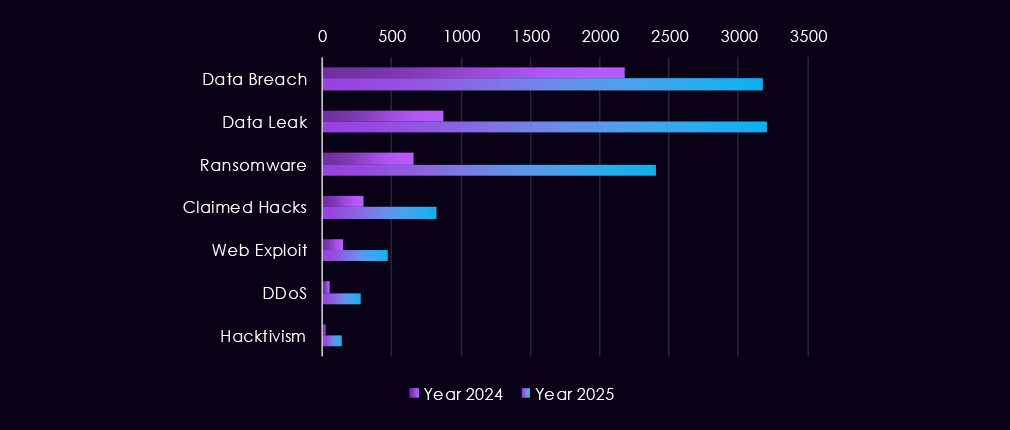
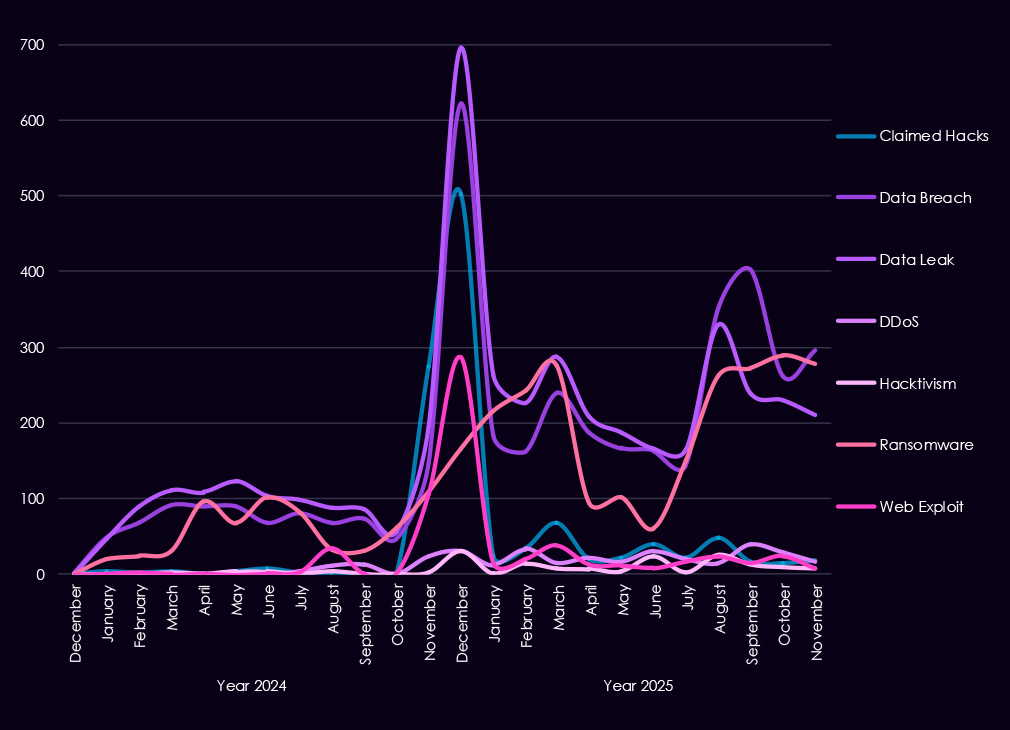
Over the past 23 months, CYFIRMA’s telemetry has identified 67,960 finance industry-linked mentions. This is from a total of 2.5 million posts across various underground and dark web channels and forums.
The chart above shows the total counts of industry-linked mentions for the finance industry and individual categories of context for the mentions.
The chart below shows Year-over-Year growth for each category in this industry.
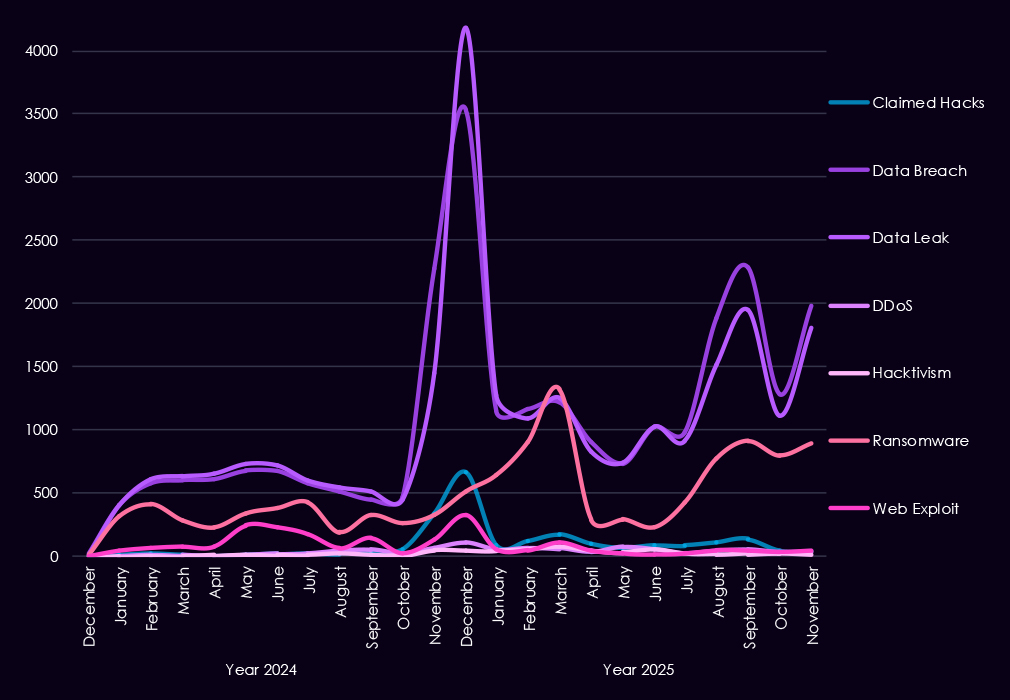
Underground and dark web discussions linked to the finance industry increased significantly from late 2024 into 2025, pointing to both higher attack activity and greater public exposure of incidents. Data breaches and data leaks dominate online chatter, with a sharp rise starting in Q4 2024 and remaining elevated through 2025, suggesting ongoing large-scale data exposures rather than isolated events. Ransomware-related discussions show the strongest growth, with repeated peaks in 2025 following a steady buildup in late 2024, reflecting sustained extortion pressure on financial organizations.
At the same time, mentions of claimed hacks and web exploits increase but remain secondary, indicating that many attacks likely move beyond initial compromise into data theft or extortion before becoming publicly discussed. DDoS and hacktivism activity remains relatively low and uneven, appearing in short-lived spikes rather than consistent campaigns. Overall, the 2025 trend suggests a shift away from sporadic criminal claims toward persistent, high-volume data exposure and extortion-focused narratives, consistent with more organized and mature threat activity targeting the financial sector.
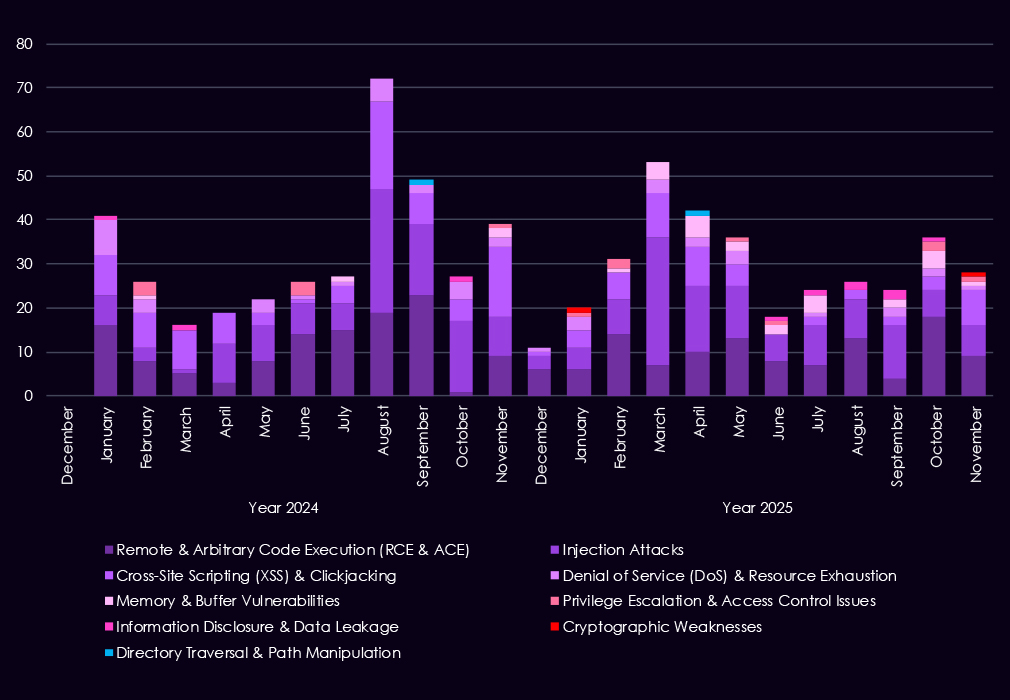
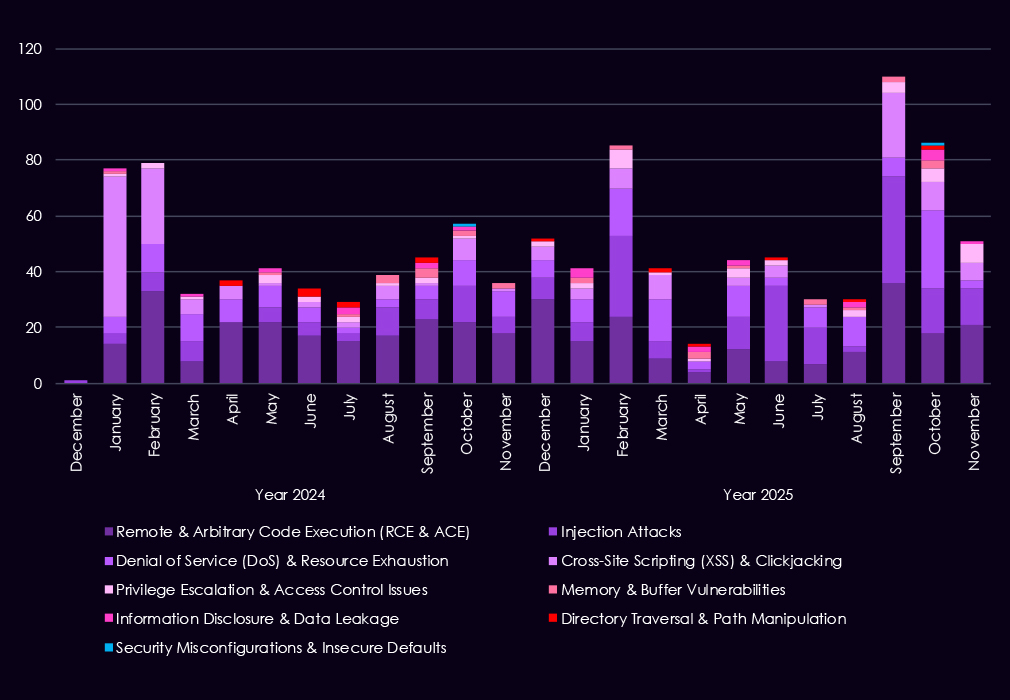
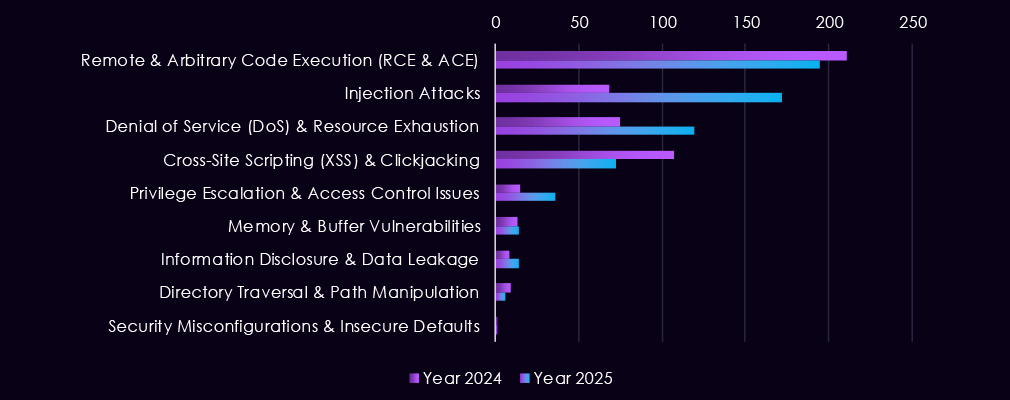
Over the past 23 months, CYFIRMA’s telemetry has identified 713 finance industry-linked mentions. This is from over 90k CVEs reported and updated in the same time period.
The chart above shows total counts of industry-linked mentions for finance technology and individual categories of reported vulnerabilities.
The chart below shows Year-over-Year growth for each category in this industry.
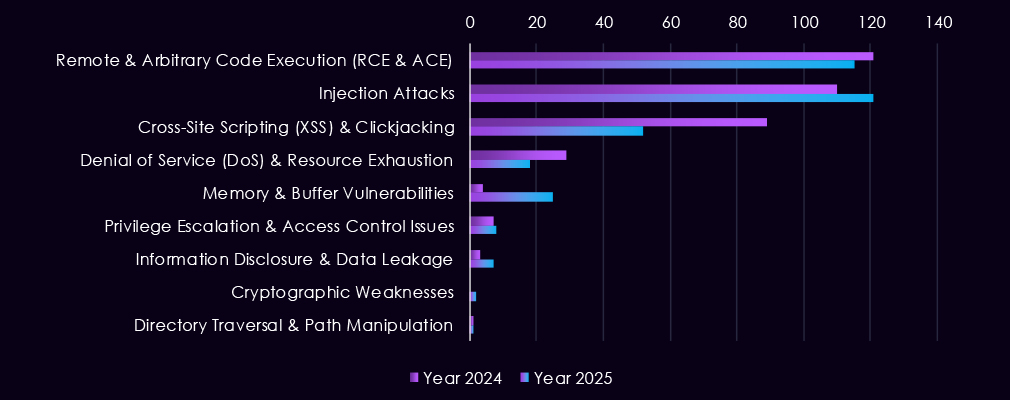
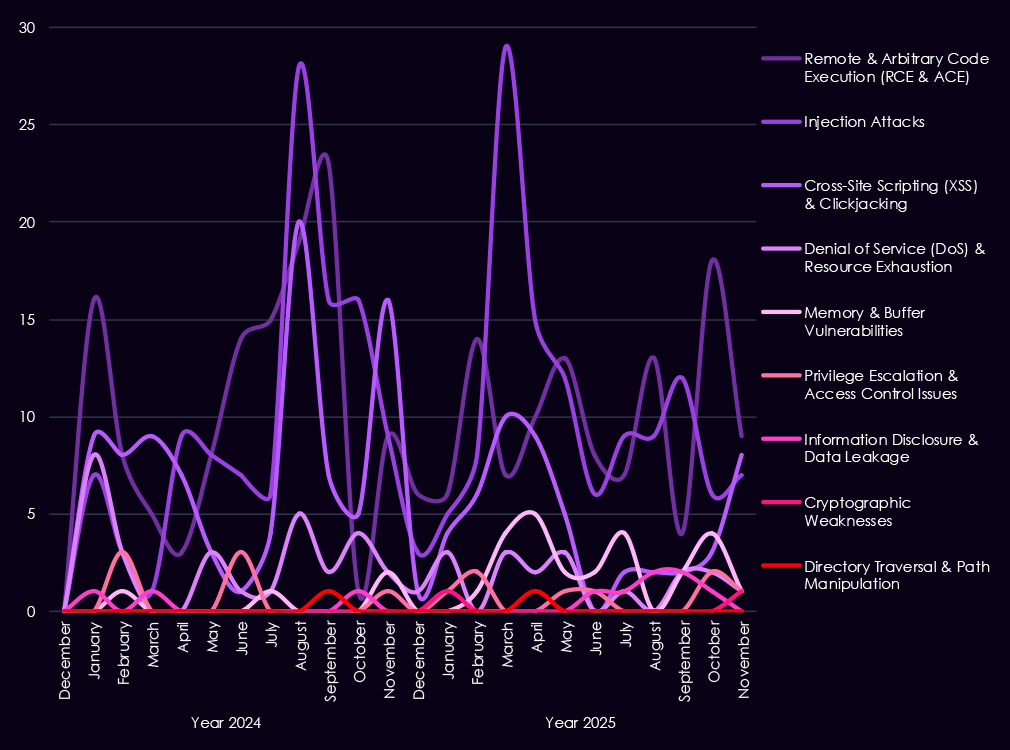
Reported vulnerabilities affecting the financial services sector show a clearer focus in 2025 on flaws that are easier to exploit and have a higher impact. Remote and arbitrary code execution (RCE/ACE) vulnerabilities remain the most common, but in 2025, they appear more consistently month to month, pointing to sustained attention on weaknesses that allow direct system takeover.
Injection flaws continue to appear in spikes, especially in early to mid-2025, showing that web-facing financial applications remain exposed despite long-standing awareness of these risks. In contrast, XSS and clickjacking decline in importance, suggesting attackers are placing less value on lower-impact client-side issues. While less frequent, memory corruption, privilege escalation, and access control weaknesses show up more regularly in 2025, indicating a growing focus on post-compromise activity and vulnerability chaining.
Overall, the 2025 trend reflects fewer low-impact findings and greater emphasis on vulnerabilities that support control, persistence, and follow-on exploitation in financial environments.
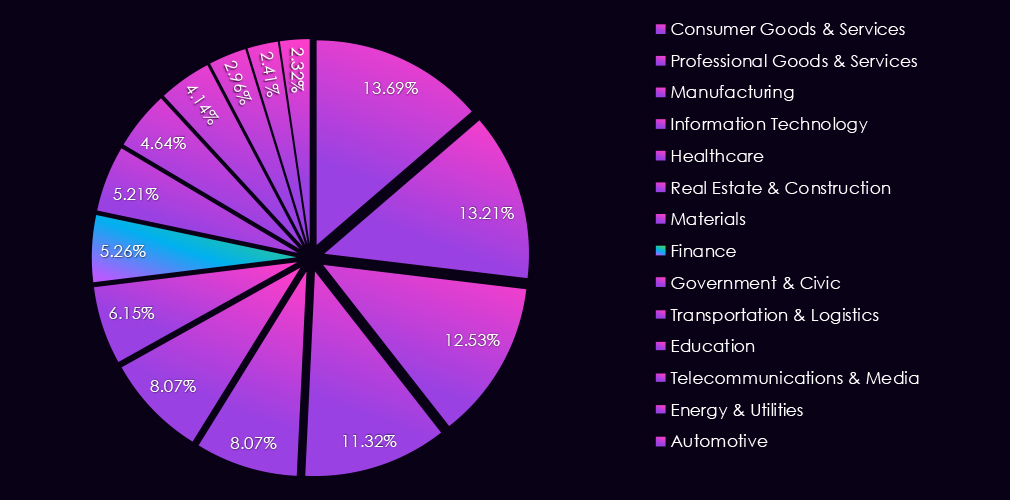
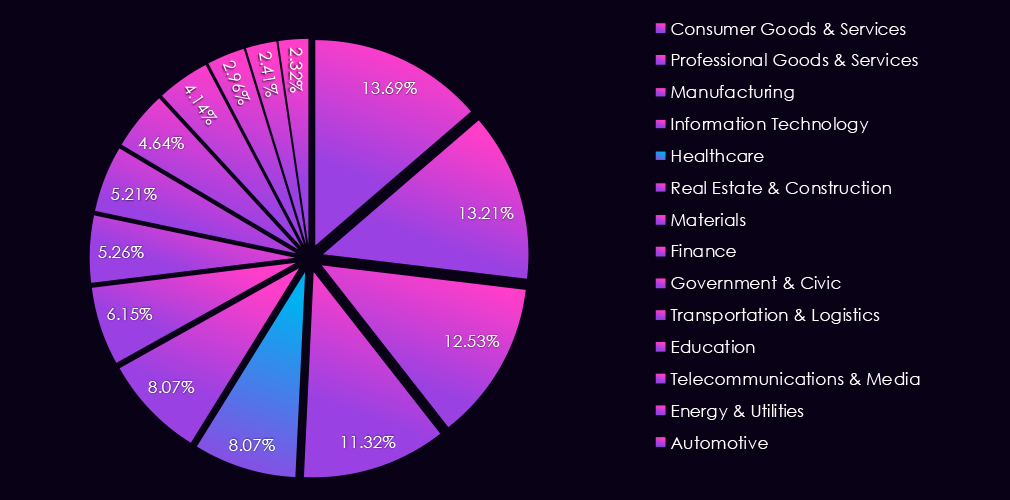
In the past 12 months, CYFIRMA has identified 364 verified finance industry ransomware victims. 43% increase from 254 victims in the previous year, which recorded a major dip from 423 victims during 2023.
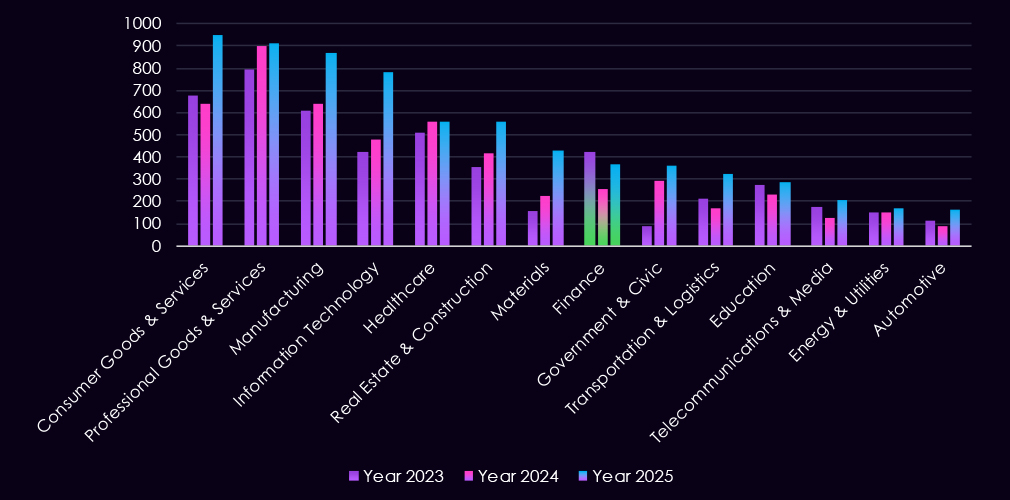
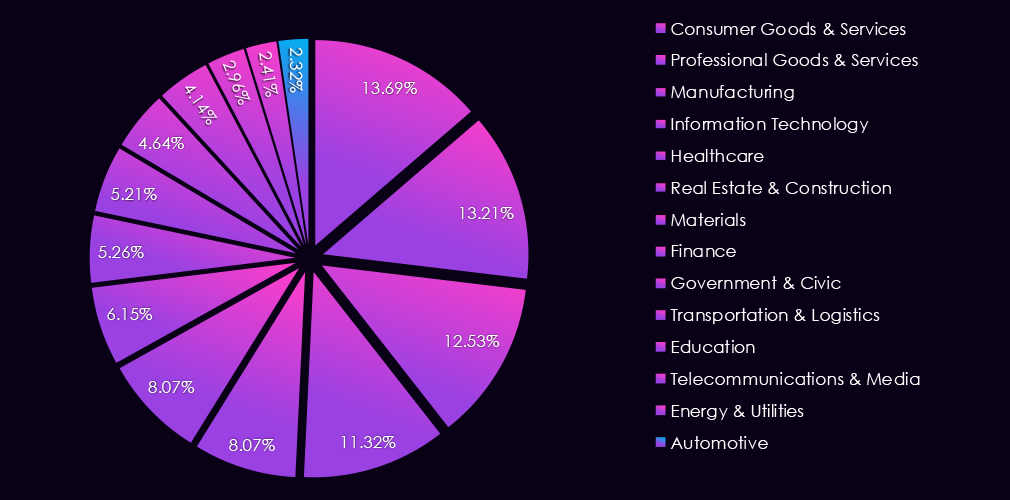
The finance industry accounts for 5.26% of the overall total of 7,099 ransomware victims during the same period. That is an increase from 4.87% in the previous year, but still significantly lower than 8.45% during 2023.
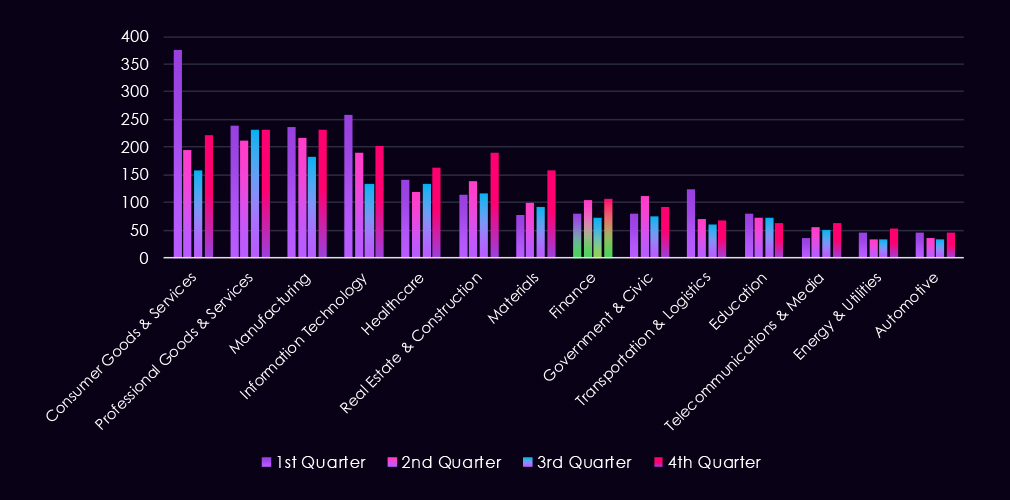
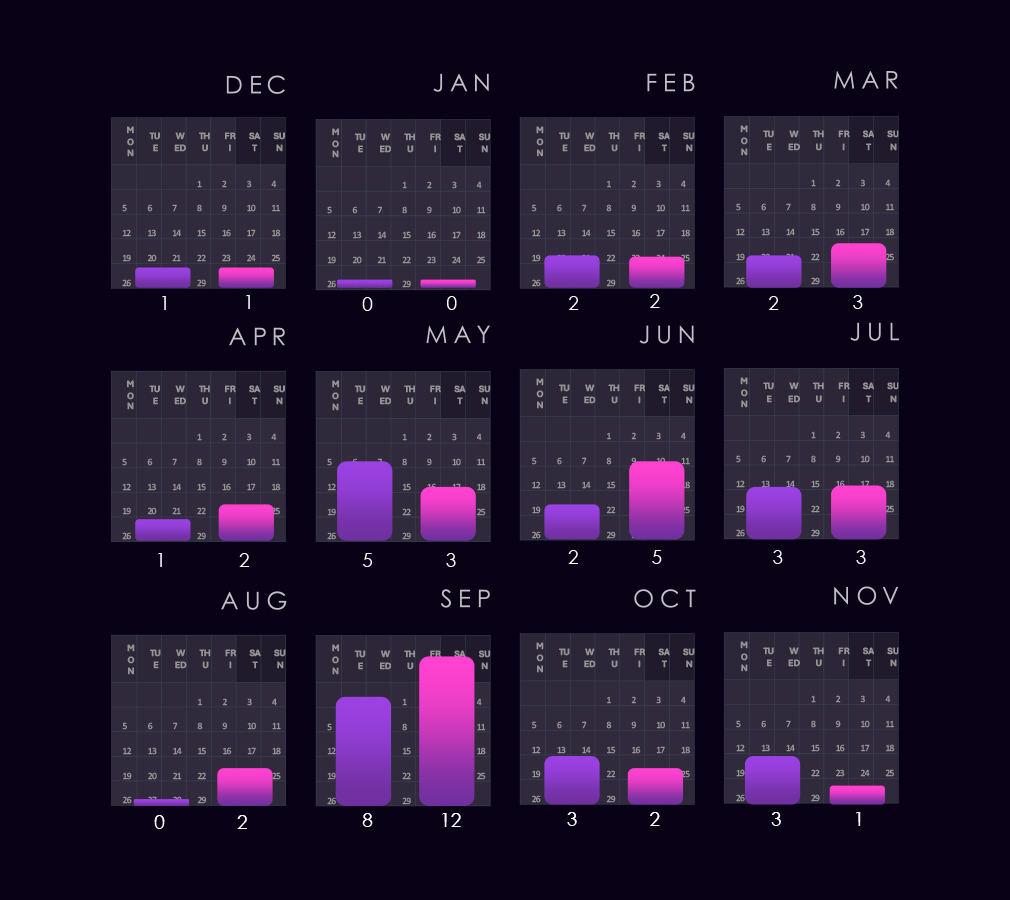
The bar chart above is focused only on 2025, and the victim counts per quarter are shown clearly and easily to see the trends. The finance industry recorded alternating activity between quarters.
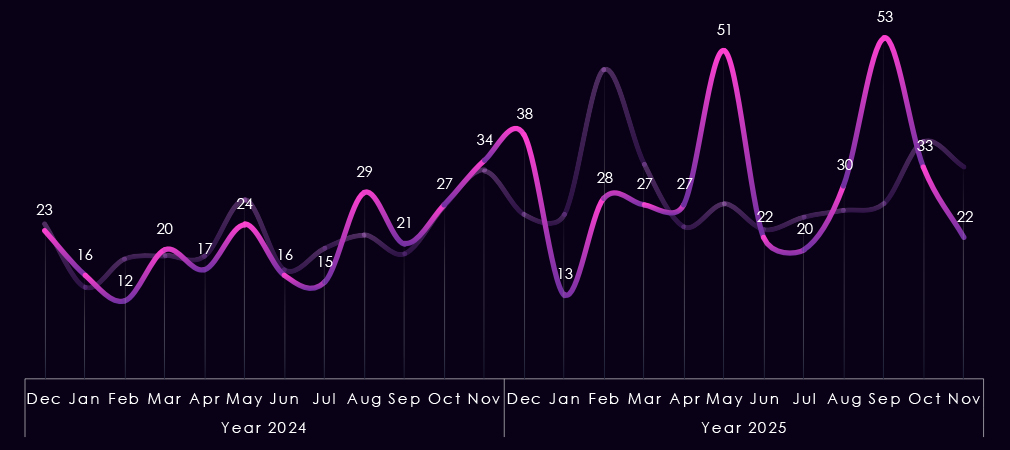
Monthly activity charted over scaled-down global all industries victims counts, showing that in 2024, the Finance industry followed the global trendline very closely.
In 2025, though, we see major divergences in January and February, where Finance victims count went low compared to the global spike; however, in May and September, we saw large spikes of Finance victims where global activity was flat.
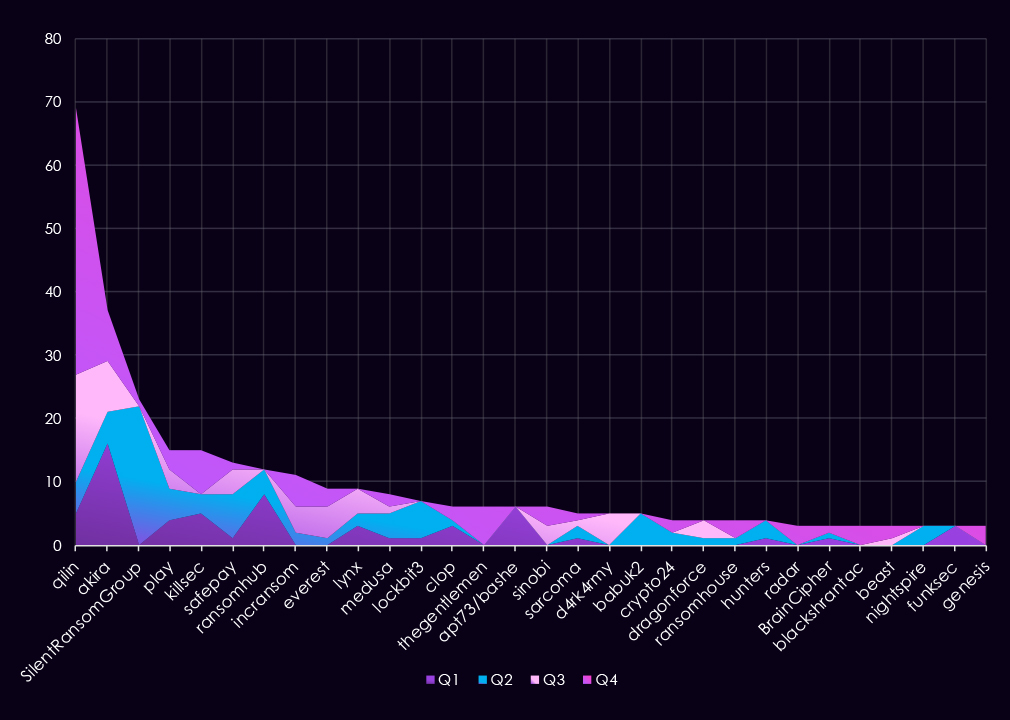
In total, 75 out of 124 gangs active in 2025 recorded victims in the finance industry, with 60% participation.
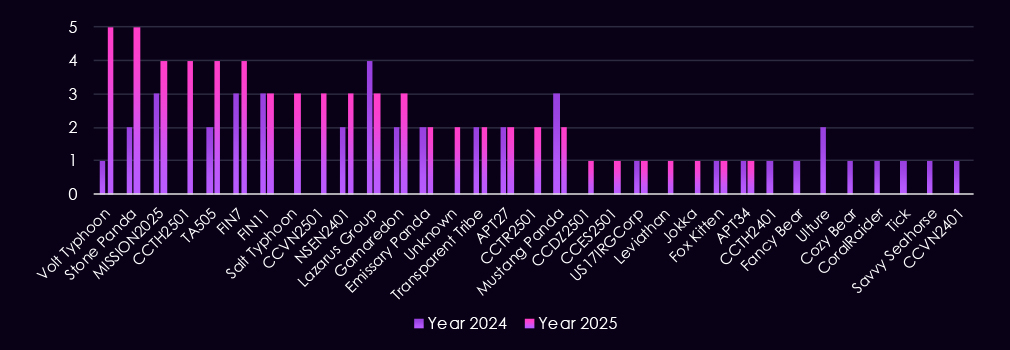
A breakdown of the top 30 gangs’ quarterly activity provides insights into which gangs were the most active each quarter.
Q1 activity was relatively distributed, with Akira leading the quarter at 16 victims, followed by RansomHub and APT73/Bashe. No single group dominated early in the year, suggesting a mix of opportunistic targeting rather than sustained focus by any one actor.
In Q2, activity increased unevenly. SilentRansomGroup stood out with a sudden spike in victim numbers, while several other groups recorded moderate but short-lived activity. This surge was not sustained in later quarters, indicating a limited or time-bound campaign.
Q3 marked a change in momentum. Qilin became the most active group in the finance sector, significantly increasing its victim count compared to earlier quarters. Overall activity narrowed to fewer groups, but with higher volumes among leading actors.
By Q4, activity was highly concentrated. Qilin dominated the quarter with 42 victims, accounting for a large share of observed incidents. While several other gangs, including KillSec, IncRansom, and TheGentlemen, increased activity toward year-end, none approached Qilin’s scale.
Overall, the data shows a shift from broadly distributed activity in the first half of the year to a more concentrated threat landscape by Q4, driven primarily by a single dominant ransomware actor.
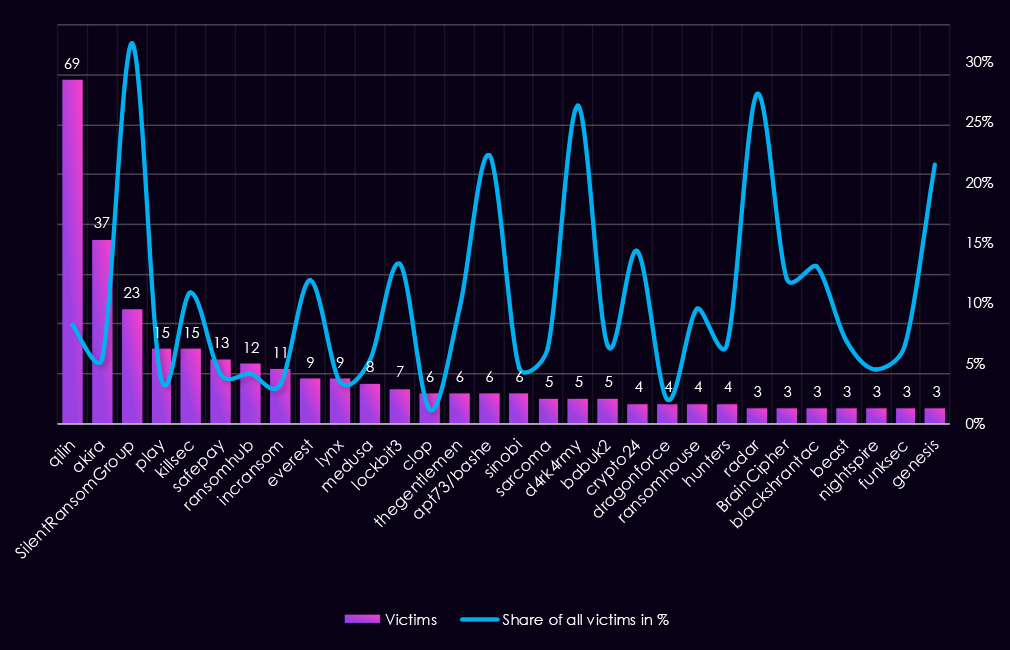
Here we have another view of the top 30 gangs during 2025 for this industry, showing total counts for the year and the respective share of all their victims. This allows us to differentiate opportunistic and focused industry targeting.
Qilin recorded the highest number of finance victims (69), but finance represents only 8.2% of its total victims, indicating scale rather than focused targeting. Akira shows a similar pattern, with 37 victims and a 5.5% share, consistent with broad, multi-sector targeting.
Several gangs show a relatively high finance concentration (>10%). SilentRansomGroup stands out, with 31.5% of its victims in finance, indicating a strong sector focus. KillSec (10.9%), Everest (11.8%), LockBit3 (13.2%), APT73/Bashe (22.2%), and D4rk4rmy (26.3%) also show disproportionate exposure to the sector.
Some high percentage values are driven by low overall victim counts. Radar (27.3%), Genesis (21.4%), Crypto24 (14.3%), and BlackShrantac (13.0%) each recorded only three to four finance victims, making these shares statistically skewed and less indicative of sustained targeting.
Most gangs fall into a low focus range (<5%), including Play, SafePay, RansomHub, IncRansom, Lynx, Sinobi, NightSpire, and DragonForce.
Overall, high victim volume does not consistently align with high sector specialization, and only a few gangs show meaningful focus on the finance industry.
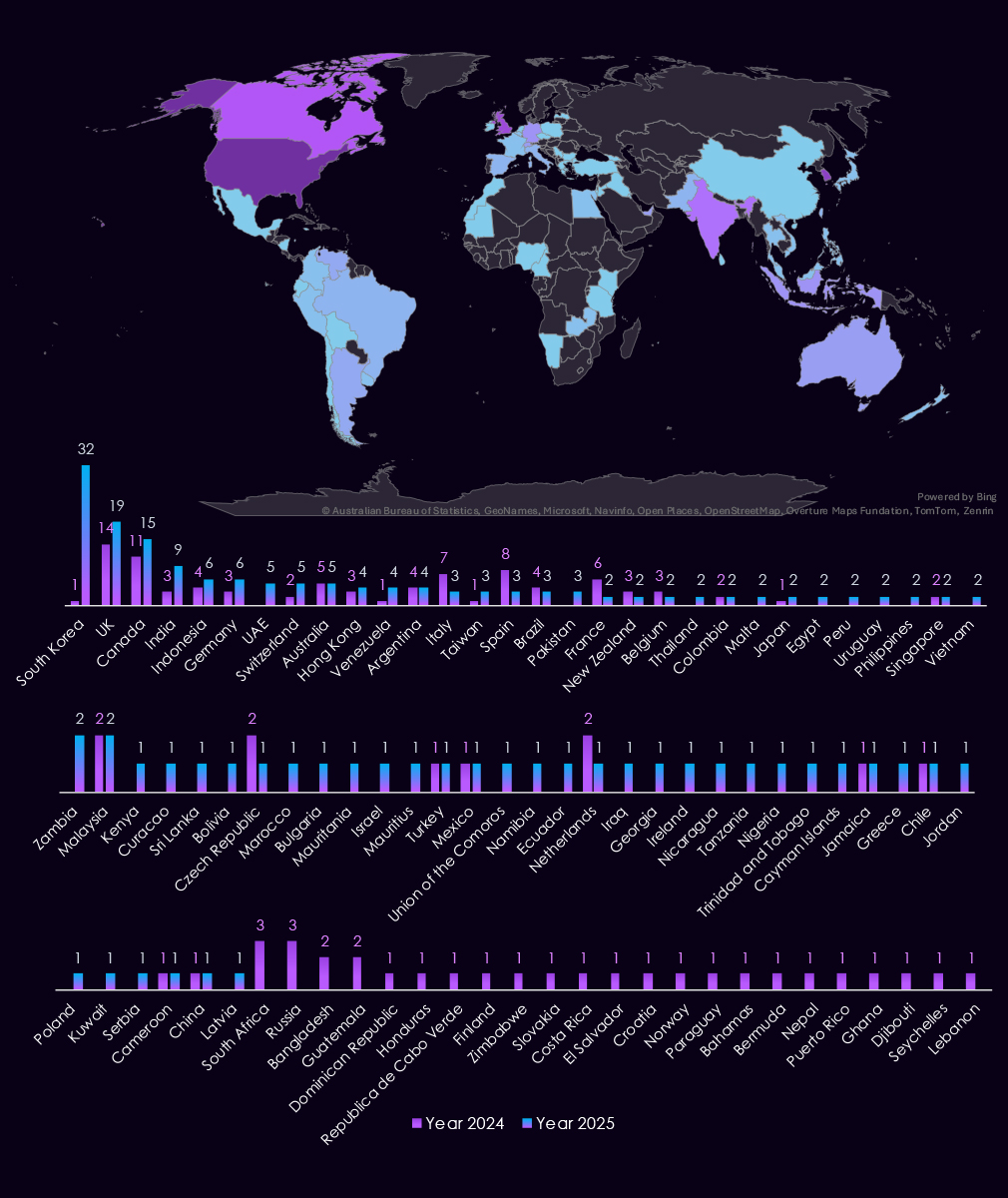
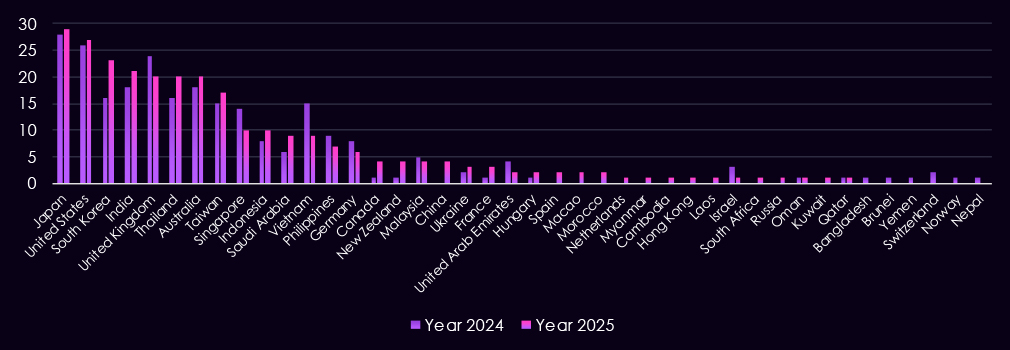
With 170 victims, the USA accounts for 47% of finance industry victims in 2025. The US also recorded a major increase from 125 victims in 2024.
South Korea, in second, is the biggest outlier, jumping from 1 to 32 victims as local asset management firms were hit by Qilin ransomware in late 2025.
A total of 67 countries recorded victims in 2025, an increase from 54 in 2024.
Year-over-Year Risk Elevation : High

In 2025, the finance industry experienced a clear year-over-year escalation in external threat activity, with victims observed in 84% of tracked APT campaigns, up from 70% in 2024. Threat actor behaviour shifted toward state-aligned access and persistence operations, particularly from China-linked groups, while financially motivated actors remained consistently active. Geographic targeting remained concentrated in Asia-Pacific and Western economies but expanded further into Southeast Asia, the Middle East, and Europe, reflecting a broader and more opportunistic reach compared to 2024.
Attack activity increasingly moved beyond perimeter exploitation, with web applications still the primary entry point but operating system targeting more than doubling year over year, signalling greater emphasis on persistence and lateral movement. The technology attack surface widened to include internal management tools, databases, cloud services, and monitoring platforms, indicating growing abuse of trusted systems.
Underground and dark web chatter rose sharply from late 2024 into 2025, driven primarily by ransomware, data breaches, and data leaks, with ransomware showing the strongest growth and sustained visibility throughout the year. Vulnerability focus similarly shifted toward high-impact, easily exploitable flaws, particularly remote and arbitrary code execution, with increased attention to privilege escalation and post-compromise chaining.
Ransomware victims in the finance sector increased 43% year over year, reversing the 2024 decline. Activity shifted from broadly distributed targeting in early 2025 to highly concentrated attacks by fewer actors in the second half of the year. Geographic exposure widened, with the United States remaining the primary target and notable year-over-year outliers emerging in Asia. Overall, 2025 reflects a more persistent, globally distributed, and maturity-driven threat environment for the finance industry.
Over the past 12 months, energy & utilities organizations recorded victims across 6 of the 43 Advanced Persistent Threat (APT) campaigns observed – an incidence rate of 14%. That is lower than 8 campaigns in the previous year.
These victims spanned multiple segments within the energy & utilities industry, as shown below:
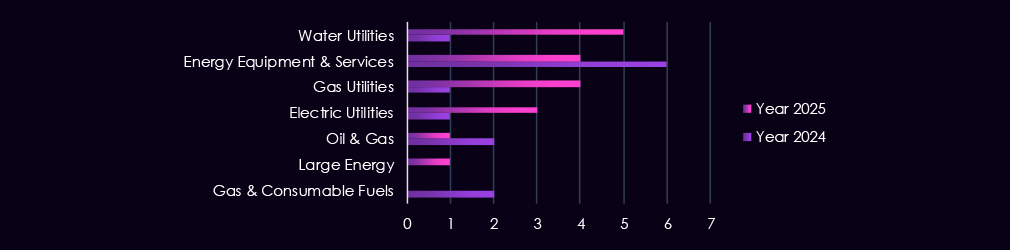
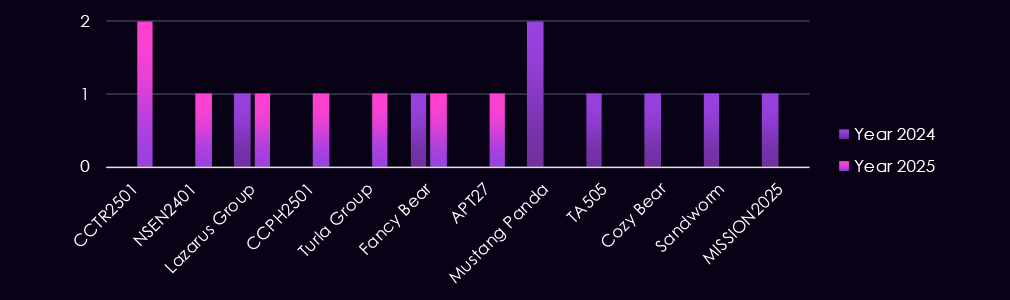
The energy & utilities sector is targeted by a mix of nation-state and cybercrime actors, with activity primarily reflecting espionage, strategic access, and potential disruption objectives. Observed campaigns involve established state-linked groups such as Turla Group, Fancy Bear, Cozy Bear, Sandworm, Mustang Panda, MISSION2025, and APT27, underscoring continued state interest in critical infrastructure.
At the same time, Lazarus Group remains present, indicating financial or dual-use motivations within the sector. The appearance of newly tracked clusters such as CCTR2501 and CCPH2501, alongside activity attributed to TA505, suggests that cybercrime actors also continue to probe energy and utilities environments, either opportunistically or in support of broader access and monetization efforts.
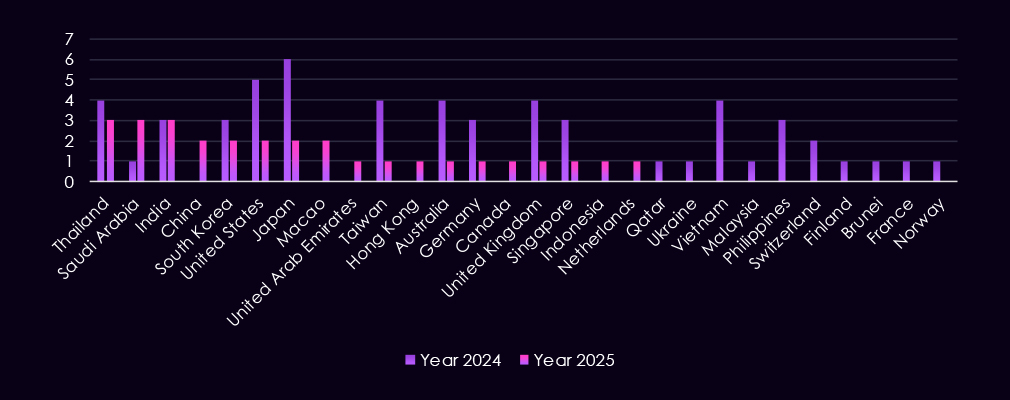
The geographic targeting is concentrated across Asia-Pacific, North America, Europe, and the Middle East. In 2025, the most frequently affected countries include Saudi Arabia, Thailand, and India, followed by repeated targeting of South Korea, the United States, Japan, China, and Macao.
Compared to 2024, 2025 shows slightly broader dispersion across additional jurisdictions, including single-observation cases in Europe, Southeast Asia, and the Middle East (for example, Canada, UAE, Netherlands, Germany, and Indonesia).
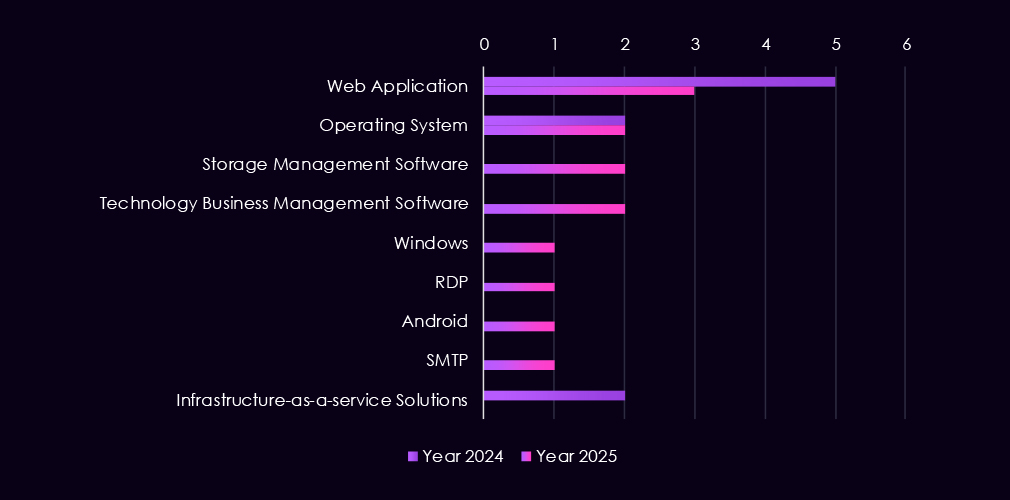
Attacks observed in the energy & utilities sector focus on a small but telling set of technologies, reflecting both opportunistic access attempts and targeted intrusion activity. In 2025, web applications remain the most frequently targeted systems, reinforcing their role as internet-facing and exposed entry points. Operating systems and Windows-specific components also appear, pointing to efforts to establish control and persistence after initial access.
Notably, 2025 shows a broader technology variety despite lower overall volume. Targeting expands to include storage management platforms, technology business management (TBM) software, SMTP services, RDP, and mobile operating systems (Android). This suggests attackers are probing supporting and management layers, not just primary IT systems, potentially to move laterally or access sensitive operational data.
Overall, the pattern indicates targeting of both external-facing services and internal management tooling, consistent with reconnaissance and early-stage access activity against energy % utilities environments.
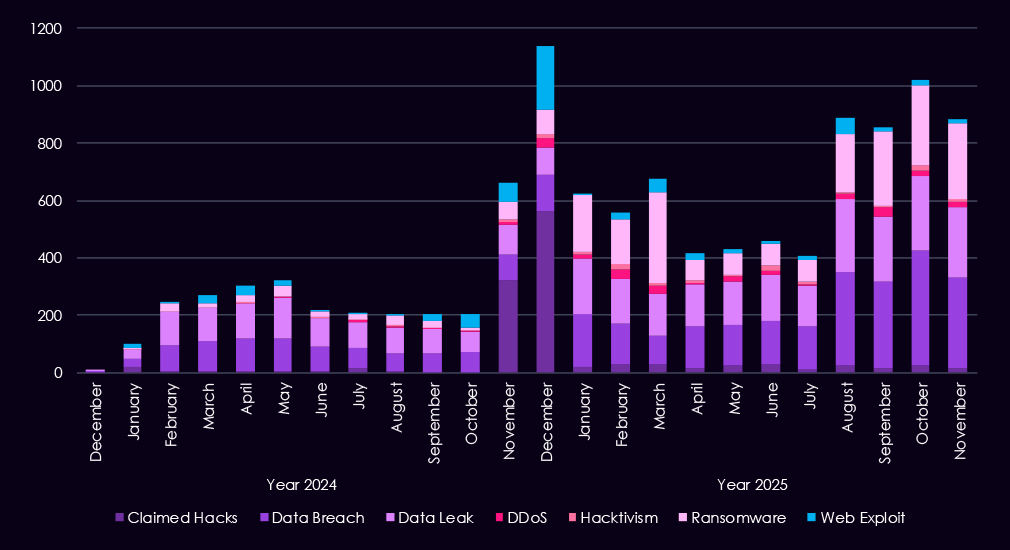
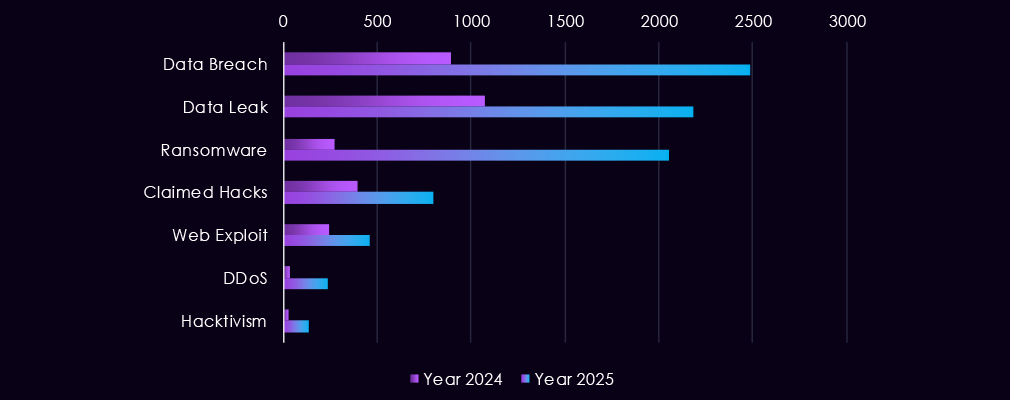
Over the past 23 months, CYFIRMA’s telemetry has identified 11,295 energy & utilities industry-linked mentions. This is from a total of 2.5 million posts across various underground and dark web channels and forums.
The chart above shows total counts of industry-linked mentions for the energy & utilities industry and individual categories of context for the mentions.
The chart below shows Year-over-Year growth for each category in this industry.
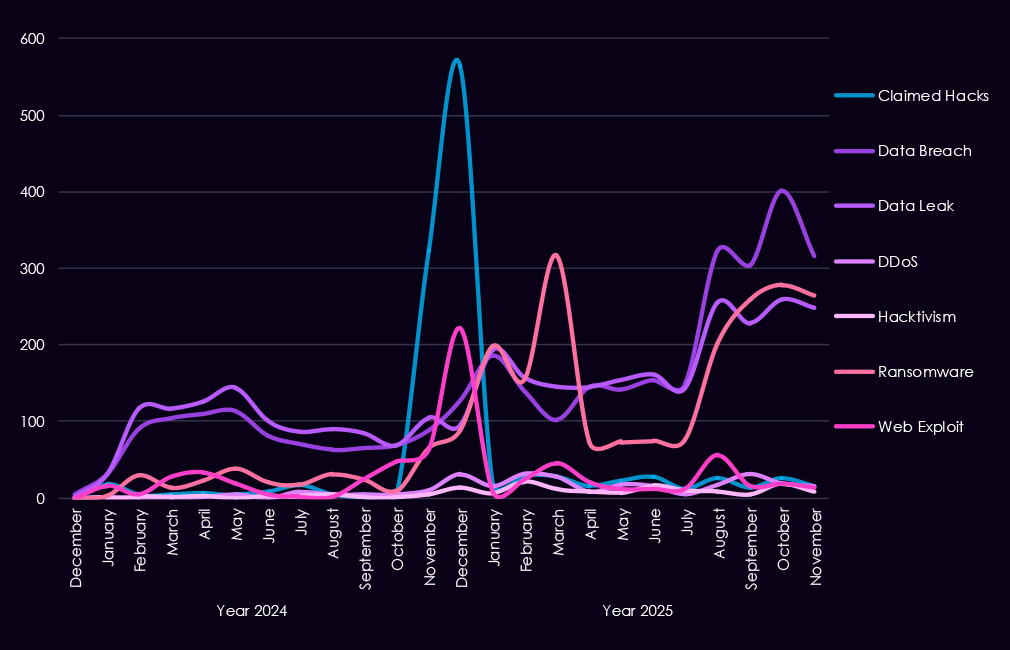
Underground and dark web chatter related to the energy & utilities sector increased steadily from late 2024 into 2025, indicating rising threat activity and greater visibility of incidents. Data breach and data leak discussions dominate, with volumes climbing through early 2025 and remaining consistently high, pointing to ongoing exposure of sensitive operational and corporate data rather than isolated disclosures. Ransomware chatter shows a clear escalation, with sharp spikes in 2025 following more moderate activity in 2024, suggesting increased extortion pressure against energy & utilities organizations.
Mentions of claimed hacks and web exploits also rise, particularly toward the end of 2024 and into 2025, indicating growing interest among actors to publicize intrusions or weaponized access. DDoS and hacktivism remain lower in volume and uneven, appearing in short bursts rather than sustained campaigns.
Overall, the 2025 pattern reflects a shift toward more frequent, higher-volume discussions of data exposure and ransomware, consistent with increasingly organized and monetization-driven activity targeted by even lower-skill threat actors driving most of the chatter.
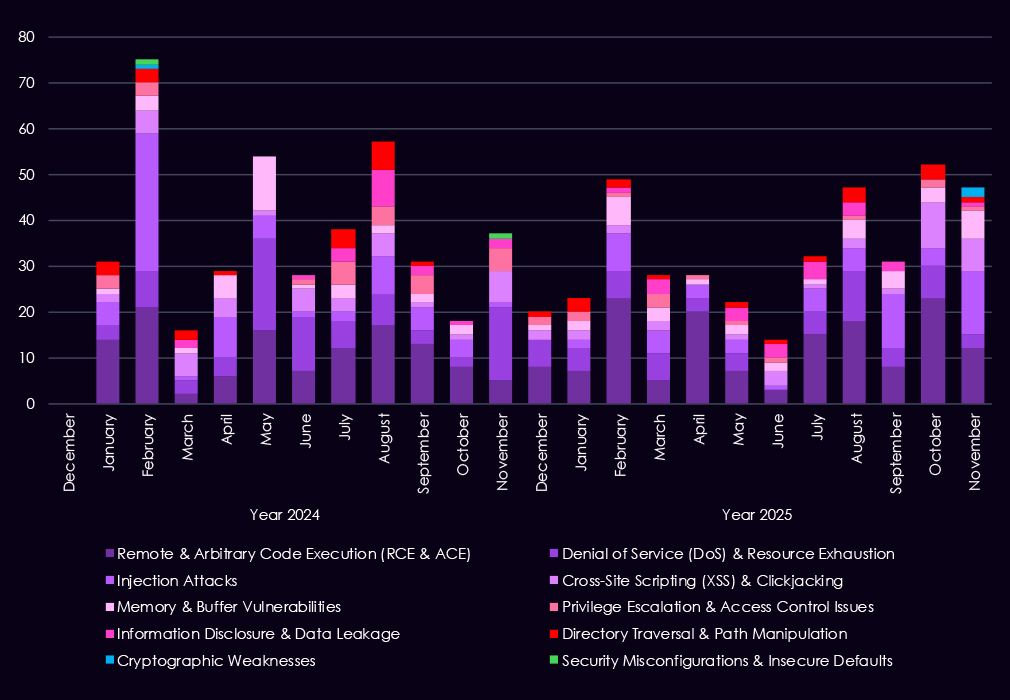
Over the past 23 months, CYFIRMA’s telemetry has identified 807 energy & utilities industry-linked mentions. This is from over 90k CVEs reported and updated in the same time period.
The chart above shows the total counts of industry-linked mentions for energy & utilities technology and individual categories of reported vulnerabilities.The chart below shows Year-over-Year growth for each category in this industry.
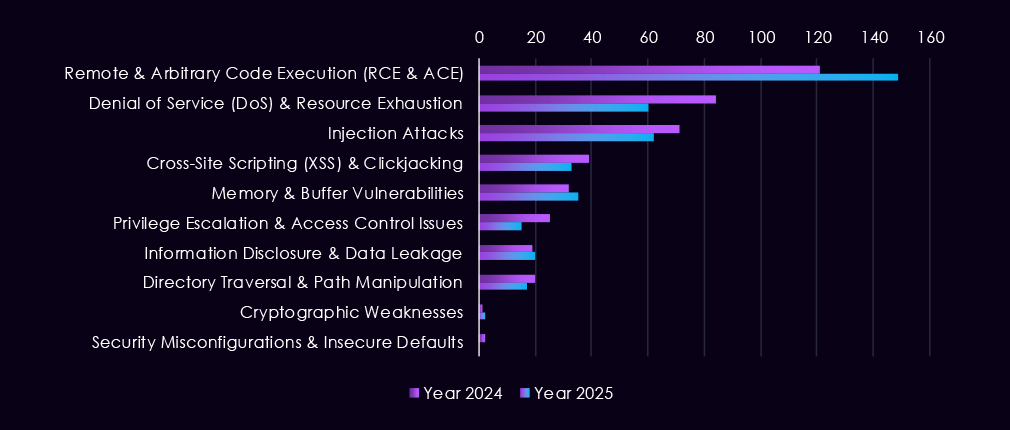
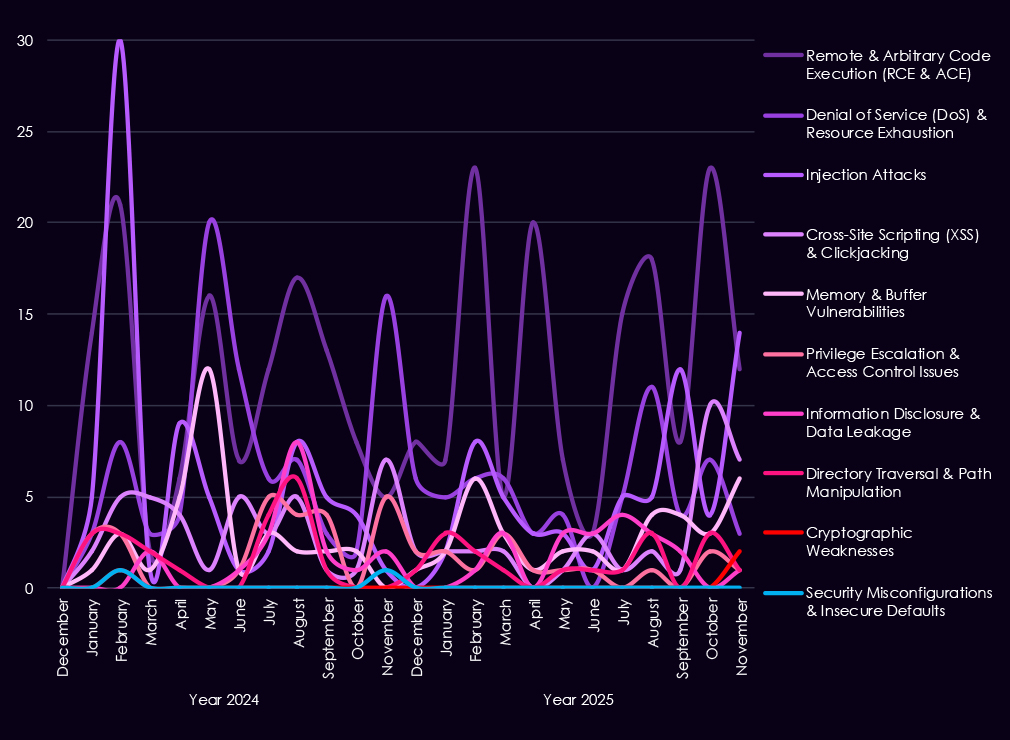
Reported CVEs affecting the energy and utilities sector show a continued emphasis on high-impact vulnerability classes, with 2025 maintaining steady discovery across multiple categories. Remote and arbitrary code execution (RCE/ACE) vulnerabilities remain the most prominent, appearing consistently throughout 2025 and illustrating their importance as direct paths to system compromise.
Denial-of-service and injection flaws remain regularly observed, reflecting both the exposure of internet-facing services and the operational sensitivity of energy systems to availability issues. While less frequent, memory and buffer vulnerabilities, privilege escalation, and access control weaknesses appear steadily across 2025, indicating attention to post-compromise activity and vulnerability chaining rather than standalone exploitation. Lower but persistent sightings of information disclosure, directory traversal, and path manipulation issues further highlight weaknesses in application and system design.
Overall, the 2025 vulnerability profile points to sustained risk from exploit-ready flaws that enable control, disruption, or follow-on access, rather than a dominance of low-impact configuration issues.
In the past 12 months, CYFIRMA has identified 167 verified energy & utilities industry ransomware victims. 12% increase from 149 victims in the previous year, which recorded sustained levels from 152 victims during 2023.
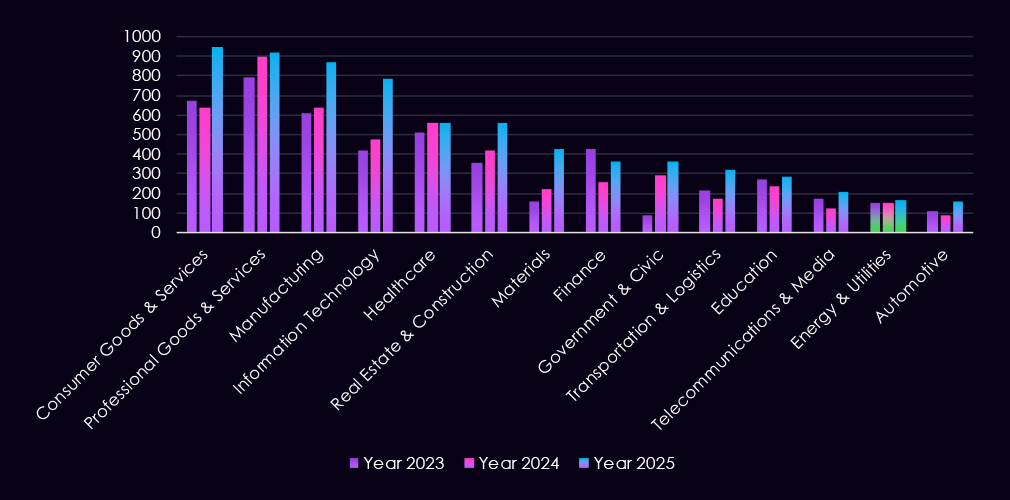
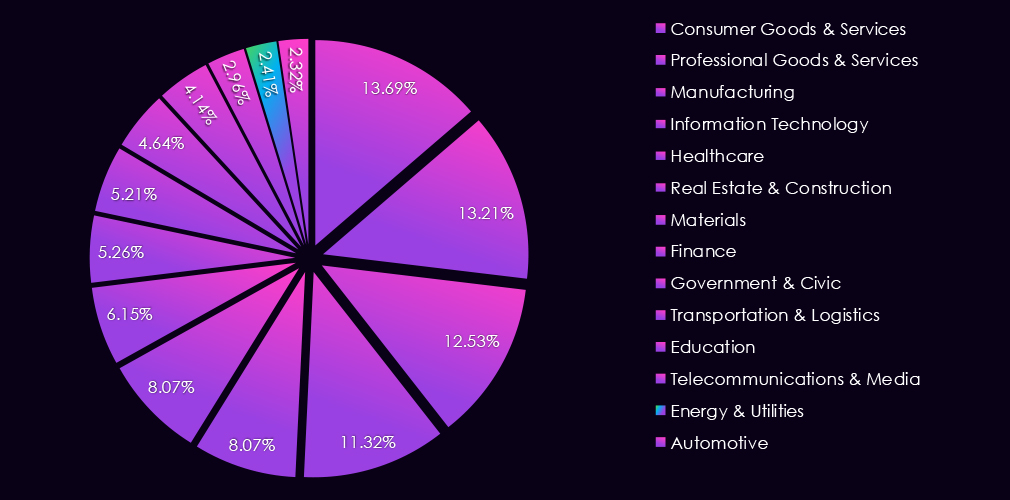
The energy & utilities industry accounts for 2.41% of the overall total of 7,099 ransomware victims during the same period. That is down from 2.85% in the previous year, lower still than 3.04% during 2023, showing a gradual decline of interest in this industry.
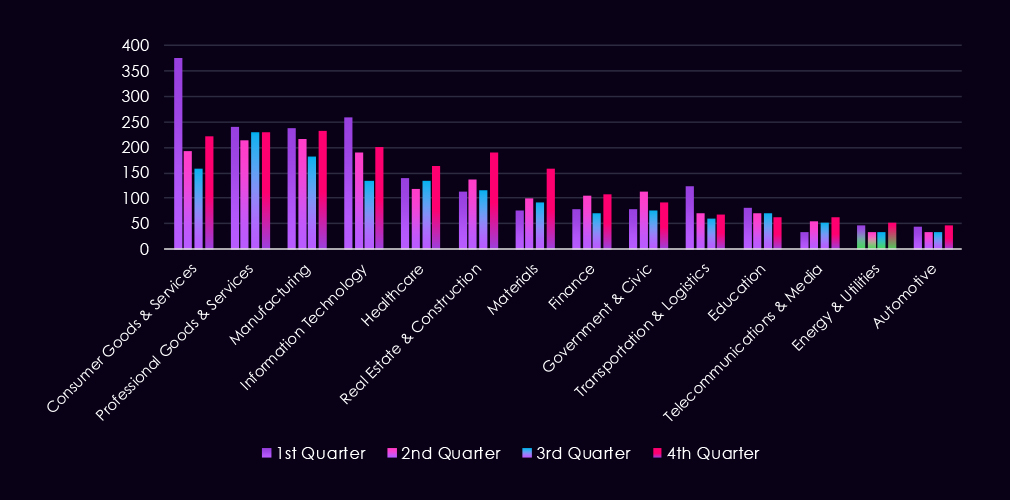
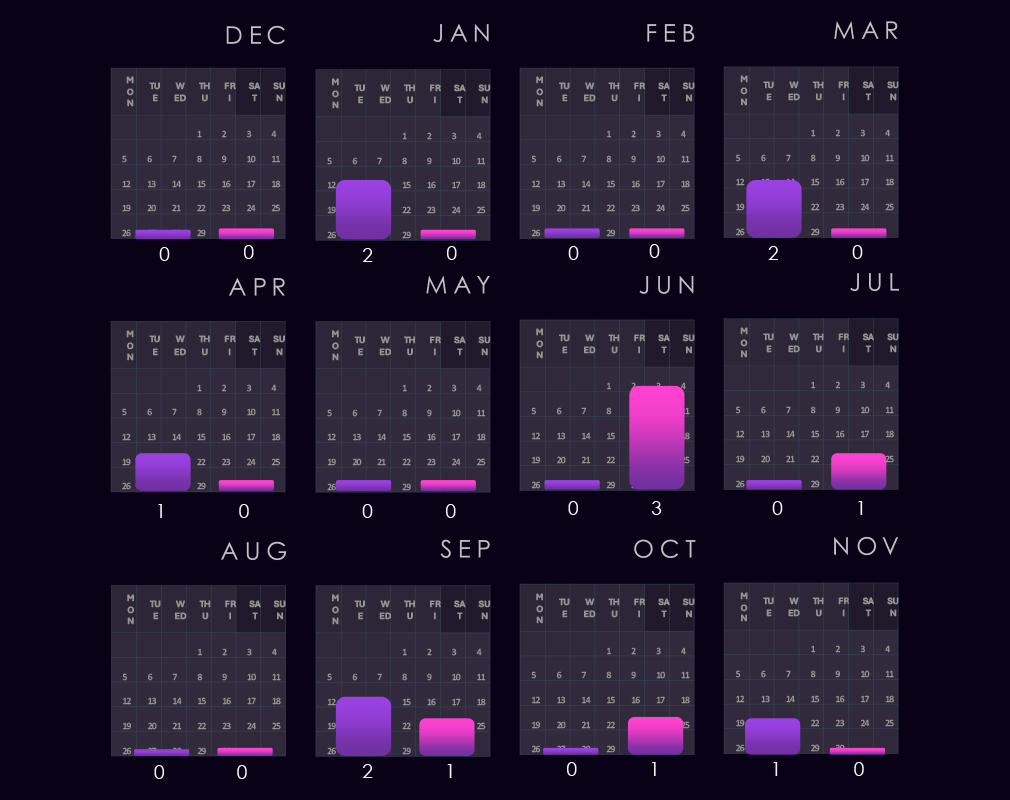
The bar chart above is focused only on 2025, and the victim counts per quarter are shown clearly and easily to see the trends. Energy & utilities have a higher victim count in Q1 and Q4, with a minor dip in between.
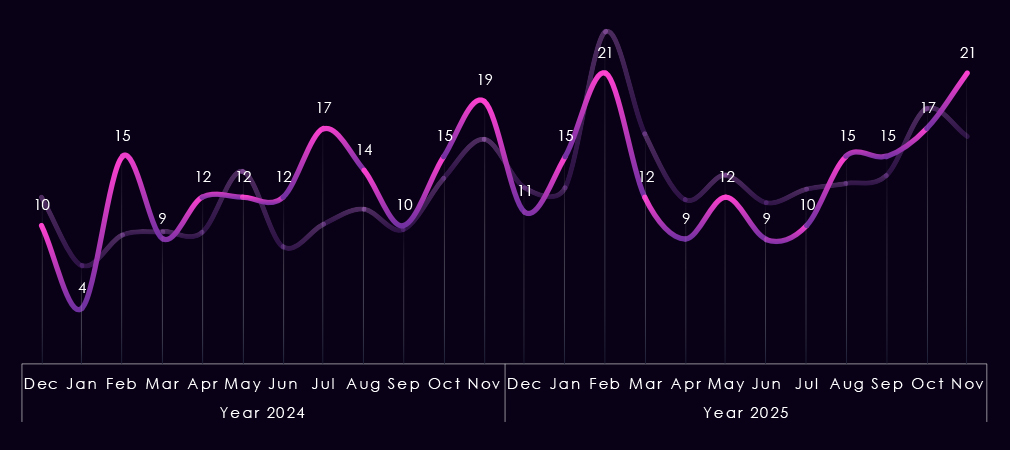
Monthly activity charted over scaled-down global all industries victims counts shows that in 2024; the energy & utilities industry followed the global trendline very closely.
A major spike occurred in February across industries, and gradual growth from July until December also followed the global trend. November 2025 saw divergence, where the trendline for energy & utilities kept growing while the global line had finally moved down.
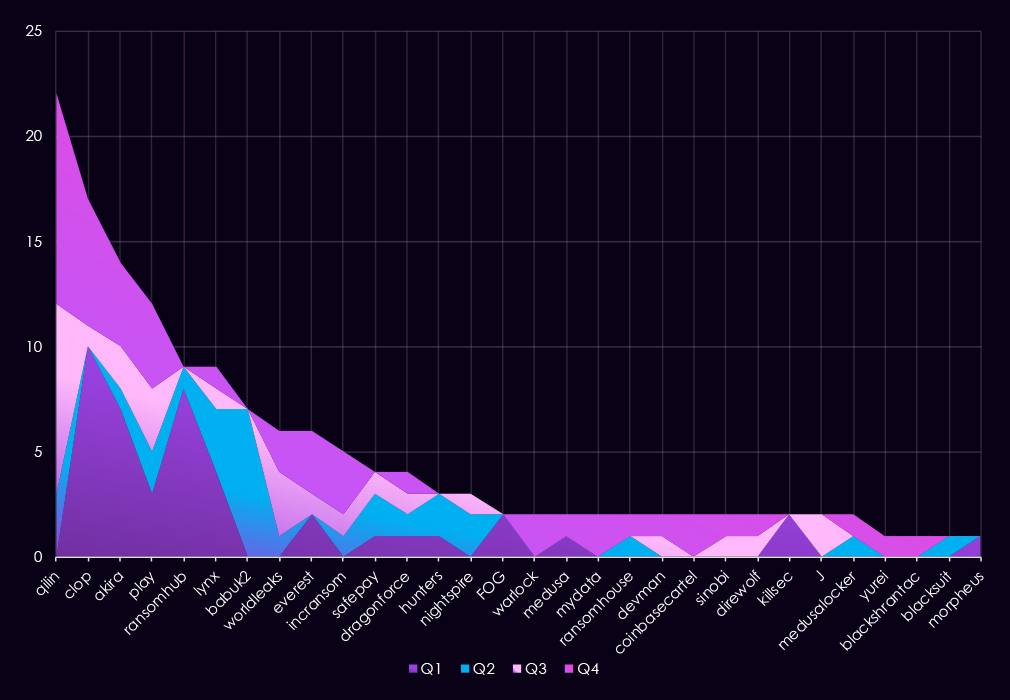
In total, 48 out of 124 gangs active in 2025 recorded victims in the energy & utilities industry, with 39% participation.
A breakdown of the top 30 gangs’ quarterly activity provides insights into which gangs were the most active each quarter.
Q1 activity was led by Clop (10), followed by RansomHub (8) and Akira (7). Several other gangs showed limited, single-digit activity, but overall volume was concentrated among a small number of actors early in the year.
In Q2, activity became more fragmented. Babuk2 (7) emerged as the most active group, while Qilin (3), Lynx (3), and Play (2) maintained a lower but consistent presence. No gang sustained the high Q1 volumes, indicating a temporary easing in pressure rather than a coordinated surge.
Q3 marked a clear increase in activity from Qilin (9), making it the most active gang for the quarter. Several other groups, including Play (3) and WorldLeaks (3), contributed to a broader but still moderate threat landscape.
By Q4, activity remained elevated but dispersed. Qilin (10) continued to lead, while Clop (6), Akira (4), and Play (4) showed renewed or sustained engagement. A long tail of low-volume gangs appeared with one to two victims each, suggesting opportunistic targeting rather than concentrated campaigns.
Concerning is the middle and right end of the chart, where we can see a number of smaller groups highly active in Q4, responsible for the upward trend, and suggesting an elevation into 2026.
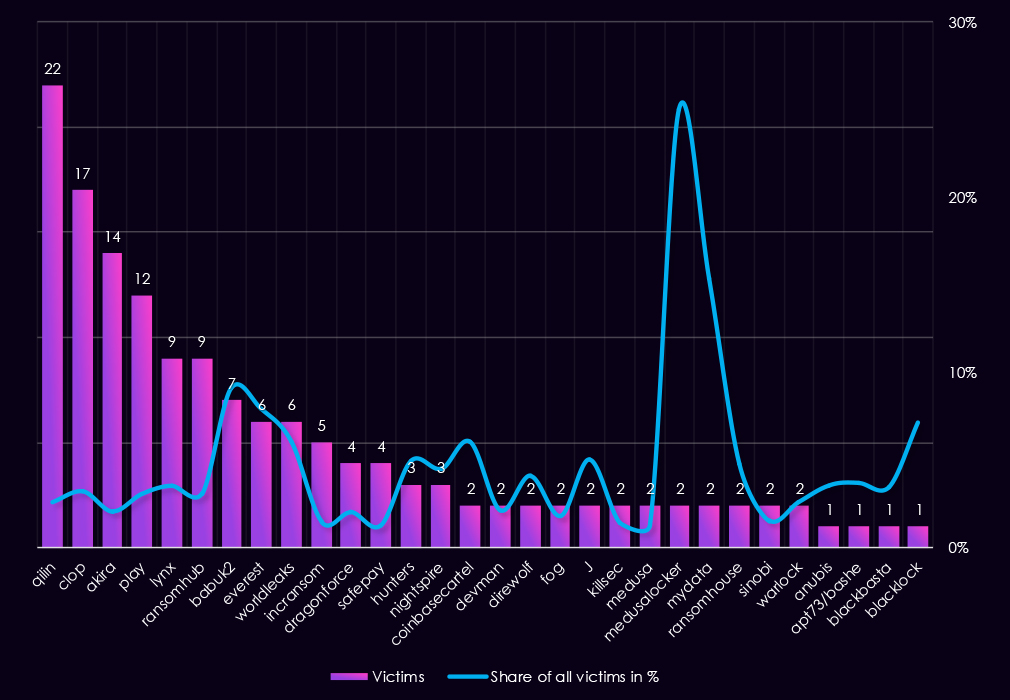
Reviewing the total 2025 victim counts alongside each gang’s share of victims in the energy & utilities sector helps identify whether observed activity reflects scale or sector-specific focus.
By absolute victim count, Qilin (22), Clop (17), Akira (14), and Play (12) were the most active gangs. However, energy & utilities represent a small portion of their overall activity, with shares ranging from 2.1% to 3.2%, indicating broad targeting rather than a concentrated sector focus.
Only a limited number of gangs show a relatively high sector concentration (>10%). MedusaLocker stands out most clearly, with 25.0% of its victims in energy & utilities, followed by MyData (15.4%) and Babuk2 (9.1%), which approaches that threshold. These figures suggest a stronger proportional emphasis on the sector, though not necessarily sustained volume.
Several high percentage values are driven by very low total victim counts, making them statistical outliers. MedusaLocker and MyData each recorded only two energy & utilities victims, meaning small changes in activity significantly inflate percentage shares. Similar skew is visible for BlackLock (7.1%), Everest (7.9%), and CoinbaseCartel (6.1%), all with limited overall activity.
The majority of gangs fall into a low focus range (<5%), including RansomHub, Lynx, DragonForce, SafePay, KillSec, Medusa, Sinobi, and Warlock. This distribution suggests that for most actors, energy & utilities were not a priority sector in 2025.
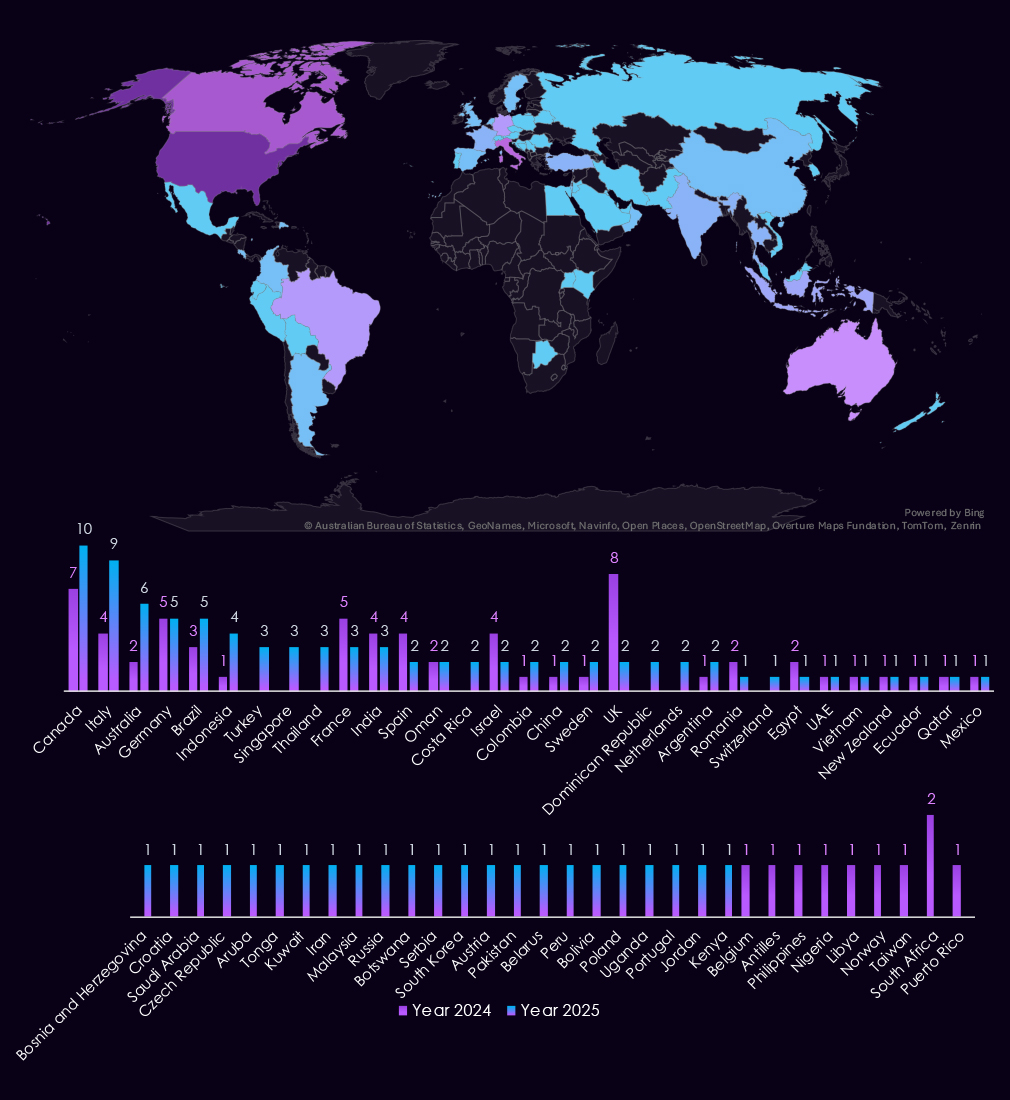
With 58 victims, the USA accounts for 35% of finance industry victims in 2025. The US also recorded a major decline from 76 victims in 2024.
Notably, the UK has also observed a major decline. Whereas Italy, Australia, Turkey, Singapore, and Thailand were among the most newly targeted.
A total of 55 countries recorded victims in 2025, a major increase from 34 in 2024.
Year-over-Year Risk Elevation: Low

In 2025, the energy and utilities sector experienced continued but relatively limited APT exposure, with victims observed in 14% of tracked campaigns, reflecting persistent but selective targeting compared to higher-volume industries. Activity remained dominated by state-linked actors focused on espionage, strategic access, and potential disruption of critical infrastructure, with cybercrime actors present largely in opportunistic or secondary roles. Geographic targeting remained concentrated across Asia-Pacific, North America, Europe, and the Middle East, with slightly broader dispersion year over year into additional jurisdictions.
Observed attacks continued to favour web applications as primary entry points, but 2025 showed broader technology probing despite lower overall volume, including operating systems, remote access services, mobile platforms, and internal management tooling. This expansion suggests increased reconnaissance and early-stage access activity against supporting IT and operational layers rather than large-scale exploitation.
Underground and dark web chatter rose steadily from late 2024 into 2025, driven primarily by data breaches, data leaks, and ransomware-related discussions, indicating growing visibility and monetization pressure even where incident volumes remained moderate. Vulnerability activity remained centred on high-impact exploit classes, particularly remote code execution, denial-of-service, and injection flaws, with consistent appearance of post-compromise weaknesses such as privilege escalation and access control issues.
The number of ransomware victims increased 12% year over year, but the sector’s share of global ransomware activity continued to decline, reinforcing its status as a secondary target for most groups. Activity remained dispersed across many actors, with limited evidence of sustained sector specialization. Geographic exposure widened significantly in 2025, with more countries affected despite declining victim counts in traditional hotspots, indicating broader but lower-intensity targeting likely to persist into 2026.
Over the past 12 months, healthcare organizations recorded victims in only 1 of the 43 Advanced Persistent Threat (APT) campaigns observed – an incidence rate of 2.3%. It is also a decline from 2 campaigns in the previous year.
There were also only single-sector victims compared to multiple in last year’s campaigns.
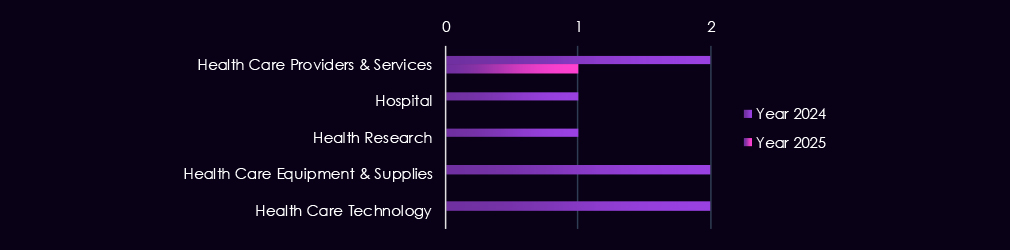
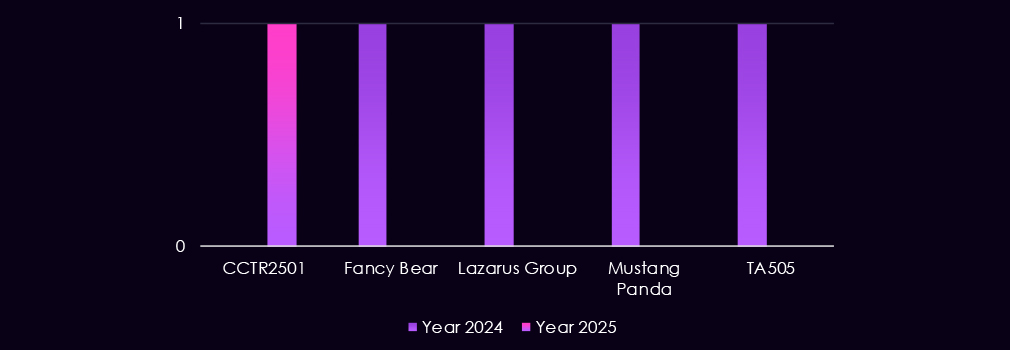
Turkish-speaking cybercriminal group CCTR2501 was the only observed threat actor in the 2025 campaign.
Last year, we saw overlapping TTPs between Russian cybercrime syndicate TA505 and nation-state Fancy Bear groups in one campaign. And the North Korean Lazarus Group overlaps with the Chinese Mustang Panda in the second campaign.
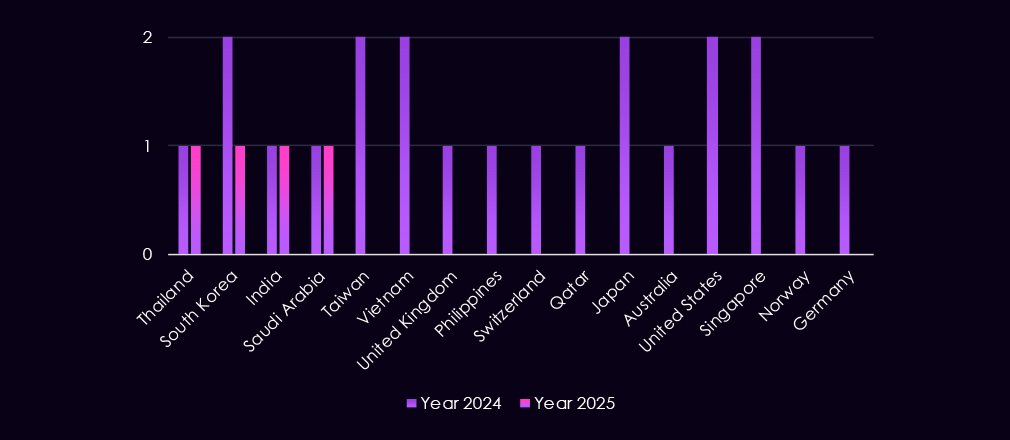
The geographic targeting is scattered for the Turkish-speaking group. This suggests opportunistic targeting in line with financial motivation over political.
Last year’s victimology shows a similar scattered pattern, leaning towards the financially motivated TA505 and Lazarus Group as more likely threat actors in the overlapping TTP attributions.
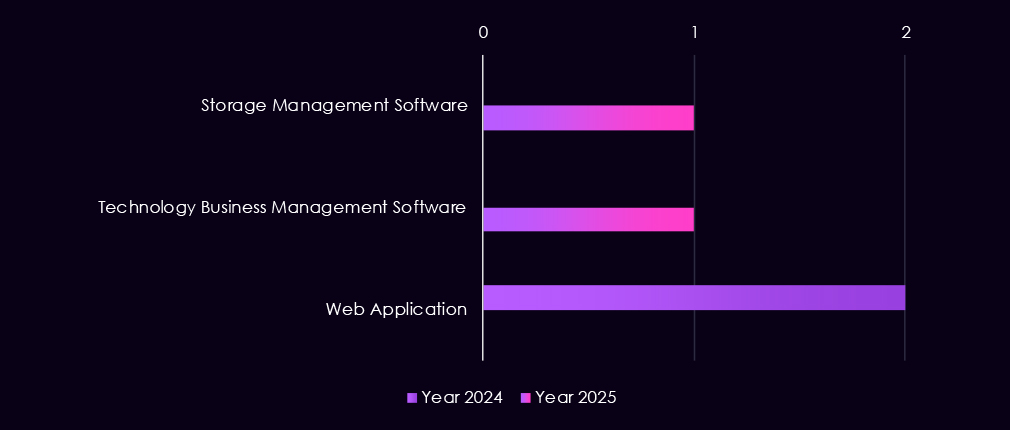
Web Applications were targeted in both of the 2024 campaigns.
However, the Turkish-speaking group went with Storage and Business Technology Management software in their 2025 campaign.
We would like to point out data bias in the APT campaigns dataset, where we omit most of the ransomware, as we track it separately in great detail. Some cybercrime syndicates run their own ransomware as opposed to using Ransomware-as-a-Service and end up included. Typically, the long-running Russian syndicates.
Due to this bias, we see such low volume against the healthcare industry in this category, as it seems like most APT groups are not despicable enough to target hospitals and other healthcare services.
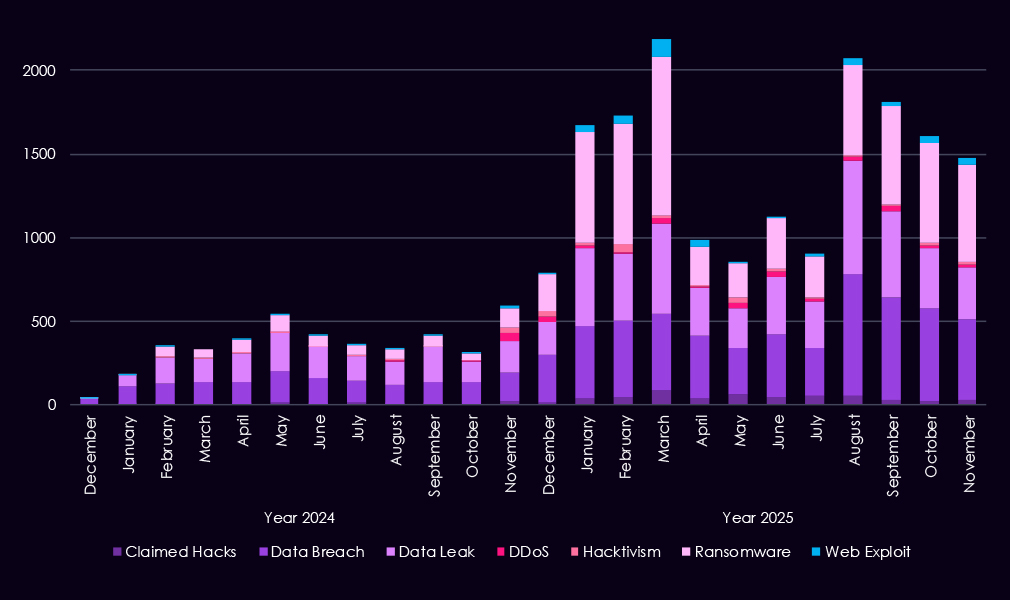
Over the past 23 months, CYFIRMA’s telemetry has identified 21,451 healthcare industry-linked mentions. This is from a total of 2.5 million posts across various underground and dark web channels and forums.
The chart above shows the total counts of industry-linked mentions for the healthcare industry and individual categories of context for the mentions.
The chart below shows Year-over-Year growth for each category in this industry.
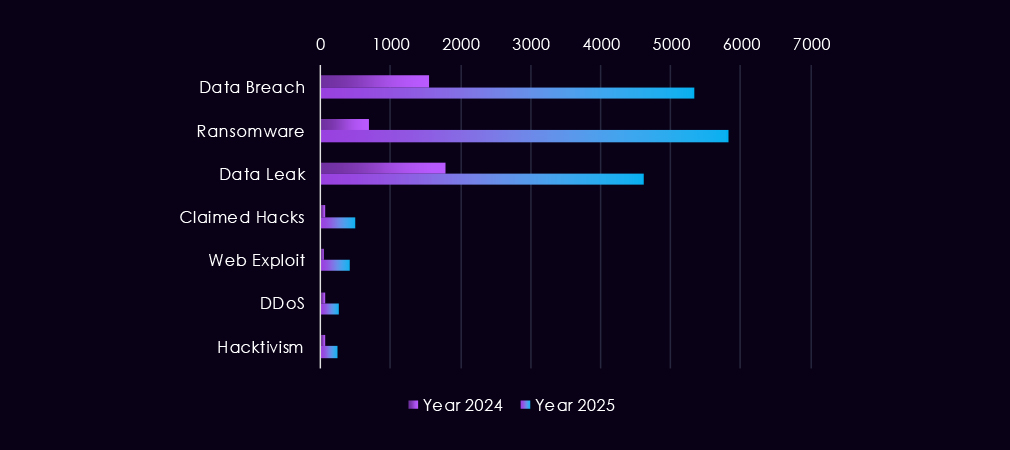
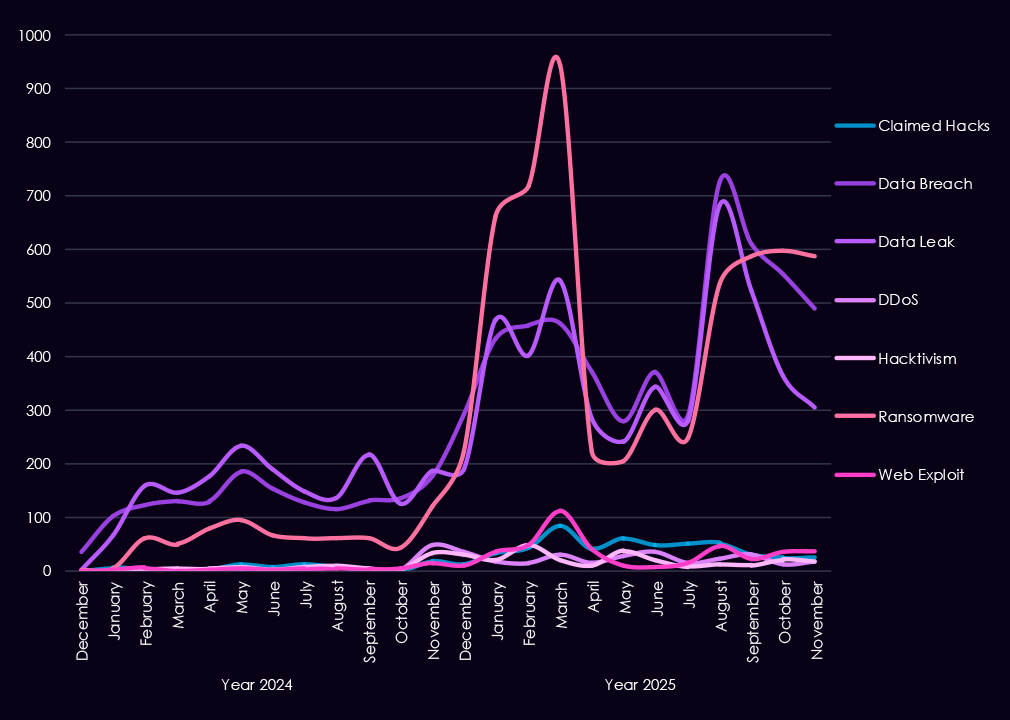
Underground and dark web chatter linked to the healthcare sector increased sharply from late 2024 into 2025, reflecting both rising attack activity and greater public exposure of incidents. Data breaches and data leaks dominate discussions, with volumes climbing steadily and remaining high throughout 2025, indicating continued large-scale exposure of sensitive patient and operational data rather than isolated cases. Ransomware-related chatter shows the most dramatic growth, surging early in 2025 and after a dip, growing once more, highlighting sustained extortion pressure against healthcare organizations.
Mentions of claimed hacks and web exploits also rise notably in 2025, suggesting increased interest in compromises or leveraging exposed vulnerabilities. DDoS and hacktivism remain lower in overall volume but show periodic spikes, often tied to short-lived campaigns rather than persistent activity.
Overall, the 2025 pattern points to healthcare remaining a high-impact, high-payoff target, with threat activity increasingly centered on valuable data exposure and ransomware-driven extortion rather than simple disruption.
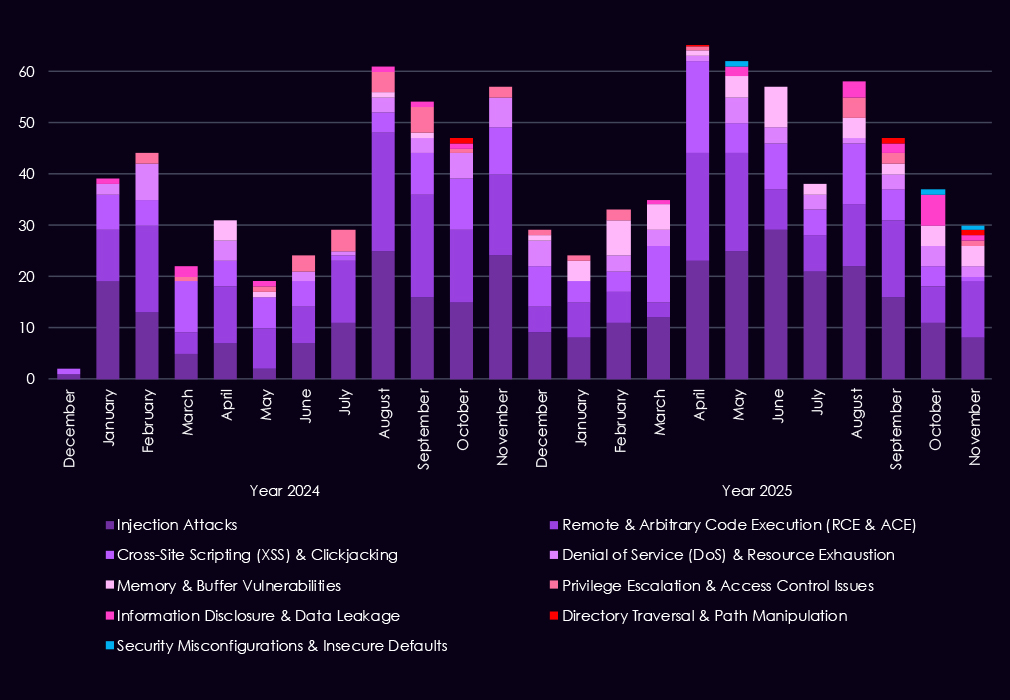
Over the past 23 months, CYFIRMA’s telemetry has identified 945 healthcare industry-linked mentions. This is from over 90k CVEs reported and updated in the same time period.
The chart above shows the total counts of industry-linked mentions for healthcare technology and individual categories of reported vulnerabilities.
The chart below shows Year-over-Year growth for each category in this industry.
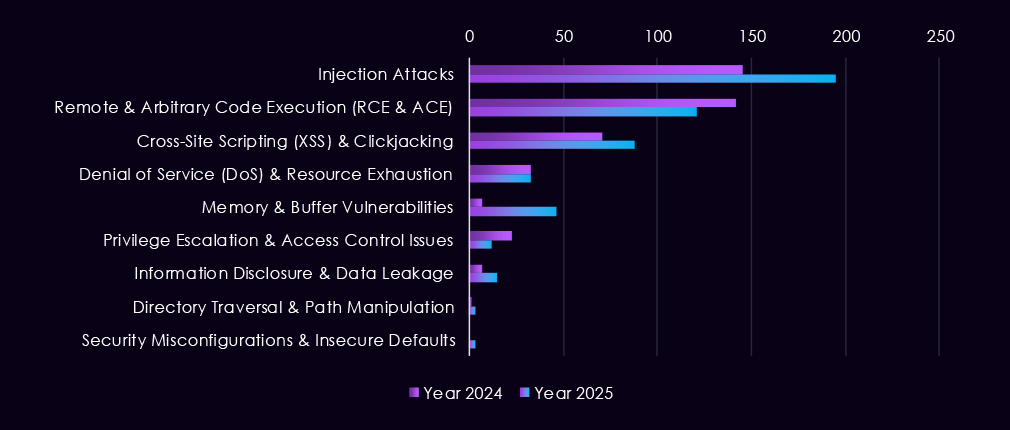
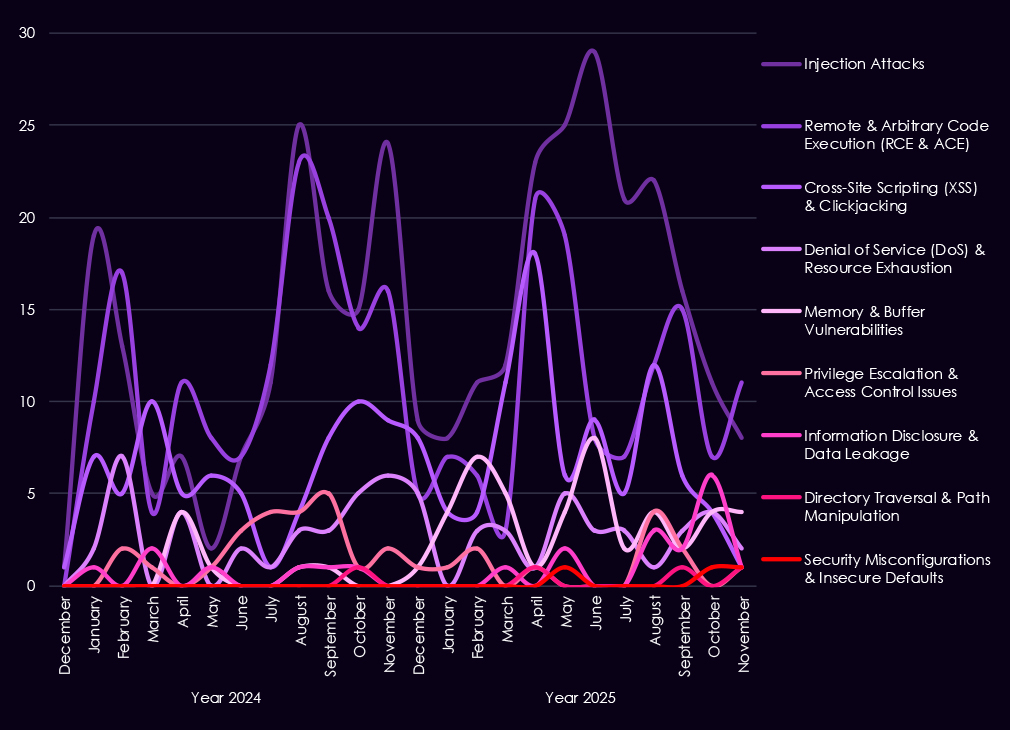
Reported CVEs affecting the healthcare industry highlight continued exposure of web-facing and application-layer technologies, with 2025 maintaining steady discovery across several high-risk vulnerability classes. Injection attacks remain the most frequently reported issue, reflecting ongoing weaknesses in healthcare web applications and patient-facing systems. Remote and arbitrary code execution (RCE/ACE) vulnerabilities also remain prominent, underlining the risk of direct system compromise in environments that often run complex and legacy software.
XSS and clickjacking issues continue to appear regularly, though they carry lower impact compared to injection and RCE flaws. At the same time, memory and buffer vulnerabilities show increased presence in 2025, suggesting more attention to deeper technical flaws that can support post-exploitation and vulnerability chaining. Lower but persistent reporting of denial-of-service, privilege escalation, and information disclosure issues points to ongoing risk across both availability and data protection.
Overall, the 2025 vulnerability profile indicates broad, sustained weakness across healthcare application stacks, with attackers likely prioritizing flaws that enable data access, control, or follow-on exploitation rather than simple misconfigurations.
In the past 12 months, CYFIRMA has identified 559 verified healthcare industry ransomware victims. Only two more than 557 in the previous year, and a relatively mild elevation of 10.3% from 507 victims in 2023.
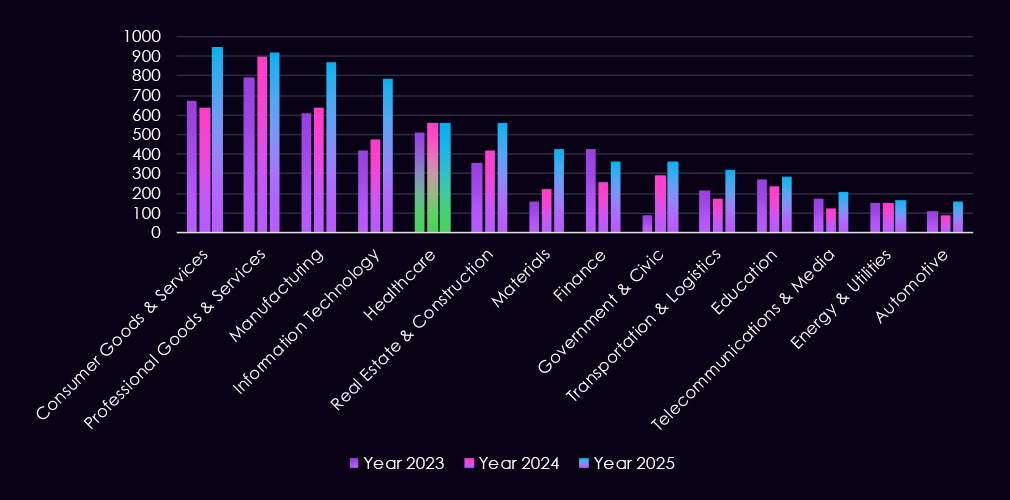
The healthcare industry accounts for 8.07% of the overall total of 7,099 ransomware victims during the same period. That is a decline from 10.67% in the previous year despite a nearly identical victim count. In 2023, healthcare comprised 10.12% of all victims.
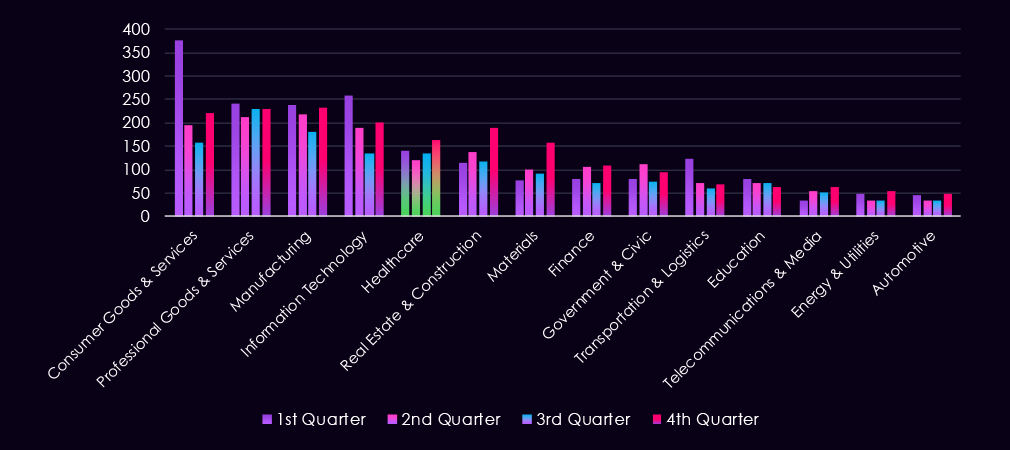
The bar chart above is focused only on 2025, and the victim counts per quarter are shown clearly and easily to see the trends. The healthcare industry dipped mildly after Q1 and then grew each quarter, with Q4 finally surpassing Q1.
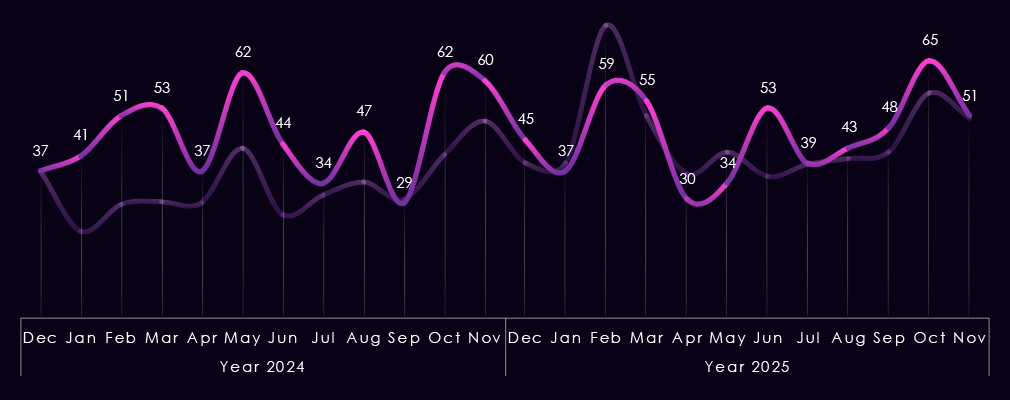
Monthly activity charted over scaled-down global all industries victims counts shows that the healthcare industry followed the global trendline quite closely.
In early 2024, there was an upward divergence before alignment with the global trend until another, more minor uptick in October.
2025 shows downwards divergence during the February global spike and only one major uptick during June.
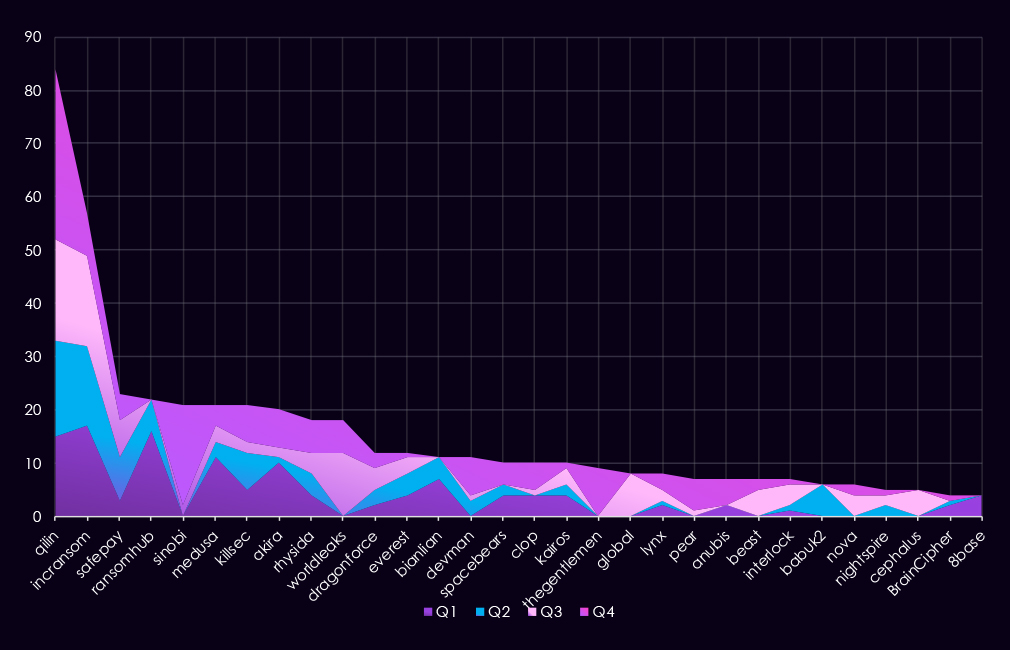
In total, 81 out of 124 gangs recorded victims in the healthcare industry, a 65% participation.
A breakdown of the top 30 gangs’ quarterly activity provides insights into which gangs were active each quarter.
Q1 activity was led by IncRansom (17), RansomHub (16), and Qilin (15), with Medusa (11) and Akira (10) also showing significant presence. The distribution indicates broad targeting by multiple established actors rather than reliance on a single dominant group.
In Q2, overall activity remained high but became more concentrated. Qilin (18) and IncRansom (15) continued to lead, while SafePay (8) and KillSec (7) increased activity. Several Q1-active groups, including RansomHub and Akira, declined sharply during the quarter.
Q3 marked a notable shift. Qilin (19) maintained high volume, while IncRansom (17) remained consistently active. New or resurging actors appeared, including WorldLeaks (12), Global (8), and Cephalus (5), contributing to a broader threat landscape despite stable leadership at the top.
By Q4, activity intensified further. Qilin (32) clearly dominated the quarter, while Sinobi (19) emerged abruptly as a major contributor. TheGentlemen (9), DevMan (7), KillSec (7), and Akira (7) also showed increased late-year activity, indicating renewed or expanded targeting of healthcare organizations.
Overall, the healthcare sector experienced sustained and escalating ransomware pressure across all quarters, with Qilin and IncRansom acting as persistent high-volume threats and several groups demonstrating sharp, late-year surges. The pattern suggests both long-running campaigns and opportunistic waves, making healthcare one of the more consistently targeted sectors in 2025.
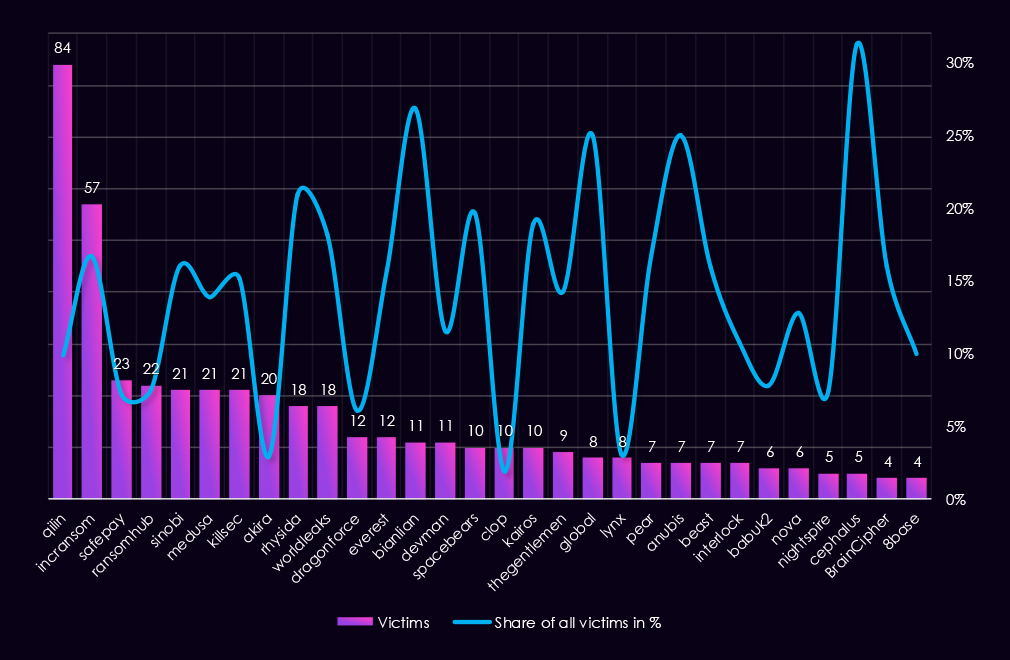
Reviewing the total 2025 victim counts alongside each gang’s share of healthcare victims highlights which actors showed a disproportionate focus on the sector versus broad-based activity.
By absolute volume, Qilin recorded the highest number of healthcare victims (84), but healthcare represents 9.9% of its total victims, indicating scale rather than sector specialization. In contrast, IncRansom (57 victims, 16.7%), Sinobi (21 victims, 16.0%), and KillSec (21 victims, 15.2%) combine sustained volume with a relatively high proportional focus, suggesting healthcare was a meaningful part of their targeting strategy.
Several gangs show a high healthcare concentration (>10%), including Rhysida (20.9%), WorldLeaks (18.2%), Medusa (13.9%), Everest (15.8%), BianLian (26.8%), SpaceBears (19.6%), Kairos (18.9%), and TheGentlemen (14.3%). These figures indicate healthcare was disproportionately affected relative to these groups’ overall activity.
Cephalus (31.3%), Global (25.0%), Anubis (25.0%), and Pear (16.7%) each recorded fewer than ten healthcare victims, yet collectively still present a focused threat.
Several high-volume actors show low healthcare focus (<5%), including Akira (3.0%), Clop (1.9%), and Lynx (3.1%), indicating healthcare played a minor role in their overall operations despite notable absolute victim counts.
Overall, the healthcare sector shows a higher concentration of gangs with disturbingly high proportional exposure than many sectors.
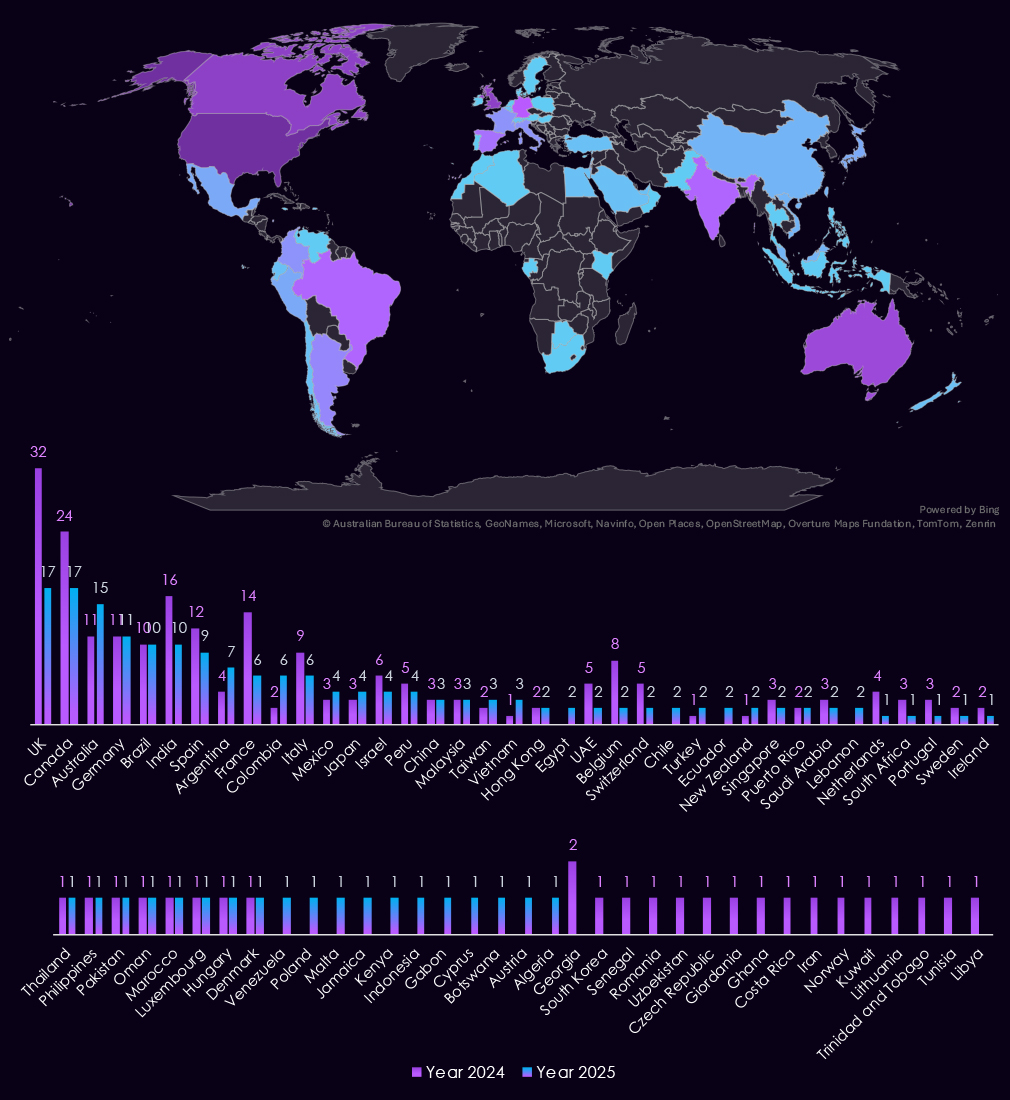
With 364 victims, the USA accounts for 65% of healthcare industry victims in 2025. The US also recorded a substantial increase from 316 victims in 2024. This is likely driven by the for-profit healthcare system in the US.
Many of the previously hard-hit countries, like the UK, Canada, India, and Belgium, have seen major declines in 2025. However, Australia, Argentina, Colombia, Vietnam, and Egypt have seen increases, Victimology shows sustained volume but shifting geographies.
A total of 57 countries recorded victims in 2025, one less from 58 in 2024.
Year-over-Year Risk Elevation: Low

In 2025, the healthcare sector saw minimal APT activity, with victims observed in only one tracked campaign (2.3%), down from two in 2024. This represents both a year-over-year decline in APT exposure and a narrowing of activity to a single, financially motivated cybercriminal group, rather than the overlapping state and cybercrime activity seen previously. Geographic targeting remained scattered, reinforcing the assessment of opportunistic, profit-driven intrusion rather than coordinated strategic campaigns.
In contrast, underground and dark web activity increased sharply from late 2024 into 2025, driven primarily by data breaches, data leaks, and ransomware-related discussions. Ransomware chatter showed the strongest growth, underscoring healthcare’s continued attractiveness as a high-impact, extortion-friendly sector due to the sensitivity and value of patient and operational data.
Vulnerability trends in 2025 indicate persistent, broad exposure across healthcare application stacks, with injection and remote code execution flaws remaining dominant. Increased visibility of memory corruption, privilege escalation, and availability-impacting issues suggests attackers are increasingly positioned to chain vulnerabilities and sustain post-compromise access, rather than relying on isolated exploits.
Ransomware victimization remained consistently high year over year, with healthcare accounting for 8.1% of global victims despite a declining overall share, reflecting stable pressure amid expanding ransomware activity elsewhere. Attacks were widely distributed across many actors, but several groups showed disproportionate healthcare focus, and activity intensified toward year-end. The United States remained the primary target, with victimization increasing further in 2025, while other regions declined or shifted, reinforcing healthcare’s status as a persistently targeted, high-risk sector entering 2026.
Over the past 12 months, the transportation & logistics industry recorded victims across 10 of the 43 Advanced Persistent Threat (APT) campaigns observed – an incidence rate of 23%. It is also one more than the 9 campaigns in 2024.
These victims spanned multiple segments within the industry, as shown below:
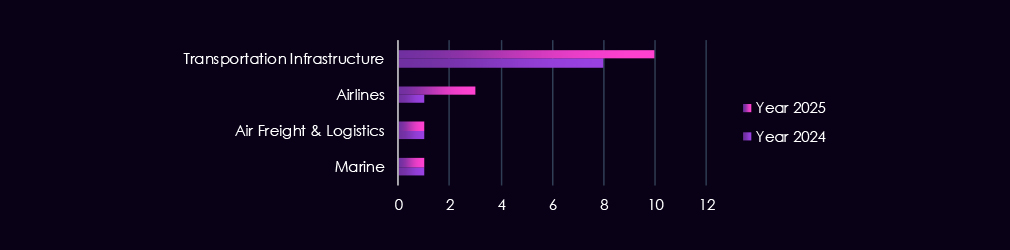
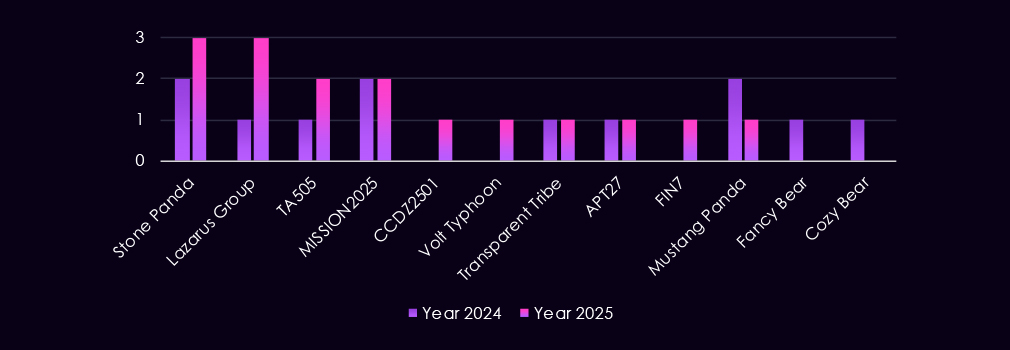
The transportation & logistics sector is targeted by a mix of nation-state and financially motivated threat actors, reflecting its strategic importance to trade flows, supply chains, and national infrastructure. Notably, activity attributed to the Lazarus Group increases in 2025. China-aligned groups such as Stone Panda, MISSION2025, Mustang Panda, APT27, and Volt Typhoon are also observed, pointing to interest in logistics networks, transportation infrastructure, and operational visibility.
At the same time, financially motivated groups such as TA505 and FIN7 remain active. Continued activity from Transparent Tribe and the appearance of a newly tracked Algerian group CCDZ2501 further suggest an evolving and diversifying threat landscape.
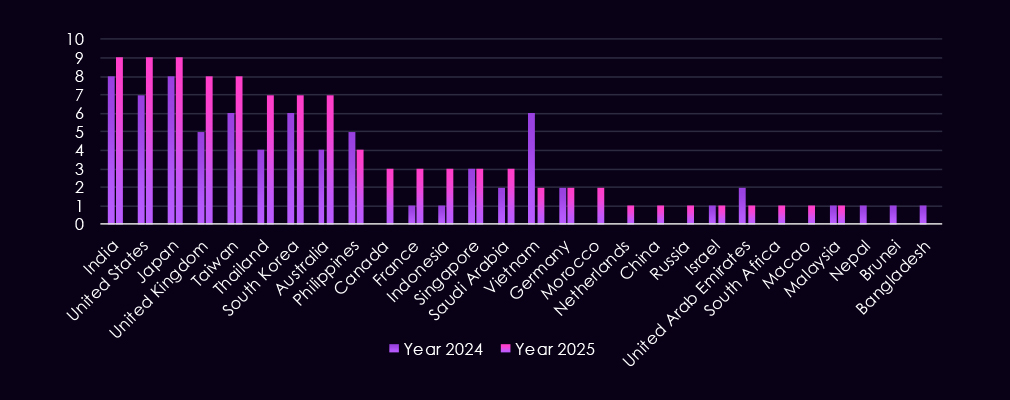
Observed victims are spread across major global trade and transit hubs, in line with the sector’s role in international supply chains. In 2025, the most frequently attacked countries include the United States, Japan, India, Taiwan, and the United Kingdom, alongside sustained activity in South Korea, Australia, and Thailand.
Additional victim reporting spans Southeast Asia, the Middle East, Europe, and Africa, including Singapore, the Philippines, Indonesia, Saudi Arabia, France, Germany, and a smaller number of single-observation locations.
Overall, the distribution shows geographically broad targeting aligned with international shipping routes, logistics hubs, and multinational transportation operations.
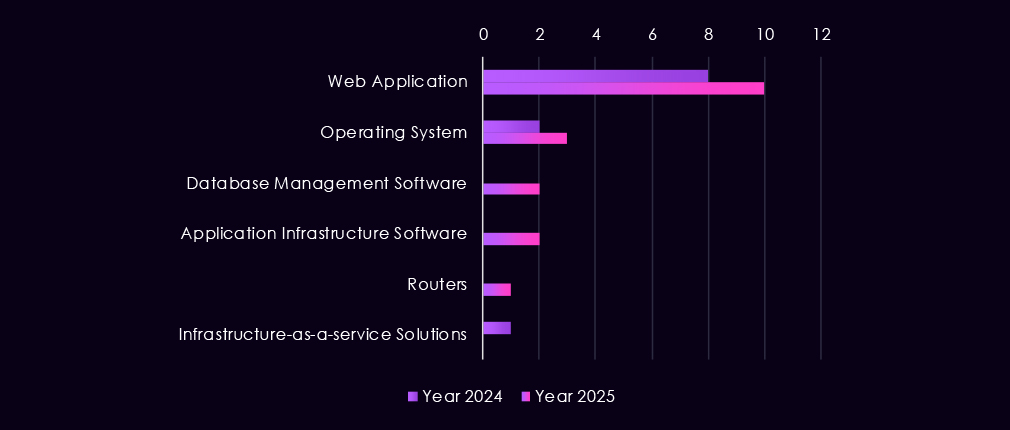
Attacks against the transportation & logistics sector continue to center on web applications, which remain the most frequently targeted systems in both 2024 and 2025. Their prominence reflects widespread exposure across booking platforms, freight management systems, and customer-facing portals, making them a consistent entry point for initial compromise.
In 2025, activity expands modestly beyond web applications to include operating systems, application infrastructure software, and database management platforms, indicating increased focus on gaining deeper access and maintaining control after initial entry beyond web applications. Targeting of network devices such as routers also appears, suggesting higher sophistication of some advanced threat actors.
Overall, the technology mix points to campaigns aimed at both exposed service layers and the supporting backend systems that underpin logistics operations, rather than narrow, single-vector attacks.
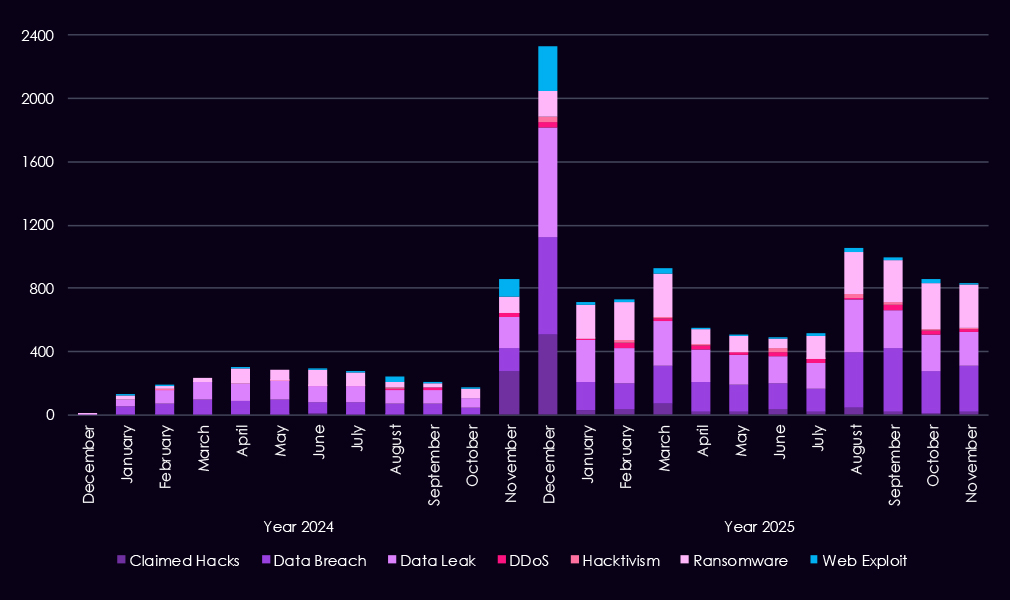
Over the past 23 months, CYFIRMA’s telemetry has identified 14,736 transportation & logistics industry-linked mentions. This is from a total of 2.5 million posts across various underground and dark web channels and forums.
The chart above shows total counts of industry-linked mentions for the transportation & logistics industry and individual categories of context for the mentions.
The chart below shows Year-over-Year growth for each category in this industry.
Underground and dark web chatter related to the transportation & logistics sector increased sharply from late 2024 into 2025, indicating higher attack activity and greater public exposure of incidents. Data breach and data leak discussions dominate, with volumes rising steadily and remaining elevated throughout 2025, pointing to ongoing exposure of sensitive operational, customer, and partner data rather than isolated events.
Ransomware-related chatter shows sustained growth, with repeated peaks across 2025 following a strong rise at the end of 2024, highlighting continued extortion pressure on logistics & transportation organizations. Mentions of claimed hacks and web exploits also increase, especially in early and mid-2025. DDoS and hacktivism remain lower in overall volume but show periodic spikes, consistent with short-lived campaigns rather than continuous activity.
Overall, the 2025 pattern reflects persistent, high-volume discussion of data exposure and ransomware activity, aligning with organized and monetization-focused threat behavior targeting the transportation and logistics industry.
Over the past 23 months, CYFIRMA’s telemetry has identified 1,136 transportation & logistics industry-linked mentions. This is from over 90k CVEs reported and updated in the same time period.
The chart above shows total counts of industry-linked mentions for transportation & logistics technology and individual categories of reported vulnerabilities.
The chart below shows Year-over-Year growth for each category in this industry.
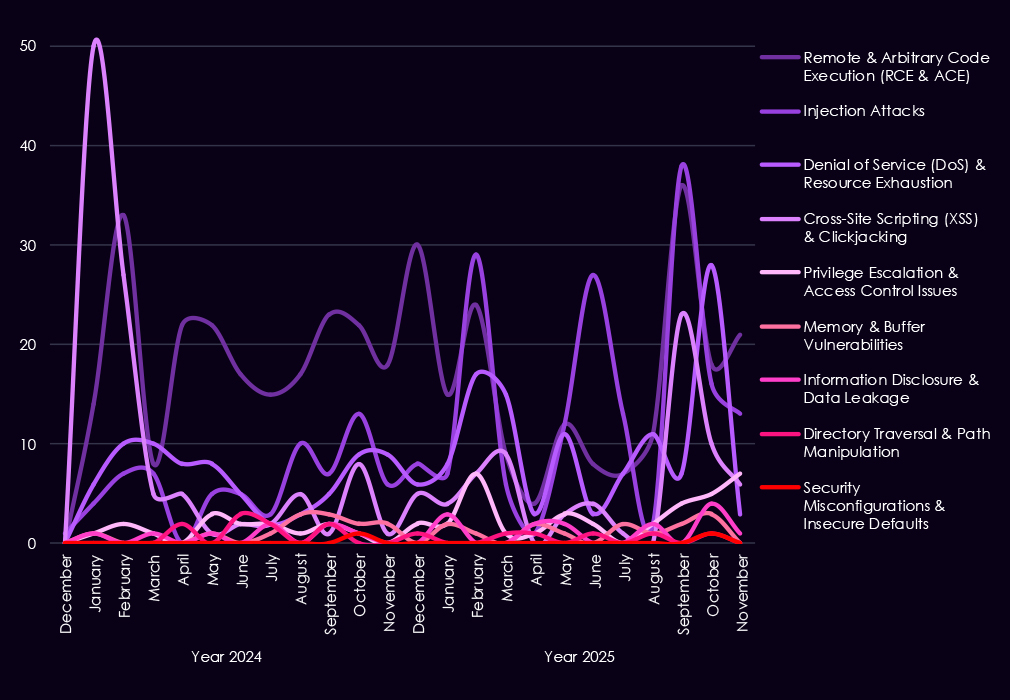
Reported CVEs affecting the transportation & logistics sector continue to be dominated by high-impact vulnerability classes, with 2025 showing sustained activity across several exploit-relevant categories. Remote and arbitrary code execution (RCE/ACE) vulnerabilities remain the most prevalent, appearing consistently throughout the year and highlighting the ongoing risk of direct system compromise in logistics platforms and supporting infrastructure.
Injection attacks also feature prominently, with multiple spikes in 2025, reinforcing persistent weaknesses in web-based and backend systems commonly used for scheduling, tracking, and operations. Denial-of-service vulnerabilities remain regularly reported, reflecting the sensitivity of transportation systems to availability disruption. While lower in volume, privilege escalation, memory corruption, and information disclosure issues continue to appear across 2025, indicating exposure to post-compromise and vulnerability-chaining scenarios.
Overall, the CVE profile suggests continued emphasis on flaws that enable control, disruption, or deeper access, rather than isolated or low-impact configuration issues, within transportation & logistics environments.
In the past 12 months, CYFIRMA has identified 321 verified transportation & logistics industry ransomware victims. That is a dramatic increase of 88% from 171 in the previous year, and 51% more than 212 victims in 2023.
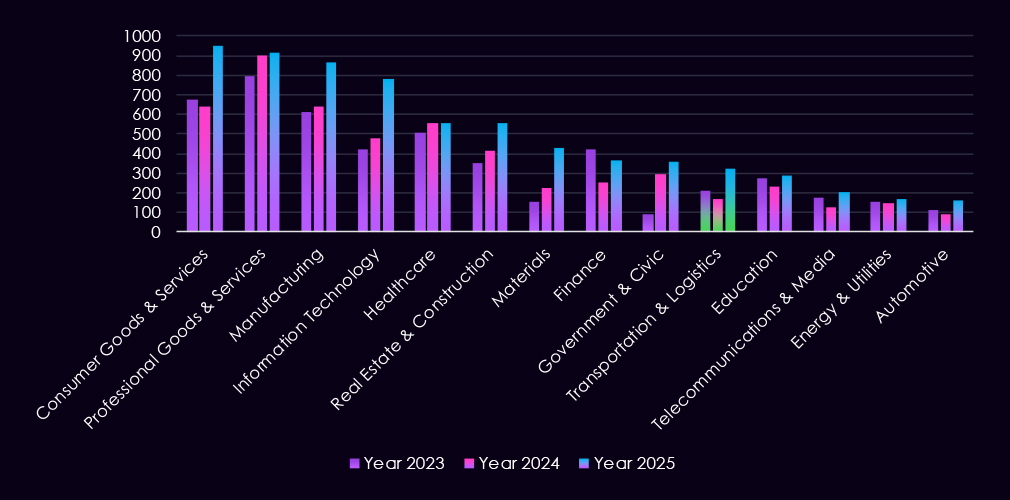
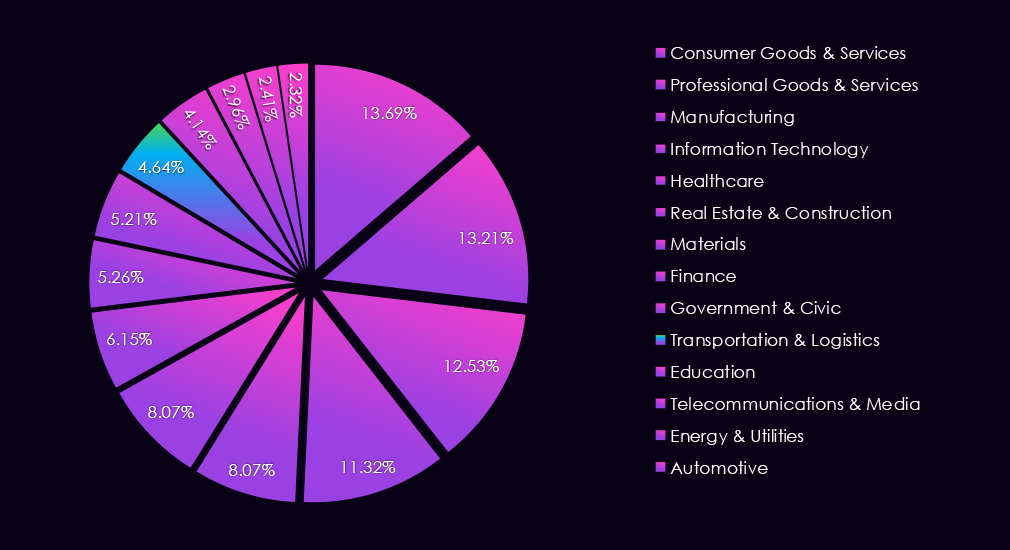
The transportation & logistics industry accounted for 4.64% of the total 7,099 ransomware victims during the same period. This is an increase from 3.28% in the previous year and also from 4.23% in 2023.
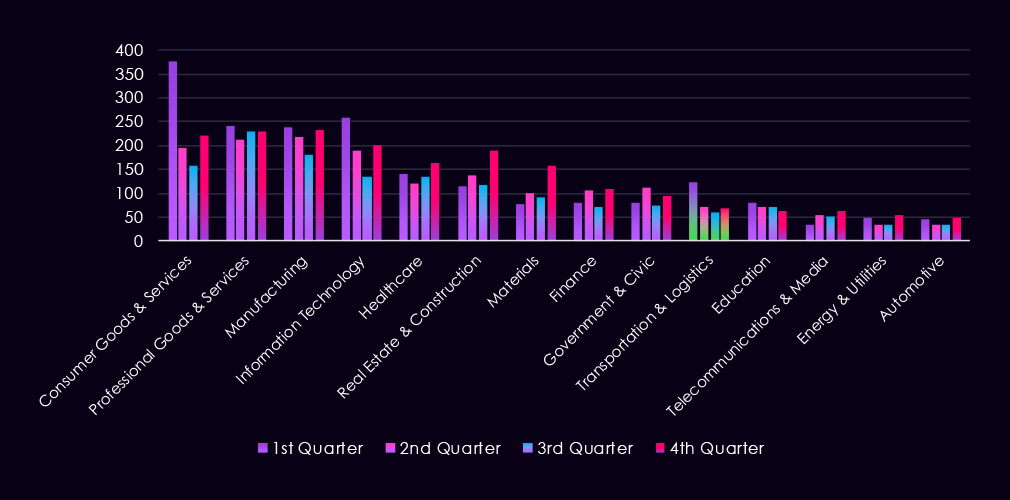
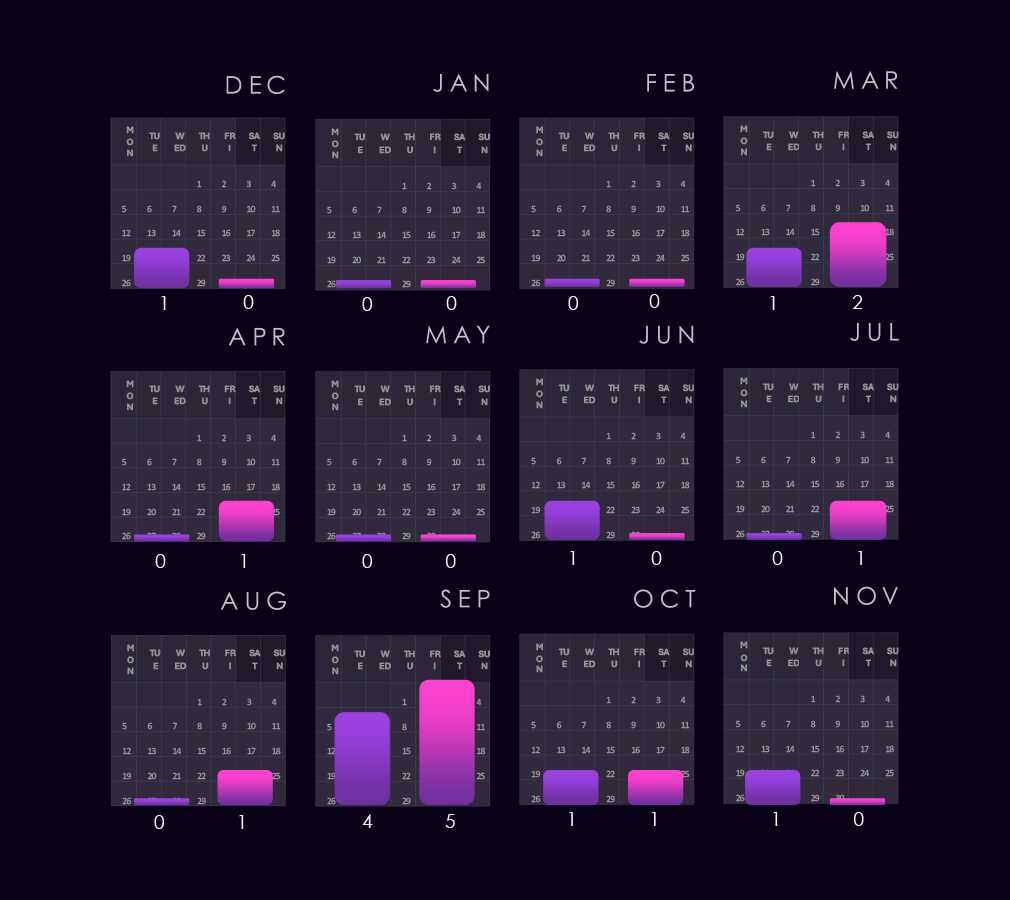
The bar chart above is focused only on 2025, and the victim counts per quarter are shown clearly and easily to see trends. Transportation & logistics recorded a major spike during Q1, followed by lower, but evenly sustained numbers for the rest of the year.
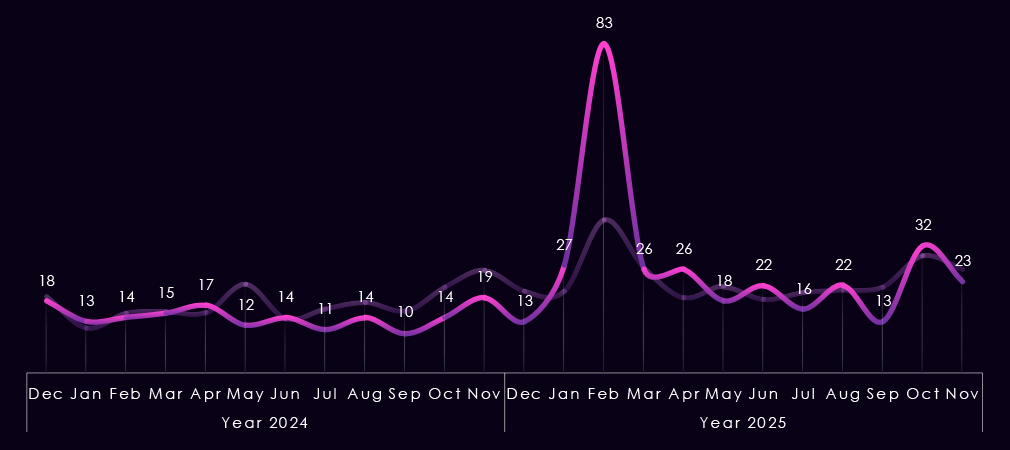
Monthly activity charted over scaled-down global all industries victims counts shows that in 2024, the transportation & logistics industry followed the global trendline until April, where it diverged below the global trendline until December, but kept with global mild spikes.
In 2025, we can see a massive spike in February, when this industry was disproportionately hit by the Clop gang rampage. The rest of the year is oscillating closely around the global trendline, with only a notable divergence being the September dip.
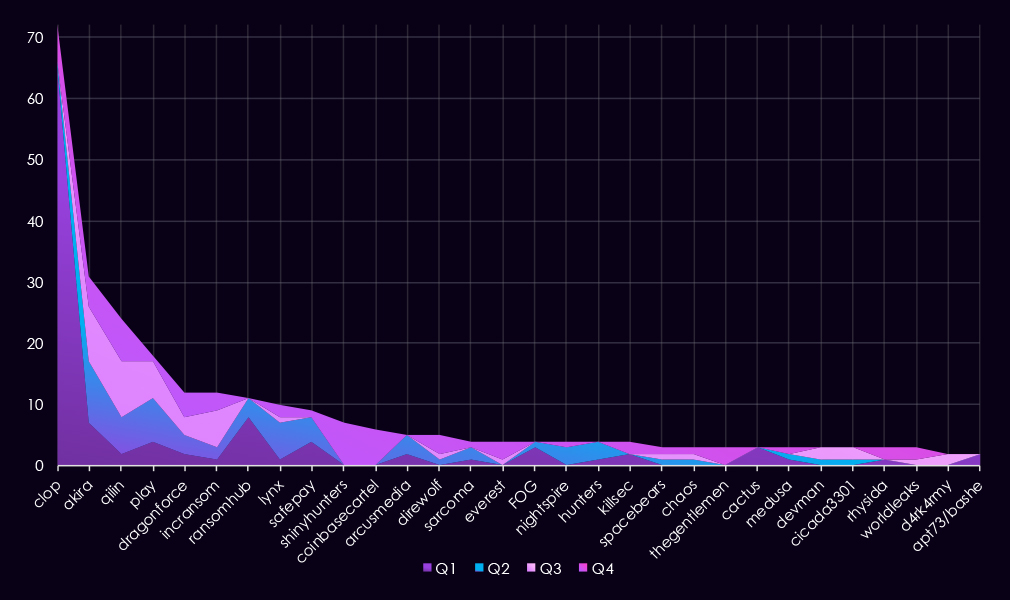
In total, 63 out of 124 gangs recorded victims in the transportation & logistics industry. That is 51% participation.
A review of quarterly top 30 ransomware gangs’ activity in 2025 shows the massive February spike followed by more distributed activity in the second half of the year.
Q1 activity was overwhelmingly driven by Clop (65), which accounted for the majority of observed victims during the quarter. RansomHub (8) and Akira (7) followed at a much lower level, while all other gangs showed only limited activity. This distribution indicates a highly concentrated, specific exploit-driven surge.
In Q2, activity dropped significantly from Q1 levels and became more fragmented. Akira (10) emerged as the most active group, followed by Play (7) and Qilin (6). Several other gangs recorded low but steady activity, suggesting a return to more opportunistic targeting patterns.
Q3 showed a relatively stable threat environment. Akira (9) and Qilin (9) led the quarter, with Play (6) and IncRansom (6) also maintaining moderate activity. No single actor dominated, and overall volumes stayed lower than the Q1 peak.
By Q4, activity remained distributed across a wider set of actors. Qilin (7) led the quarter, while ShinyHunters (7) and CoinbaseCartel (6) appeared abruptly with notable late-year activity. Clop (6) re-emerged after minimal activity in Q2 and Q3, alongside several other low-volume groups.
Overall, transportation and logistics saw a pronounced Q1 spike driven by a single actor, followed by a more balanced and lower-intensity threat landscape for the remainder of the year. Late-year activity reflects an upward global trend.
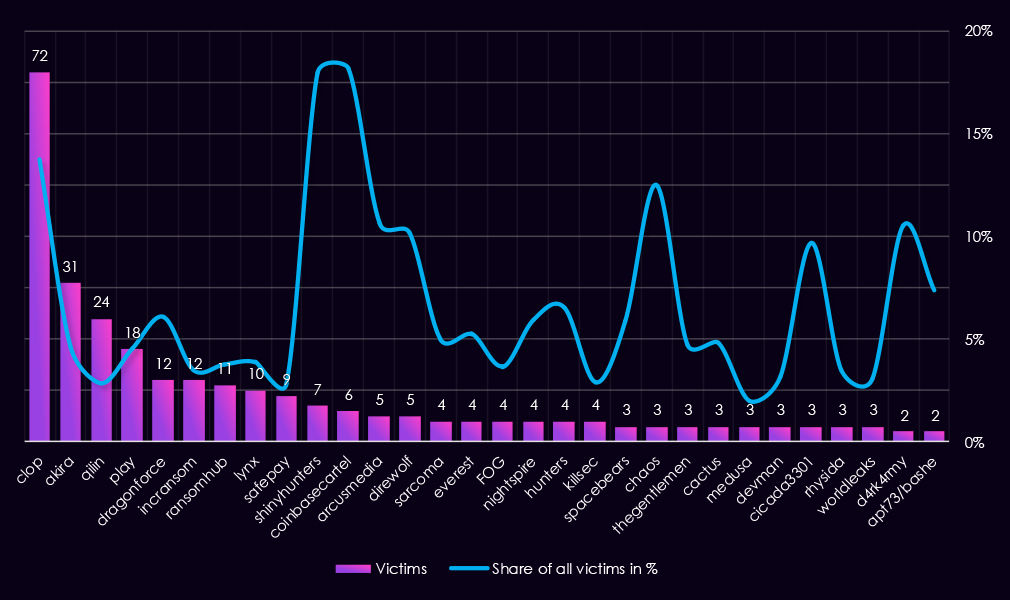
Reviewing the same top 30 gangs counts alongside each gang’s share of victims in the transportation & logistics sector helps distinguish high-volume activity from sector-specific focus.
By absolute volume, Clop (72 victims) was the most active gang. Unlike several other high-volume actors, transportation & logistics accounts for a meaningful portion of Clop’s overall activity (13.7). In contrast, Akira (31 victims, 4.6%), Qilin (24 victims, 2.8%), and Play (18 victims, 4.6%) show high activity but low proportional exposure, consistent with broad targeting.
Several gangs show a relatively high sector concentration (>10%). ShinyHunters (17.9%) and CoinbaseCartel (18.2%) stand out, along with ArcusMedia (10.6%), DireWolf (10.2%), Chaos (12.5%), and D4rk4rmy (10.5%). These figures suggest transportation and logistics represented a disproportionate share of these groups’ activity during 2025.
As in other sectors, some elevated percentage values are driven by low overall victim counts. Chaos and D4rk4rmy recorded only 3 and 2 sector victims, meaning small absolute changes significantly inflate their percentage shares and should be interpreted cautiously.
Most gangs fall into a low focus range (<5%), including RansomHub, Lynx, SafePay, IncRansom, KillSec, Medusa, and WorldLeaks, indicating that transportation & logistics was not a primary target for the majority of ransomware actors.
Overall, the sector shows a mix of one high-volume, high-focus actor alongside numerous low-volume outliers. While a subset of gangs demonstrates elevated proportional exposure, most activity reflects opportunistic targeting rather than sustained sector focus.
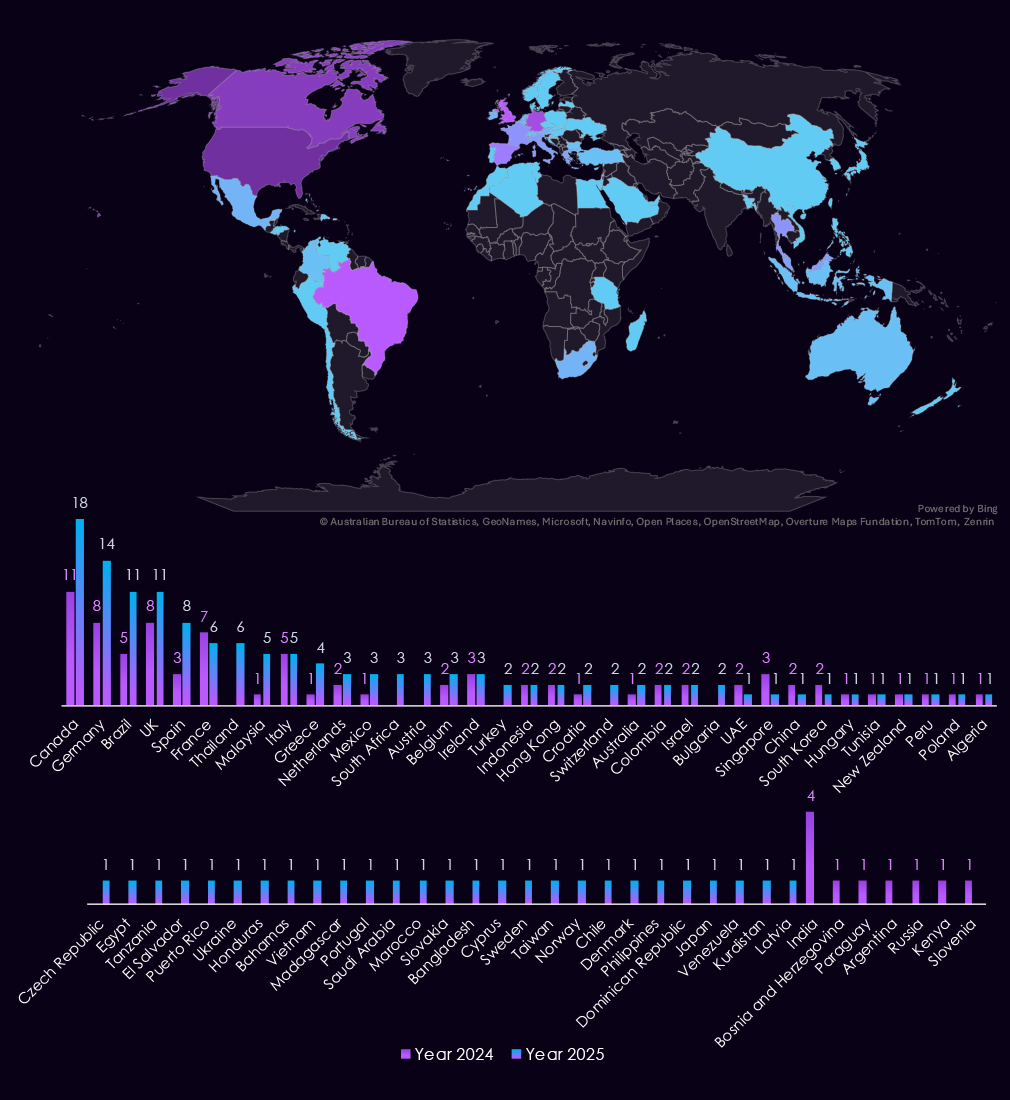
In 2025, the United States will account for 49% of transportation & logistics industry victims, with a total of 159 victims. This is a significant increase from 79 victims in 2024.
Most countries experienced an increase in the number of victims, reflecting the overall rise in industry victims. Curiously, India stands out as the only exception, with a decrease from 4 victims to zero.
A total of 63 countries reported victims in 2025, a substantial increase from the 37 in 2024.
Year-over-Year Risk Elevation: Moderate
In 2025, the transportation & logistics sector experienced a moderate year-over-year increase in APT exposure, with victims observed in 23% of tracked campaigns, up slightly from 2024. Activity reflected a mixed threat model, combining state-aligned interest in supply chains and infrastructure visibility with financially motivated intrusion. Targeting remained geographically broad and aligned with major trade routes and logistics hubs, reinforcing the sector’s strategic relevance to global commerce.
Attack activity continued to center on web applications as primary entry points, consistent with the sector’s reliance on exposed booking, tracking, and customer-facing systems. Compared to 2024, 2025 showed modest expansion into backend systems, including operating systems, application infrastructure, databases, and selected network devices, indicating greater emphasis on deeper access and persistence beyond initial compromise.
Underground and dark web chatter rose sharply from late 2024 into 2025, driven primarily by data breaches, data leaks, and ransomware-related discussions. Ransomware chatter showed sustained growth across the year, while mentions of claimed hacks and web exploits also increased, pointing to heightened visibility and monetization of incidents rather than isolated intrusion claims.
Ransomware victimization increased dramatically year over year (+88%), making transportation & logistics one of the fastest-growing ransomware-impacted sectors in 2025. Activity was highly skewed early in the year, driven by a single large-scale campaign, before settling into a more distributed, opportunistic pattern across many actors. Geographic exposure expanded significantly, with more countries affected than in 2024, and the United States accounting for nearly half of all sector victims.
Overall, 2025 reflects a transition toward higher-volume, globally distributed ransomware risk, layered on top of persistent but selective advanced threat activity.
Over the past 12 months, the automotive industry recorded victims across 12 of the 43 Advanced Persistent Threat (APT) campaigns observed – an incidence rate of 28%. It is also a dramatic change from 2024, when the industry victims showed in only 1 observed campaign.
Victims spanned multiple segments within the industry, as shown below:
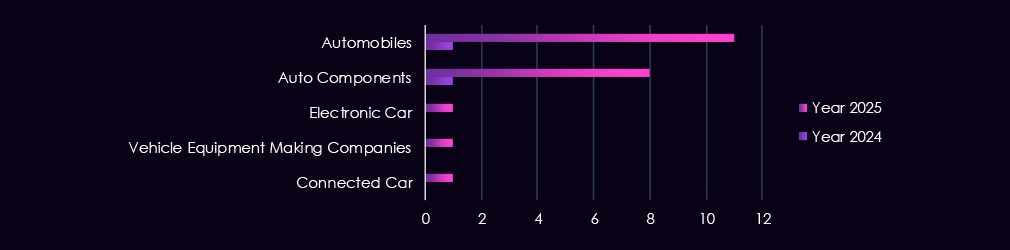
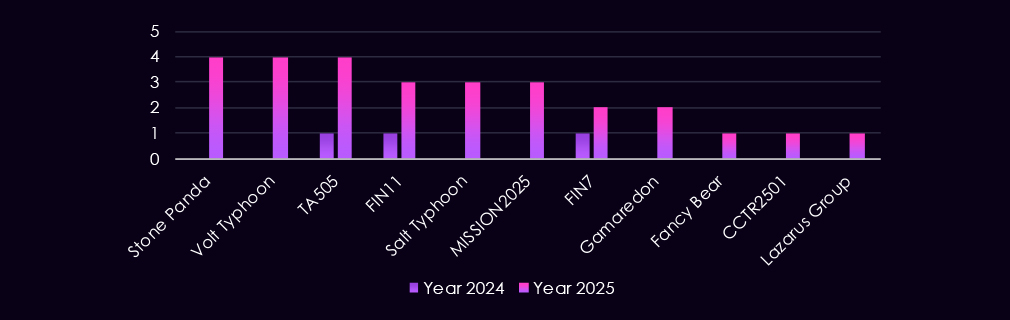
The automotive industry shows a clear expansion of threat actor activity in 2025, following a single detection in 2024. This single 2024 campaign exhibited overlapping TTPs across three Russian-linked cybercrime groups – TA505, FIN11, and FIN7. These overlaps are the result of using shared commodity tools, common loaders, and similar access-broker infrastructure, blurring attribution rather than collaboration.
In 2025, China-aligned groups such as Volt Typhoon, Salt Typhoon, Stone Panda, and MISSION2025 become prominent, signaling renewed interest in automotive, specifically EV and connected technology. Financially motivated actors (TA505, FIN11, FIN7) remain active in 2025, indicating continued ransomware. Additional activity from Gamaredon, Fancy Bear, Lazarus Group, and a newly tracked cluster (CCTR2501) highlights a diverse mix and nation-state interest in advancing smart technology in the industry.
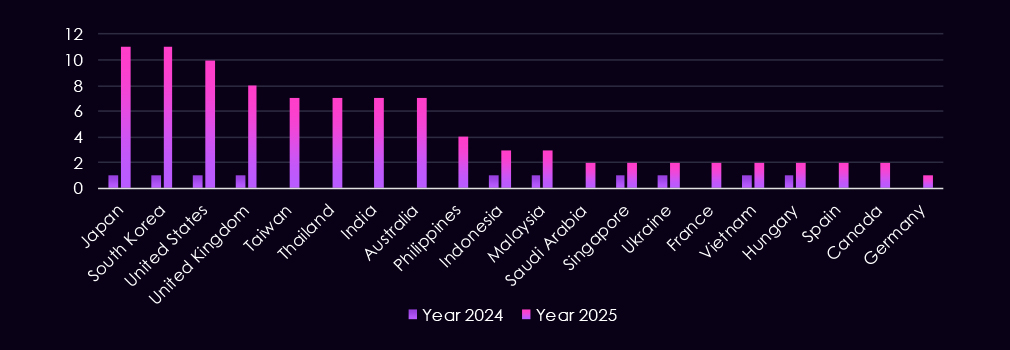
Observed victims are concentrated in countries with established automotive manufacturing bases, supply chains, or critical supplier ecosystems. In 2025, the most frequently affected countries include Japan, South Korea, the United States, the United Kingdom, and Taiwan. These countries host major vehicle manufacturers, Tier 1 and Tier 2 suppliers, semiconductor producers, and advanced R&D centers.
Further affected countries include Germany, France, Spain, Hungary, and Canada, all of which play key roles in vehicle manufacturing, assembly, or specialized component production. Consistent activity was also seen across Southeast and South Asia – including Thailand, India, Malaysia, Indonesia, Vietnam, and the Philippines.
This geographic spread indicates campaigns aligned to automotive supply chains rather than individual manufacturers.
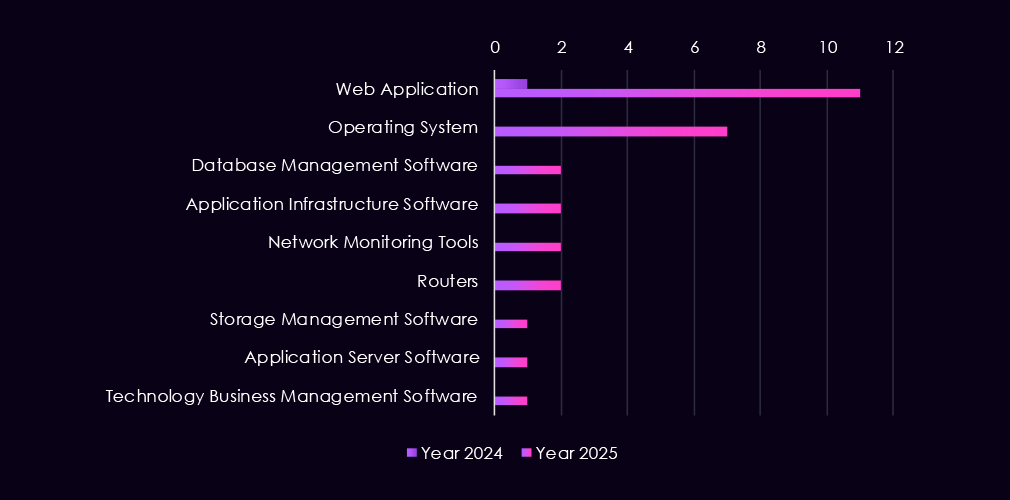
Attacks observed in automotive-focused APT campaigns primarily target core enterprise and manufacturing-adjacent technologies, with web applications serving as the main entry point in 2025. Their prominence reflects widespread use across supplier portals, manufacturing execution systems, and connected service platforms that bridge corporate IT and production environments.
Beyond initial access, 2025 activity shows deeper targeting of operating systems, indicating efforts to establish persistence and move laterally within automotive networks. Additional targeting of application servers, application infrastructure, and database management systems points to attempts to access proprietary designs, production data, and supplier information.
The presence of activity against routers and network monitoring tools suggests deliberate efforts to observe or control internal traffic flows.
Overall, the technology mix indicates that campaigns move from exposed web services into backend and management layers, consistent with reconnaissance and long-term access objectives within automotive environments.
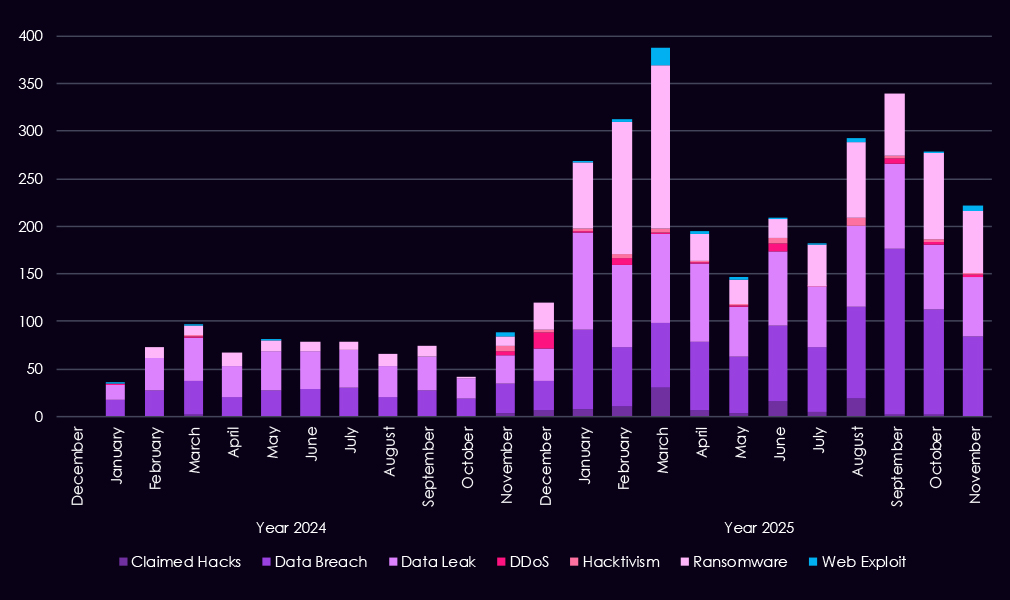
Over the past 23 months, CYFIRMA’s telemetry has identified 3,732 automotive industry-linked mentions. This is from a total of 2.5 million posts across various underground and dark web channels and forums.
The chart above shows total counts of industry-linked mentions for the automotive industry and individual categories of context for the mentions.
The chart below shows Year-over-Year growth for each category in this industry.
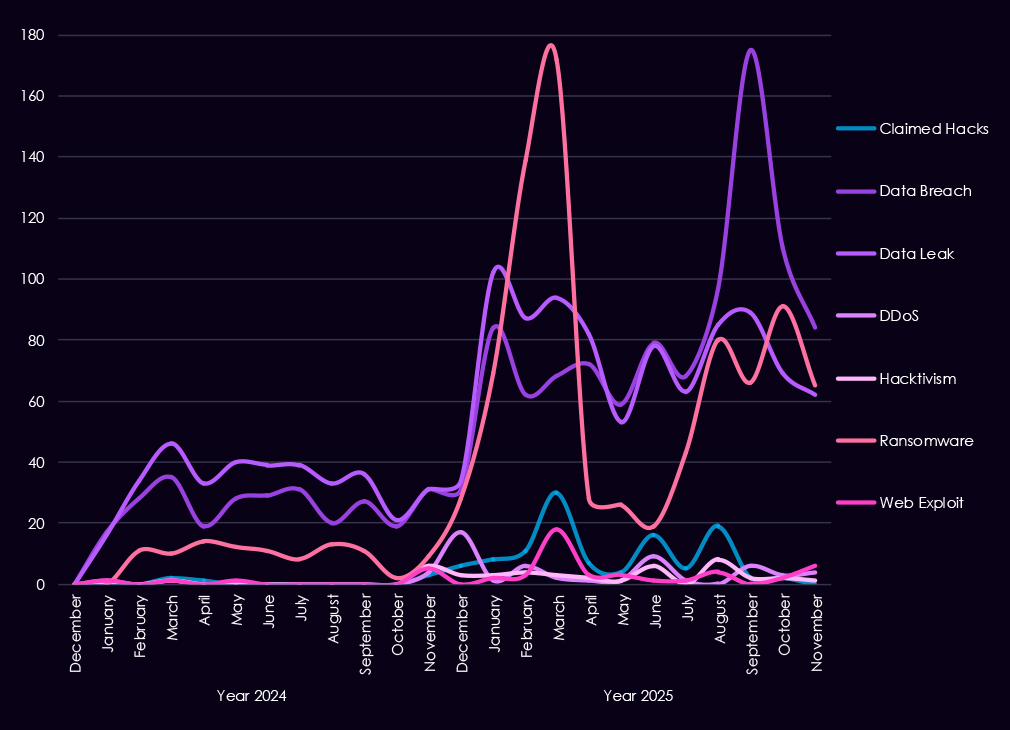
Underground and dark web chatter linked to the automotive sector increases sharply from late 2024 into 2025, signaling both higher attack activity and greater public exposure of incidents. Data breaches and data leaks dominate discussion, with volumes rising steadily through 2025, indicating ongoing exposure of sensitive manufacturing, supplier, and customer data rather than isolated events.
Ransomware-related chatter shows the strongest escalation, climbing rapidly in early 2025, dipping mid-year, and escalating again by the end of the year. This pattern aligns with recorded ransomware victims in the automotive industry and supplier networks, where operational disruption can carry a high financial impact. Mentions of claimed hacks and web exploits also rise in early 2025.
By contrast, DDoS and hacktivism remain low and episodic, appearing in short-lived spikes rather than sustained campaigns. Overall, the 2025 chatter profile reflects a shift toward persistent, monetization-driven activity centered on data theft and ransomware, consistent with both low-tier threat actors driving the majority of the chatter as well as more sophisticated ransomware.
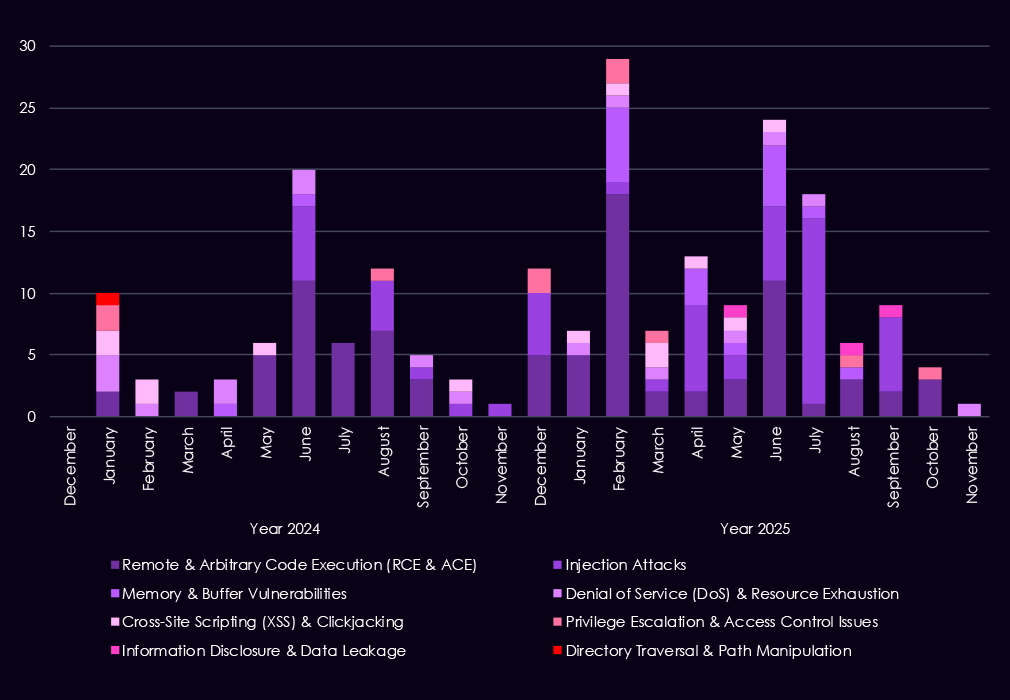
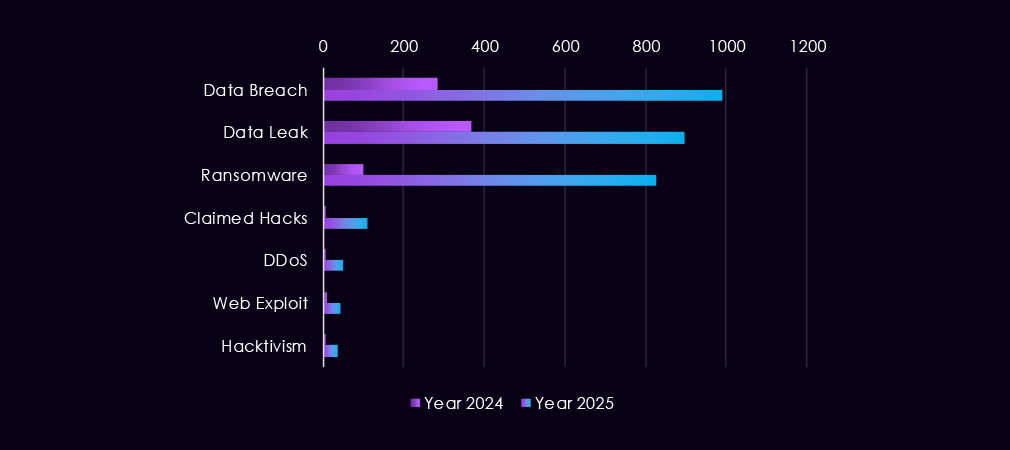
Over the past 23 months, CYFIRMA’s telemetry has identified 210 automotive industry-linked mentions. This is from over 90k CVEs reported and updated in the same time period.
The chart above shows total counts of industry-linked mentions for automotive technology and individual categories of reported vulnerabilities.
The chart below shows Year-over-Year growth for each category in this industry.
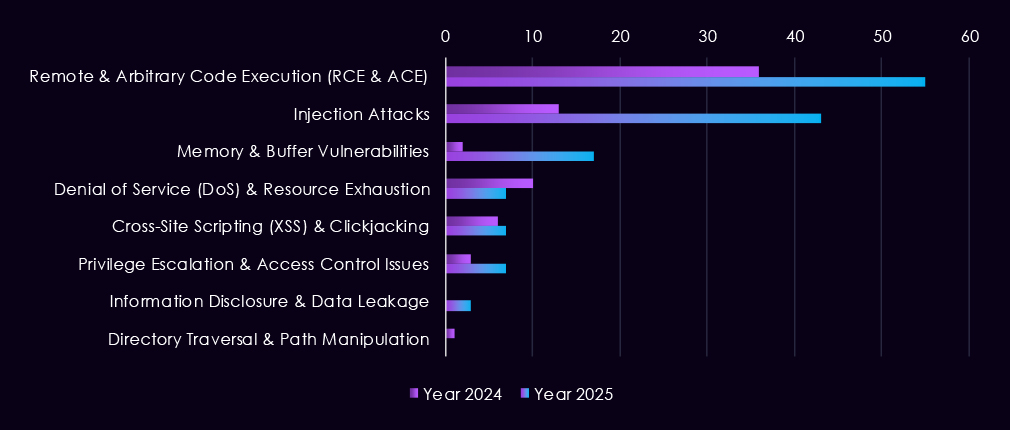
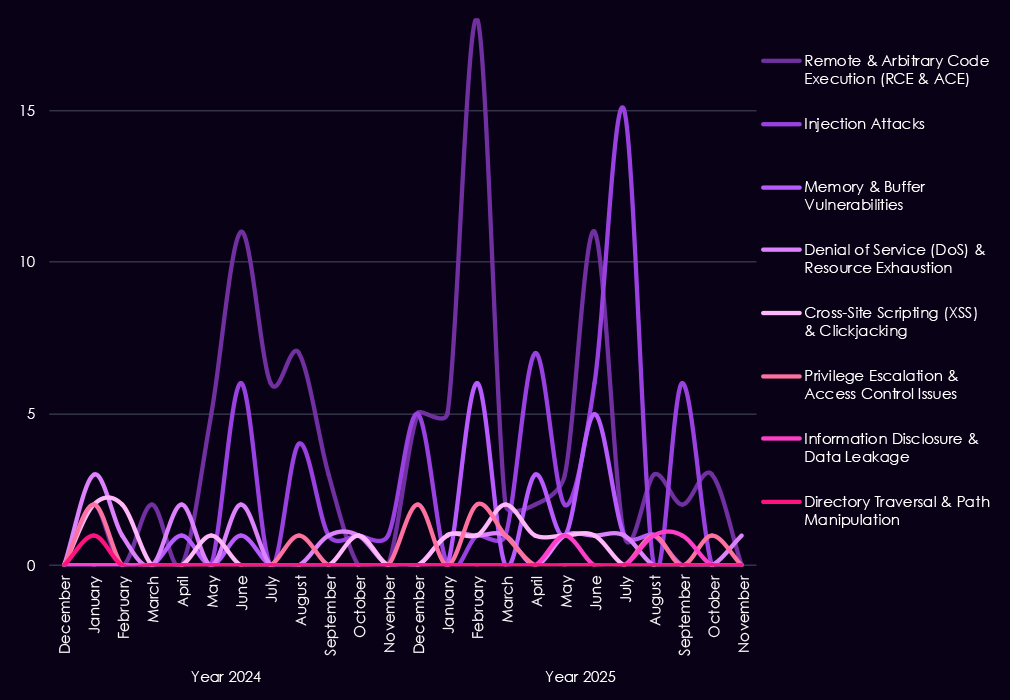
Reported CVEs linked to the automotive sector remain relatively low in volume but show a clear concentration on high-impact flaw types, particularly in 2025. Remote and arbitrary code execution (RCE/ACE) vulnerabilities are the most prominent category, with multiple spikes across the year, highlighting the continued risk of direct system compromise in automotive IT and connected production environments.
Injection attacks emerge more clearly in 2025, with several spikes, suggesting ongoing weaknesses in web-facing and backend systems used by manufacturers and suppliers. While less frequent, memory and buffer vulnerabilities appear intermittently, pointing to deeper technical flaws that could support post-exploitation or vulnerability chaining. Denial-of-service and XSS issues remain present at low levels, reflecting limited but persistent exposure to availability and client-side risks.
Overall, the CVE profile suggests that automotive-focused risk is driven less by volume and more by exploitability, with prominence of flaws that enable control or follow-on access into production, supply chain, and enterprise environments rather than low-impact misconfigurations or cosmetic issues.
In the past 12 months, CYFIRMA has identified 161 verified automotive industry ransomware victims. A major increase of 77% from 91 victims in the previous year and a substantial elevation of 45% from 111 victims in 2023.
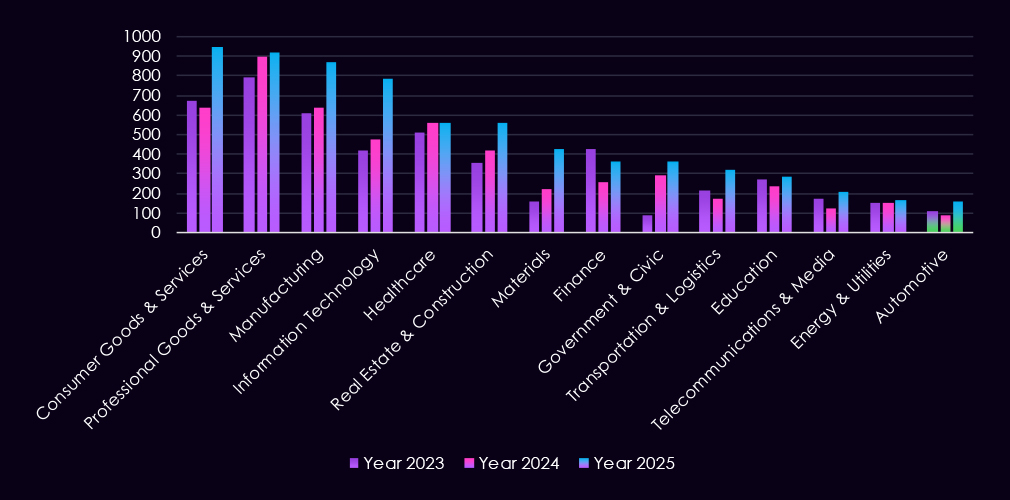
The automotive industry accounts for 2.32% of the overall total of 7,099 ransomware victims during the same period. That is an increase from 1.74% in the previous year, but near 2.22% in 2023 despite a lower victim count.
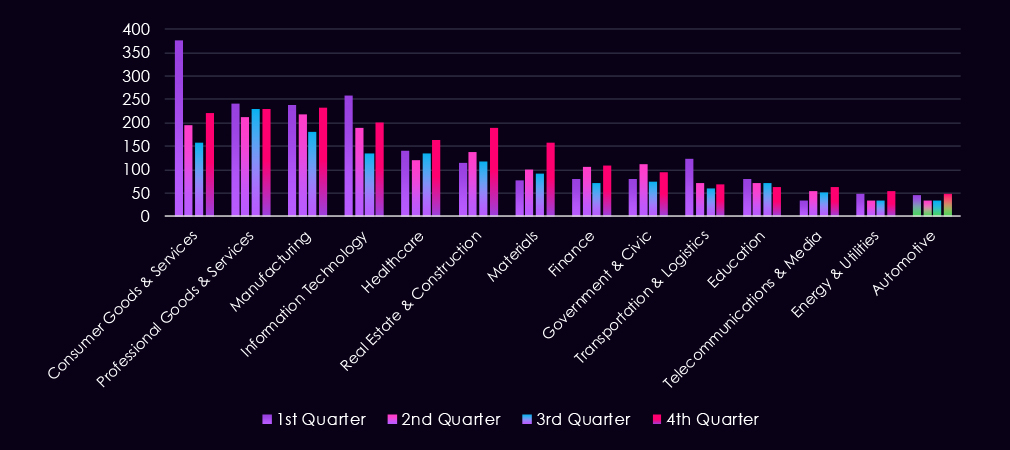
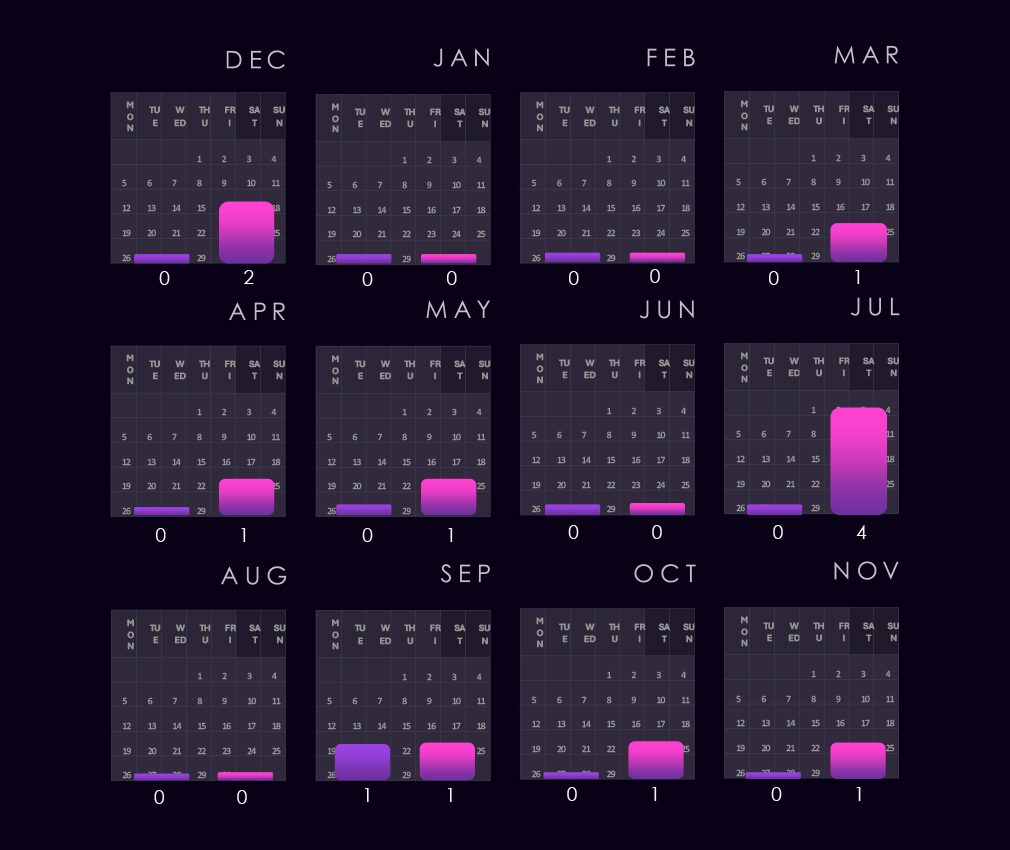
The bar chart above is focused only on 2025, and the victim counts per quarter are shown clearly and easily to see the trends. The automotive industry recorded a strong Q1, followed by lower victim counts up to Q4, where the number grew again.
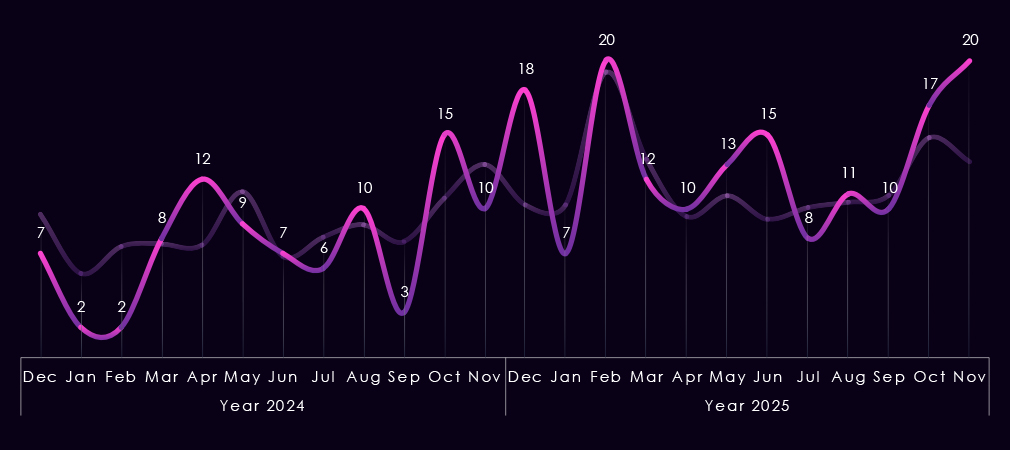
Monthly activity charted over scaled-down global all industries victims counts shows choppy yet roughly aligned with the global data trendline. This is due to the automotive industry having a relatively low total count. Still, January, February, and September 2024 dips, as well as the October spike, are notable.
December 2024 is counted into 2025, and we see the first major spike that is way above the global trendline. The next spike in February is aligned with the overall activity spike, and both June and November elevations are again above global trends.
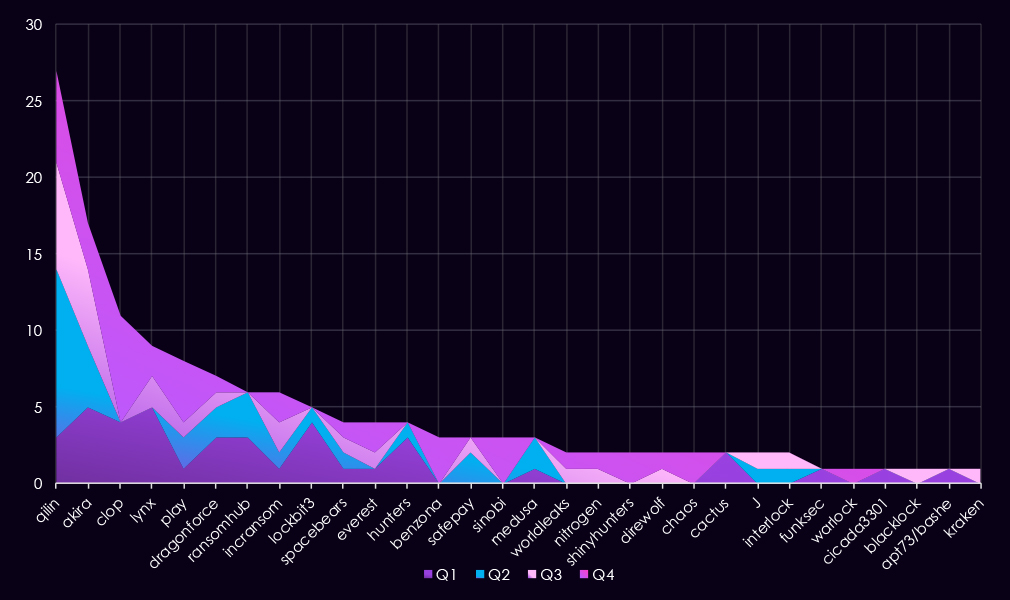
In total, 49 out of 124 gangs recorded victims in the automotive industry, a 40% participation.
Breakdown of quarterly top 30 gangs’ activity against the automotive sector in 2025 shows moderate and relatively stable pressure, with shifts in leading actors across the year but no sustained dominance by a single group.
Q1 activity was distributed across several gangs, with Akira (5) and Lynx (5) leading, followed by Clop (4) and LockBit3 (4). Overall volumes were low and spread across multiple actors, indicating opportunistic targeting rather than coordinated campaigns.
In Q2, activity increased slightly and became more concentrated. Qilin (11) emerged as the most active gang for the quarter, while Akira (4) and RansomHub (3) maintained a moderate presence. Several Q1-active groups, including Lynx and LockBit3, declined sharply.
Q3 activity remained relatively flat. Qilin (7) continued to lead, with Akira (5) and IncRansom (2) showing consistent engagement. The appearance of several one-off actors with single victims suggests continued opportunistic activity rather than sustained targeting.
By Q4, activity remained moderate but more fragmented. Clop (7) led the quarter, followed by Qilin (6) and Play (4). A number of low-volume gangs appeared exclusively in Q4, including Benzona, Sinobi, ShinyHunters, and Chaos, contributing to a longer tail of activity.
Overall, the automotive sector experienced steady but low-intensity ransomware activity throughout 2025. Activity shifted between leading gangs’ quarter to quarter, with no single gang consistently shaping the threat landscape, and late-year activity was characterized by short-lived or isolated campaigns.
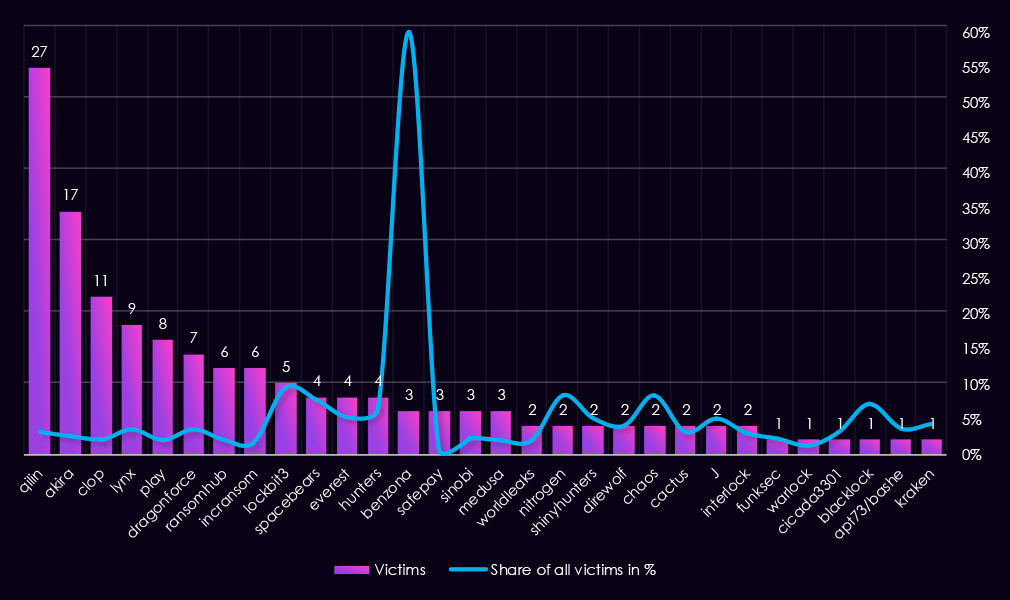
Reviewing the top 30 gangs counts alongside their share of victims highlights limited focused targeting of the automotive industry.
By absolute volume, Qilin (27) was the most active gang, but automotive represents only 3.2% of its total victims, indicating broad targeting rather than sector focus. Akira (17 victims, 2.5%), Clop (11 victims, 2.1%), and Play (8 victims, 2.0%) show similar patterns, with automotive accounting for a small share of overall activity.
Only a small number of gangs show high proportional exposure (>10%), and these are almost entirely driven by very low total victim counts. Benzona is the most extreme outlier, with 60.0% of its victims in automotive, but only 5 total victims, making this figure highly skewed.
Several gangs fall into a moderate focus range (5–10%), including SpaceBears (7.8%), Hunters (6.6%), Everest (5.3%), ShinyHunters (5.1%), and BlackLock (7.1%).
The majority of gangs show a low automotive focus (<5%), indicating that automotive was a secondary or opportunistic target for most ransomware actors in 2025.
Overall, automotive does not appear to be a prioritized sector for most gangs. However, it is important to note that automotive is but a small slice of a much larger manufacturing pie, which is among the most attacked industries.
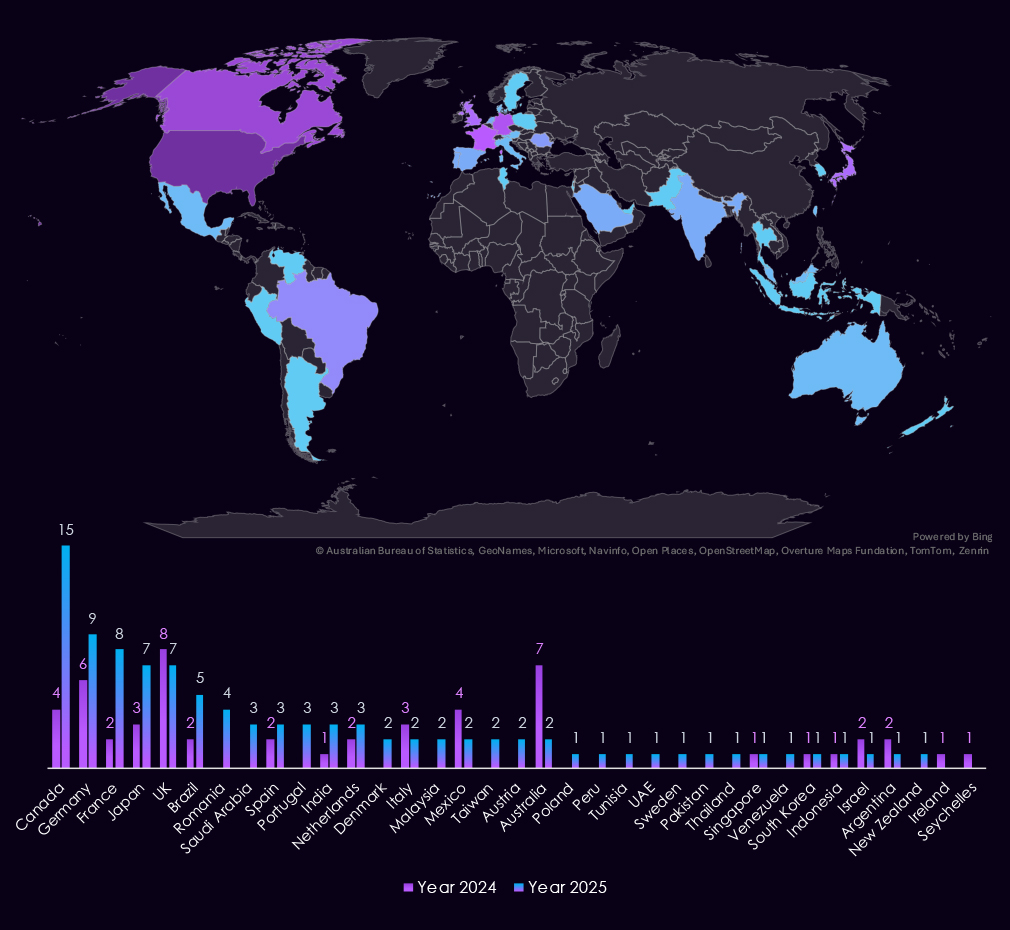
The USA accounts for 39% of ransomware, with 63 victims in the automotive industry in 2025. This is nearly double the 38 victims in the previous year.
Canada, Germany, France, Japan, Romania, Saudi Arabia, and Portugal recorded the highest elevations. Most countries recorded more or new victims as ransomware activity grew globally in this industry.
Australia and Mexico are notable exceptions with major declines.
A total of 34 countries reported victims, which is another significant increase from 20 in 2024.
Year-over-Year Risk Elevation: High

In 2025, the automotive sector experienced a sharp year-over-year increase in APT exposure, with victims observed in 28% of tracked campaigns, up from a single campaign in 2024. This shift reflects a material change in threat posture, driven by renewed nation-state interest alongside persistent financially motivated activity. Campaigns increasingly aligned with connected vehicles, EV ecosystems, and automotive supply chains, with targeting spread across manufacturers, suppliers, and supporting technology providers.
Attack activity continued to originate primarily from web applications, reflecting exposure across supplier portals, manufacturing systems, and connected service platforms. Compared to 2024, 2025 showed deeper progression into backend environments, including operating systems, application infrastructure, databases, and network components. This pattern indicates movement beyond initial access toward persistence, lateral movement, and access to proprietary production and supply chain data.
Underground and dark web chatter rose notably from late 2024 into 2025, dominated by data breaches, data leaks, and ransomware-related discussions. Ransomware chatter showed repeated escalation across the year, aligning with increased victimization across manufacturers and suppliers where operational disruption carries a high financial impact. In contrast, DDoS and hacktivism remained low and episodic, suggesting monetization rather than disruption as the primary driver.
Ransomware victimization increased 77% year over year, confirming automotive as a fast-growing ransomware target. Activity was elevated, but still low-intensity, with shifting leading actors and limited evidence of sustained sector specialization. Geographic exposure widened significantly in 2025, with more countries affected and the United States accounting for the largest share of victims, underscoring automotive’s growing exposure as a globally distributed, technology-driven industry entering 2026.
Over the past year, the manufacturing industry has been targeted by 23 out of the 43 Advanced Persistent Threat (APT) campaigns observed, with a presence in 53% of observed campaigns. This is a significant increase of 43% from the 16 campaigns observed in 2024.
The victims of these campaigns have spanned various segments within the industry, as illustrated below:
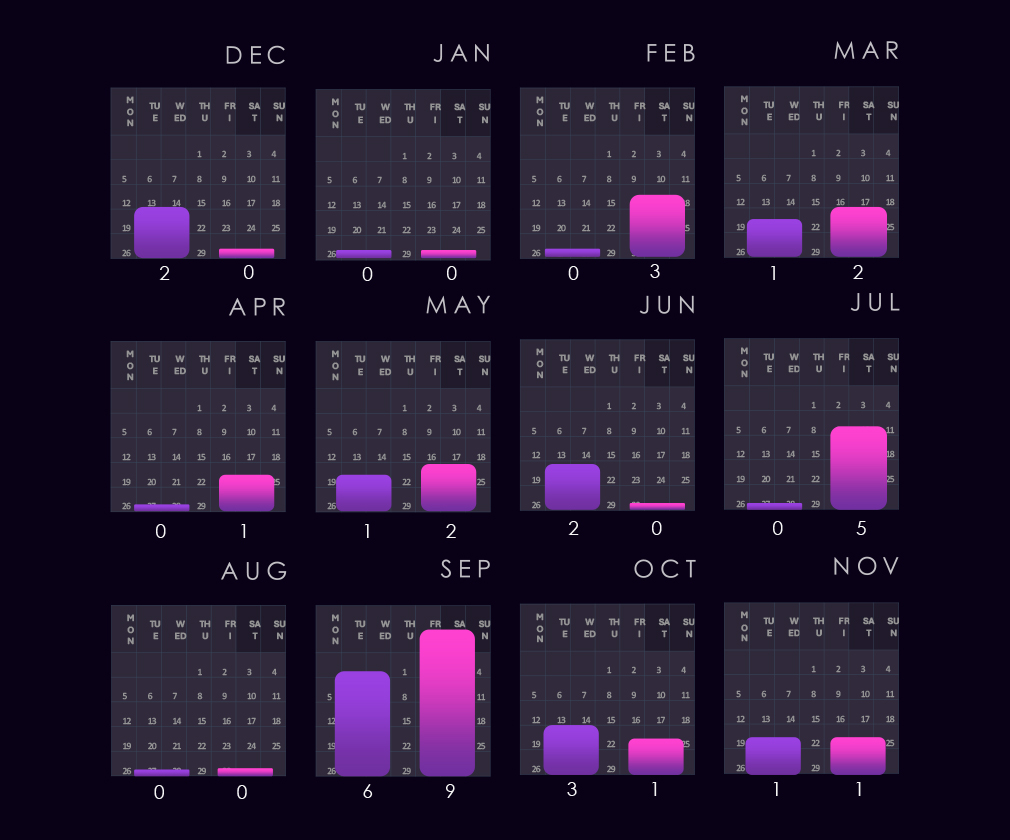
We observed a mix of nation-state and financially motivated threat actors. In 2025, activity was led by China-aligned groups such as Volt Typhoon, Salt Typhoon, Stone Panda, MISSION2025, Mustang Panda, Emissary Panda, and APT27, indicating sustained interest in manufacturing operations, proprietary processes, and supplier relationships.
Russia- and Iran-linked actors, including Turla Group, Fancy Bear, Gamaredon, Fox Kitten, and APT34, continue to appear. Lazarus Group remains consistently active.
Financially motivated groups such as TA505 and FIN7 are also present, reflecting ongoing ransomware and access monetization risk. The growing presence of newly tracked CC- and NS-prefixed clusters (for example, CCVN2501, CCTH2501, CCES2501, NSEN2401) in 2025 highlights increasingly diverse threat actors.
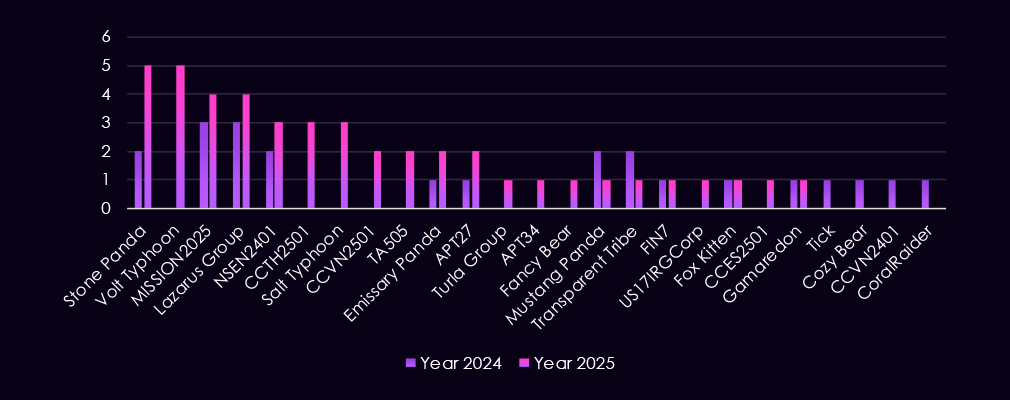
APT campaigns are concentrated in major industrial economies and global production hubs. In 2025, the most frequently affected countries include Japan, the United States, South Korea, Taiwan, the United Kingdom, and Australia. These countries host large-scale manufacturing operations, advanced R&D, and critical suppliers, making them consistent targets.
Sustained victimization is also observed across South and Southeast Asia, including Thailand, India, Vietnam, the Philippines, Indonesia, and Singapore, regional manufacturing hubs and supplier ecosystems. Additional activity across Europe and the Middle East – including Germany, France, Spain, Saudi Arabia, the United Arab Emirates, and Qatar – points to globally distributed targeting aligned with production capacity, energy inputs, and logistics connectivity, rather than focus on a narrow set of manufacturers.
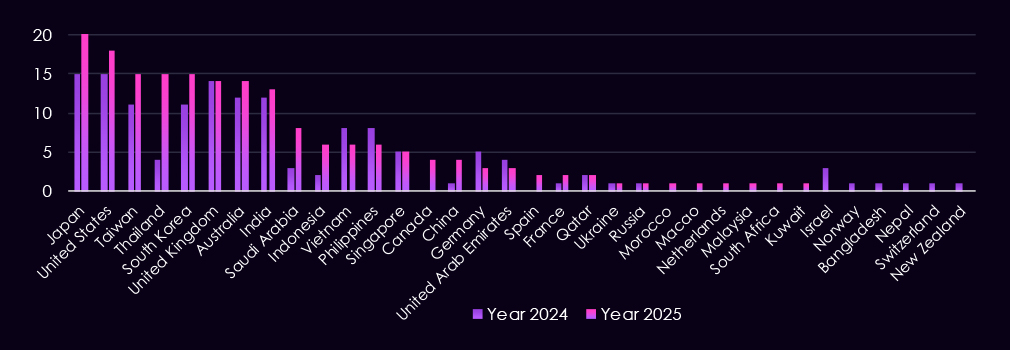
Attacks observed in manufacturing APT campaigns continue to focus on exposed enterprise technologies, with web applications clearly dominating as the primary entry point in both 2024 and 2025. Their prominence reflects widespread use across supplier portals, production management systems, and externally exposed business applications that bridge corporate IT and industrial operations.
In 2025, targeting expanded beyond initial access into operating systems and core backend platforms, indicating greater emphasis on persistence and lateral movement once access is obtained. Activity against application servers, application infrastructure, and database management systems suggests attempts to reach sensitive production data, intellectual property, and supplier information. More limited but notable targeting of VPNs, routers, RDP, and SMTP services for initial access. Network monitoring tools point to espionage motivation and traffic interception.
Overall, the technology mix indicates campaigns that move from perimeter-facing services into trusted internal systems, aligning with objectives focused on long-term access, operational insight, and downstream impact across manufacturing.
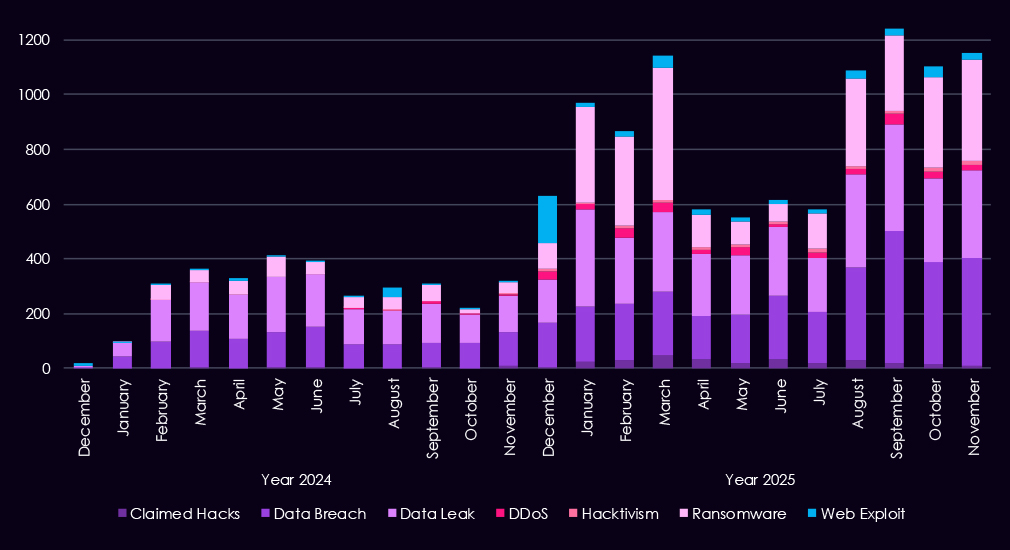
Over the past 23 months, CYFIRMA’s telemetry has identified 13,846 manufacturing industry-linked mentions. This is from a total of 2.5 million posts across various underground and dark web channels and forums.
The chart above shows the total counts of industry-linked mentions for the manufacturing industry and individual categories of context for the mentions.
The chart below shows Year-over-Year growth for each category in this industry.
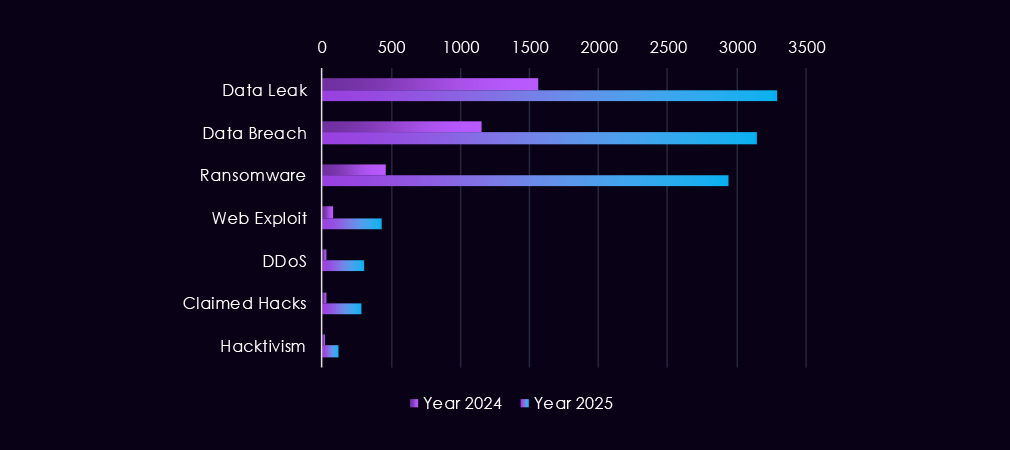
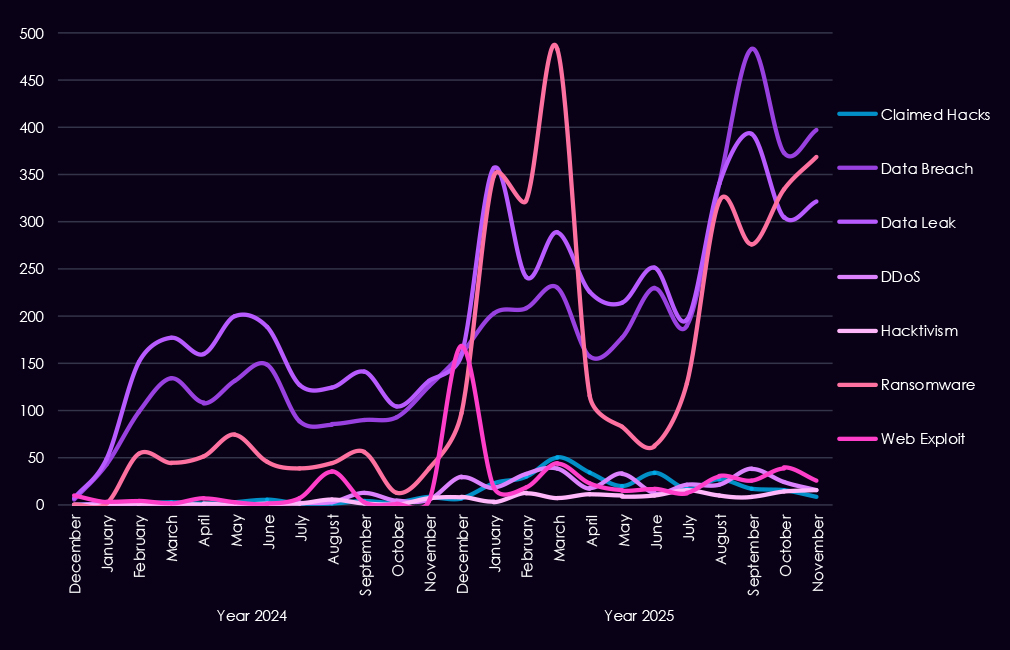
Underground and dark web chatter linked to the manufacturing sector increased sharply from late 2024 into 2025, pointing to higher activity and greater public exposure of incidents. Data breach and data leak discussions dominate, with volumes rising steadily through 2025, indicating continued exposure of sensitive production data, intellectual property, and supplier information rather than isolated disclosures.
Ransomware-related chatter shows the strongest growth, surging in early 2025, retracting in mid-year, and jumping again by the end of the year. This pattern reflects sustained extortion pressure against manufacturers, where operational disruption and downtime can carry significant financial and downstream supply chain impact. Mentions of claimed hacks and web exploits also increase, suggesting vulnerabilities and exploits chatter among threat actors linked to advertising access or successful compromise.
By contrast, DDoS and hacktivism remain lower in overall volume but show periodic spikes, typically tied to short-lived campaigns rather than sustained operations.
Overall, the 2025 chatter profile points to persistent, monetization-driven activity centered on data theft and ransomware, consistent with organized for-profit threat behavior targeting manufacturing environments.
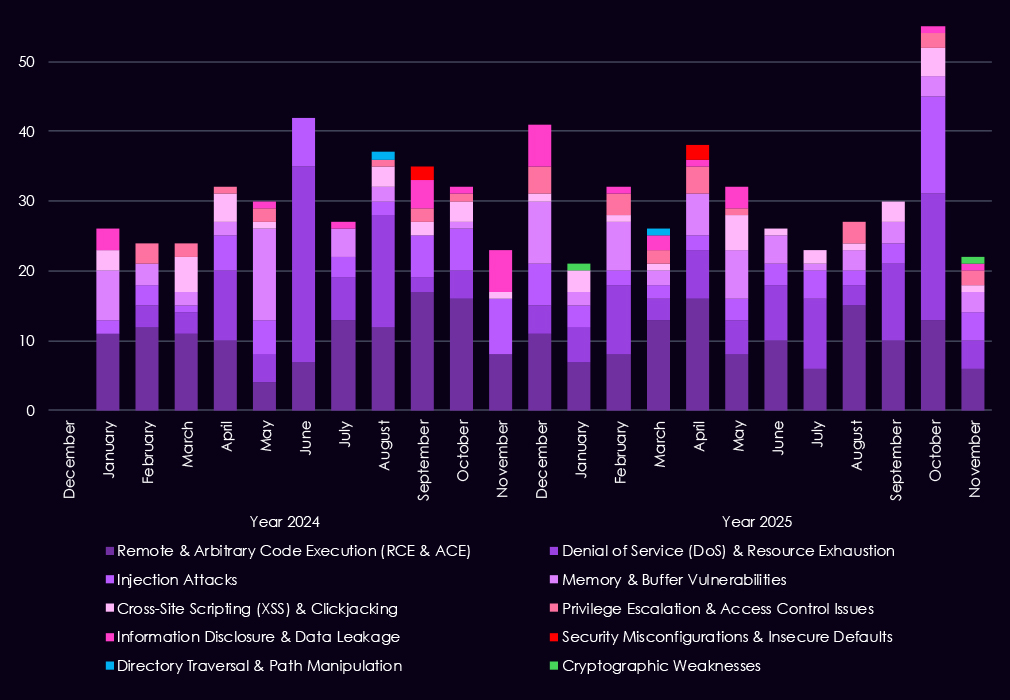
Over the past 23 months, CYFIRMA’s telemetry has identified 707 manufacturing industry-linked mentions. This is from over 90k CVEs reported and updated in the same time period.
The chart above shows total counts of industry-linked mentions for manufacturing technology and individual categories of reported vulnerabilities.
The chart below shows Year-over-Year growth for each category in this industry.
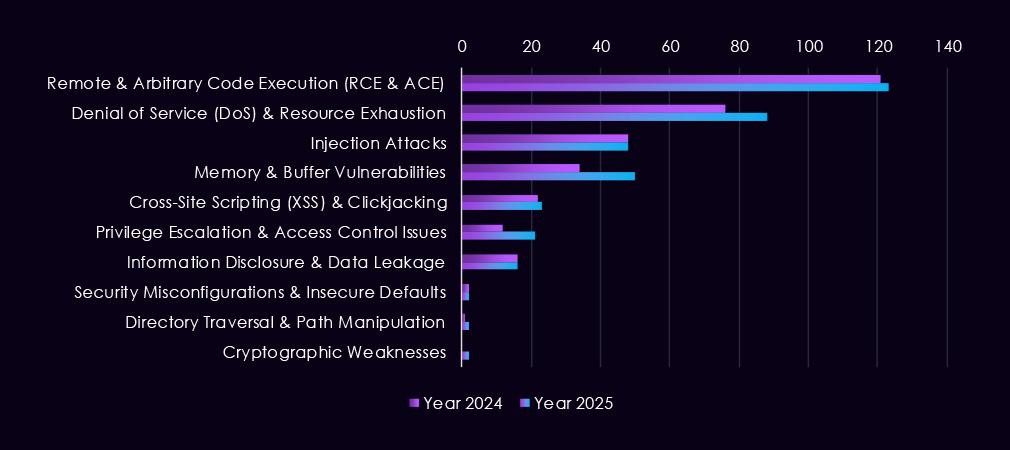
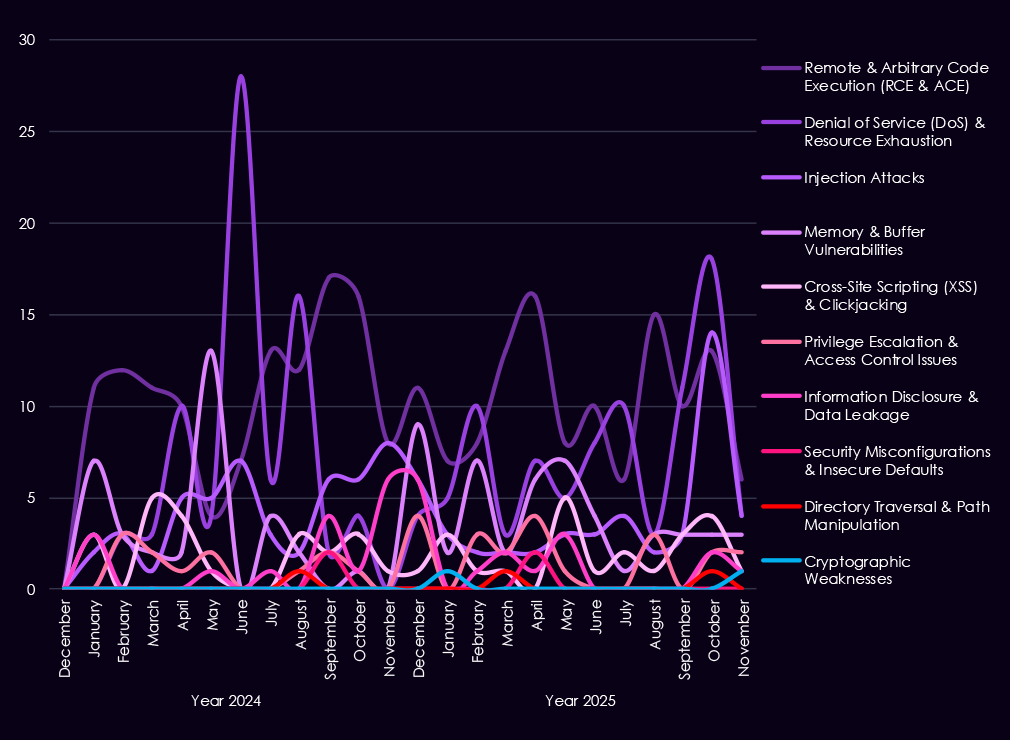
Reported CVEs affecting the manufacturing industry and technology show a strong and sustained concentration on high-impact vulnerability classes, with 2025 marking a clear increase in volume and consistency across most categories. Remote and arbitrary code execution (RCE/ACE) vulnerabilities dominate, appearing persistently throughout the year and accounting for the largest share of reported issues. This highlights the ongoing risk of direct system compromise across manufacturing IT and industrial-adjacent environments.
Denial-of-service and injection vulnerabilities also remain prominent, reflecting continued exposure of internet-facing services and the operational sensitivity of manufacturing systems to availability and input validation flaws. Memory and buffer vulnerabilities appear regularly, indicating attention to deeper technical weaknesses that can allow post-compromise activity and vulnerability chaining. While lower in volume, privilege escalation and information disclosure issues continue to surface, reinforcing the risk of attackers moving laterally once inside a network.
Lower-frequency categories such as XSS, directory traversal, and security misconfigurations persist but remain secondary compared to exploit-ready flaws.
Overall, the 2025 CVE profile for manufacturing reflects broad, sustained exposure to vulnerabilities that can enable control, disruption, and follow-on exploitation, aligning with the sector’s attractiveness for both espionage and financially motivated campaigns.
In the past 12 months, CYFIRMA has identified 868 verified manufacturing industry ransomware victims, a 36% increase from 637 victims in the previous year, which recorded a sustained level of activity from 611 victims during 2023.
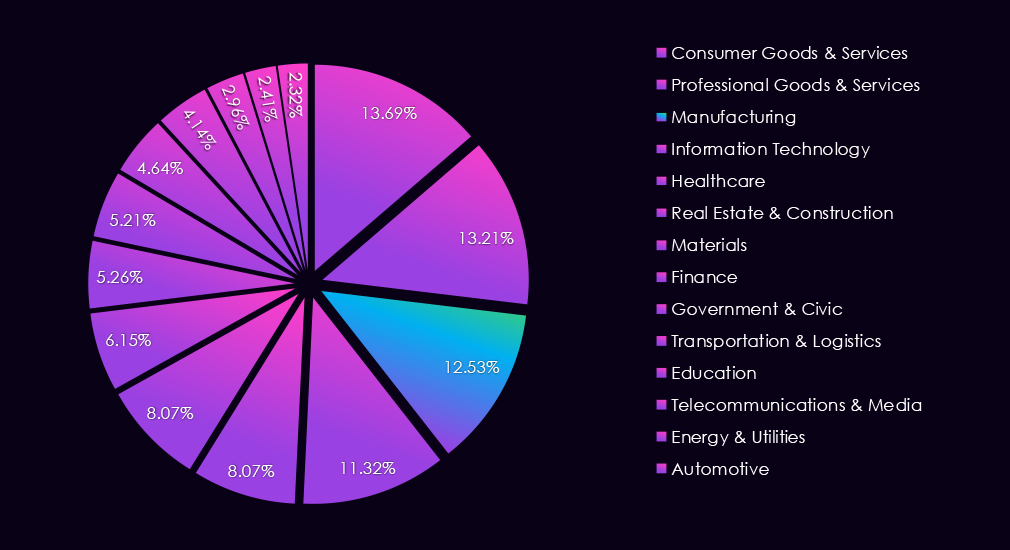
Manufacturing industry accounts for 12.53% of the overall total of 7,099 ransomware victims during the same period. That is just mildly higher and remarkably consistent with previous years of 2024 and 2023, during which both recorded a share of exactly 12.20%.
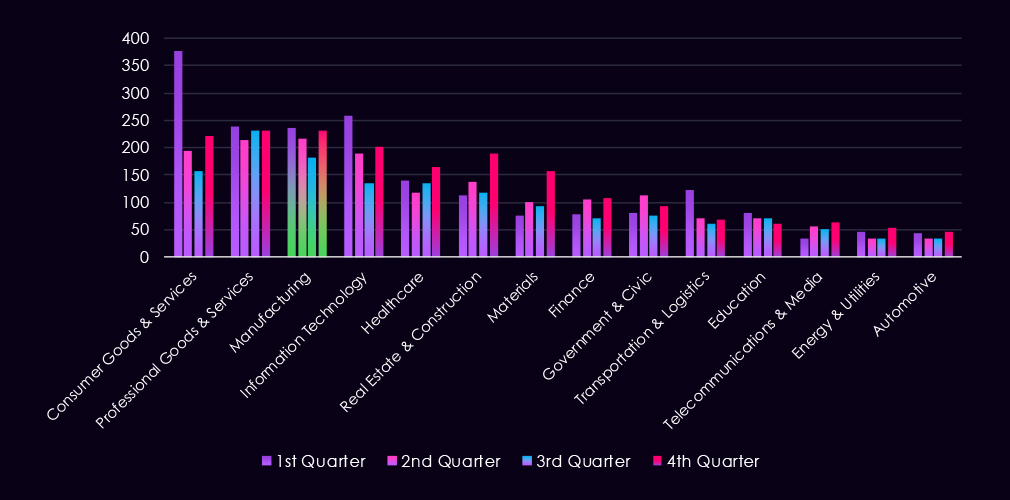
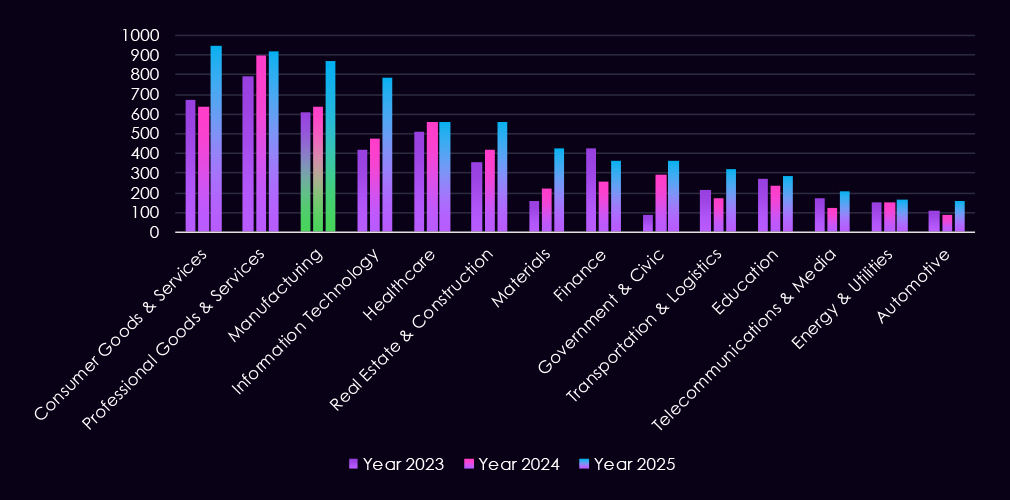
The bar chart above is focused only on 2025, and the victim counts per quarter are shown clearly and easily to see the trends. The manufacturing industry saw declining numbers from Q1 to Q3, followed by a jump to the Q1 level during Q4.
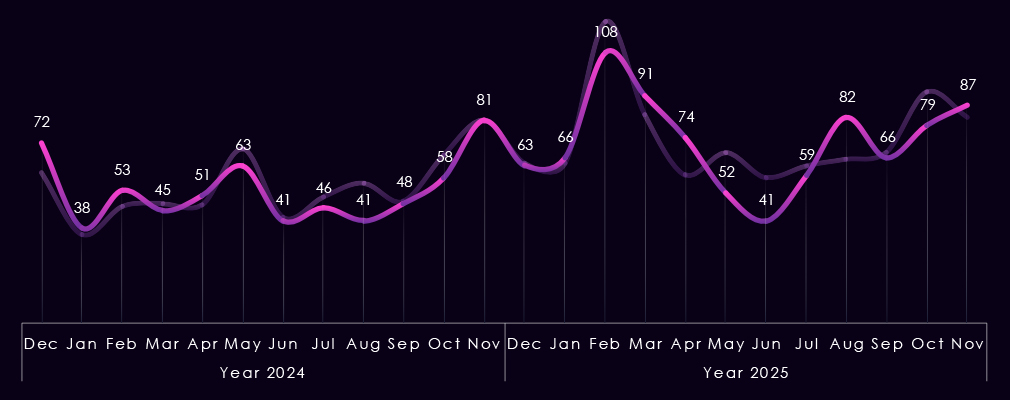
The monthly activity charted over the scaled-down global all industries victims trendline, reflecting the fact that manufacturing represents a high share of all victims. Naturally, it follows the global trendline very closely.
In 2024, the only notable divergence is the August dip. In 2025, we can see a slightly lower February spike, but a less sharp taper towards a more pronounced dip during June. August recorded a spike above the global trendline and a milder, but continued growth towards the end of the year.
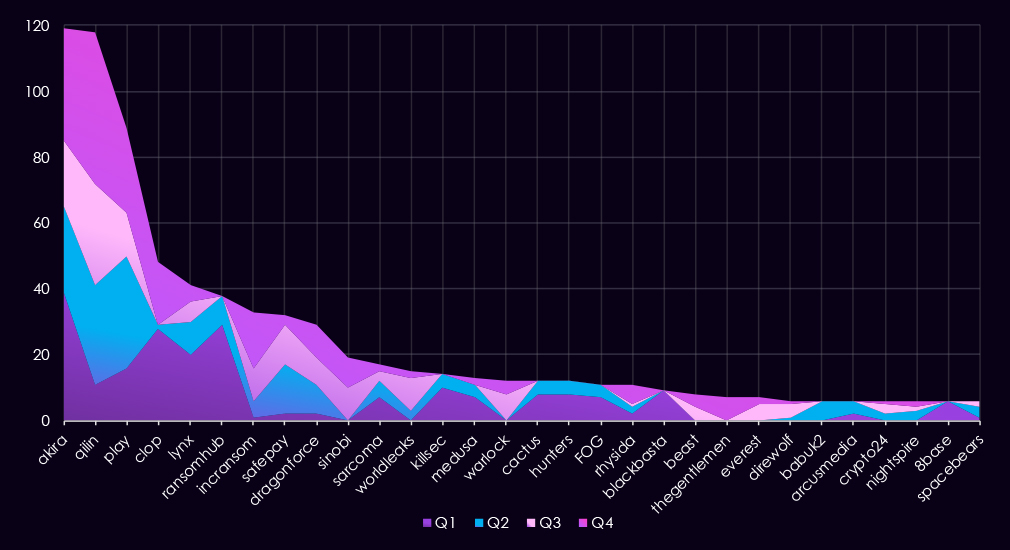
In total, 88 out of 124 gangs recorded victims in the manufacturing industry during 2025, representing 71% participation.
A review of quarterly top 30 ransomware gang activity against the manufacturing sector in 2025 shows sustained targeting throughout the year, driven by several consistently active gangs and pronounced surges in the second half.
Q1 activity was led by Akira (39), RansomHub (29), and Clop (28), with Lynx (20) and Play (16) also recording high volumes. The distribution indicates broad targeting by multiple highly active gangs rather than reliance on a single dominant group.
In Q2, overall activity remained elevated but shifted in gangs. Play (34) and Qilin (30) emerged as the most active gangs, while Akira (26) maintained a strong presence. Several Q1-dominant groups, including RansomHub and Clop, declined sharply, indicating short-lived campaigns rather than sustained activity.
Q3 activity stayed high but became more concentrated. Qilin (31) led the quarter, followed by Akira (20) and Play (13). A number of groups, including Sinobi (10) and WorldLeaks (10), appeared or increased activity, contributing to a broader mid-year threat landscape.
By Q4, activity intensified further. Qilin (46) recorded the highest quarterly volume of the year, while Akira (34) and Play (26) remained highly active. Several gangs, including IncRansom (17), DragonForce (10), and TheGentlemen (7), also increased late-year activity, adding to overall pressure on the sector.
Overall, manufacturing experienced mildly varied, but overall high ransomware activity across all quarters in 2025. Top spot rotated among a small group of dominant gangs, with Akira emerging as the most persistent and highest-volume threat by year-end, with Qilin very close second. A long tail of secondary actors contributed a scattered but notable volume of activity.
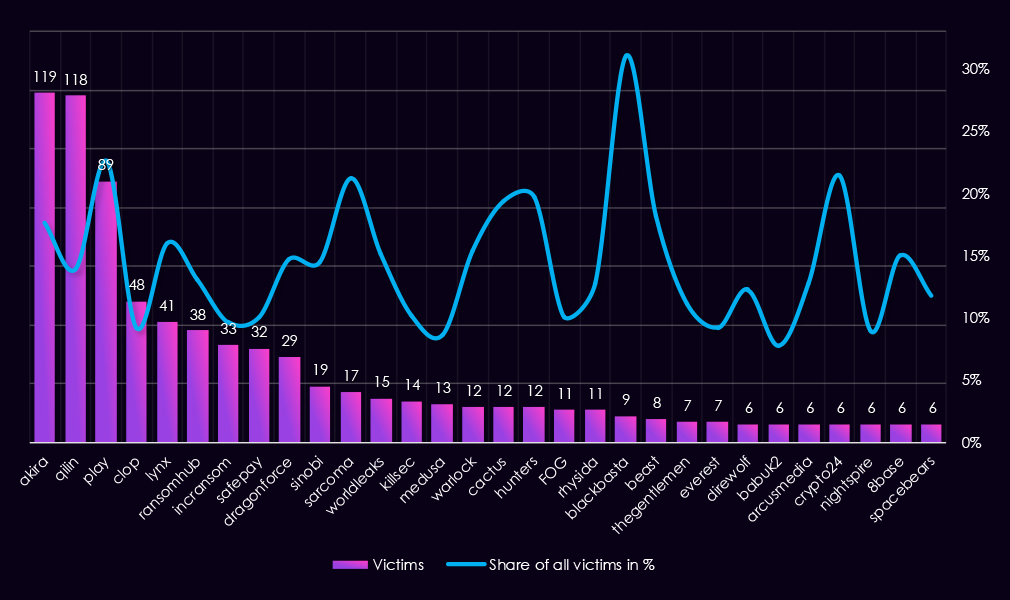
Reviewing 2025 manufacturing victim counts alongside each top 30 gang’s share of total victims highlights both sustained high-volume activity and a relatively large number of actors with meaningful proportional exposure.
By victim count, Akira (119) and Qilin (118) were the most active gangs, followed by Play (89) and Clop (48). For these high-volume actors, manufacturing represents a meaningful and relatively high focus, ranging from 13.9% (Qilin) to a very high 22.6% (Play), indicating sustained engagement with the sector alongside broader targeting.
A large portion of gangs show a relatively high manufacturing concentration (>10%). This includes not only high-volume actors such as Akira (17.7%), Play (22.6%), Lynx (16.0%), RansomHub (13.1%), and DragonForce (14.7%), but also mid- and lower-volume groups such as Sarcoma (21.3%), WorldLeaks (15.2%), Warlock (15.4%), Cactus (19.4%), and Hunters (19.7%). This pattern suggests manufacturing was a consistently targeted sector across a wide range of actors.
Several outliers show very high proportional exposure, driven by smaller overall victim pools. BlackBasta (31.0%), Crypto24 (21.4%), and Beast (18.2%) all show elevated shares, but their absolute manufacturing victim counts remain limited, meaning these percentages are more sensitive to small changes in activity.
Only a small number of gangs fall into a low focus range (<5%), indicating that manufacturing was rarely incidental. Even groups with modest victim counts often show manufacturing accounting for a notable share of their overall activity.
Overall, manufacturing stands out as a sector with broad and sustained ransomware interest. High victim volumes align more closely with high proportional exposure than in other sectors, suggesting manufacturing was not only heavily targeted in absolute terms but also a focused target for many ransomware gangs in 2025.
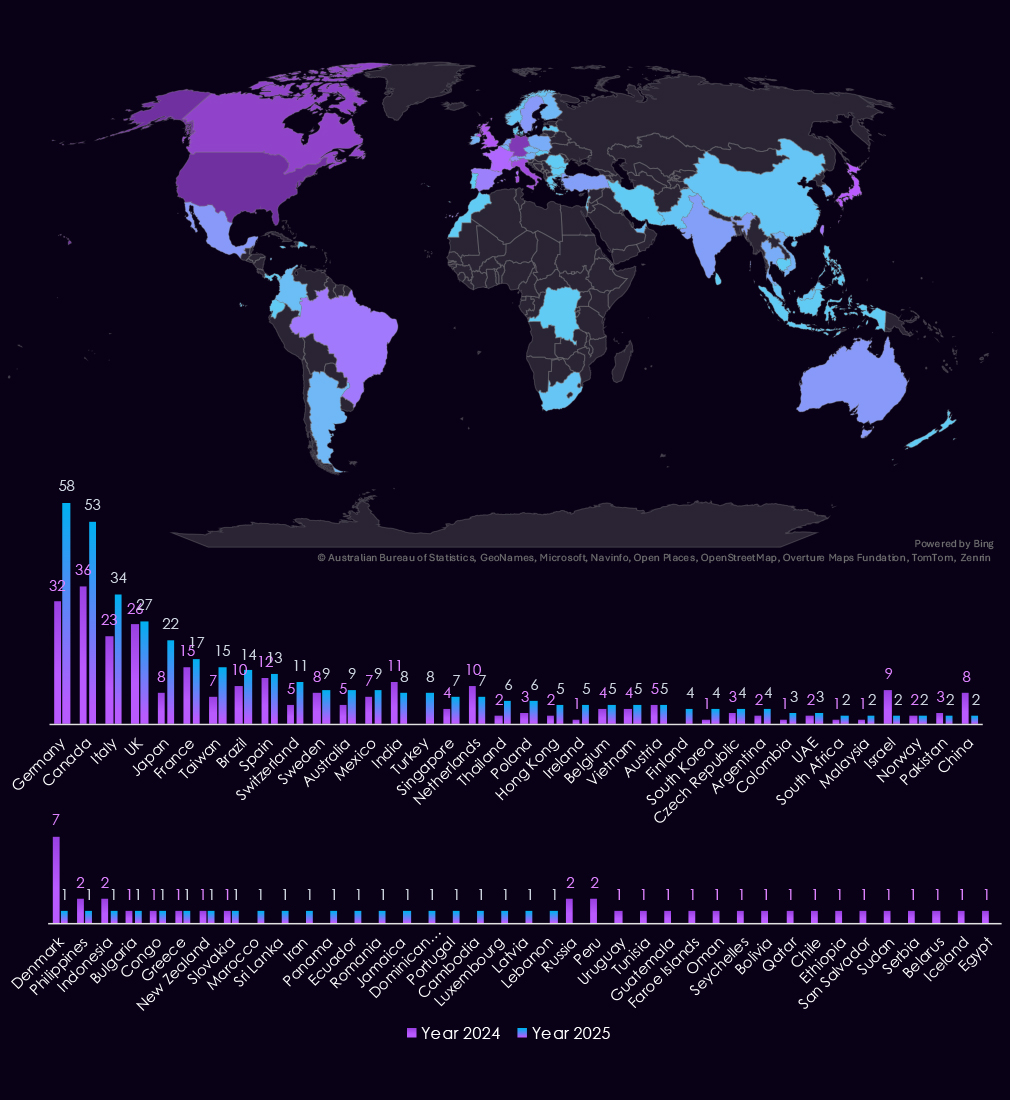
The USA recorded a staggering 453 manufacturing victims and accounted for 52% of ransomware victims in 2025. This is nearly 40% increase from 326 in 2024.
Germany, Canada, Italy, Japan, Taiwan, and Turkey are among the countries with the highest year-over-year elevations. Switzerland, Singapore, and Finland also deserve a mention.
Israel, China, and Denmark, on the other hand, are countries with the largest declines.
A total of 58 countries reported victims, which is three fewer than 61 in 2024. That is remarkably even; however, as shown on the bar charts above, many countries are targeted opportunistically, recording one or two victims only in one of the two years.
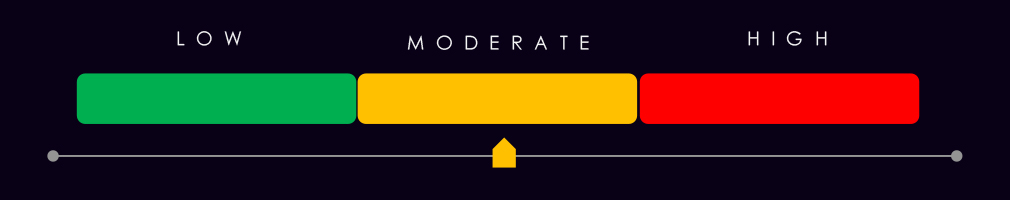
Year-over-Year Risk Elevation: Moderate
In 2025, the manufacturing sector experienced a substantial year-over-year escalation in APT exposure, with victims observed in 53% of tracked campaigns, up sharply from 37% in 2024. Activity reflected a broad mix of nation-state and financially motivated actors, with a particularly strong presence from state-aligned groups focused on manufacturing operations, proprietary processes, and supplier ecosystems. Geographic targeting remained concentrated in major industrial economies but was globally distributed, aligning with production capacity, supply chains, and logistics connectivity rather than individual manufacturers.
Attack activity continued to originate primarily from web applications, reflecting widespread exposure across supplier portals, production management systems, and externally facing business platforms. Compared to 2024, 2025 showed deeper penetration into backend and core systems, including operating systems, application infrastructure, databases, and selected network services. This progression indicates increased emphasis on persistence, lateral movement, and access to sensitive production data and intellectual property once initial access is achieved.
Underground and dark web chatter increased sharply from late 2024 into 2025, dominated by data breaches, data leaks, and ransomware-related discussions. Ransomware chatter showed repeated escalation across the year, consistent with sustained extortion pressure against manufacturers where downtime and supply chain disruption carry significant financial impact. Mentions of claimed hacks and web exploits also increased, while DDoS and hacktivism remained lower-volume and episodic.
Ransomware victimization rose 36% year over year, with manufacturing maintaining a stable and consistently high share of global ransomware victims. Activity was sustained across all quarters, driven by a wide set of actors rather than a single dominant group, and many gangs showed meaningful proportional focus on manufacturing compared to other sectors. The United States accounted for over half of all manufacturing ransomware victims, while geographic exposure remained broad, reinforcing manufacturing as one of the most persistently and strategically targeted sectors entering 2026.
Over the past 12 months, the materials industry recorded victims across 12 of the 43 Advanced Persistent Threat (APT) campaigns observed – a presence in 28% of observed campaigns. It is also a major increase from only 2 campaigns in the previous year.
These victims were observed across multiple segments within the industry, as shown below:
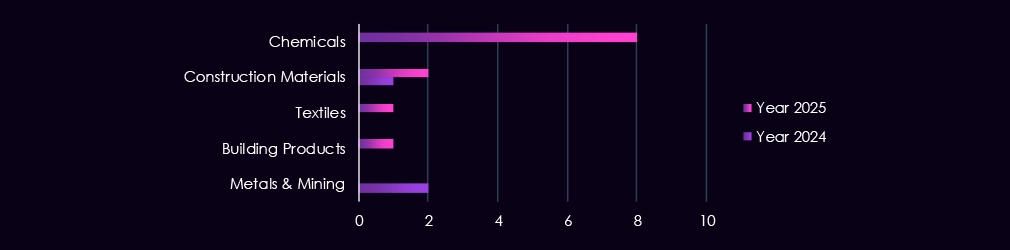
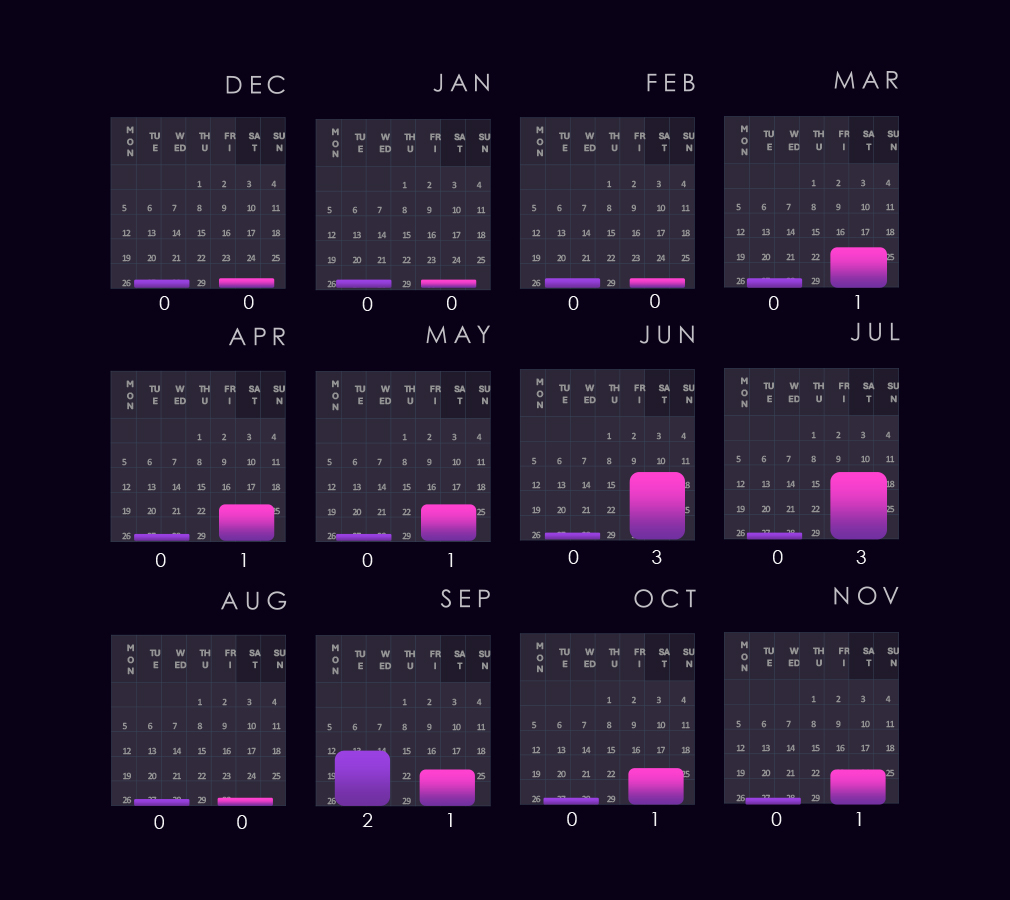
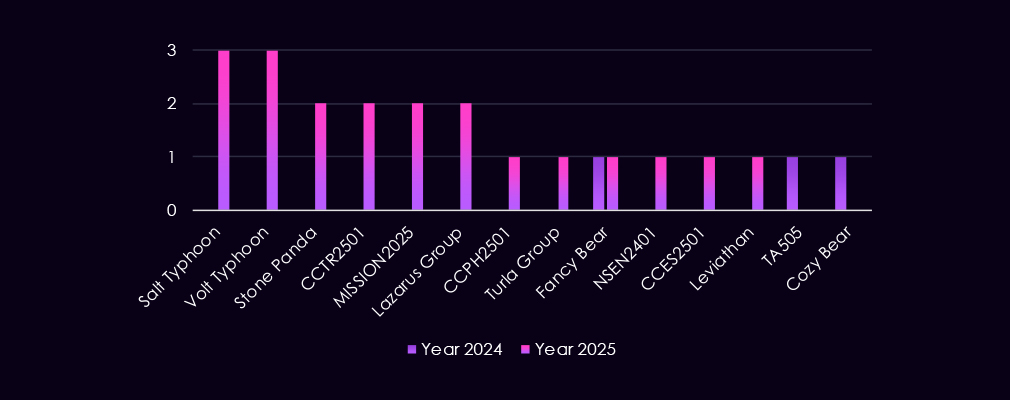
The materials industry recorded increased diversity and activity in 2025. In the 2024 data set, only two campaigns were identified. One campaign displayed overlapping TTPs associated with TA505 and Fancy Bear. The second campaign was attributed to Cozy Bear, consistent with focused espionage activity.
In 2025, China-aligned actors such as Volt Typhoon, Salt Typhoon, Stone Panda, and MISSION2025 featured prominently, indicating sustained interest in materials production, extraction technologies, and upstream supply chains. Lazarus Group also appears, reflecting continued dual-use targeting tied to both strategic and financial objectives.
Additional activity from Turla Group and the presence of newly tracked clusters such as CCTR2501, CCPH2501, CCES2501, and NSEN2401 point to a growing number of persistent threat actors. Overall, materials-focused campaigns reflect a mix of state-linked espionage and opportunistic cybercrime.
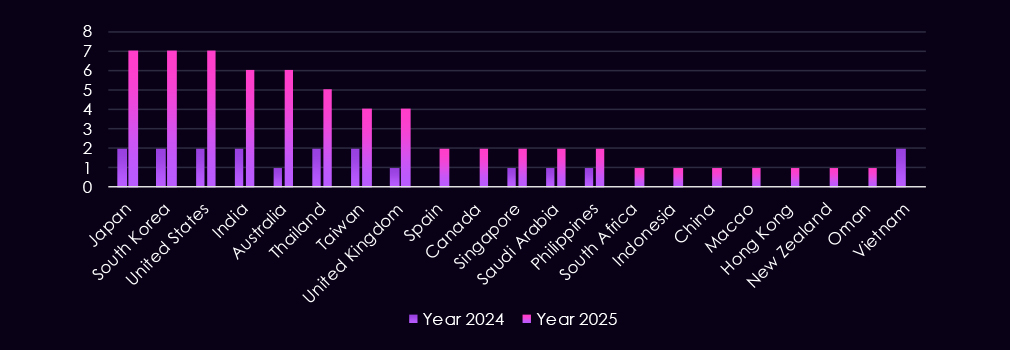
Observed victims are concentrated in countries with known strong mining, metals, chemicals, and upstream industrial supply chains. In 2025, the most targets include Japan, South Korea, the US, Australia, and India, alongside sustained activity in Taiwan and the UK. These locations host major extraction operations, advanced materials processing, and globally integrated suppliers.
Furthermore, in Southeast Asia and the Middle East – including Thailand, the Philippines, Singapore, Saudi Arabia, and Oman –targeting is aligned with resource extraction, processing hubs, and export corridors. Smaller numbers of cases in Europe and other regions (for example, Spain, Canada, South Africa) show a pattern suggesting a focus on supply chains.
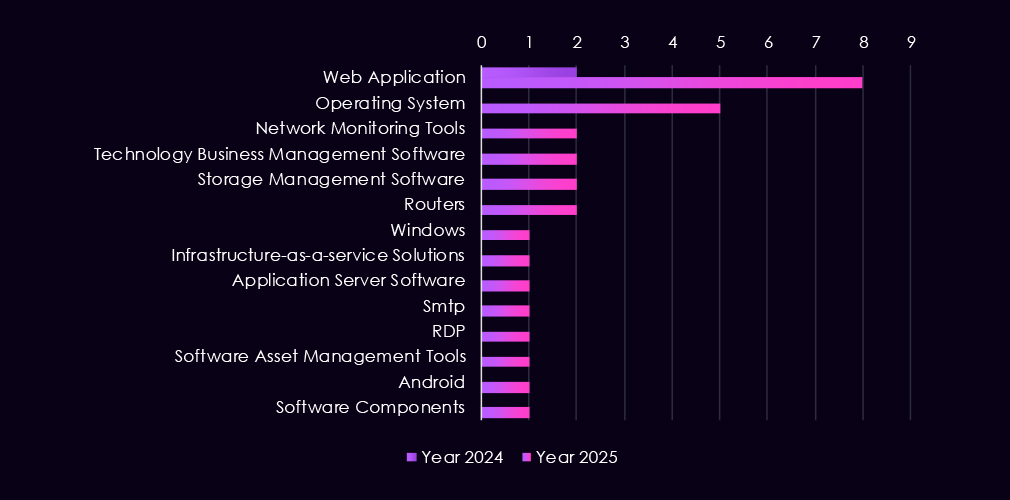
Attacks observed in materials-sector APT campaigns primarily target exposed enterprise technologies, with web applications serving as the main entry point in 2025. This reflects their widespread use across supplier portals, procurement platforms, and operational systems that connect extraction, processing, and distribution environments.
Beyond initial access, operating systems are a frequent secondary target, indicating efforts to establish persistence and move laterally within materials organizations. Activity against storage management platforms, technology business management (TBM) software, application servers, and infrastructure-as-a-service environments suggests attempts to access sensitive operational data, production metrics, or proprietary processes. More limited targeting of remote access technologies (RDP) and SMTP services is linked to initial access. Routers and network monitoring tools point to network sniffing and espionage.
Overall, the technology mix reflects campaigns that move from externally exposed systems into trusted internal platforms, consistent with reconnaissance and longer-term access objectives in the materials sector.
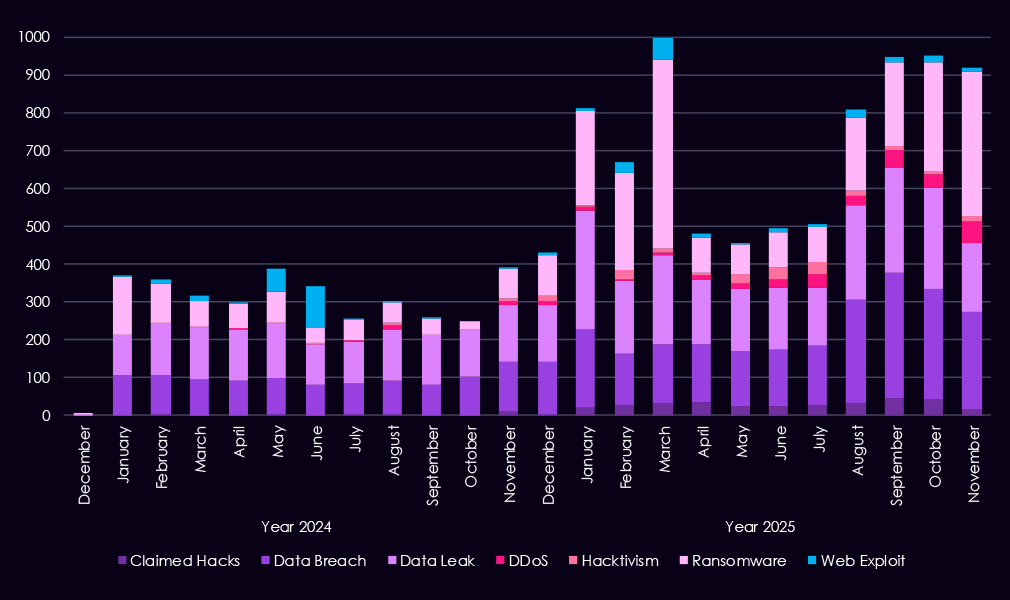
Over the past 23 months, CYFIRMA’s telemetry has identified 11,993 materials industry-linked mentions. This is from a total of 2.5 million posts across various underground and dark web channels and forums.
The chart above shows the total counts of industry-linked mentions for the materials industry and individual categories of context for the mentions.
The chart below shows Year-over-Year growth for each category in this industry.
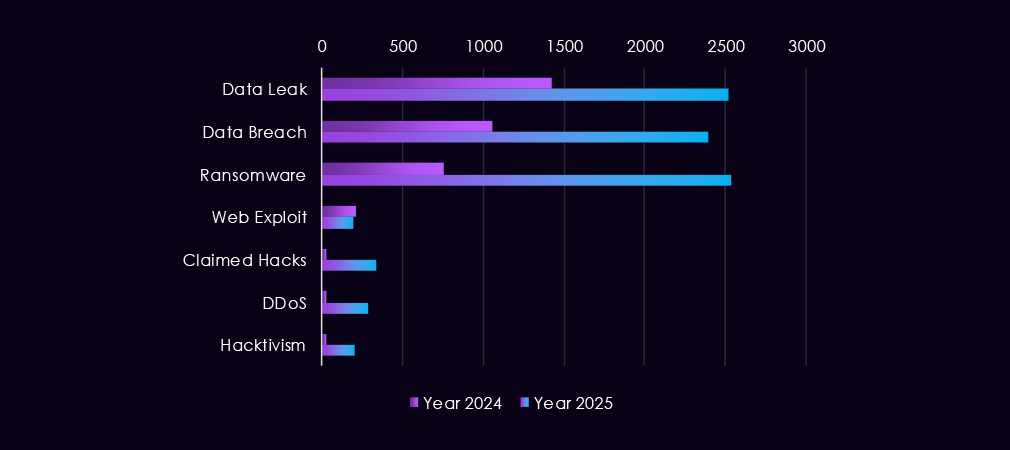
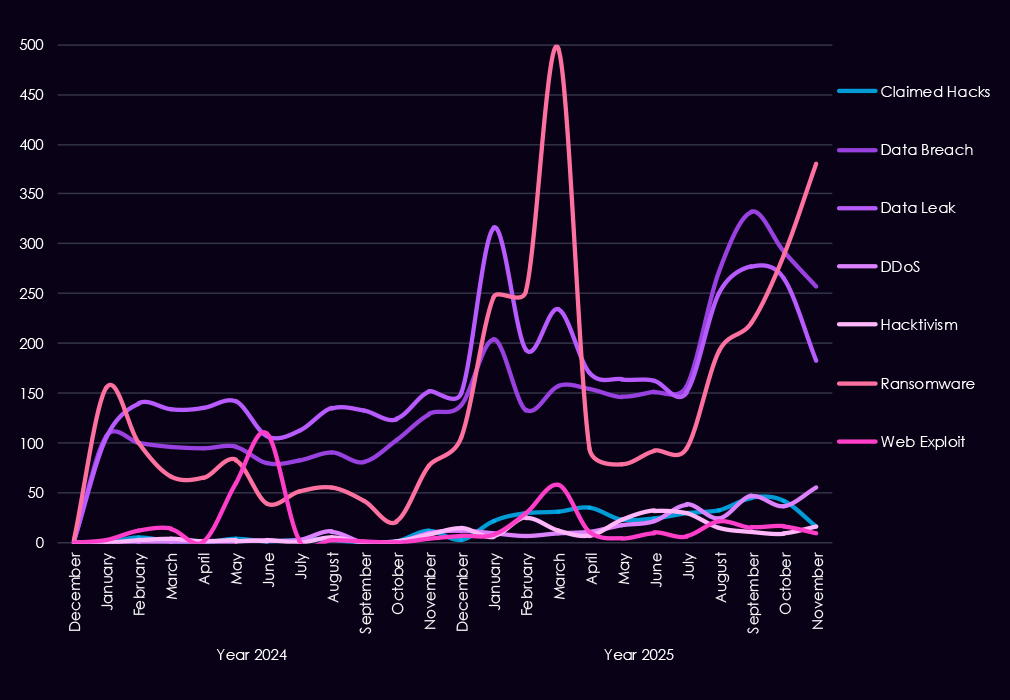
Underground and dark web chatter linked to the materials sector increases notably from late 2024 into 2025, indicating higher threat activity and growing chatter underground publishing of incidents. Data breaches and data leaks dominate discussions, with consistently high volumes throughout 2025, pointing to sustained exposure of sensitive operational data, supplier information, and proprietary materials-related processes.
Ransomware chatter shows the clearest escalation, rising sharply in early 2025 and peaking again toward the end of the year. This pattern reflects continued extortion targeting materials organizations, where production downtime and supply disruption can have outsized financial and downstream impact. Mentions of claimed hacks also increase steadily, suggesting greater willingness by actors to publicly advertise or claim successful compromises.
DDoS and hacktivism activity also becomes more visible in 2025, showing sharper and more frequent spikes than in 2024, though still secondary to data theft and ransomware narratives. Web exploit discussions remain present but uneven, appearing in short bursts linked to exploit discoveries.
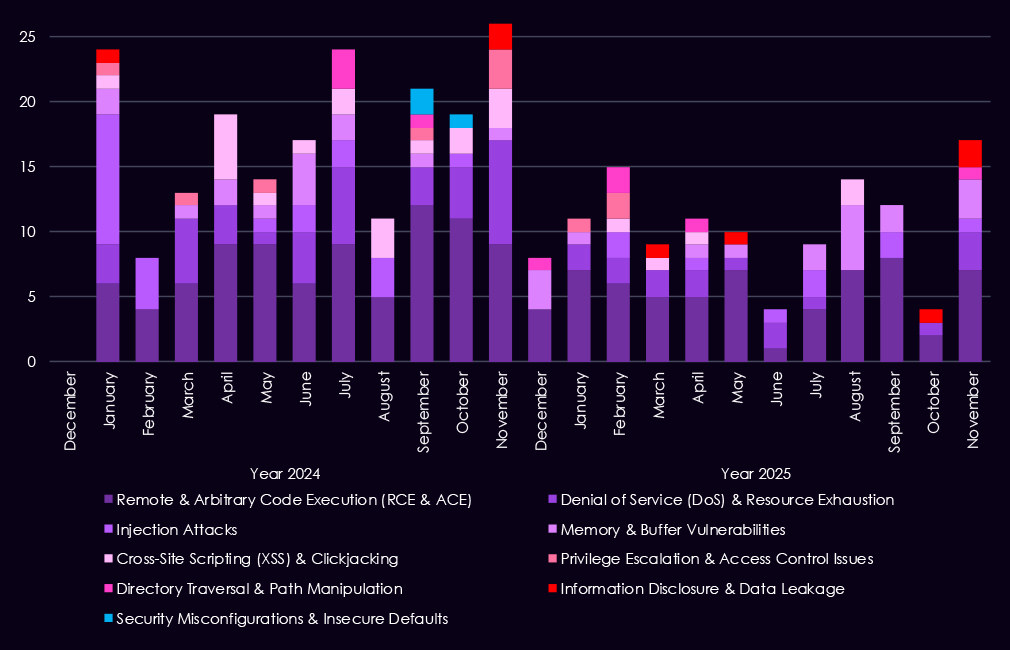
Over the past 23 months, CYFIRMA’s telemetry has identified 320 materials industry-linked mentions. This is from over 90k CVEs reported and updated in the same time period.
The chart above shows total counts of industry-linked mentions for materials technology and individual categories of reported vulnerabilities.
The chart below shows Year-over-Year growth for each category in this industry.
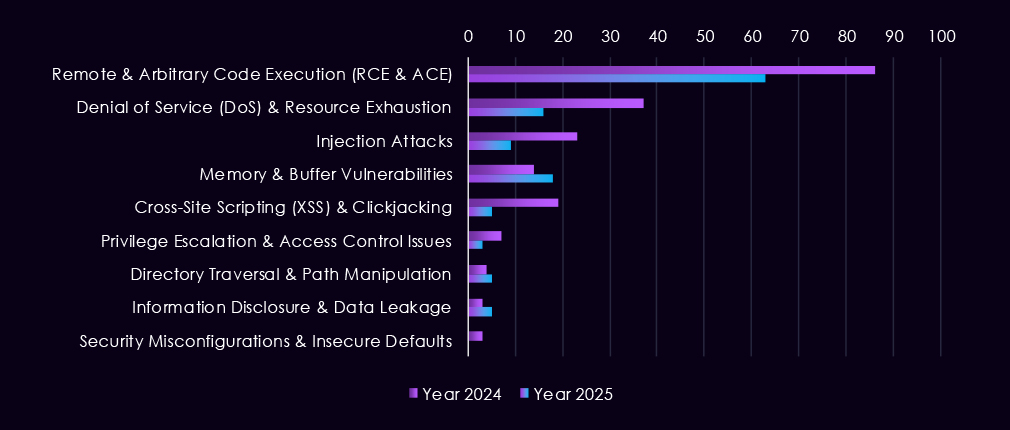
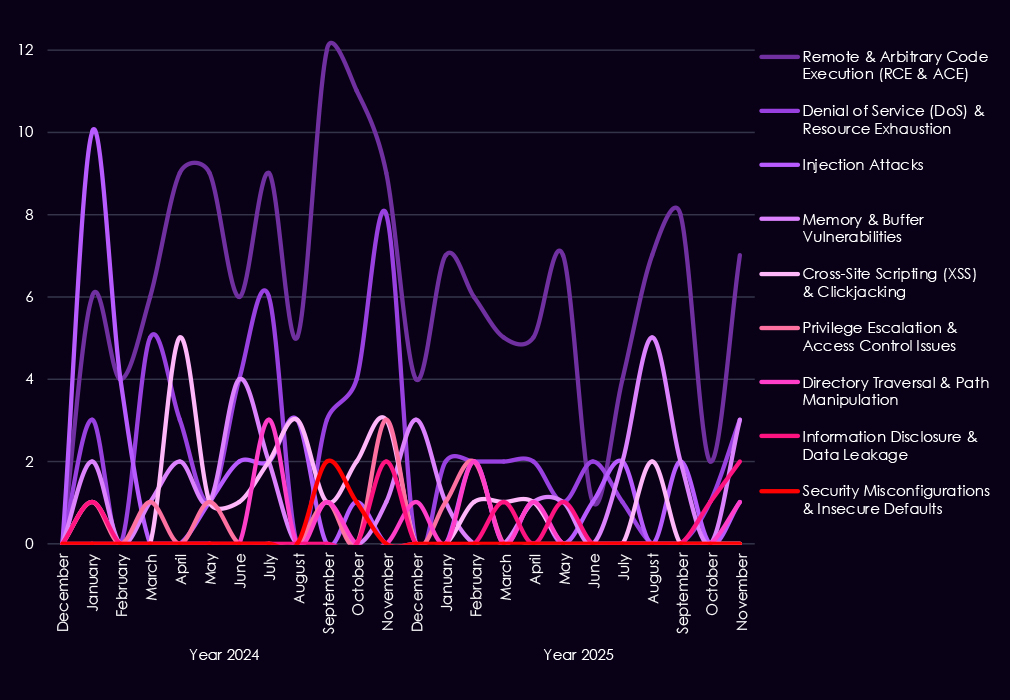
Reported CVEs affecting the materials industry technology show a steady concentration on high-impact vulnerability classes, with 2025 maintaining consistent discovery across several categories rather than sharp, short-lived spikes. Remote and arbitrary code execution (RCE/ACE) vulnerabilities remain the most prominent, appearing regularly throughout 2025 and highlighting the continued risk of direct system compromise in materials production and processing environments.
Denial-of-service and injection vulnerabilities appear intermittently, reflecting exposure of internet-facing services and the operational sensitivity of materials operations to availability issues. Memory and buffer vulnerabilities continue to surface at low but steady levels, suggesting attention to deeper technical flaws that can enable post-compromise or vulnerability chaining. Other categories – including XSS, privilege escalation, directory traversal, and information disclosure – remain present but comparatively limited in volume.
Overall, the 2025 CVE profile for the materials sector indicates persistent exposure to exploit-ready flaws rather than widespread misconfigurations, with attackers more likely to prioritize vulnerabilities that enable system control, disruption, or follow-on access within materials-related environments.
In the past 12 months, CYFIRMA has identified 426 verified materials industry ransomware victims. The highest year-over-year increase of 91% across all industries was from 223 victims in 2024. This escalation has continued since 2023, when we recorded 155 victims, making it a 175% elevation since 2023.
The materials industry accounts for 6.15% of the overall total of 7,099 ransomware victims during the same period. That is an increase from 4.25% in 2024 and even more so from 3.10% in 2023. This growth in share truly underlines the quickly escalating risk factor for the materials industry.
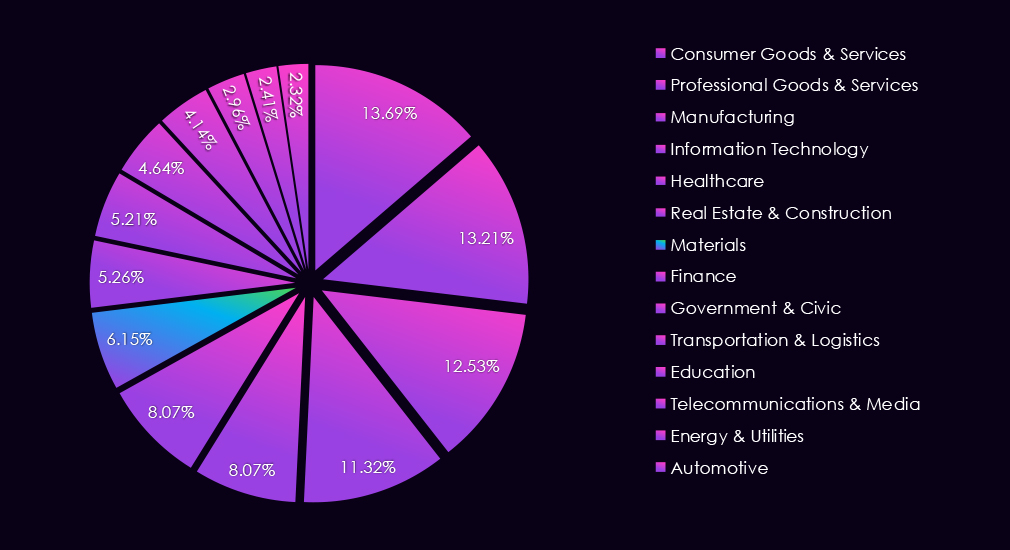
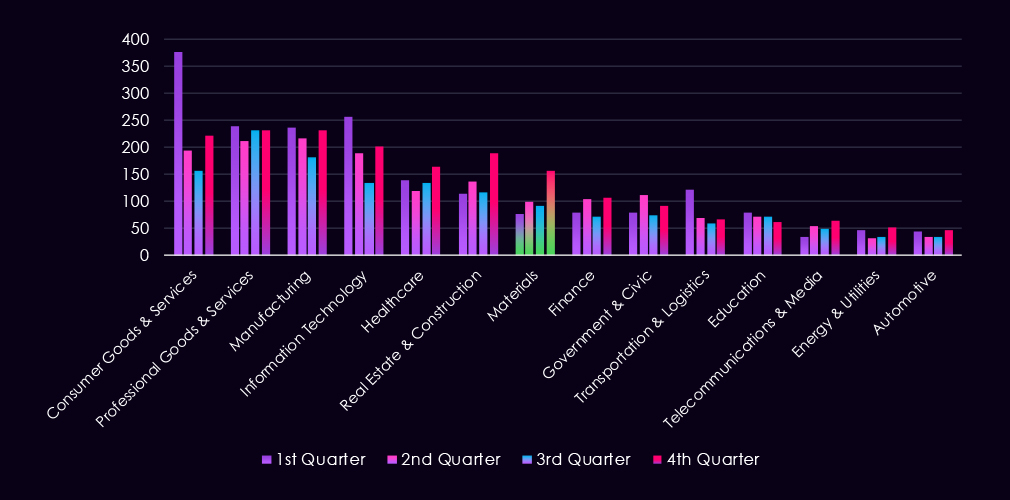
The bar chart above is focused only on 2025, and the victim counts per quarter are clear and easy to see trends. The materials industry recorded relatively even first three quarters of the year with a substantial spike in Q4, suggesting an elevation into 2026.
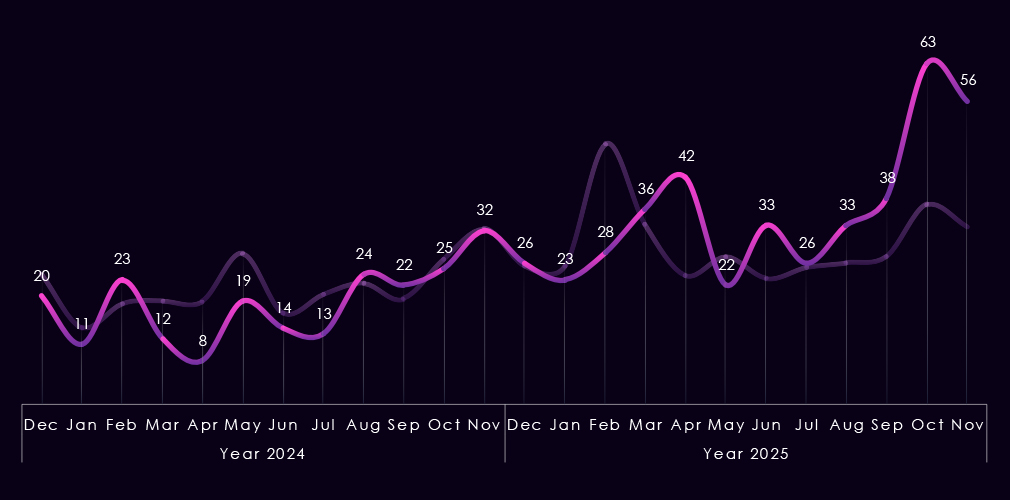
Monthly activity charted over scaled-down global all industries victims counts, showing the middle of 2024 activity below the global trendline with a notable dip in April.
From August 2024 until January 2025, activity was in line with the global trendline. The February spike of ransomware did not affect this industry, but from March to April, materials experienced their own spike, followed by a smaller elevation in June, and in August, the number of victims skyrocketed to an all-time high and stayed there.
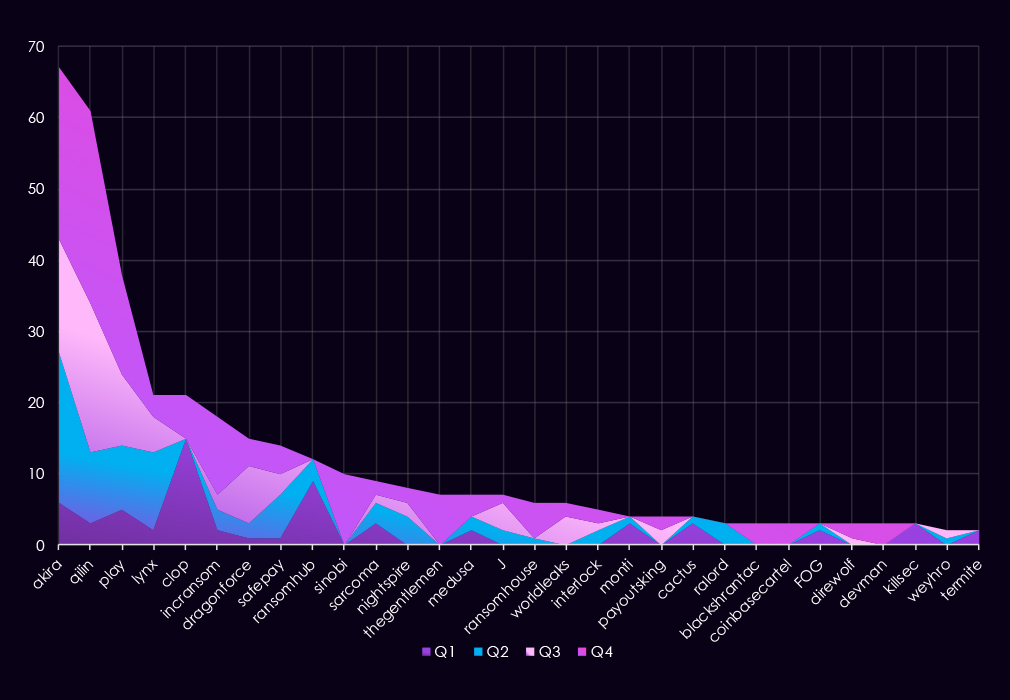
In total, 73 out of 124 gangs active in 2025 recorded victims in the materials industry, with 59% participation.
Analysis of top 30 ransomware gangs’ activity against the materials industry in 2025 shows steadily increasing pressure over the year, with a clear concentration among a small group of consistently active gangs.
Q1 activity was led by Clop (15), followed by RansomHub (9) and Akira (6). Most other gangs recorded low, single-digit activity, indicating limited but distributed targeting early in the year.
In Q2, activity increased and became more competitive. Akira (21) emerged as the most active gang, while Qilin (10), Lynx (11), and Play (9) also showed significant growth. The decline of Clop and RansomHub suggests early-year campaigns did not persist into the second quarter.
Q3 marked a further escalation and shift in leadership. Qilin (21) overtook other actors, followed by Akira (16) and Play (10). Several additional gangs, including DragonForce (8) and WorldLeaks (4), appeared or increased activity, contributing to a broader threat landscape.
By Q4, activity reached its highest level of the year. Qilin (27) and Akira (24) dominated the quarter, with Play (14) maintaining sustained pressure. Several gangs, including Sinobi (10), TheGentlemen (7), and RansomHouse (5), showed sharp late-year increases, indicating short-term campaigns or renewed targeting.
Overall, the materials sector experienced a clear upward trend in ransomware activity through 2025. Leadership shifted from early-year surges to sustained dominance by Qilin and Akira in the second half, while late-year activity featured a long tail of lower-volume but newly active actors contributing to elevated numbers.
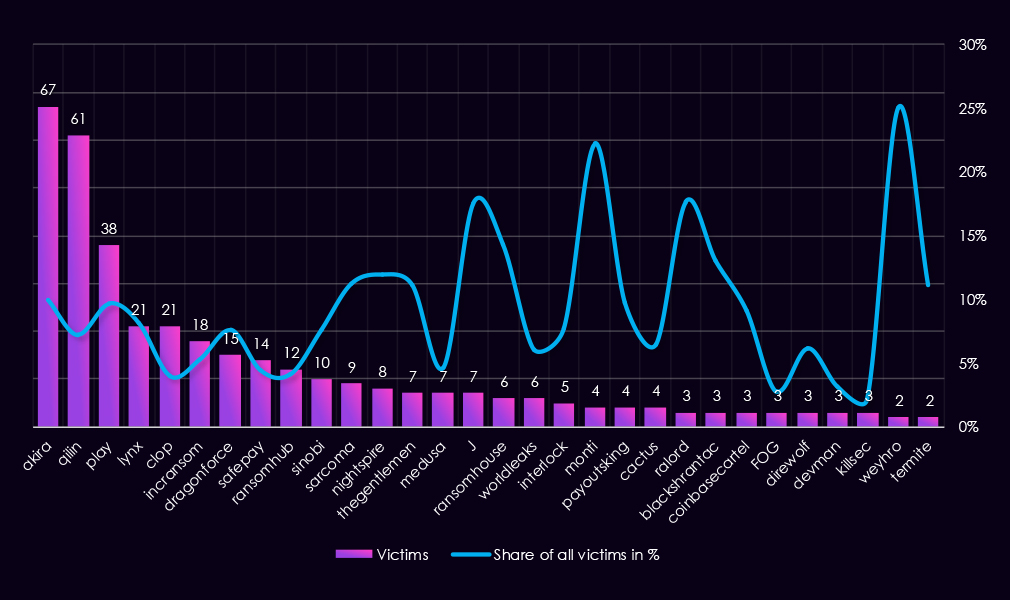
Look at 2025 materials industry victim counts alongside each of the top 30 gangs’ share of total victims shows broad engagement by high-volume actors, alongside a number of smaller groups with elevated proportional exposure.
By materials victim count, Akira (67) and Qilin (61) were the most active gangs, followed by Play (38) and Lynx (21). For these high-volume actors, materials represent a moderate share of overall activity, ranging from 7.2% (Qilin) to 9.9% (Akira), indicating sustained targeting without clear sector specialization.
Several gangs show a relatively high materials concentration (>10%). This includes Sarcoma (11.3%), NightSpire (11.9%), TheGentlemen (11.1%), J (17.5%), and RansomHouse (14.3%), suggesting possible focused targeting during 2025.
A number of outliers display very high proportional exposure, driven by low overall victim volumes. Monti (22.2%), Ralord (17.6%), BlackShrantac (13.0%), and Weyhro (25.0%) each recorded only two to four material victims, meaning small absolute counts inflate their percentage shares and should be interpreted with caution.
Most remaining gangs fall into a low to moderate focus range (<10%), including Clop, SafePay, RansomHub, Medusa, WorldLeaks, and DragonForce, indicating materials was generally a secondary or opportunistic target rather than a primary focus.
Overall, the materials sector shows consistent but not concentrated ransomware interest. However, this is a possible indicator of spillover from the highly targeted manufacturing industry. Gangs are discovering and branching into materials, finding similar vulnerabilities to exploit.
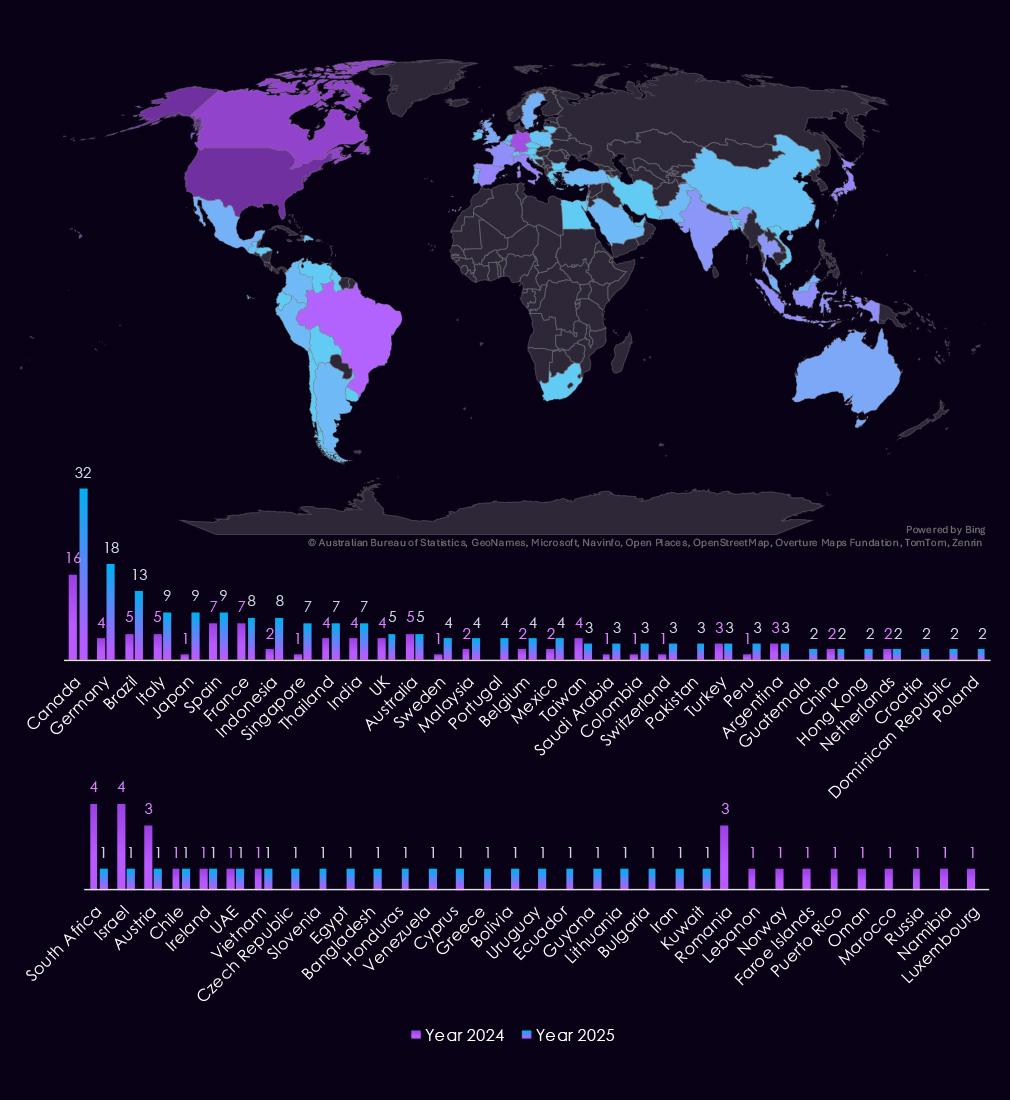
The USA recorded 207 materials industry victims and accounted for 48% of ransomware in 2025. This is almost double the 106 victims in 2024.
Canada, Germany, Brazil, Japan, Indonesia, and Singapore are among the countries with the highest increase year-over-year. Italy, Thailand, India, Sweden, and Portugal also show meaningful elevations.
South Africa, Israel, Romania, and Austria, on the other hand, are countries with the largest declines.
A total of 57 countries reported victims, also a notable increase from 44 in 2024.
Year-over-Year Risk Elevation: High

In 2025, the materials sector experienced a marked year-over-year increase in APT exposure, with victims observed in 28% of tracked campaigns, up sharply from just two campaigns in 2024. Activity reflected a broader and more diverse threat landscape, combining state-linked espionage focused on materials production, extraction technologies, and upstream supply chains with opportunistic cybercrime. Geographic targeting aligned closely with resource-rich regions and globally integrated supply chains, rather than isolated organizations.
Attack activity continued to originate primarily from web applications, reflecting exposure across procurement platforms, supplier portals, and operational systems connecting extraction, processing, and distribution environments. Compared to 2024, 2025 showed greater progression into internal platforms, including operating systems, storage management, application servers, and cloud infrastructure. This shift indicates increased emphasis on persistence, lateral movement, and access to sensitive operational data and proprietary processes once initial access is achieved.
Underground and dark web chatter rose notably from late 2024 into 2025, dominated by data breaches, data leaks, and ransomware-related discussions. Ransomware chatter showed the clearest escalation, with repeated peaks across the year, reflecting sustained extortion pressure where production downtime and supply disruption carry significant financial impact. Mentions of claimed hacks also increased, while DDoS and hacktivism became more visible but remained secondary to monetization-driven narratives.
Ransomware victimization increased 91% year over year, representing the largest growth rate among tracked industries and driving a significant rise in the sector’s share of global ransomware victims. Activity intensified toward year-end, with a broad set of actors contributing sustained pressure rather than dominance by a single group. The United States accounted for nearly half of all materials-sector ransomware victims, while geographic exposure widened substantially, reinforcing materials as a rapidly escalating and increasingly attractive target entering 2026.