


South Africa’s cyber threat landscape has intensified sharply in 2025, reflecting the country’s position as Africa’s most digitally integrated economy and a prime target for both financially motivated criminals and politically driven actors.
Ransomware remains the most damaging threat. Underground forums have also seen a rise in the sale of South African data leaks, access credentials, and network footholds, offering ransomware groups and other adversaries a gateway into corporate and government environments. This commoditization of access further fuels the cycle of extortion, disruption, and espionage.
Hacktivism adds another layer of risk, with ideologically motivated groups using defacement campaigns against government and corporate sites to protest South Africa’s geopolitical positions. Though technically less sophisticated, these disruptions undermine public trust and can cripple essential services.
South Africa is facing a convergence of financially motivated ransomware, large-scale data leaks, and politically driven hacktivism, making it one of the continent’s most targeted nations. Without significant investment in cyber resilience, threat monitoring, and workforce readiness, organizations risk severe operational, financial, and reputational damage.
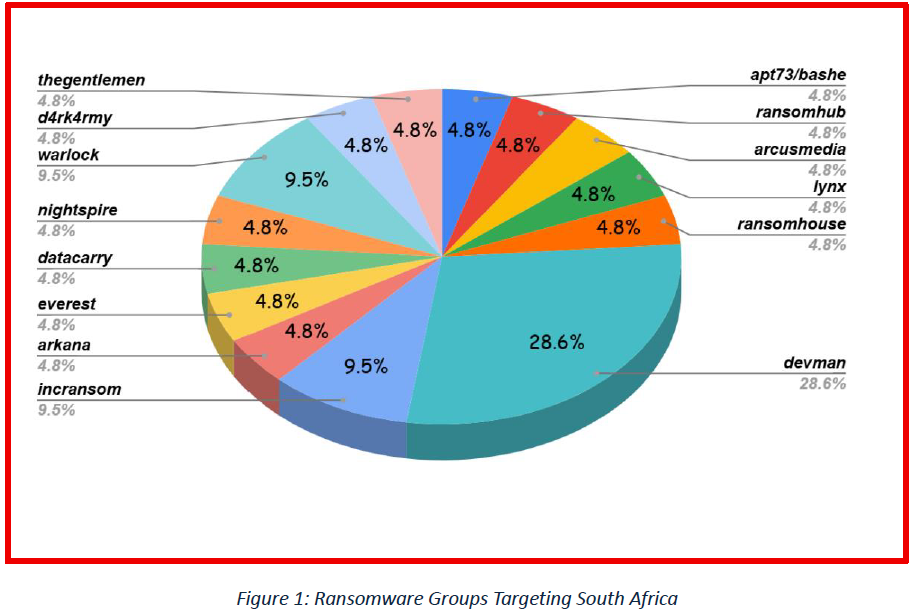
Ransomware continues to be the most disruptive threat to South African organizations, with attacks driven by both dominant and emerging groups. Devman alone accounts for 28.6% of the ransomware activity, making it the most aggressive actor in the region. Other significant groups include Warlock, Incransom, and Arkana, each responsible for around 9.5% of observed incidents. A broad spectrum of smaller operators, such as Thegentlemen, d4rk4rmy, Nightspire, Datacarry, Everest, Apt73/Bashe, Ransomhub, Arcusmedia, Lynx, and Ransomhouse, collectively contribute to the remaining activity, each with a share of 4.8%. This distribution highlights the fragmented yet persistent nature of the ransomware ecosystem in South Africa, where organizations face not only large-scale, repeat offenders but also a wide range of opportunistic groups seeking to exploit vulnerabilities across critical sectors.
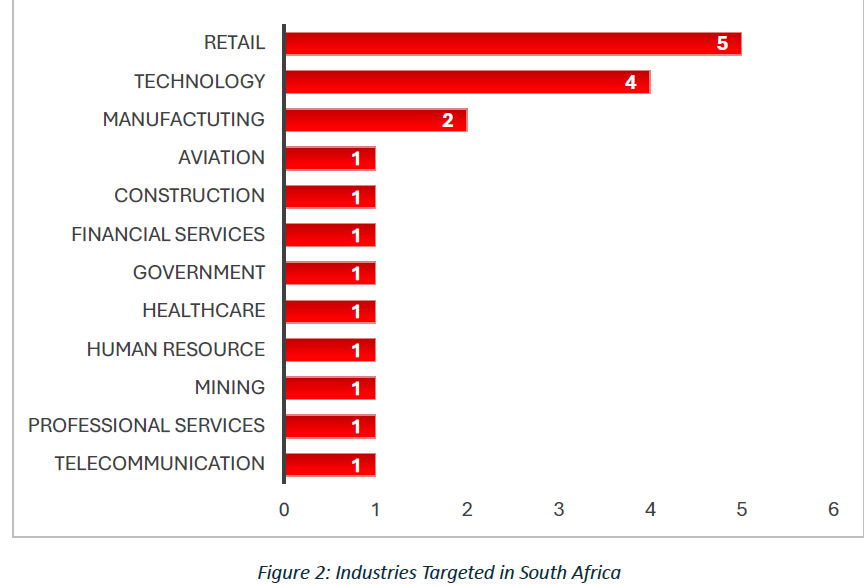
The Retail sector leads with five incidents, followed closely by Technology with four. The manufacturing sector reported two attacks, indicating that critical infrastructure is a high-risk target. Meanwhile, Telecommunications, Professional Services, Mining, Human Resources, Healthcare, Financial Services, Government, Construction & Mining Services, and Aviation each experienced one attack.
This spread highlights how ransomware groups are not confined to a single sector but instead exploit vulnerabilities across diverse industries. The heavy focus on Retail and Technology suggests attackers are prioritizing sectors with high transaction volumes, extensive customer data, and reliance on digital operations, while Manufacturing and Government attacks underline risks to operational continuity and essential public services.
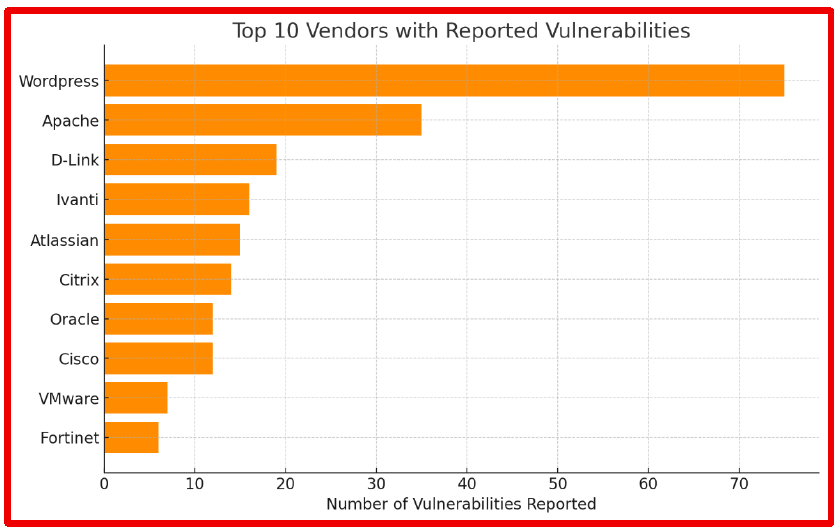
WordPress leads by a wide margin with over 70 reported issues, significantly higher than others. Apache follows with around 35, while vendors like D-Link, Ivanti, Atlassian, and Citrix cluster between 14–20 reported vulnerabilities. Oracle, Cisco, VMware, and Fortinet have fewer, ranging from about 7 to 12. This emphasizes how widely used platforms, especially content management systems and web servers, are frequent targets for vulnerability disclosures, reflecting both their popularity and attractiveness to attackers.
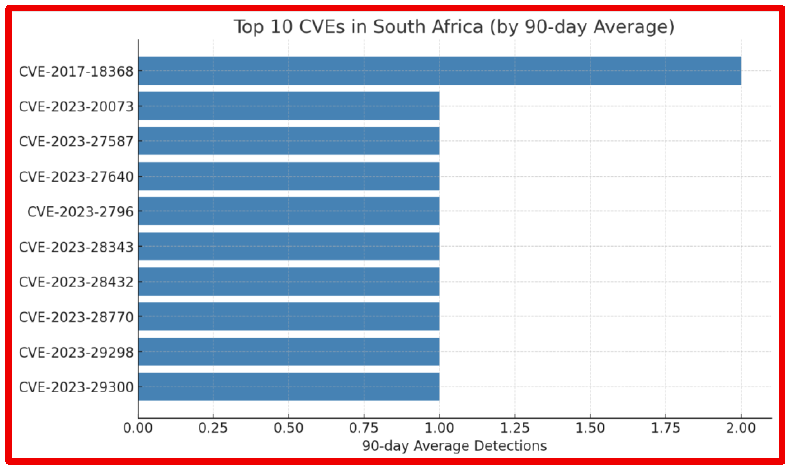
Based on their 90-day average detection rates. CVE-2017-18368 leads the list, followed by several 2023 vulnerabilities, highlighting the persistent and evolving nature of cyber threats in the region. The data provides valuable insights for security teams to prioritize patching and mitigation efforts where exposure is highest.
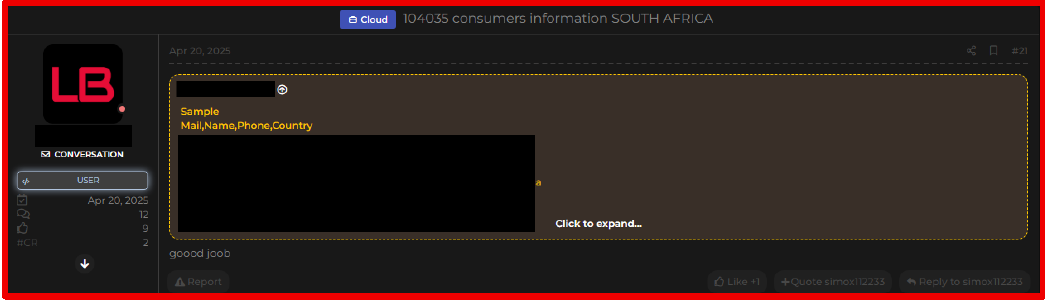
On April 20, 2025, a threat actor claimed to have leaked consumer data from South Africa. The dataset contains 104,035 records, including names, email addresses, phone numbers, and country information.
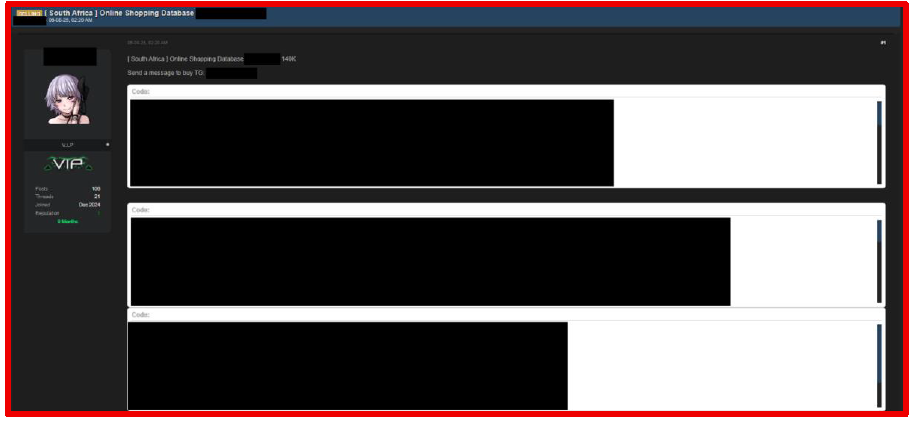
On August 6, 2025, a threat actor claimed to have leaked data associated with an online shopping platform based in South Africa. The package contains 140,000 records, including first names, last names, IDs, company details, email addresses, and more.
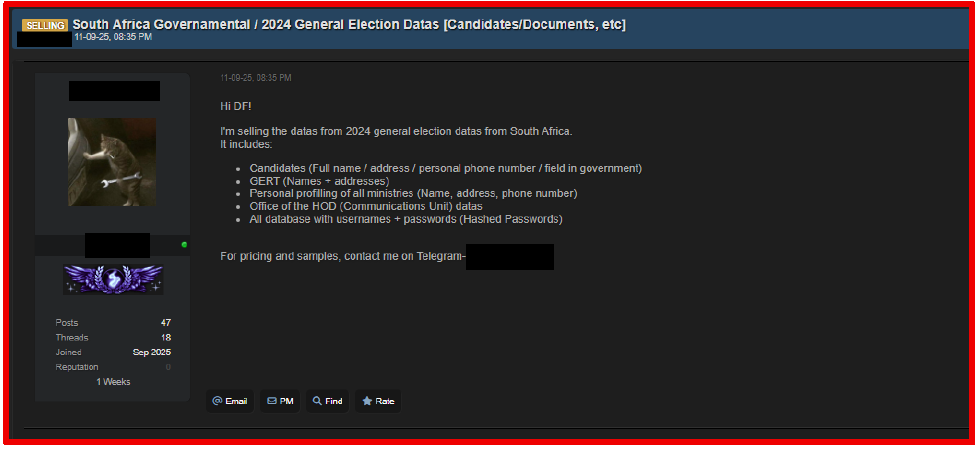
On September 11, 2025, a threat actor claimed to be selling data associated with South Africa’s 2024 general elections. The package is said to contain candidate full names, addresses, phone numbers, government roles, GERT names and addresses, as well as personal profiles of ministries.
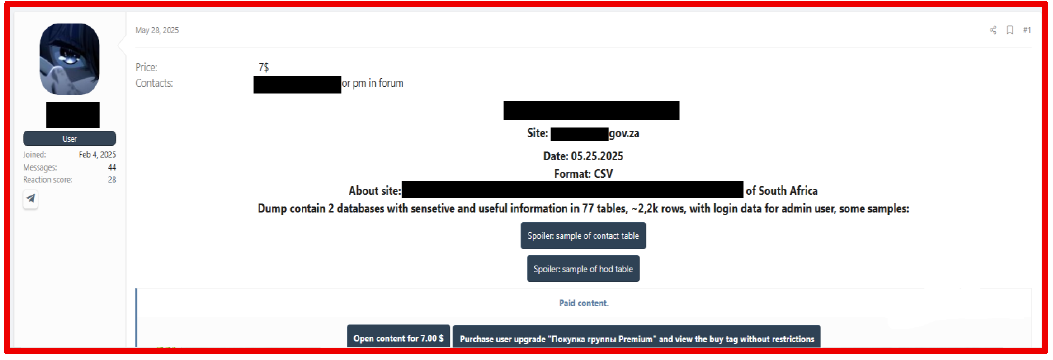
On May 28, 2025, a threat actor claimed to be selling data associated with the official government website of South Africa. The package is said to contain 77 tables, comprising 2,200 rows of administrative details. The data package is available for 7 USD.
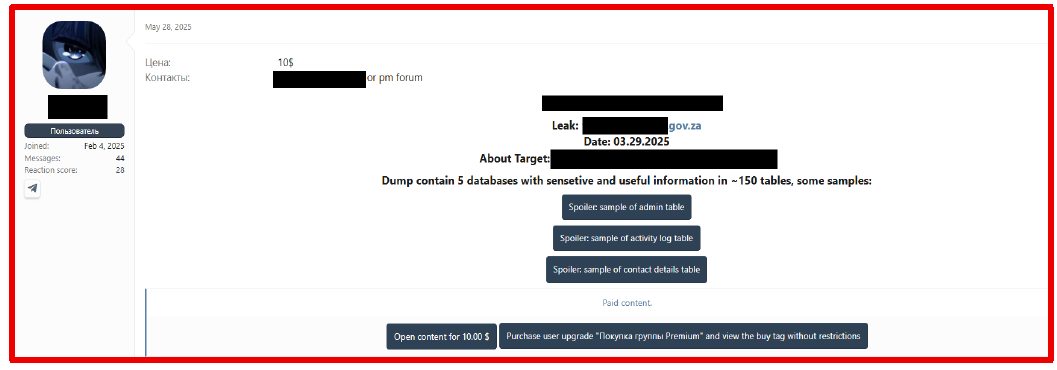
On May 28, 2025, the same threat actor released another dataset associated with the official government website of South Africa. The package contains 5 databases with a total of 150 tables and was offered for sale at 10 USD.
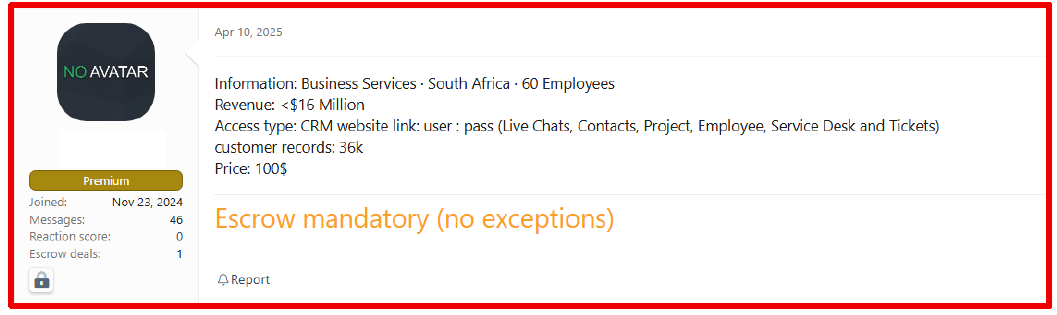
On April 10, 2025, a threat actor claimed to sell CRM access and the associated database for an organization in South Africa in the Business Services industry, generating over 16 million USD in revenue. The package contains 36,000 customer records and was offered for 100 USD.
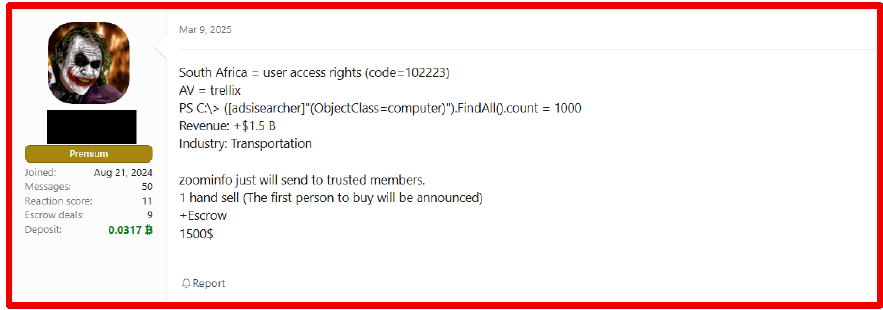
On March 9, 2025, a threat actor advertised user access rights for an organization in South Africa in the transportation industry, generating over 1.5 billion USD in revenue. The access includes approximately 1,000 computers (as enumerated via ADSI), with Trellix AV in use. The threat actor offered the sale exclusively to trusted buyers through a one-hand sale model, with escrow, for 1,500 USD.
Access bought from an initial-access broker can enable a wide range of malicious activity: ransomware deployment (encryptors and extortion), large-scale data exfiltration for sale or blackmail, privilege escalation and lateral movement across corporate networks, deployment of persistent backdoors and long-term C2 implants, web shells and remote code execution on public hosts, credential harvesting leading to account takeover and BEC/spear-phishing, pivoting into supply-chain partners, wiper/destructive attacks in high-impact scenarios, espionage or targeted surveillance by state-sponsored actors, DDoS or availability attacks to disrupt services, disinformation or influence operations using stolen context, and lower-probability abuses, such as cryptojacking or resource abuse.
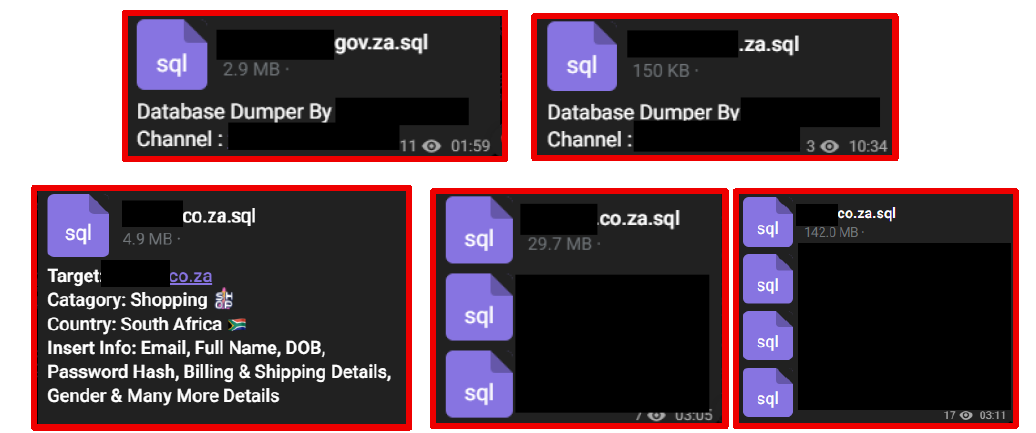
Multiple South African organizations’ data has been leaked and circulated on Telegram.
Dark-web monitoring has revealed a steady stream of data leaks and access sales involving South African organizations, emphasizing the country’s growing exposure in underground markets. These listings provide cybercriminals with ready-made entry points, fuelling ransomware campaigns, fraud, and long-term espionage against critical sectors.
The cyber threat landscape in South Africa during 2025 reflects a convergence of persistent ransomware campaigns, widespread industry targeting, and systemic vulnerability exposure. Ransomware groups such as Devman, Warlock, Incransom, and Arkana remain the most aggressive actors, while opportunistic operators continue to exploit government, retail, and technology sectors. At the same time, South Africa is burdened with hundreds of known exploited vulnerabilities (KEVs), including long-standing flaws like CVE-2017-18368 alongside newer 2023 exposures.
This combination of legacy unpatched systems and emerging critical CVEs provides attackers with multiple entry points, amplified by the ongoing sale of access and data leaks on dark-web forums. The findings confirm that South Africa’s digital growth is outpacing its defensive maturity, leaving organizations exposed to both old and new attack vectors. Without urgent improvements in patch management, threat intelligence adoption, and cross-sector resilience, the country will remain a prime target for financially motivated and politically driven adversaries.