


Between January and September 2025, Nigeria experienced a surge in data breaches and cybercrime activities across banking, telecom, government, healthcare, and possibly critical infrastructure sectors. Dark web and Russian forum actors were observed actively selling banking databases, stolen credentials, and unauthorized access to Nigerian financial institutions, including the Chartered Institute of Bankers of Nigeria and Princeps Credit Systems Limited, which suffered a ransomware attack by Killsec. Telecom data sales were rampant, with claims of over 60 million Nigerian records being traded. Government agencies, including the Lower Niger River Basin Development Authority and the Nigerian Navy, were also targeted, with sensitive internal data leaked. Healthcare records comprising 130,000 patient entries were exposed, highlighting risks to personal data privacy. In addition, offers of compromised MikroTik routers raise concerns over Nigeria’s broader critical infrastructure security.
The following accounts of alleged breaches have not been independently verified. They are presented only as claims attributed to threat actors.
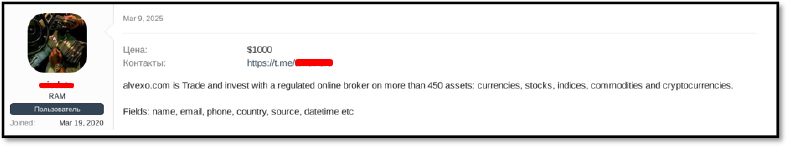
On March 9, 2025, a user on a Russian forum advertised a dataset of trading leads for sale, priced at $1,000. The seller claimed that the data originated from alvexo.com, a regulated online broker, though this claim remains unverified. According to the listing, the dataset includes information, such as name, email, phone number, country, source, and datetime, with entries from multiple countries. Notably, it mentions 166 leads specifically from Nigeria.
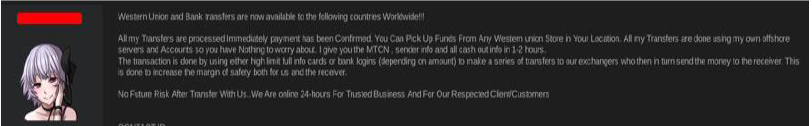
On May 13, a dark web forum user operating under the alias “SimonCheshire” advertised international Western Union and bank transfer services, including offerings for Nigeria. The seller claimed that transfers were processed immediately via offshore servers, with MTCN codes or bank details delivered within hours — though this claim remains unverified.
For Western Union transactions, recipient details (name, city, country, email) were required, and fees ranged from $100 to $800 depending on the transfer amount. First-time buyers were offered $500 transfers for $60. Bank transfers required full account information, were said to take up to 24 hours, and carried fees between $250 and $1,500. The post emphasized 24/7 service availability and assured clients of “no future risk”. This claim also remains unverified.
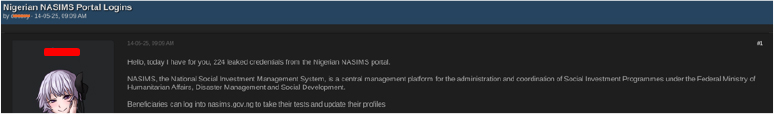
On May 14, a dark web forum user going by the name “desoxy” posted a batch of 224 leaked credentials allegedly sourced from the Nigerian NASIMS portal. NASIMS, the National Social Investment Management System, is the central platform used to manage and coordinate social investment programs under Nigeria’s Federal Ministry of Humanitarian Affairs, Disaster Management, and Social Development.
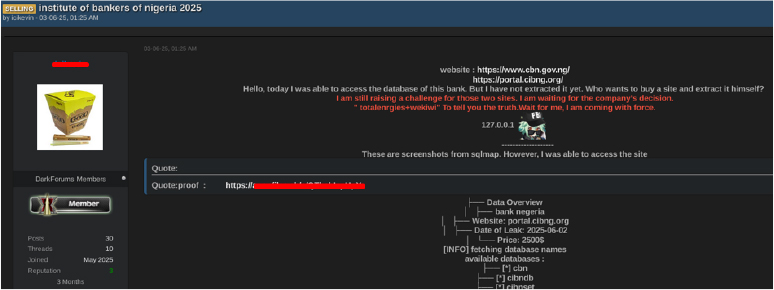
On June 3, a dark web forum user using the alias “icikevin” claimed to have gained access to the Institute of Bankers of Nigeria website and offered it for sale to anyone willing to extract the data themselves. According to the post, the breach occurred on June 2, 2025, and the asking price was $2,500. The listing displayed several available database names, including cbn, cibndb, cibnset, and msdb. The seller stated that while they had accessed the database, they had not yet extracted any data, though all of these claims remain unverified.
On June 5, a dark web forum user identified as “Broxq” advertised a service called STASHBANKS.VIP, claiming to offer verified premium bank accounts from multiple countries, including Nigeria. The post alleged that buyers would have easy access to these accounts.

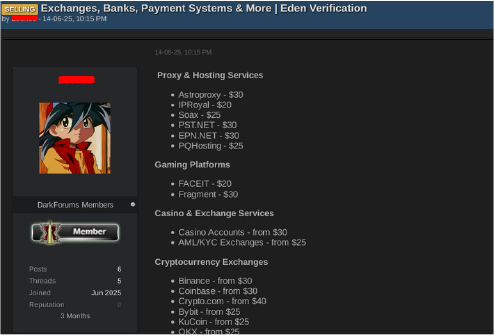
On June 14, a dark web user operating under the alias “Eden88” advertised access to a wide range of compromised accounts spanning exchanges, banks, payment systems, proxy/hosting services, gaming platforms, and other digital services. According to the post, proxy/hosting and gaming accounts were priced between $20–$30, while casino, AML, and KYC-verified exchange accounts started from $25. Cryptocurrency exchange accounts — including those from Binance, Coinbase, KuCoin, and OKX were listed for $20–$40, and banking/payment service accounts, such as Wise, Revolut, Skrill, and Payoneer, ranged from $25 to $350.
Additionally, the seller offered compromised Nigerian fintech accounts, including MoniePoint ($90), Kuda ($70), Chipper Cash ($70), and Paga ($75). Other items listed included eSIMs and Telegram Wallets, reflecting an attempt to monetize access to both global and region-specific digital services.
On July 1, a dark web forum user using the alias “httpd” posted a partial database leak allegedly linked to the Chartered Institute of Bankers of Nigeria (CIBN). CIBN is the umbrella professional body representing bankers across Nigeria.
According to the post, the leaked dataset contains sensitive personal information of certain CIBN members, including names, email addresses, and membership details.

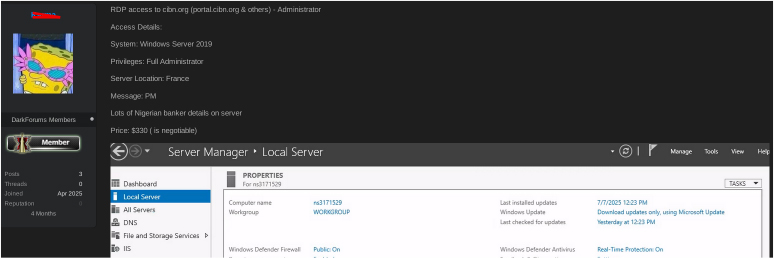
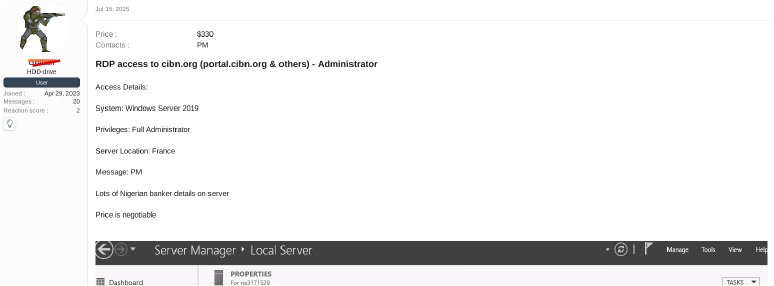
On July 15, a dark web forum user operating under the alias “Karma” advertised Remote Desktop Protocol (RDP) access to the domain cibn.org, including subdomains such as portal.cibn.org and other associated hosts. The seller claimed to have full Administrator privileges on a Windows Server 2019 instance reportedly located in France.
According to the post, the server contains numerous records related to Nigerian bankers, and interested buyers were instructed to contact the seller via private message. The access was listed for $330, with the price noted as negotiable.
The same post was also discovered on a Russian forum the same day, under a different alias.
On September 10, 2025, the ransomware group Killsec claimed responsibility for breaching Princeps Credit Systems Limited, a subsidiary of Princeps Holdings Limited in Nigeria. Princeps Credit Systems is a prominent micro-lender serving over 70,000 clients, having disbursed approximately ₦25 billion through its Credit Wallet platform and various loan products. The group allegedly compromised the company, with samples of the stolen data published on September 18, 2025. The disclosed samples reportedly include leave application forms, tax invoices, bills, payslips, and ID cards; however, the full scope and size of the exfiltrated data remain unknown.

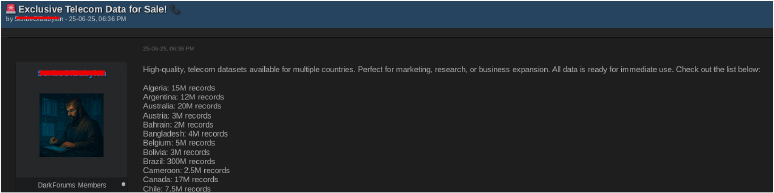
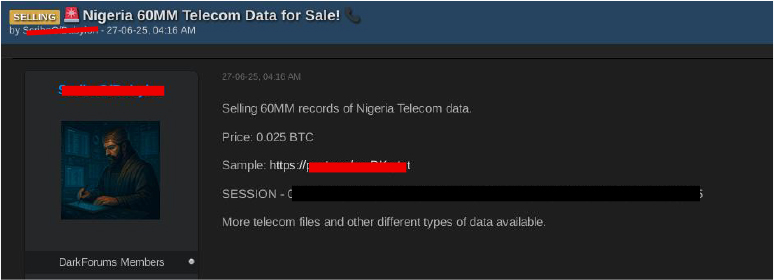
On June 25, a dark web forum user known as “ScribeOfBabylon” posted an advertisement titled “Exclusive Telecom Data for Sale!”, claiming to offer high-quality telecom datasets from multiple countries. The listing specifically mentioned approximately 60 million records from Nigeria.
On June 27, a dark web forum user identified as “ScribeOfBabylon” claimed to be selling a database containing 60 million records of Nigerian telecom data for 0.025 BTC. The user also stated that additional telecom files and various other types of data were available. A sample link was provided with the post; however, the link is currently inaccessible, raising doubts about the legitimacy of the claim.
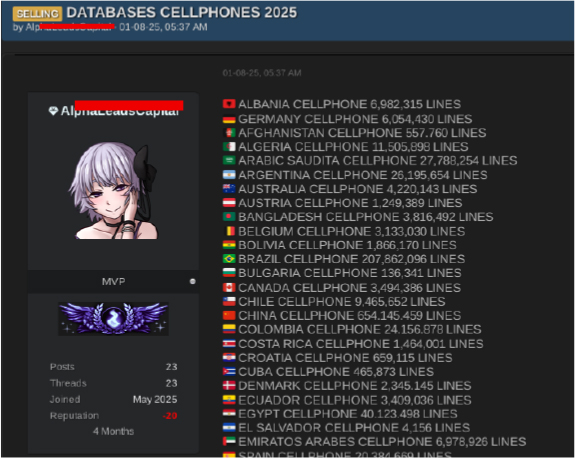
On August 1, a dark web forum user operating under the alias “AlphaLeadsCapital” advertised cellphone databases for 2025 from multiple countries, specifically claiming to offer 8,012,658 records from Nigeria, among other datasets.
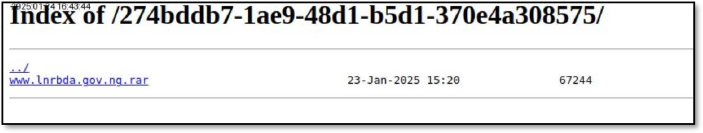
On January 27, 2025, the threat actor GDLockerSec was observed targeting lnrbda.gov.ng, the official domain of the Lower Niger River Basin Development Authority, a Nigerian government agency responsible for agricultural land preparation and water resource management. This incident reportedly resulted in a data leak of approximately 5MB.
On April 18th, The Shadow Unit claimed responsibility for a cyber operation that compromised the official website of the Lower Niger River Basin Development Authority (lnrbda.gov.ng). According to the statement, attackers gained control of the Authority’s servers and extracted data from the system, including project records, employee files, and internal communications, while reportedly leaving no significant technical traces.
The group framed the intrusion as part of a broader campaign against regimes they allege support hostile forces, warning that online systems are not secure while such actors operate. The statement concludes with a direct message: “We monitor, we watch, and we strike when the time comes. Your data is in our hands, and your options are limited.” However, the authenticity of the claim and the extent of the breach remain unverified.

On June 9, a dark web forum user identifying as “Zabaniah”, claiming to be a Russian hacker, advertised the sale of data allegedly belonging to the Nigerian Navy, consisting of more than 200 documents. The materials reportedly include internal reports, personal data of members, and other sensitive information. The actor also shared sample images, including a list of Nigerian Navy engineering officers dated April 7, 2025.

On August 8, the pro-Yemeni hacker group Yemen Cyber Army claimed responsibility for breaching multiple Nigerian government ministry domains, including eep.rea.gov.ng, eei.rea.gov.ng, and minigridafrica2017.rea.gov.ng. However, the authenticity of these claims and the extent of the breaches remain unverified.
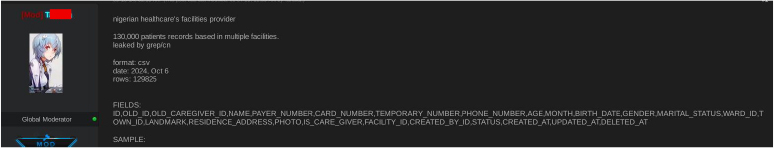
On October 9, 2025, a dark web forum user identified as “Tanaka” posted a dataset allegedly sourced from a Nigerian healthcare facilities provider. The dataset, reportedly containing approximately 130,000 patient records across multiple facilities, was shared in CSV format and dated October 6, 2024, with a total of 129,825 rows. The leaked data purportedly includes sensitive information such as patient names, payer and card numbers, phone numbers, ages, birth dates, genders, marital statuses, residence details, facility IDs, and timestamps, among other fields.
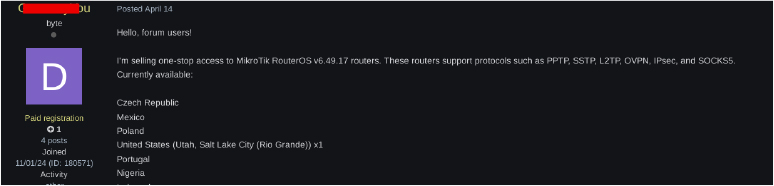
On April 14th, a dark web forum user known as “GermanyYou” advertised access to MikroTik RouterOS systems offering VPN and SOCKS5 services in countries including Nigeria. The price was listed at $75–$100. The post also mentioned providing tips to keep routers accessible longer
The access advertised does not directly mention Nigerian systems, but it can still indirectly impact Nigeria’s Telecom, Banks & Financial Services, Government, and Critical Infrastructure. Compromised MikroTik routers abroad can be weaponized as proxies or C2 nodes for cyberattacks targeting these sectors in Nigeria, making them vulnerable to masked intrusions and DDoS attempts. However, the authenticity of the claims and the extent of the impact remain unverified.
The 2025 wave of cyber incidents highlights Nigeria’s growing exposure to financially motivated and politically driven cyber threats. Banking and fintech institutions remain prime targets, with ransomware, data leaks, and credential sales posing systemic risks. Telecom and government sector compromises demonstrate that critical citizen data and national systems are vulnerable to exploitation. Healthcare data exposure further underscores the lack of sector-wide data protection and monitoring measures. Without stronger cybersecurity controls, monitoring, and public-private cooperation, Nigeria’s digital and financial ecosystems will remain at high risk.