



CVE-2024-9264 is a critical vulnerability in Grafana 11, which allows low-privilege users to execute arbitrary SQL commands, potentially leading to code execution and unauthorized access to sensitive files. This flaw impacts industries like finance, healthcare, and critical infrastructure. Threat actors are actively discussing and sharing exploits for this vulnerability in underground forums, indicating a high level of concern in the cybercriminal community. Organizations must urgently update to the latest Grafana versions or take mitigating actions to prevent exploitation. Enhanced monitoring and global collaboration are essential to defend against this and similar threats.
CYFIRMA’s research team has evaluated CVE-2024-9264, a vulnerability causing significant concern within the cybersecurity community due to its critical impact on organizations globally. This vulnerability could result in arbitrary command execution or the leakage of sensitive files, potentially leading to severe damage if exploited. Operating with a vulnerable version increases the risk of attacks, emphasizing the urgent need for robust cybersecurity measures and proactive threat intelligence to mitigate evolving cyber threats effectively.
Impact on Industries: The vulnerability poses risks to industries handling sensitive information, such as financial institutions, healthcare organizations, and critical infrastructure sectors, with the potential for targeted attacks from nation-state actors and cybercriminals.
Low-Privilege Exploitation: The vulnerability allows low-privilege users to exploit the flaw, which can lead to significant compromises of confidentiality, integrity, and availability.
Urgent Action Required: Organizations using vulnerable Grafana versions must immediately update to the latest versions or take alternative mitigation steps to avoid exploitation.
Acknowledgements:
The CYFIRMA Research team acknowledges security researchers who responsibly disclosed this vulnerability.
Vulnerability Type: It leads to arbitrary code execution or unauthorized access to sensitive files.
CVE ID: CVE-2024-9264
CVSS Severity Score: 9.4
Application: Grafana
Impact: low privileges can execute arbitrary commands.
Severity: CRITICAL
Affected Versions: Grafana versions less than 11.0.5, 11.1.6, and 11.2.1.
Patch Available: Yes
A vulnerability has been identified in Grafana, stemming from an experimental feature called SQL Expressions, which was introduced to enable the post-processing of query outputs using SQL. The feature’s insufficient SQL query sanitization resulted in a command injection and local file inclusion vulnerability. This flaw allows any user with VIEWER or higher permissions to exploit the vulnerability.
The impact of this vulnerability is severe, as it allows attackers with low privileges to execute arbitrary commands and exploit local file inclusion, potentially compromising sensitive data and system integrity. This could lead to unauthorized access, data breaches, and the complete compromise of affected systems. Organizations using vulnerable versions of Grafana are at significant risk and should prioritize remediation efforts.
The vulnerability affects Grafana versions earlier than 11.0.5, 11.1.6, and 11.2.1, leaving systems running these versions vulnerable to exploitation. To mitigate the risk, users must update to the latest patched versions.
Is there already an exploit tool to attack this vulnerability?
Yes, an exploit tool for this vulnerability has already been developed, increasing the urgency for organizations to patch their systems immediately. With the availability of an exploit, the risk of attacks leveraging this vulnerability is significantly heightened, potentially leading to widespread exploitation.
Has this vulnerability already been used in an attack?
There have been no confirmed reports of this vulnerability being actively exploited in the wild. However, with an exploit tool now available, it is only a matter of time before threat actors begin using it in attacks.
Are hackers discussing this vulnerability in the Deep/Dark Web?
Yes, hackers are actively discussing CVE-2024-9264 in underground forums, with exploit tools being shared. The proof-of-concept exploit is publicly available, increasing the likelihood of its widespread use.
What is the attack complexity level?
The attack complexity level for CVE-2024-9264 is considered critical. This is because the vulnerability allows low-privilege users to execute arbitrary commands or access sensitive files with minimal effort, making it highly exploitable, especially since the affected versions are widely used.
CVE-2024-9264 is a severe vulnerability affecting Grafana versions earlier than 11.0.5, 11.1.6, and 11.2.1, specifically in systems that use the DuckDB integration for SQL Expressions.
This vulnerability arises due to improper sanitization of SQL queries, allowing remote attackers to inject arbitrary SQL commands, which can lead to critical exploits, such as arbitrary code execution, and unauthorized access to sensitive files.
The flaw is triggered when an attacker injects a malformed SQL expression, especially utilizing the read_csv_auto() function, which is part of the SQL Expressions feature. This function is meant to read CSV files but can be manipulated to perform actions beyond its intended use. By crafting a malicious SQL query like SELECT * FROM read_csv_auto(‘/etc/passwd’), attackers can read system files, such as the /etc/passwd file, which contains sensitive information about system users. Additionally, using the query, attackers can create arbitrary files with malicious content on the system, and further escalate the attack by executing shell commands embedded within these files.
One of the most dangerous aspects of this vulnerability is that it does not require any user interaction to be exploited. Attackers can remotely execute these malicious queries without needing the victim to click on anything or take any specific action. The ease of exploitation, combined with the critical nature of the potential damage (remote code execution, unauthorized file access, and manipulation), makes this vulnerability extremely impactful on organizations running affected versions of Grafana.
The attack’s impact spans the confidentiality, integrity, and availability of the system. Sensitive data can be compromised by reading system files, and arbitrary commands can be executed, potentially taking control of the server and launching further attacks. Once the exploit is successful, attackers can escalate privileges, compromise sensitive data, and disrupt operations, causing significant damage.
Users of vulnerable Grafana versions should immediately update to the latest versions (11.0.5, 11.1.6, or 11.2.1) to address CVE-2024-9264. In cases where patching is not possible, manual mitigation steps include removing or excluding the DuckDB executable from the system’s PATH to prevent exploitation. Additionally, organizations should implement monitoring and detection measures to identify unusual SQL queries or other suspicious activities associated with Grafana’s SQL Expressions feature.
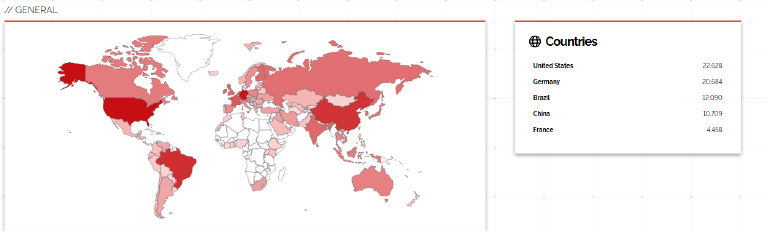
Target Geography:
CVE-2024-9264 allows low-privilege users to execute arbitrary commands or gain unauthorized access to sensitive files, potentially leading to arbitrary code execution. This vulnerability affects regions including the United States, Brazil, China, and France. For effective external threat landscape management, it’s essential to monitor global security developments, collaborate with international cybersecurity bodies, and understand the tactics, techniques, and procedures (TTPs) of threat actors across various regions. By staying informed and analyzing regional threats, organizations can better anticipate and defend against attacks from nation-state actors, cybercriminal groups, hacktivists, and insider threats.
Target Industry:
CVE-2024-9264 is a critical vulnerability in Grafana that poses significant risks across various industries. Financial institutions may be targeted for access to sensitive files, while the energy and critical infrastructure sectors are at risk from nation-state actors seeking to disrupt services. Healthcare organizations are also vulnerable, especially due to increasing geopolitical tensions. Given that threat actors often target sectors based on the value of their data or services, industries handling sensitive information or relying on Grafana for operational continuity should remain especially vigilant. Effective external threat landscape management should include sector-specific risk monitoring and assessment to better defend against potential exploits.
Target Technology:
CVE-2024-9264 was introduced in Grafana 11 through the implementation of an experimental feature called ‘SQL Expressions’. This feature allows the output of data source queries to be post-processed using SQL queries. The process involves passing the query and the resulting data to the DuckDB CLI in the backend, where the query is executed against the formatted results, referred to as DataFrames. This design flaw exposes systems to significant risks, as it enables low-privilege users to exploit SQL injection vulnerabilities for arbitrary code execution or unauthorized access to sensitive files. Effective external threat landscape management should focus on understanding the impact of such vulnerabilities across industries, particularly for organizations relying on Grafana for operational continuity and sensitive data management.
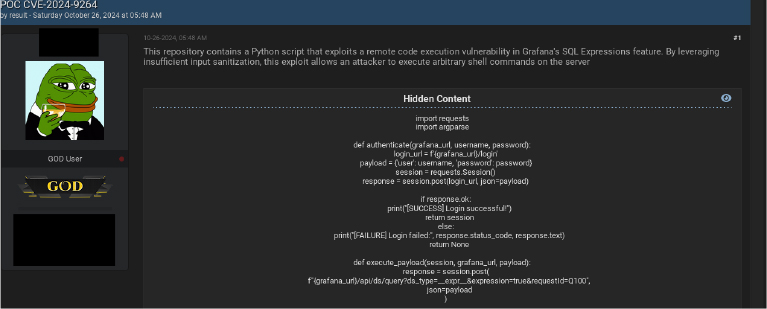
In underground forums, threat actors are actively focusing on the exploitation of the recently discovered CVE-2024-9264 vulnerability in Grafana. Malicious actors are sharing and analyzing exploits related to this vulnerability, including technical details and potential impacts of associated proof-of-concepts (PoCs). This level of attention highlights the serious concern within the cybercriminal community about the severity and potential consequences of this vulnerability.
CVE-2024-9264 is a critical vulnerability that poses a significant risk to systems using vulnerable versions of Grafana integrated with DuckDB. Its ability to allow arbitrary code execution and unauthorized access to sensitive files, combined with the ease of exploitation, makes it highly dangerous. Organizations should take immediate action to apply patches and mitigate the risk of exploitation.