



CVE-2024-7479 and CVE-2024-7481 are vulnerabilities in TeamViewer’s Remote Client and Remote Host products on Windows. Both flaws involve improper cryptographic signature verification during driver installation. Specifically, CVE-2024-7479 pertains to VPN drivers, while CVE-2024-7481 relates to printer drivers. These vulnerabilities allow local, unprivileged attackers to escalate their privileges by exploiting TeamViewer’s installation process and loading malicious drivers onto the system. Immediate patching is essential to mitigate these risks. It is also recommended to implement enhanced security measures to prevent exploitation.
CYFIRMA’s research team has evaluated CVE-2024-7479 and CVE-2024-7481, which are causing significant concern in the cybersecurity community due to their critical impact on organizations globally. These flaws affect multiple versions prior to 15.58.4. They enable an attacker with local unprivileged access to elevate privileges and install unauthorized drivers. Users should update to version 15.58.4 or later to mitigate these risks. This highlights the imperative for enhanced cybersecurity measures and proactive threat intelligence to effectively defend against such evolving cyber threats.
Key Takeaways:
High Severity: CVE-2024-7479 and CVE-2024-7481 represent a critical risk by allowing a locally authenticated attacker to gain elevated privileges due to improper verification of cryptographic signatures during VPN and Printer driver installation.
Extensive Reach: TeamViewer is installed on over 2.5 billion devices globally, including many Windows systems. It is widely used across industries for remote access and support, with a significant user base among both businesses and individuals. The free version also makes it popular for personal use.
Immediate Action Required: Organizations must promptly apply security patches, review and update configurations, and enhance monitoring to defend against potential exploitation of this vulnerability.
CYFIRMA Research recognizes the joint efforts of security researchers and the cybersecurity community in discovering and addressing the CVE-2024-7479 and CVE-2024-7481 vulnerabilities.
Vulnerability Type: Privilege Escalation
CVE ID: CVE-2024-7479 and CVE-2024-7481
CVSS Severity Score: 8.8 (High)
Attack Complexity: Low
Attack Vector: Local
Availability Impact: High
Confidentiality Impact: High
Integrity Impact: High
User Interaction Required: None
Affected Application: TeamViewer’s Remote Client and Remote Host products on Windows.
Impact: These vulnerabilities involve improper cryptographic signature verification during the installation of VPN and printer drivers, allowing local attackers to escalate privileges and install unauthorized drivers
Affected Versions: These vulnerabilities affect TeamViewer Remote Clients for Windows versions prior to 15.58.4.
Patch Availability: Yes
Mitigation: Users should update to TeamViewer version 15.58.4 or later to mitigate these security risks.
CVE-2024-7479 and CVE-2024-7481 are vulnerabilities found in TeamViewer’s Remote Client and Remote Host for Windows. Both issues stem from inadequate cryptographic signature verification during the installation of drivers. CVE-2024-7479 specifically targets VPN drivers, while CVE-2024-7481 focuses on printer drivers. These vulnerabilities enable local, unprivileged attackers to escalate their privileges. By exploiting the installation process, they can load malicious drivers onto the system. These flaws primarily impact industries reliant on remote access solutions, such as IT, telecommunications, healthcare, education, and finance. Organizations using TeamViewer for remote support and management may face significant security risks due to these vulnerabilities.
These flaws pose serious risks, including privilege escalation, which allows local attackers to gain elevated access to sensitive systems. This can compromise system integrity through malicious drivers, leading to instability and potential data breaches. Organizations may also face reputational damage and operational disruptions if exploited, resulting in significant impacts on business continuity. Overall, these vulnerabilities highlight critical security concerns for any organization using TeamViewer for remote access.
CVE-2024-7479 and CVE-2024-7481 affect multiple versions before 15.58.4, for a detailed list of the specific versions impacted, please refer to the following link here.
Are hackers discussing this vulnerability in the Deep/Dark Web?
As of now, CYFIRMA has not observed discussions or the potential exploitation of CVE-2024-7479 and CVE-2024-7481 on the Deep and Dark Web but there are discussions regarding Team Viewer on the dark web, so it is crucial to continuously monitor threat intelligence sources and cybersecurity forums for updates on this activity.
What is the attack complexity level?
The attack complexity level of CVE-2024-7479 and CVE-2024-7481 is classified as Low. This means that exploiting the vulnerability does not require sophisticated techniques or extensive conditions, making it relatively easier for attackers to exploit.
Is there already an exploit tool to attack this vulnerability?
Currently, there are no widely reported exploit tools for CVE-2024-7479 and CVE-2024-7481. However, it’s crucial to remain vigilant and keep software updated, as vulnerabilities can quickly attract exploitation efforts.
Has this vulnerability already been used in an attack?
Currently, there are no confirmed reports of CVE-2024-7479 and CVE-2024-7481 being exploited in attacks. It’s crucial to stay vigilant and apply security patches promptly to mitigate potential risks.
What are the Threat actors associated with this vulnerability?
As of now, there are no specific threat actors publicly associated with CVE-2024-7479 and CVE-2024-7481. Monitoring security reports and threat intelligence sources is essential to identify any emerging groups or individuals that may exploit this vulnerability.
Our analysis found that more than 3161 TeamViewers are public, which can be vulnerable to both CVE-2024-7479 and CVE-2024-7481.
CVE-2024-7479
CVE-2024-7481
Location of the flaw: CVE-2024-7479 is located in the TeamViewer_service.exe component of TeamViewer Remote Clients, specifically during the VPN driver installation process. CVE-2024-7481 is similarly found in the same component during the installation of printer drivers. Both vulnerabilities arise from improper verification of cryptographic signatures, allowing local unprivileged users to exploit these flaws and gain elevated privileges to install arbitrary drivers.
Script Overview: An attacker must possess local access to a Windows system with TeamViewer installed, which constrains the attack vector to primarily internal threats. This limitation poses a significant risk in environments where unprivileged users have either physical or remote local access. By exploiting this access, attackers can spoof a legitimate TeamViewer client to establish a connection with the SYSTEM service through Inter-Process Communication (IPC), facilitated via sockets. Through the transmission of meticulously crafted messages, they can illicitly trigger the installation of malicious drivers, circumventing the essential cryptographic signature verification process. This exploitation underscores the critical need for robust security measures within vulnerable environments.
TeamViewer’s service exhibits a critical deficiency in its ability to filter parameters transmitted by clients, thereby allowing the installation of unverified drivers.
This communication framework employs Overlapped I/O and IoCompletionPort, with the service actively listening on port 5939/TCP at localhost, underscoring a significant security oversight.
The exploits harness the well-established technique known as “Bring Your Own Vulnerable Driver” (BYOD), facilitating the loading of a valid signed driver into the Windows Kernel.
Upon successful loading, this driver can be manipulated to execute privileged actions, including the alteration of process tokens, thereby enabling unauthorized access to elevated system capabilities.
Potential attack scenarios for CVE-2024-7481 and CVE-2024-7479 include:
Privilege Escalation: An attacker with local access could exploit these vulnerabilities during the TeamViewer installation process to gain elevated privileges, enabling the installation of malicious software or drivers.
Malicious Driver Installation: Attackers might create malicious VPN or printer drivers that bypass cryptographic signature checks, allowing unauthorized control over system functions or the ability to intercept data.
Data Exfiltration: After obtaining elevated privileges, attackers could exfiltrate sensitive information, such as user credentials or confidential files, posing significant risks to data security.
Persistence Mechanisms: Attackers could install rootkits or other malware that ensures continued control over the system, even after a reboot, facilitating long-term access.
Disruption of Services: Exploiting these vulnerabilities could lead to disruptions in critical services, resulting in operational downtime and negatively impacting business continuity.
Organizations should remain vigilant and implement robust security measures to mitigate the risks associated with these vulnerabilities.
Mitigation strategies for CVE-2024-7479 and CVE-2024-7481 include applying security updates by ensuring TeamViewer and related software are regularly updated to close known vulnerabilities. Organizations should limit local access to trusted personnel, monitor system activity for unusual behaviors, and educate users about the risks of remote access tools. Implementing the principle of least privilege and conducting regular security audits can further enhance protection. Specifically, these vulnerabilities affect TeamViewer Remote Clients for Windows versions prior to version 15.58.4, so users should update to version 15.58.4 or later to mitigate the risk.
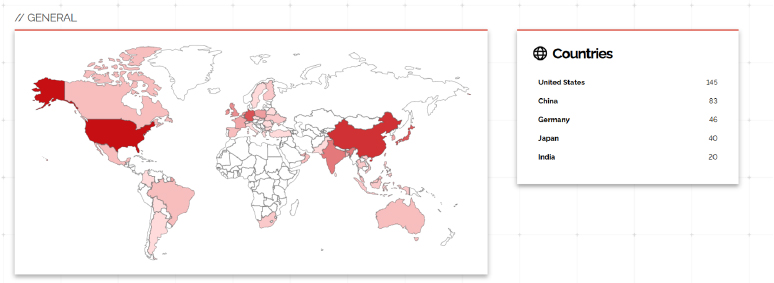
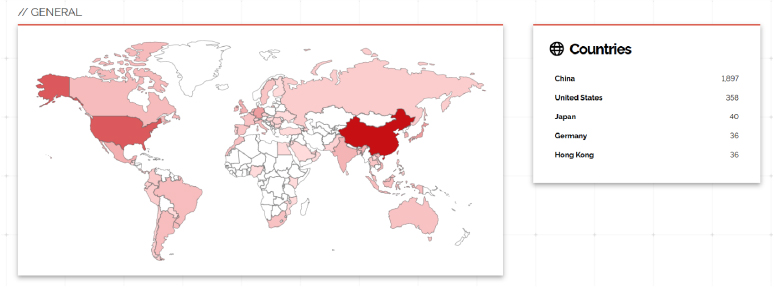
Target Geography:
CVE-2024-7479 and CVE-2024-7481 are not geographically targeted vulnerabilities; they affect TeamViewer’s software, which is used globally. However, they are particularly relevant for organizations in countries like the USA, China, Germany, Japan, and India, where TeamViewer has widespread adoption. As a result, any organization or user utilizing TeamViewer on Windows systems in these regions is potentially at risk, making it crucial for all users to implement mitigation measures and keep their software updated.
Target Industry:
CVE-2024-7479 and CVE-2024-7481 primarily affect industries that depend on remote access and support solutions, including Information Technology, Telecommunications, Healthcare, Education, and Finance. IT support teams often use TeamViewer for troubleshooting, while telecommunications companies rely on it for device management. In healthcare, remote access tools are essential for telemedicine, and educational institutions utilize them for remote learning and IT support. Given their reliance on these tools, these industries are particularly vulnerable, highlighting the critical need for robust security measures.
Target Technology:
CVE-2024-7479 and CVE-2024-7481 primarily target remote access technologies, specifically within TeamViewer’s software solutions. These vulnerabilities compromise the functionality of remote desktop software, making it a significant target for exploitation. They also involve improper cryptographic signature verification during the installation of VPN and printer drivers, which are critical for remote access setups. While the vulnerabilities primarily affect Windows systems, their implications can extend to any device using TeamViewer for remote connectivity. Overall, these issues underscore the risks associated with remote access technologies and driver management.
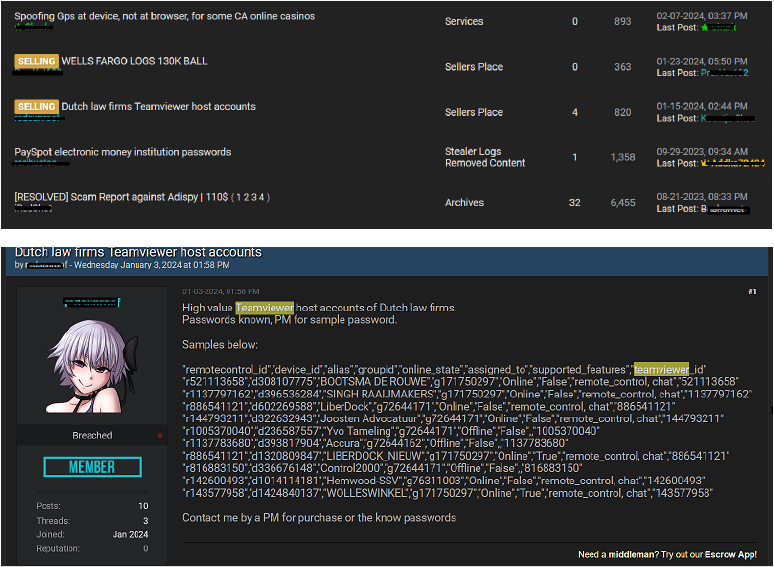
We have identified discussions about Team Viewer on underground forums. While these discussions are not directly related to CVE-2024-7481 and CVE-2024-7479, they do involve references to other vulnerabilities in Team Viewer of Windows. Additionally, there have been previous instances where Team Viewer was exploited. This highlights a continuing interest in the platform’s security vulnerabilities within malicious communities, suggesting that other exploits could potentially be leveraged in future attacks.
CVE-2024-7479 and CVE-2024-7481 represent significant vulnerabilities in TeamViewer’s remote access solutions, primarily affecting the installation processes of VPN and printer drivers on Windows systems. These vulnerabilities allow local attackers to escalate privileges, potentially compromising sensitive data and system integrity. Given the widespread use of TeamViewer across various industries, including IT, healthcare, and finance, it is crucial for organizations to prioritize security measures. Implementing timely updates, restricting local access, and conducting regular security audits can help mitigate the risks associated with these vulnerabilities. Ultimately, Swift patching, proactive monitoring, and collaboration are key to protecting critical assets, as emphasized by CYFIRMA. Quick action and ongoing vigilance are crucial for maintaining system security.