


Saudi Arabia’s cyber threat landscape between 2025 and early 2026 reflects a convergence of state-aligned espionage, ransomware industrialization, AI-enabled social engineering, and expanding identity-focused attack surfaces. Government, energy, defense, financial services, and critical infrastructure sectors remain primary targets due to their geopolitical significance and economic centrality.
Advanced Persistent Threat (APT) groups with regional alignment continue to prioritize intelligence collection and long-term access operations, while ransomware actors demonstrate increasing operational maturity through multi-vector intrusion methods and structured extortion models. Simultaneously, AI-assisted phishing campaigns and credential harvesting operations are enhancing initial access success rates, particularly against cloud-integrated and identity-dependent environments.
Dark web activity indicates sustained targeting of Saudi-linked datasets, access credentials, and enterprise systems, reinforcing the Kingdom’s positioning as a high-value cyber target amid geopolitical friction and rapid digital transformation. The cumulative threat model reflects layered risk combining espionage, financially motivated disruption, data monetization, and influence-driven cyber activity.
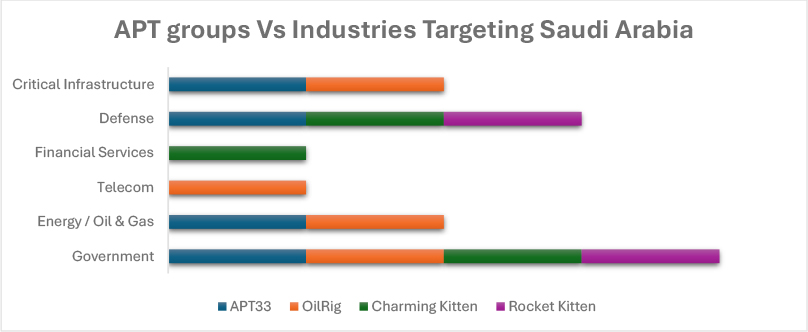
The below graph highlights a clear pattern of state-aligned cyber espionage activity concentrated primarily on government and strategic sectors. Government entities emerge as the most consistently targeted sector, with multiple Iran-linked threat actors including APT33, OilRig, Charming Kitten, and Rocket Kitten demonstrating overlapping interest in Saudi Arabian governmental institutions. The energy and oil and gas sector also shows significant targeting, particularly from APT33 and OilRig, reflecting Saudi Arabia’s strategic importance as a global energy leader.
Defense-related organizations are another prominent focus area, targeted by APT33, Charming Kitten, and Rocket Kitten, indicating intelligence-gathering objectives tied to regional security dynamics. OilRig shows additional activity against telecommunications and critical infrastructure, while Charming Kitten extends targeting into financial services. Overall, the APT landscape reflects sustained geopolitical and intelligence-driven operations aimed at long-term access, surveillance, and strategic advantage within high-value national sectors.
The graph below reflects a broader mix of espionage, disruption, and infrastructure-focused threats. Backdoor malware such as PipeMagic demonstrates targeting of government, financial services, and critical infrastructure, suggesting efforts to establish persistent access within enterprise and public-sector environments. MarsSnake shows notable activity across energy, telecom, and defense sectors, aligning with espionage-driven campaigns aimed at sensitive operational data. In contrast, Mirai primarily impacts telecom networks, IoT ecosystems, and smart systems, indicating threats to availability and service disruption rather than direct espionage. Meanwhile, the destructive wiper Shamoon demonstrates significant impact on critical infrastructure and the energy sector, emphasizing the continued risk of disruptive or retaliatory cyber operations.
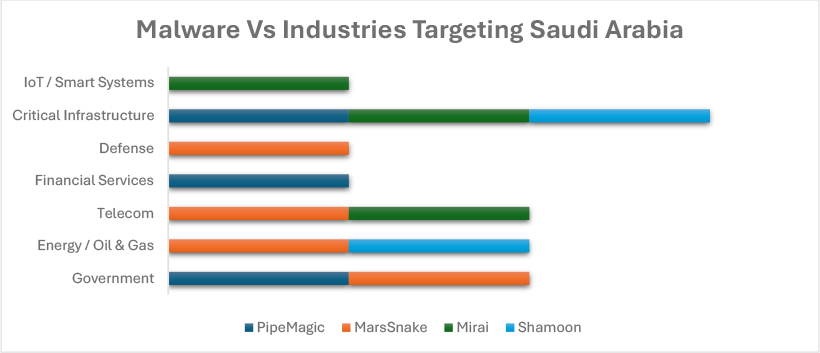
When analyzed together, both APT groups and malware reveal a possible layered threat environment in Saudi Arabia: APT groups focus heavily on government, defense, and energy sectors for strategic intelligence collection, while malware families expand the threat surface by targeting enterprise systems, industrial environments, and connected infrastructure. This convergence of state-driven espionage and operational malware activity highlights the Saudi Arbia position as a high-value cyber possible target due to its geopolitical influence, energy dominance, and digital transformation initiatives.
AI-Enabled Phishing and Social Engineering Escalation
Phishing activity possible targeting Saudi Arabia is evolving in both scale and sophistication, aligning with the broader global adoption of AI-assisted tradecraft and increasingly automated social engineering techniques. Generative AI has proven capable of producing realistic and tailored phishing content that mimics human language and context-specific cues, aiding effective social engineering in phishing campaigns. AI technologies are also being leveraged to automate attack creation and deployment at scale, enabling adversaries to generate high volumes of unique, context-aware messages that traditional defense struggle to detect. Continued growth in malicious email traffic reinforces phishing as a primary initial access vector, with automation and AI-powered content generation lowering operational barriers for threat actors.
Credential Harvesting Campaigns Targeting Government and Critical Infrastructure
Recent threat intelligence reporting has identified ongoing credential-theft operations linked to newly tracked espionage clusters conducting broad phishing campaigns across Middle Eastern networks. These campaigns commonly leverage spoofed authentication portals, cloud service impersonation, and session token capture techniques to circumvent multi-factor authentication protections. While not exclusively focused on Saudi Arabia, regional telemetry indicates credible spillover risk, particularly affecting government entities, energy operators, and telecommunications infrastructure. The operational objectives observed in these campaigns align with long-term persistence, intelligence collection, and strategic pre-positioning within high-value networks rather than immediate disruptive activity.
Exploitation of Edge and Perimeter Infrastructure
Recent telemetry reflects sustained exploitation attempts targeting externally exposed identity services, VPN gateways, and web-facing enterprise applications across the region. Threat actors are prioritizing authentication bypass vulnerabilities, remote code execution flaws, and session hijacking techniques to compromise perimeter assets and establish initial access. This edge-centric intrusion model reduces reliance on traditional endpoint malware delivery and enables more covert footholds within internal environments. The observed pattern aligns with tradecraft commonly used by both espionage-motivated actors seeking persistent access and ransomware affiliates aiming to accelerate lateral movement and operational impact.
Fileless and In-Memory Post-Exploitation Frameworks
Recent activity indicates an increased reliance on fileless malware frameworks and in-memory loaders engineered to evade traditional signature-based detection mechanisms. Adversaries are leveraging PowerShell abuse, living-off-the-land binaries (LOLBins), and reflective loading techniques to minimize disk artifacts and reduce forensic visibility. This tradecraft supports extended dwell time, enabling credential harvesting, privilege escalation, and staged data aggregation prior to exfiltration. Such techniques significantly degrade the effectiveness of static detection controls and require behavioral analytics and endpoint telemetry correlation for reliable identification.
Ransomware Operational Maturity and Multi-Vector Entry
Ransomware operations impacting the region continue to demonstrate growing operational maturity through multi-vector intrusion models. Threat actors are combining phishing, exploitation of exposed services, and previously compromised credentials often sourced through access broker ecosystems to gain initial access. Observed patterns indicate shortened intrusion-to-encryption timelines, reflecting improved automation and structured attack playbooks. Double-extortion remains the dominant monetization model, with data exfiltration preceding encryption to amplify negotiation leverage. Organizations operating within economically strategic sectors remain high-probability targets due to their operational criticality and reputational sensitivity.
Note: The authenticity of the below breaches remain unverified at the time of reporting, as the claims originate solely from the threat actor.
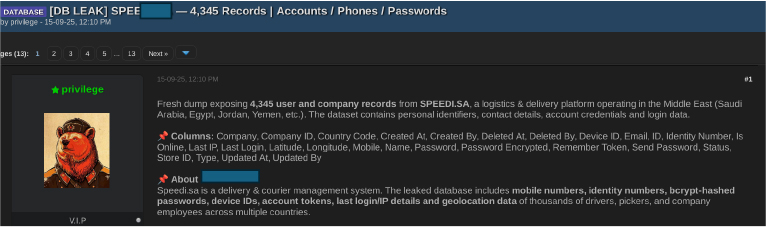
On September 15, 2025, a threat actor using the alias “privilege” advertised a database leak allegedly involving 4,345 user and corporate records from a Middle East–based logistics and delivery services platform operating in Saudi Arabia and neighbouring countries. According to the post, the dataset includes a range of account and operational metadata. While specific fields were listed by the actor, the exposed information reportedly consists of personal identifiers, contact details, device-related information, login activity records, and credential data (sensitive elements redacted). The listing suggests that both individual users and company-associated accounts may be affected. If authentic, such exposure poses risks including account takeover attempts, phishing campaigns, identity misuse, and potential targeting of operational staff. Given the platform’s role in logistics and courier management, compromised data could also introduce downstream risks to supply-chain operations and business partners. Independent verification of the dataset’s authenticity and scope would be required to assess material impact;
On November 19, 2025, a reported cyber intrusion targeting an IT company highlights the growing threat posed by politically and ideologically motivated actors to digital infrastructure. Although the incident appears to have been limited in scope and largely symbolic in nature, it reflects a broader trend of increased cyber activity aimed at organizations that support critical sectors. Even relatively contained events can serve as indicators of intent, capability development, or reconnaissance efforts that may precede more disruptive operations. Such activity highlights the importance of strengthening cybersecurity resilience across interconnected networks. Beyond immediate technical impacts, these incidents carry reputational and operational implications, including potential erosion of stakeholder confidence and increased exposure to future risk.
On November 20, 2025, an online post by a user operating under a pseudonym claimed unauthorized access to network infrastructure associated with the energy sector. The listing referenced elevated system privileges and control over security devices, though it did not provide technical evidence or details indicating active exploitation. While such claims on online forums are sometimes exaggerated, they warrant careful review due to the potential severity of the alleged access. If substantiated, unauthorized control over perimeter security infrastructure could significantly impact operational resilience. Such access may enable network manipulation, disruption of critical processes, or facilitate further movement within interconnected systems. Given the strategic importance of the energy sector to national stability and global markets, even unverified claims of this nature represent a high-risk scenario that should prompt timely investigation, validation, and, where necessary, coordinated mitigation measures to safeguard operational integrity and broader economic interests.
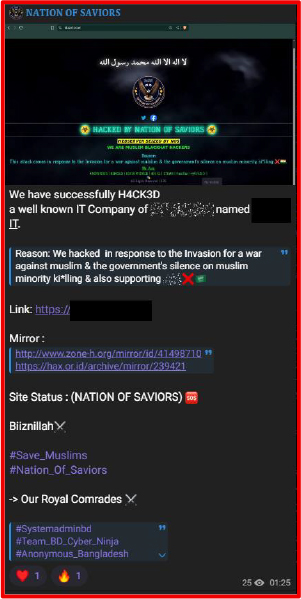
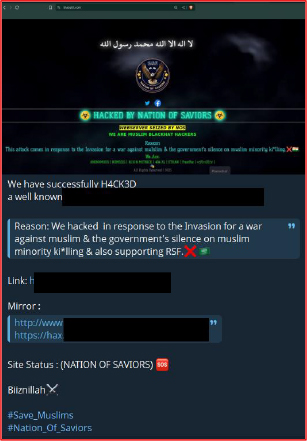
On November 22, 2025, a hacktivist group publicly claimed responsibility for compromising a regional IT services provider from Saudi Arabia , framing the alleged incident within a broader narrative of political and ideological grievance. The group referenced website disruptions and archived defacement records as proof of activity, using the announcement to project both capability and intent. While the technical validity of such claims remains unverified, the messaging itself is indicative of sustained interest in targeting digital infrastructure within the region. This pattern reflects a wider trend of ideologically motivated cyber activity aimed at organizations perceived as symbolically or strategically significant. Even when operational impact is limited, public claims of intrusion can heighten reputational exposure, invite copycat behavior, and amplify risk through coordinated social media campaigns or harassment efforts.
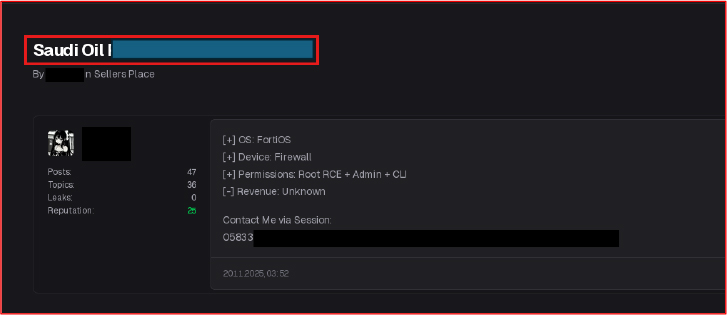
On December 2, 2025, an online forum post by a pseudonymous user advertised alleged privileged remote access to a network security device associated with a government-linked development entity. The listing claimed high-level system control over a Linux-based firewall, though it did not include technical proof, evidence of exploitation, or clear indications of monetization. The limited transparency surrounding the post leaves the claim unverified, but not without potential significance. If such access were genuine, it could expose sensitive systems to risks including unauthorized data access, operational disruption, and broader network compromise. Security infrastructure devices, particularly those positioned at the perimeter of critical environments, represent high-value targets due to their role in controlling and monitoring network traffic. Even unconfirmed claims of this nature warrant timely validation and technical assessment, as proactive investigation is essential to mitigating potential vulnerabilities and safeguarding institutional resilience, especially where public-sector systems and nationally significant functions may be involved.
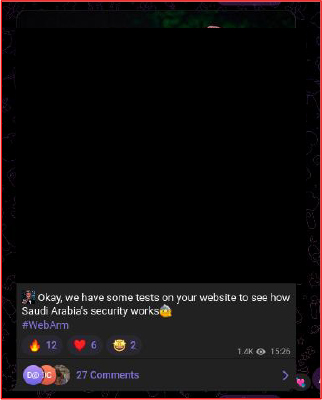
A Telegram post on December 4 and attributed to a hacktivist-affiliated channel reflects an emerging threat narrative directed at Saudi Arabia, blending geopolitical commentary with implied cyber intent. By referencing political alignments and asserting that “tests” were conducted against a Saudi website, the group appears to be positioning digital infrastructure as a symbolic target within a broader ideological campaign. Although no verified evidence of a successful intrusion has been presented, such messaging can function as pre-operational signaling. Even in the absence of confirmed technical compromise, rhetoric of this nature increases the risk of opportunistic activity, including website defacements, distributed denial-of-service (DDoS) attempts, or other low-complexity disruptions aimed primarily at visibility and symbolic impact. Public-facing digital assets are often the first targets in such campaigns due to their accessibility and reputational significance.
On December 6, 2025, an underground forum thread advertised access to several large-scale consumer and business datasets, including one described as containing hundreds of thousands of records related to Saudi Arabia. The listing was presented alongside other international data offerings, suggesting the potential commercial circulation of region-specific consumer information within cybercrime marketplaces. No technical validation or source attribution accompanied the post, leaving the authenticity and origin of the data unconfirmed. Nevertheless, the explicit marketing of a Saudi consumer dataset raises concerns regarding possible unauthorized aggregation or misuse of personal information. Even unverified listings can indicate demand-driven activity that fuels phishing campaigns, financial fraud, identity theft, and the resale of data to secondary actors.
On December 11, 2025, a threat actor using an online alias was observed on an underground forum and associated messaging channels seeking access to sensitive personal data related to Saudi nationals, specifically national identification numbers and dates of birth. Although no transaction or dataset was publicly confirmed, the inquiry itself reflects active interest in acquiring high-value identity information within cybercriminal communities. Requests of this nature are commonly associated with fraud schemes, identity misuse, account takeover attempts, and other forms of downstream criminal exploitation. Even exploratory posts can signal intent, facilitate connections between buyers and sellers, and contribute to a broader ecosystem of illicit data trading.
On December 17, 2025, a threat actor publicly alleged a breach involving Al-Ahli Saudi FC, claiming the exposure of more than one hundred internal documents. The purported materials were described as including contractual records, identification documents, and internal administrative files. While the authenticity of the claim remains unverified, if substantiated, such an incident would represent a significant cybersecurity and reputational risk to the organization and the wider sports sector.
Unauthorized disclosure of sensitive contractual or personal information could enable identity fraud, extortion attempts, contract-related manipulation, or targeted social engineering directed at players, staff, and management.

On December 17, 2025, Saudi-related email and password combinations began circulating across multiple underground forums, highlighting a significant cyber risk to government and education institutions, even though the original source of the breach remains unverified. The repeated appearance of overlapping credentials linked to government entities suggests that the data likely originates from previously compromised accounts or credential-stealing malware. The widespread redistribution of these credentials amplifies exposure, enabling large-scale credential-stuffing attacks, phishing campaigns, and potential account takeovers targeting employees, educators, and institutional systems. Successful exploitation could result in unauthorized access to internal portals, sensitive communications, and connected systems, potentially serving as an entry point for more advanced intrusions. The breadth of dissemination transforms this from a localized event into a systemic concern, emphasizing the critical importance of robust credential hygiene, multifactor authentication, and proactive monitoring to reduce the likelihood of downstream attacks against public-sector digital infrastructure.
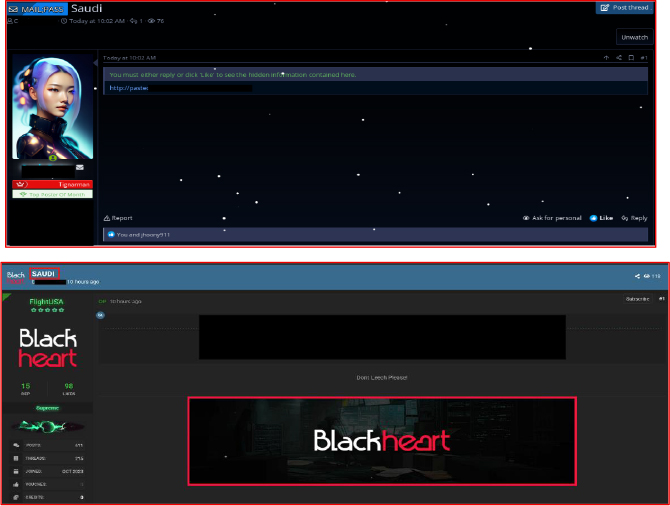
On December 20, 2025, the threat actor known as Big-Bro posted financial impact estimates related to cybercriminal activity targeting Saudi Arabia. The figures included approximately $8.1 million associated with sectors such as Industrial Machinery & Equipment, Manufacturing, Energy, Utilities & Waste, Oil & Gas Exploration & Service, and Finance. Additionally, $6.9 million was attributed to Holding Companies within the country.
These amounts reflect cyber threats spanning critical industries that underpin Saudi Arabia’s economic and industrial infrastructure. The breadth of impacted sectors underscores the wide-ranging nature of cyber risks facing both public and private organizations, highlighting the urgent need for robust, sector-wide cybersecurity defenses to protect operational continuity and sensitive information.
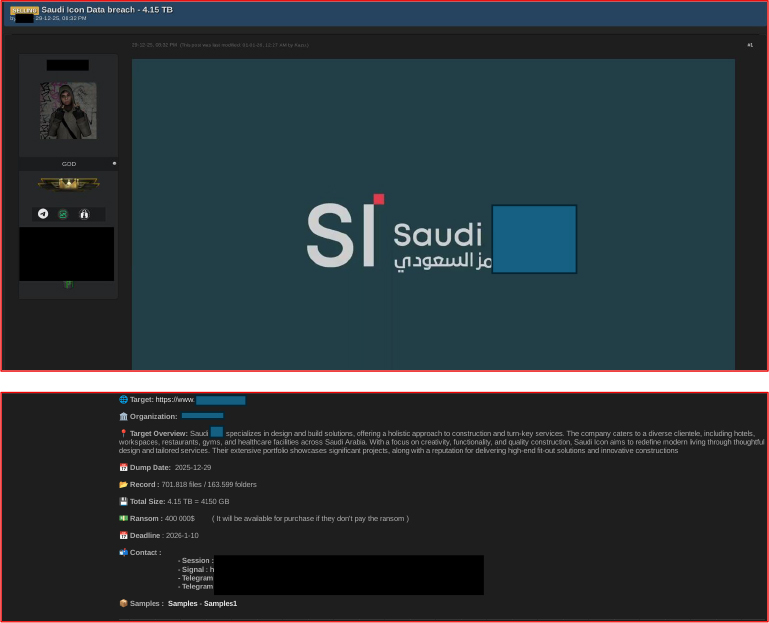
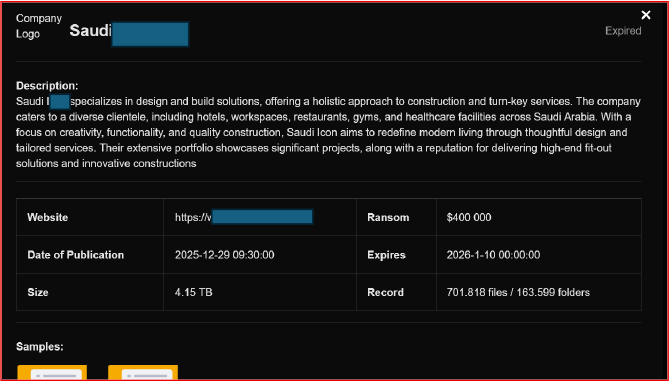
On December 29, 2025, an underground forum post claimed a large-scale breach of Saudi constructions, reporting the exfiltration of approximately 4.15 TB of data. The threat actor allegedly demanded a ransom of USD 400,000, warning that the stolen data would be sold or publicly released if payment was not made, and shared sample files as proof of compromise. The incident carries elevated strategic risk beyond commercial implications, as Saudi Icon operates across hospitality, retail, healthcare, and large-scale construction sectors that frequently intersect with government entities, regulated environments, and national development projects. Exfiltrated information may include architectural designs, project documentation, client contracts, supplier details, facility layouts, and access credentials, which could be leveraged for industrial espionage, supply-chain compromise, physical security breaches, or targeted attacks against critical facilities, particularly in healthcare and high-profile infrastructure.
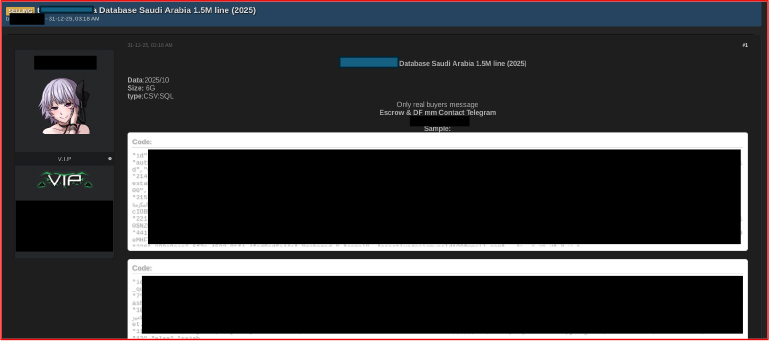
On December 31, 2025, a dataset allegedly linked to Taskawk surfaced online, reportedly containing approximately 1.5 million records, including user email addresses and account information. Notably, the presence of government email domains suggests potential exposure of Saudi government employees or affiliated partners. Even if limited to account metadata, verified government email addresses present a direct downstream risk to operations. Such information can be leveraged for credential-stuffing, spear-phishing, impersonation, and account takeover, particularly when combined with other breached datasets. The availability of this data enhances the precision of social engineering campaigns and target validation, increasing the likelihood of follow-on intrusions into government networks, third-party service providers, and digitally integrated public platforms. Collectively, these factors elevate risks to institutional trust, operational security, and the resilience of public-sector digital infrastructure.
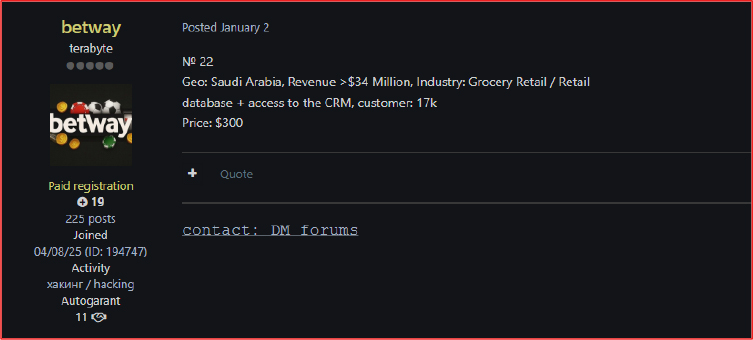
On January 2, 2026, a threat actor using the alias “Betway” claimed to be selling CRM and database access tied to a Saudi Arabia–based retail company for USD 300, without revealing the organization’s identity or the method of compromise. While the listing appears low-cost and opportunistic, such access presents latent risks to the broader economic and government ecosystem. Compromised retail CRM systems can contain customer personal data, loyalty program information, employee credentials, and API integrations, which may be exploited for credential harvesting, lateral movement, financial fraud, or supply-chain intrusion. In Saudi Arabia, where large retailers frequently interface with government platforms such as e-invoicing, VAT systems, digital identity, logistics, and payment gateways unauthorized access could escalate into secondary compromises affecting state-linked services or regulated infrastructure.
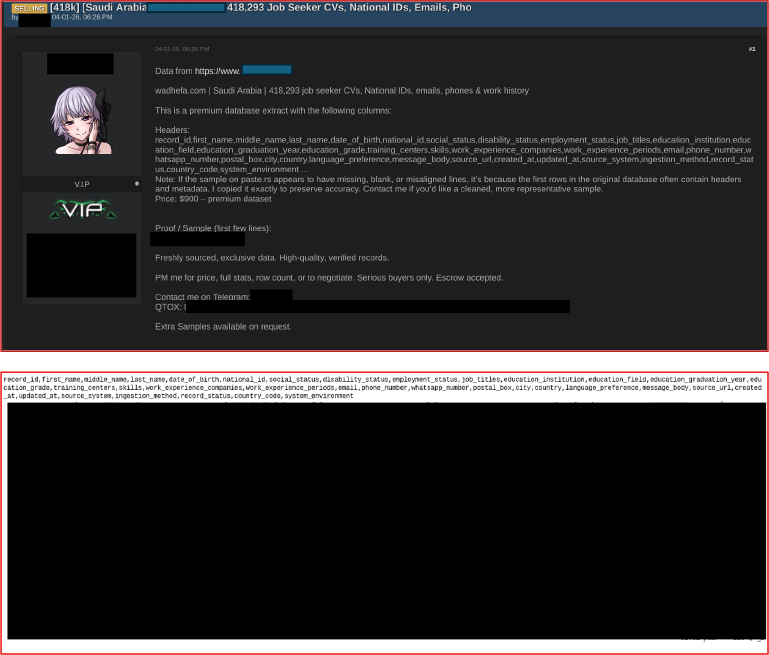
On January 4, 2026, a threat actor advertised a leaked dataset allegedly sourced from Wadhefa, claiming it contained approximately 418,000 job seeker CVs. The dataset was reported to include sensitive personal information such as national IDs, email addresses, phone numbers, employment histories, education details, and profile data. Given the platform’s likely use by applicants for public-sector, military, and defense-related roles, this incident represents a significant strategic risk to government and defense-related operations. Such data can be exploited for precision spear-phishing, identity fraud, credential pretexting, and long-term profiling of individuals with potential access to sensitive environments. When combined with other breached or publicly available datasets, the information could facilitate mapping of recruitment pipelines, clearance-eligible personnel, and human assets within defense supply chains.
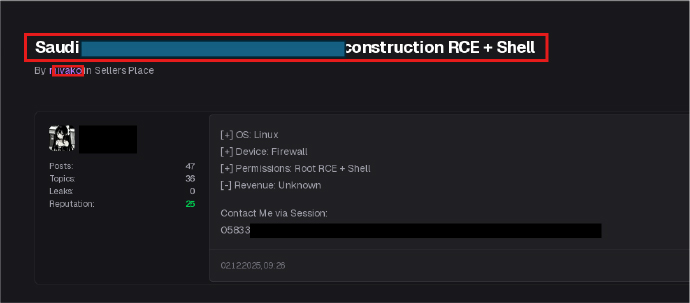
On January 14, 2026, a threat actor using the alias miya, identifying as an Initial Access Broker, advertised alleged access to a Saudi Post domain controller. The actor claimed root-level remote code execution (RCE) with shell and firewall administrator privileges, describing the targeted asset as a firewall, and offered access for USD 400 on a non-negotiable basis. An encrypted session identifier was shared for communication, and the actor denied any group affiliation. At the time of reporting, these claims remain unverified. If substantiated, such access could constitute a high-severity compromise, potentially impacting government communications, citizen data, and critical postal service operations.
On January 16, 2026, a threat actor using the alias B4baYega claimed responsibility for a data breach affecting Arabian Health Care Supply (AHC), which operates across Saudi Arabia and the broader Middle East. The claim appeared on an underground forum from a newly registered member with minimal posting history. The actor alleged possession of the breached data in CSV format and offered database access via direct message, with download links conditioned on forum interaction. At the time of reporting, no independent verification had confirmed the authenticity, content, or scale of the dataset. Given AHC’s role in supplying hospitals and clinics, a confirmed compromise could expose sensitive business and healthcare-related information, potentially leading to regulatory implications, disruption of supply-chain operations, and secondary targeting of healthcare facilities or partners.
On January 17, 2026, a threat actor using the alias zer0sintt reposted claims regarding a potential compromise of General Authority for Military Industries (GAMI) . The actor alleged that internal source code had been made publicly accessible via a third-party file-hosting service and advertised root-level database credentials for sale through messaging platforms such as Telegram and qTox. This repost followed a prior takedown and was presented as indirect confirmation of the alleged breach. At the time of reporting, no independent verification had confirmed the authenticity of the materials, the extent of access, or the validity of the credential claims. Nevertheless, the circulation of such allegations raises the risk of follow-on exploitation, including credential reuse, targeted phishing, and social-engineering attacks against government and defense-related networks. If proven accurate, the incident could expose sensitive operational, regulatory, or supply-chain information associated with military industrial oversight, representing heightened national security and defense-sector risks.
The dark web continues to serve as a major underground marketplace where hackers and threat actors exchange information and trade illicit data. Analysis of dark web activity shows an increasing focus on targeting enterprises within Saudi Arabia. The CYFIRMA research team identified numerous posts from various threat actors aimed at Saudi-based organizations, with most involving the sale of customer databases and unauthorized access to corporate networks. Government institutions, healthcare and financial services are the most frequently targeted sectors in Saudi Arabia, followed closely by transportation and additional healthcare-related industries. These patterns highlight the growing cyber risks faced by critical sectors in the Kingdom and emphasize the urgent need for enhanced cybersecurity measures to defend against evolving threats.
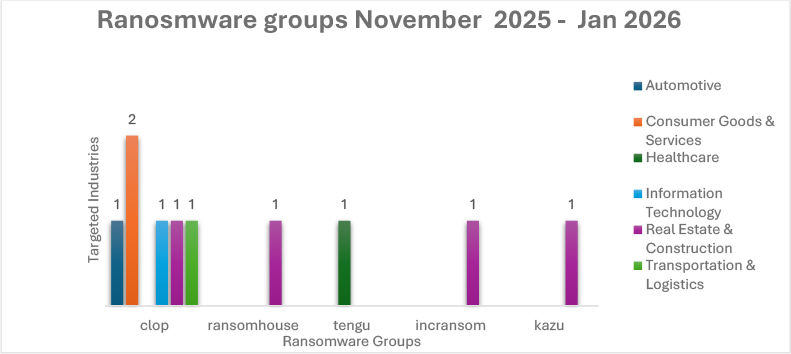
The below chart outlines sectoral targeting between November 2025 and January 2026, showing Clop conducting multi-industry operations across Automotive, Consumer Goods & Services (two incidents), Healthcare, Information Technology, Real Estate & Construction, and Transportation & Logistics demonstrating diversified victimology. RansomHouse, Incransom, and Kazu primarily targeted Real Estate & Construction, making it the most consistently impacted sector during the period. Tengu focused on Healthcare. Overall, the data reflects a mix of broad-spectrum targeting by high-capability actors and sector-specific operations by others, with Real Estate & Construction emerging as the most recurrently targeted industry.
The below graph highlights ransomware activity across 2025–2026, showing Clop as the most active group with six victims, followed by Incransom, Ransom Hub, and Killsec with four each, indicating sustained campaign momentum. RansomHouse and Qilin recorded three victims, while DarkVault, Ralord, and Everest reported two each. The remaining groups were linked to single incidents. Overall, activity is concentrated among a few high-tempo operators, with multiple smaller actors conducting limited or opportunistic attacks.
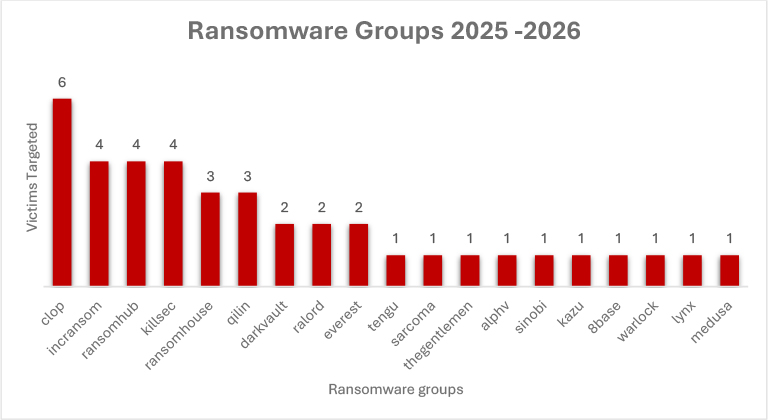
Clop Ransomware
During a concentrated campaign in late November, a prominent ransomware collective targeted multiple Saudi-based entities across diversified commercial verticals within a narrow timeframe, suggesting coordinated intrusion efforts. The selection of victims demonstrates sector-spanning targeting designed to create cascading operational and reputational impact across interconnected industries.
Looking ahead to 2026, ransomware threats in the Saudi Arbia are expected to intensify, with actors increasingly leveraging cross-platform exploitation, rapid payload deployment, and techniques aimed at virtualized and hybrid environments. This trajectory reinforces the need for strengthened incident response readiness, improved network segmentation, hardened perimeter controls, and enterprise-wide resilience strategies to mitigate both operational disruption and data extortion risks.
Confirmed Victims and Breach Details
| Sector | Date |
| Automotive | 20/11/2025 |
| Real Estate & Construction | 21/11/2025 |
| Transportation & Logistics | 21/11/2025 |
INC Ransom Ransomware
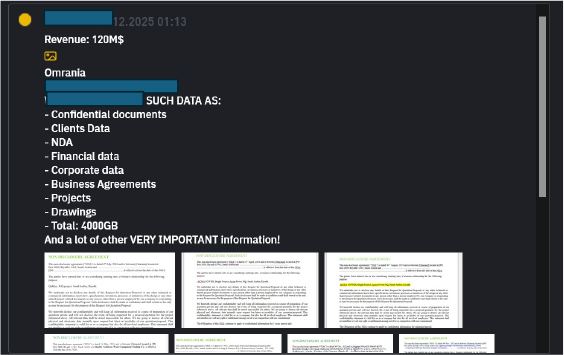
On December 29, 2025, at approximately 01:13, a Saudi Arabia organization was listed on a ransomware group’s data leak site. The threat actor claimed to have exfiltrated a significant volume of data, reportedly around 4,000 GB, and referenced the organization’s public website in the disclosure. According to the post, the compromised data allegedly includes confidential internal documents, client information, non-disclosure agreements, financial records, corporate and operational data, business contracts, and project-related materials such as designs and technical drawings. The listing also referenced the organization’s annual revenue and provided sample files as proof of the alleged breach. No independent technical validation or further forensic details were made available at the time of reporting.
RansomHouse Ransomware
On December 19, 2025, an organization operating in the engineering and project development sector was listed on a ransomware group’s disclosure platform, with the encryption date reportedly recorded as December 8, 2025. The case was marked as “Evidence” and attributed to the respective threat actor. The listing claimed possession of internal company data, including confidential corporate materials and project-related documentation. Although no confirmed data volume was specified, an evidence package was reportedly made publicly accessible without password protection. The disclosure noted that prior attempts to contact the organization had not received a response at the time of publication. The post also referenced estimated company revenue and workforce size; however, no additional technical details or independent verification were provided.
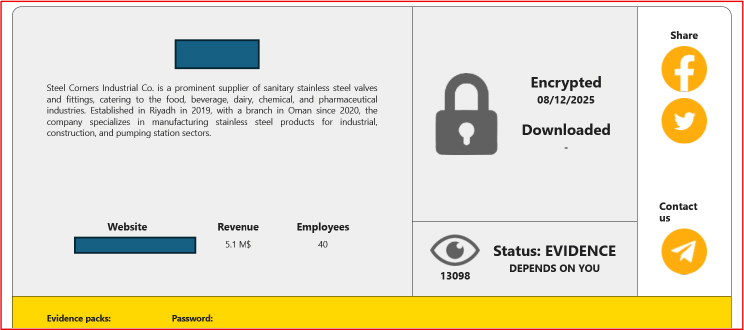
Kazu Ransomware
On December 29, 2025, at approximately 09:30, an organization operating in the construction and infrastructure sector was listed on a ransomware group’s disclosure platform. The entry referenced a ransom demand of USD 400,000 with a stated deadline of January 10, 2026. The threat actor claimed to have exfiltrated approximately 4.15 TB of data, reportedly comprising around 701,818 files across 163,599 folders. Sample data packages were shared as proof of alleged access to the compromised environment; however, no additional technical validation or forensic details were provided at the time of publication.
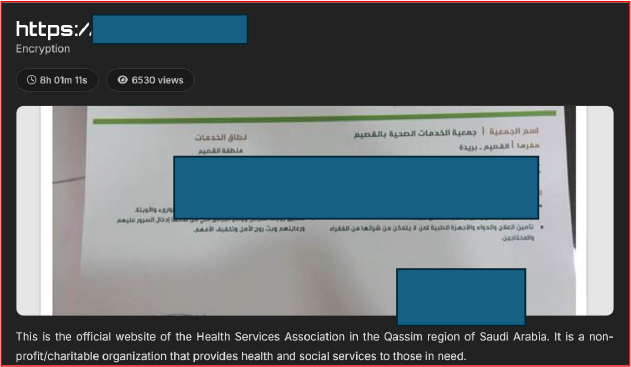
Tengu Ransomware
The Health Services Association in the Qassim region of Saudi Arabia was listed by the Tengu ransomware group in connection with an encryption incident. The disclosure referenced the organization’s official website and described it as a non-profit entity providing health and social services in the region. At the time of reporting, the listing recorded approximately 6,530 views. The entry included a timed access mechanism, with restricted content scheduled to unlock on January 20, 2026, at 16:43:48. Sample images were published by the ransomware group as evidence of access to internal or organizational data, though no additional technical verification or details were provided.
Between November and January, telemetry indicates sustained scanning and exploitation attempts against Saudi Arabia–based internet-facing infrastructure, primarily targeting critical RCE vulnerabilities (CVSS 9.0–10.0) across externally exposed web servers, enterprise middleware, application frameworks, and search platforms to gain initial access via web shells and remote command execution. Simultaneously, edge infrastructure including VPN gateways, firewalls, and management interfaces was heavily targeted, reflecting adversary intent to harvest credentials, hijack sessions, and establish persistent footholds within internal networks. Continued exploitation of legacy IoT and SOHO devices further indicates automated mass scanning for unpatched or end-of-life assets to support botnet activity or staging infrastructure. Overall, the activity reflects a possible hybrid threat model combining opportunistic large-scale reconnaissance with selective targeting of high-value enterprise systems, sustaining elevated risk of espionage, credential compromise, data exfiltration, or disruptive operations where patch governance and external attack surface management remain weak.
| Vulnerability | CVSS | Vendor | Product |
| CVE-2025-55182 | 10 | Meta | React Server Components |
| CVE-2017-9841 | 9.8 | PHPUnit – Sebastian Bergmann | PHPUnit |
| CVE-2021-42013 | 9.8 | Apache | Apache HTTP Server |
| CVE-2019-1653 | 7.5 | Cisco | Cisco RV320/RV325 |
| CVE-2017-18368 | 9.8 | Zyxel/Billion | ZyXEL P660HN-T1A v1, ZyXEL P660HN-T1A v2, Billion 5200W-T |
| CVE-2015-1427 | 9.8 | Elastic | Elasticsearch |
| CVE-2016-1555 | 9.8 | NETGEAR | WN604, WN802Tv2, WNAP210v2, WNAP320, WNDAP350, WNDAP360, and WNDAP660 |
| CVE-2016-3088 | 9.8 | Apache | ActiveMQ |
| CVE-2017-1000486 | 9.8 | PrimeFaces | PrimeTek |
| CVE-2017-10271 | 7.5 | Oracle | Oracle Weblogic Server |
| CVE-2017-15944 | 9.8 | Palo Alto Networks | PAN-OS |
| CVE-2017-5521 | 8.1 | NETGEAR | NETGEAR (multiple routers) |
| CVE-2017-9805 | 8.1 | Apache | Struts |
| CVE-2018-10562 | 9.8 | Dasan | Dasan GPON Home Router |
| CVE-2018-1273 | 9.8 | Spring | Spring Data Commons |
| CVE-2020-15415 | 9.8 | Draytek | Vigor3900, Vigor2960, Vigor300B |
| CVE-2021-42013 | 9.8 | Apache | Apache HTTP Server |
| CVE-2017-9841 | 9.8 | PHPUnit – Sebastian Bergmann | PHPUnit |
| CVE-2014-8361 | Realtek | Realtek SDK | |
| CVE-2015-2051 | 8.8 | D-Link | D-Link DIR-645, DAP-1522 revB, DAP-1650 revB, DIR-880L, DIR-865L, DIR-860L revA, DIR-860L revB DIR-815 revB, DIR-300 revB, DIR-600 revB, DIR-645, TEW-751DR, TEW-733GR |
| CVE-2018-10562 | 9.8 | Dasan | Dasan GPON Home Router |
| CVE-2020-16846 | 9.8 | SaltStack | Salt |
| CVE-2022-24816 | 10 | Geoserver | Geoserver (JAI-EXT) |
| CVE-2023-29357 | 9.7 | Microsoft | SharePoint |
| CVE-2023-20198 | 10 | Cisco | Cisco IOS XE |
| CVE-2023-42793 | 9.8 | JetBrains | TeamCity |
| CVE-2020-3580 | 6.1 | Cisco | Cisco ASA and Cisco Firepower Threat Defense |
| CVE-2020-8193 | 6.5 | Citrix | Citrix ADC, Citrix Gateway, Citrix SDWAN WAN-OP |
| CVE-2023-22515 | 9.8 | Atlassian | Confluence |
| CVE-2023-36845 | 9.8 | Juniper | Junos OS (J-Web) |
| CVE-2023-36844 | 5.3 | Juniper | Junos OS (J-Web) |
| CVE-2023-4966 | 7.5 | Citrix | Citrix ADC and Citrix Gateway |
| CVE-2023-35078 | 9.8 | Ivanti | Endpoint Manager Mobile (EPMM), formerly MobileIron Core |
| CVE-2022-24816 | 10 | Geoserver | Geoserver (JAI-EXT) |
| CVE-2021-42013 | 9.8 | Apache | Apache HTTP Server |
During November 2025 to early 2026, regional dynamics in the Middle East were marked by intensifying confrontation, diplomatic stagnation, and shifting alliance structures.
Tensions between the United States and Iran escalated significantly. Washington increased political and military pressure amid stalled negotiations, while Tehran maintained its long-standing strategy of limiting talks strictly to the nuclear file. Iran continued to reject U.S. demands to expand negotiations to include ballistic missiles and regional proxy activities, insisting that uranium enrichment remains a sovereign and non-negotiable right. The widening gap between both sides’ positions reduced the likelihood of a comprehensive agreement.
Iranian leadership interpreted U.S. military buildup and strike rhetoric as indicative of regime-change intentions rather than policy recalibration. Hardline elements within Iran’s security establishment appeared emboldened, viewing confrontation as a means to consolidate domestic legitimacy. The risk of both horizontal (regional spread) and vertical (intensity) escalation increased, particularly given Tehran’s signaling that any further strikes on strategic assets especially missile infrastructure would provoke a broader and more forceful response. The strategic calculus on both sides during this period suggested heightened volatility with limited diplomatic flexibility.
In Syria, the geopolitical landscape continued to shift following the December 2024 fall of Bashar al-Assad. The US administration reinforced its policy pivot away from the Kurdish-led Syrian Democratic Forces and toward the transitional government in Damascus led by Ahmed al-Sharaa. This realignment emphasized territorial unity and centralized authority over Kurdish autonomy, reflecting Washington’s assessment that the counter-ISIS mission had largely diminished. Damascus formally joined the U.S.-led Global Coalition to Defeat ISIS, marking a significant diplomatic shift and reinforcing efforts to stabilize the country under a unified framework.
Saudi Arabia played a pivotal role in supporting Syria’s transitional authorities, aligning closely with Washington to counter Iranian influence. However, this evolving alignment contributed to broader regional resentment among rival actors and militant networks.
Simultaneously, the Saudi–UAE relationship deteriorated sharply. The crisis centered on Yemen, where the UAE-backed Southern Transitional Council launched a late-December offensive into eastern provinces, threatening Saudi border security and coalition cohesion. Riyadh responded decisively with air operations and support for counteroffensive measures, asserting dominance and reshaping the balance of influence within Yemen. The confrontation underscored a transition from strategic competition to open rivalry between the Gulf powers, with spillover implications across military, economic, and diplomatic domains.
Beyond Yemen, Saudi Arabia sought to consolidate its regional position amid Red Sea and Horn of Africa competition by pursuing closer defense coordination with Pakistan, Turkey, and Egypt. While this strengthened Riyadh’s deterrent posture, it also increased exposure to asymmetric retaliation, including cyber espionage, sabotage, and influence operations by competing regional actors.
Overall, November 2025 early 2026 reflected a period of mounting strategic friction. U.S.–Iran tensions, Syrian political realignment, and the Saudi–UAE rupture collectively contributed to a more fragmented and volatile regional environment, with elevated risks of military escalation and expanded proxy confrontation.
Saudi Arabia faces a layered and evolving cyber threat environment characterized by the convergence of state-aligned espionage, ransomware industrialization, AI-enabled phishing, and expanding identity attack surfaces. The intersection of geopolitical volatility and accelerated digital transformation has elevated the Kingdom’s exposure to both strategic intelligence operations and financially motivated disruption. Sustained targeting of critical sectors underscores the need for adaptive, intelligence-driven cybersecurity posture enhancements to counter increasingly automated, scalable, and persistent adversarial tradecraft.
Strategic Recommendations
Operational Recommendations
Tactical Recommendations