



At CYFIRMA, we provide timely insights into emerging threats and malicious tactics targeting organizations and individuals. CYFIRMA’s research team recently identified a sophisticated dropper binary designed to deploy an information stealer, dubbed BLX Stealer – now also called the XLABB stealer – which has been actively advertised on Telegram and other online platforms.
The BLX stealer is available as an open-source tool on a GitHub repository. Notably, the tool is under constant development. This report provides a detailed analysis of the dropper’s behaviour, its payloads, and the potential impact on targeted systems.
The BLX Stealer (or XLABB Stealer) is a highly sophisticated malware developed to steal sensitive information from compromised systems. It primarily targets credentials, browser data, cryptocurrency wallets, and other valuable personal data.
The malware is actively promoted on platforms such as Telegram and Discord, with both free and premium versions available, the latter of which offers enhanced capabilities, including full undetectability (FUD). Additionally, BLX Stealer is engineered to steal browser passwords, gaming platform accounts, and cryptocurrency wallet details while ensuring persistence by dropping its payload in the startup folder, allowing it to survive system reboots.
BLX Stealer was initially advertised on Telegram, where the developer made free and premium versions available.
The malware has the capability to drop its payload into the startup folder, allowing it to persist across system reboots. Additionally, BLX Stealer is capable of stealing:
Furthermore, it can collect gaming session data from platforms like Growtopia.
| File Name | Node.exe |
| File Size | 91.80 MB |
| File Hash | 8c4daf5e4ced10c3b7fd7c17c7c75a158f08867aeb6bccab6da116affa424a89 |
| File Type | Executable |
Process Tree
On running the primary file, multiple processes are triggered, the first of which opens the command prompt as an initial step on execution to run a suspicious command.
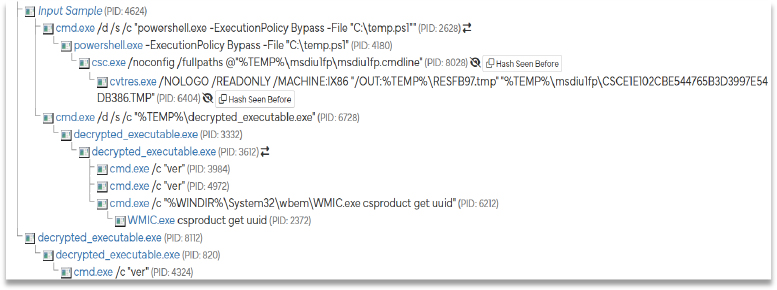
Execution
The command prompt opens and then triggers the below command to bypass the PowerShell file named temp.ps1, which is located in the %Temp% folder.
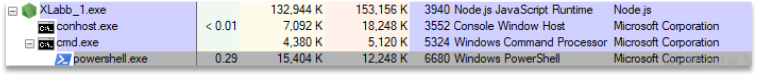
C:\Windows\system32\cmd.exe /d /s /c “powershell.exe -ExecutionPolicy Bypass -File “C:\Users\User \AppData\Local\Temp\temp.ps1
| File Name | Temp.ps1 |
| File Size | 367 Bytes |
| File Hash | D3DA2061327B09F1EBA1B9D5DB0C61DB24B9F6B13BAE96510BB791057067AB34 |
| File Type | PowerShell |
Upon further analysis, we found that the installed script is used to hide the PowerShell window by calling the Windows API functions, which are often used in malware or automation scripts to make the execution of the script invisible to the user by hiding the console window.
In the next execution flow, Csc.exe and Cvtres.exe are triggered, as these are both legitimate Microsoft utilities that can be abused by the malware to compile and manipulate executable files, making them useful tools in the hands of an attacker.
Persistence
Later, it invokes the command run to execute the decrypted_executable file which is dropped in the %TeMP% folder.
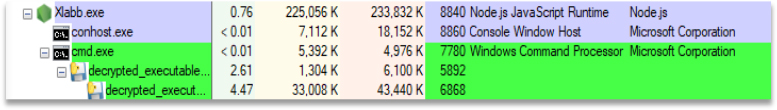
C:\Windows\system32\cmd.exe /d /s /c “C:\Users\Admin\AppData\Local\Temp\decrypted_executable.exe”
The same file is dropped in the users’ %Startup% folder, ensuring the malware runs every time the computer is restarted. The attacker then copies the malware executable to the Startup folder or creates a shortcut in the Startup folder pointing to the malware executable. As a result, each time the user logs in, the malware is executed, maintaining the attacker’s control over the system.
Discovery
From the decrypted executable file, the malware also attempts to discover the victim’s IP and Geolocation details to obtain further information about the target.
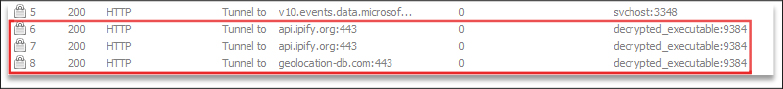
Defense Evasion
The malware executes WMI queries commonly used to detect virtual machines (VMs) which helps the malware identify if it’s running in a sandboxed or virtualized environment.
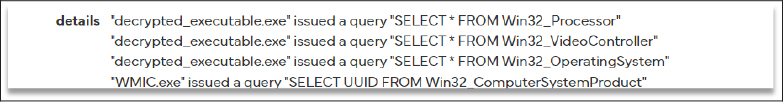
Collection
The Python extension files – which include Python dynamic modules (‘.pyd’ files) and DLLs files – are dropped in the %Temp% folder and named _MEI81882.
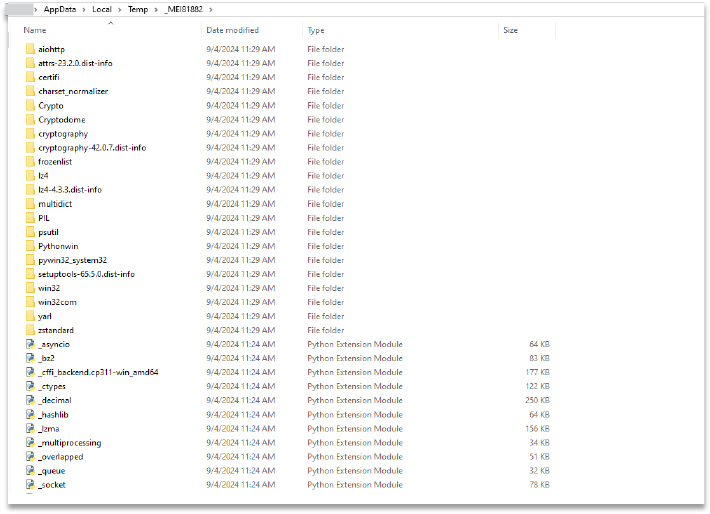
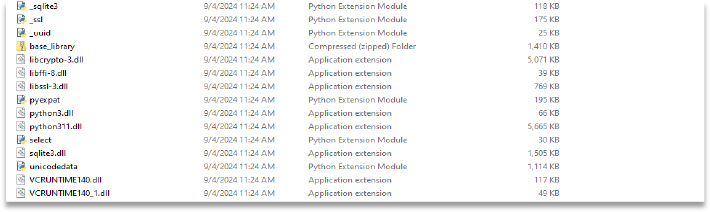
Additionally, within the “base_library” directory, a folder named “collection” was found. No valuable information was identified, however, further investigation into its contents was not pursued.
Credential Access
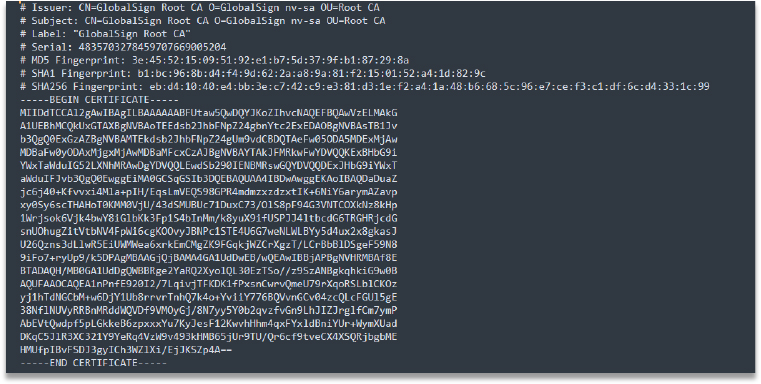
The cacert.pem file (Temp/onefile_1512_…/certifi/cacert.pem) contains multiple CA certificates, which BLX-stealer uses to encrypt data over the network.
Exfiltration
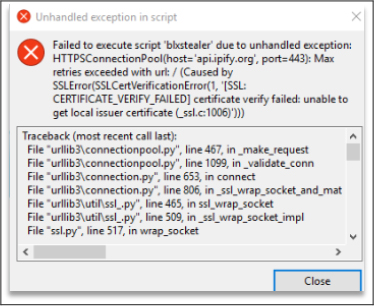
Based on the error shown in the below screenshot, the payload failed to connect to its Command and Control (C2) server due to unhandled exceptions in the script. These errors prevent further analysis of the C2 infrastructure and hinder a deeper understanding of its operational characteristics.
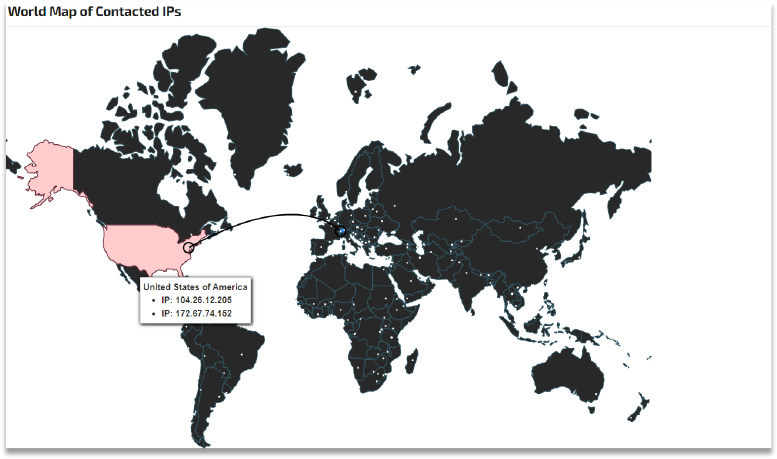
On further OSINT analysis, we found that its server IPs are based in the North American region (however, the IP servers were down at the time of our analysis).
The malware has also been found to use Discord Webhook as a C2 server, enabling data exfiltration to the attacker’s server.
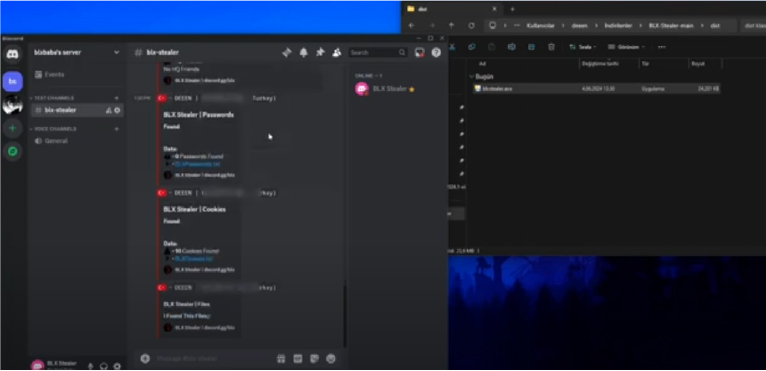
The BLX Stealer, referred to as BLX channel, was established on a Telegram channel on May 28th, 2023, and currently has 473 subscribers.
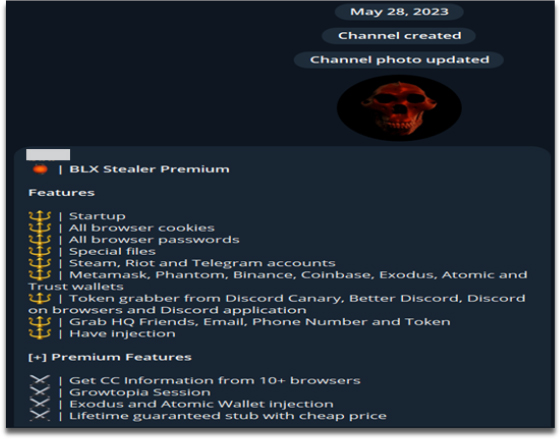
On September 30, 2023, the BLX Stealer expanded its presence by opening an account on Discord. An event, created by a user named blx in the dark, is scheduled until July 2025 at 7:30 PM (as depicted in the attached screenshot).
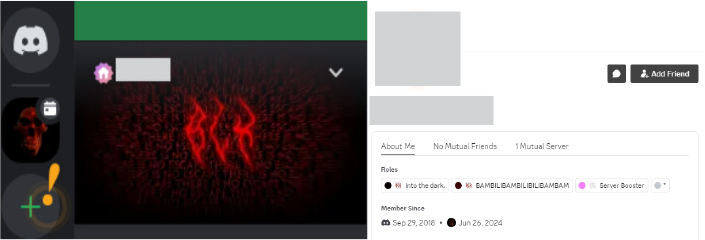
Upon further investigation, the username blx in the dark was also identified on other social media platforms. A YouTube channel under this name was found promoting a video related to the BLX Stealer: the account was created on September 17, 2023; however, the video was uploaded two months prior.
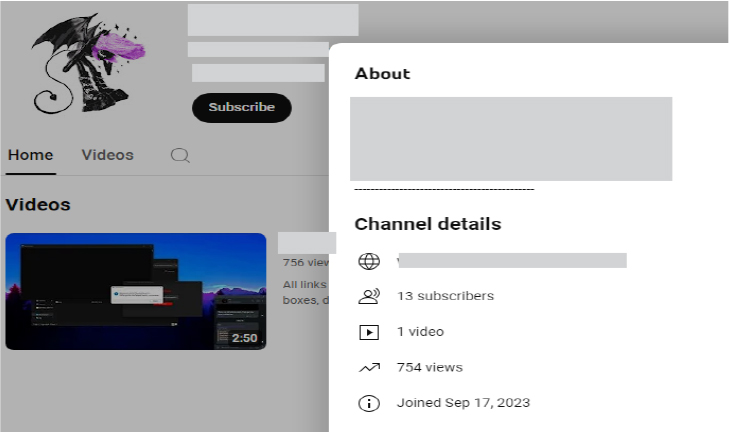
Further investigation revealed that the stealer has been consistently updating its payload to bypass antivirus detection, making the program fully undetectable (FUD). They are offering the BLX Stealer Premium Version with FUD for $25, and FUD for any custom *.exe file for $45, which can be used in other stealers, RATs, clippers, etc.
The BLX Stealer presents a serious cybersecurity threat due to its advanced capabilities in stealing sensitive information and maintaining persistence. Its use of Discord Webhook for exfiltration and continuous updates for antivirus evasion highlight its growing sophistication, therefore, to defend against this evolving threat, organizations must adopt a Zero Trust Security Model, invest in advanced threat intelligence, and enforce strong cybersecurity practices. Proactive measures such as multi-factor authentication (MFA), endpoint detection and response (EDR), and regular security audits are critical in preventing the malicious impact of the BLX Stealer.
| No. | Tactics | Techniques |
| 1. | Execution | T1059.001 – Command and Scripting Interpreter: PowerShell |
| 2. | Execution | T1129 – Shared Modules |
| 3. | Execution | 1059.006 – Command and Scripting Interpreter: Python |
| 4. | Privilege Escalation | T1543 – Create or Modify System Process |
| 5. | Persistence | T1543.003 – Privilege Escalation |
| 6. | Persistence | T1547 – Boot or Logon Autostart Execution |
| 7. | Credential Access | T1649 – Steal or Forge Authentication Certificates |
| 8. | Collection | T1560.001 – Archive via Utility |
| 9. | Collection | T1560.002 – Archive via Library |
| 10. | Discovery | T1016 – System Network Configuration Discovery |
| 11. | Defense Evasion | T1497.001 – System check |
| 12. | Command and Control | T1102 – Web Service |
| File Indicators – Sha256 Hash | File Name |
| 8c4daf5e4ced10c3b7fd7c17c7c75a158f08867aeb6bccab6da116affa424a89 | Node.exe |
| e74dac040ec85d4812b479647e11c3382ca22d6512541e8b42cf8f9fbc7b4af6 | Node.exe |
| 32abb4c0a362618d783c2e6ee2efb4ffe59a2a1000dadc1a6c6da95146c52881 | Decryptable executable |
| 5b46be0364d317ccd66df41bea068962d3aae032ec0c8547613ae2301efa75d6 | Decryptable executable |