



In an exclusive analysis conducted by the CYFIRMA Research team, a critical zero-day vulnerability, CVE-2023-22515, has been unveiled within Atlassian Confluence Data Center and Server. The flaw poses a substantial risk, allowing unauthorized access and critical privilege escalation. The analysis not only dissects the technical intricacies of CVE-2023-22515 but also provides strategic mitigation measures, enhancing the collective defense against this actively exploited threat. This comprehensive analysis serves as a vital resource for organizations striving to fortify their cybersecurity posture amidst the evolving threat landscape.
A critical zero-day vulnerability, CVE-2023-22515, has been uncovered in the Atlassian Confluence Data Center and Server, sparking widespread concern among cybersecurity experts. Exploiting broken access control mechanisms, this vulnerability poses a severe threat to organizations relying on Confluence for collaboration and documentation.
1. Critical Vulnerability (CVE-2023-22515):
A critical zero-day vulnerability, CVE-2023-22515, has been discovered in Atlassian Confluence Data Center and Server.
2. Access Control Exploitation:
Exploiting broken access control, the flaw allows for privilege escalation, raising concerns about unauthorized access and potential data breaches.
3. Active Security Response:
Security teams are actively responding to mitigate the risks associated with vulnerability, emphasizing the need for prompt action.
4. Cross-Source Recognition:
Highlighted by various security sources, including Tenable, S3Curiosity, and Imperva, the vulnerability is widely recognized, underlining its critical nature.
Acknowledgements:
CYFIRMA Research acknowledges the collaborative efforts of security researchers, Atlassian Confluence contributors, and the cybersecurity community in identifying and addressing CVE-2023-22515. The Atlassian team’s prompt response and mitigation efforts are commendable, highlighting the significance of coordinated security research in safeguarding digital ecosystems.
Vulnerability Type: Remote Code Execution (RCE)
CVE ID: CVE-2023-22515
CVSS Severity Score: 10
Application: Atlassian Confluence Data Center and Server
Impact: Remote code execution, unauthorized access, data breaches, network compromise
Severity: Critical
Affected Versions: 8.0.0 to 8.5.1
Patched Available: Yes
CVE-2023-22515 is characterized by a broken access control mechanism in the Atlassian Confluence Data Center and Server. The flaw allows attackers to escalate privileges, gaining unauthorized access to sensitive information and compromising the integrity of the Confluence platform.
The exploitation of this vulnerability can have severe consequences, ranging from unauthorized access to critical data to potential manipulation or deletion of sensitive information. Organizations using Confluence are urged to address this issue promptly to safeguard their digital assets.
This vulnerability affects the Atlassian Confluence Data Center and Server versions up to the reported issue. Organizations using these versions are at risk and should take immediate action. Check here.
Is there already an exploit tool to attack this vulnerability? Yes, a known public exploit tool for CVE-2023-22515 in Atlassian Confluence is available.
Has this vulnerability already been used in an attack? There is no specific information confirming whether CVE-2023-22515 in Atlassian Confluence has been exploited. However, given its critical severity, organizations should remain vigilant and actively monitor their systems for signs of compromise.
Are hackers discussing this vulnerability in the Deep/Dark Web? As per CYFIRMA observation, hackers are actively discussing or exploiting CVE-2023-22515 in the Deep/Dark Web. Continuous monitoring of underground forums and channels is necessary to stay updated on any emerging discussions or potential threats.
What is the attack complexity level? The attack complexity level for CVE-2023-22515 in Atlassian Confluence is currently LOW.
Historical Trends and Known Exploits: Threat actors have historically exploited vulnerabilities in similar software products. Given the pattern of exploiting such vulnerabilities, it is important to acknowledge that threat actors may attempt to exploit CVE-2023-22515 in Atlassian Confluence. This could lead to unauthorized access, data breaches, or network compromise. Organizations should take this risk seriously and apply patches or updates to secure their systems.
Our analysis found that more than 75000 confluence servers are public, which can be vulnerable to CVE-2023-22515 (figure 1.0 below).
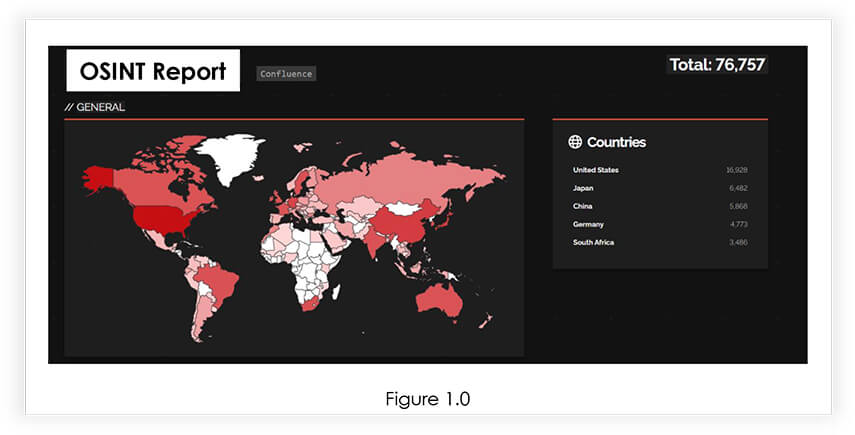
To mitigate CVE-2023-22515, organizations must promptly apply recommended patches from Atlassian. Implementing strict access controls and monitoring systems enhances security, preventing unauthorized access and exploitation. Security teams must remain vigilant and proactive, ensuring the protection of digital environments.
Target Geography: Organizations worldwide that have deployed Atlassian Confluence instances falling within the affected versions may potentially be at risk. Atlassian Confluence is used globally, making the vulnerability relevant to organizations across different geographical regions.
The impact of this vulnerability is not limited by geography but instead extends to any region where Atlassian Confluence is used. As such, organizations in regions such as North America, Europe, Asia-Pacific, and other areas with a significant presence of Atlassian Confluence installations could be exposed to the risk of exploitation.
Target Industry: The CVE-2023-22515 vulnerability in Atlassian Confluence has the potential to affect organizations across a wide spectrum of industries. This includes but is not limited to healthcare, finance, government, telecommunications, and various other sectors that rely on Atlassian Confluence for collaboration and content management.
Threat actors with knowledge of this vulnerability may selectively target industries based on the perceived value of the data or services handled by Atlassian Confluence instances. Organizations dealing with sensitive information or those heavily dependent on Atlassian Confluence’s collaborative capabilities may be particularly attractive targets.
Target Technology: The CVE-2023-22515 vulnerability is specific to Atlassian Confluence, a widely used collaboration and content management tool. While the immediate impact is on Atlassian Confluence instances, it is crucial to recognize that the ramifications of successful exploitation can extend beyond the Confluence environment.
A successful exploitation of this vulnerability can result in unauthorized access to sensitive data, potentially compromising the broader technological ecosystem. This includes servers, applications, and interconnected systems integrated with Atlassian Confluence, amplifying the potential impact on an organization’s technology infrastructure.
Understanding the potential impact on different geographic regions, industries, and technologies helps organizations assess their exposure to the CVE-2023-22515 vulnerability. It underscores the importance of promptly addressing the issue through patching, proactive security measures, and vigilant monitoring to mitigate the risks associated with this vulnerability.
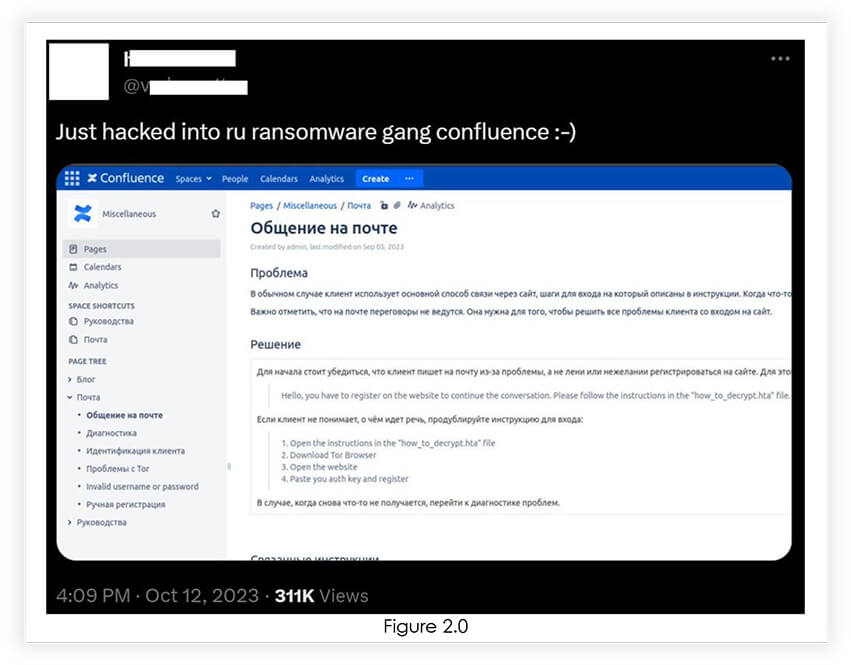
As per our previous analysis, an individual from VX underground compromised a confluence server belonging to Trigona ransomware, using the same vulnerability exploit (figure 2.0).
In Figure 2.1 (below) the VX underground forum has access to the Confluence server, where the onion link can be seen:
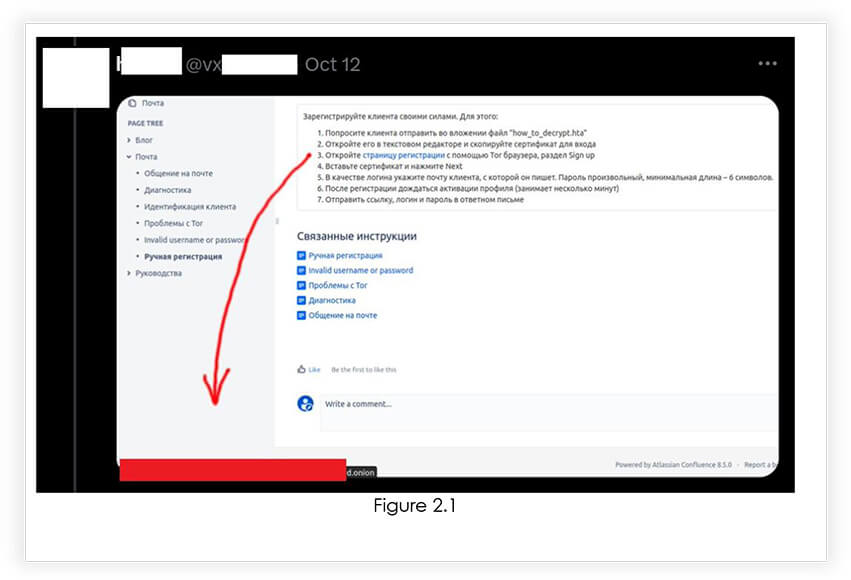
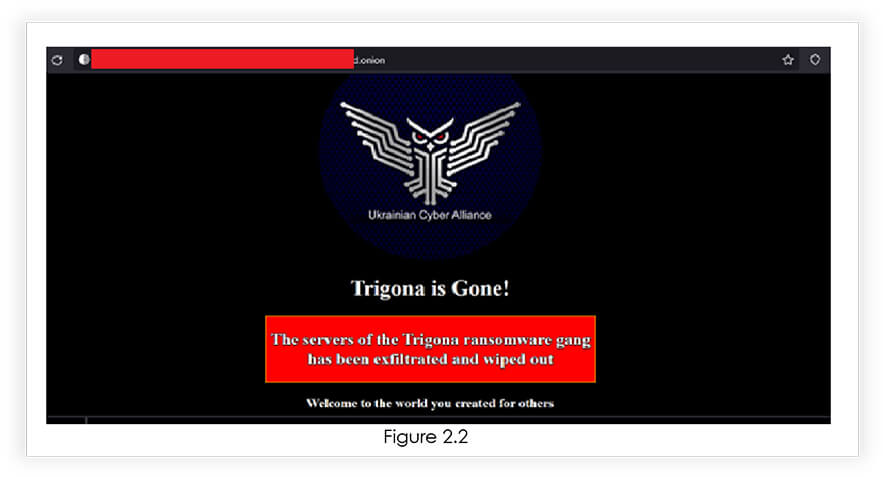
Figure 2.2 (below) demonstrates the removal of Trigona Ransomware’s onion link server by the VX Underground staff member.
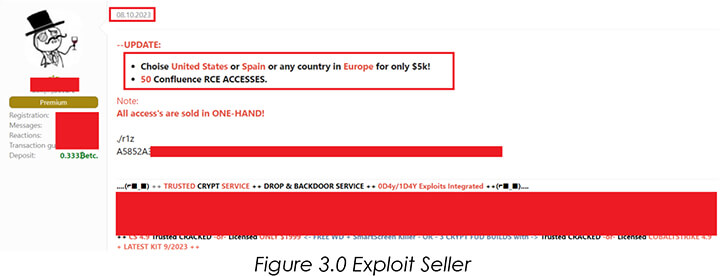
Using the dark web, CYFIRMA researchers have discovered unknown hackers selling Atlassian Confluence Exploits.
In conclusion, the CVE-2023-22515 vulnerability in Atlassian Confluence Data Center and Server represents a critical threat to organizations globally. The broken access control mechanism exposes a pathway for privilege escalation, posing severe risks such as unauthorized access, data breaches, and potential compromise of Confluence platforms. Security teams must act swiftly, applying recommended patches and reinforcing access controls to mitigate the vulnerability’s impact.
The global reach of Atlassian Confluence makes this vulnerability relevant across various geographical regions and industries, emphasizing the need for a widespread response. Threat actors, potentially aware of this flaw, may target industries with valuable data or those heavily reliant on Confluence for collaboration.
CYFIRMA’s observations on hacker discussions in the Deep/Dark Web underscore the urgency of the situation. Active discussions or potential exploitation in these forums heighten the risk, necessitating continuous monitoring and proactive measures.