


APT36, also known as Transparent Tribe, is a Pakistan-based cyber espionage group that has been actively targeting Indian defense personnel through highly sophisticated phishing campaigns. According to CYFIRMA’s findings, the group disseminates phishing emails containing malicious PDF attachments that are meticulously designed to resemble official government documents.
When a recipient opens one of these PDFs, it displays a blurred background along with a button that imitates the login interface of the National Informatics Centre (NIC). Clicking this button redirects a user to a fraudulent URL and initiates the download of a ZIP archive containing a malicious executable file, which is disguised as a legitimate application.
This campaign highlights APT36’s ongoing emphasis on credential theft and its strategic objective of establishing long-term infiltration within Indian defense networks. The operation highlights the urgent need for robust email security mechanisms, comprehensive user awareness programs, and proactive threat detection and monitoring systems to mitigate such targeted cyber threats.
In today’s increasingly complex cyber threat landscape, nation-state actors continue to evolve their tactics to conduct targeted espionage. One such threat actor is “APT36” (AKA Transparent Tribe), a Pakistan-based cyber-espionage group, which has come under renewed scrutiny for its sophisticated campaigns aimed at infiltrating India’s defense infrastructure.
The group distributes malicious PDFs that mimic official documents and lead users to fake NIC login pages, ultimately downloading disguised malware with the aim of credential-harvesting for long-term access to sensitive networks. This highlights the urgent need for strong email security, user awareness training, and continuous threat monitoring.
| Target Technologies | Windows Operating System |
| Threat Type | Phishing Campaign |
| Written In | C/C++ |
| File Types | PE (Portable Executable) |
| Key Malware Identifiers | PO-003443125.pdf, PO-003443125.pdf.7z |
| Observed First | 2025-05-07 |
| Impact | Credential Harvesting, Data Exfiltration |
| MD5 Hashes | PO-003443125.pdf “6ee3b0f4cb84e18751e7088043741e9a” PO-003443125.pdf.7z“cdb9fb87dcb44d8f3040f4fb87d89508” PO-003443125.pdf.exe “154f4cdcd4b822314293ad566d7255fa” |
In this campaign, the group distributes phishing emails containing an embedded PDF file named “PO-003443125.pdf”.
When opened, the document presents a blurred background (a deliberate tactic used to create a false sense of authenticity), a PDF icon, the file name “PO-003443125.pdf”, and a message stating: “This is a protected document. Click the button below to access content”. A prominently displayed button – labeled “Click to View Document” – lures the recipient to engage.
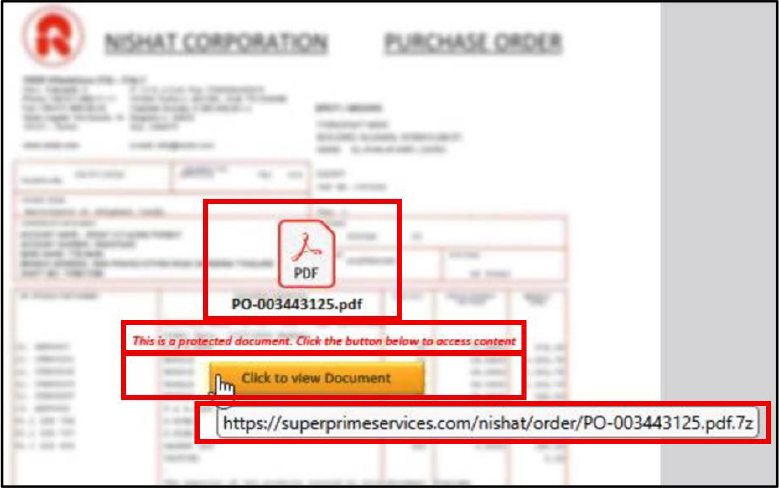
Upon interaction, the user is redirected to a malicious URL “hXXps://superprimeservices[.]com/nishat/order/PO-003443125.pdf.7z”, that initiates the download of a “PO-003443125.pdf.7z” archive.
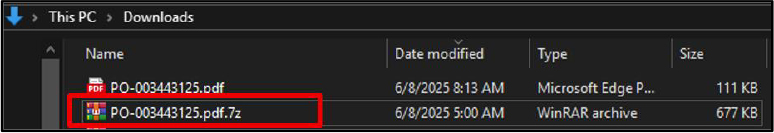
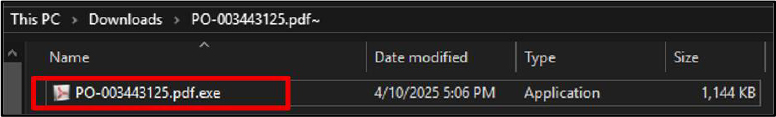
The archive contains a malicious executable file named “PO-003443125.pdf.exe”, deceptively displaying a PDF icon to appear legitimate. This file is crafted to mislead users and when executed, can compromise the target system by enabling unauthorized access.
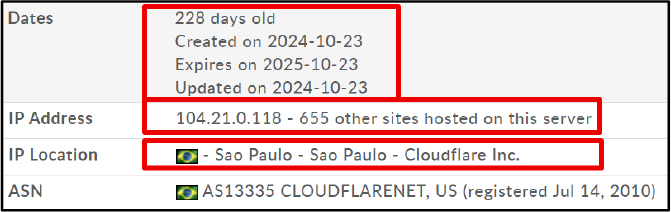
The domain in question was registered on October 23, 2024, with an expiration date of October 23, 2025, indicating its recent creation and potential use for short-term malicious purposes. It resolves to the IP address 104[.]21[.]0[.]118, which is hosted by Cloudflare Inc. in São Paulo, Brazil, and is currently shared with more than 655 other domains.
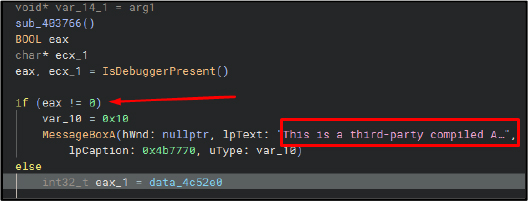
Upon further investigation, it is revealed that the executable file is built by using a freeware scripting language.
The Windows API function “IsDebuggerPresent” is commonly utilized as an anti-analysis technique to determine whether the program is being executed within a debugging environment, such as x64dbg, WinDbg, or OllyDbg. If detected, the malware displays a critical message (“This is a third-party compiled script”) and then terminates the process.
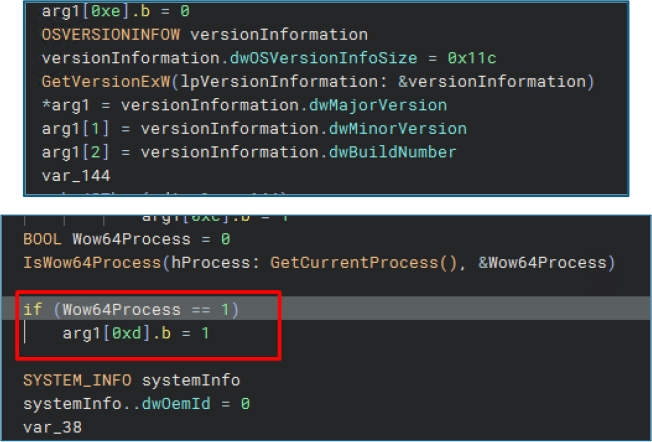
The malware uses IsWow64Process to detect if it’s running in a 32-bit process on a 64-bit system, a common sign of an analysis environment.
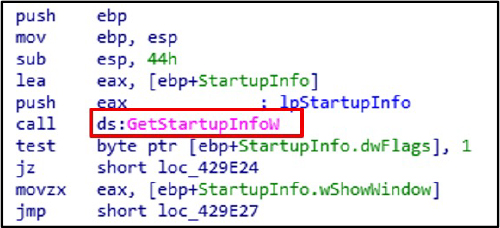
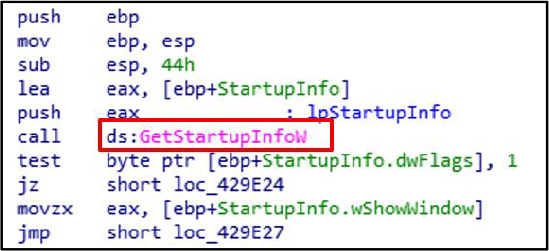
The GetStartupInfo function obtains process startup parameters. The malware uses it to adapt execution and enhance stealth.
FindResourceExW locates a resource named “SCRIPT”, type 0x0A in its own module. It then loads and locks this resource, obtaining its size and data, which is written into a stream created via CreateStreamOnHGlobal.
Finally, it invokes method calls (likely COM or ActiveScript interfaces) to execute or parse the embedded script, enabling fileless or in-memory execution.
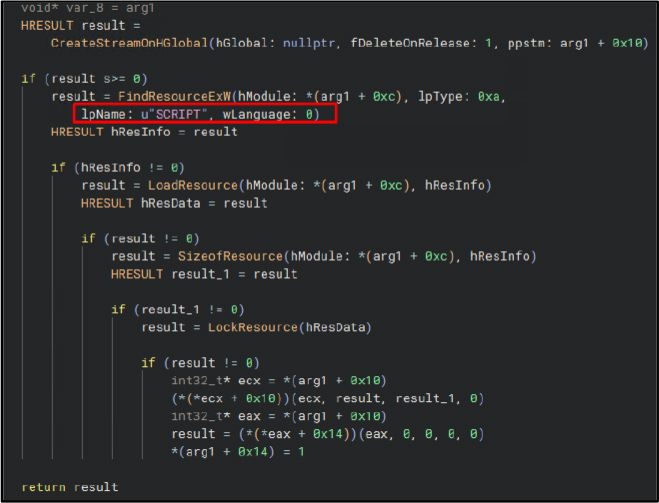
ShellExecuteW is used to trigger secondary stages of an attack.
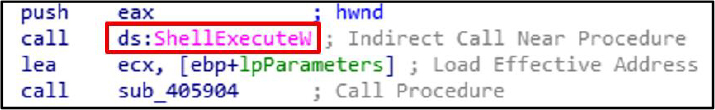
The OpenWindowStationW, GetProcessWindowStation, SetProcessWindowStation, and OpenDesktopW functions are used to access and manipulate window stations and desktops, enabling the malware to interact with user sessions, inject code, evade detection, and maintain persistence within targeted environments.
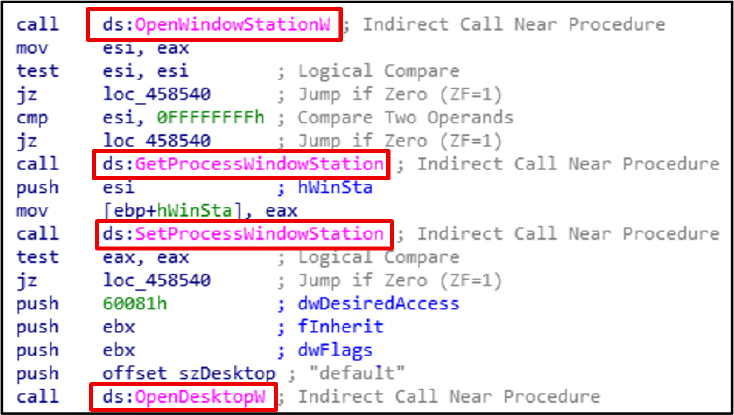
The Sleep function suspends execution temporarily. The malware leverages it to delay activities, evade analysis, and avoid detection.
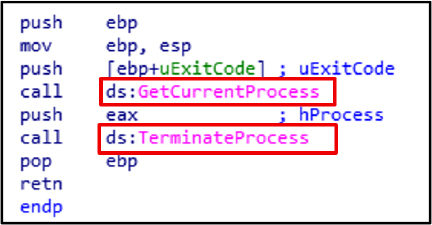
The malware uses GetCurrentProcess and TerminateProcess for process control, privilege escalation, code injection, and anti-analysis.
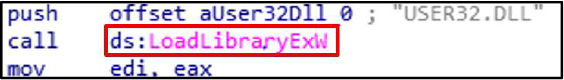
The LoadLibraryExW function loads a DLL into a process address space, which attackers exploit for DLL side-loading to execute malicious code by loading unauthorized libraries through legitimate applications.
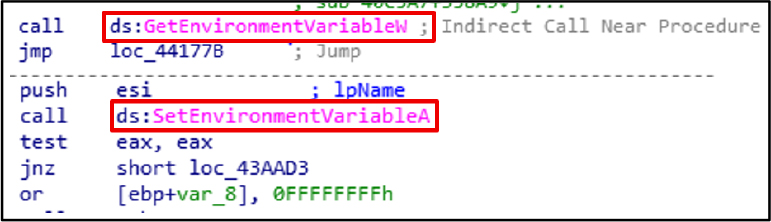
SetEnvironmentVariableA and GetEnvironmentVariableW are used by the malware to modify and access system environment variables, supporting persistence, configuration, and evasion techniques.
The GetStartupInfo function obtains process startup parameters. The malware uses it to adapt execution and enhance stealth.
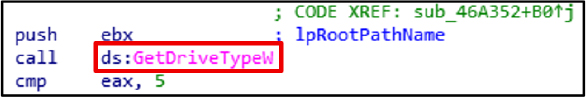
GetDriveTypeW is used by attackers to identify removable or network drives as targets for their attacks.
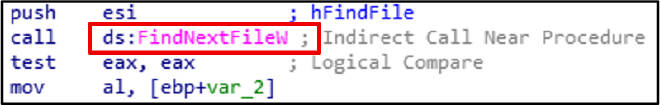
FindNextFileExW is used to search the files in the directory for data exfiltration.
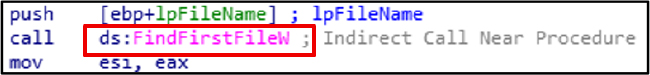
FileNextFilew is used to continue the files enumeration started by FindFirstFileExW
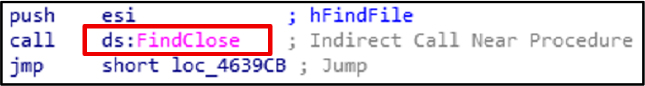
FileClose is used to release the handle from FindFirstFileExW.
The GetForegroundWindow function is used to identify the currently active window, often to capture user activity.
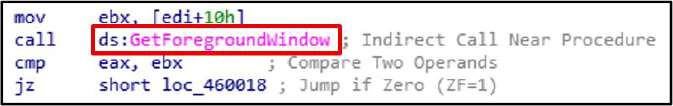
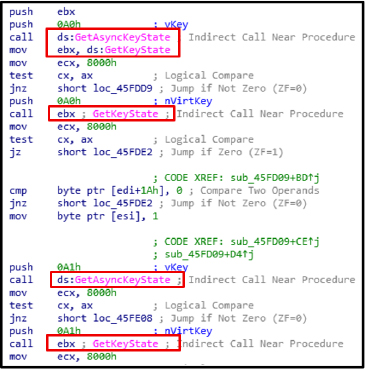
The functions GetAsyncKeyState and GetKeyState are utilized to monitor and capture keystrokes in real time. The malware leverages these APIs to detect user input, facilitating keylogging activities and enabling the theft of sensitive data, such as credentials and confidential messages.
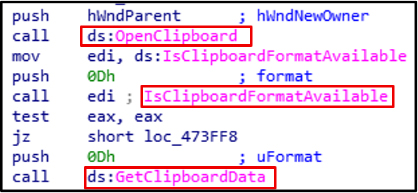
OpenClipboard, IsClipboardFormatAvailable, and GetClipboardData are used to access clipboard contents and steal sensitive information, such as copied passwords or cryptocurrency wallet addresses.
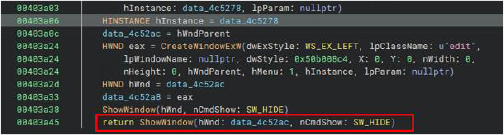
The program creates a concealed window with a specific class name and embeds an “edit” control as its child. Both the parent and child windows are hidden using standard window manipulation functions (e.g., ShowWindow with the SW_HIDE flag). This configuration allows the script to simulate user interactions in a covert manner, potentially evading basic keylogger or automation detection mechanisms by mimicking the behavior of legitimate applications.
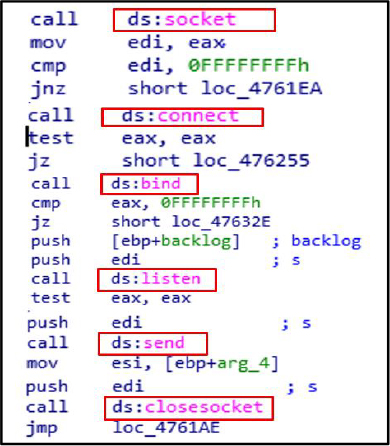
Malware utilizes the socket, connect, bind, listen, send, and closesocket functions to establish, manage, and terminate network communications. These functions facilitate command-and-control (C2) interactions, data exfiltration, and remote access operations.
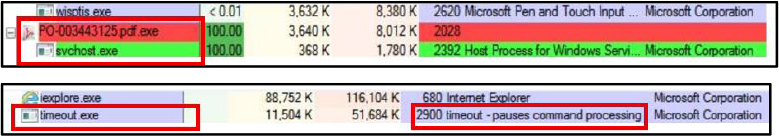
Anti-Analysis Behavior: The executable PO-003443125[.]pdf[.]exe exhibits anti-analysis behaviour by masquerading as a legitimate PDF document. This naming convention is intentionally misleading, designed to trick users and evade casual detection by analysts or basic security tools that may not display full file extensions. Additionally, spawning a legitimate-looking Windows process (svchost.exe) as a child can be an attempt to blend into normal system activity and avoid suspicion during manual inspection or automated monitoring.
Process Activity: The process tree shows PO-003443125[.]pdf[.]exe as a parent process launching svchost.exe as a child. This is anomalous, as svchost.exe is typically started by the Windows operating system, not by user-launched applications. The parent process is consuming 100% of a CPU core, which may indicate resource-intensive malicious behavior such as crypto mining, keylogging, or network beaconing. This irregular activity pattern is a strong indicator of potential malware execution.
Obfuscation: The file uses a double extension (.pdf.exe), a classic obfuscation technique to appear benign. This approach leverages the common user setting in Windows that hides known file extensions, thereby displaying the file deceptively as a harmless PDF. This technique is frequently used to bypass user scrutiny and simple file-type filters, increasing the chances of successful execution.
Credential and Data Theft: The malware targets browser data cookies, saved credentials, form inputs, email client credentials, and system clipboard contents. It employs form-grabbing techniques, keylogging via API hooks, and clipboard surveillance to exfiltrate sensitive data before it is encrypted or masked by legitimate applications.
Network Communication: DNS queries to multiple low-reputation and malicious domains, many using suspicious TLDs like .xyz, .buzz, .ru, and .sbs, are observed.
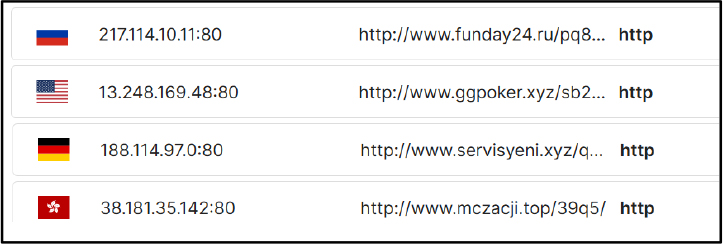
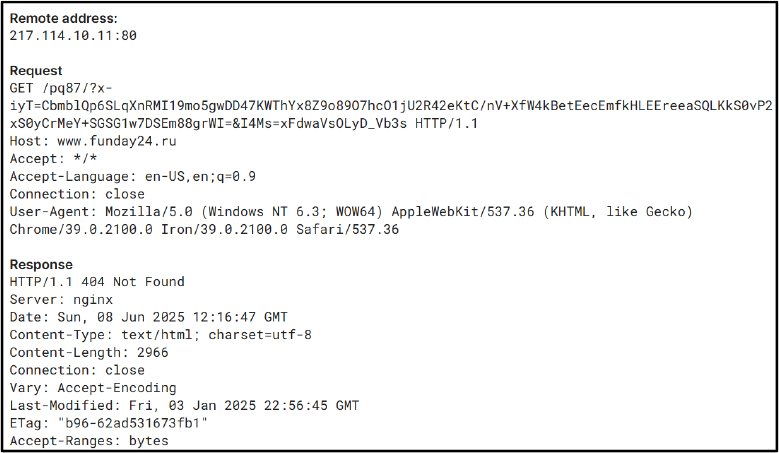
Encrypted HTTP(S) communication with C2 servers is detected, with infrastructure hosted on major CDN providers (e.g., Cloudflare, AWS), likely for concealment and delivery resilience.
| MITRE MAPPING | ||
| Tactic | ID | Technique Name |
| Initial Access | T1566 | Phishing |
| T1566.001 | Spear phishing Attachment | |
| Execution | T1203 | Exploitation for Client Execution |
| T1059 | Command and Scripting Interpreter | |
| Persistence | 1542 | Pre-OS Boot |
| T1542.003 | Bootkit | |
| T1574 | Hijack Execution Flow | |
| T1574.002 | DLL Side-Loading | |
| T1112 | Modify Registry | |
| T1547 | Boot or Logon AutoStart Execution | |
| T1547.009 | Shortcut Modification | |
| Privilege Escalation | T1055 | Process Injection |
| T1574 | Hijack Execution Flow | |
| T1574.002 | DLL Side-Loading | |
| T1134 | Access Token Manipulation | |
| T1134.001 | Token Impersonation/ Theft | |
| T1547 | Boot or Logon AutoStart Execution | |
| T1547.009 | Shortcut Modification | |
| Defense Evasion | T1014 | Rootkit |
| T1036 | Masquerading | |
| T1055 | Process Injection | |
| T1542 | Pre-OS Boot | |
| T1542.003 | Bootkit | |
| T1564 | Hide Artifacts | |
| T1564.001 | Hidden Files and Directories | |
| T1564.003 | Hidden Window | |
| T1497 | Virtualization/Sandbox Evasion | |
| T1562 | Impair Defenses | |
| T1562.001 | Disable or Modify Tools | |
| T1027 | Obfuscated Files of Information | |
| T1027.002 | Software Packing | |
| T1112 | Modify Registry | |
| T1134 | Access Token Manipulation | |
| T1134.001 | Token Impersonation/ Theft | |
| T1222 | Files and Directory Permission Modification | |
| T1497.002 | User Activity Based Checks | |
| T1574 | Hijack Execution Flow | |
| T1574.002 | DLL Side-Loading | |
| Credential Access | T1003 | OS Credential Dumping |
| T1056 | Input Capture | |
| T1056.001 | Keylogging | |
| Discovery | T1012 | Query Registry |
| T1057 | Process Discovery | |
| T1083 | Files and Directory Discovery | |
| T1010 | Application Window Discovery | |
| T1082 | System Information Discovery | |
| T1497 | Virtualization/Sandbox Evasion | |
| T1518 | Software Discovery | |
| T1518.001 | Security Software Discovery | |
| T1016 | System Network Configuration Discovery | |
| T1018 | Remote System Discovery | |
| T1614 | System Location Discovery | |
| T1033 | System Owner/User Discovery | |
| T1087 | Account Discovery | |
| T1497.002 | User Activity Based Checks | |
| T1614.001 | System Language Discovery | |
| Collection | T1005 | Data from Local System |
| T1114 | Email Collection | |
| T1057 | Input Capture | |
| T1056.001 | Keylogging | |
| T1113 | Screen Capture | |
| T1115 | Clipboard Data | |
| T1185 | Browser Session Hijacking | |
| Command and control | T1071 | Application Layer Protocol |
| T1095 | Non-Application Layer Protocol | |
| T1573 | Encrypted Channel | |
| T1105 | Ingress Tool Transfer | |
| Impact | T1485 | Data Destruction |
| T1496 | Resource Hijacking | |
| T1529 | System Shutdown/Reboot | |
APT36 poses a significant and ongoing cyber threat to national security, specifically targeting Indian defense infrastructure. The group’s use of advanced phishing tactics and credential theft exemplifies the evolving sophistication of modern cyber espionage. Addressing this challenge requires the implementation of a comprehensive, multi-layered cybersecurity framework, encompassing robust email security measures, continuous user education, and vigilant threat detection and response capabilities.
Based on the detailed analysis of the APT36 campaign targeting Indian defense personnel through phishing emails and disguised malware, CYFIRMA recommends the following recommendations and mitigation strategies are specifically tailored for the Indian defense sector:
Enhance Email Security Infrastructure
User Awareness and Training
Network and Endpoint Security
Access Control and Authentication
Infrastructure and Threat Intelligence Monitoring
Incident Response Preparedness
Stay updated with CYFIRMA’s threat intelligence sharing platform to effectively detect emerging TTPs, enhance situational awareness, and enable timely mitigation of threats relevant to your industry and region.
Leverage YARA rules and Indicators of Compromise (IOCs) provided by CYFIRMA to enhance the detection of malicious files and behavior through file integrity monitoring and behavioral analysis. Regularly update them on your SIEM platform.
Kindly refer to the IOCs section to exercise controls on your security systems.
| S.No | Indicator | Remarks | |
| 1 | f03ac870cb91c00b51ddf29b6028d9ddf42477970eafa7c556e3a3d74ada25c9 | Block | |
| 2 | 55b7e20e42b57a32db29ea3f65d0fd2b2858aaeb9307b0ebbcdad1b0fcfd8059 | Block | |
| 3 | 55972edf001fd5afb1045bd96da835841c39fec4e3d47643e6a5dd793c904332 | Block | |
| 4 | SuperPrimeServices[.]com | Block | |
| 5 | Advising-Receipts[.]com | Block | |
| 6 | FunDay24[.]ru | Block | |
| 7 | slotgacorterbaru[.]xyz | Monitor | |
| 8 | servisyeni[.]xyz | Monitor | |
| 9 | chillchad[.]xyz | Monitor | |
| 10 | ggpoker[.]xyz | Monitor | |
| 11 | boldcatchpoint[.]shop | Monitor | |
| 12 | zhangthird[.]shop | Monitor | |
| 13 | vipwin[.]buzz | Monitor | |
| 14 | wholly-well[.]info | Monitor | |
| 15 | rapio[.]site | Monitor | |
| 16 | 55cc[.]info | Monitor | |
| 17 | megasofteware[.]net | Monitor | |
| 18 | worrr19[.]sbs | Monitor | |
| 19 | kp85[.]cyou | Monitor | |
| 20 | mczacji[.]top | Monitor | |
| 21 | 59292406[.]xyz | Monitor | |
| 22 | 76[.]223[.]54[.]146 | Monitor | |
| 23 | 188[.]114[.]97[.]7 | Monitor | |
| 24 | 13[.]248[.]169[.]48 | Monitor | |
| 25 | 84[.]32[.]84[.]32 | Monitor | |
| 26 | 217[.]114[.]10[.]11 | Monitor | |
| 27 | 207[.]244[.]126[.]106 | Monitor | |
| 28 | 172[.]67[.]148[.]140 | Monitor | |
| 29 | 198[.]252[.]111[.]31 | Monitor | |
| 30 | 15[.]197[.]148[.]33 | Monitor | |
| 31 | 162[.]254[.]38[.]217 | Monitor | |
| 32 | 104[.]21[.]41[.]144 | Monitor | |
rule APT36_IOCs_Indicators
{
meta:
author = “Cyfirma Research”
description = “Detects known APT36-related indicators (hashes, IP, domains)”
date = “2025-06-08”
threat_group = “APT36 / Transparent Tribe”
strings:
// SHA256 file hashes (can be used for memory or file scan)
$hash1 = “f03ac870cb91c00b51ddf29b6028d9ddf42477970eafa7c556e3a3d74ada25c9”
$hash2 = “55b7e20e42b57a32db29ea3f65d0fd2b2858aaeb9307b0ebbcdad1b0fcfd8059”
$hash3 = “55972edf001fd5afb1045bd96da835841c39fec4e3d47643e6a5dd793c904332”
// Domains used by APT36
$domain1 = “SuperPrimeServices.com”
$domain2 = “Advising-Receipts.com”
$domain3 = “FunDay24.ru”
$domain4 = “slotgacorterbaru.xyz”
$domain5 = “servisyeni.xyz”
$domain6 = “chillchad.xyz”
$domain7 = “ggpoker.xyz”
$domain8 = “boldcatchpoint.shop”
$domain9 = “zhangthird.shop”
$domain10 = “vipwin.buzz”
$domain11 = “wholly-well.info”
$domain12 = “rapio.site”
$domain13 = “55cc.info”
$domain14 = “megasofteware.net”
$domain15 = “worrr19.sbs”
$domain16 = “kp85.cyou”
$domain17 = “mczacji.top”
$domain18 = “59292406.xyz”
// IPs used by APT36
$ip1 = “76.223.54.146”
$ip2= “188.114.97.7”
$ip3= “13.248.169.48”
$ip4= “84.32.84.32”
$ip5= “217.114.10.11”
$ip6= “207.244.126.106”
$ip7= “172.67.148.140”
$ip8= “198.252.111.31”
$ip9= “15.197.148.33”
$ip10= “162.254.38.217”
$ip11= “104.21.41.144”
condition:
any of ($hash*) or any of ($domain*) or any of ($ip*)
}