Published On : 2024-10-15
Volt Typhoon is a Chinese state-sponsored hacker group that has been targeting critical infrastructure in the United States and other countries. The group is believed to be working on behalf of the Chinese government and has been accused of conducting espionage and sabotage.
Alias: BRONZE SILHOUETTE, Dev-0391, Insidious Taurus, UNC3236, Vanguard Panda, Voltzite
Motivation: Espionage, Information theft, Intelligence gathering
Target Technologies: Cisco, Net Gear routers, SOHO routers, firewalls & VPN, Zoho
Techniques: Credential Harvesting, Custom Malware Implant, Spear-Phishing, Vulnerabilities & Exploits, Living of the land
Targeted Countries
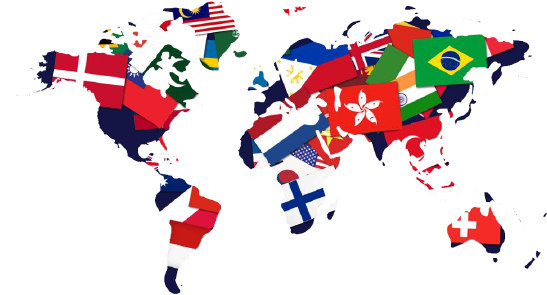
The United States of America, the United Kingdom, Canada, India, Japan, Taiwan, South Korea, New Zealand, and Australia
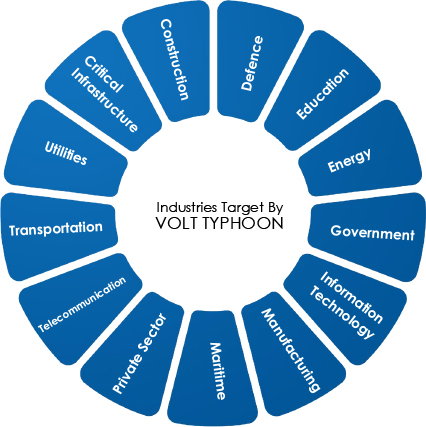
Volt Typhoon Campaigns Tracked by CYFIRMA
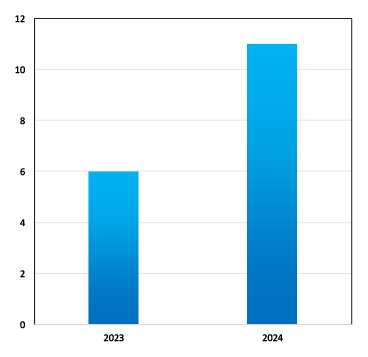
Volt Typhoon’s Recent Campaign Highlights and Trends
- Recent reports indicate that the Volt Typhoon has been exploiting zero-day vulnerabilities in software like Versa Director, which is widely used by Internet service providers and managed service providers.
- In the recent campaign the China-based threat actor, Volt Typhoon targeted various sectors globally. They use operational relay box networks (ORBs), comprising virtual private servers (VPS), compromised IoT devices, and routers, to disguise external traffic and evade detection. The ORBs are run of stolen or leased proxies or via home or small office routers. Their motive is believed to be espionage, using these networks to gain an advantage and potentially disrupt critical infrastructure.
- The threat actor, Volt Typhoon, has targeted various organizations across various sectors. These include communication, manufacturing, utility, transportation, construction, maritime, government, information technology, and education sectors. They issue commands via the command line to collect data, including credentials from local and network systems. They then put the data into an archive file to stage it for exfiltration and use the stolen valid credentials to maintain persistence.