Published On : 2025-01-09
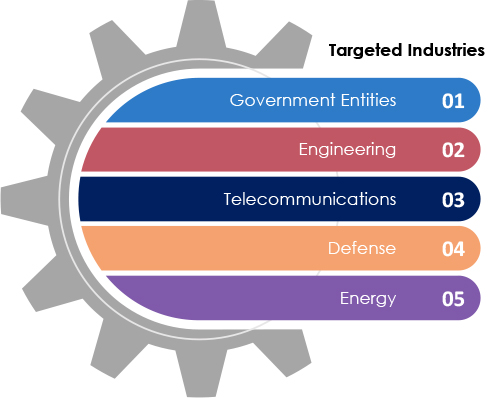
Threat actor TA397, also known as Bitter, is a South Asia-nexus cyber espionage group targeting government, energy, telecommunications, defense, and engineering organizations in the EMEA and APAC regions. Their operations typically involve spear-phishing emails with malicious attachments, leading to the installation of remote access trojans (RATs) like WmRAT and MiyaRAT. These RATs enable the attackers to steal sensitive information and intellectual property.
Alias: Bitter
Motivation: Information Theft and Espionage
Target Technologies:
Office Suites Software, Operating System, Web Application
Targeted Regions:
EMEA (Europe, Middle East, and Africa) and APAC (Asia-Pacific).
Malware used by TA397:
ArtraDownloade, BitterRAT, WmRAT, and MiyaRAT
Targeted Countries
Saudi Arabia, Turkey, Bangladesh, China, Pakistan
Recently Exploited Vulnerabilities by TA397
- CVE-2018-0802
- CVE-2017-11882
- CVE-2021-26858
- CVE-2021-27065
Here are some key highlights and trends from their recent activities:
- Targeted Spearphishing: TA397 has been using highly targeted spearphishing emails to deliver malware. For instance, a recent campaign targeted a Turkish defense sector organization with emails about public infrastructure projects in Madagascar.
- Advanced Techniques: The group employs advanced techniques such as using RAR archives with alternate data streams (ADS) to deliver malicious payloads. These archives often contain decoy PDF files and malicious LNK files that execute PowerShell code to download further payloads.
- Malware Deployment: TA397 has been observed deploying two main types of malware: WmRAT and MiyaRAT. WmRAT is a legacy tool used for gathering system data and exfiltrating files, while MiyaRAT is a newer, more sophisticated tool with advanced encryption and reverse shell capabilities.
- Persistence and Exfiltration: The campaigns often establish scheduled tasks to ensure persistence and enable regular communication with command and control (C2) servers. This allows the attackers to exfiltrate data and deliver additional payloads.
- Infrastructure: TA397’s infrastructure includes staging and C2 domains that are meticulously planned. They use domains like jacknwoods[.]com for staging and academymusica[.]com for C2 communication.