


MISSION2025 is a Chinese state-sponsored advanced persistent threat (APT) group linked to APT41. Active since at least 2012, the group has conducted cyberespionage and financially motivated campaigns targeting over 40 industries globally. Its operations align with China’s strategic economic goals, particularly the “Made in China 2025” initiative, focusing on intellectual property (IP) theft, corporate espionage, and infrastructure compromise.
Alias: APT 41, APT-41, BARIUM, Blackfly, Brass Typhoon, BrazenBamboo, Double Dragon, Earth Baku, Earth Freybug, Earth Longzhi, Gref, Hodoo, IQGRABBER, Mana Mr. StealYoShoes, PassCV, RedGolf, SparklingGoblin, UNC78, UNIT2025, Winnti, Winnti Umbrella Group
Motivation: Cyberespionage, Financial Gain, Strategic Disruption
Target Technologies: Office Suites Software, Operating System, Web Application
Targeted Industries
Targeted Countries: U.S.A., UK, Japan, India, EU nations, Southeast Asia, and Taiwan

Tools Used:
LOWKEY, GH0ST, Meterpreter, BlackCoffee MessageTap, Living off the Land, Crackshot, EASYNIGHT, Derusbi, HDRoot, FRONTWHEEL, XDOOR, ASPXSpy, DIRTCLEANER, TERA, HKDOOR, X-DOOR.
Credential Stealing malwares such as ACEHASH, BIOPASS RAT, Cobalt Strike, HighNote, PlugX, pwdump, Barlaiy, LIFEBOAT, Mimikatz, POTROAST, DOWNTIME, Jumpall, WIDETONE, Skip-2.0, China Chopper, RedXOR, ZXShell, COLDJAVA, CROSSWALK, GearShift, NTDSDump, ROCKBOOT, WINTERLOVE, DEADEYE, ADORE.XSEC, PipeMon, TIDYELF, PACMAN, certutil, ShadowPad Winnti, xDll, HIGHNOON, LATELUNCH, SAGEHIRE
Malware used by MISSION2025:
DeepData Framework, China Chopper, Speculoos Backdoor, PRIVATELOG Loader, CUNNINGPIGEON Backdoor, gh0st RAT, Derusbi, SHADOWGAZE Backdoor, njRAT, BLACKCOFFEE, WINDJAMMER Malware, ASPXSpy, ZxShell, UNAPIMON Malware, DEATHLOTUS Backdoor, MoonBounce, Winnkit, WyrmSpy, TOUGHPROGRESS, DragonEgg, UNAPIMON, Winnti, ROCKBOOT, DUSTPAN, LightSpy
| Resource Development | Persistence | Defense Evasion |
| T1588.002 | T1542.003 | T1027 |
| T1546.008 | T1112 | |
| Initial Access | T1574.001 | T1070.001 |
| T1078 | T1543.003 | T1014 |
| T1133 | T1078 | T1055 |
| T1566.001 | T1133 | T1078 |
| T1195.002 | T1197 | T1197 |
| T1190 | T1053.005 | T1480.001 |
| T1574.006 | T1218.011 | |
| Execution | T1136.001 | T1542.003 |
| T1203 | T1574.002 | T1574.001 |
| T1047 | T1547.001 | T1036.005 |
| T1569.002 | T1218.001 | |
| T1053.005 | Privilege Escalation | T1553.002 |
| T1059.003 | T1546.008 | T1036.004 |
| T1059.001 | T1574.001 | T1574.006 |
| T1059.004 | T1543.003 | T1070.004 |
| T1055 | T1574.002 | |
| Credential Access | T1078 | T1070.003 |
| T1110.002 | T1053.005 | |
| T1056.001 | T1574.006 | |
| T1003.001 | T1574.002 | |
| T1547.001 |
| CVE-2017-0199 |
| CVE-2017-0147 |
| CVE-2017-11882 |
| CVE-2021-44228 |
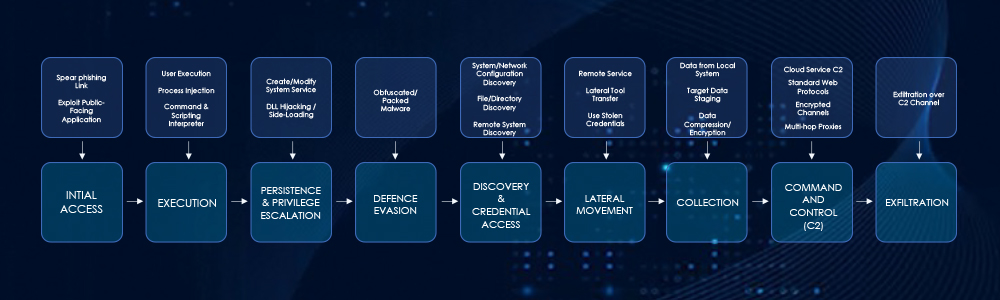
MISSION2025(APT41) Recent Campaign Highlights
Based on observations, here are MISSION2025(APT41’s) TTPs mapped to the MITRE ATT&CK framework:
1. Initial Access
Spearphishing Attachment: Sending targeted emails with malicious attachments (e.g., ZIP archives containing LNK files masquerading as PDFs).
Spearphishing Link: Delivering links to malicious payloads hosted on compromised or free web hosting sites.
Exploit Public-Facing Application: Actively exploiting vulnerabilities in popular enterprise software (e.g., Ivanti EPMM, historical use of SQL injections in web applications, server virtualization software).
External Remote Services: Exploiting legitimate remote access solutions for initial access or persistence.
2. Execution
User Execution: Malicious File: Relying on victims to open malicious files (e.g., LNK files, disguised documents).
Command and Scripting Interpreter: Windows Command Shell: Using cmd.exe for various commands.
Command and Scripting Interpreter: PowerShell: Often used for fileless execution or scripting.
Windows Management Instrumentation (WMI): For execution and potentially lateral movement.
Process Injection: Injecting malicious code into legitimate processes (e.g., PLUSINJECT performing process hollowing on svchost.exe).
System Services: Service Execution: Creating or modifying services for execution.
3. Persistence
Create or Modify System Process: Windows Service: Creating new services for persistence.
Boot or Logon Autostart Execution: Registry Run Keys / Startup Folder: Modifying registry keys for autostart.
BITS Jobs: Utilizing Background Intelligent Transfer Service for persistence or data transfer.
Hijack Execution Flow: DLL Search Order Hijacking/DLL Side-Loading/Dynamic Linker Hijacking: Techniques to load malicious DLLs by manipulating legitimate program’s loading processes.
Scheduled Task/Job: Scheduled Task: Creating scheduled tasks for recurring execution.