


The Lazarus Group is a highly sophisticated, state-sponsored cyber threat group attributed to the North Korean government. They are also known by many other names, including Hidden Cobra, APT38, and Guardians of Peace. Active since at least 2009, this group is one of the most prolific and dangerous advanced persistent threat (APT) actors in the world. Their attacks are not only for cyber espionage but also for financially motivated cybercrime, which sets them apart from most other state-backed actors.
Alias:
Onyx Sleet, APT 38, APT-38, APT38, Alluring Pisces, Andariel, AppleJeus, Appleworm, Bluenoroff, Bureau 121, CL-STA-240, CageyChameleon, Chollima, Citrine Sleet, Covellite, CryptoCore, Dark Seoul, Diamond Sleet, Group 77, Group77, Guardians of Peace, Hastati Group, Hidden Cobra, Jade Sleet, Jumpy Pisces, Labyrinth Chollima, Lazarus, Moonstone Sleet, NICKEL ACADEMY, NewRomanic Cyber Army Team, Operation DarkSeoul, Operation GhostSecret, Operation Troy, PUKCHONG, REF9135, Sapphire Sleet, Silent Chollima, Slow Pisces, Stardust, Stonefly group, TA444, TraderTraitor, UNC4899, Unit 121, Who is Hacking Team, ZINC
Motivation:
Financial Gain, Espionage, Political Agenda.
Targeted Industries
Targeted Countries
South Korea, Japan, India, Vietnam, United States, Brazil, China, Russia, Poland, Thailand, Turkey, Indonesia, Malaysia, Mexico, Iran, Iraq, Saudi Arabia, Taiwan, United Kingdom, France, Germany, Italy, Ukraine, Netherlands, Bangladesh, Chile, Australia, Canada, Singapore, Switzerland.

Tools Used:
NestEgg, Tdrop2 , SHARPKNOT, RawDisk, Destover, CleanToad, ELECTRICFISH, Quickcafe, Http Dr0pper, NachoCheese, DeltaCharlie, PowerBrace, BTC Changer, HotelAlfa, Castov, Volgmer, DoublePulsar, Plink, BlindToad, PowerRatankba, PowerShellRAT, RomeoNovember, ValeforBeta, PEBBLEDASH, Koredos, RomeoEcho, RomeoWhiskey, ARTFULPIE, RmeoGolf, Yort, NukeSped, RomeoFoxtrot, Vyveva, Troy, Bookcode, Bitsran, CheeseTray, RedShawl, SierraCharlie, TFlower, Hawup, SheepRAT, FallChil RAT, Stunnel, RomeoCharlie, RomeoDelta, Rifdoor, Jokra, Romeos, SierraAlfa, SLICKSHOES, Aryan, ClientTraficForwarder, HOPLIGHT, WolfRAT, Tdrop, Andaratm, BanSwift, Recon, 3Rat Client, Duuzer, BUFFETLINE, EternalBlue, netsh, Mydoom, Concealment Troy, DaclsRAT, KillDisk, BADCALL, MATA, OpBlockBuster, CookieTime, Dtrack, Hermes, ATMDtrack, Mimikatz, COPPERHEDGE, DyePack, RomeoMike,Hotwax, RomeoBravo, Gh0stRAT, PowerTask, RomeoAlfa, Wormhole, Brambul, Fimlis, AuditCred, BISTROMATH, Joanap, HTTPTroy, KEYMARBLE, RisingSun, Bankshot, PhanDoor, 3proxy, ProcDump , RatankbaPOS, VHD, HOTCROISSANT, PSLogger, RomeoHotel, PowerSpritz, HtDnDownLoader, WbBot, VSingle, BLINDINGCAN, TAINTEDSCRIBE, BootWreck, Contopee, Dozer.
Malware used by the Lazarus Group:
JuicyPotato, Volgmer, BADCALL, NineRAT, HARDRAIN, Destover, LightlessCan, RATANKBA, Proxysvc, OpenCarrot, Vyveva, RUSTBUCKET, Torisma Spyware, Lazardoor, AndarLoader, Marstech1, DarkComet, TYPEFRAME, ModeLoader, AuditCred, WannaCry, APPLEJEUS, CivetQ, Koi Stealer, MATA, SIGNBT, RustBucket, RustDoor, ThreatNeedle, Bankshot, XORIndex, BeaverTail, FALLCHILL, QuiteRAT, PyLangGhost RAT, HOPLIGHT, KEYMARBLE, Kaolin RAT, Scout, DLRAT, BottomLoader, LPEClient.
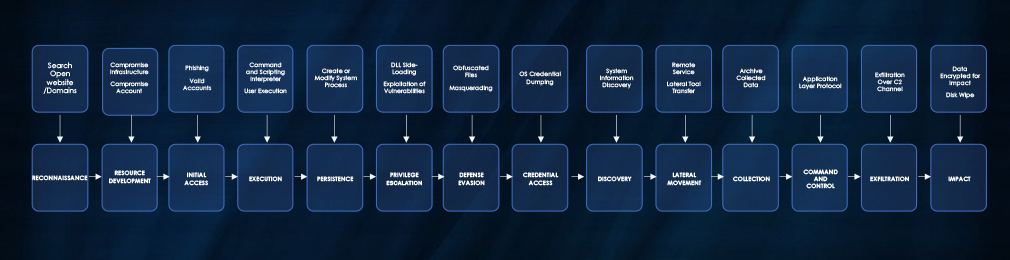
ATTACK FLOW DIAGRAM OF APT THREAT ACTOR LAZARUS GROUP
RECENTLY EXPLOITED VULNERABILITIES BY THE LAZARUS GROUP
| CVE-2021-44228 |
| CVE-2023-4966 |
| CVE-2023-22518 |
The following TTPs are based on the MITRE ATT&CK framework and represent a high-level overview of Lazarus Group’s recent activities:
| Tactic | ID | Technique |
| Reconnaissance | T1591.004 | Gather Victim Org Information:Identify Roles |
| Reconnaissance | T1593.001 | Search Open Websites/Domains:Social Media |
| Reconnaissance | T1591 | Gather Victim Org Information |
| Reconnaissance | T1589.002 | Gather Victim Identity Information:Email Addresses |
| Resource Development | T1584.004 | Compromise Infrastructure:Server |
| Resource Development | T1588.002 | Obtain Capabilities:Tool |
| Resource Development | T1584.001 | Compromise Infrastructure:Domains |
| Resource Development | T1588.003 | Obtain Capabilities:Code Signing Certificates |
| Resource Development | T1588.004 | Obtain Capabilities:Digital Certificates |
| Resource Development | T1585.002 | Establish Accounts:Email Accounts |
| Resource Development | T1583.006 | Acquire Infrastructure:Web Services |
| Resource Development | T1608.001 | Stage Capabilities:Upload Malware |
| Resource Development | T1583.004 | Acquire Infrastructure: Server |
| Resource Development | T1608.002 | Stage Capabilities:Upload Tool |
| Resource Development | T1587.001 | Develop Capabilities:Malware |
| Resource Development | T1583.001 | Acquire Infrastructure:Domains |
| Resource Development | T1585.001 | Establish Accounts:Social Media Accounts |
| Initial Access | T1566.003 | Phishing:Spearphishing via Service |
| Initial Access | T1189 | Drive-by Compromise |
| Initial Access | T1078 | Valid Accounts |
| Initial Access | T1566.001 | Phishing:Spearphishing Attachment |
| Initial Access | T1566.002 | Phishing:Spearphishing Link |
| Execution | T1203 | Exploitation for Client Execution |
| Execution | T1047 | Windows Management Instrumentation |
| Execution | T1059.003 | Command and Scripting Interpreter:Windows Command Shell |
| Execution | T1053.005 | Scheduled Task/Job:Scheduled Task |
| Execution | T1204.001 | User Execution:Malicious Link |
| Execution | T1204.002 | User Execution:Malicious File |
| Execution | T1059.005 | Command and Scripting Interpreter:Visual Basic |
| Execution | T1106 | Native API |
| Execution | T1059.001 | Command and Scripting Interpreter:PowerShell |
| Persistence | T1542.003 | Pre-OS Boot:Bootkit |
| Persistence | T1543.003 | Create or Modify System Process:Windows Service |
| Persistence | T1547.009 | Boot or Logon Autostart Execution:Shortcut Modification |
| Persistence | T1078 | Valid Accounts |
| Persistence | T1098 | Account Manipulation |
| Persistence | T1053.005 | Scheduled Task/Job:Scheduled Task |
| Persistence | T1574.002 | Hijack Execution Flow:DLL Side-Loading |
| Persistence | T1547.001 | Boot or Logon AutoStart Execution:Registry Run Keys / Startup Folder |
| Persistence | T1574.013 | Hijack Execution Flow:KernelCallbackTable |
| Privilege Escalation | T1134.002 | Access Token Manipulation:Create Process with Token |
| Privilege Escalation | T1543.003 | Create or Modify System Process:Windows Service |
| Privilege Escalation | T1547.009 | Boot or Logon Autostart Execution:Shortcut Modification |
| Privilege Escalation | T1078 | Valid Accounts |
| Privilege Escalation | T1053.005 | Scheduled Task/Job:Scheduled Task |
| Privilege Escalation | T1574.002 | Hijack Execution Flow:DLL Side-Loading |
| Privilege Escalation | T1547.001 | Boot or Logon Autostart Execution:Registry Run Keys / Startup Folder |
| Privilege Escalation | T1574.013 | Hijack Execution Flow:KernelCallbackTable |
| Privilege Escalation | T1055.001 | Process Injection:Dynamic-link Library Injection |
| Defense Evasion | T1036 | Masquerading |
| Defense Evasion | T1078 | Valid Accounts |
| Defense Evasion | T1497.001 | Virtualization/Sandbox Evasion:System Checks |
| Defense Evasion | T1564.001 | Hide Artifacts:Hidden Files and Directories |
| Defense Evasion | T1027.007 | Obfuscated Files or Information:Dynamic API Resolution |
| Defense Evasion | T1218 | System Binary Proxy Execution |
| Defense Evasion | T1218.005 | System Binary Proxy Execution:Mshta |
| Defense Evasion | T1542.003 | Pre-OS Boot:Bootkit |
| Defense Evasion | T1218.011 | System Binary Proxy Execution:Rundll32 |
| Defense Evasion | T1218.010 | System Binary Proxy Execution:Regsvr32 |
| Defense Evasion | T1070 | Indicator Removal |
| Defense Evasion | T1574.013 | Hijack Execution Flow:KernelCallbackTable |
| Defense Evasion | T1055.001 | Process Injection: Dynamic-link Library Injection |
| Defense Evasion | T1202 | Indirect Command Execution |
| Defense Evasion | T1620 | Reflective Code Loading |
| Defense Evasion | T1134.002 | Access Token Manipulation:Create Process with Token |
| Defense Evasion | T1027 | Obfuscated Files or Information |
| Defense Evasion | T1562.001 | Impair Defenses:Disable or Modify Tools |
| Defense Evasion | T1220 | XSL Script Processing |
| Defense Evasion | T1221 | Template Injection |
| Defense Evasion | T1562.004 | Impair Defenses:Disable or Modify System Firewall |
| Defense Evasion | T1036.005 | Masquerading:Match Legitimate Resource Name or Location |
| Defense Evasion | T1027.002 | Obfuscated Files or Information:Software Packing |
| Defense Evasion | T1553.002 | Subvert Trust Controls:Code Signing |
| Defense Evasion | T1036.003 | Masquerading:Rename Legitimate Utilities |
| Defense Evasion | T1036.004 | Masquerading:Masquerade Task or Service |
| Defense Evasion | T1140 | Deobfuscate/Decode Files or Information |
| Defense Evasion | T1070.004 | Indicator Removal:File Deletion |
| Defense Evasion | T1070.003 | Indicator Removal:Clear Command History |
| Defense Evasion | T1574.002 | Hijack Execution Flow:DLL Side-Loading |
| Defense Evasion | T1070.006 | Indicator Removal:Timestomp |
| Credential Access | T1110.003 | Brute Force:Password Spraying |
| Credential Access | T1110 | Brute Force |
| Credential Access | T1557.001 | Adversary-in-the-Middle:LLMNR/NBT-NS Poisoning and SMB Relay |
| Credential Access | T1056.001 | Input Capture:Keylogging |
| Discovery | T1049 | System Network Connections Discovery |
| Discovery | T1016 | System Network Configuration Discovery |
| Discovery | T1057 | Process Discovery |
| Discovery | T1046 | Network Service Discovery |
| Discovery | T1124 | System Time Discovery |
| Discovery | T1033 | System Owner/User Discovery |
| Discovery | T1012 | Query Registry |
| Discovery | T1497.001 | Virtualization/Sandbox Evasion:System Checks |
| Discovery | T1010 | Application Window Discovery |
| Discovery | T1614.001 | System Location Discovery:System Language Discovery |
| Discovery | T1087.002 | Account Discovery:Domain Account |
| Discovery | T1082 | System Information Discovery |
| Discovery | T1083 | File and Directory Discovery |
| Lateral Movement | T1021.004 | Remote Services:SSH |
| Lateral Movement | T1021.002 | Remote Services:SMB/Windows Admin Shares |
| Lateral Movement | T1021.001 | Remote Services:Remote Desktop Protocol |
| Lateral Movement | T1534 | Internal Spearphishing |
| Collection | T1005 | Data from Local System |
| Collection | T1074.001 | Data Staged:Local Data Staging |
| Collection | T1560 | Archive Collected Data |
| Collection | T1557.001 | Adversary-in-the-Middle:LLMNR/NBT-NS Poisoning and SMB Relay |
| Collection | T1560.002 | Archive Collected Data:Archive via Library |
| Collection | T1560.003 | Archive Collected Data:Archive via Custom Method |
| Collection | T1056.001 | Input Capture:Keylogging |
| Command and Control | T1573.00 | Encrypted Channel:Asymmetric Cryptography |
| Command and Control | T1001.003 | Data Obfuscation: Protocol or Service Impersonation |
| Command and Control | T1104 | Multi-Stage Channels |
| Command and Control | T1071.001 | Application Layer Protocol:Web Protocols |
| Command and Control | T1102.002 | Web Service: Bidirectional Communication |
| Command and Control | T1571 | Non-Standard Port |
| Command and Control | T1132.001 | Data Encoding:Standard Encoding |
| Command and Control | T1090.002 | Proxy:External Proxy |
| Command and Control | T1090.001 | Proxy:Internal Proxy |
| Command and Control | T1008 | Fallback Channels |
| Command and Control | T1105 | Ingress Tool Transfer |
| Exfiltration | T1048.003 | Exfiltration Over Alternative Protocol:Exfiltration Over Unencrypted Non-C2 Protocol |
| Exfiltration | T1567.002 | Exfiltration Over Web Service:Exfiltration to Cloud Storage |
| Exfiltration | T1041 | Exfiltration Over C2 Channel |
| Impact | T1561.002 | Disk Wipe:Disk Structure Wipe |
| Impact | T1489 | Service Stop |
| Impact | T1561.001 | Disk Wipe:Disk Content Wipe |
| Impact | T1485 | Data Destruction |
| Impact | T1529 | System Shutdown/Reboot |
| Impact | T1491.001 | Defacement:Internal Defacement |