


Kimsuky is a North Korean hacking group identified as a moderately sophisticated cyber operator, active since at least 2018. This group primarily engages in espionage and financially motivated cybercrime to support its operations and align with the geopolitical interests of the North Korean government.
Alias:
Kimsuki APT43
Motivation:
Espionage
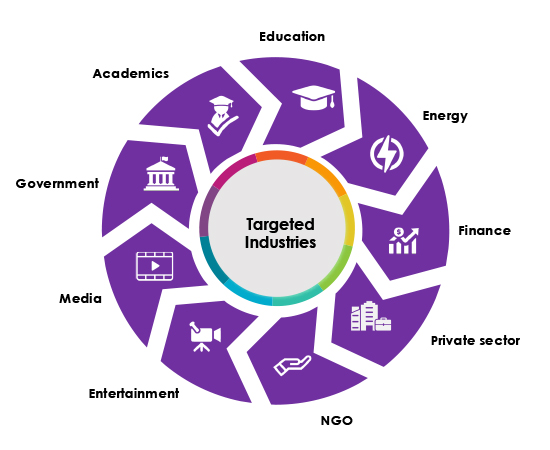
Target Technologies
Office Suites Software, Operating System, Web Application
Targeted Countries
South Korea, the United States, Japan, Vietnam, and European countries (particularly those with ties to NATO)
| CVE-2024-21338 | CVE-2021-44228 |
| CVE-2017-17215 | CVE-2017-11882 |
| CVE-2020-0787 | CVE-2017-0199 |
| CVE-2017-0144 |
MITRE ATT&CK Techniques used by Kimsuky
| Reconnaissance | Execution | Defense Evasion | Lateral Movement | Discovery |
| T1594 | T1053.005 | T1027 | T1550.002 | T1016 |
| T1593.001 | T1059.003 | T1562.001 | T1021.001 | T1518.001 |
| T1593.002 | T1059.001 | T1112 | T1534 | T1057 |
| T1591 | T1204.001 | T1036 | T1012 | |
| T1589.002 | T1059.006 | T1055 | Collection | T1040 |
| T1598.003 | T1204.002 | T1078.003 | T1005 | T1082 |
| T1589.003 | T1059.007 | T1564.002 | T1114.003 | T1083 |
| T1059.005 | T1564.003 | T1074.001 | T1007 | |
| Resource Development | T1562.004 | T1114.002 | ||
| T1587 | Persistence | T1218.005 | T1560.001 | |
| T1585.002 | T1505.003 | T1218.011 | T1560.003 | |
| T1583.006 | T1543.003 | T1218.010 | T1056.001 | |
| T1608.001 | T1176 | T1036.005 | T1557 | |
| T1583.004 | T1133 | T1027.002 | ||
| T1588.002 | T1078.003 | T1553.002 | Command and Control | |
| T1584.001 | T1098 | T1550.002 | T1071.001 | |
| T1588.005 | T1053.005 | T1036.004 | T1102.002 | |
| T1587.001 | T1136.001 | T1140 | T1219 | |
| T1583.001 | T1547.001 | T1070.004 | T1071.003 | |
| T1586.002 | T1546.001 | T1070.006 | T1071.002 | |
| T1585.001 | T1055.012 | T1105 | ||
| Privilege Escalation | ||||
| Initial Access | T1543.003 | Credential Access | Exfiltration | |
| T1133 | T1055 | T1111 | T1567.002 | |
| T1566.001 | T1078.003 | T1555.003 | T1041 | |
| T1078.003 | T1053.005 | T1552.001 | ||
| T1566.002 | T1547.001 | T1040 | ||
| T1190 | T1546.001 | T1003.001 | ||
| T1055.012 | T1056.001 | |||
| T1557 |
Kimsuky’s Recent Campaign Highlights and Trends: