


Kimsuki, an advanced persistent threat (APT) group active since at least 2012, is suspected to be operating out of North Korea in direct support of the regime’s strategic objectives. The group’s intelligence collection priorities are closely aligned with the mission of the Reconnaissance General Bureau (RGB), North Korea’s primary foreign intelligence agency. Kimsuki possesses moderately sophisticated technical capabilities and is known for employing highly targeted social engineering tactics, especially against South Korean and U.S.-based government agencies, academics, and think tanks focused on geopolitical issues related to the Korean Peninsula. In addition to its espionage operations, Kimsuki engages in cybercriminal activities to generate revenue, helping to finance its overarching mission of acquiring strategic intelligence.
Alias: APT43, Thallium, Velvet Chollima, Black Banshee, Emerald Sleet
Motivation: Cyber Espionage, Strategic Intelligence Collection, Credential Theft
Targeted Industries

Targeted Country
Belgium, Bulgaria, Canada, Croatia, Denmark, Estonia, Finland, France, Germany, Greece, Hungary, Iceland, Italy, Latvia, Lithuania, Luxembourg, Montenegro, North Macedonia, Norway, Poland, Portugal, Romania, Slovakia, Slovenia, the Czech Republic, Netherlands, Albania, Japan, South Korea, Thailand, USA, Vietnam.
Target Technologies: Office Suites Software, Operating System, Web Application
Targeted Regions: East Asia, Southeast Asia, Asia-Pacific, North America, Europe, and globally
Tools Used by Kimsuki: BabyShark, AppleSeed (KGH_SPY), AlphaSeed, GoldDragon, Custom Phishing Frameworks, Browser Credential Stealers, PowerShell, MSHTA, WMIC, Certutil, BITSAdmin.
Malware used by Kimsuki: BabyShark, AppleSeed, AlphaSeed, GoldDragon, KGH_SPY variants, Custom Android Spyware, Lightweight Downloaders.
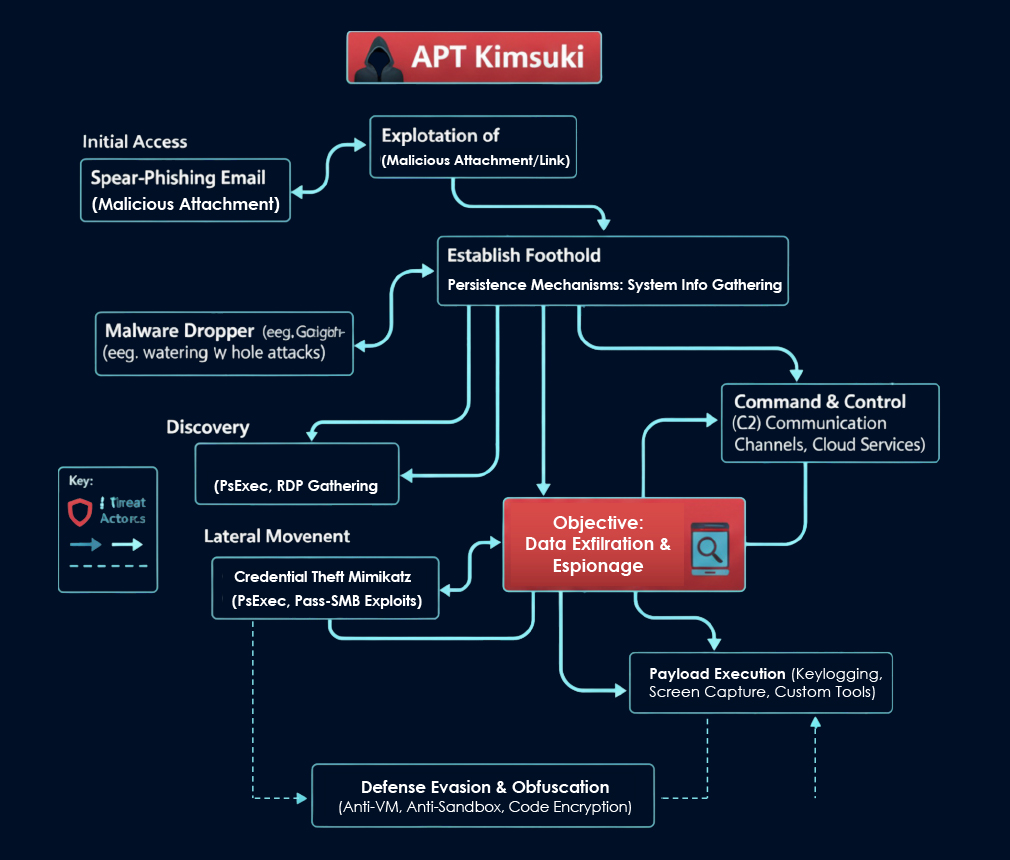
Campaign highlights
| CVE ID | Affected Products | CVSS Score | Exploit Links |
| CVE-2017-11882 | Microsoft Office | 7.8 | link |
| CVE-2019-0708 | Remote Desktop Services | 9.8 | link1, link2, link3, link4, link5 |
| Tactic | ID | Technique |
| Reconnaissance | T1589.002 | Gather Victim Identity Information: Email Addresses |
| Reconnaissance | T1589.003 | Gather Victim Identity Information: Employee Names |
| Reconnaissance | T1591 | Gather Victim Org Information |
| Reconnaissance | T1598 | Phishing for Information |
| Reconnaissance | T1598.003 | Phishing for Information: Spear phishing Link |
| Reconnaissance | T1596 | Search Open Technical Databases |
| Reconnaissance | T1593 | Search Open Websites/Domains |
| Reconnaissance | T1593.001 | Search Open Websites/Domains: Social Media |
| Reconnaissance | T1593.002 | Search Open Websites/Domains: Search Engines |
| Reconnaissance | T1594 | Search Victim-Owned Websites |
| Resource Development | T1583 | Acquire Infrastructure |
| Resource Development | T1583.001 | Acquire Infrastructure: Domains |
| Resource Development | T1583.006 | Acquire Infrastructure: Web Services |
| Resource Development | T1583.004 | Acquire Infrastructure: Server |
| Resource Development | T1586.002 | Compromise Accounts: Email Accounts |
| Resource Development | T1584.001 | Compromise Infrastructure: Domains |
| Resource Development | T1587 | Develop Capabilities |
| Resource Development | T1587.001 | Develop Capabilities: Malware |
| Resource Development | T1585 | Establish Accounts |
| Resource Development | T1585.001 | Establish Accounts: Social Media Accounts |
| Resource Development | T1585.002 | Establish Accounts: Email Accounts |
| Resource Development | T1588.002 | Obtain Capabilities: Tool |
| Resource Development | T1588.003 | Obtain Capabilities: Code Signing Certificates |
| Resource Development | T1588.005 | Obtain Capabilities: Exploits |
| Resource Development | T1608.001 | Stage Capabilities: Upload Malware |
| Initial Access | T1133 | External Remote Services |
| Initial Access | T1190 | Exploit Public-Facing Application |
| Initial Access | T1566 | Phishing |
| Initial Access | T1566.001 | Phishing: Spear phishing Attachment |
| Initial Access | T1566.002 | Phishing: Spear phishing Link |
| Initial Access | T1078.003 | Valid Accounts: Local Accounts |
| Execution | T1059.001 | Command and Scripting Interpreter: PowerShell |
| Execution | T1059.003 | Command and Scripting Interpreter: Windows Command Shell |
| Execution | T1059.005 | Command and Scripting Interpreter: Visual Basic |
| Execution | T1059.006 | Command and Scripting Interpreter: Python |
| Execution | T1059.007 | Command and Scripting Interpreter: JavaScript |
| Execution | T1053.005 | Scheduled Task/Job: Scheduled Task |
| Execution | T1204.001 | User Execution: Malicious Link |
| Execution | T1204.002 | User Execution: Malicious File |
| Reconnaissance | T1598.003 | Phishing for Information: Spear phishing Link |
| Reconnaissance | T1596 | Search Open Technical Databases |
| Reconnaissance | T1593 | Search Open Websites/Domains |
| Reconnaissance | T1593.001 | Search Open Websites/Domains: Social Media |
| Reconnaissance | T1593.002 | Search Open Websites/Domains: Search Engines |
| Reconnaissance | T1594 | Search Victim-Owned Websites |
| Resource Development | T1583 | Acquire Infrastructure |
| Resource Development | T1583.001 | Acquire Infrastructure: Domains |
| Resource Development | T1583.006 | Acquire Infrastructure: Web Services |
| Resource Development | T1583.004 | Acquire Infrastructure: Server |
| Resource Development | T1586.002 | Compromise Accounts: Email Accounts |
| Resource Development | T1584.001 | Compromise Infrastructure: Domains |
| Resource Development | T1587 | Develop Capabilities |
| Resource Development | T1587.001 | Develop Capabilities: Malware |
| Resource Development | T1585 | Establish Accounts |
| Resource Development | T1585.001 | Establish Accounts: Social Media Accounts |
| Resource Development | T1585.002 | Establish Accounts: Email Accounts |
| Resource Development | T1588.002 | Obtain Capabilities: Tool |
| Resource Development | T1588.003 | Obtain Capabilities: Code Signing Certificates |
| Resource Development | T1588.005 | Obtain Capabilities: Exploits |
| Resource Development | T1608.001 | Stage Capabilities: Upload Malware |
| Initial Access | T1133 | External Remote Services |
| Initial Access | T1190 | Exploit Public-Facing Application |
| Initial Access | T1566 | Phishing |
| Initial Access | T1566.001 | Phishing: Spear phishing Attachment |
| Initial Access | T1566.002 | Phishing: Spear phishing Link |
| Initial Access | T1078.003 | Valid Accounts: Local Accounts |
| Execution | T1059.001 | Command and Scripting Interpreter: PowerShell |
| Execution | T1059.003 | Command and Scripting Interpreter: Windows Command Shell |
| Execution | T1059.005 | Command and Scripting Interpreter: Visual Basic |
| Execution | T1059.006 | Command and Scripting Interpreter: Python |
| Execution | T1059.007 | Command and Scripting Interpreter: JavaScript |
| Execution | T1053.005 | Scheduled Task/Job: Scheduled Task |
| Execution | T1204.001 | User Execution: Malicious Link |
| Execution | T1204.002 | User Execution: Malicious File |
| Defense Evasion | T1562.004 | Impair Defenses: Disable or Modify System Firewall |
| Defense Evasion | T1656 | Impersonation |
| Defense Evasion | T1070.004 | Indicator Removal: File Deletion |
| Defense Evasion | T1070.006 | Indicator Removal: Timestomp |
| Defense Evasion | T1036.004 | Masquerading: Masquerade Task or Service |
| Defense Evasion | T1036.005 | Masquerading: Match Legitimate Resource Name or Location |
| Defense Evasion | T1112 | Modify Registry |
| Defense Evasion | T1027 | Obfuscated Files or Information |
| Defense Evasion | T1027.002 | Obfuscated Files or Information: Software Packing |
| Defense Evasion | T1055 | Process Injection |
| Defense Evasion | T1055.012 | Process Injection: Process Hollowing |
| Defense Evasion | T1620 | Reflective Code Loading |
| Defense Evasion | T1553.002 | Subvert Trust Controls: Code Signing |
| Defense Evasion | T1218.005 | System Binary Proxy Execution: Mshta |
| Defense Evasion | T1218.010 | System Binary Proxy Execution: Regsvr32 |
| Defense Evasion | T1218.011 | System Binary Proxy Execution: Rundll32 |
| Defense Evasion | T1205 | Traffic Signaling |
| Defense Evasion | T1550.002 | Use Alternate Authentication Material: Pass the Hash |
| Defense Evasion | T1078.003 | Valid Accounts: Local Accounts |
| Credential Access | T1557 | Adversary-in-the-Middle |
| Credential Access | T1555.003 | Credentials from Password Stores: Credentials from Web Browsers |
| Credential Access | T1003.001 | OS Credential Dumping: LSASS Memory |
| Credential Access | T1056.001 | Input Capture: Keylogging |
| Credential Access | T1111 | Multi-Factor Authentication Interception |
| Defense Evasion | T1562.004 | Impair Defenses: Disable or Modify System Firewall |
| Defense Evasion | T1656 | Impersonation |
| Defense Evasion | T1070.004 | Indicator Removal: File Deletion |
| Defense Evasion | T1070.006 | Indicator Removal: Timestomp |
| Defense Evasion | T1036.004 | Masquerading: Masquerade Task or Service |
| Defense Evasion | T1036.005 | Masquerading: Match Legitimate Resource Name or Location |
| Defense Evasion | T1112 | Modify Registry |
| Defense Evasion | T1027 | Obfuscated Files or Information |
| Defense Evasion | T1027.002 | Obfuscated Files or Information: Software Packing |
| Defense Evasion | T1055 | Process Injection |
| Defense Evasion | T1055.012 | Process Injection: Process Hollowing |
| Defense Evasion | T1620 | Reflective Code Loading |
| Defense Evasion | T1553.002 | Subvert Trust Controls: Code Signing |
| Defense Evasion | T1218.005 | System Binary Proxy Execution: Mshta |
| Defense Evasion | T1218.010 | System Binary Proxy Execution: Regsvr32 |
| Defense Evasion | T1218.011 | System Binary Proxy Execution: Rundll32 |
| Defense Evasion | T1205 | Traffic Signaling |
| Defense Evasion | T1550.002 | Use Alternate Authentication Material: Pass the Hash |
| Defense Evasion | T1078.003 | Valid Accounts: Local Accounts |
| Credential Access | T1557 | Adversary-in-the-Middle |
| Credential Access | T1555.003 | Credentials from Password Stores: Credentials from Web Browsers |
| Credential Access | T1003.001 | OS Credential Dumping: LSASS Memory |
| Credential Access | T1056.001 | Input Capture: Keylogging |
| Credential Access | T1111 | Multi-Factor Authentication Interception |
| Command and Control | T1071.001 | Application Layer Protocol: Web Protocols |
| Command and Control | T1071.002 | Application Layer Protocol: File Transfer Protocols |
| Command and Control | T1071.003 | Application Layer Protocol: Mail Protocols |
| Command and Control | T1219.002 | Remote Access Tools: Remote Desktop Software |
| Command and Control | T1105 | Ingress Tool Transfer |
| Command and Control | T1205 | Traffic Signaling |
| Command and Control | T1102.001 | Web Service: Dead Drop Resolver |
| Command and Control | T1102.002 | Web Service: Bidirectional Communication |
| Exfiltration | T1041 | Exfiltration Over C2 Channel |
| Exfiltration | T1567.002 | Exfiltration Over Web Service: Exfiltration to Cloud Storage |
| Impact | T1657 | Financial Theft |