


Group123 is a North Korean state-sponsored advanced persistent threat (APT) group active since at least 2012. It is also tracked under other names such as APT37, Reaper, and ScarCruft by various cybersecurity firms. The group is known for its cyber espionage campaigns primarily targeting South Korea, but since 2017, it has expanded its operations to Japan, Vietnam, the Middle East, and other regions.
Alias: Cloud Dragon, InkySquid, APT 37, APT-37, ITG10, Reaper, Red Eyes, RedAnt, Ricochet Chollima, ScarCruft, TEMP.Reaper
Motivation: Information Theft, Espionage
Target Technologies: Office Suites Software, Operating System, Web Application
Targeted Regions: East Asia, Southeast Asia, the Middle East
Targeted Industries

Targeted Countries
South Korea, Japan, Vietnam, China, Russia, Nepal, India, Kuwait, Romania, Czechia, Poland, the Middle East countries, and the United States

SLOWDRIFT, MS Office exploits, Konni, Oceansalt, HAPPYWORK, Freenki Loader, N1stAgent, KevDroid, PoohMilk Loader, WINERACK, KARAE, RUHAPPY, GELCAPSULE, FlashExploits, RICECURRY, SOUNDWAVE, ZUMKONG, Nokki, Syscon, CARROTBALL, GreezeBackdoor, NavRAT, RokRat, DOGCALL, CARROTBAT, CORALDECK, POORAIM, MILKDROP, SHUTTERSPEED, Final1stSpy, ScarCruft, Erebus
KARAE, HAPPYWORK, PoohMilk Loader, Oceansalt, BLUELIGHT, WINERACK, CORALDECK, Chinotto, RokRat, SHUTTERSPEED, Konni, Erebus, GreezeBackdoor, Final1stSpy, Syscon, N1stAgent, Nokki, SOUNDWAVE, GELCAPSULE, ScarCruft, RUHAPPY, ROKRAT, POORAIM, KevDroid, KoSpy, CARROTBALL, NavRAT, Freenki Loader, DOGCALL, SLOWDRIFT, M2RAT, CARROTBAT, ZUMKONG, Final1stspy, RICECURRY, MILKDROP.
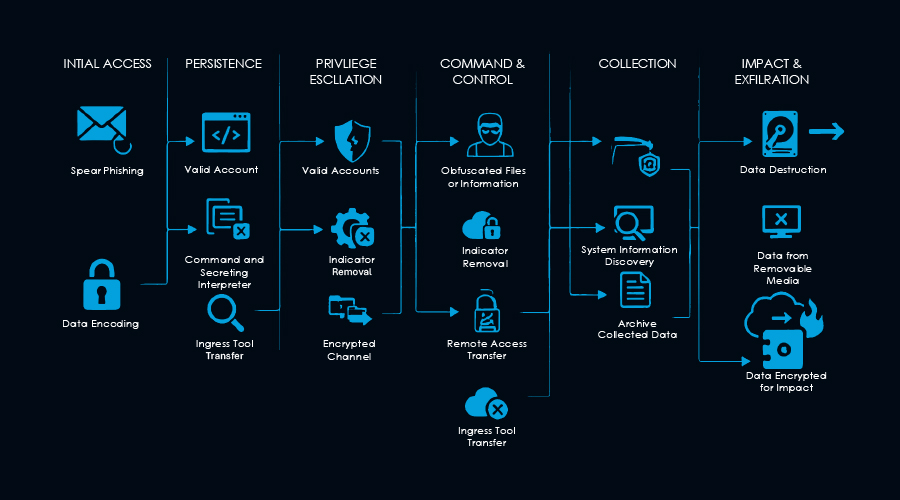
Campaign highlights
Tactical and strategic trends
| CVE ID | Affected Products | CVSS Score | Exploit Links |
| CVE-2018-4878 | Adobe Flash Player | 9.8 | link |
| CVE-2022-41128 | Windows Scripting Languages | 8.8 | – |
| CVE-2024-38178 | Scripting Engine Memory | 7.5 | – |
| CVE-2020-1380 | Internet Explorer | 8.8 | Link |
| CVE-2017-8291 | Artifex Ghostscript | 7.8 | link |
| Tactic | ID | Technique |
| Initial Access | T1189 | Drive-by Compromise |
| Initial Access | T1566.001 | Phishing: Spear phishing Attachment |
| Execution | T1059 | Command and Scripting Interpreter |
| Execution | T1059.003 | Command and Scripting Interpreter: Windows Command Shell |
| Execution | T1059.005 | Command and Scripting Interpreter: Visual Basic |
| Execution | T1059.006 | Command and Scripting Interpreter: Python |
| Execution | T1203 | Exploitation for Client Execution |
| Execution | T1559.002 | Inter-Process Communication: Dynamic Data Exchange |
| Execution | T1106 | Native API |
| Execution | T1053.005 | Scheduled Task/Job: Scheduled Task |
| Execution | T1204.002 | User Execution: Malicious File |
| Persistence | T1547.001 | Boot or Logon Autostart Execution: Registry Run Keys / Startup Folder |
| Persistence | T1053.005 | Scheduled Task/Job: Scheduled Task |
| Privilege Escalation | T1053.005 | Scheduled Task/Job: Scheduled Task |
| Privilege Escalation | T1548.002 | Abuse Elevation Control Mechanism: Bypass User Account Control |
| Privilege Escalation | T1547.001 | Boot or Logon Autostart Execution: Registry Run Keys / Startup Folder |
| Privilege Escalation | T1055 | Process Injection |
| Defense Evasion | T1548.002 | Abuse Elevation Control Mechanism: Bypass User Account Control |
| Defense Evasion | T1036.001 | Masquerading: Invalid Code Signature |
| Defense Evasion | T1027 | Obfuscated Files or Information |
| Defense Evasion | T1027.003 | Obfuscated Files or Information: Steganography |
| Defense Evasion | T1055 | Process Injection |
| Credential Access | T1555.003 | Credentials from Password Stores: Credentials from Web Browsers |
| Discovery | T1120 | Peripheral Device Discovery |
| Discovery | T1057 | Process Discovery |
| Discovery | T1082 | System Information Discovery |
| Discovery | T1033 | System Owner/User Discovery |
| Collection | T1123 | Audio Capture |
| Collection | T1005 | Data from Local System |
| Command and Control | T1105 | Ingress Tool Transfer |
| Command and Control | T1071.001 | Application Layer Protocol: Web Protocols |
| Command and Control | T1102.002 | Web Service: Bidirectional Communication |
| Impact | T1561.002 | Disk Wipe: Disk Structure Wipe |
| Impact | T1529 | System Shutdown/Reboot |