


Fancy Bear is a well-documented Russian state-sponsored threat actor that has been active since at least 2007 and is widely assessed to operate in close coordination with Russian intelligence services. Security researchers have attributed multiple high-profile cyber operations to the group, including election interference activities in several countries, aimed at influencing political outcomes in favor of the Russian government.
Alias: Apt28, Apt-28, Blue athena, Bluedelta, Frozenlake, Fighting ursa, Forest blizzard, Group 74, Gruesomelarch, Iron twilight, Itg05, Pawn storm, Sig40, Strontium, Sednit, Sofacy, Sofacygroup, Swallowtail, Ta422, Tag-110, Tg-4127, Threat group-4127, Tsar team, Uac-0001, Uac-0028, Uac-0063, Unit 26165, and Unit 74455.
Motivation: Financial Gain, Reputation Damage, Espionage, Political Agenda
Targeted Industries

Targeted Countries:
Afghanistan, Brazil, Cambodia, France, Georgia, Germany, India, Indonesia, Kazakhstan, Malaysia, Moldova, Pakistan, Romania, Russia, South Africa, Syria, Thailand, Turkey, Ukraine, United States, Vietnam, Australia, Mexico
Target Technologies:
Office Suites Software, Operating System, Web Application
Tools Used:
Forfiles, Computrace, Living off the Land, DealersChoice, Sedkit, Mimikatz
Malware used by Fancy Bear:
Steelhook, Headlace, Sedreco, Winexe, Oceanmap, Oldbait, Procdump, Winids, Certutil, Chopstick, Hidedrv, Skinnyboy, Xagentosx, Drovorub, Fysbis, Downdelph, Advstoreshell, Responder, Gooseegg, Xtunnel, Sofacy, Cannon, Usbstealer, Foozer, Vpnfilter, Koadic, Coreshell, Komplex, Slimagent, Jhuhugit, Seduploader, Zebrocy, Pythocydbg, Beardshell, Pocodown, Masepie, Nimcy, and Lojax.
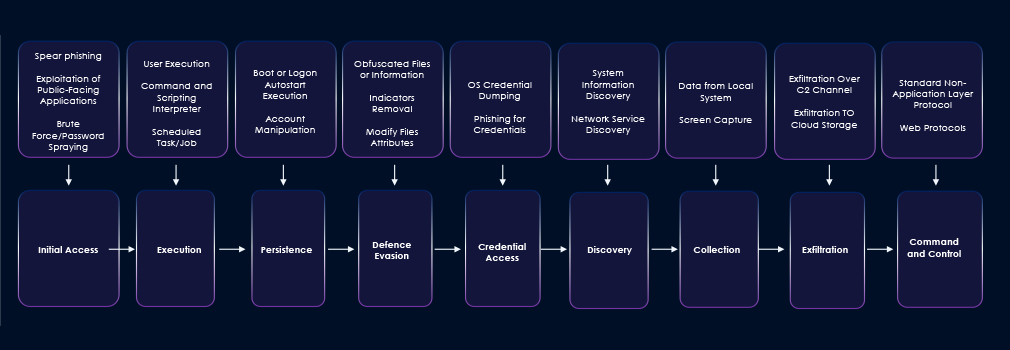
Exploitation of Recent Vulnerabilities for Initial Access
Recently, researchers observed that Fancy Bear weaponized a recently disclosed Microsoft Office vulnerability (CVE-2026-21509 CVSS Score:7.8) to compromise government and defense-aligned organizations in Eastern Europe and the EU. By embedding exploit logic within crafted Office documents, the group achieved stealthy code execution, bypassed conventional security controls, and established persistent access for long-term intelligence collection. This approach underscores the threat actor’s rapid adoption of fresh exploit opportunities to enhance intrusion success rates.
Targeting Energy, Defense, and Communication Sectors
Recent reporting confirms that Fancy Bear has broadened its targeting to include energy research institutes, defense collaboration entities, and government communication networks across multiple regions. The group has impersonated legitimate portals — including webmail and VPN services — to harvest credentials from organizational users. This targeting aligns with strategic interests in energy and critical infrastructure intelligence.
Continued Global Espionage and Hybrid Operations
Fancy Bear’s operational scope remains global, with historical ties to high-profile espionage campaigns against NATO, the EU, and Western government entities. Its persistent cyber operations include spear-phishing, credential theft, and long-term covert access in support of Russia’s broader geopolitical objectives. Analysts continue to observe steady campaigns leveraging minimal but effective tradecraft such as spear-phishing and credential harvesting rather than exclusively complex malware.
Tactic Evolution:
Rather than relying solely on heavy malware usage, Fancy Bear increasingly employs lightweight, high-ROI techniques such as credential theft, phishing, and exploitation of publicly disclosed vulnerabilities shortly after disclosure.
Rapid Exploit Adoption:
The speed at which the group integrates new vulnerabilities into active campaigns demonstrates sophisticated operational planning and exploitation readiness — an ongoing trend in state-aligned cyber espionage.
Credential Theft as a Persistent Objective:
Credential harvesting remains a central pillar of Fancy Bear’s playbook, enabling access expansion, lateral movement, and longer dwell times without reliance on noisy malware.
Target Diversification:
While traditional targets have included defense, government, and political organizations, more recent campaigns indicate a strategic shift that also targets energy research, defense collaboration, logistics support firms, and infrastructure entities with implications for regional operational support networks.
| CVE ID | Affected Products | CVSS Score | Exploit Links |
| CVE-2023-38831 | WinRAR | 7.8 | Link |
| CVE-2021-4034 | pkexec application | 7.8 | Link 1, Link 2 |
| CVE-2016-5195 | Linux kernel | 7.0 | Link1, Link2, Link3, Link4, Link5, and Link6 |
| CVE-2020-0688 | Microsoft Exchange | 8.8 | Link 1 and Link 2 |
| CVE-2015-2545 | Microsoft Office | 7.8 | – |
| Tactic | ID | Technique |
| Reconnaissance | T1591 | Gather Victim Org Information |
| Reconnaissance | T1598.003 | Phishing for Information: Spear phishing Link |
| Reconnaissance | T1598 | Phishing for Information |
| Reconnaissance | T1596 | Search Open Technical Databases |
| Resource Development | T1583.001 | Acquire Infrastructure: Domains |
| Resource Development | T1583.003 | Acquire Infrastructure: Virtual Private Server |
| Resource Development | T1583.006 | Acquire Infrastructure: Web Services |
| Resource Development | T1586.002 | Compromise Accounts: Email Accounts |
| Resource Development | T1584.008 | Compromise Infrastructure: Network Devices |
| Resource Development | T1588.002 | Obtain Capabilities: Tool |
| Initial Access | T1189 | Drive-by Compromise |
| Initial Access | T1190 | Exploit Public-Facing Application |
| Initial Access | T1133 | External Remote Services |
| Initial Access | T1091 | Replication Through Removable Media |
| Initial Access | T1199 | Trusted Relationship |
| Initial Access | T1078 | Valid Accounts |
| Initial Access | T1078.004 | Valid Accounts: Cloud Accounts |
| Initial Access | T1566.001 | Phishing: Spear phishing Attachment |
| Execution | T1204.001 | User Execution: Malicious Link |
| Execution | T1203 | Exploitation for Client Execution |
| Execution | T1559.002 | Inter-Process Communication: Dynamic Data Exchange |
| Execution | T1204.002 | User Execution: Malicious File |
| Persistence | T1098.002 | Account Manipulation: Additional Email Delegate Permissions |
| Persistence | T1547.001 | Boot or Logon Autostart Execution: Registry Run Keys / Startup Folder |
| Persistence | T1037.001 | Boot or Logon Initialization Scripts: Logon Script (Windows) |
| Persistence | T1546.015 | Event Triggered Execution: Component Object Model Hijacking |
| Persistence | T1133 | External Remote Services |
| Persistence | T1137.002 | Office Application Startup: Office Test |
| Persistence | T1542.003 | Pre-OS Boot: Bootkit |
| Persistence | T1505.003 | Server Software Component: Web Shell |
| Persistence | T1078 | Valid Accounts |
| Persistence | T1078.004 | Valid Accounts: Cloud Accounts |
| Privilege Escalation | T1134.001 | Access Token Manipulation: Token Impersonation/Theft |
| Privilege Escalation | T1098.002 | Account Manipulation: Additional Email Delegate Permissions |
| Privilege Escalation | T1547.001 | Boot or Logon Autostart Execution: Registry Run Keys / Startup Folder |
| Privilege Escalation | T1037.001 | Boot or Logon Initialization Scripts: Logon Script (Windows) |
| Privilege Escalation | T1546.015 | Event Triggered Execution: Component Object Model Hijacking |
| Privilege Escalation | T1078.004 | Valid Accounts: Cloud Accounts |
| Defense Evasion | T1134.001 | Access Token Manipulation: Token Impersonation/Theft |
| Defense Evasion | T1564.001 | Hide Artifacts: Hidden Files and Directories |
| Defense Evasion | T1564.003 | Hide Artifacts: Hidden Window |
| Defense Evasion | T1070.001 | Indicator Removal: Clear Windows Event Logs |
| Defense Evasion | T1070.004 | Indicator Removal: File Deletion |
| Defense Evasion | T1070.006 | Indicator Removal: Timestomp |
| Defense Evasion | T1036 | Masquerading |
| Defense Evasion | T1036.005 | Masquerading: Match Legitimate Resource Name or Location |
| Defense Evasion | T1027.013 | Obfuscated Files or Information: Encrypted/Encoded File |
| Defense Evasion | T1542.003 | Pre-OS Boot: Bootkit |
| Defense Evasion | T1014 | Rootkit |
| Defense Evasion | T1218.011 | System Binary Proxy Execution: Rundll32 |
| Defense Evasion | T1221 | Template Injection |
| Defense Evasion | T1550.001 | Use Alternate Authentication Material: Application Access Token |
| Defense Evasion | T1550.002 | Use Alternate Authentication Material: Pass the Hash |
| Defense Evasion | T1078.004 | Valid Accounts: Cloud Accounts |
| Credential Access | T1557.004 | Adversary-in-the-Middle: Evil Twin |
| Credential Access | T1110 | Brute Force |
| Credential Access | T1110.001 | Brute Force: Password Guessing |
| Credential Access | T1110.003 | Brute Force: Password Spraying |
| Credential Access | T1056.001 | Input Capture: Keylogging |
| Credential Access | T1040 | Network Sniffing |
| Credential Access | T1003 | OS Credential Dumping |
| Credential Access | T1003.001 | OS Credential Dumping: LSASS Memory |
| Credential Access | T1003.002 | OS Credential Dumping: Security Account Manager |
| Credential Access | T1003.003 | OS Credential Dumping: NTDS |
| Credential Access | T1528 | Steal Application Access Token |
| Discovery | T1083 | File and Directory Discovery |
| Discovery | T1040 | Network Sniffing |
| Discovery | T1120 | Peripheral Device Discovery |
| Discovery | T1057 | Process Discovery |
| Lateral Movement | T1210 | Exploitation of Remote Services |
| Lateral Movement | T1091 | Replication Through Removable Media |
| Lateral Movement | T1550.001 | Use Alternate Authentication Material: Application Access Token |
| Lateral Movement | T1550.002 | Use Alternate Authentication Material: Pass the Hash |
| Collection | T1557.004 | Adversary-in-the-Middle: Evil Twin |
| Collection | T1560 | Archive Collected Data |
| Collection | T1560.001 | Archive Collected Data: Archive via Utility |
| Collection | T1119 | Automated Collection |
| Collection | T1213 | Data from Information Repositories |
| Collection | T1213.002 | Data from Information Repositories: SharePoint |
| Collection | T1005 | Data from Local System |
| Collection | T1039 | Data from Network Shared Drive |
| Collection | T1025 | Data from Removable Media |
| Collection | T1074.001 | Data Staged: Local Data Staging |
| Collection | T1074.002 | Data Staged: Remote Data Staging |
| Collection | T1114.002 | Email Collection: Remote Email Collection |
| Collection | T1056.001 | Input Capture: Keylogging |
| Collection | T1113 | Screen Capture |
| Command and Control | T1001.001 | Data Obfuscation: Junk Data |
| Command and Control | T1071.001 | Application Layer Protocol: Web Protocols |
| Command and Control | T1071.003 | Application Layer Protocol: Mail Protocols |
| Command and Control | T1092 | Communication Through Removable Media |
| Command and Control | T1573.001 | Encrypted Channel: Symmetric Cryptography |
| Command and Control | T1105 | Ingress Tool Transfer |
| Command and Control | T1090.001 | Proxy: Internal Proxy |
| Command and Control | T1090.002 | Proxy: External Proxy |
| Command and Control | T1090.003 | Proxy: Multi-hop Proxy |
| Command and Control | T1102.002 | Web Service: Bidirectional Communication |
| Exfiltration | T1030 | Data Transfer Size Limits |
| Exfiltration | T1048.002 | Exfiltration Over Alternative Protocol: Exfiltration Over Asymmetric Encrypted Non-C2 Protocol |
| Impact | T1498 | Network Denial of Service |