Published On : 2024-12-16
Earth Estries is a Chinese Advanced Persistent Threat (APT) group that has gained prominence for its sophisticated cyber espionage activities targeting critical infrastructure and government entities globally.
Alias:
Famous Sparrow, Ghost Emperor, Salt Typhoon, UNC2286
Motivation:
Espionage, Data Exfiltration
Target Technologies:
VPS, Windows, IoT
Techniques Used:
Keylogging, Malware Implant DLL Sideloading
Malware used by Earth Estries:
HemiGate , GHOSTSPIDE , Zingdoor, Cobalt Strike, MASOL RAT, SNAPPYBE
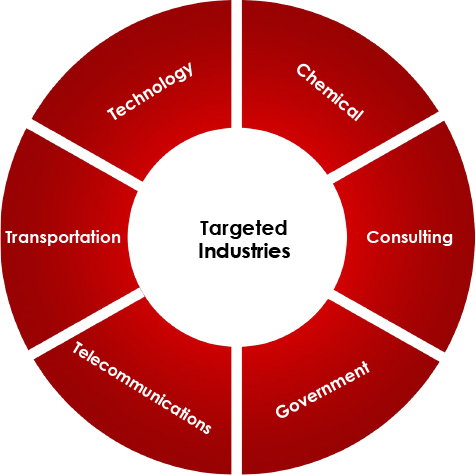
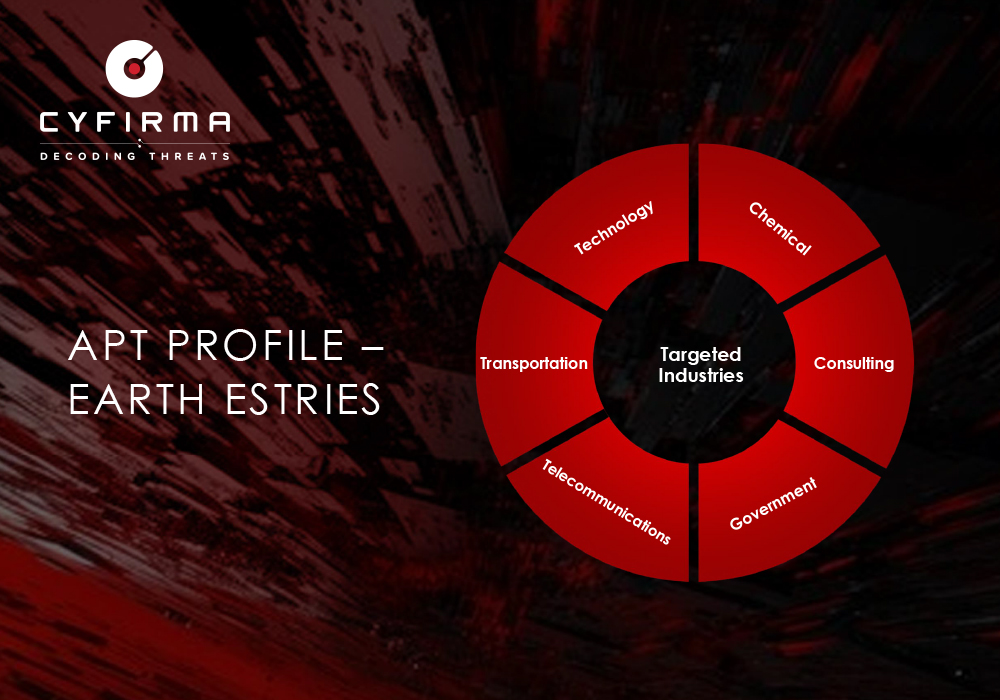
Targeted Countries
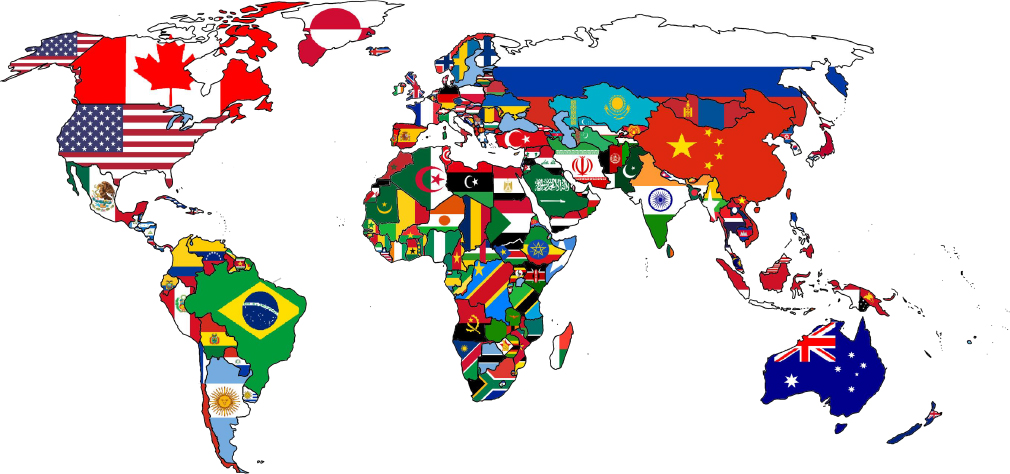
The United States, Germany, South Africa, Malaysia, the Philippines, Taiwan, India, Canada, and Singapore.
Recently Exploited Vulnerabilities by Earth Estries
- CVE-2023-46805
- CVE-2024-21887
- CVE-2023-48788
Earth Estries’s Recent Campaigns Highlights and Trends
Here are some recent highlights and trends from Earth Estries’ campaigns:
Persistent Tactics and Techniques:
- Earth Estries employs two main attack chains. The first uses tools like PsExec, Trillclient, Hemigate, and Crowdoor, delivered via CAB files. The second chain involves malware such as Zingdoor and SnappyBee, delivered through cURL downloads.
- They exploit vulnerabilities in systems like Microsoft Exchange servers and network adapter management tools to gain initial access.
Use of Advanced Malware:
- Earth Estries has been using advanced malware like GhostSpider, MASOL RAT, and Demodex rootkit. GhostSpider, in particular, is known for its modular architecture, encrypted communications, and persistence mechanisms.
- These tools enable Earth Estries to conduct prolonged cyber espionage campaigns targeting critical industries globally, including telecommunications, government entities, and critical infrastructure.
Exploitation of Public-Facing Vulnerabilities:
- They exploit multiple N-day vulnerabilities in products like Ivanti Connect Secure, Fortinet FortiClient EMS, Sophos Firewall, and Microsoft Exchange Server.
- This allows them to bypass authentication, execute commands with elevated privileges, and maintain long-term access to targeted systems.
Data Exfiltration and Stealth:
- Earth Estries uses tools like Trillclient for data collection and exfiltration, often sending information to anonymized file-sharing services.
- They employ advanced stealth techniques, such as operating primarily in memory and using encrypted C&C communications, to evade detection.