


BRONZE BUTLER, also known as Tick or REDBALDKNIGHT, is a sophisticated and persistent cyber espionage group believed to originate from China. The group primarily targets Japanese organizations, focusing on sectors such as government, manufacturing, biotechnology, electronics, and heavy industry, with a consistent goal of stealing intellectual property and sensitive business information. BRONZE BUTLER isknown for its advanced capabilities in exploiting zero-day vulnerabilities—most recently in 2025, when it leveraged a critical zero-day in MotexLanscopeEndpoint Manager to gain SYSTEM-level access, sharply increasing its impact on Japanese strategic industries.
Alias:
REDBALDKNIGHT, TAG-74, Tick Group
Motivation:
Espionage, Information theft
Target Technologies:
Office Suites Software, Operating System, Web Application, Lanscope Endpoint Manager.
Tools Used:
SymonLoader, Gofarer, Datper, HomamDownloader, Daserf, PsExec, WCE, 9002 RAT, cmd, Net, gsecdump, Blogspot, Elirks, schtasks, 8.t Dropper, Lilith RAT, VBS, at, whoami, Mimikatz, Minzen, Gh0st RAT, Windows Credential Editor, ShadowPad Winnti, rarstar, procdump.
Malware used by the BRONZE BUTLER:
Bisonal,8.t Dropper, PsExec, ShadowPy, Windows Credential Editor, SymonLoader, Netboy, Daserf, Gofarer, Lilith RAT, Elirks,9002 RAT,rarstar,gsecdump,whoami,Ghostdown,ReVBShell,Minzen,HomamDownloader,Mimikatz,Datper,ShadowPad Winnti,Gh0st RAT, Gokcpdoor, procdump.
Targeted Countries:
Japan, South Korea, Taiwan, and Russia
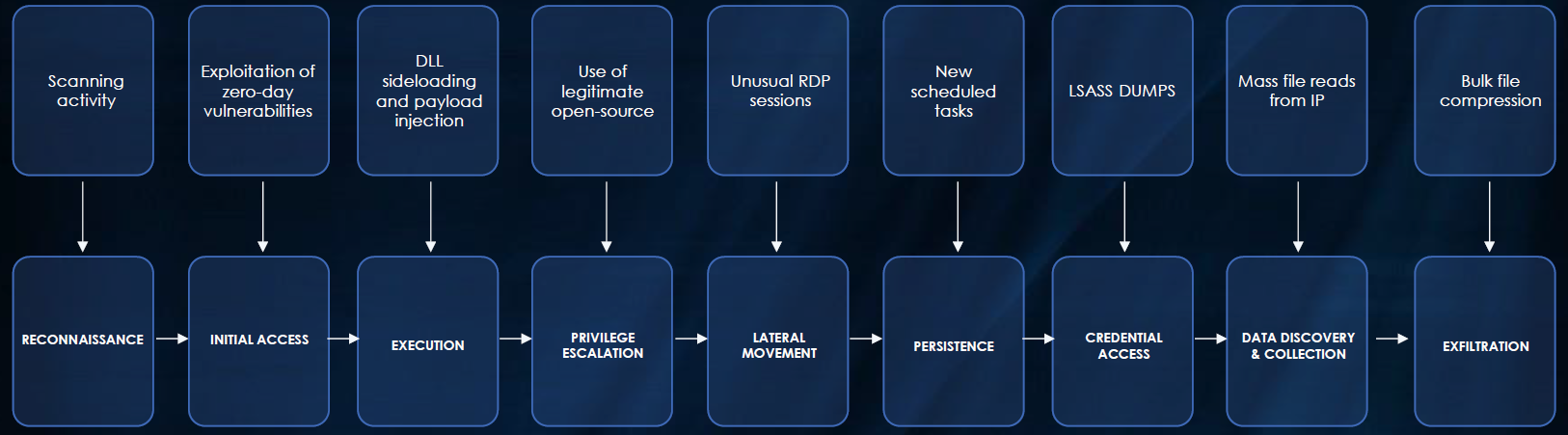
ATTACK FLOW DIAGRAM OF APT THREAT ACTOR BRONZE BUTLER
Recently Exploited Vulnerabilities by the BRONZE BUTLER
| CVE ID | Affected Products | CVSS Score | Exploit Links |
| CVE-2025-61932 | Lanscope Endpoint Manager | 9.8 | – |
| CVE-2021-27065 | Microsoft Exchange Server | 7.8 | Link1, link2 |
| CVE-2021-26855 | Microsoft Exchange Server | 9.8 | Link1, link2, link3, link4 |
| CVE-2021-26858 | Microsoft Exchange Server | 7.8 | – |
| CVE-2021-26857 | Microsoft Exchange Server | 7.8 | – |
| CVE-2018-0802 | Microsoft Office | 7.8 | – |
BRONZE BUTLER’s Recent Campaign Highlights and Trends
Recent Campaign Highlights
Key Trends in Recent Campaigns
| Tactic | ID | Technique |
| Resource Development | T1588.002 | Obtain Capabilities: Tool |
| Initial Access | T1189 | Drive-by Compromise |
| Initial Access | T1566.001 | Phishing: Spear phishing Attachment |
| Execution | T1059.001 | Command and Scripting Interpreter: PowerShell |
| Execution | T1059.003 | Command and Scripting Interpreter: Windows Command Shell |
| Execution | T1059.005 | Command and Scripting Interpreter: Visual Basic |
| Execution | T1059.006 | Command and Scripting Interpreter: Python |
| Execution | T1204.002 | User Execution: Malicious File |
| Execution | T1203 | Exploitation for Client Execution |
| Execution | T1053.005 | Scheduled Task/Job: Scheduled Task |
| Execution | T1053.002 | Scheduled Task/Job: At |
| Persistence | T1547.001 | Boot or Logon Autostart Execution: Registry Run Keys / Startup Folder |
| Persistence | T1574.001 | Hijack Execution Flow: DLL |
| Persistence | T1053.002 | Scheduled Task/Job: At |
| Persistence | T1053.005 | Scheduled Task/Job: Scheduled Task |
| Privilege Escalation | T1548.002 | Abuse Elevation Control Mechanism: Bypass User Account Control |
| Privilege Escalation | T1547.001 | Boot or Logon Autostart Execution: Registry Run Keys / Startup Folder |
| Privilege Escalation | T1574.001 | Hijack Execution Flow: DLL |
| Privilege Escalation | T1053.005 | Scheduled Task/Job: Scheduled Task |
| Privilege Escalation | T1053.002 | Scheduled Task/Job: At |
| Defense Evasion | T1070.004 | Indicator Removal: File Deletion |
| Defense Evasion | T1550.003 | Use Alternate Authentication Material: Pass the Ticket |
| Defense Evasion | T1548.002 | Abuse Elevation Control Mechanism: Bypass User Account Control |
| Defense Evasion | T1140 | Deobfuscate/Decode Files or Information |
| Defense Evasion | T1574.001 | Hijack Execution Flow: DLL |
| Defense Evasion | T1562.001 | Impair Defenses: Disable or Modify Tools |
| Defense Evasion | T1036.005 | Masquerading: Match Legitimate Resource Name or Location |
| Defense Evasion | T1036 | Masquerading |
| Defense Evasion | T1027.003 | Obfuscated Files or Information: Steganography |
| Defense Evasion | T1027.001 | Obfuscated Files or Information: Binary Padding |
| Defense Evasion | T1036.002 | Masquerading: Right-to-Left Override |
| Credential Access | T1003.001 | OS Credential Dumping: LSASS Memory |
| Discovery | T1083 | File and Directory Discovery |
| Discovery | T1007 | System Service Discovery |
| Discovery | T1124 | System Time Discovery |
| Discovery | T1087.002 | Account Discovery: Domain Account |
| Discovery | T1518 | Software Discovery |
| Discovery | T1018 | Remote System Discovery |
| Lateral Movement | T1080 | Taint Shared Content |
| Lateral Movement | T1550.003 | Use Alternate Authentication Material: Pass the Ticket |
| Collection | T1113 | Screen Capture |
| Collection | T1560.001 | Archive Collected Data: Archive via Utility |
| Collection | T1039 | Data from Network Shared |
| Collection | T1005 | Data from Local System |
| Command and Control | T1071.001 | Application Layer Protocol: Web Protocols |
| Command and Control | T1132.001 | Data Encoding: Standard Encoding |
| Command and Control | T1573.001 | Encrypted Channel: Symmetric Cryptography |
| Command and Control | T1105 | Ingress Tool Transfer |
| Command and Control | T1102.001 | Web Service: Dead Drop Resolver |