


APT42 is an Iranian state-sponsored cyber espionage group tasked with conducting information collection and surveillance operations against individuals and organizations of strategic interest to the Iranian government. We estimate with moderate confidence that APT42 operates on behalf of the Islamic Revolutionary Guard Corps (IRGC) Intelligence Organization (IRGC-IO) based on targeting patterns that align with the organization’s operational mandates and priorities.
Active since at least 2015, APT42 is characterized by highly targeted spear phishing and surveillance operations against individuals and organizations of strategic interest to Iran. The group’s operations, which are designed to build trust and rapport with their victims, have included accessing the personal and corporate email accounts of government officials, former Iranian policymakers or political figures, members of the Iranian diaspora and opposition groups, journalists, and academics who are involved in research on Iran. After gaining access, the group deployed mobile malware capable of tracking victim locations, recording phone conversations, accessing videos and images, and extracting entire SMS inboxes. APT42 has demonstrated the ability to alter its operational focus as Iran’s priorities evolve over time. We anticipate APT42 will continue to conduct cyber espionage operations in support of Iran’s strategic priorities in the long term based on its extensive operational history and imperviousness to public reporting and infrastructure takedowns.
Alias: APT42 Alias Mint Sandstorm, TA453, Yellow Garuda
Motivation: Espionage
USA, Canada, United Kingdom, Germany, France, Middle East, Australia

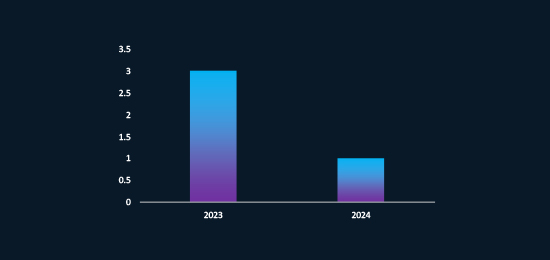
Malware used by APT 42
NICECURL,TAMECAT,NokNok
Tools used by APT42:
CHAIRSMACK, GHAMBAR, POWERPOST, BROKEYOLK, MAGICDROP, PINEFLOWER, TABBYCAT, TAMECAT, VBREVSHELL, VINETHORN, DOSTEALER
| Reconnaissance | Execution | Defense Evasion | Lateral Movement |
| T1595.002 | T1047 | T1218.011 | T1021.001 |
| T1589.001 | T1053.005 | T1027 | |
| T1598.003 | T1059.003 | T1562.001 | Collection |
| T1589.002 | T1059.001 | T1036.005 | T1114 |
| T1589 | T1204.001 | T1112 | T1005 |
| Resource Development | T1204.002 | T1562 | T1113 |
| T1585.002 | T1059.005 | T1564.003 | T1114.002 |
| T1583.006 | T1070.004 | T1114.001 | |
| T1588.002 | Persistence | T1562.004 | T1560.001 |
| T1584.001 | T1505.003 | T1070.003 | T1056.001 |
| T1583.001 | T1053.005 | ||
| T1586.002 | T1136.001 | Credential Access | Command and Control |
| T1585.001 | T1547.001 | T1003.001 | T1071.001 |
| Initial Access | T1098.002 | T1056.001 | T1571 |
| T1566.003 | T1102.002 | ||
| T1189 | Privilege Escalation | Discovery | T1065 |
| T1566.002 | T1053.005 | T1016 | T1071 |
| T1190 | T1547.001 | T1049 | T1105 |
| T1057 | |||
| T1087.003 | |||
| T1033 | |||
| T1082 | |||
| T1083 |