


CYFIRMA Research has conducted an in-depth analysis of a critical vulnerability, CVE-2023-50164, that has been discovered in Apache Struts 2, affecting multiple organizations and systems globally. This flaw enables remote code execution and file upload attacks, posing a severe threat to security. The affected versions of Apache Struts 2 necessitate immediate attention, and organizations are urged to implement mitigation measures outlined by cybersecurity experts to safeguard their systems.
Apache Struts 2, a widely used open-source web application framework, has become the focal point of concern due to the identification of CVE-2023-50164, a critical vulnerability with the potential for remote code execution. This vulnerability exposes organizations to severe security risks, allowing attackers to upload malicious files and execute arbitrary code.
Key Takeaways:
Acknowledgements:
CYFIRMA Research acknowledges the collaborative efforts of security researchers and the cybersecurity community in identifying and addressing CVE-2023-50164 vulnerability.
Vulnerability Type: Unauthenticated Remote Code Execution (RCE) via Apache Struts File Upload
CVE ID: CVE-2023-50164
CVSS Severity Score: 9.8 (Critical)
Application: Apache Struts 2
Impact: Allows unauthenticated attackers to execute arbitrary code by exploiting a file upload vulnerability
Severity: Critical
Affected Versions: Multiple versions of Apache Struts 2 are impacted; refer to the link
Patch Available: Yes
CVE-2023-50164 is a critical vulnerability in Apache Struts 2, allowing attackers to execute arbitrary code and perform file upload attacks remotely. CYFIRMA researchers have dissected the intricacies of the flaw, revealing its potential severity. The vulnerability stems from a weakness in the file upload mechanism, making it exploitable by malicious actors to compromise targeted systems.
The impact of CVE-2023-50164 is severe, as it opens the door for remote code execution and unauthorized file uploads. Malicious actors can leverage this vulnerability to compromise the integrity and confidentiality of affected systems, leading to potential data breaches, unauthorized access, and system manipulation.
The vulnerability affects multiple versions of Apache Struts 2. Organizations using these versions are at risk and must take immediate action to remediate the issue. For detailed information and affected versions, check here.
Is there already an exploit tool to attack this vulnerability?
As of the latest available information, there is a known public exploit tool for CVE-2023-50164 targeting Apache Struts 2. The availability of a publicly available exploit tool provides a limited opportunity for organizations to address and remediate the vulnerability before potential malicious actors can capitalize on it.
Has this vulnerability already been used in an attack?
Specific information confirming exploitation of CVE-2023-50164 is currently not available. Although there are no concrete reports or observations of exploitation attempts in the last 30 days, continuous monitoring is essential to detect any emerging threats or exploitation activities.
Are hackers discussing this vulnerability in the Deep/Dark Web?
CYFIRMA’s observations indicate current discussions or identified potential exploitation of CVE-2023-50164 in the Deep/Dark Web. The dynamic nature of the threat landscape emphasizes the importance of ongoing monitoring of underground forums and channels to promptly identify any evolving discussions or emerging threats.
What is the attack complexity level?
The attack complexity level for CVE-2023-50164 in Apache Struts 2 is assessed as LOW. While there is a public exploit tool currently available, the potential for exploitation remains, and organizations should prioritize mitigation efforts.
Historical Trends and Known Exploits:
There are few known exploits or historical trends for CVE-2023-50164 as of the latest information. However, given the historical context of threat actors targeting vulnerabilities, organizations should stay vigilant, as exploitation attempts could lead to unauthorized access, data breaches, or compromise of web applications. Regular updates and proactive security measures are essential to safeguard against evolving cyber threats.
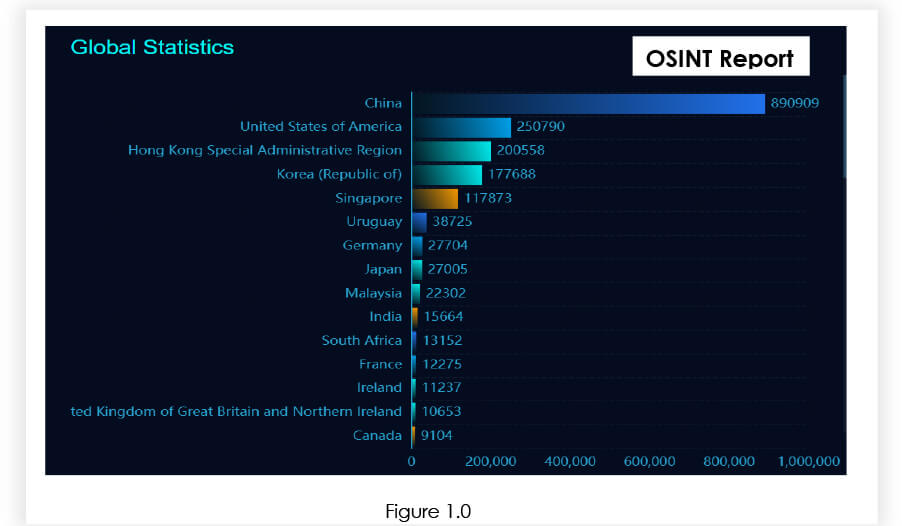
During our analysis we found that more than 1,718,898+ Struts2 are public, and which can be vulnerable to CVE-2023-50164. Refer fig 1.0.
The vulnerability exploits case sensitivity in HTTP parameters, enabling attackers to introduce lowercased parameters and override critical internal variables, as exemplified by cases like param1=”value1″ versus Param1=”Value1″.
Recent commits by the Apache team signify a strategic response to mitigate the vulnerability. The introduction of case-insensitive comparison through the equalsIgnoreCase() method represents a critical enhancement, seeking to eliminate susceptibility to case sensitivity manipulation. This adjustment aims to fortify the Apache Struts framework against potential exploitation.
At the core of the vulnerability is parameter pollution, wherein attackers manipulate requests by introducing lowercased parameters. This manipulation, when processed by the ActionSupport class, facilitates the introduction of path traversal characters. The flaw, residing in AbstractMultiPartRequest.java, circumvents the getCanonicalName function, allowing the persistence of path traversal payloads in the final filename.
A parallel concern relates to the handling of temporary files generated during uploads. Initial vulnerabilities allowed for non-deletion of these files if they exceeded a certain size, potentially enabling persistence.
Recognizing this risk, a pivotal commit “Always delete uploaded file” was introduced by the Apache team. This commitment ensures the consistent deletion of temporary files after upload, effectively closing a potential avenue for persistent attacks. The detailed process and significance of this commit highlight the proactive measures taken to address identified security risks.
The practical manifestation of this vulnerability is revealed through intentionally crafted requests. Notably, the parameter “Upload” is deliberately mixed with uppercase and lowercase letters, highlighting the real-world nuances of case sensitivity manipulation in an actual request.
The exploitation and analysis of CVE-2023-50164 underscore the intricate interplay of case sensitivity in HTTP parameters, potential path traversal risks, and the evolution of temporary file handling within the Apache Struts framework. The proactive responses from the Apache team, reflected in recent code changes, attest to an ongoing commitment to fortify the security posture of this widely used framework.
To mitigate the risk posed by CVE-2023-50164, organizations should promptly apply security updates provided by Apache Struts 2. Additionally, implementing custom rules, monitoring file uploads, and enhancing web application firewall configurations can enhance protection against potential exploitation. Timely mitigation is crucial to prevent unauthorized access and code execution on vulnerable systems.
Target Geography: Organizations worldwide relying on Apache Struts 2, falling within the affected versions of CVE-2023-50164, may face potential risks. The impact of this vulnerability is not constrained by geography, extending to regions like North America, Europe, Asia-Pacific, and other areas where Apache Struts 2 is deployed. Organizations globally, regardless of location, may be exposed to the risk of exploitation if they utilize the affected versions of Apache Struts 2.
Target Industry: The CVE-2023-50164 vulnerability in Apache Struts 2 poses a threat to organizations across various industries, including healthcare, finance, government, telecommunications, and other sectors relying on Apache Struts 2 for web application development. Threat actors with knowledge of this vulnerability may selectively target industries based on the perceived value of the data or services handled by Apache Struts 2 instances. Industries dealing with sensitive information or heavily dependent on Apache Struts 2 for web application security may become specific targets.
Target Technology: The CVE-2023-50164 vulnerability specifically impacts Apache Struts 2, a critical framework for web application development. While the immediate impact is on Apache Struts 2 instances, successful exploitation may extend beyond, compromising interconnected systems, applications, and servers linked with Apache Struts 2. This amplifies the potential impact on an organization’s technological infrastructure, emphasizing the need for comprehensive mitigation measures.
Understanding the potential impact across different geographic regions, industries, and technologies is imperative for organizations to assess their exposure to CVE-2023-50164. It underscores the urgent need for addressing the issue through prompt patching, proactive security measures, and continuous monitoring to mitigate the risks associated with this critical vulnerability.
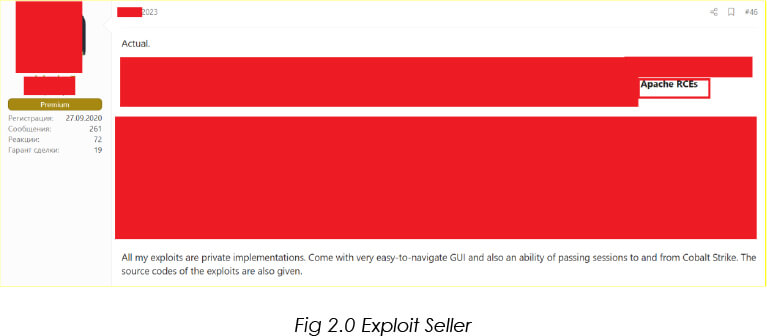
From underground forums, CYFIRMA Research team has observed that unknown hackers are selling exploit.
The severity of CVE-2023-50164 demands immediate attention from organizations to safeguard the ongoing integrity and confidentiality of their digital infrastructure. CYFIRMA’s research enhances the understanding of the nuances surrounding this vulnerability, empowering organizations with valuable insights to fortify their defenses. Organizations relying on Apache Struts 2 must expedite the application of available patches, implement proactive security measures, and engage in continuous monitoring to thwart potential exploitation.