



At CYFIRMA, we are dedicated to delivering current insights into prevalent threats and malicious tactics targeting both organizations and individuals. This report examines a newly identified threat, dubbed “Ailurophile Stealer,” which has been discovered on GitHub. The stealer is designed to compromise the victim’s system by extracting sensitive browser data, including stored credentials, cookies, and browsing history. This report details the threat’s mechanisms, distribution methods, and potential impact on cybersecurity.
The Ailurophile Stealer was first discovered on GitHub. The threat actor behind this malware operates a website shielded by Cloudflare, which promotes and supports its distribution. This site features a referral program and offers a free three-day trial to attract users. Additionally, it includes a web panel that allows users to customize and generate malware stubs, amplifying the malware’s reach and effectiveness.

● The stealer places Portable Executable (PE) files in the startup folder to ensure they run automatically with each system boot.
● The malware seeks to collect and exfiltrate browser data, such as browsing history and passwords.
● The stealer attempts to load any missing Dynamic Link Libraries (DLLs) that may be essential for its operation or to enhance its functionality.
Behavioral Analysis:
| File Name | Ailurophile_build_test.exe |
| File size | 9.44MB |
| Signed | Not signed |
| MD5 Hash | 520e6676a4e53b73d9f8afab560767b9 |
| SHA-256 Hash | 5508e6e9f62af269f48301f4149cabfb7d421b39d94559ae88a96dc88ddf7501 |
| First seen in the wild | August 2024 |
The Analysis of the file established that it is packed with UPX-encrypted files.
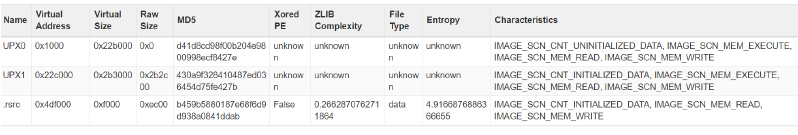
Step 1: Initial Execution
Ailurophile_build_test.exe: The malware begins its execution when the user or system launches the executable. This is the primary process that initiates all subsequent activities. The executable is packed with the UPX packer, making it harder to analyze by compressing and obfuscating its contents.
Step 2: Command Prompt (cmd.exe) Initiation
Instance 1:
Command: cmd.exe /s /c “cls”: Clears the command prompt screen, possibly to remove traces of previous commands or to prepare for further actions without leaving obvious artifacts.
Instance 2:
Command: cmd.exe /s /c “wmic OS get Caption”: Executes a command to retrieve the operating system’s caption, which is part of the discovery process, helping the malware understand the environment it is operating in.
Instance 3:
Command: cmd.exe /s /c “wmic OS get Version” Queries the OS version, another step in the discovery process to tailor the malware’s behavior based on the specific OS version.
Step 3: Windows Management Instrumentation (WMIC) Execution
Instance 1:
Command: wmic OS get Caption: Retrieves the OS caption, as queried by the previous cmd.exe command. WMIC is a powerful tool for interacting with the Windows Management Instrumentation (WMI) to extract system details.
Instance 2:
Command: wmic OS get Version: Retrieves the OS version information, completing the discovery commands initiated earlier.
Step 4: PowerShell Execution
powershell.exe: Executes a PowerShell script that alters the execution policy and decrypts data using the Windows Data Protection API (DPAPI). The script likely retrieves sensitive information, such as decryption keys, which could be used to access encrypted data or files.
Step 5: Task List Retrieval
Command: cmd.exe /s /c “tasklist”: Executes the tasklist command to retrieve a list of currently running processes. This can be used by the malware to identify security software or other processes that might interfere with its operations.
Step 6: Console Host (conhost.exe) Interaction
The malware spawns a conhost.exe process, which acts as a console host for the cmd.exe processes. This is a normal system process, but its use here indicates that the malware is leveraging command-line interactions extensively.
Step 7: Network Communication Initiation
The malware initiates network communication, particularly sending HTTP GET requests to external domains like api.ipify.org to check the external IP address. This information could be used to tailor further actions based on the network environment.
Step 8: Command and Control (C2) Communication
The malware establishes communication with its external C2 server. This server connection is used to receive commands, exfiltrate data, and potentially download additional malicious payloads.
Step 9: Telegram API Interaction
The malware interacts with the Telegram API via api.telegram.org, likely as an alternative C2 channel. Telegram is used due to its encrypted communication, making it a stealthy method for attackers to manage the malware.

Resource Development:
The malware likely engaged in resource development by leveraging external infrastructure and APIs (api.telegram.org) to support its operations, including data exfiltration and communication with a command-and-control server. These resources would have been established prior to deployment to ensure the malware’s effectiveness in carrying out its objectives.
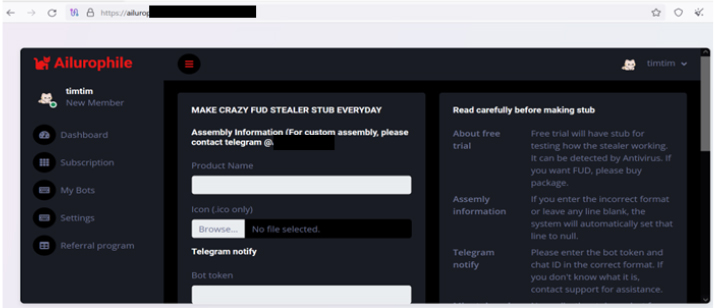
Execution:
The malware executes its payload by launching processes such as cmd.exe and powershell.exe to run system commands and scripts, which allows it to initiate its malicious activities. The invocation of these processes indicates that the malware directly interacts with the system to carry out its tasks, such as modifying settings and downloading additional payloads.

Credential Access:
The malware likely harvests browser information, which could include stored credentials such as passwords and session tokens. This data is then exfiltrated to the attacker’s server, providing them with access to the victim’s accounts and sensitive information.

Discovery:
The use of WMIC.exe by the malware suggests that it conducts system discovery to gather information about the operating environment. This might include querying system configurations, running processes, and installing software, which can inform subsequent actions or targeting decisions.

Collection:
The malware is designed to collect sensitive information, including browser data, which is then sent to its command-and-control server. This collected data may include credentials, browsing history, and other personal information, which could be used for further exploitation or sold on illicit markets.

Command and Control:
The malware establishes command-and-control communication with external servers, such as api.telegram.org, to receive instructions and exfiltrate stolen data. This connection allows the attacker to maintain control over the infected system and dynamically adjust the malware’s behavior based on real-time commands.

During our investigation, we discovered that the Ailurophile Stealer was first established on GitHub in August 2024.
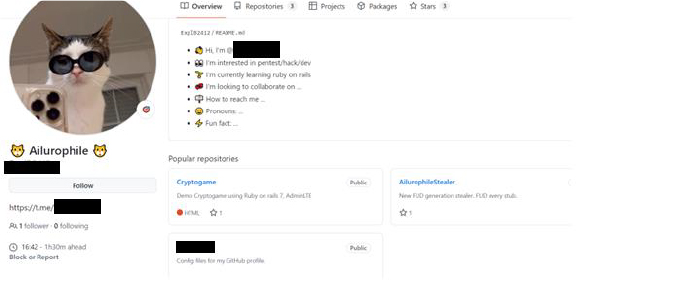
It has also been identified that the threat actor is likely based in Vietnam. This assessment is supported by the IP address 103.252.123.135 associated with http.favicon.hash:-145938113 which provides medium confidence in confirming the threat actor’s location.

The time zone indicated in the screenshot indicates Vietnam.

Using the icon hash, additional domains that resemble the login pages of the Ailurophile Stealer website are identified:

The threat actor behind the Ailurophile Stealer has also created a repository on Giter.Club, where they have shared details about the Ailurophile Stealer. The information shared on this platform includes specifics about the malware and potentially other technical or operational details related to its deployment and functionality.


Ailurophile Stealer poses a significant threat to both organizations and individuals by targeting sensitive browser data, such as stored credentials and browsing history. Utilizing various system processes and communication channels, the malware efficiently exfiltrates data while maintaining command-and-control communication. Its distribution through GitHub and a referral-based web platform amplifies its reach. To mitigate such threats, organizations should strengthen data protection policies, enhance threat intelligence capabilities, and deploy robust anti-malware solutions.
Strategic Recommendations
Management Recommendations
Tactical Recommendations
| No | Indicator | Remarks |
| 1 | 520e6676a4e53b73d9f8afab560767b9 | Block |
| 2 | 103[.]252[.]123[.]135 | Monitor |
| 3 | 58bd748483b75a3a6470075e2e57d679 | Block |