



The CYFIRMA research team has identified a destructive malware; WinDestroyer. The ransomware lacks ransom demands, pointing to non-financial motivation. This sophisticated threat employs advanced techniques, such as DLL reload attacks, API hammering, and lateral movement capabilities, rendering systems unusable. The geopolitical motivation is evident through the associated YouTube channel featuring praise for the Russian president. By investigating Russian leaked databases, we were able to reveal the real identity of the threat actor behind the malware. This report talks about WinDestroyer’s capabilities, the hacktivist angle, and the identified threat actor, providing valuable insights for attribution and proactive cybersecurity measures.
During the inspection of submissions to public sandboxes, the CYFIRMA research team came across a new malware named “WINDESTROYER.exe” that encrypts files and renders the targeted system unusable.
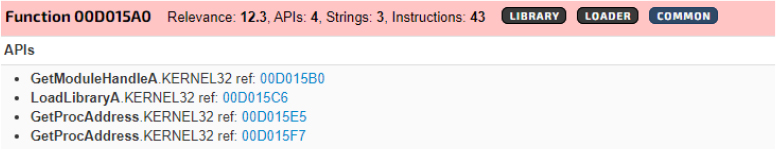
Functionality to make API calls
Enables the attacker to interact with the operating system, facilitating the execution of malicious commands and manipulation of system functions.
Infects the Volume Boot Record (VBR) of the hard disk
Alters the boot sector, giving the attacker persistence and control over the system during startup, allowing for stealthy and persistent malware execution.
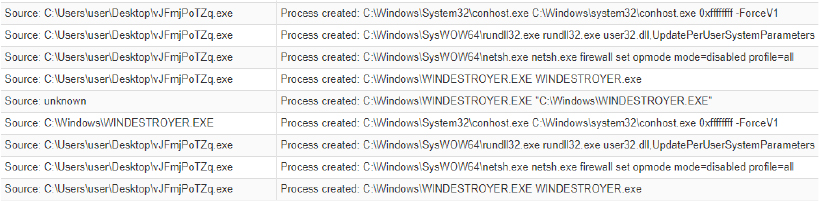
Process Injection
Permits the attacker to inject malicious code into legitimate processes, evading detection and executing unauthorized actions within the context of trusted applications.
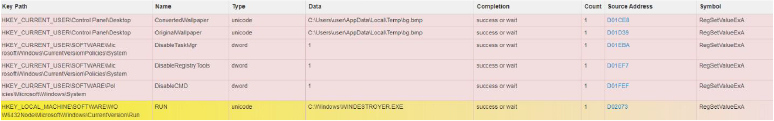
Registry changes
Facilitates the modification of critical system registry settings, enabling the attacker to achieve persistence and manipulate system configurations.
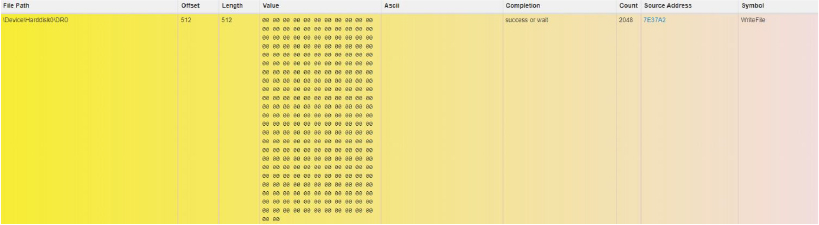
Functionality to open port and listen to incoming connections
Creates a backdoor for the attacker, allowing unauthorized access to the system and potentially facilitating the exfiltration of sensitive data.
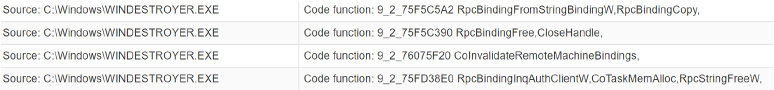
Creation of a DirectInput object for checking user activity
Provides the attacker with the ability to monitor and analyze user input, potentially capturing sensitive information such as passwords or keystrokes. The malware also takes a screenshot of the victim system using BitBlt API. The BitBlt function, which stands for “Bit Block Transfer,” is a Windows API function used for copying a rectangular block of pixels from one device context to another. It is often employed in graphics programming and is part of the Windows GDI (Graphics Device Interface) subsystem.
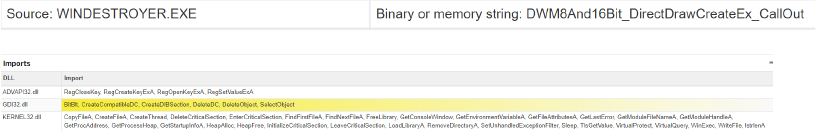
Functionality to enumerate network shares
Looks for low hanging fruits within the network by identifying and accessing shared resources, allowing unauthorized access to sensitive data on connected systems.
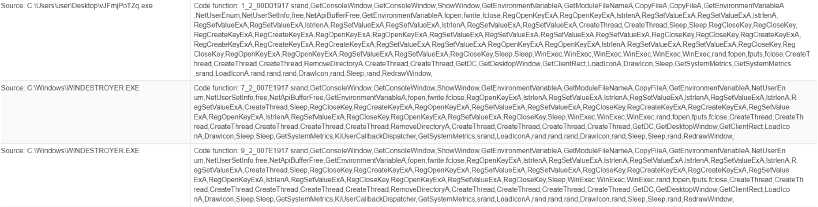
Functionality to list files within a directory
Facilitates reconnaissance by allowing the attacker to gather information on file structures, aiding in the encryption process.
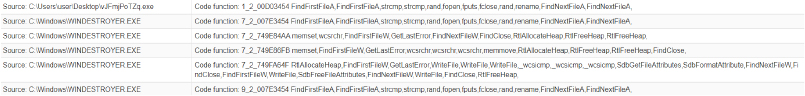
Functionality to prevent local debugging
Impedes the debugging process, making it more challenging for security professionals to analyze and detect malicious activities during the investigation.
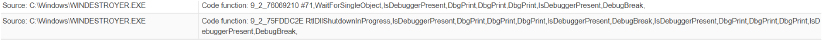
Infects Executable Files
Compromises the integrity of executable files, allowing the attacker to implant malicious code, leading to the execution of unauthorized commands or actions.
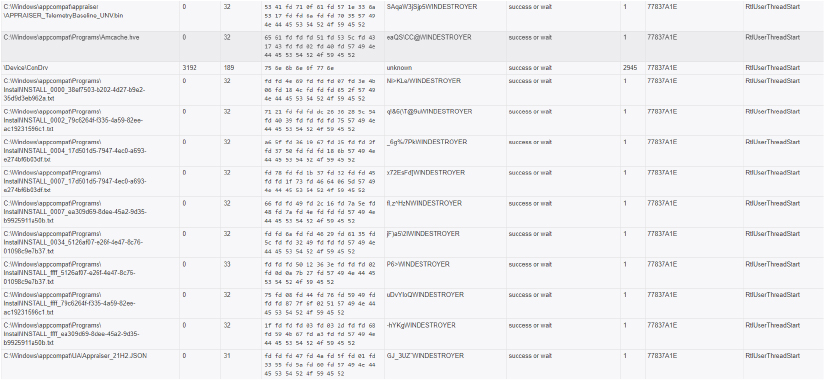
Encrypts documents and EXEs
Since the threat actor is not looking to make money with this encryptor, the other most common motivator is geopolitics. The malware is designed to render the victim systems non-functional once it’s executed, which is something hacktivists are likely going to enjoy taking credit for.
Upon investigating further, we came across a YouTube Channel with the name The WinDestroyer.
Email: theWinDestroyer@gmail[.]com

Note how the YouTube account profile picture has the Windows logo followed by the word “Destroyer”. The only post on the channel is a video glorifying Russian president Vladimir Putin.
This information was a valuable pointer for attribution. Including other evidence, we can ascertain with high confidence that the malware developer is from Russia and has likely created WinDestroyer to be used for hacktivism.
The sample was uploaded to one of the public sandboxes from the UK and Ukraine, which is in line with our victimology assessment that the Russian threat actor is actively spreading it in the wild to targets in countries that are “not friendly” to Russia.
Further to this, we started looking into people from Russian origin who might have used this username (since the developer is clearly obsessed with it). Not to our surprise, we found multiple hits for “WinDestroyer” within leaked Russian databases. This led us to find the real name, city of residence, previously used IP address and suspected social media handles of the geopolitically motivated malware developer.
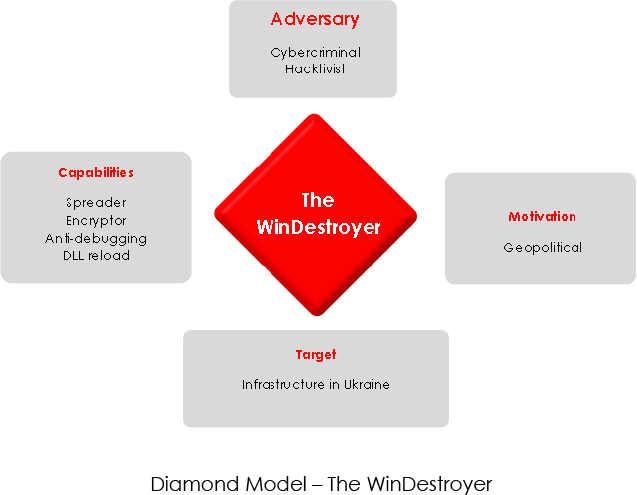
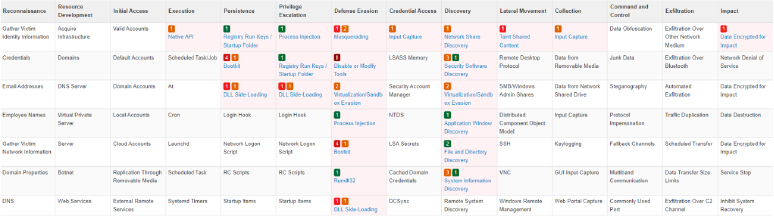
WinDestroyer’s intent aligns with hacktivist intent, emphasizing disruption over financial gain. Amidst the ongoing Russia-Ukraine conflict, the malware could be employed strategically as a digital weapon. Being a noisy malware, any harm from this malware can be prevented by implementing basic endpoint detection and response controls. However, this will still pose a risk to some of the SMBs who lack those controls. By disrupting critical systems, disabling communication channels, and compromising sensitive data, the malware could significantly impact the targeted infrastructure. CTI practitioners must prioritize international collaboration and intelligence sharing to gain a deeper understanding of such emerging threats.
| Name | Indicator | Type |
| WINDESTROYER.exe | 83c23480f87f08d645b62bbd2448c40f | MD5 |