MATERIALS Q1 I 2026 : INDUSTRY REPORT
EXECUTIVE SUMMARY The CYFIRMA Industry Report delivers original cybersecurity insights and telemetry-driven


EXECUTIVE SUMMARY The CYFIRMA Industry Report delivers original cybersecurity insights and telemetry-driven

Fortnightly Vulnerability Summary CHECK OUT THESE FAST FACTS ON FORTNIGHTLY OBSERVED VULNERABILITIES.

Executive Summary The cyber threat landscape in the Philippines has intensified significantly over

EXECUTIVE SUMMARY CYFIRMA has identified a targeted malware campaign attributed to the Pakistan-aligned

EXECUTIVE SUMMARY Telegram is no longer just a messaging application. It has evolved into a primary

EXECUTIVE SUMMARY The CYFIRMA Industry Report delivers original cybersecurity insights and telemetry-driven

Executive Summary Saudi Arabia’s cyber threat landscape between 2025 and early 2026 reflects a convergence

EXECUTIVE SUMMARY CharlieKirk Grabber is a Python-based Windows infostealer, designed for rapid credential

Fortnightly Vulnerability Summary CHECK OUT THESE FAST FACTS ON FORTNIGHTLY OBSERVED VULNERABILITIES.

EXECUTIVE SUMMARY The CYFIRMA Industry Report delivers original cybersecurity insights and telemetry-driven

EXECUTIVE SUMMARY The January 2026 Ransomware Threat Report highlights a ransomware ecosystem that

Fancy Bear is a well-documented Russian state-sponsored threat actor that has been active since at

EXECUTIVE SUMMARY The CYFIRMA Industry Report delivers original cybersecurity insights and telemetry-driven
EXECUTIVE SUMMARY At CYFIRMA, we analyze attacker techniques that rely on legitimate installers and

INTRODUCTION CYFIRMA has identified an active and evolving Telegram phishing operation that abuses

EXECUTIVE SUMMARY CVE-2026-23760 represents a severe authentication bypass vulnerability in SmarterTools
EXECUTIVE SUMMARY The CYFIRMA Industry Report delivers original cybersecurity insights and telemetry-driven
EXECUTIVE SUMMARY Ransomware activity accelerated sharply from late 2025 into early 2026, with a growing
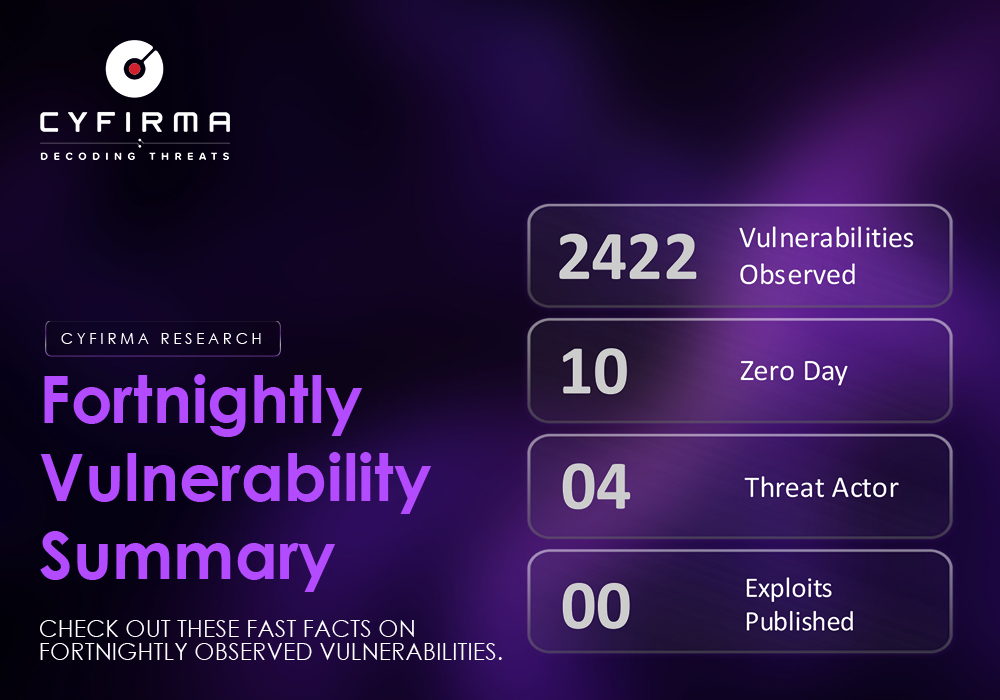
Fortnightly Vulnerability Summary CHECK OUT THESE FAST FACTS ON FORTNIGHTLY OBSERVED VULNERABILITIES.

EXECUTIVE SUMMARY The Android application Hicas, publicly advertised as a Smart Travel Packing Companion,