Published On : 2023-07-05
EXECUTIVE SUMMARY
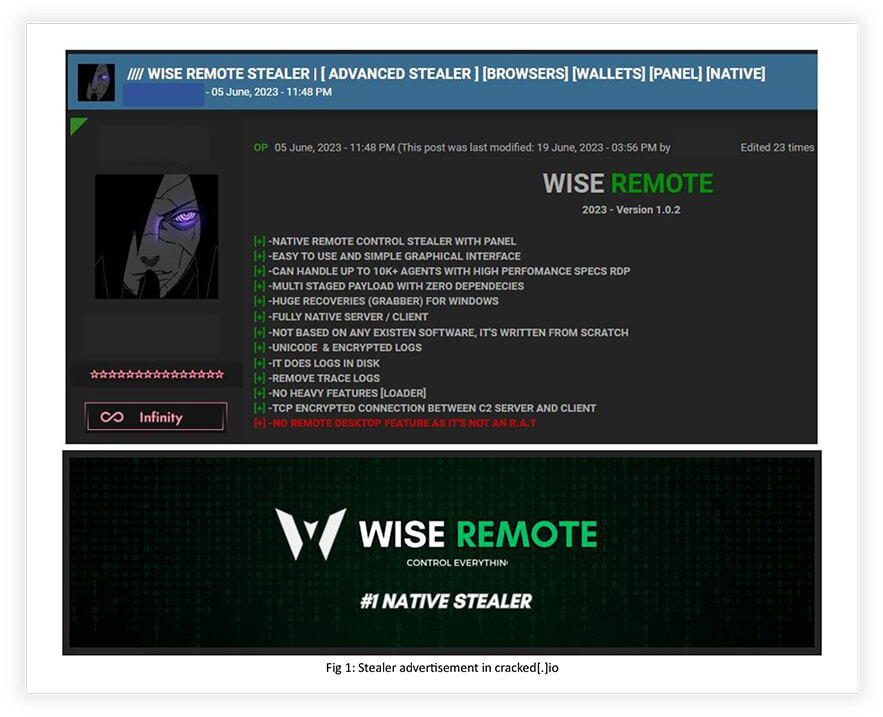
Information stealers remain an enduring and evolving security concern for individuals and organizations alike. CYFIRMA’s Research team has recently uncovered an advanced information stealer, known as “WISE REMOTE Stealer,” that functions as both a stealer and a Remote Access Trojan (RAT). This sophisticated malware has gained significant traction through promotion in underground forums such as HF and cracked[.]io. To facilitate their activities, the threat actor utilizes Telegram and Discord.
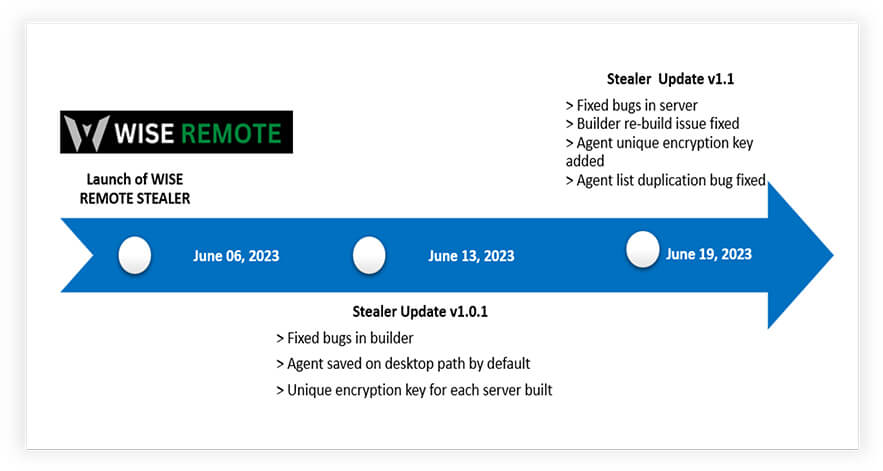
Continual enhancements are observed within the WISE REMOTE Stealer, as the threat actor diligently incorporates new features to amplify its effectiveness and expand its user base. This report offers in-depth insights into the comprehensive capabilities and features of WISE REMOTE Stealer, empowering stakeholders with a thorough understanding of its operational scope, and potential consequences to mitigate the associated risks effectively.
INTRODUCTION
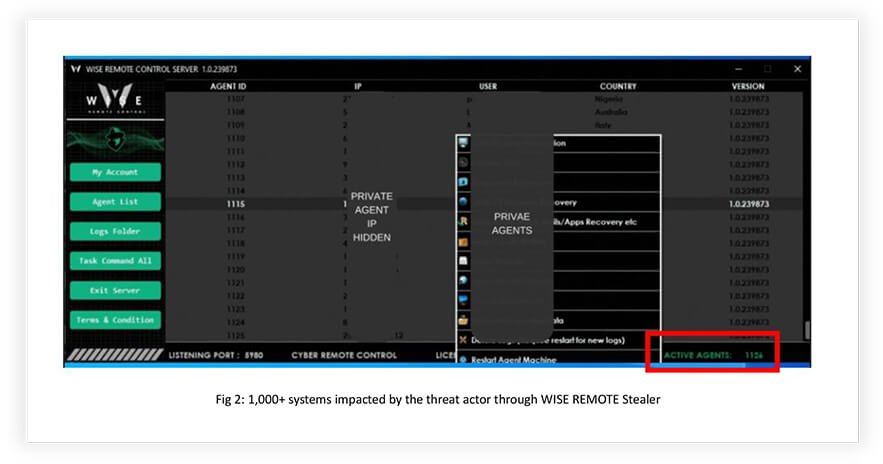
During the initial weeks of June 2023, the emergence of WISE REMOTE Stealer gathered significant interest within prominent underground forums due to its compelling features, capabilities, and competitive pricing. To establish credibility, the stealer underwent a testing phase, involving renowned veterans of the forum, who validated its efficacy and contributed valuable feedback for subsequent improvements, following a customary practice, when introducing new tools in the underground community. The demonstration of the tool revealed that the threat actor had already compromised over 1,000 systems independently across the globe, indicating the stealer’s effectiveness and potential to target a substantial number of systems in the upcoming days.
KEY OBSERVATIONS
- Demonstration of the tool indicated 1,000+ systems (Fig 2) already impacted across the globe by the threat actor alone, hinting at its effectiveness and capability to add a large number of victims in the coming days.
- The Stealer’s subscription is available for USD 40 per month, while a lifetime subscription costs USD 150. Added new features will be made available only for lifetime subscribers. Purchase payments are accepted only with cryptos and using HF contracts.
- This advanced stealer supports the conduct of Distributed Denial-of-Service (DDoS) operations, Ransomware attack, and other malicious activities.
Key Features of WISE REMOTE Stealer
- The WISE REMOTE Stealer malware is written in the Go language, and the threat actor prefers to code their malware using Go, C++, C#, and Python.
- The malware utilizes code manipulation techniques to evade detection by most antivirus products, making it difficult to detect and mitigate.
- The primary target of the malware is Windows operating systems, specifically versions 8, 10, and 11.
- The connection between the malware’s Command and Control (C2) server and the infected clients is encrypted using TCP , ensuring secure communication. Client-side modules are imported through a cloud server, and logs are temporarily stored in the disk’s temporary folder. Logs are then sent to the C2 panel for decryption and subsequently removed to leave no trace.
- The minimum server requirements for hosting the WISE Remote Stealer C2 panel include a CPU with 2+ cores, at least 3GB of RAM, and a Windows Server with Remote Desktop Protocol (RDP) enabled.
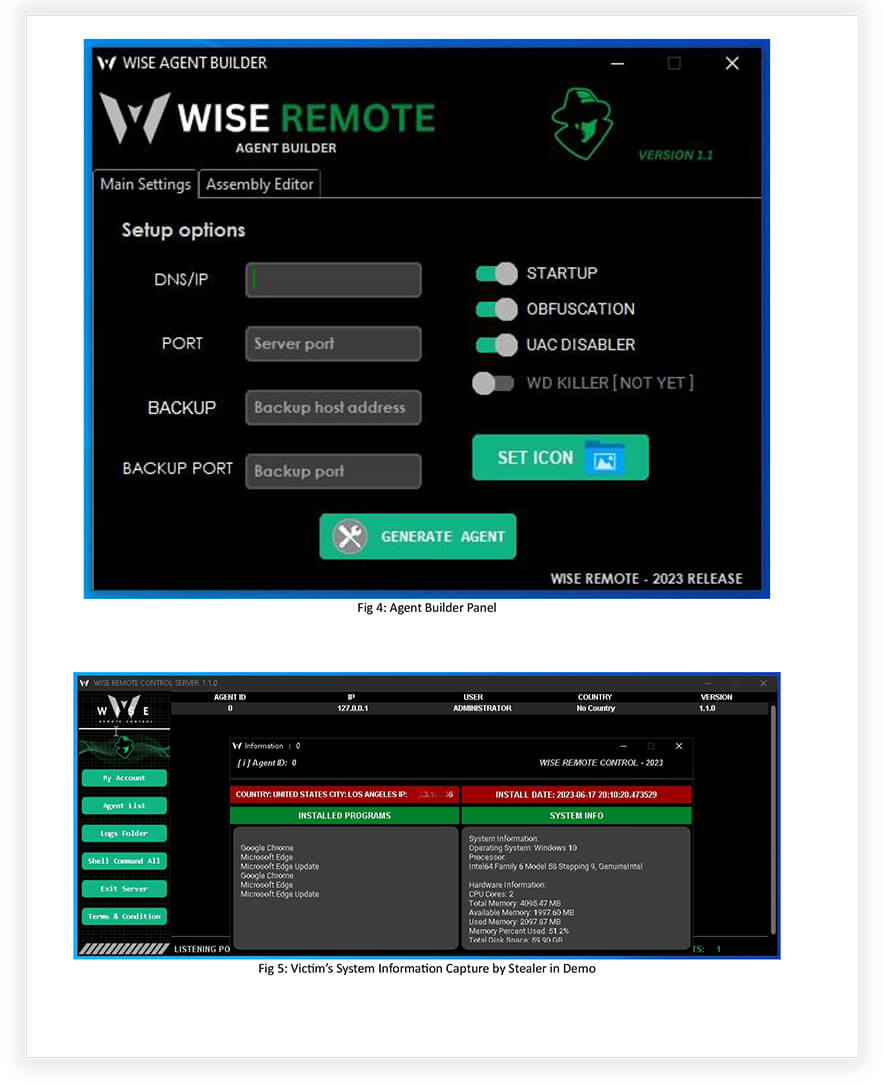
- The WISE Remote Stealer C2 panel provides an easy-to-use and visually appealing graphical interface, enabling monitoring of up to 10,000 victims with high performance. This panel has received positive feedback from veterans in the underground forum due to its simplicity and preconfigured build options, facilitating effortless malware creation.
- The builder tool associated with the malware simplifies the creation of .exe files, allowing customization of icons for easy propagation, based on the desired infection chain. The resulting builds are lightweight, typically less than 100 KB in size.
- Similar to a Remote Access Trojan (RAT), the builder offers the option to download and execute payloads by providing source URLs. This capability opens the door to launching further stages of attack, including ransomware deployment.
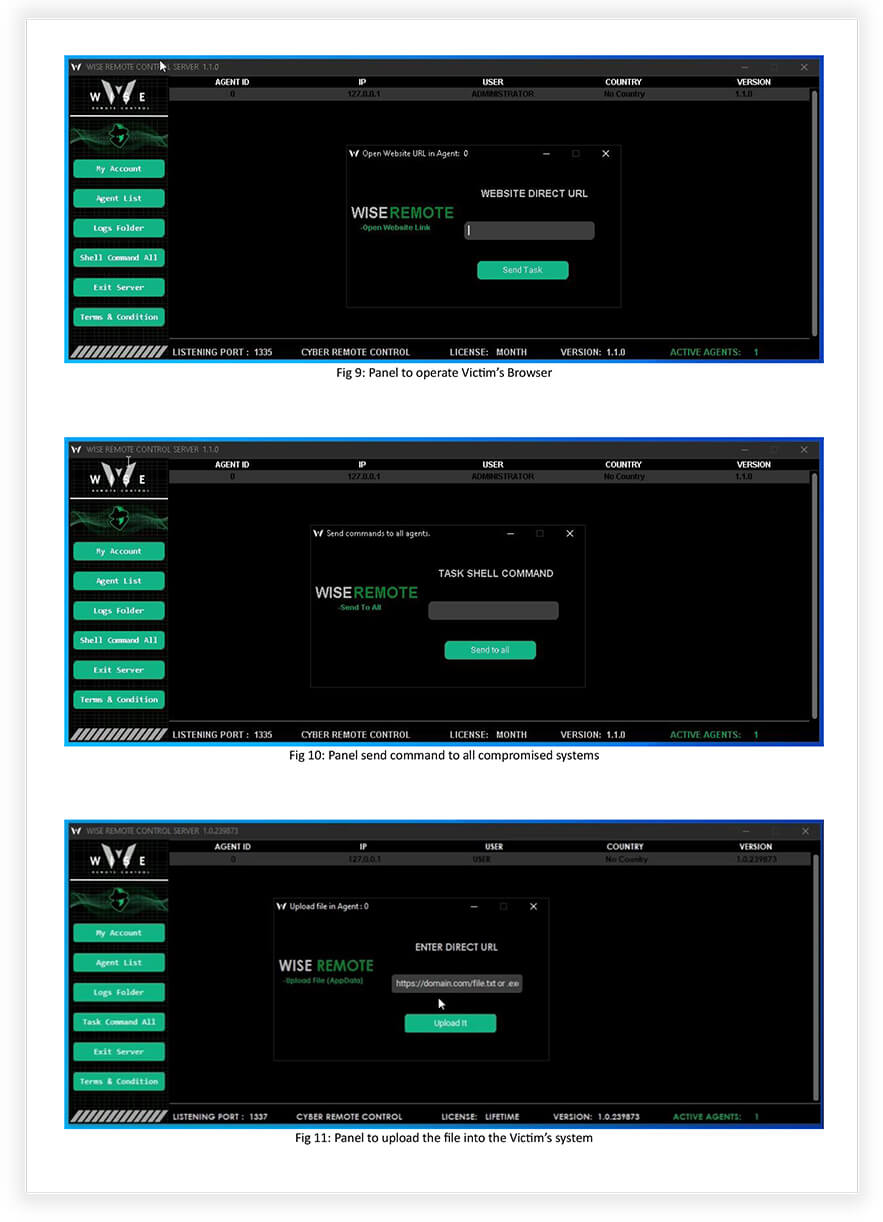
- Through the C2 panel, the threat actor can send shell commands (Fig 10) to all infected victims. By crafting specific commands, compromised systems can be transformed into bots, possibly enabling the threat actor to conduct Distributed Denial-of-Service (DDoS) operations or other malicious activities.
MALWARE CAPABILITIES
The “WISE REMOTE Stealer” possesses a range of advanced capabilities that allow it to compromise and control targeted systems. It has the ability to gather detailed information about the victim’s system, establish remote access, and execute commands from a remote location. This enables the attacker to carry out various malicious actions discreetly.
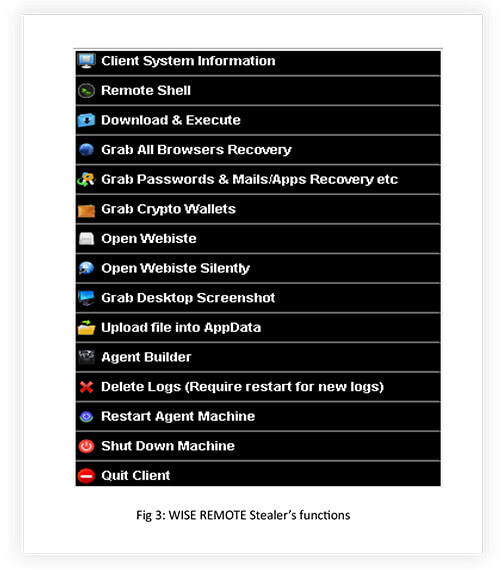
- Client System Information: Gather information about the targeted system to gain insight into its configuration and setup (Fig 5).
- Remote Shell: Gain unauthorized remote access to the compromised system, allowing the attacker to execute commands and control the system remotely.
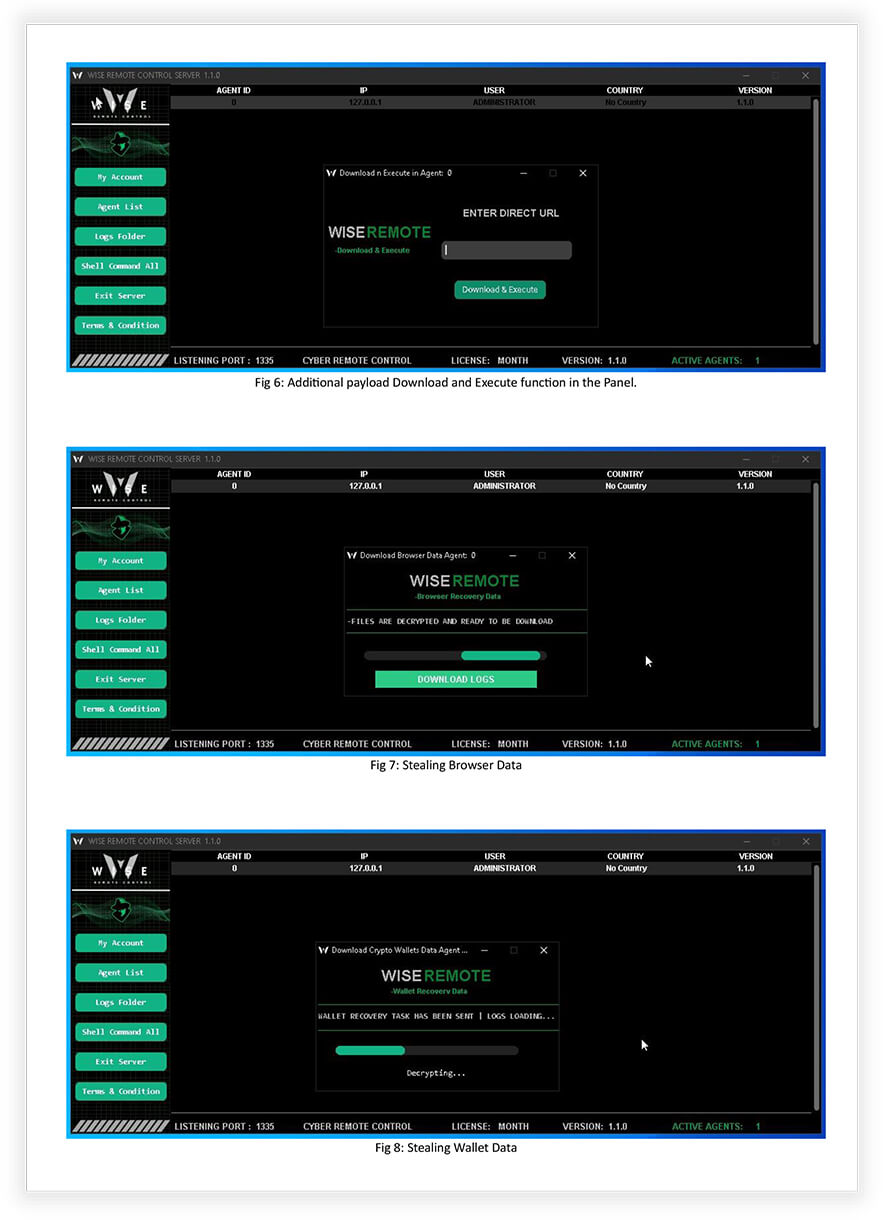
- Download and Execute: Download and run malicious files or programs on the compromised system, potentially enabling further malicious activities (Fig 6).
- Browser Data Extraction: Extract sensitive information from web browsers, including bookmarks, autofill data, credit card details, passwords, download history, browser extensions, browsing history, cookies, and local storage data (Fig 7).
- Grab Crypto Wallets: Steal cryptocurrency wallets stored on the compromised system, potentially gaining access to the victim’s digital assets (Fig 8).
- Open Website: Interact with websites, opening them or performing actions on them, potentially for malicious purposes (Fig 9). Stealthy Website Access: Open websites without alerting the user or displaying any visible indications of activity.
- Desktop Screenshot Capture: Capture screenshots of the victim’s desktop, potentially exposing sensitive information or monitoring user activity.
- AppData File Upload: Upload files to the AppData directory on the compromised system, potentially enabling persistence or facilitating further malicious actions (Fig 11).
- Agent Builder: Create and customize malware agents or components for specific attack scenarios or targets (Fig 4).
- Log Deletion: Delete or manipulate system logs and records to cover the tracks of the attacker’s activities and evade detection.
EVOLUTION TIMELINE
C&C PANEL VIEW
EXTERNAL THREAT LANDSCAPE MANAGEMENT (ETLM) OVERVIEW:
Impact Assessment
WISE REMOTE “Advanced” Stealer poses a serious threat through data compromise, system exploitation, propagation of malicious payloads, and botnet formation. The malware has the capability to exfiltrate sensitive information, leading to identity theft, financial losses, and reputational damage. It can gain unauthorized access to compromised systems, enabling unauthorized modifications and potential disruption of critical operations. The builder tool allows for the easy propagation of malicious payloads, including ransomware, causing significant disruption and financial harm. Additionally, compromised systems can be transformed into bots, forming a botnet that can conduct large-scale Distributed Denial-of-Service (DDoS) attacks, resulting in service outages and financial impact.
Victimology
WISE REMOTE Advanced Stealer poses a threat to individuals, enterprises, especially financial institutions, and critical infrastructure. Individuals using Windows versions 8, 10, and 11 are at risk of data compromise and financial losses if they store sensitive information on their devices. Enterprises with limited cybersecurity resources face the potential for infiltration and data breaches, leading to financial losses, reputational damage, and legal consequences. Financial institutions are particularly vulnerable to this malware, due to its ability to target cryptocurrency wallets and steal financial data, potentially resulting in significant financial and reputational damage. While not the primary target, WISE REMOTE Advanced Stealer could also impact critical infrastructure systems, leading to disruptions in essential services such as energy, transportation, and communication networks, if successfully deployed.
CONCLUSION
Our research on the WISE REMOTE Stealer malware highlights its advanced capabilities and the significant cybersecurity risks it poses. This malware, coded in Go programming language, employs sophisticated techniques to evade antivirus detection, making it difficult to detect and mitigate. It primarily targets Windows operating systems, especially versions 8, 10, and 11. The malware ensures secure communication with its encrypted connection between the Command-and-Control server and infected clients. The C2 panel, with its user-friendly interface, allows for easy monitoring of a large number of victims. Additionally, malware provides the ability to download and execute payloads, opening the door for further malicious activities, including ransomware deployment. The threat actor can also control compromised systems through shell commands, potentially enabling activities like Distributed Denial-of-Service attacks. Given the advanced nature of the WISE REMOTE Stealer malware, it is crucial for organizations to implement robust cybersecurity measures to protect their systems and data from this significant threat.
MITIGATION STRATEGIES / RECOMMENDATIONS
To effectively manage the impact of WISE REMOTE Stealer and similar threats, organizations should focus on proactive measures:
- Implement Robust Endpoint Protection: Deploy and maintain advanced antivirus and endpoint protection solutions that can detect and block the WISE REMOTE Stealer malware. Regularly update these security tools with the latest threat intelligence to enhance detection capabilities.
- Conduct Regular Security Awareness Training: Educate individuals and employees about the risks associated with malware attacks, including phishing emails, suspicious downloads, and social engineering tactics. Promote safe browsing habits, strong password practices, and the importance of reporting any suspicious activities.
- Keep Systems and Software Up-to-Date: Apply timely security patches and updates to operating systems, applications, and software. Regularly check for patches from trusted sources and implement a patch management process to ensure all systems are up-to-date and protected against known vulnerabilities.
- Implement Network Segmentation: Use network segmentation techniques to isolate critical systems and sensitive data from less secure areas. This helps limit the potential impact of a WISE REMOTE Stealer infection and prevent lateral movement within the network.
- Maintain Regular Data Backups: Perform regular backups of critical data and store them securely offline or in an isolated environment. This ensures that even if data is compromised or encrypted by malware, it can be restored from backup sources.
- Establish an Incident Response Plan: Develop a comprehensive incident response plan that outlines the steps to be taken in the event of a WISE REMOTE Stealer infection. Define roles and responsibilities, establish communication channels, and conduct regular drills to ensure an efficient and coordinated response.
- Regularly Conduct Vulnerability Assessments and Penetration Testing: Perform periodic vulnerability assessments and penetration testing to identify and address any weaknesses in your systems and network infrastructure. This helps proactively identify and remediate potential entry points for WISE REMOTE Stealer and other malware.
- Engage with Cybersecurity Service Providers: Consider partnering with reputable cybersecurity service providers, who can offer specialized expertise, threat intelligence, and ongoing monitoring to detect and mitigate the risks posed by WISE REMOTE Stealer. These providers can augment your existing cybersecurity capabilities and provide timely response and mitigation support.
By implementing these mitigation strategies and recommendations, individuals, organizations, and infrastructure operators can enhance their resilience against WISE REMOTE Stealer and reduce the potential impact of this sophisticated malware.
APPENDIX I
Indicators of Compromise
| Indicator |
Type |
Remarks |
| 193.32.127.137 |
IP |
Command Control |










