



Recently, researchers noticed various campaigns abusing Google Ads platform to deliver malware to novice users searching for popular applications and cracked versions of legitimate software. Threat actors use cloned websites of legitimate applications to distribute malicious versions of these applications and promote such malicious websites to a wide audience using Google Ad campaigns. Threat actors used similar domain names which resembles the official legitimates sites by using technique known as “typosquatting” and further promote them as Ads abusing Google Ads campaign by using SEO poisoning technique.
CYFIRMA research team has been observing such campaigns closely and in this report, we are going to provide preliminary analysis of a new RAT known as “VagusRAT” and its possible attribution to Iranian Threat actors. The VagusRAT is also delivered to the victims by exploiting Google Ads.
The VagusRAT is the remote access tool to control victim’s machine when compromised. It has various capabilities and is also available as Malware as a Service to other threat actors.
It seems that the VagusRAT is offered by malware authors as MAS (Malware as a service) to other threat actors. Our research team at various instances interacted with VagusRAT malware authors and the authors confirmed that the malware is customisable as per the need of the user. Further, the RAT owners are likely to come up with a better customized version that allows user to incorporate multiple variations using the builder like putting custom file extensions.
We have accessed the video tutorials released by malware authors. The videos are available publicly on “vimeo” platform.
By examining microscopically, the videos, we have identified following inferences:
Two public IPs of the Threat Actors gets exposed as tabs are switched (highlighted in below screenshot).
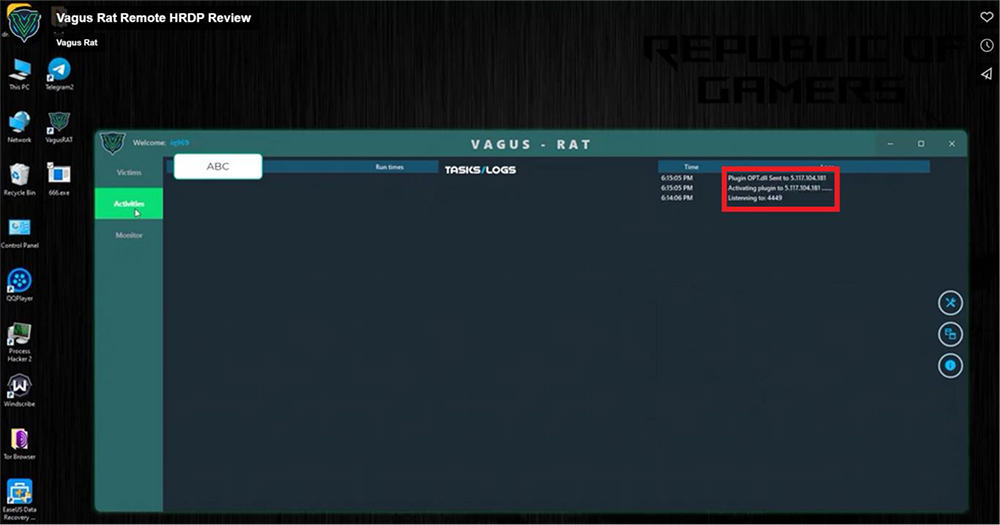
One of the IP originates from Iran thereby leading to an assessment that probably malware author/propagator seems to be from Iran. In another instance, malware author uses a datacentre from Germany and uses a VPN to mask IPs.
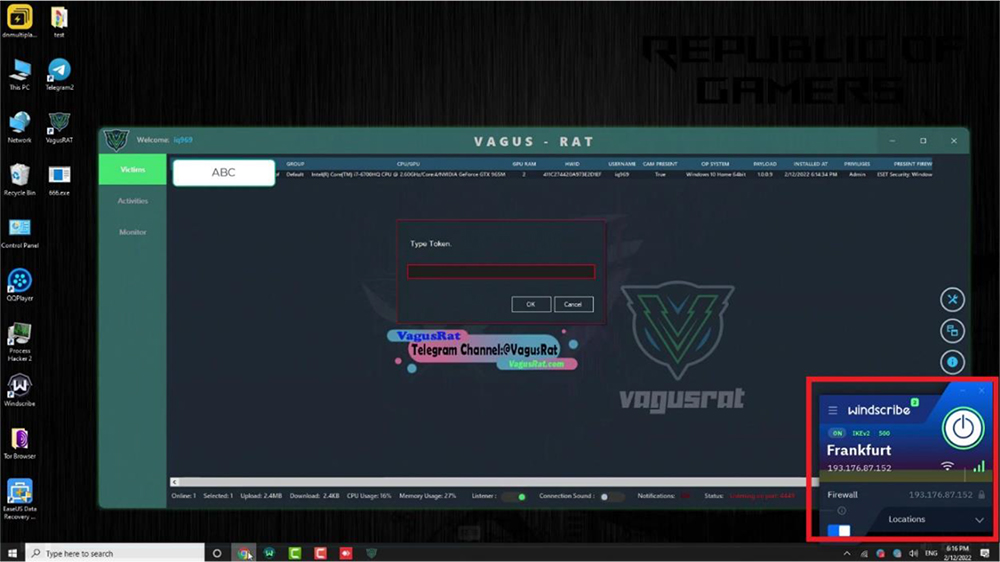
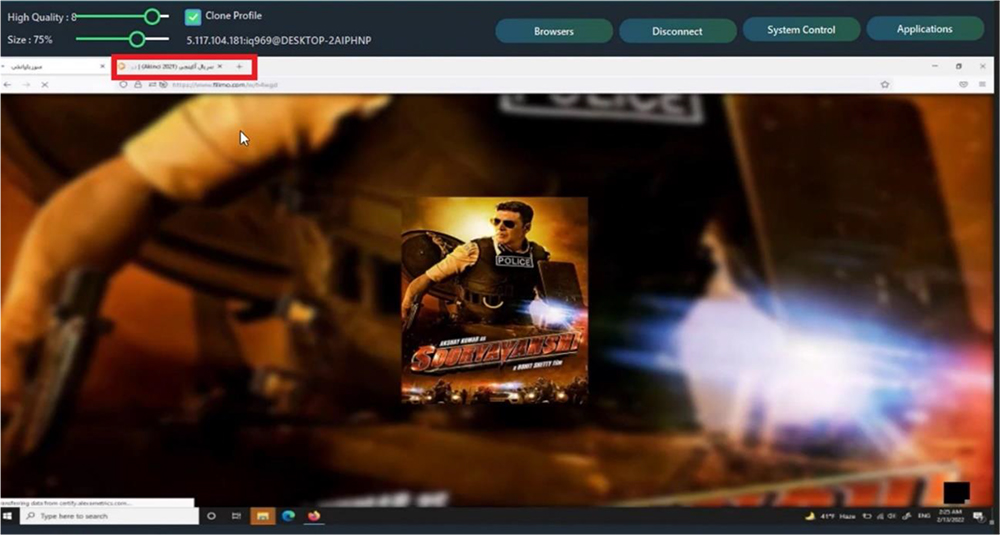
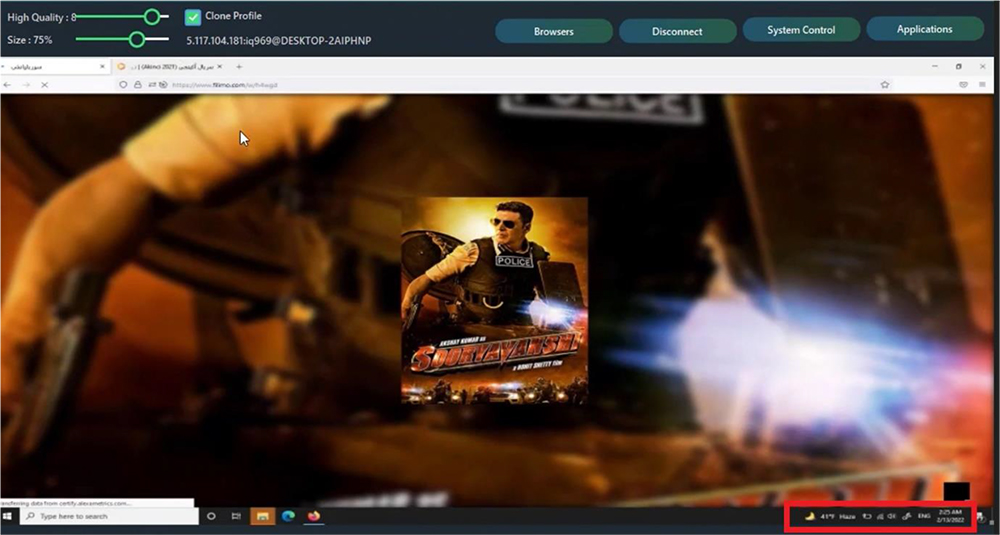
Our research team also noticed few observations during video tutorial when Threat Actor switches tabs to showcase more features of the RAT. During this activity, for a fraction of a second, another tab is visible. Upon taking a closer look, the website title tags are in Persian, which suggests that it is a movie dubbed in Persian. Furthermore, the hostname of the device being used by the attacker to record the demo tutorials, was exposed in the same screenshot, along with the public IP.
The public IP address, the temperature mapped with the time, and the language preferences point towards the direction that the Threat Actors are from Iran.
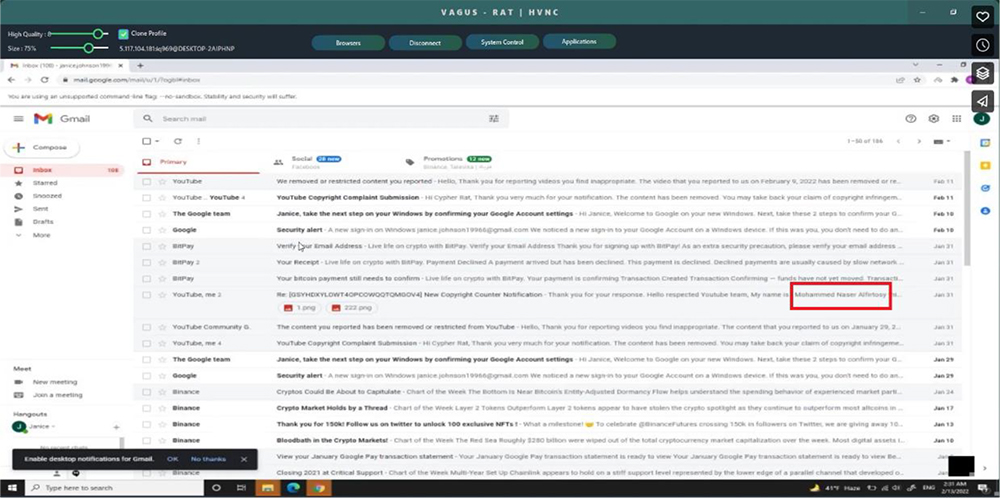
Further, when Threat Actor switches tab for other fractions of second during video tutorial, another tab is visible. It’s the Threat Actor’s Gmail inbox this time, revealing Threat Actor alias email addresses, transaction platform preferences, possibly real name and associated RATs.

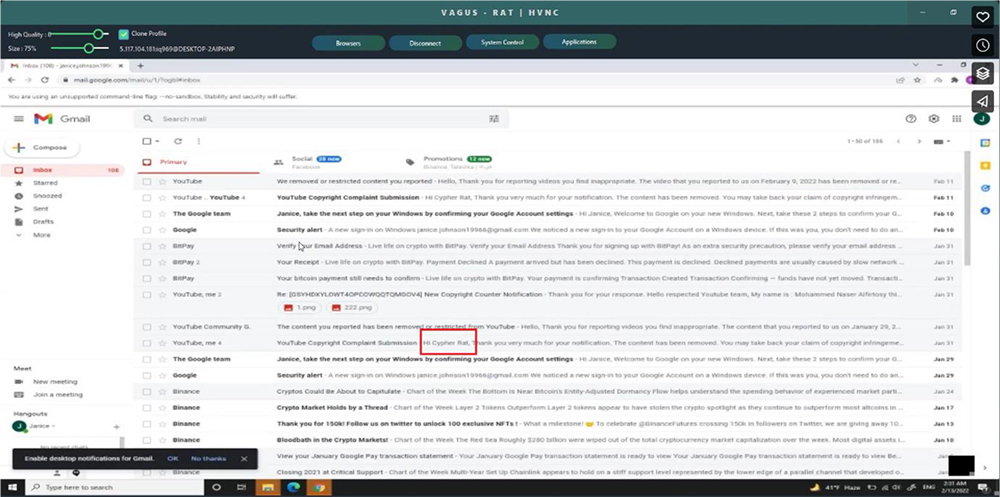
During video tutorial, Threat Actor switches tabs to showcase more features of the RAT. Our researcher noticed email inbox of the threat actor revealing Threat Actor alias email addresses, transaction platform preferences, possible real name and associated RATs. One of the emails mentioned his name as “Mohammed Naser Alfirtosy”. Threat Actor may have exposed the real name behind the aliases as “Mohammed Naser Alfirtosy” while in another email he was addressed as “Cypher RAT” where Cypher RAT is the name used for operating YouTube channel as shown in following screenshots. Cypher RAT is an Android Remote Control tool that allows the user to control and monitor Android phones. Threat Actor seems to be linked with Cypher RAT but we are not able to confirm how they are related or if it’s just use of some popular name. One more Gmail account we identified in the emails is “Janice.jhonson19966@gmail[.]com”.
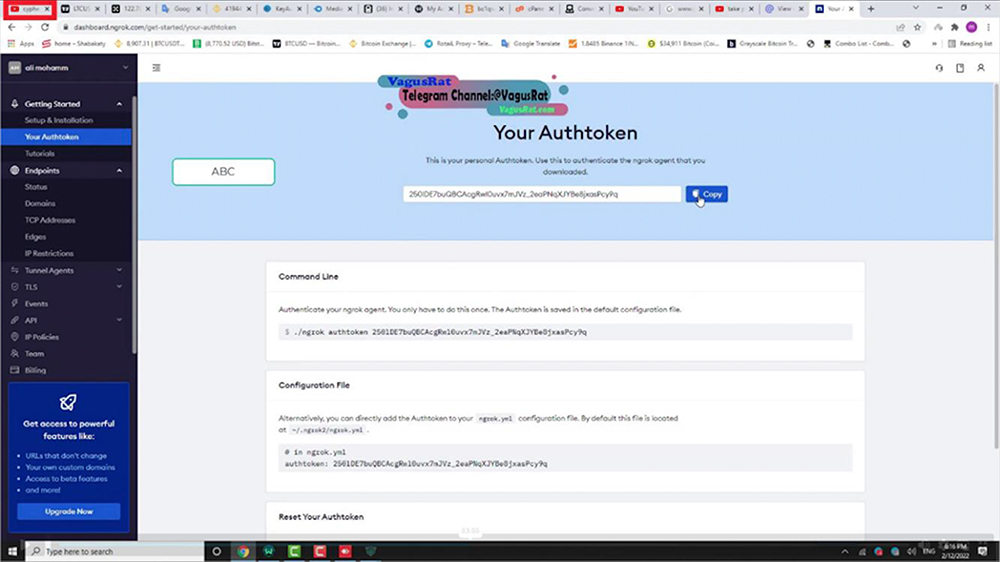
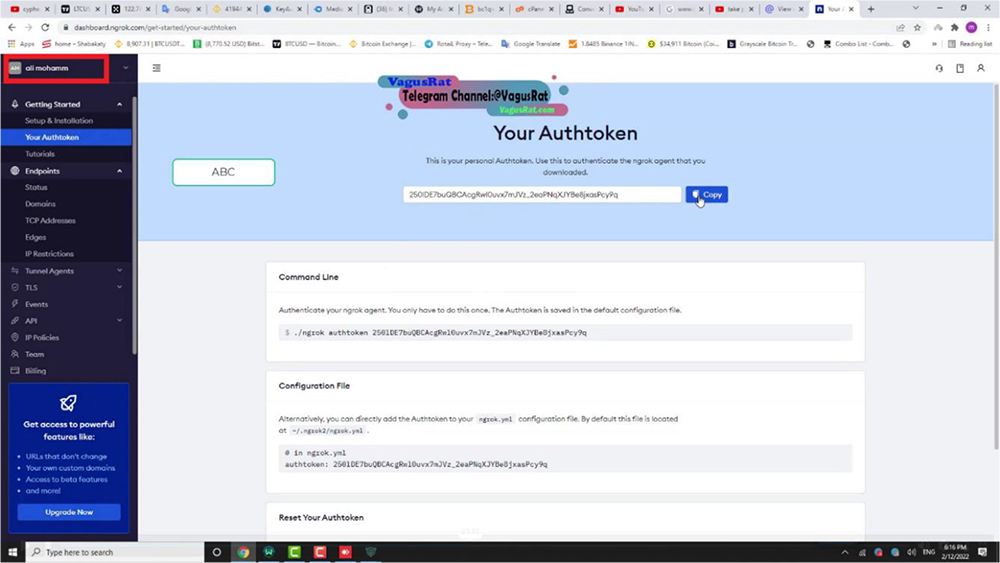
Threat Actor are observed using BitPay and Binance, and also seem interested in getting some kind of content removed from YouTube. Further, from other screenshots it seems that VagusRAT uses ngrok authentication token for authenticating the RAT installed on victim device with the admin console.
Our research team identified a sample from public repository delivered via Google Ad which leads to Fake adobe reader page, delivering a malware which turns out to be VagusRAT.
GOOGLE AD URL:
https[:]//www.googleadservices[.]com/pagead/aclk?sa=L&ai=DChcSEwjy4sagmJ_8AhVJFdQBHY3OAxEYABAD GgJvYQ&ae=2&ohost=www.google[.]com&cid=CAASJuRokbSmQNuTK23Kw7UbgirwiJVLfiVKasNW9fqwpyfMA NvnxVw2&sig=AOD64_2C1NIk9OeXrYlcz91FT042ICksIQ&q&adurl&ved=2ahUKEwi_xrqgmJ_8AhXOlmoFHaFDA pUQ0Qx6BAgHEAE&nis=8&dct=1
The above URL lands to
“https[:]//bdppay[.]com/?gclid=EAIaIQobChMI8uLGoJif_AIVSRXUAR2NzgMREAAYASAAEgLOo_D_BwE” which further redirects the user to “https[:]//acrobatsadobes[.]icu/” as shown below.
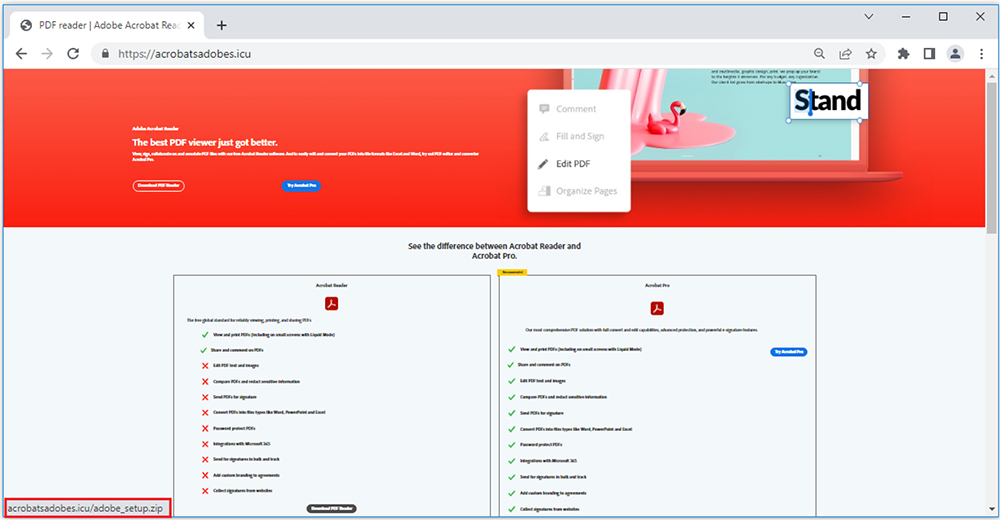
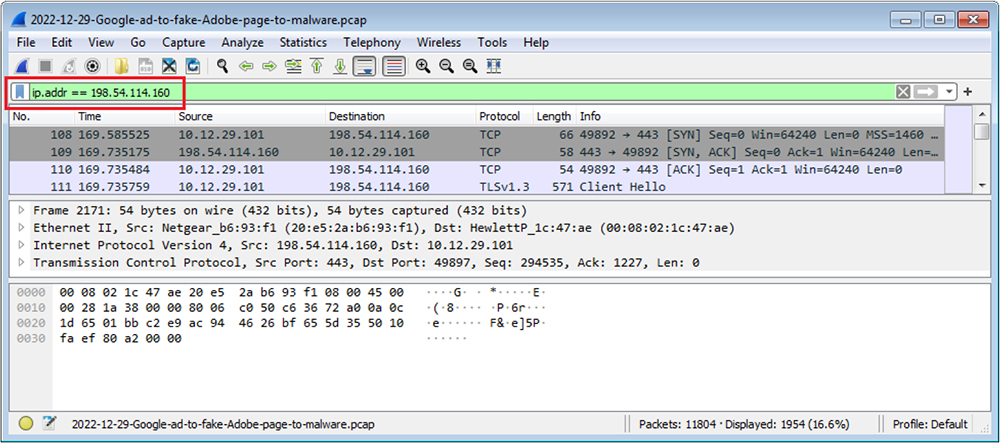
On clicking link to download the adobe, it redirects to “198.54.114[.]160 port 443 – hxxps://bravebrowsers[.]cc/setup_4.21.exe” to download malware with name “setup_4.21.exe” on the machine.
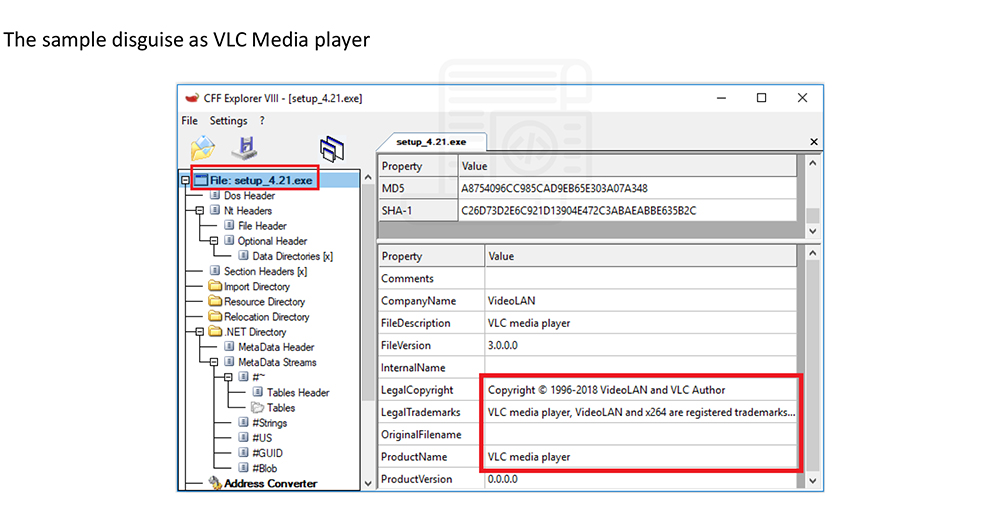
File: setup_4.21.exe
Subsystem: CONSOLE
MD5: a8754096cc985cad9eb65e303a07a348
SHA1: c26d73d2e6c921d13904e472c3abaeabbe635b2c
SHA256: 37082f0b757d6c249b870c29872a9bf8e38e344150735d9b6d2a64364b18b226
File Type: PE32 Executable (GUI) Intel 80386 Mono/.Net assembly, for MS Windows
The sample disguise as VLC Media player
The sample is .NET based and is packed with Confuser packer. Confuser is a free, open-source protector for .NET applications.
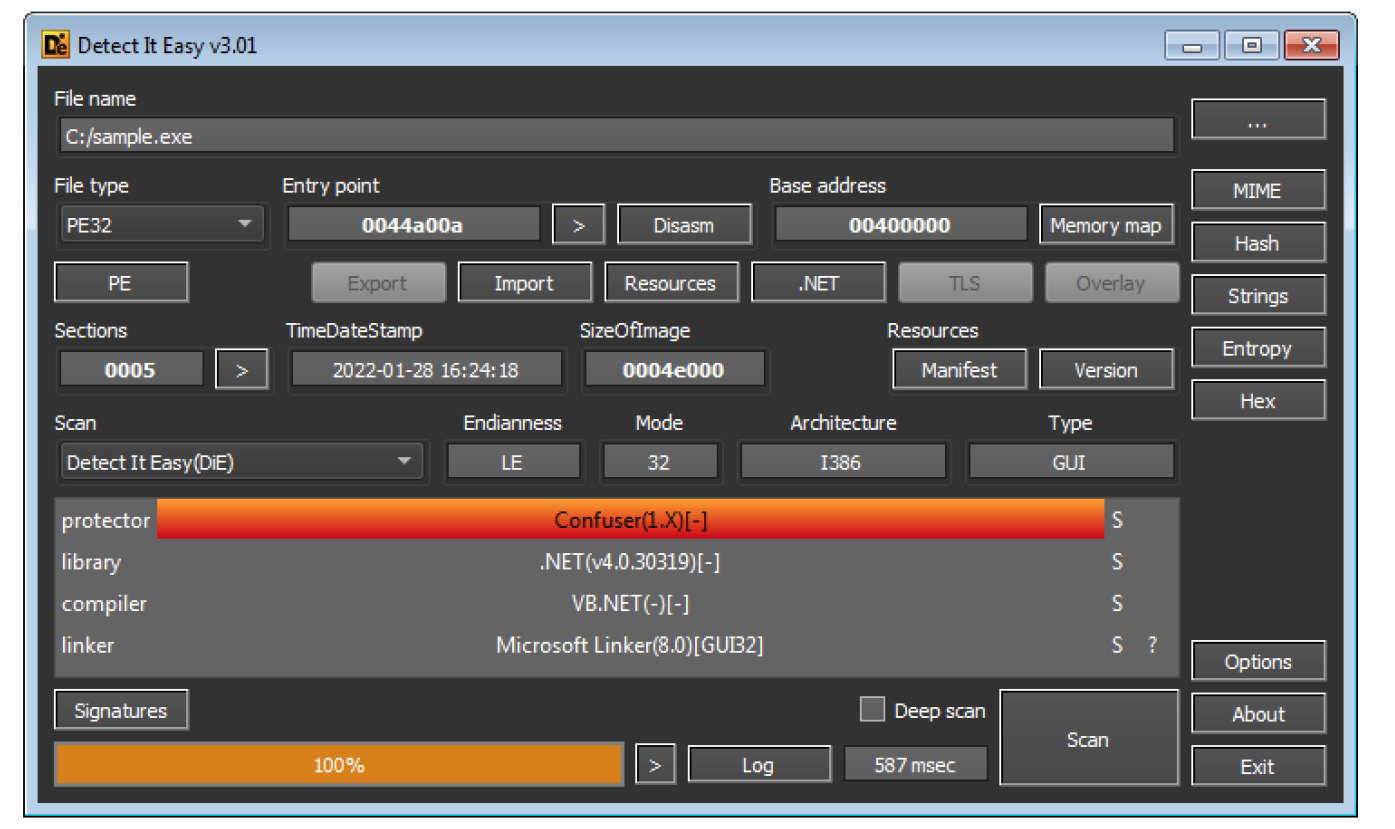
The sample code also mentions Confuser attributes & obfuscator name.
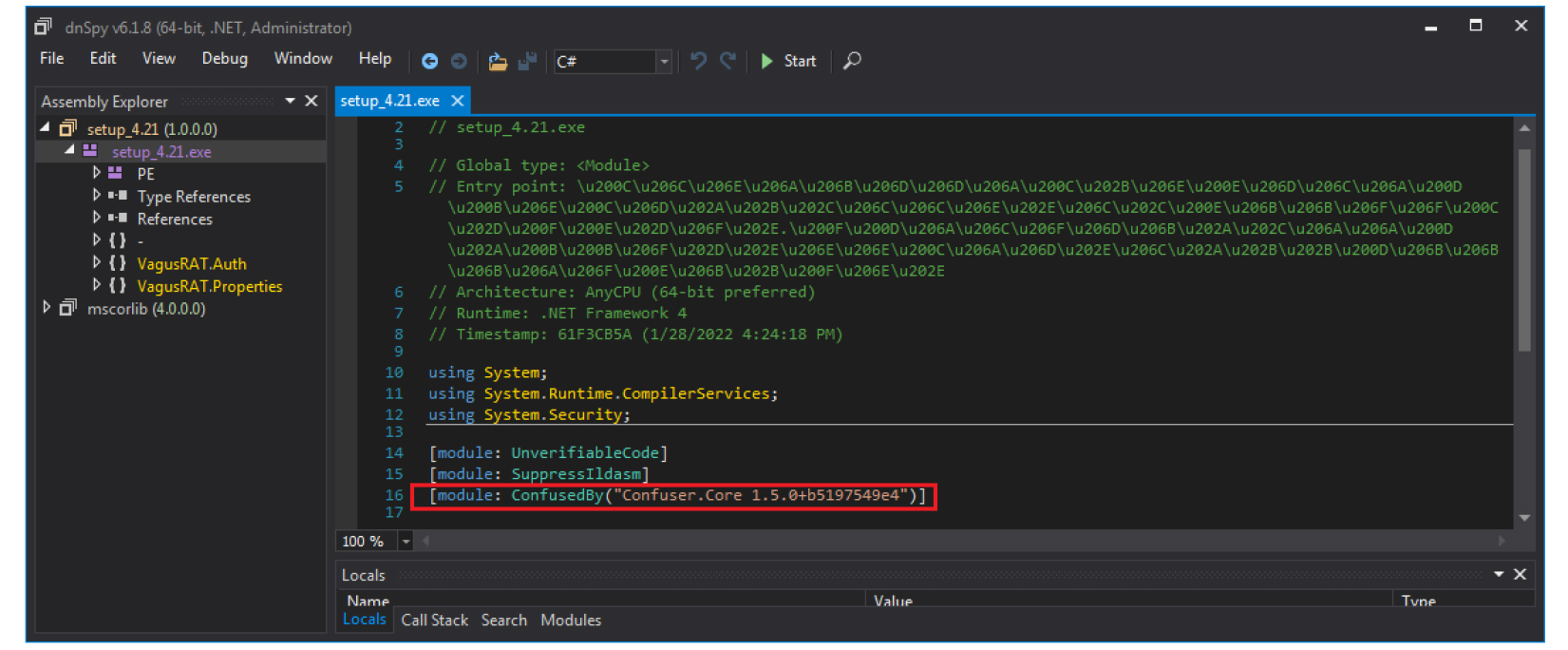
The class names, entry point and code are obfuscated to evade analysis.
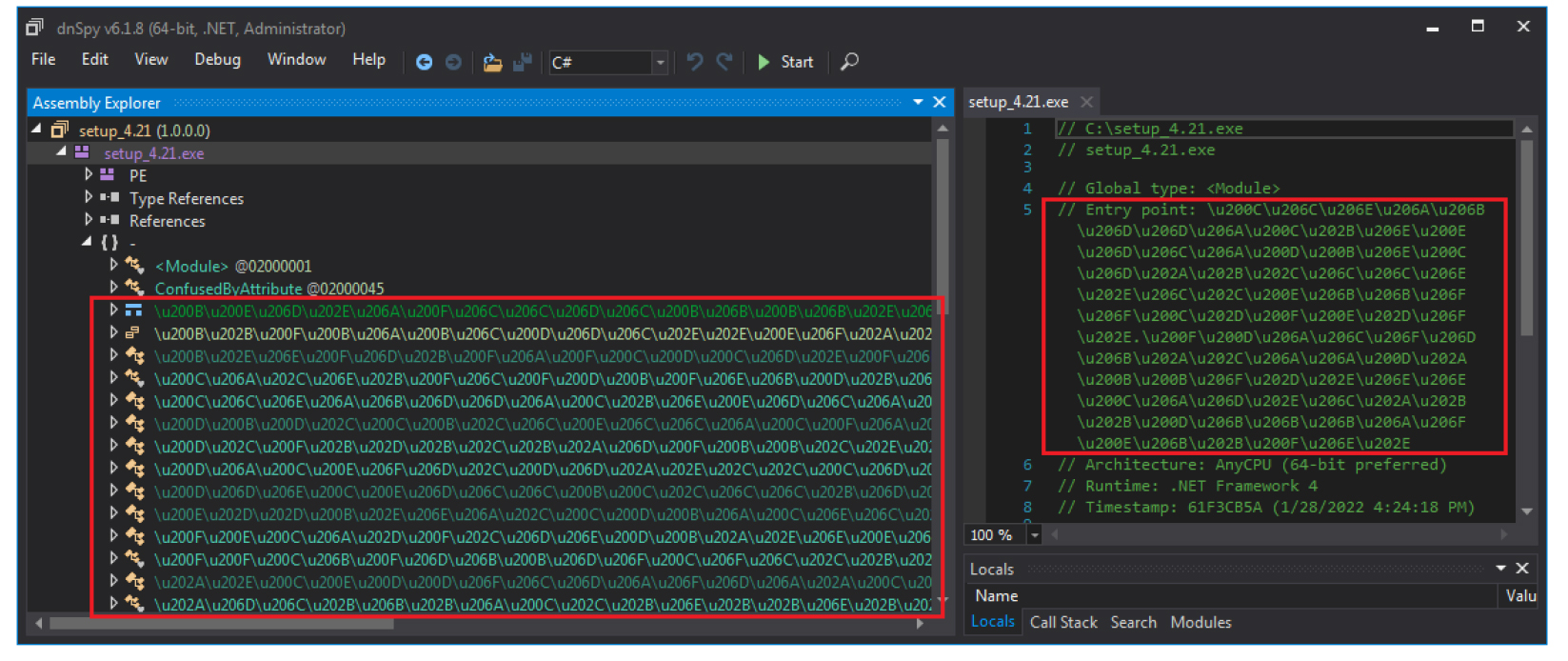
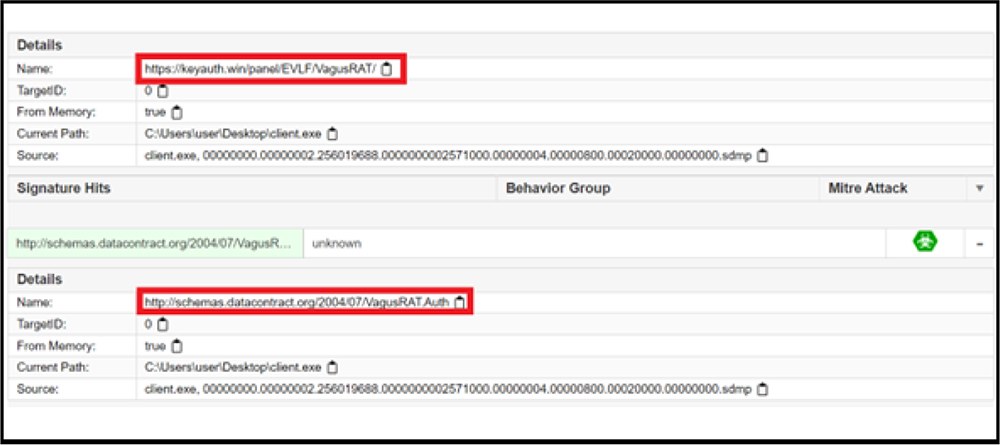
On unpacking the code, we further analysed the same. As shown in below screenshot, two projects with the VagusRAT project names are identified in the setup_4.21.exe sample. Also, projects have VagusRAT.Auth & VagusRAT.Properties namespaces.
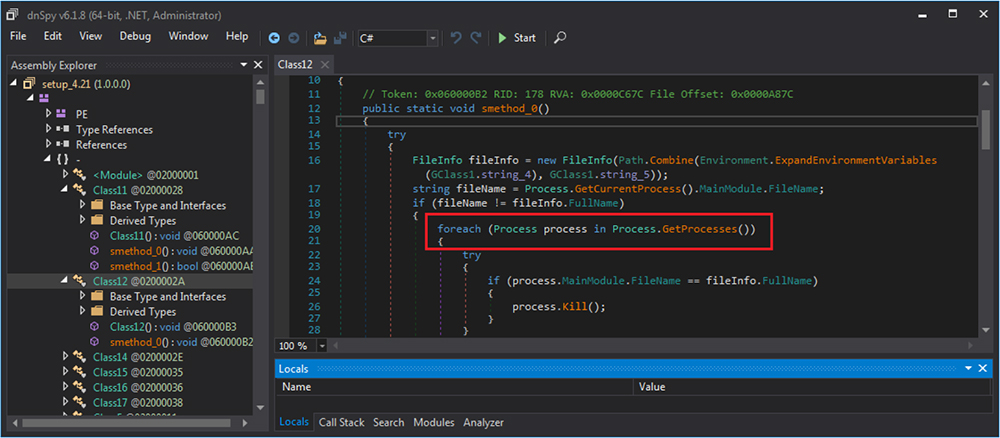
It enumerates the processes and also creating new directories/folder on the system.
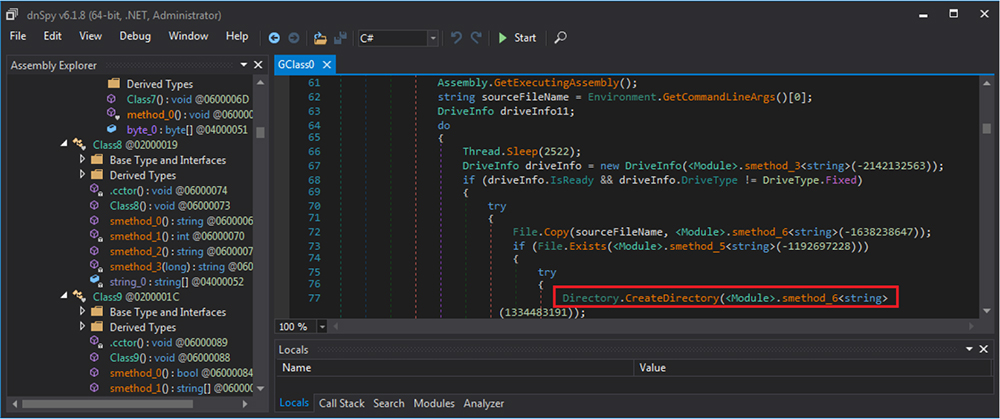
The binary has the capability to access and modify registry. On execution it modifies various registry entries including “HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\Run” for persistence.
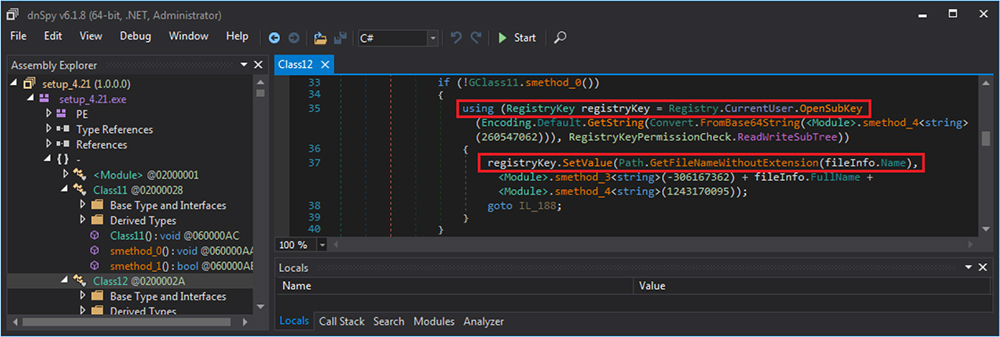
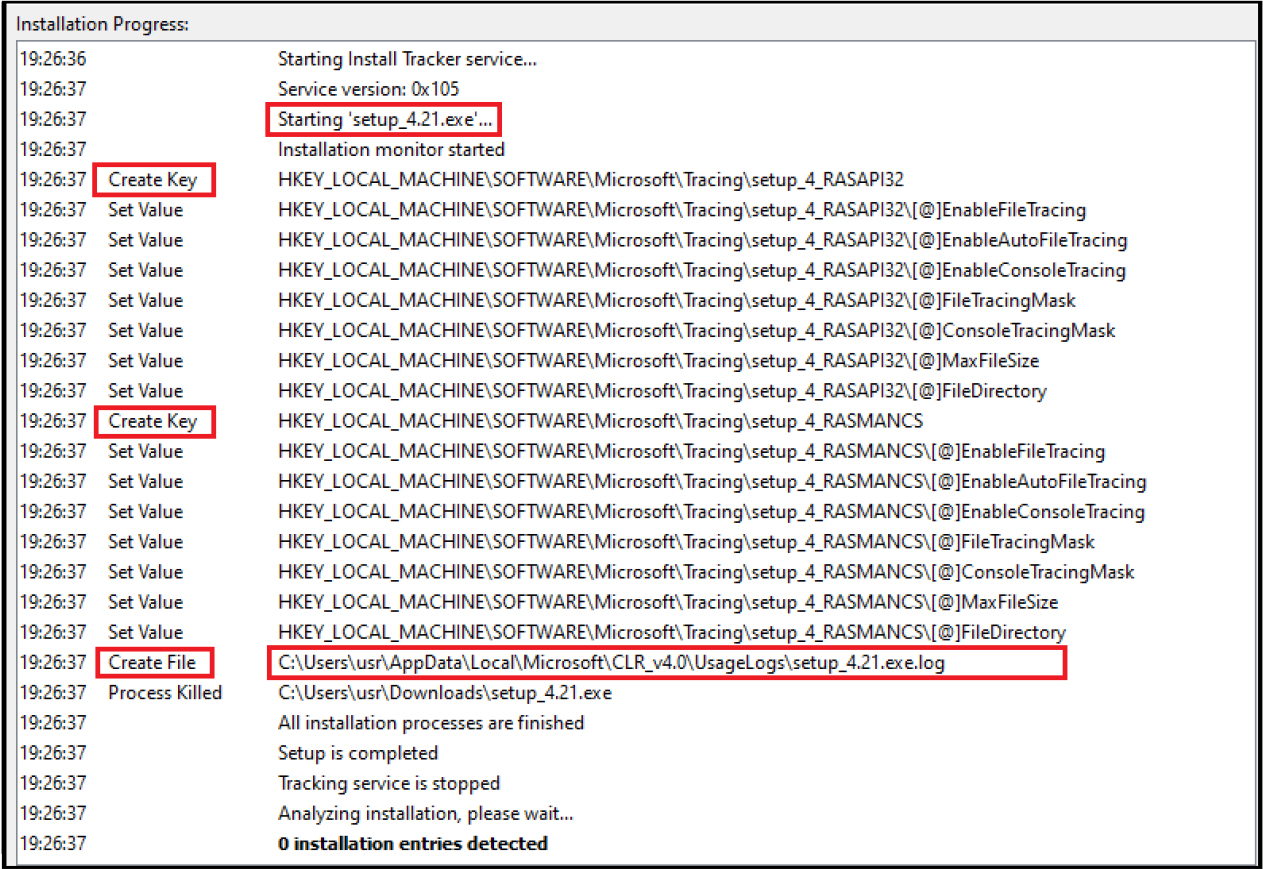
Following registries entries were also accessed. The malware also drops the file with.log extension at path: “C:\Users\usr\AppData\Local\Microsoft\CLR_v4.0\Usage\setup_4.21.exe.log”.
When we click on the fake adobe website “https[:]//acrobatsadobes[.]icu/” to download adobe reader, it redirects to “198.54.114[.]160 port 443 – hxxps://bravebrowsers[.]cc/setup_4.21.exe” to download malware with name “setup_4.21.exe” on the machine.
CYFIRMA researchers also detected a sample (MD5: 7ce22135f9a3eeaf1653101bbfe68272) in the wild that was active in March 2022. This is just a month later from when VagusRAT started their telegram channel in Feb 2022.
The VagusRAT authors started their telegram channel in Feb 2022.
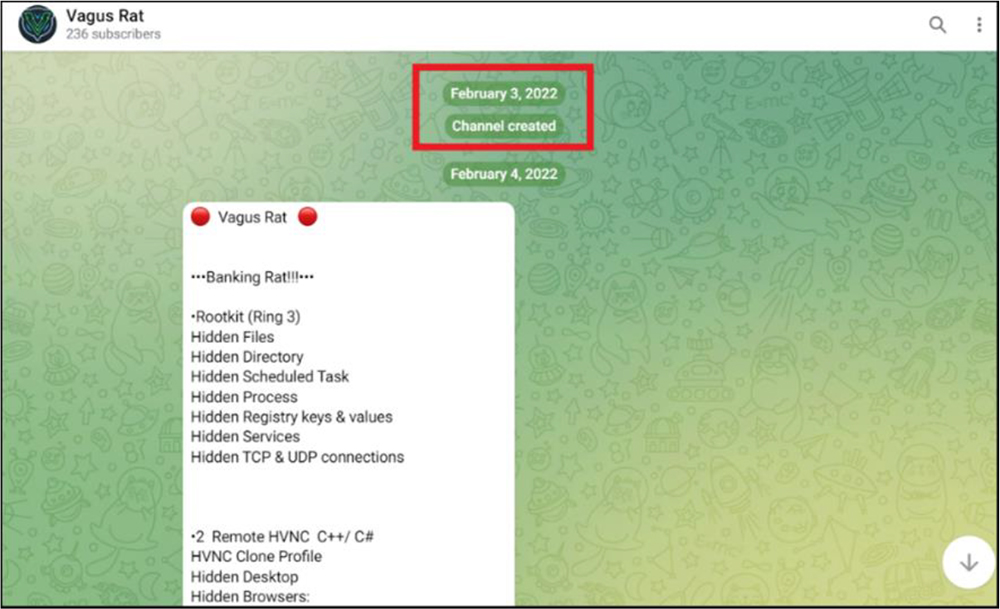
Sample (MD5: 7ce22135f9a3eeaf1653101bbfe68272) active in March 2022.
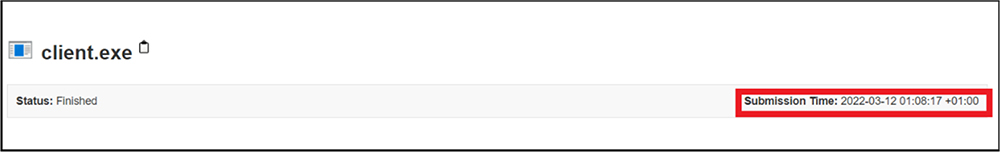
Hash value comparison of this sample with threat intelligence feeds flags the sample as other RAT like AsyncRAT, Qasar RAT and Agent Tesla.
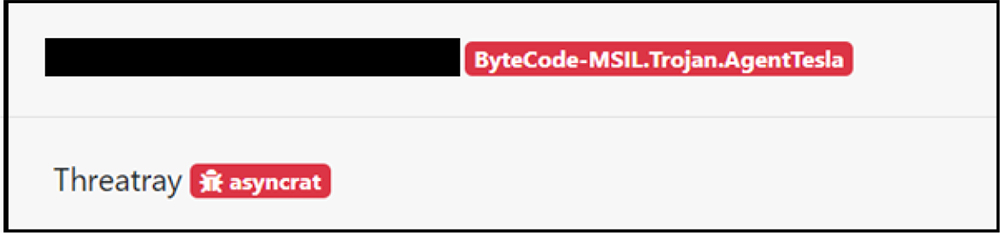
Binary on execution, communicates to URLs with VagusRAT references
Further, it drops a file with .log extension after execution. The same behaviour noticed during analysis of the original sample (MD5: a8754096cc985cad9eb65e303a07a348) delivered recently via Google Ads.
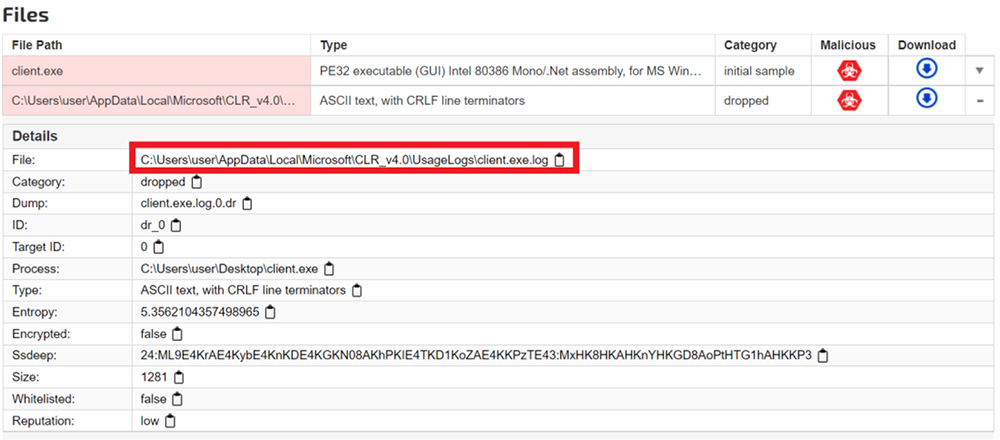
This indicates that the Threat Actors involved with VagusRAT have been operating for almost a year now; and is likely a derive from other popular RATs.
The VagusRAT also has a site “https[:]//www.vagusrat[.]com/” providing information about the RAT and various subscription option for use.
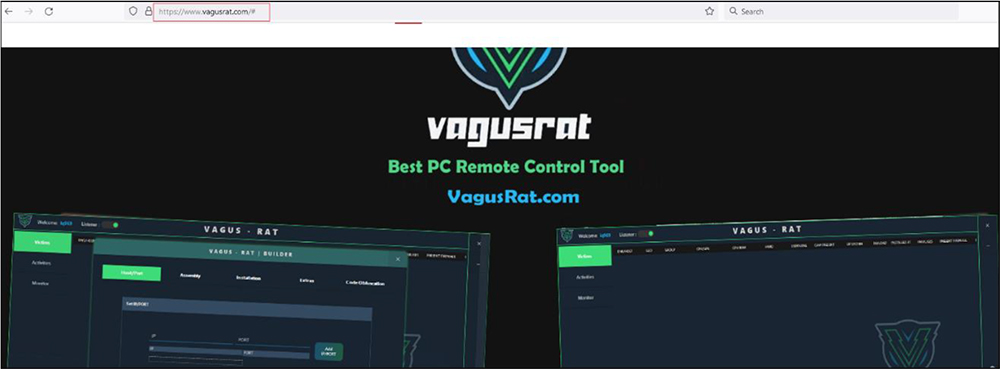
The VagusRAT offers various option to subscribe the RAT with full capabilities.

VagusRAT authors are seen to be providing different subscriptions at discounted prices. VagusRAT is available for lifetime for $800, 6-months subscription available at $500, and 3-months subscription available at $300.
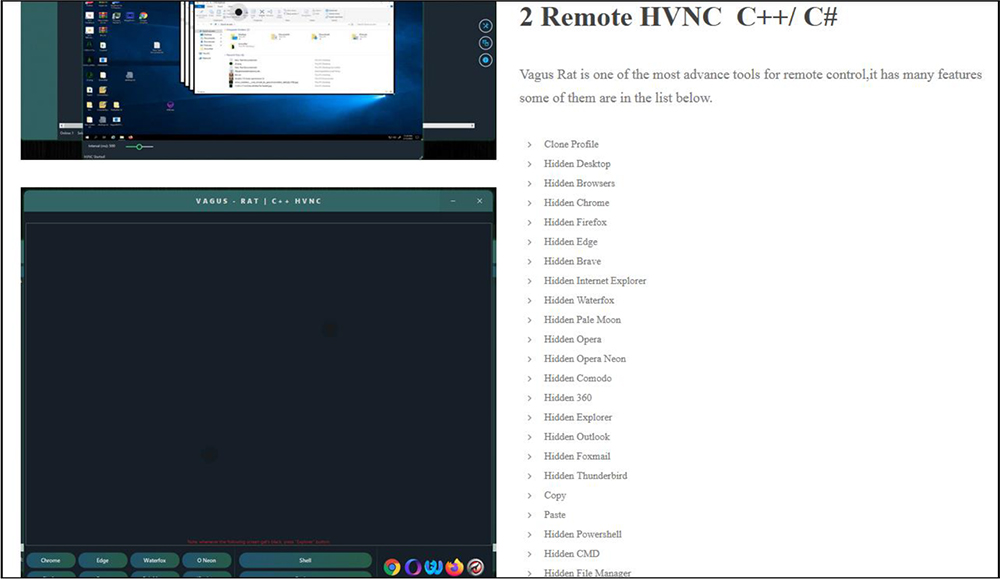
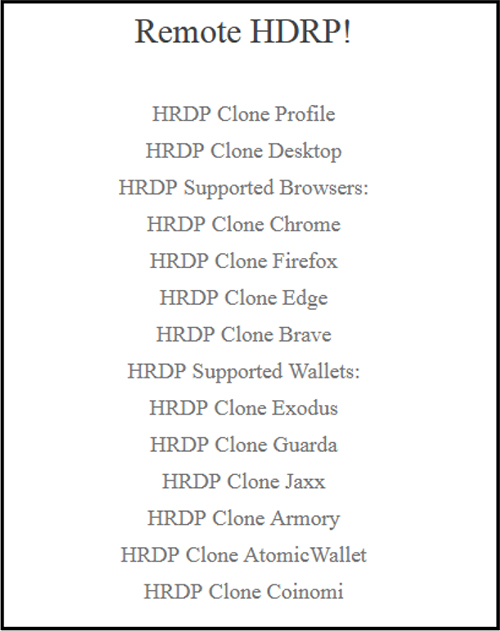
The site mention various features carried by the RAT including HVNC. The Hidden Virtual Network Computing (HVNC) is a tactical means for malware to control a machine without the victim’s knowledge. Hidden VNC is the technique used by threat actors to manage or control victim’s computer system without interacting with the main desktop at all, simply because it creates a new hidden desktop.
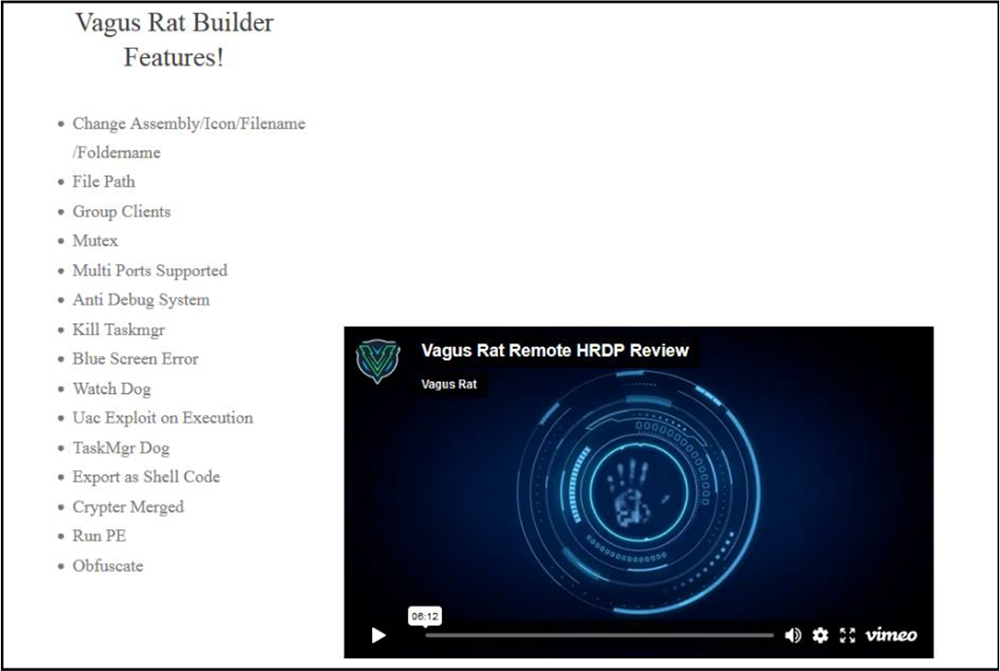
VagusRAT has tremendous capabilities and numerous menu options to control and infect victim’s PC: Remote System, Remote Tasks, Mass Desktop Preview, Remote shell, Remote desktop, Remote camera, Registry Editor, File management, Process management, Network Connections, Remote recording, Process notification, Send file, Inject file, Download and Execute, Execute .reg, Execute .bat, Execute .vbs, Send notification, Chat Room, Open website, Keylog Viewer, Disable Windows Defender, Disable UAC, Password recovery, Bypass Uac, Get computer information, Task on connection, Mutex, Process protection, Install with schtasks, TaskMgrDog, WatchDog.
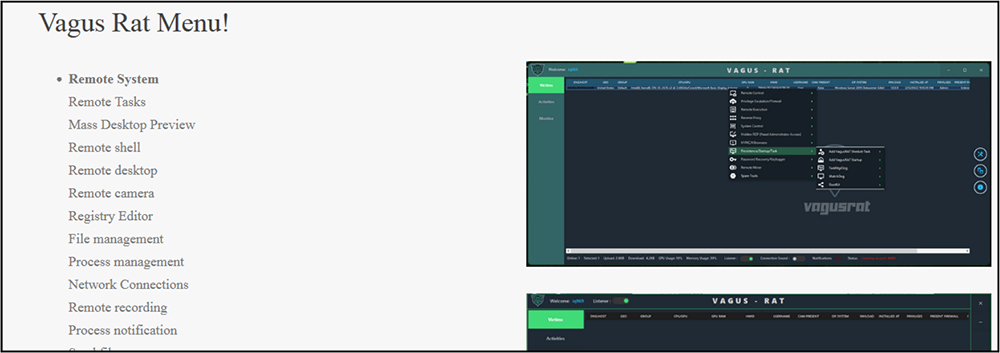
VagusRAT is also providing a builder to build the malware with different options as per the requirement of the user. You can obfuscate the code, implement anti-debugging techniques, export it as shellcode or as EXE file and so on.
VagusRAT also supports HRDP (Hidden Remote Desktop Protocol). HRDP functionality allows the attacker to access the system at the same time as the victim without alerting them.
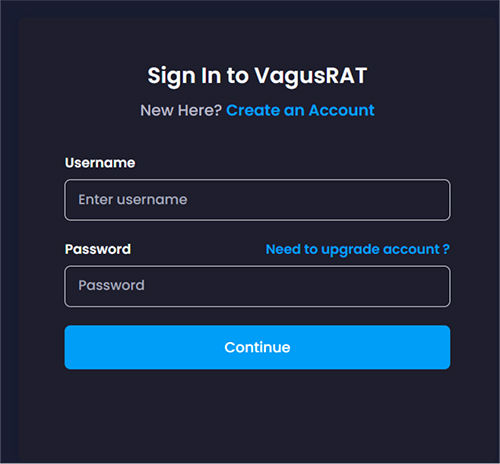
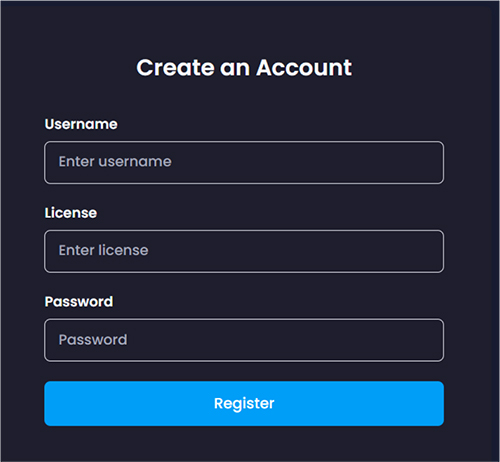
CYFIRMA research team identified the URL “hxxps://keyauth[.]cc/panel/EVLF/VagusRAT” that provides a sign-in and create-account option to user as shown below. This is the control panel used by VagusRAT subscribers to login and perform administration of RATs as and when needed.
We have also identified some telegram bots related to VagusRAT. Other RATs also used telegram as a C2 in past.
The VagusRAT is comparatively a new entrant in the current external threat landscape and has the capability to remotely control the victim machine. It has lots of features to control the compromised machine including HVNC, and HDRP. It also provides builder to build customized malware as per the requirement. VagusRAT is available as Malware as a Service for other threat actors and cyber-criminals on subscription basis. Our research team has attributed the VagusRAT to Iranian threat actors with medium confidence. Malware like VagusRAT are abusing Google Ads via SEO poisoning to promote their malware and distribute it to broader audience. We recommend being cautious regarding such ad campaigns and to block malicious ad campaigns, and at minimum use an ad-blocker on web browsers. Further, users can always scroll down to find the official website of the application/software by searching for.
| Sr.no | Tactics | Type | Remarks |
| 1 | a8754096cc985cad9eb65e303a07a348 | File Hash | MD5 |
| 2 | 7ce22135f9a3eeaf1653101bbfe68272 | File Hash | MD5 |
| 3 | 198.54.114[.]160 | IP | Download Malware |
| Sr.no | Tactics | Technique ID |
| 1 | Resource Development (TA0042) | T1608.006: SEO Poisoning |
| 2 | Execution (TA0002) | T1106: Native API |
| 3 | Defense Evasion (TA0005) | T1027: Obfuscated Files or Information T1027.002: Obfuscated Files or Information: Software Packing |
| 4 | Persistence (TA0003) | T1547.001: Modify Registry |
| 5 | Discovery (TA0007) | T1082: System Information Discovery T1012: Query Registry |
| 6 | Command and Control (TA0011) | T1071: Application Layer Protocol |