


The CYFIRMA research team has discovered a new Malware-as-a-service (MaaS) operator that goes by the moniker EVLF DEV. This threat actor is responsible for the development of CypherRAT and CraxsRAT, which in the last 3 years was purchased by over 100 distinct threat actors on a lifetime license. These RATs are designed to allow an attacker to remotely perform real-time actions and control the victim device’s camera, location, and microphone: in this research report, we will discuss more about the MaaS operator, and the malware being developed by them.
‘Malware-as-a-service’ has been around for some time, however of late, it has become increasingly convenient for cybercriminals to kickstart their activities without having to learn malware development itself. MaaS operators like EVLF, FusionCore, and others are making it easier for threat actors to weaponize their malware arsenal based on specific use cases: we’re delving into the investigation of MaaS distributing an Android RAT, which exhibits more destructiveness than any other Android RAT documented by cybersecurity organizations.
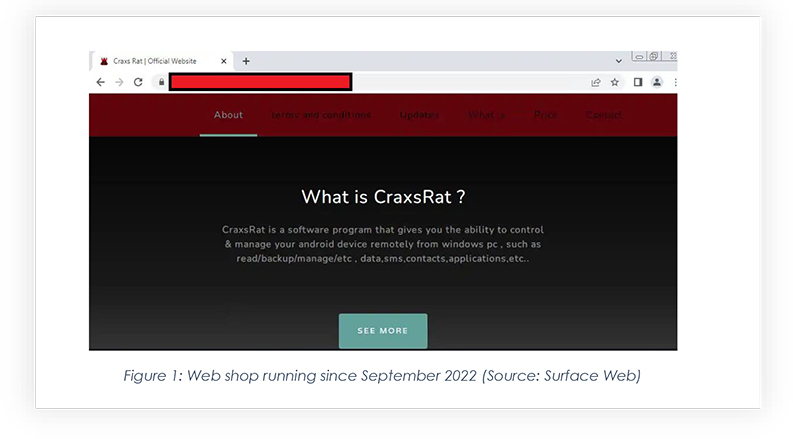
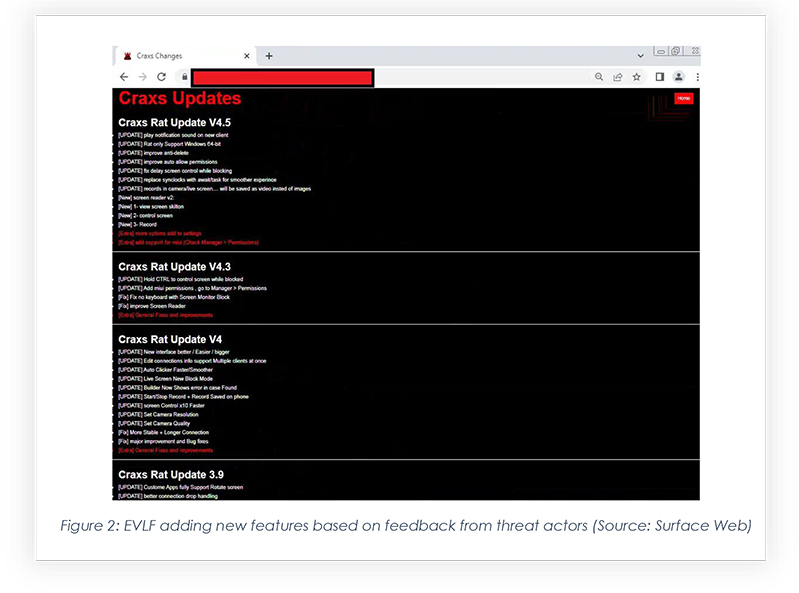
The CYFIRMA research team obtained the CraxsRAT, which is one of the most dangerous purchasable Android RATs currently available to threat actors. During our analysis, we found that the code in the Android package generated from the CraxsRAT builder is highly obfuscated, coming in different types of builds, and providing options to threat actors for planting malicious applications, according to type of attack. There is even a custom option to inject a web view page during payload generation, which opens a malicious website once downloaded. Below is an overview of the panel and a few snippets part of the code review:
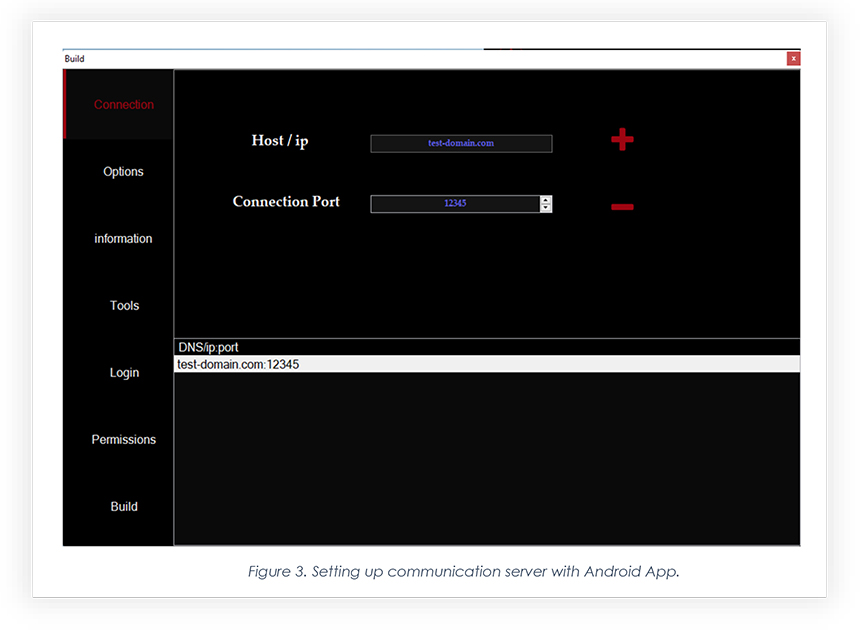
The below screenshot from CraxsRAT’s builder shows setting up the connection server.
Below is the option to customize the payload and let threat actors insert the website for the WebView page, allowing threat actors to choose icons for an app.
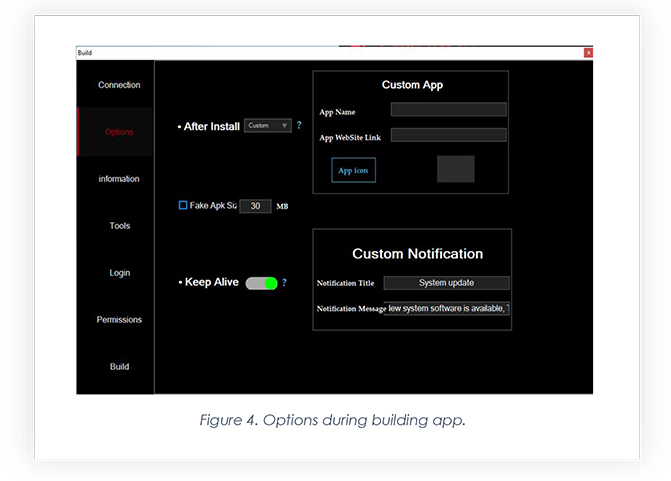
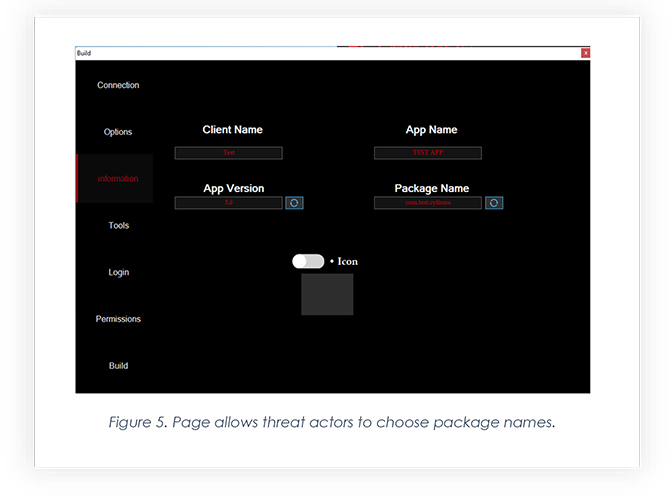
The builder also allows the threat actor to choose package names, including app name.
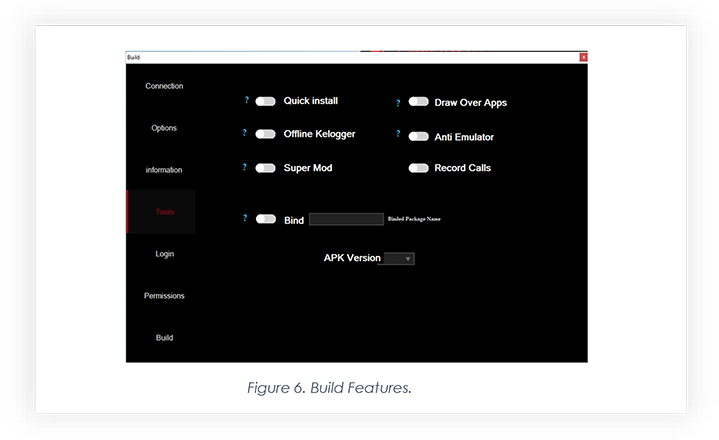
The builder allows threat actors to choose features according to their requirements, making the generated Android package more deadly: the quick install feature generates an app with very limited permissions, which makes the app less suspicious and bypasses detection, however, when the app is installed, the threat actor can send requests to turn on permissions. The “Super Mod” feature rends the app more deadly still, as making it hard for victims to uninstall the app (whenever the victim tries to uninstall, it crashes the page).
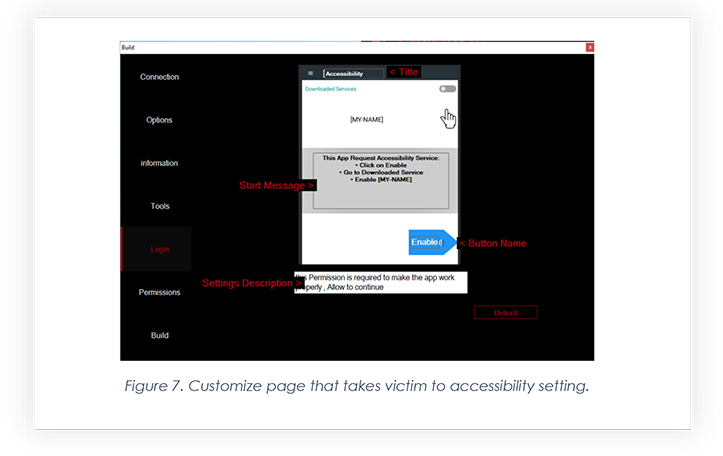
In order to gain access to the device’s screen and keystrokes, the app needs to enable its accessibility in settings. So, the builder allows the threat actor to edit the page which pops up right after the app’s installation is completed.
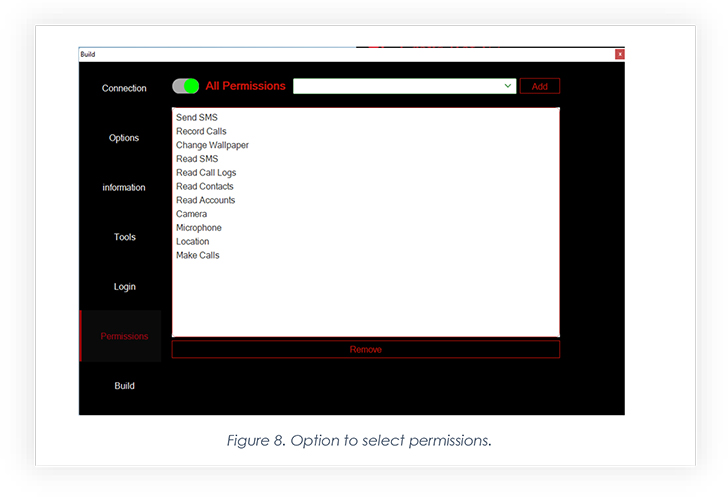
The builder’s final stage gives threat actors options to choose permissions they want the app to gain. Through the quick install feature, threat actors use no permission, as it becomes easy to install it without much user interaction like enabling accessibility. Threat actors then request the required permission to perform malicious activity.
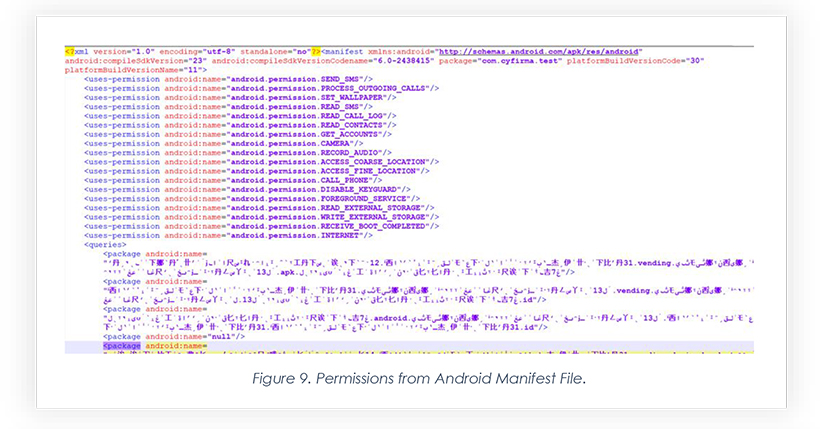
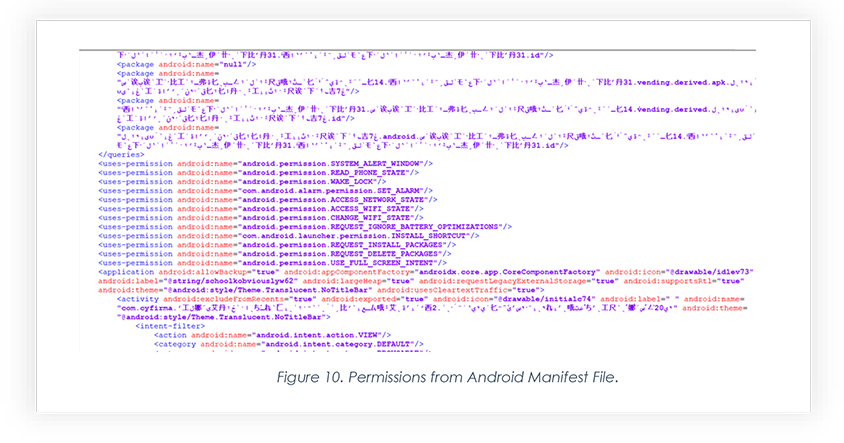
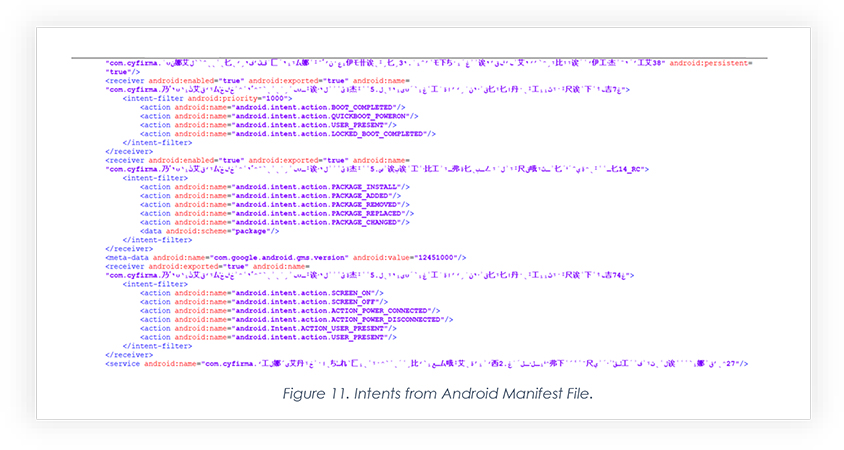
Below are a few screenshots of the Android Manifest file that reveals code to be obfuscated and many permissions exploited to make the app perform malicious activity.
The below table contains dangerous permissions that malicious app uses to perform malicious activity:
| Sr.no | Permissions | Descriptions |
| 1. | ACESS_FINE_LOCATION | Allows the threat actor to fetch precise locations and track the live movement of mobile phones. |
| 2. | READ_CONTACTS | This permission allows TA to read and fetch contacts. |
| 3. | READ_EXTERNAL_STORAGE | This permission allows the threat actor to access the file storage of the mobile. |
| 4. | READ_SMS | This allows the threat actor to read all the SMS of the device. |
| 5. | READ_CALL_LOG | This permission allows the threat actor to read call logs. |
| 6. | READ_CONTACTS | This permission allows the threat actor to read all the saved contacts in the device. |
Below are two screenshots grabbed after decompiling the Android package, generated by Craxs Builder. The name of files is part of obfuscation, including class names.

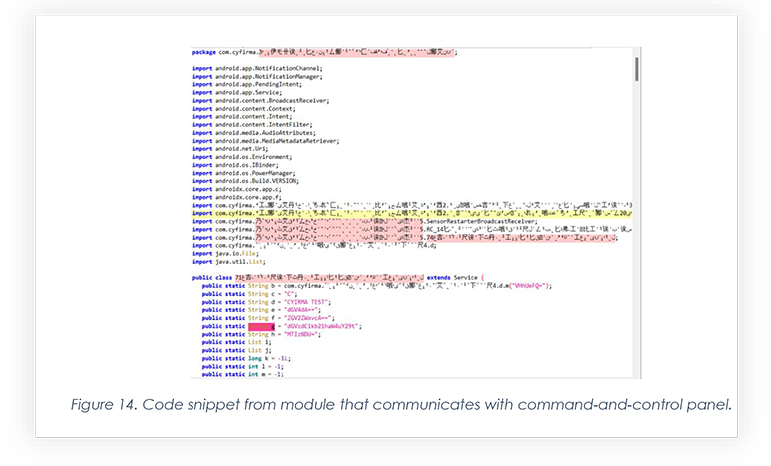
The snippet below of a module has a communication server encoded with a base64 algorithm. Upon decrypting those encodings, we found DNS and Port configured during generating the malicious Android package shown in Figure 3.
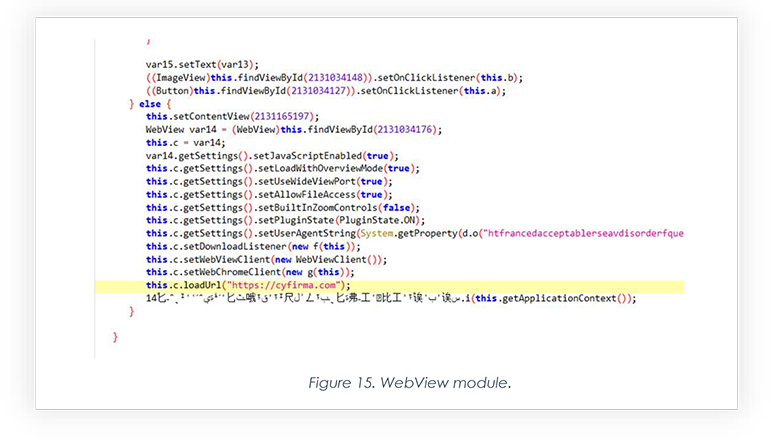
Below is a snippet part of the module which injects website web view client to make victims believe the app is performing normally. We built a sample by injecting the official website Cyfirma.com.
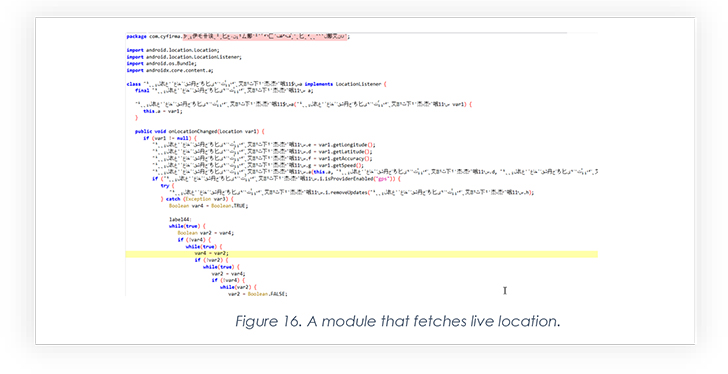
This snippet is part of module that fetches the live location of the compromised device.
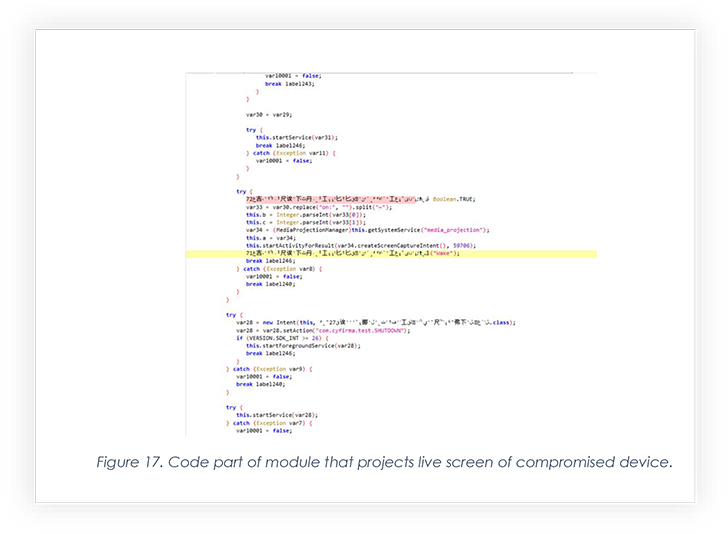
The below code is part of managing screen recording of the victim’s phone, which is arguably the most impactful feature EVLF has embedded in CraxsRAT. Threat actors can easily see the victim’s live screen after successful installation.
EVLF has over 10k channel subscribers, which indicates a high user engagement rate.
CYFIRMA researchers found out that the threat actor has been using a well-known Crypto wallet for at least the last 3 years to withdraw earnings by selling CypherRAT and CraxsRAT.
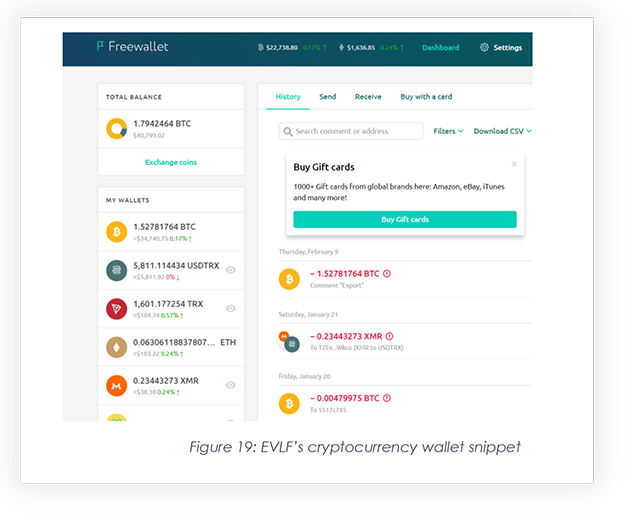
Note that the combined balance of these crypto wallets is around 75,000 USD which was accumulated over 3 years.
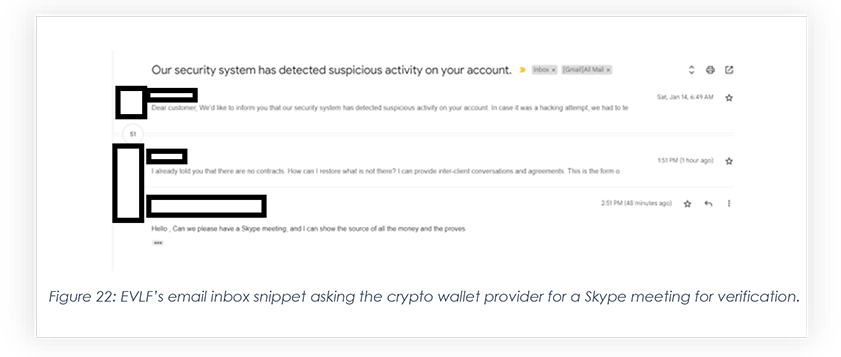
Upon receiving a request for withdrawal of funds, Freewallet reached out to the wallet owner stating that the funds have been frozen until KYC is completed. This compelled the wallet owner to send the verification details to Freewallet so that withdrawal could be made possible.
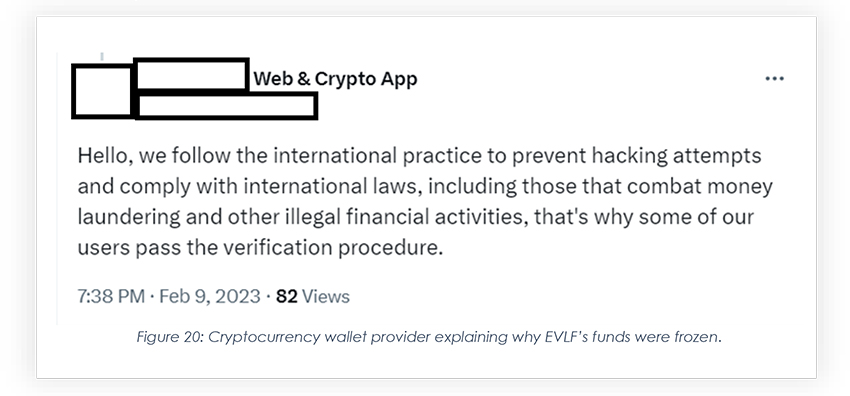
To gain support from the black hat community, after Freewallet denied releasing the frozen crypto, a thread was created by EVLF on one of the crypto discussion forums, where evidence related to KYC submission was shared after masking PII.
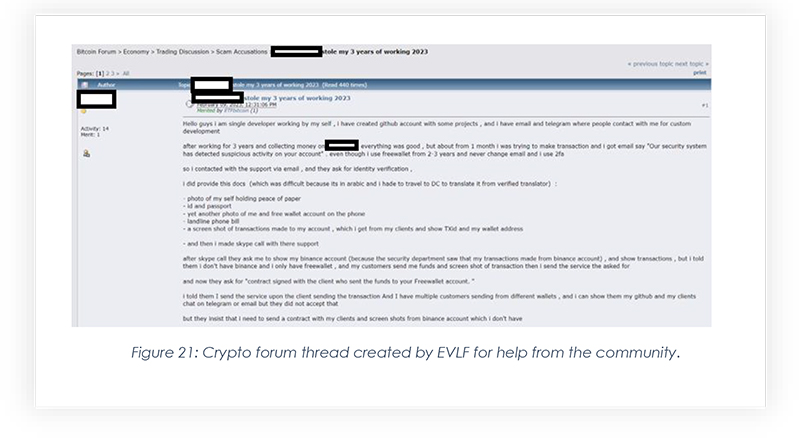
This thread led us to the screenshots posted by the threat actor, showcasing the conversation with the wallet provider.
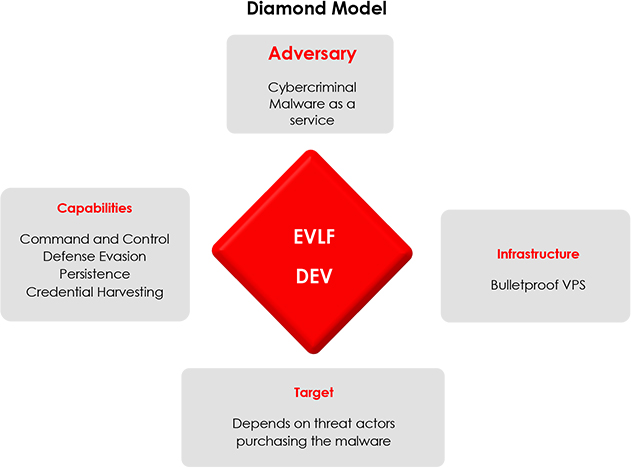
Based on our investigation, it can be ascertained with high confidence that EVLF is being operated by a man from Syria.
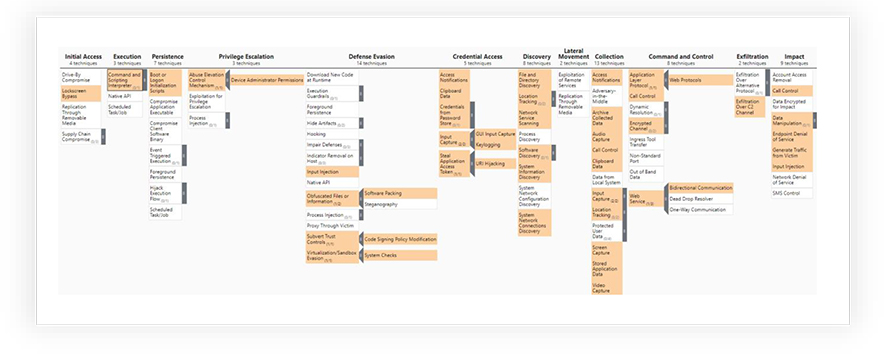
EVLF has been operating from Syria for over 8 years now, extensively working on CraxsRAT. CraxsRAT is one of the most dangerous RATs in the current Android threat landscape, with impactful features such as Google Play protect bypass, live screen view, as well as a shell for command execution. The RAT may be distributed to victims using campaigns such as phishing, third-party app stores, social engineering, in-app advertisements, drive-by downloads, and watering hole attacks. To protect against such threat actor campaigns, users should exercise caution when downloading apps, avoid clicking on suspicious links or attachments, and stick to official app stores for app installations. Regularly updating devices and using reputable security software can also help prevent the spread and installation of malicious apps.
| No. | Indicator | Remarks |
| 1 | 410b70652f923b6b3a22bd5adb9b1ff3 | CraxsRAT Builder |
| 2 | af026551f12a602d95216e74433233595455fabf | CraxsRAT Builder |
| 3 | 4803f54412bcfdb6563d7f5ceb1104c98137143099ec45aa9c4560d742d9c637 | CraxsRAT Builder |