



The CYFIRMA Monthly Ransomware report offers a thorough analysis of ransomware activity in July 2023, covering major attacks, the top ransomware families, geographical distribution, targeted industries, evolution of attacks, new ransomware groups, and evolving trends. Organizations can leverage these insights to enhance their cybersecurity strategies and effectively mitigate ransomware risks.
Welcome to the July 2023 Ransomware Report. We explore the top 5 ransomware groups responsible for the highest number of victims and the industries they targeted. Additionally, we investigate the locations that experienced the most ransomware attacks, and furthermore, we discuss the evolution of ransomware groups, focusing on emerging actors. The report aims to equip organizations with crucial insights to bolster their cybersecurity measures and combat the ransomware threat landscape effectively.
Maximus’ Reveals Data Breach
U.S. government contractor Maximus reported a data breach affecting up to 11 million individuals. The breach exploited a zero-day flaw in the MOVEit file transfer app, targeted by the Cl0p ransomware gang. The stolen data includes personal info like social security numbers and protected health information, amounting to 169GB.
Port of Nagoya Halts Operations
Japan’s largest and busiest port has experienced a ransomware attack affecting its container terminals. The port is responsible for about 10% of Japan’s total trade and is a critical facility, used by major companies like Toyota Motor Corporation.
Japanese media are linking the Nagoya port attack to LockBit ransomware and Russian hackers.
Hawaii Community College Succumbs
Hawaii Community College admitted paying a ransom to ransomware actors to prevent the exposure of approximately 28,000 individuals’ stolen data. The NoEscape ransomware gang, which surfaced recently, had threatened to release 65GB of stolen information if the ransom was not paid.
Beauty giant Estée Lauder Breached
Estée Lauder was listed as a victim on data leak sites by two ransomware actors, ALPHV/BlackCat, and Cl0p. The Cl0p ransomware gang gained access to the company through a vulnerability in the MOVEit Transfer platform. In a disgruntled message, the BlackCat gang taunted the company about their security measures, asserting their continued presence on the network. BlackCat also hinted at the potential impact of the exfiltrated information on customers, company employees, and suppliers.
Yamaha acknowledges Cyberattack
Yamaha, the Japanese manufacturing giant, confirmed a cyberattack in a recent statement. On June 14, Yamaha was listed as a victim by the Black Byte ransomware gang, and in July, it appeared on the leak site of the Akira ransomware group.
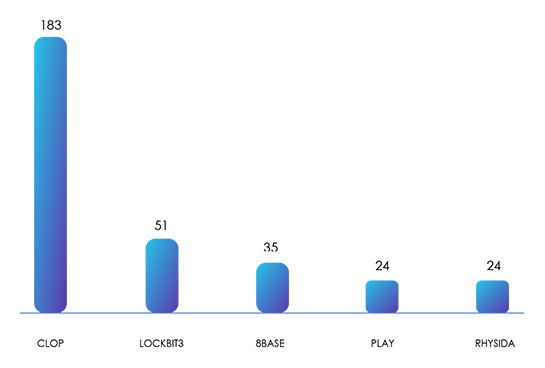
Out of the 30 ransomware groups found active, the 5 with the most victims are Cl0p with 183, LockBit3 with 51, 8Base with 35, Play with 24, and Rhysida (also with 24).
Cl0p, with its exploitation of Zero-Day vulnerabilities in various systems, has a clear lead. Their sophisticated tactics allowed them to target many victims, resulting in a significant impact on organizations and individuals.
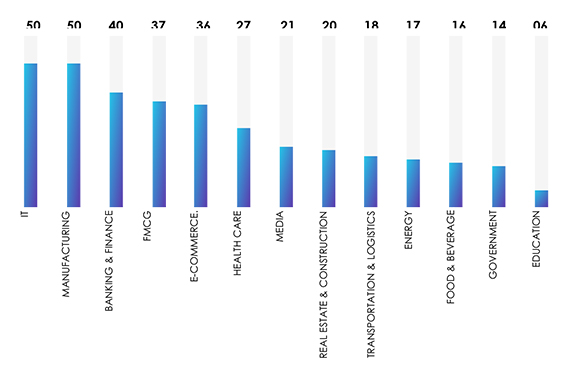
IT and Manufacturing are the most targeted industries, with each experiencing 50 incidents. The Banking and Finance sector closely followed with 40 attacks, while FMCG and E-Commerce reported 37 and 36 incidents, respectively.
These industries attract ransomware operators due to their high-value sensitive information. IT and Manufacturing hold valuable intellectual property and data, making them lucrative targets for cybercriminals seeking financial gains or intellectual property theft, and the Banking and Finance industry hold financially sensitive information, making them a prime target for extortion attempts. FMCG and E-Commerce, with their wide consumer impact and interconnected supply chains, are vulnerable to disruptions, causing significant economic losses and impacting customers’ trust.
Healthcare, Media, and Real Estate industries are also targeted due to their possession of critical patient data, sensitive information, and potential disruptions in services. Transportation, Energy, and Food & Beverage sectors, with their essential roles in daily operations, are at risk of facing business disruptions and supply chain delays.
While Government and Education sectors have fewer incidents, they should not underestimate the threats posed by ransomware attacks. Regardless of the industry, cybersecurity measures need enhancement to safeguard against this escalating menace and protect sensitive data from falling into the wrong hands.
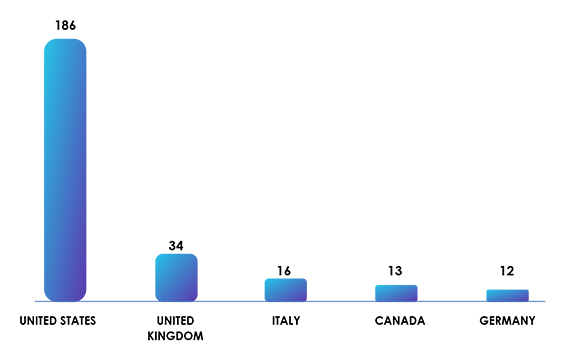
The top five targeted countries were the United States of America, experiencing 186 incidents, followed by the United Kingdom with 34, Italy with 16, Canada with 13, and Germany with 12.
The significant number of attacks on the USA can be attributed to its large economy, extensive technological infrastructure, and the presence of numerous high-value targets. The UK and other European countries were also targeted due to their economic significance and advanced technological landscape. As developed nations, they are likely to have valuable data and resources, making them lucrative targets for ransomware groups seeking maximum impact and financial gains.
Cl0p Ransomware Group Adopts Clear-web Sites
The Cl0p ransomware gang is adopting a tactic used by the ALPHV ransomware gang to increase pressure on their victims by creating freely available Clear-web websites, making it easier to leak stolen data, as they can be indexed by search engines. Security researchers have identified several created by Cl0p, focusing on companies such as PWC, Aon, EY (Ernst & Young), Kirkland, and TD Ameritrade. Unlike ALPHV’s sophisticated searchable database, Cl0p’s sites list links for downloading the data. This tactic allows ransomware groups to double-extort victims and increase the likelihood of ransom payment.
ALPHV/BlackCat Ransomware Unveils New Extortion Strategy
BlackCat has recently incorporated a fresh extortion tactic that introduces a data leak API. This novel API simplifies access to the most up-to-date details of individuals featured on their data leak site, the primary objective being the swift distribution of information regarding the gang’s newly identified victims. This heightened exposure is intended to exert substantial pressure on the victims, compelling them to meet the ransom demands.
Akira Ransomware Gang Persists
Despite the release of a decryptor for the Akira ransomware in June 2023, the group continues to successfully extort victims. In July, 15 new victims were observed. Some July victims were infected with the Linux version of Akira ransomware, based on the list of stolen files, indicating that the Akira gang is persistent and adaptive, capable of targeting different systems and evading detection.
Cactus ransomware:
Researchers have uncovered a new ransomware variant named CACTUS, designed specifically to target large commercial entities. Once infiltrated, the ransomware encrypts files, appending the .cts1 extension, with the number varying for each victim. The name “CACTUS” is derived from the ransom note’s filename, cAcTuS.readme.txt. The threat actors employ an array of tactics, techniques, and procedures (TTPs), utilizing custom scripts and tools like Chisel, Rclone, TotalExec, and Scheduled Tasks to disable security software. Initial access to target systems is achieved through exploiting VPN appliances.
After being initially discovered in April, the activity of these ransomware strains reached its peak in July 2023. The launch of the leak site, which currently lists 18 known victims, also took place in July.
Cyclops:
Researchers have recently discovered a change in the modus operandi of an emerging Ransomware-as-a-Service (RaaS) provider. Along with offering traditional ransomware services, ransomware operators have introduced a separate binary, explicitly designed for data theft. They actively advertise their services on various forums, specifically requesting a share of the profits made by those who use their malware for malicious activities. To simplify the distribution process, the RaaS operators provide a dedicated panel, facilitating the easy dissemination of their ransomware on all three major operating systems. The group declared Version 2 and renamed it as ‘Knight’, along with that, they announced the shutdown of the old panel. Ransomware activities escalated in July, with V2 declaration in the same month.
SophosEncrypt:
SophosEncrypt, a new ransomware, operates as a RaaS model and shares similarities with traditional variants. Written in Rust, it uses ‘C:\Users\Dubinin\’ path for crates. Researchers discovered one sample with advanced capabilities, acting as a RAT, not just encrypting files. It includes keystroke logging, system profiling, and language-based evasion. Another sample exhibits fewer non-ransomware functions. Both samples contain a hardcoded IP address linked to Cobalt Strike and crypto mining attacks on internet-facing computers for over a year. This ransomware demonstrates a blend of traditional and sophisticated features, making it a unique and concerning threat.
Once the encryption process is completed, each encrypted file adopts a new format, containing the original filename along with the token, email, and the ‘Sophos’ extension.
At the time of the report publishing no onion site was found for this ransomware.
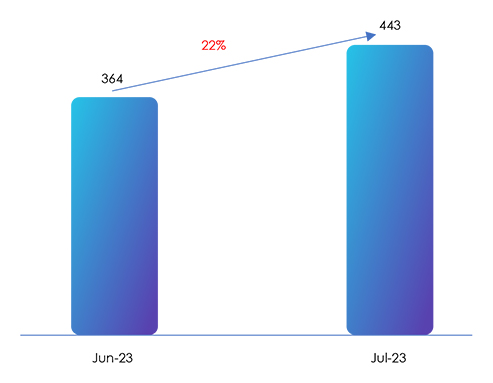
The increase in total confirmed victim count in July highlights the escalating threat of ransomware attacks.
Impact Assessment:
Ransomware poses a serious threat to both organizations and individuals in the external threat landscape, causing extensive damage by encrypting data and demanding ransom payments. The consequences are severe, including financial losses, data recovery expenses, and business disruptions that lead to downtime and reduced productivity. Additionally, ransomware attacks can lead to data breaches, exposing sensitive information and customer data, resulting in regulatory compliance challenges and legal issues. The impact on reputation can be significant, with organizations facing public scrutiny, loss of customer trust, and reduced market confidence. All must stay vigilant and implement robust cybersecurity measures to combat this growing menace.
Victimology:
Ransomware operators are drawn to companies with valuable data, like personal information, financial records, and intellectual property, making industries like manufacturing, healthcare, finance, and technology top targets. These attackers also focus on countries with strong economies and digital infrastructures, as they are likely to have more assets for ransom demand. Their goal is to exploit vulnerabilities in organizations and countries, encrypting data and insisting on large ransoms for its safe return. The potential for huge profits motivates these cybercriminals to carry out their attacks.
The ransomware landscape in July 2023 witnessed a surge in cyber threats across diverse geographies and industries. The targeting of regions like the USA and Europe underscores the global impact of ransomware attacks, driven by economic significance and advanced technological infrastructure. The variety of industries affected highlights the breadth of cybercriminal motivations, from financial gains to disrupting critical services, and the dominance of Cl0p and other ransomware groups emphasizes the evolving tactics used to exploit vulnerabilities, resulting in significant victim counts. The upward trend in victim numbers reflects the escalating danger posed by these attacks: organizations navigate these challenges, bolstering cybersecurity defenses remains imperative to safeguard data and minimize the escalating risks presented by these persistent threats.