



As per CYFIRMA’s latest research report, thousands of TP-Link routers being used globally, are still vulnerable and could be exploited by multiple threat actor groups and cybercriminals from China, Russia, and Iran. Attackers can collaborate on exploiting TP-Link routers using the Remote Code Execution vulnerability (CVE-2022-30075, CVSS Score: 8.8) and credential leaks that are available for sale in the Russian forums on the dark web.
From an External Threat Landscape Management (ETLM) analogy, the vulnerable TP-Link routers could also be used by threat actor groups and cybercriminals to “launch cyberattacks, expanding the attack surface to the target organization, and geopolitically motivated cyberwarfare for mutual interest.”
TP-Link Technologies Co., Ltd. often shortened to TP-Link, is a global manufacturer of computer networking products based in Hong Kong and Shenzhen, China.
TP-Link routers provide wireless internet access to multiple devices in your home, and organizations. TP-Link has ADSL modem routers and VDSL modem routers.
CYFIRMA researchers have observed, as per the sample analyzed, thousands of TP-Link routers are still being used, which are vulnerable and could be exploited by cybercriminals.
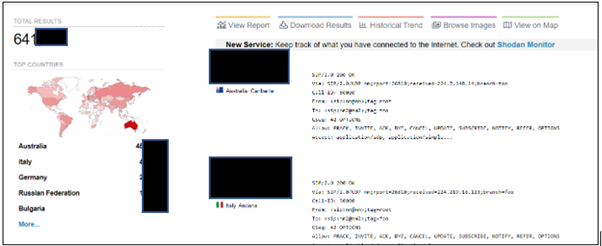
Fig: Global Deployment Landscape (August 2022, OSINT)
In the sample analysed, CYFIRMA researchers have observed multiple instances of hackers looking to collaborate on exploiting TP-Link using the remote code execution vulnerability (CVE-2022-30075) globally.
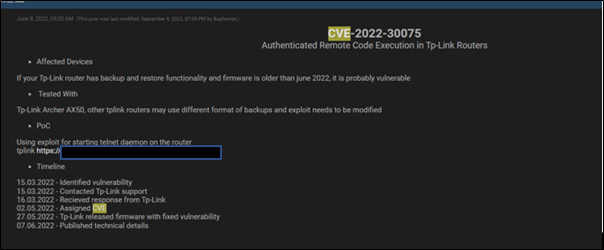
Fig: Screenshots from Underground Forums
In the Russian forums on the dark web, we have observed leaked credentials of TP-Link products available for sale. These can be leveraged by hackers to gain access to the devices and further exploit the path of attack to target an organization’s environment.
About 2 months back, a critical remote code execution vulnerability impacted the TP-Link Router AX50 firmware 210730 and older versions. The import of a malicious backup file via web interface identified as CVE-2022-30075. An attacker could exploit the vulnerability and carry out a remote code execution attack caused by a flaw in the backup and restore functionality.
Details of the vulnerability are as follows:
CVE No: CVE-2022-30075
CVSS Score: 8.8
Exploits: Link (June 2022)
Potential TTPs based on MITRE ATT&CK Framework
| Sr. No | Tactics | Techniques |
| 1 | TA0004: Privilege Escalation | T1068: Exploitation for Privilege Escalation |
Following are the advisories released by various enforcement agencies about the vulnerability and the software:
CYFIRMA researchers have observed in the sample analysed, multiple open ports which seem to be in use for TP-Link routers. These open ports could act as the initial access vectors for cybercriminals.

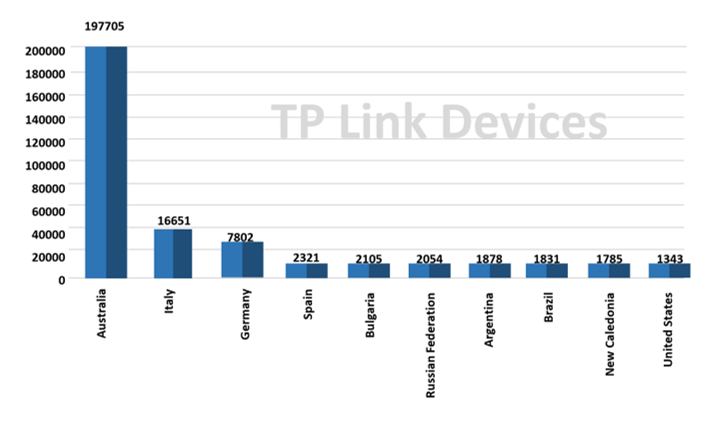
Fig: Top 10 nations using TP-Link Products (as per the sample of 280,000+ devices analysed)
Multiple hacker groups could potentially exploit the vulnerability in these devices, although any specific cybercriminal group exploiting these routers cannot be isolated at this stage.
As in the past 2 years due to the pandemic, organizations have had to support their workforce working from home to support conducting business globally. This has led to TP-Link routers being in demand for the employees to stay connected and carry out their day-to-day operations. However, the vulnerabilities identified in the TP-Link routers have not been patched in many cases, thus leaving several devices exposed.
We have reasons to believe that – Chinese threat groups such as Hafnium and its affiliates, Iranian Groups such as Charming Kitten as well as multiple Russian threat actor groups – Fancy Bear, Cozy Bear, FIN11, and TA505 could potentially exploit vulnerabilities in these devices to fulfill their motives (which may include specific geo-political considerations).
In drawing a parallel with indicators CYFIRMA research team has been observing since August 2021, multiple Russian threat actor groups – Fancy Bear, Cozy Bear, FIN11, and TA505 – were observed launching a cyber-attack campaign known as Привет бойцы aka Hello Fighters, exploiting 1512 of a specific and popular brand of routers. Industries targeted by the campaign included – Chemical & Large Manufacturing, Fertilizer, Automobiles & Components, Electronic Product Equipment, Healthcare, Shipping & Transportation, and Polymer & Fibre. Geographies targeted included – France, Germany, Ukraine, Japan, Indonesia, the UK, India, the USA, Latvia, Taiwan, and many others.
From an External Threat Landscape Management (ETLM) perspective, cybercriminals from countries that may not have a cordial relationship with other nations could use the vulnerable TP-Link routers to launch a cyber-attack on organizations that have a footprint on such vulnerable devices, or possibly for conducting geopolitically motivated cyber warfare.
The interest shown by Chinese and Russian-speaking state-sponsored threat actor groups, coupled with the huge landscape of vulnerable router implementations observed in countries like Australia; easily presents an opportunity for cybercriminals and threat actor groups to exploit such vulnerable routers – thereby expanding their attack footprint of targeting organizations from within and beyond their traditional known set of target nations.
It is paramount to patch the vulnerable software of the TP-Link routers to the latest version. Organizations need to adopt an ETLM-powered risk-based approach to cybersecurity decision-making to minimize possible exposures and external threats coming their way. Based on these and other indicators, we suspect an uptick in cyberattacks from various nation-state threat actors on critical infrastructure, state entities, and defence organizations. Open vulnerabilities and ports in such devices will only compound the negative impact on targeted organizations and their nation’s economic prowess.