



This data-driven report examines the cybersecurity dynamics of the region, with a specific focus on Singapore. It examines the evolving landscape, encompassing APT attack campaigns, phishing, and ransomware trends. Notable findings include Southeast Asia’s high global ranking in phishing campaigns and the prominence of the Lockbit3 ransomware gang in the region.
Southeast Asia, with Singapore at its core, is at a unique intersection in the cybersecurity landscape. Amidst remarkable economic and technological growth, this region becomes a focal point for cybersecurity challenges, attracting the attention of both nation-state threat actors and profit-driven cybercriminals. This data-driven report provides insights into the shifting cybersecurity landscape of Southeast Asia, shedding light on APT attacks, phishing, and ransomware victimology.
These insights include the shift from street crimes to cybercrime, illustrated by Southeast Asia’s significant presence in global phishing campaigns, the vulnerability of the thriving manufacturing sectors to ransomware, and the noteworthy prevalence of the Lockbit3 ransomware in the region.
CYFIRMA observed 86 APT attack campaigns worldwide. Notably, there was a discernible surge in campaign activity in June and July, coinciding with the discovery of the Barracuda ESG vulnerability.
Additionally, the period witnessed heightened activity from the Lazarus Group, along with a series of ransomware incidents attributed to threat actors FIN7, FIN11, and TA505. For a more in-depth look, continue reading the subsequent sections of the report.
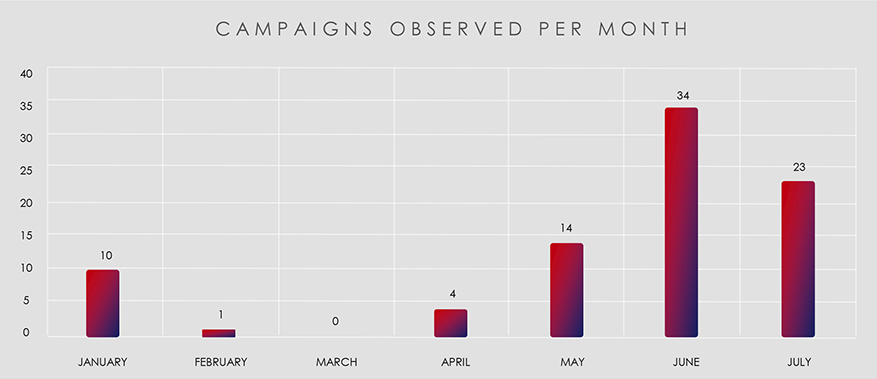
The trend is accurate, but it is important to note that the absolute numbers are slightly skewed. This is because the data is calculated from the “last seen” date, which means that some campaigns that were detected in May, June, and July were actually detected earlier. This can lead to a clustering effect in the later months.
Furthermore, one attack campaign has multiple victims in different countries and sometimes multiple suspected threat actors.
With that in mind, out of the 86 observed attack campaigns and 528 individual attacks globally, Singapore recorded 26 attacked organizations, followed by Thailand and Vietnam with 11 and 9 attacks, respectively. In the broader Southeast Asian region, there were a total of 68 recorded attacks.
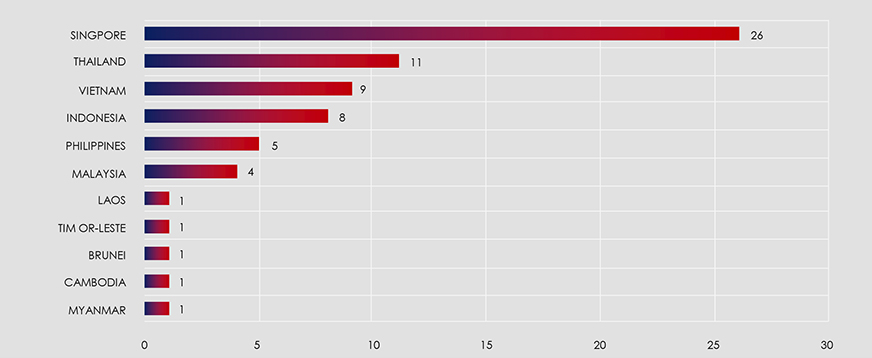
The map below highlights Singapore, Thailand, Vietnam, and Indonesia as the most frequently targeted countries in the region.
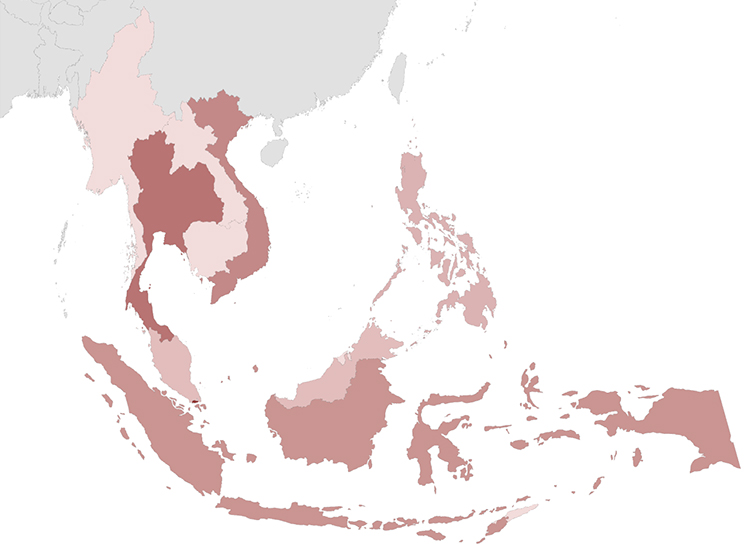
Singapore, despite its relatively small geographical footprint, records a disproportionately high number of cyberattacks. This can be attributed to its status as a host for numerous international organizations, encompassing both corporate entities and non-governmental organizations. Much like Switzerland, Singapore’s neutrality makes it a focal point for espionage activities, bridging the gap between NATO and nations like China, Russia, North Korea, and Iran, which are increasingly at odds.
The heightened Lazarus Group activity observed during this period can be attributed to the discovery of two new Remote Access Trojans (RATs), MagicRAT and QuiteRAT, and their recent detection. Additionally, the surge in Chinese cyber activity aligns with widespread campaign detections utilizing the Barracuda ESG vulnerability and other TTPs employed in that campaign, which facilitated further detections.
Furthermore, financially motivated threat actors, namely TA505 and FIN11, have affiliations with the Cl0p ransomware group. Cl0p, which includes former Conti members, recently embarked on an extensive ransomware spree, leveraging the MoveIt file transfer vulnerability.
It’s important to highlight that MISSION2025 serves as a central point for Chinese APT operations, with several instances of “Pandas” suspected to overlap with it.
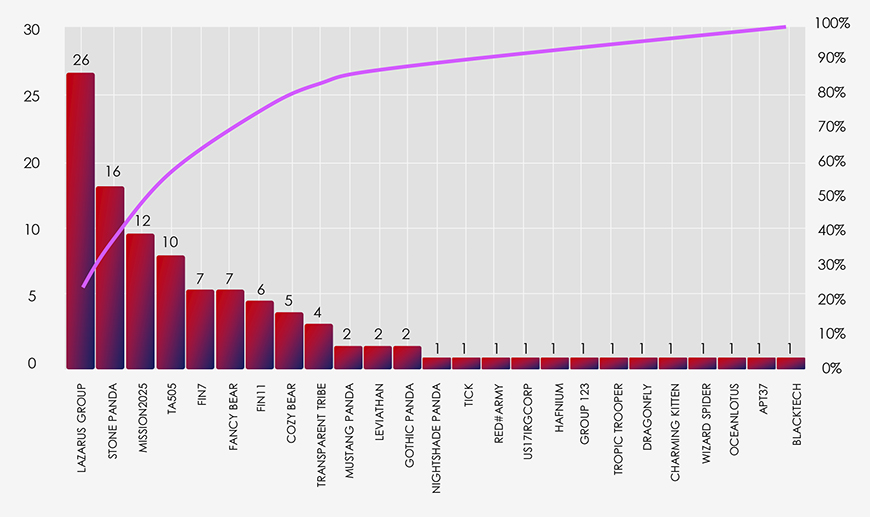
The suspected threat actors active in Singapore align with the broader threat landscape and are consistent with what one might anticipate, given Singapore’s unique geopolitical position.
Singapore’s strategic significance as a gateway and hub to the rest of the world, hosting international diplomats, businesses, and NGOs, inherently attracts regional APTs. Notably, this complex cybersecurity landscape also features the presence of other significant actors, such as the Vietnamese APT group; Ocean Lotus, and the Iranian group; Charming Kitten. Together, these diverse actors contribute significantly to the multifaceted nature of cybersecurity challenges faced within the region.
Lastly, North Korea is known to leverage private Singaporean entities for various operations in the real world and in cyberspace. This is reflected in their prominence within the observed data set.
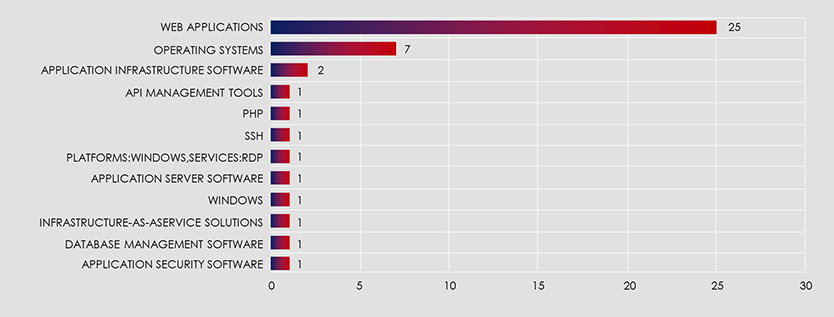
The below chart illustrates the targeted technologies and their compromise trends across observed attack campaigns. It is evident from the chart that web applications and operating systems consistently represent the most substantial and enduring security vulnerabilities.
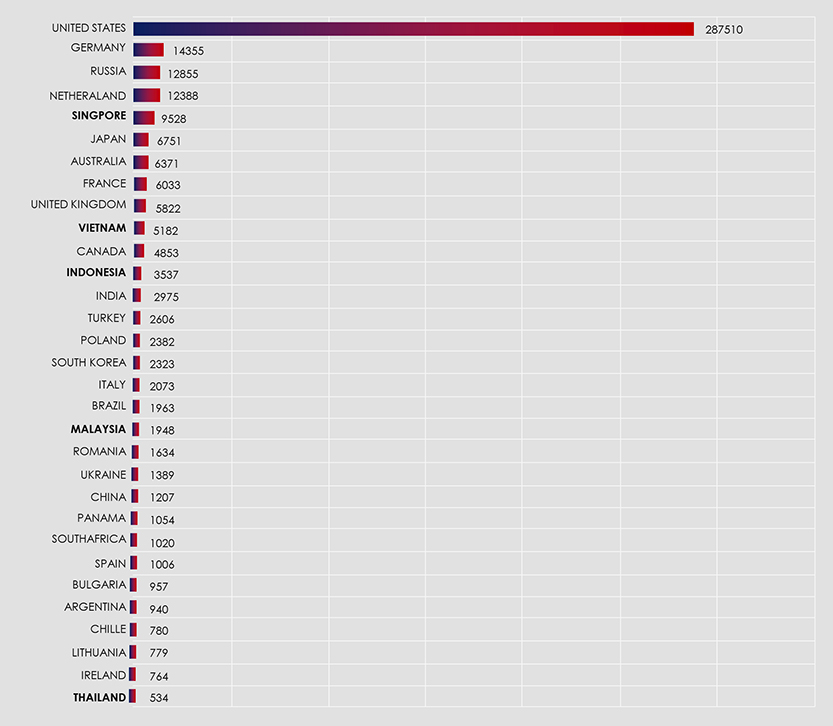
Between 1st January and 1st August, CYFIRMA’s telemetry recorded 410,793 phishing campaigns.
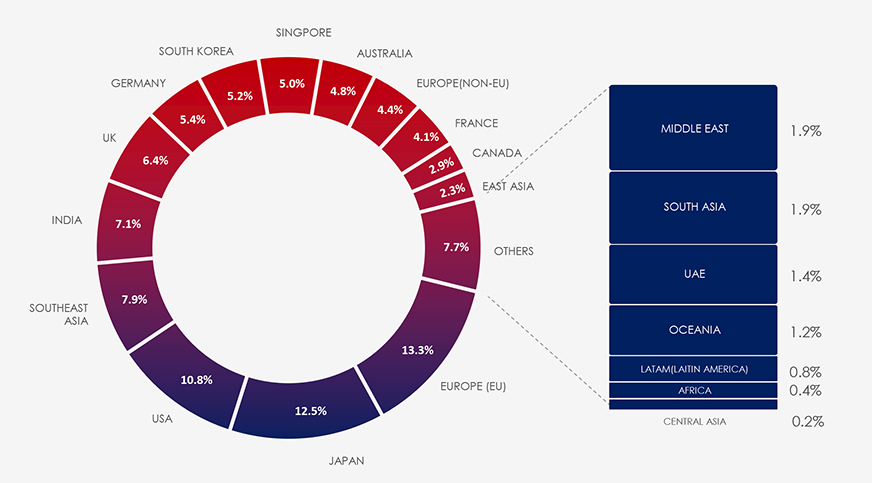
While it’s no surprise that the United States tops the list as both the primary source and target of these phishing campaigns, Singapore’s position at 5th place among over 100 countries may come as a surprise. These are data based on ASN origin telemetry, which highlights Singapore’s role as an appealing hosting location for malicious Virtual Private Servers (VPS) and exit Virtual Private Networks (VPNs). This appeal is rooted in Singapore’s outstanding high-speed, high-quality internet connectivity and its favourable business-friendly legislative environment. Unfortunately, these attributes also make it an enticing destination for cybercriminals.
Zooming out to the broader Southeast Asian region, we observe similar trends. Vietnam secures the 10th position, Indonesia ranks 12th, and Malaysia claims the 19th spot. These rankings shed light on the region’s shifting landscape, where cybercrime steadily supersedes traditional street-level criminal activities. Consequently, various phishing schemes and scams are on the rise. Finally, Thailand finds itself in the 50th position on this list.
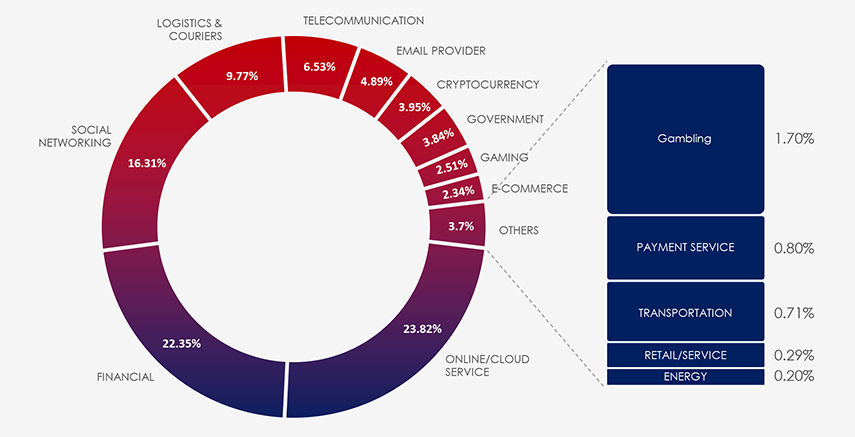
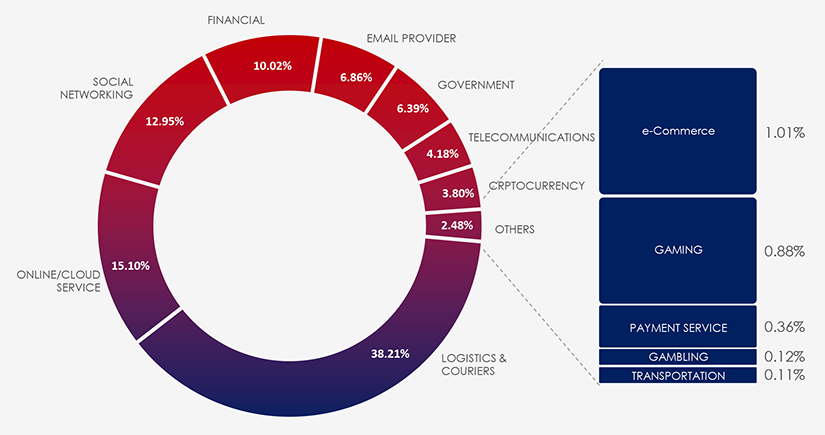
Interestingly Singapore presents a significantly different distribution of phishing themes. Among these, Logistics and Courier scams stand out as particularly prevalent in this region.
Furthermore, Singapore exhibits a notable resistance to banking-related scams. This resistance can be attributed to a collaborative effort between the government and financial institutions, which has led to heightened awareness among Singaporeans regarding various banking scams. Data indicates this effort worked and resulted in comparatively very low share of finance themed phishing campaigns.
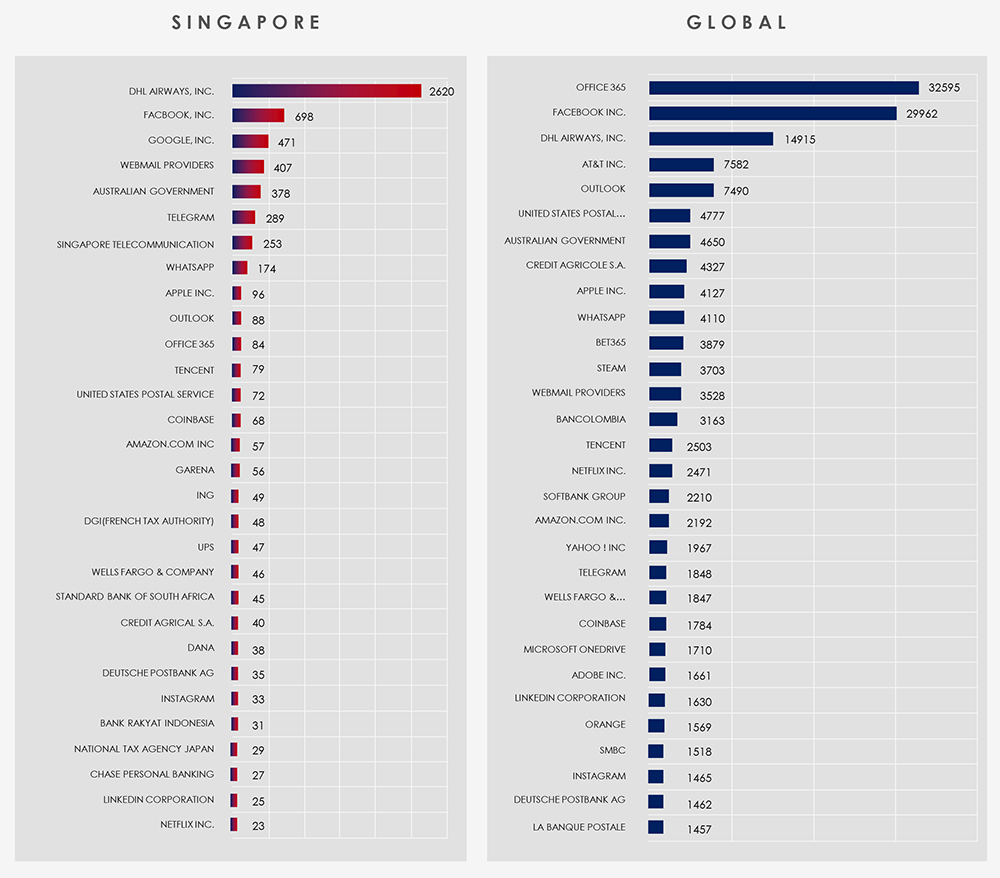
Between 1st January and 1st August, CYFIRMA has identified 2,670 ransomware victims across the globe.
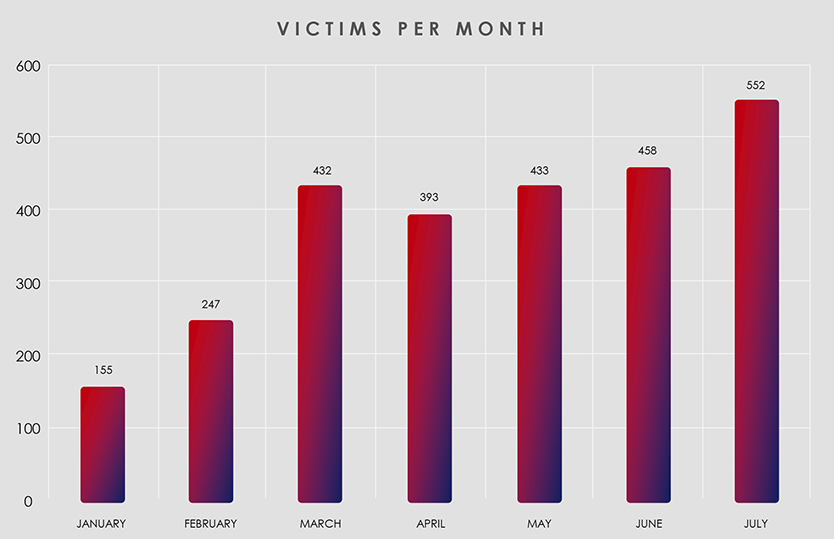
On the Monthly chart below you can see that ransomware had a slow start to 2023. If you follow the news regularly, there was a brief period where governments, businesses and organizations were delighted to finally see positive results in the fight against ransomware. Unfortunately, it did not last very long. Former Conti members together with TA505 and FIN11 regrouped and reorganized as Cl0p and came out with the largest ransomware spree to date. Using previously mentioned MoveIt vulnerability, they suddenly became 1/3 of all recorded ransomware.
The chart below breaks down the activity of each gang per month, in this case top 20 gangs. For example, number 1. Lockbit3 has been consistently active, whereas Cl0p has no victims in January and February and then skyrocketing in the rest of the year so far. Another new gang 8base is also clearly showing no victims in the first 3 months and then reporting high victim numbers since.
Going back to the previous slide of monthly activity, we can see which gangs are responsible for the rise in activity.
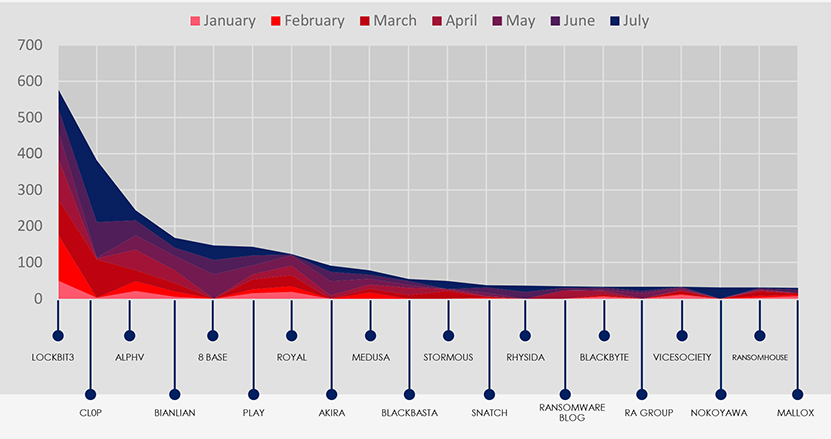
The subsequent chart underscores the dominance of major ransomware gangs, with the top 5 accounting for 57% and top 10 for 76% of all victims. Simultaneously, the chart illustrates how the collective activity of smaller groups contributes to a substantial number of victims.
ALL GANGS ACTIVITY
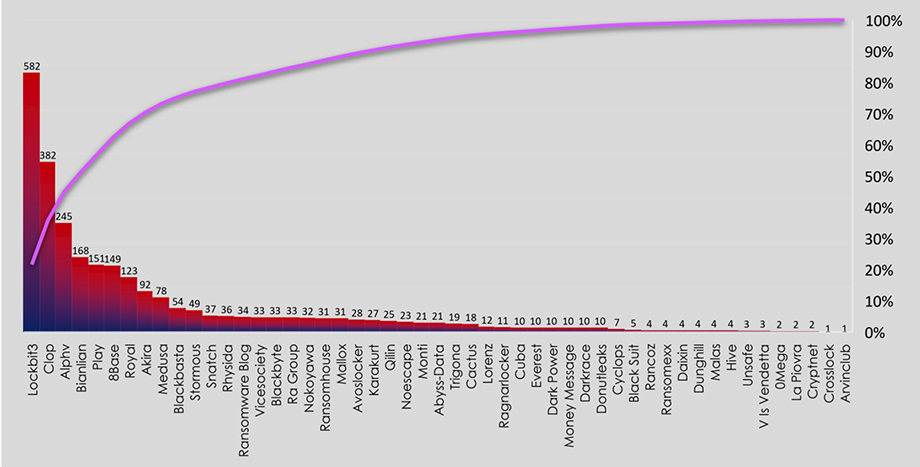
Out of a total 2,670 victims recorded, 280 have unknown geography. The chart below shows countries with the most recorded ransomware victims out of an adjusted 2,390 victims with known geography.
Similar to phishing, the US is by far the most targeted country thanks to its robust economy and digital infrastructure. And since various manufacturing organizations are the most frequent target of ransomware, countries on the list do reflect that.
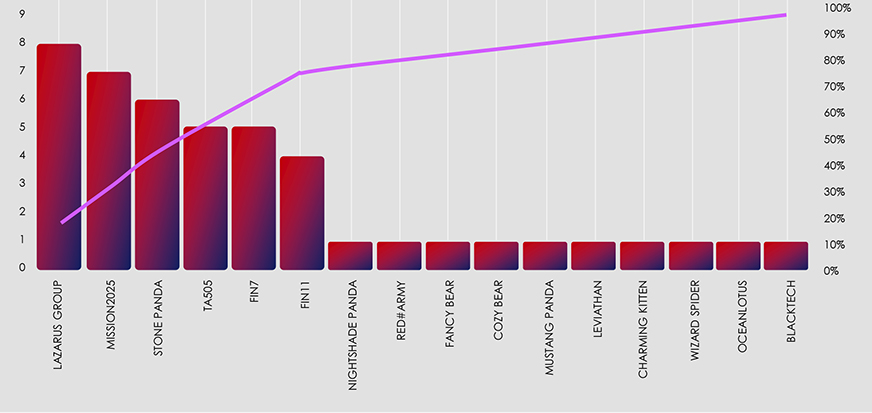
Southeast Asia as a region recorded 66 victims, accounting for 2.47% of all known victims in the same time period. Thailand is the most attacked country in the region, with shared 18th place globally. Singapore placed 35th with 8 recorded victims.
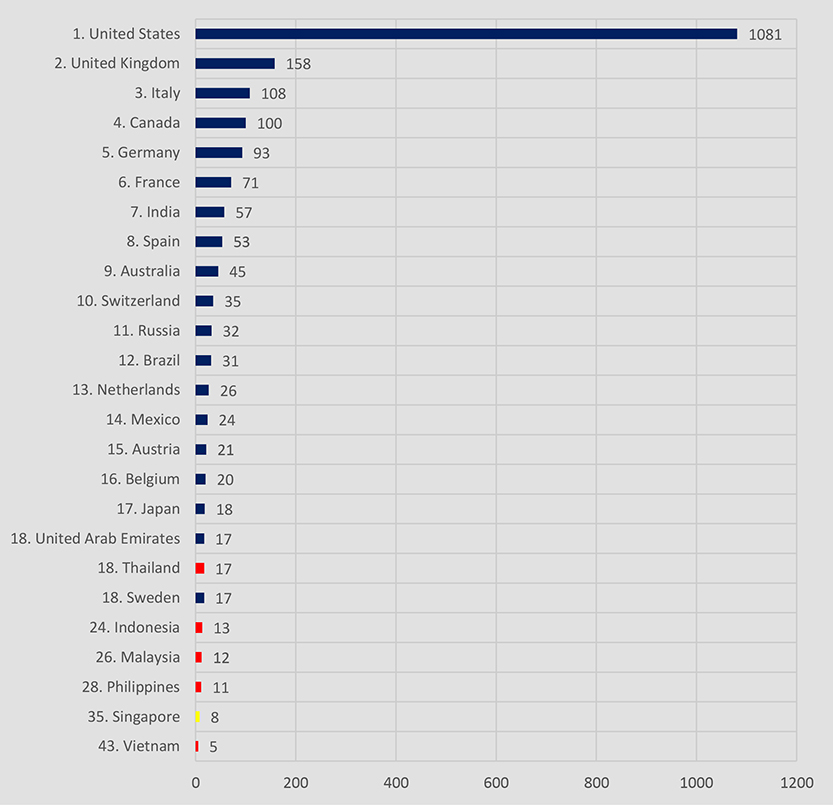
Out of the 54 active ransomware gangs, only 16 recorded victims in the region. By a large margin Lockbit3 is the most active gang, claiming 47% of all victims in Southeast Asia.
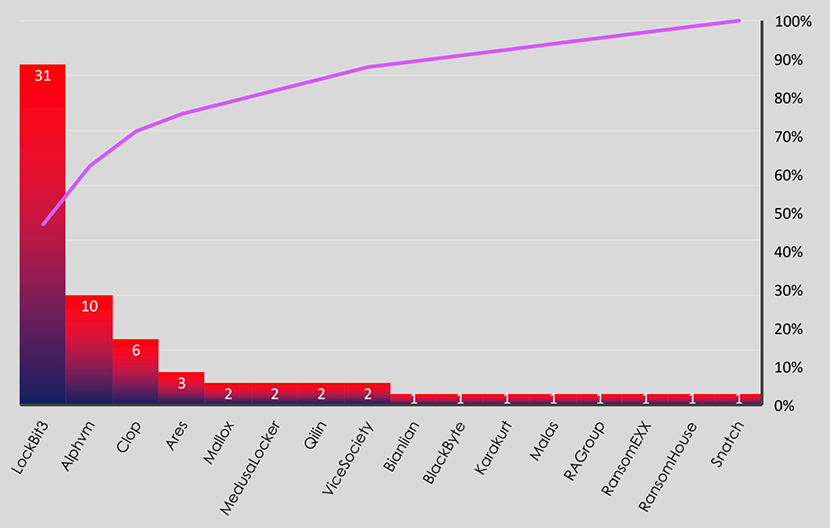
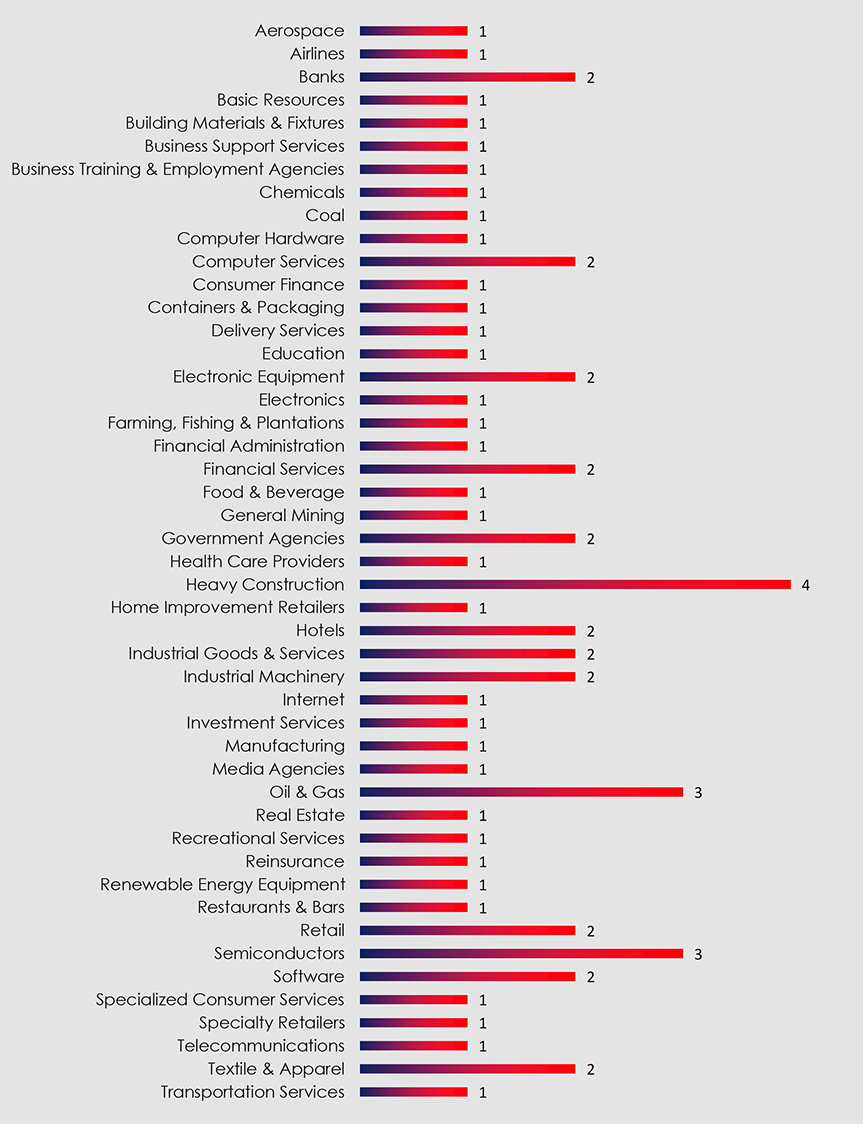
The sector chart below is in alphabetical order to easily navigate to sectors of interest. The most targeted sectors were Heavy construction, Oil & Gas and Semiconductors.
Southeast Asia has emerged as a region of considerable interest to various state- sponsored Advanced Persistent Threat (APT) groups, notably those associated with China and North Korea, along with Vietnamese actors. Singapore, positioned as a neutral diplomatic center within the region, has evolved into a significant espionage hub, including cyberspace, for nations worldwide.
In the realm of phishing, an alarming trend persists, marked by the active involvement of low to mid-skilled threat actors, who have transitioned from traditional street crimes to cybercrime. This shift coincides with Southeast Asia’s rapid digitalization and development. Notably, when examining the origins of phishing campaigns based on Autonomous System Number (ASN), countries within the region consistently secure prominent positions on a global scale. Singapore, in particular, ranks fifth, owing in part to its high-quality hosting infrastructure and relatively permissive legislative environment.
Turning our attention to ransomware, Southeast Asia boasts a thriving manufacturing sector, making it a prime target for ransomware attacks. One in every ten ransomware victims worldwide belongs to the manufacturing industry. The most active ransomware gang operating in the region; Lockbit3, stands out significantly, accounting for nearly half of all documented ransomware victims in Southeast Asia this year.
In summary, as Southeast Asia and Singapore continue their rapid growth and economic development, they have also become breeding grounds for domestic cybercrime activities, while simultaneously attracting the interest of foreign, highly sophisticated threat actors, both state-sponsored actors and those driven by financial motives.