



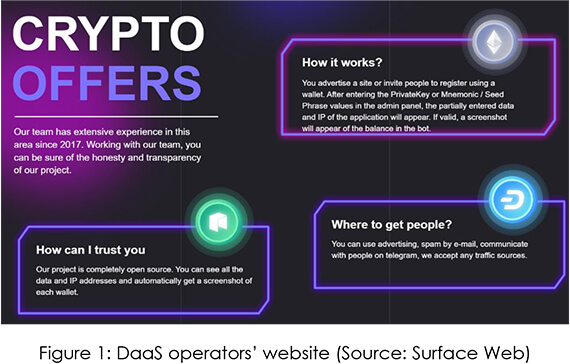
The CYFIRMA research team has discovered a Drainer-as-a-service (DaaS) project in the wild that is open to all and is being advertised over hacking forums and telegram channels. The project is gaining popularity amongst attackers due to its ease of access and simplicity of operations, which have been facilitated by the operators using free guides, free phishing templates, automatic phishing configuration setup, free domains, and more.
We have ascertained with high-confidence that the operators behind the project are of Russian-origin. The threat group was most likely operating under a different name since 2017 but underwent a rebranding in 2021, which links them to the DaaS program we have discovered.
Cryptocurrency Drainers, also known as Crypto Stealers, are designed to steal the funds from a victim’s wallet. The drainers are primarily spread using a combination of social engineering and phishing, luring victims to enter their wallet details on deceptive websites. One of the notable drainers in 2023 was Inferno Drainer – whose developers announced that they were shutting down (public) operations in November 2023, leaving a void in the crypto drainer community. We have observed multiple drainers that are trying to fill that gap with aggressive marketing, but the CG project bags the winner’s title, with close to 50k subscribers on their telegram channel and 10k affiliates working with them. The affiliates have been observed to be Russian, English and Chinese speakers.
The free crypto drainer provided by the DaaS operators is compatible with:
Supported Wallets:
Supported Tokens:
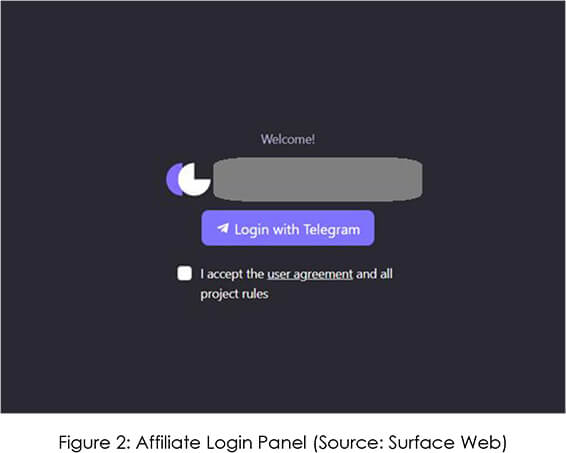
The threat group has created two websites; one for describing their affiliate program, and another; that is the admin panel for affiliates.
Drainer Configuration
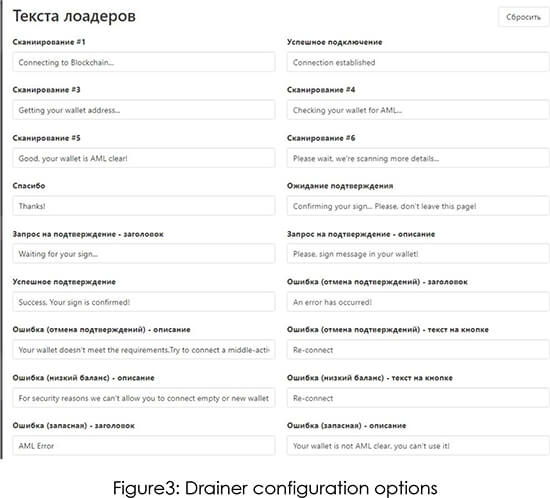
Successful connection – message that will be displayed to user when wallet is connected.
Scan #(number) – set of messages that will be displayed to the user when scanning assets. Not necessarily all of them will be used, the longer the scan (more assets), the more likely each of them will be used. Initially, it takes 3 seconds to display each message.
Acknowledgement pending – a message is displayed when a user has confirmed some transaction (e.g. Approve), and it is waiting for confirmation on the network.
Confirmation Request – This is the message the user will see when requesting any withdrawal (Approve,Permit, Contract etc)
Error (cancel confirmations) – the error which is displayed to the user when he canceled all requests for confirmations (if it is not enabled to request cyclically, of course).
Error (low balance) – Error at low wallet balance.
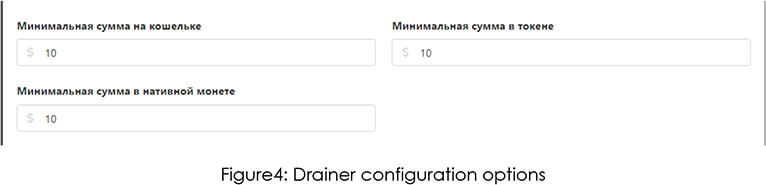
Customize the minimum amounts to request a withdrawal (can’t be less than 10) : This option may be useful when an attacker is working manually with social engineering.
The threat group has also created a separate telegram channel for posting free designs of phishing pages that mimic most of the prominent crypto exchanges.
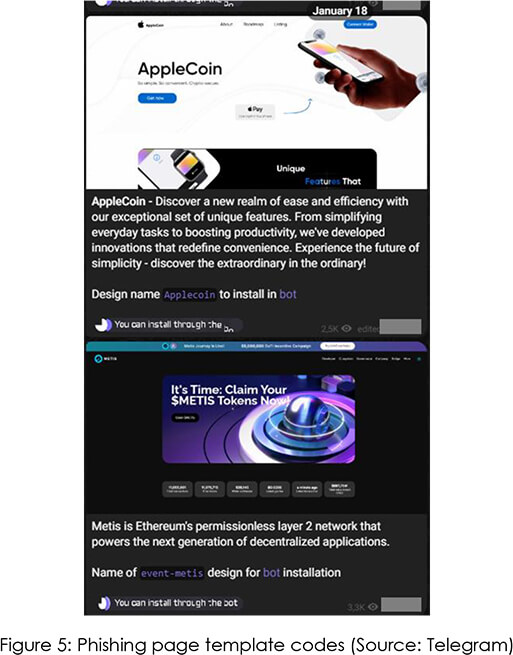
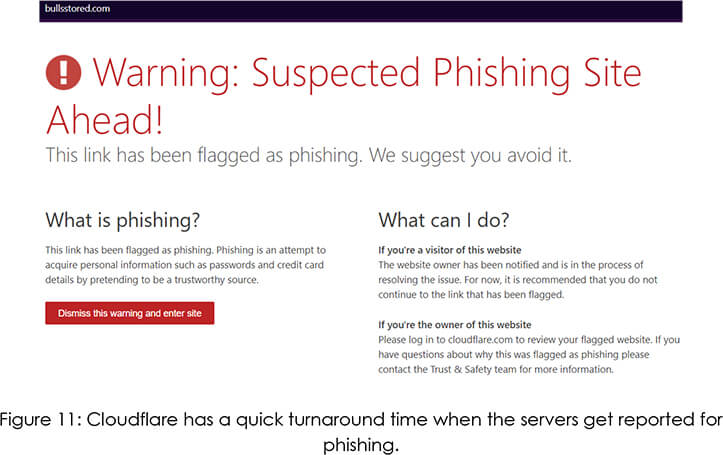
This channel refers attackers to a telegram bot that enables them to run their fraud operations without any third-party dependencies. The bot allows a user to get a domain for free, clone an existing template for the new domain, set the wallet address where the scammed funds are supposed to be sent, and also provides Cloudflare protection for that new domain.
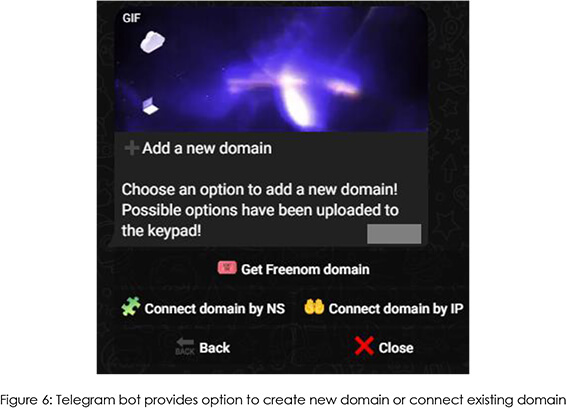
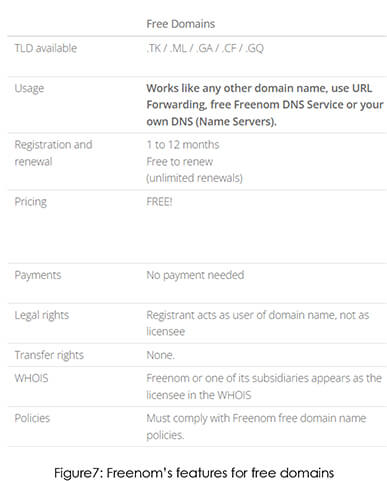
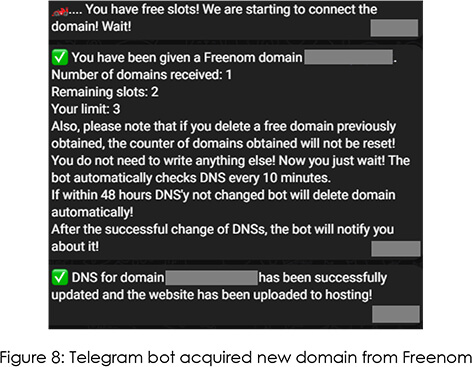
The threat actors have integrated Freenom’s free domain services to support the creation of the phishing pages. As seen below on their website, the threat actor can use .tk, .ml, .ga, .cf and .gq domain TLDs for free. However, it is important to note that existing domains can be connected to the bot using its IP address or NS records.
As we can see below, the website has Cloudflare protection enabled, which falls in line with the whois record’s last updated date.
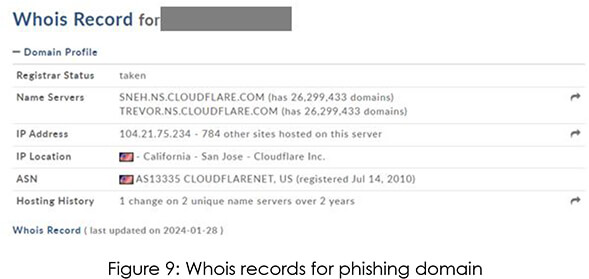
The threat group uses 2 custom telegram bots called “SiteCloner” and “CloudflarePage”. As the names suggest, they are used for cloning a website and adding Cloudflare protection to the cloned website respectively.

Based on the transactions observed, we can ascertain with high-confidence that the number of phishing and social engineering campaigns carried out by the DaaS affiliates so far, has seen a rise.
Recent Campaigns on X (formally twitter):
These campaigns are spread mostly using compromised X accounts. Other campaigns are spread by obtaining a crypto leads database, performing mass phishing and/or social engineering.
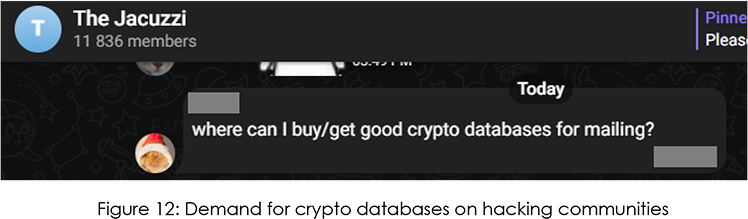
However, the scalability of the DaaS services allows anyone to create a new phishing site using a template in just a few minutes. We have observed an increasing demand in hacking communities for crypto PII databases for social engineering and phishing.
“Pretend inferiority and encourage his arrogance. ~ Sun Tzu, The Art of War”
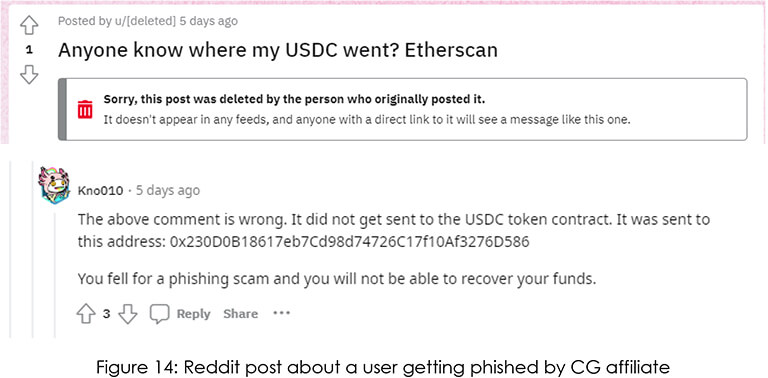
A small OPSEC mistake by threat actors can help connect the dot between seemingly unrelated entities. On a telegram channel meant for generic information dissemination by the threat group, the CYFIRMA research team noted multiple wallet transaction screenshots posted as proof of assurance.
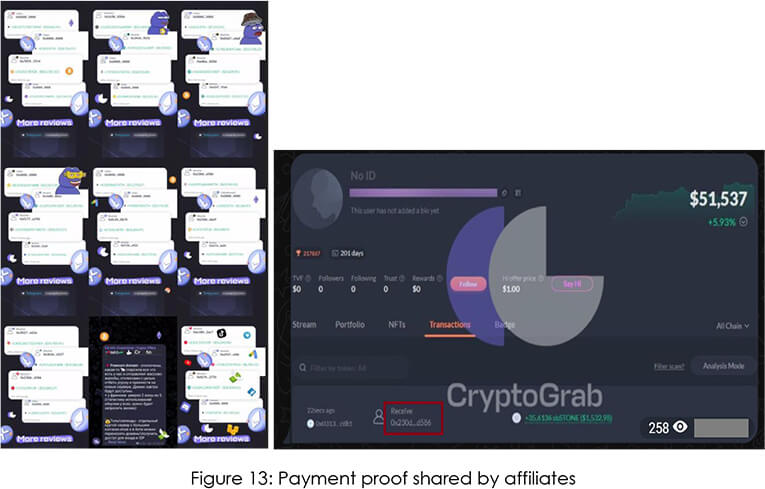
On most of the transaction screenshots, we could see the first and last few characters of the wallet addresses where the funds were received by affiliates. We started investigating and soon found out the wallet address linked with one of the affiliates.
0x230D0B18617eb7Cd98d74726C17f10Af3276D586
Upon further investigation, we noted that this wallet has recently been involved in a crypto phishing incident. In this case, the victim was using Metamask crypto wallet. The affiliate (wallet address above) followed a typical pattern used by phishing scams, where attackers trick victims into signing a permit. There is no legitimate reason to do a token transfer like this with permit2 broadcasted from a different address.
The discovery of CG, a Drainer-as-a-service (DaaS) project, shows that crypto drainers will become a bigger problem during 2024. Run by a Russian group, it’s gaining popularity because it’s easy to use, comes with free guides, and has a big affiliate network of 10,000 members. Other similar projects are making it easier for less skilled attackers to get involved. It works with major networks and wallets, using customizable phishing pages and Cloudflare protection, making it a situation where the risk is low, the skill level required is minimal, but the potential rewards are high.
Appendix1
Management Recommendations:
Incident Response Plan:
Vendor Due Diligence:
Regulatory Compliance:
Strategic Recommendations:
Educational Initiatives:
Partnerships and Information Sharing:
Tactical Recommendations:
Multi-Factor Authentication (MFA):
Phishing Simulation Exercises:
Real-time Monitoring:
| No. | Indicator | Remarks |
| 1 | spskelonline[.]com | Phishing domain |
| 2 | firstspconf[.]com | Phishing domain |
| 3 | zyberparty[.]tech | Phishing domain |
| 5 | cbrdackz[.]fun | Phishing domain |
| 6 | skellion[.]pro | Phishing domain |
| 7 | cbrzcommunity[.]fun | Phishing domain |
| 8 | Bullsstored[.]com | Phishing domain |
| 9 | Spaceskelliesstores[.]com | Phishing domain |