



The rise of Ransomware-as-a-Service (RaaS) affiliate programs has led to a surge in demand for initial access brokers within the hacking community. This trend has created a scarcity of brokers, prompting threat actors to prioritize quantity over the quality of initial access. The CYFIRMA research team recently came across a threat group who have ramped up their operations in order to keep up with the demand. The threat actors, previously known for their stealer logs from Redline, Meta and Raccoon, have recently introduced a MaaS model for their proprietary information stealer too. In this report, we dive into the operations of the Russian-speaking threat group, their history, and capabilities along with their newly released infostealer, called Monster Stealer.
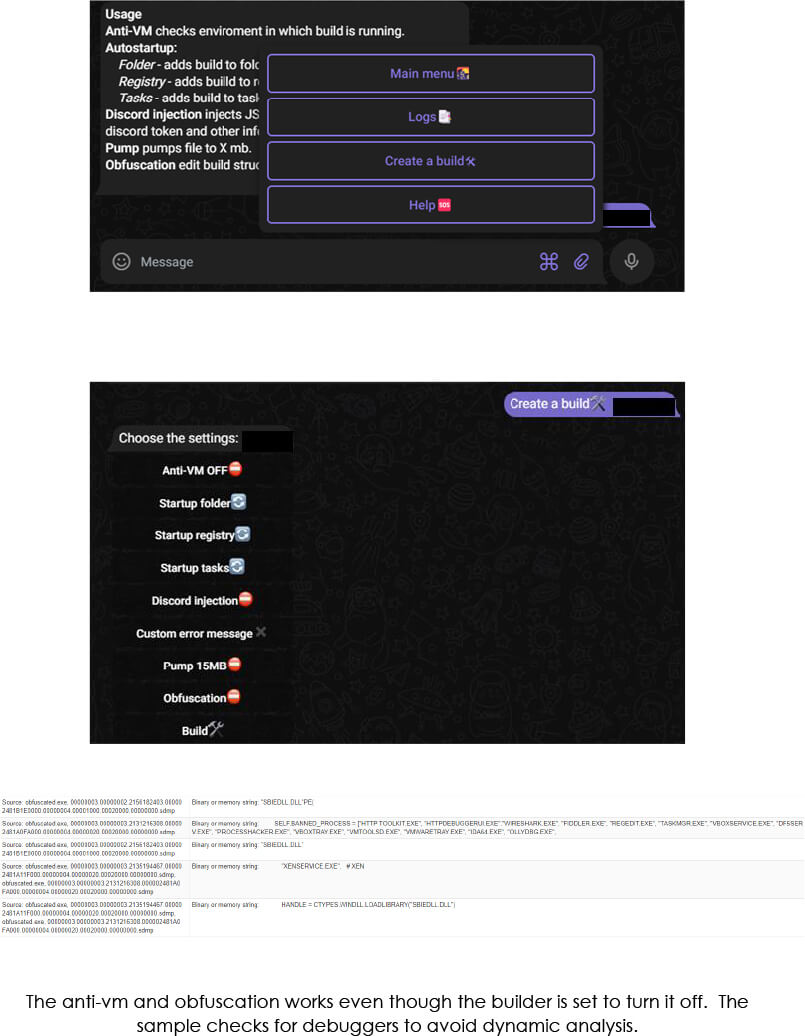
The builder is hosted on a bulletproof VPS and uses a telegram bot to take inputs from an attacker.
The malware uses KERNEL32.dll and msvcrt.dll for most imports.
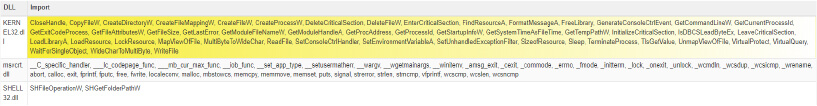
Imports by DLLs
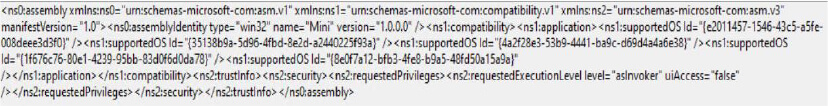
Manifest (level > AsInvoker) – indicating that the malware is set to run with the same privileges as the parent process.
Malware can leverage this function to obtain the unique identifier of the current process.
GetStartupInfoW
Malware can utilize this function to retrieve information about the startup configuration of the current process.
GetSystemTimeAsFileTime
Malware can employ this function to acquire the current system time in FILETIME format.
LoadResource
Malware can use this function to load various resources, such as executable files or DLLs.
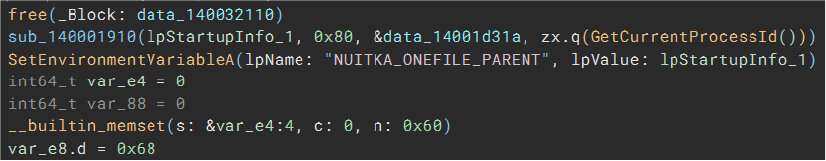
SetEnvironmentVariableA
Malware can use this function to set the value of an environment variable in ASCII format.
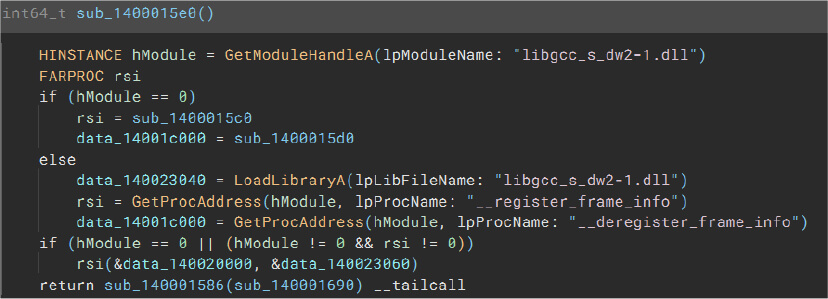
LoadLibraryA
Malware can employ this function to load a dynamic-link library (DLL) into the address space of the calling process.
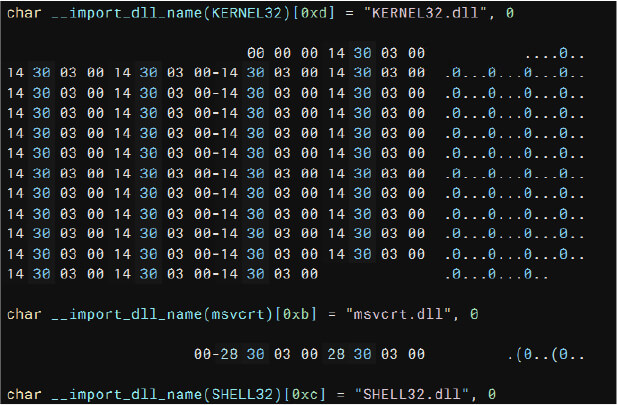
Importing necessary DLLs
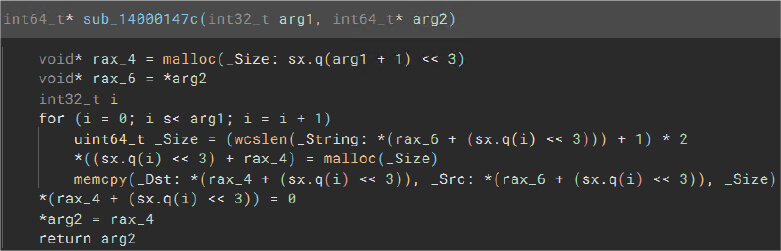
Malloc and memcpy
Malware can use these functions to allocate memory and perform memory copying operations.
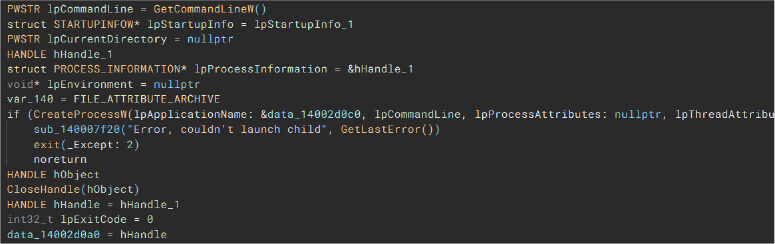
CreateProcessW
Malware can leverage this function to create a new process and its primary thread.
MapViewOfFile
Malware can use this function to map a view of a file into the address space of the calling process.
ReadFile
Malware can use this function to read data from a file.
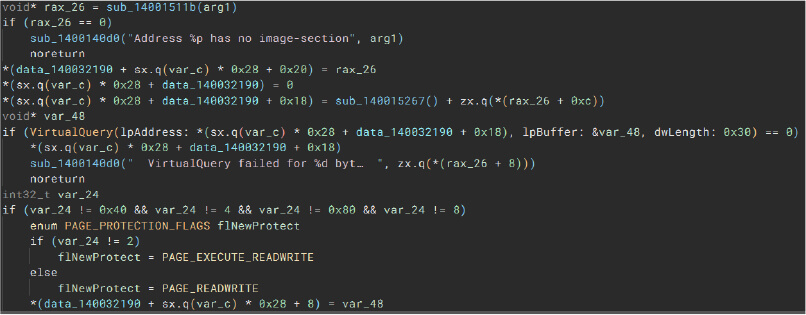
VirtualQuery
Malware can use this function to retrieve information about a range of pages in the virtual address space.
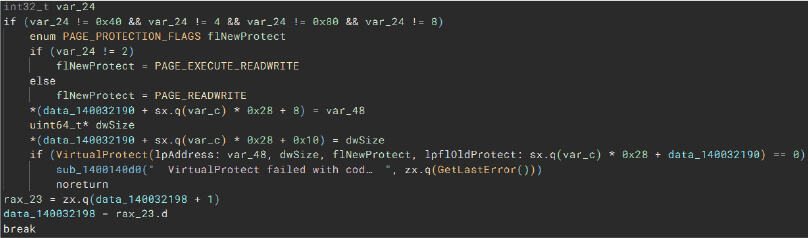
VirtualProtect
Malware can leverage this function to change the access protection of a region of virtual memory.
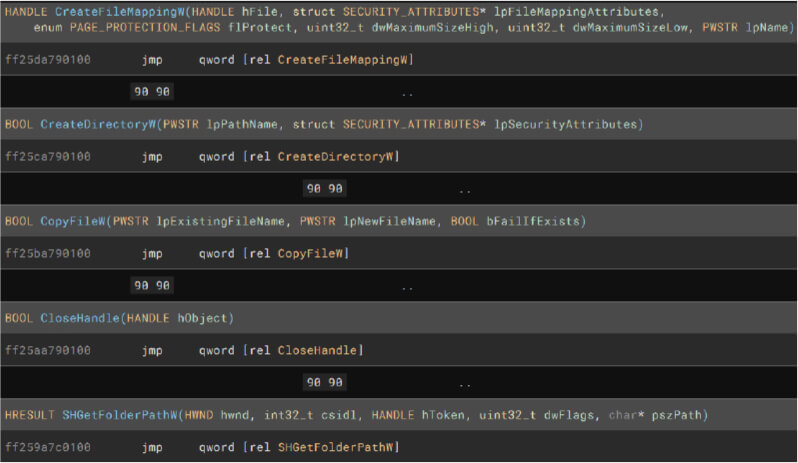
File and Folder Actions
Threat Actor Profile: Russian-speaking, financially motivated, stealer log aggregator, botnet owner, initial access broker
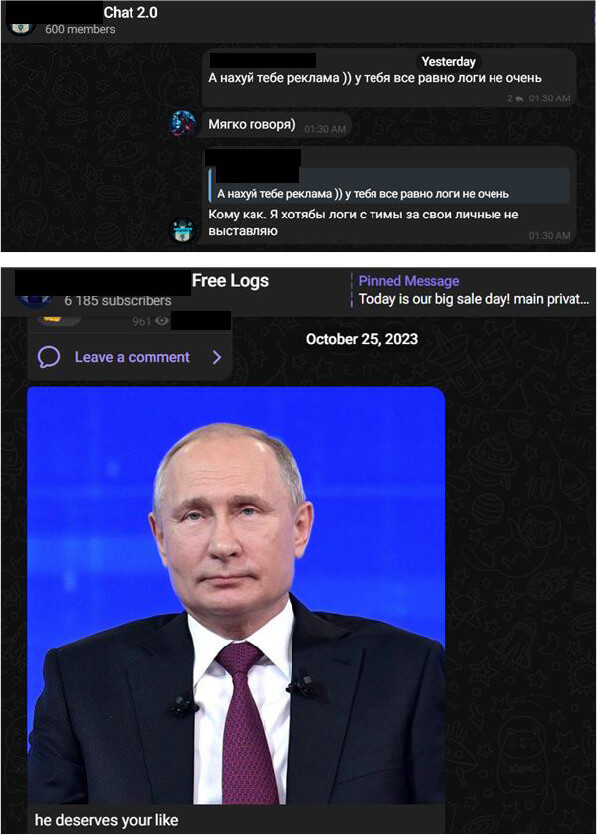
Threat Landscape: The TA uses malware spreading techniques such as malvertising and social engineering to spread the stealers to unsuspecting people. Upon successful infection, the stealer logs from those individuals are shared freely to all.
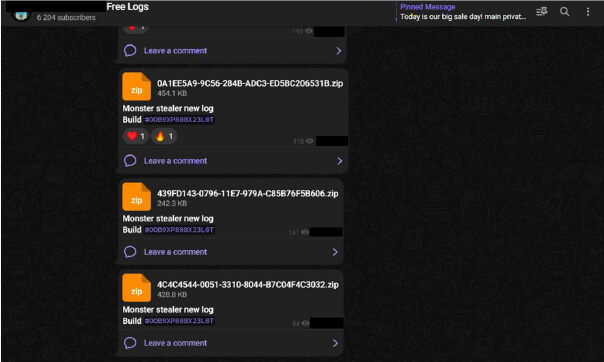
In addition to the free logs, the TA also shared live stealer logs on another private channel.
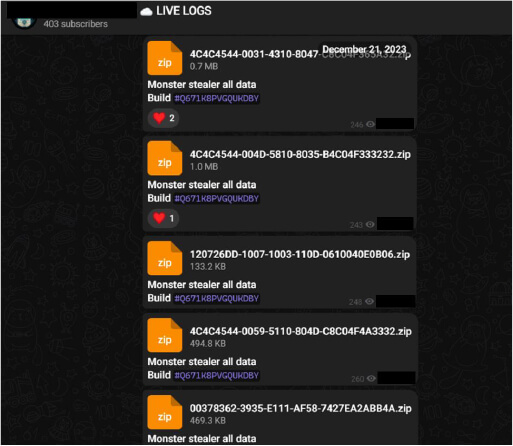
What’s the difference? While Free Logs might have been partially used by other people before it’s posted freely, the live logs are relatively new and have a higher chance of compromising the accounts associated with the individual infected with the infostealer.
In summary – many of these compromised individuals work in large corporations. The stealer logs can be easily leveraged by a TA to gain initial access to a corporate asset using a valid employee account. Lack of MFA and session management controls are icing on the cake for an attacker using this methodology.
The threat actors operate solely on Telegram. They have two channels dedicated to stealer logs, one for chat and one for the newly released stealer. We have observed increased engagement on their telegram channels, indicating visibility among threat actors.
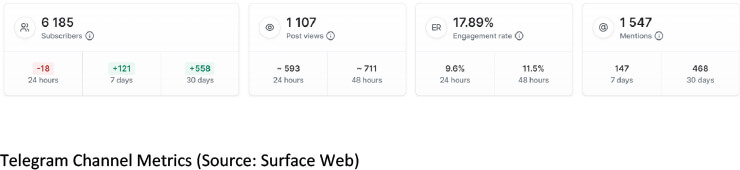
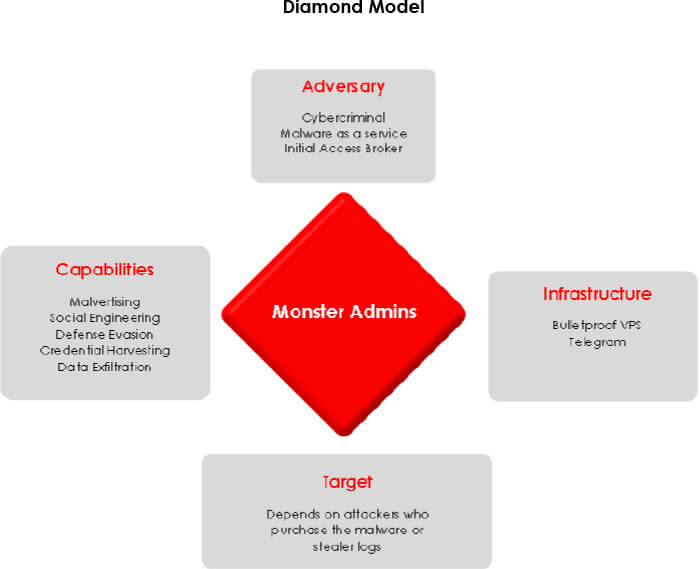
With the increase in the number of RaaS affiliate programs, the demand for initial access brokers has seen a surge amongst the hacking community. As a result, an increasing number of threat actors are focusing on quantity over quality of initial access, due to scarcity of brokers. Hence, we can see that more and more IABs are resorting to the use of stealer logs to gain initial foothold on a target, along with the old school way of exploiting vulnerabilities. Monster operators have gauged this situation well and are gradually coming into the spotlight of prominent stealer log aggregators. Noticing how lucrative MaaS is, they released their own stealer, which underscores the fact that they are financially motivated. Organizations need to be proactively looking into their exposure within the stealer log threat landscape and mitigate the risks posed by low-hanging fruits before they can cause an impact.
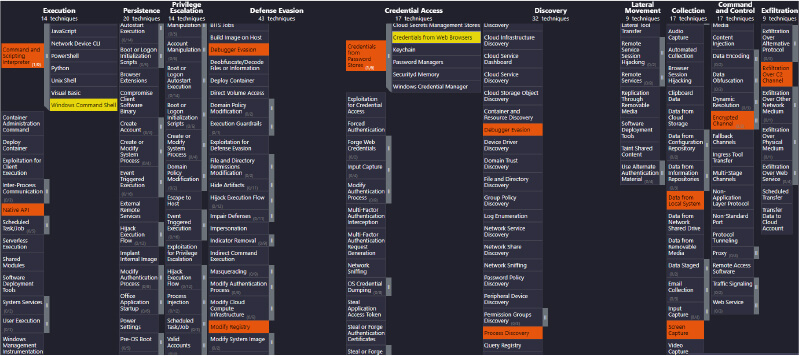
MITRE Mapping
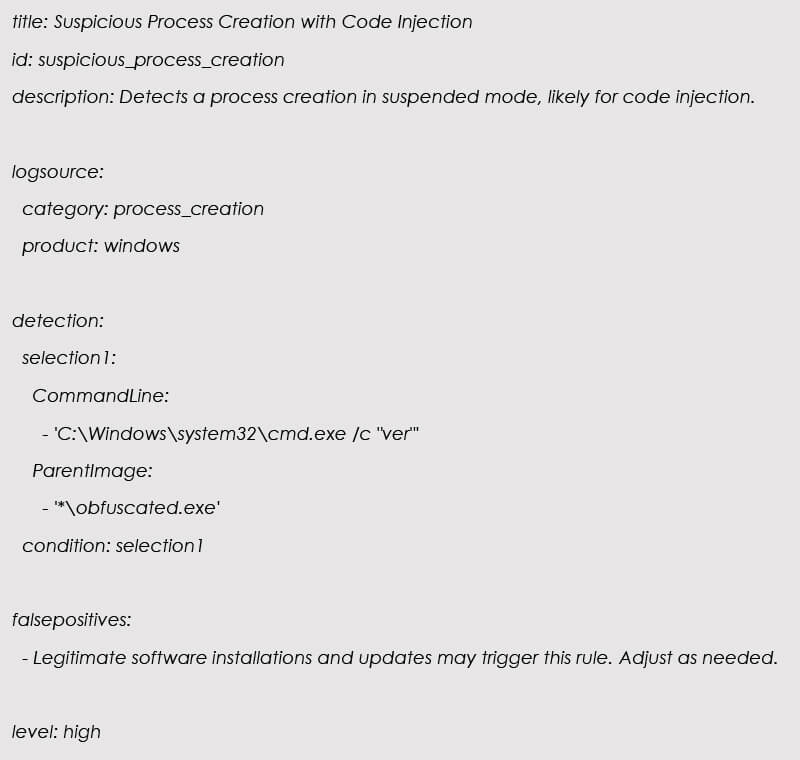
Sigma Rule
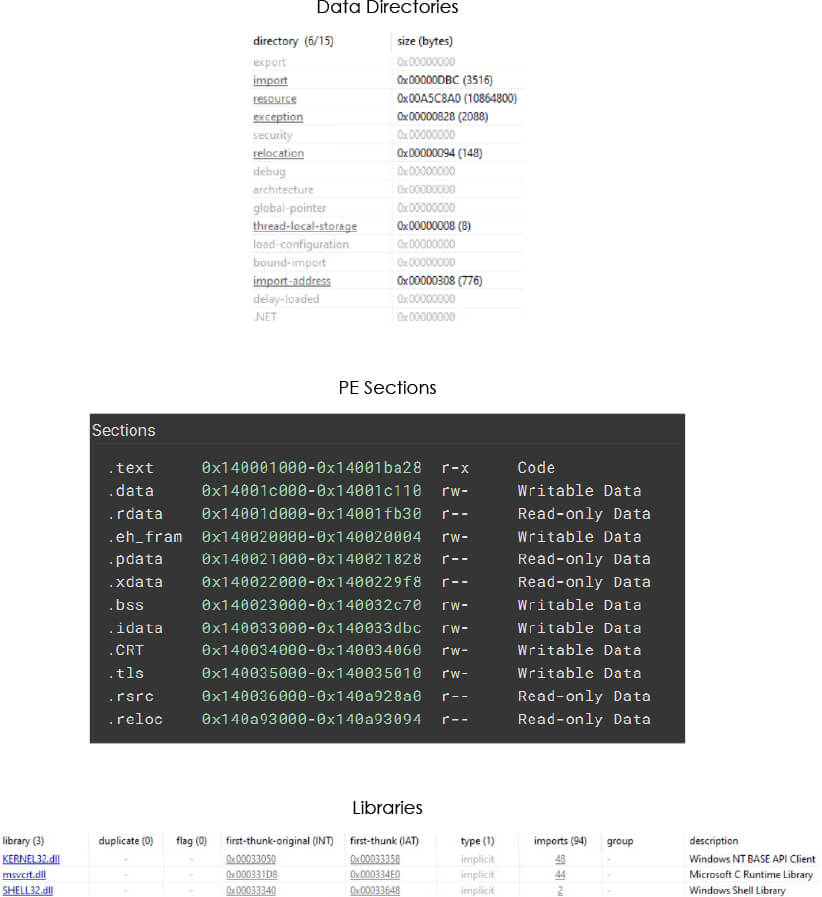
Note: We have not added malware hashes in this report as the builder generates EXEs with different hashes each time, even when the settings are same.
Develop a Robust Security Policy:
A comprehensive security policy establishes guidelines and controls for data handling, laying the foundation for protecting sensitive information.
Invest in Employee Training:
Well-trained employees are less likely to fall victim to phishing attacks or unknowingly download malicious content, reducing the risk of information stealers.
Implement Least Privilege Principle:
Limiting user privileges minimizes the potential impact of information stealers by restricting unauthorized access to critical systems and data.
Regular Security Audits:
Routine security audits help identify and remediate vulnerabilities, reducing the likelihood of exploitation by information stealers.
Endpoint Protection:
Advanced endpoint protection tools can detect and block information stealers before they compromise sensitive data stored on endpoints.
Network Segmentation:
Isolating critical systems through network segmentation limits the lateral movement of information stealers, preventing them from spreading across the network.
Email Security:
Robust email security measures filter out phishing attempts and malicious attachments, mitigating the risk of information stealers gaining access through email-based attacks.
Application Whitelisting:
Application whitelisting ensures that only approved and secure applications run on endpoints, preventing the execution of unauthorized or malicious software.
Incident Response Plan:
An effective incident response plan helps minimize the impact of information stealers by providing a structured and timely response to security incidents.
Threat Intelligence Integration:
Integrating threat intelligence enhances the organization’s ability to proactively defend against information stealers by staying informed about evolving threats.
Continuous Monitoring:
Continuous monitoring identifies and responds to anomalies, enabling early detection and mitigation of information stealers before they can cause significant harm.
Data Encryption:
Encryption protects sensitive data, rendering it useless to information stealers even if they manage to access it, adding an additional layer of defense.
Vendor Risk Management:
Assessing and managing third-party vendor risks helps prevent information stealers from exploiting vulnerabilities in external systems connected to the organization’s network.
Regular Updates and Patching:
Timely patching and updates address known vulnerabilities, reducing the attack surface and minimizing the risk of information stealers exploiting weaknesses.
Backups and Recovery:
Regular backups ensure that data can be restored in case of an information stealer attack, preventing data loss and minimizing downtime.
Collaboration and Information Sharing:
Sharing threat intelligence and best practices with industry peers strengthens the collective defense against information stealers and other cyber threats.