Published On : 2023-06-24
EXECUTIVE SUMMARY
The CYFIRMA research team has identified a new marketplace run by unknown threat actors, known as the Zero-Day Shop. The marketplace facilitates the synergy between malware developers and black hats – enabling malware developers with a platform to sell their tools to other black hats around the world. In addition to malicious tools, the platform acts as a middleman between initial access brokers who want to sell data or access to other threat actors who are specialized in the further stages of the cyber kill chain and are capable of exploitation, privilege escalation, and causing business disruption to individuals and businesses.
INTRODUCTION
This report aims to highlight the services and operating structure of this new marketplace and the risks posed by its products. We also provide an analytical overview of our attribution assessment as to the motivations, operating model and potential geolocation origins.
The marketplace operators created a Telegram channel in order to spread the word about the launch.
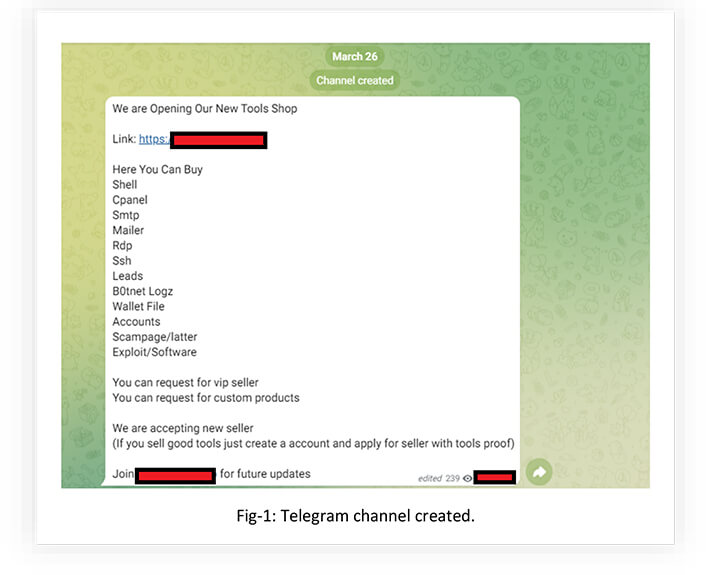
There’s a wide range of attacks that are possible using these products. Threat actors who buy these products can use the data within their operations and leverage it for further attacks.
KEY FINDINGS
CYFIRMA researchers noted that the threat actors are using CDN and WAF services to mask the real IP address of the webshop. Upon further investigation using OSINT sources, we were able to discover the VPS on which the webshop has been hosted.
https://www.virustotal.com/gui/ip-address/62.204.41.77/relations
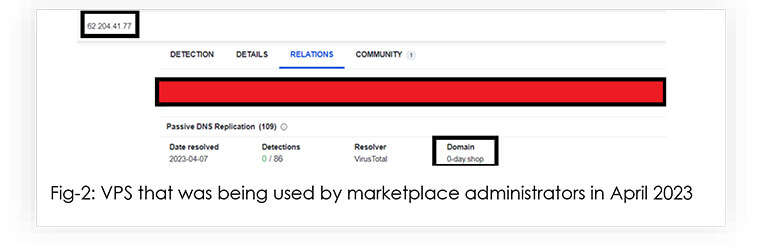
The IP address is registered with Horizon LLC and can be geolocated to Moscow, Russia.
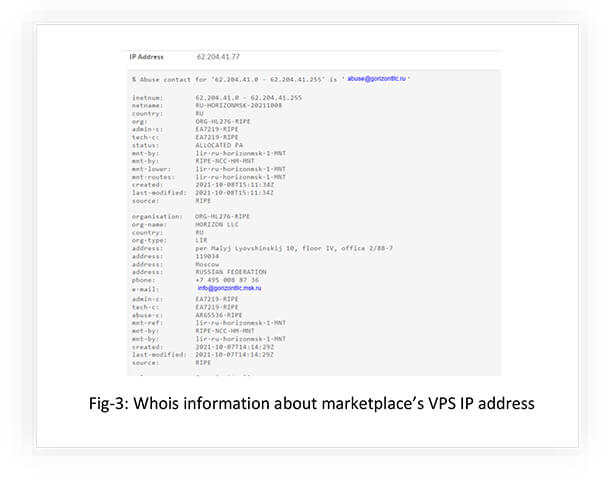
Horizon LLC offers comprehensive services for promotion of European business in Russia, mainly aiming at cooperation with producers of technological equipment in B2B sector.
ZERO-DAY SHOP: MARKETPLACE OVERVIEW
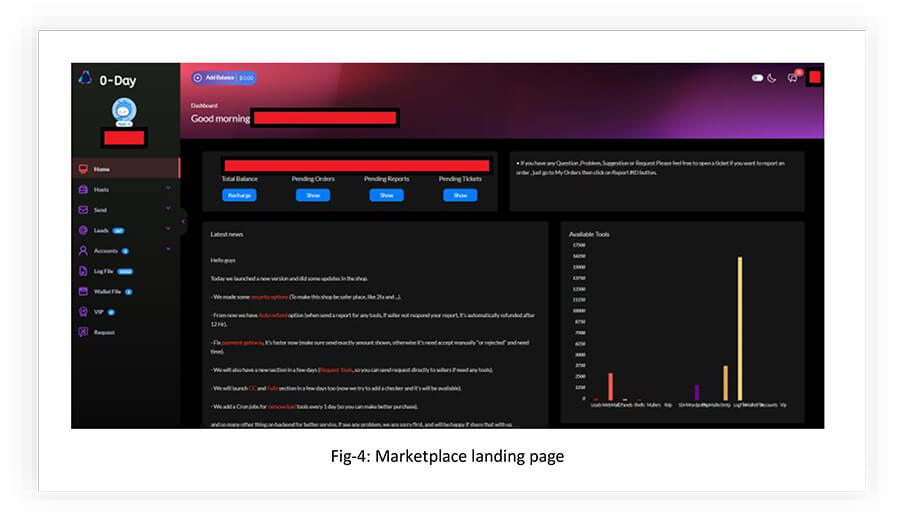
The webshop requires an account to be created on the forum. CYFIRMA researchers noted that there is no verification for the email address being used to sign up to the forum.
- The absence of email verification can allow attackers to create multiple accounts easily. This can help them hide their true identity and conduct malicious activities anonymously on the forum.
- Attackers can use email addresses of unsuspecting people to create accounts on the forum, impersonating them and conducting activities that can harm their reputation. This can lead to legal issues and other repercussions for the impersonated individual.
THE BELOW ARE OFFERED FOR PURCHASE ON THE WEBSHOP : RDPS
By purchasing RDPs (Remote Desktop Protocol) from the marketplace, attackers can gain access to remote systems and potentially carry out various malicious activities.
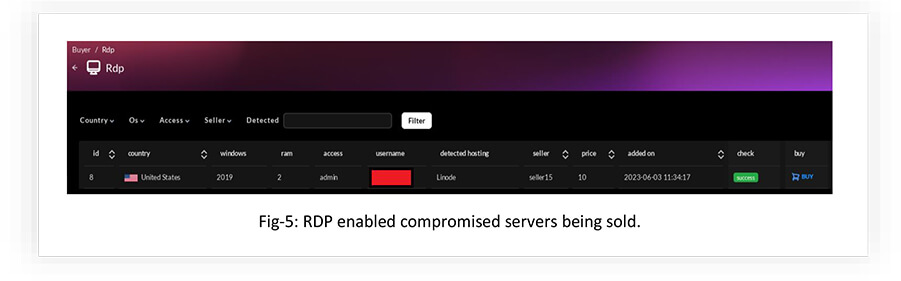
Some of the actions an attacker can perform by buying RDPs include:
- Unauthorized access: Attackers can use the purchased RDP credentials to gain unauthorized access to remote systems. Once inside, they can navigate the system, execute commands, and perform activities as if they were physically present on the machine.
- Data theft: Attackers can browse through files, directories, and databases on the compromised system to steal sensitive data such as personal information, financial records, intellectual property, or customer databases.
- Malware deployment: Attackers can use the RDP connection to upload and execute malware on the remote system, thereby infecting it with malicious software. This malware can be used for various purposes, including further data exfiltration, remote control, or launching larger-scale attacks.
- Privilege escalation: If the compromised system has limited user privileges, attackers can attempt to escalate their privileges using techniques like privilege escalation exploits or credential harvesting. This allows them to gain higher-level access and control over the system and potentially move laterally within the network.
- Botnet recruitment: Attackers can use the RDP access to install and control botnet agents on the compromised system, effectively adding it to their network of compromised devices. These botnets can be used for distributed denial-of-service (DDoS) attacks, spam distribution, or other malicious activities.
- Sell or rent access: In some cases, attackers may not directly use the RDP access themselves but instead sell or rent it to other threat actors who are interested in compromising specific targets. This allows them to profit from the access without engaging in subsequent malicious activities.
WEBMAILS, SMTPS AND CPANELS
By purchasing these types of access from the marketplace, an attacker can gain control over web hosting accounts and perform various malicious activities.
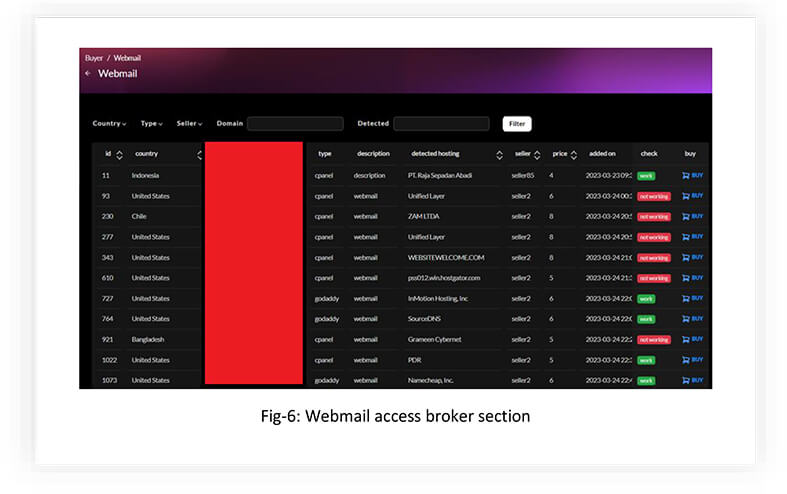
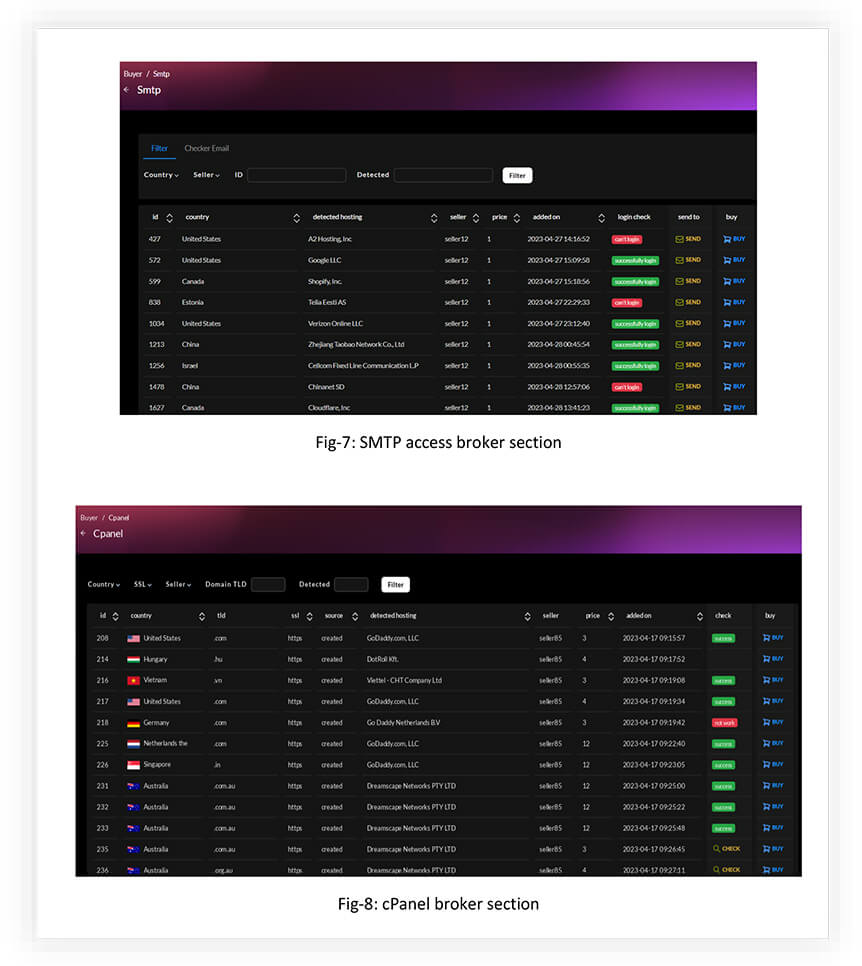
As we can see in the figures above, the marketplace has the option to check the validity of the listings made by the sellers. This highly increases the credibility of the data being sold, making it a lucrative alternative to other marketplaces without this functionality.
Here are some actions an attacker can potentially carry out by buying cPanel access:
- Website Defacement: Attackers can modify the content of websites hosted on compromised cPanel accounts. They may deface the websites by replacing legitimate content with malicious or unauthorized content, causing reputational damage to the website owner.
- Data Theft: Attackers can access and steal sensitive data stored within the compromised cPanel accounts. This can include customer databases, login credentials, personal information, or financial data. Stolen data can be used for identity theft, sold on the black market, or leveraged for further malicious activities.
- Malware Distribution: Attackers can use compromised cPanel accounts to distribute malware by injecting malicious code into websites hosted on these accounts. This malware can infect visitors to the compromised websites, leading to further compromise of their systems or the theft of sensitive information.
- Email-based Attacks: With cPanel access, attackers can manipulate email settings to send out spam, phishing emails, or distribute malware-laden attachments. They can exploit the compromised accounts to launch large-scale email campaigns, impacting the reputation of the targeted domain and potentially leading to financial losses or data breaches.
- Account Takeover: Attackers can hijack user accounts hosted on compromised cPanel accounts by resetting passwords or modifying account settings. This can lead to unauthorized access to sensitive information, unauthorized transactions, or further compromise of associated services or systems.
- Credential Harvesting: Attackers can attempt to harvest login credentials by intercepting and recording login attempts on compromised cPanel accounts. These credentials can then be used for further unauthorized access or sold on the black market.
WORDPRESS and PHP-MAILERS
By purchasing WordPress access from the marketplace, an attacker can gain unauthorized control over WordPress websites and exploit them for various malicious purposes.
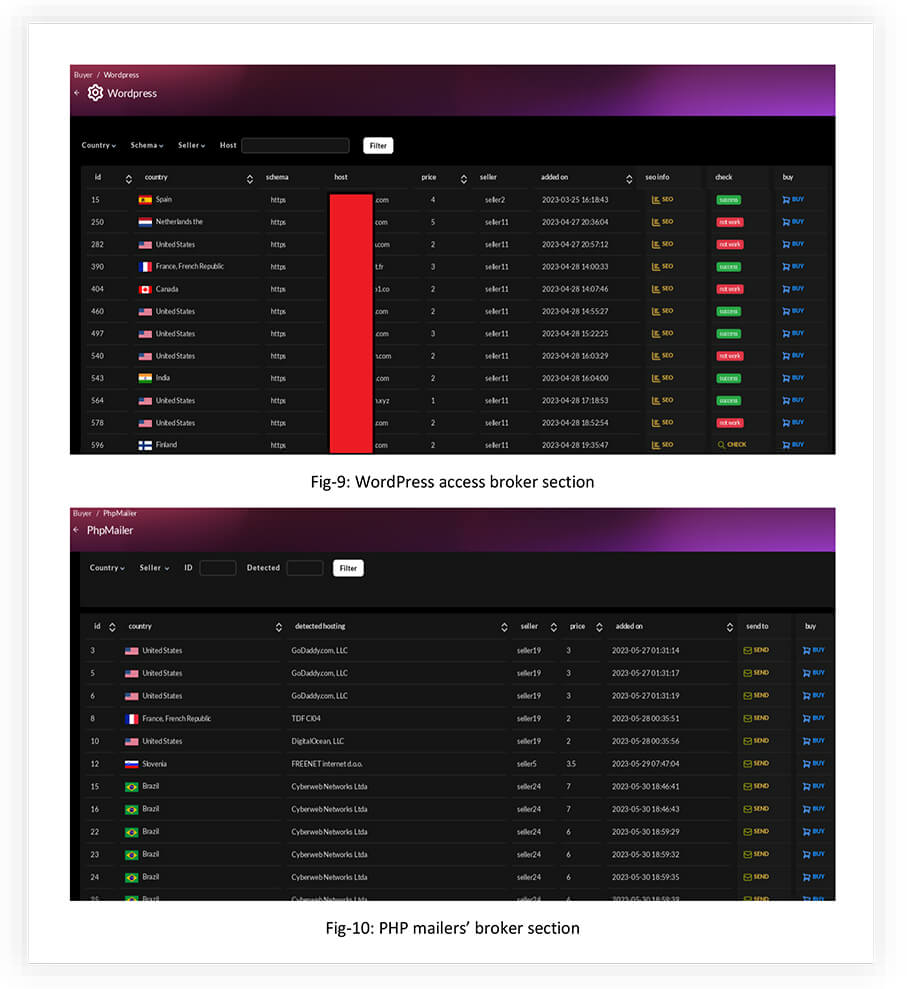
The marketplace provides the option for attackers to check the SEO performance of the victims they are buying access to.
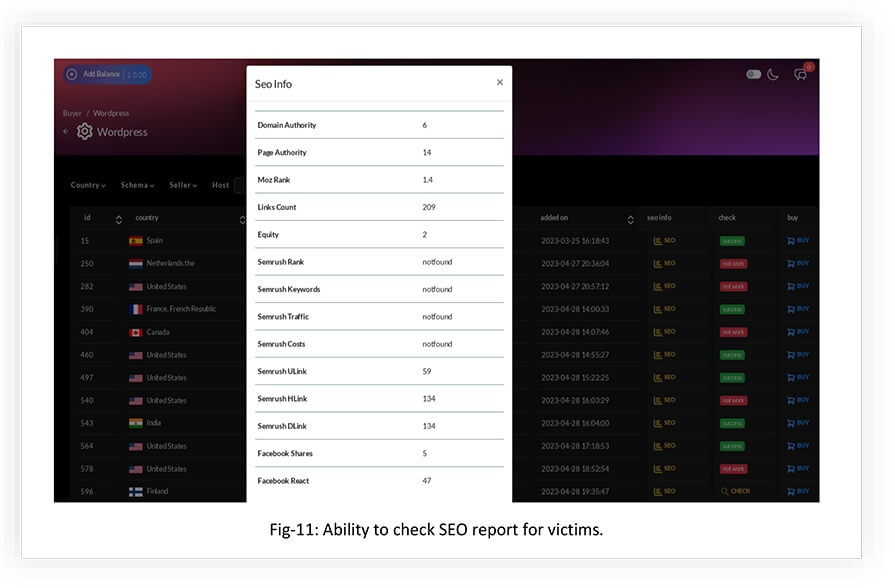
Here are some actions an attacker can potentially carry out by buying WordPress access:
- Phishing Attacks: Attackers can create phishing pages within compromised WordPress websites to trick visitors into revealing their sensitive information, such as login credentials, credit card details, or personal data. These phishing pages can mimic legitimate login or payment pages, deceiving users and facilitating identity theft or financial fraud.
- SEO Spamming: Attackers can use compromised WordPress websites to inject spammy content or links that manipulate search engine rankings. This can negatively impact the website’s reputation, visibility, and search engine rankings, potentially resulting in financial losses for the website owner.
- Botnet Recruitment: Attackers can use compromised WordPress websites to host and control botnet agents, turning them into part of a larger network of compromised devices. These botnets can be used for various malicious activities, including distributed denial-of-service (DDoS) attacks, spam distribution, or cryptocurrency mining.
SMTP TO SMS
By purchasing SMTP to SMS services from the marketplace, an attacker can leverage the capabilities of this service to carry out various malicious activities. SMTP to SMS services allow sending emails that are converted into SMS messages and delivered to mobile devices.
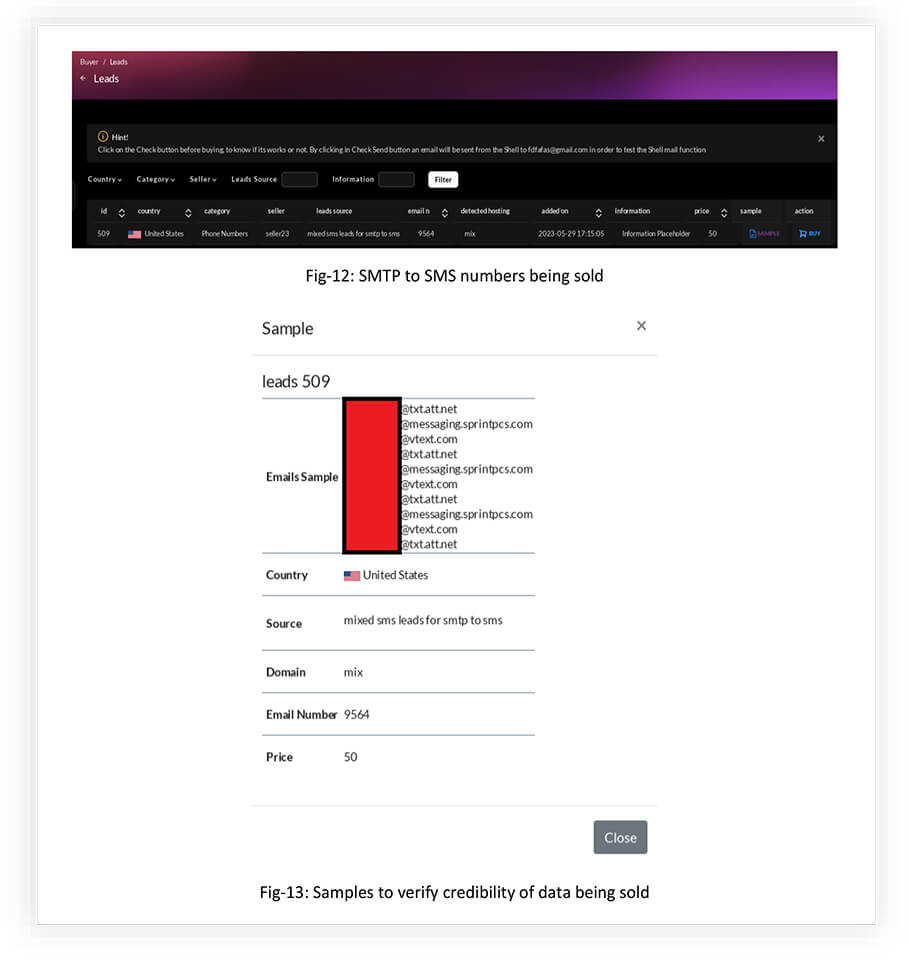
Here are some actions an attacker can potentially carry out with SMTP to SMS services:
- Phishing and Social Engineering: Attackers can use SMTP to SMS services to send phishing messages via SMS, tricking recipients into revealing sensitive information or performing certain actions. These messages can mimic legitimate organizations or services, luring users into sharing their credentials, personal data, or financial information.
- Spam and Unsolicited Messages: Attackers can send bulk SMS messages using SMTP to SMS services to distribute spam or unsolicited content. These messages can promote scams, malicious websites, or unwanted products and services, causing annoyance and potentially leading to further fraudulent activities.
- Malware Distribution: Attackers can include malicious links or attachments within SMS messages sent through SMTP to SMS services. When recipients interact with these links or open the attachments, malware can be downloaded and installed on their mobile devices, leading to data breaches, unauthorized access, or financial loss.
- Account Takeover: Attackers can exploit the SMS-based authentication or password reset mechanisms of targeted services. By using SMTP to SMS services, they can intercept SMS messages containing verification codes or password reset links, enabling them to gain unauthorized access to user accounts.
- Denial-of-Service Attacks: By sending a massive volume of SMS messages through SMTP to SMS services, attackers can overload mobile networks or specific phone numbers, causing service disruptions and rendering the targeted devices or networks temporarily unavailable.
- Smishing: Smishing refers to SMS-based phishing attacks where attackers try to deceive users into revealing sensitive information or taking certain actions through SMS messages. Attackers can use SMTP to SMS services to conduct smishing campaigns, exploiting the trust associated with SMS communications to manipulate victims.
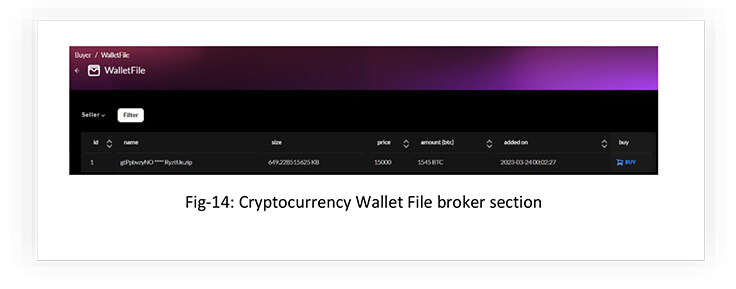
WALLET FILES
The marketplace also has a section for listing wallet files. A wallet file typically contains a user’s private keys, which are used to access and transfer cryptocurrency from their wallet. When a threat actor obtains a victim’s wallet file, they can use the private keys to gain access to the victim’s cryptocurrency and transfer it to their own account.
WEBSHELLS
Buying shells from the marketplace equips threat actors with the ability to carry out a wide range of attacks on a victim’s system.
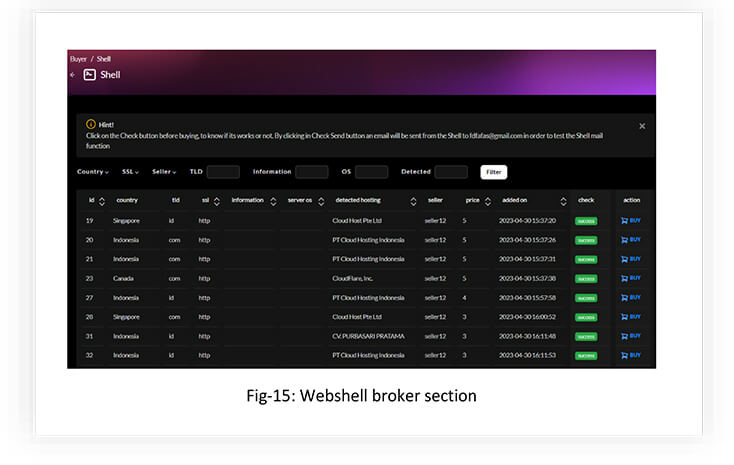
Following are some of the ways an attacker can benefit from buying a webshell from the marketplace:
- Remote access: With a shell, a threat actor can gain remote access to a victim’s system and execute commands as if they were physically present on the system. This can allow the attacker to carry out a variety of attacks, such as data theft, malware installation, and privilege escalation.
- Persistence: A shell can be used to establish a persistent backdoor on a victim’s system, allowing the attacker to maintain access even if the victim detects and removes the initial attack vector.
- Privilege escalation: Once a threat actor gains access to a victim’s system, they can use a shell to run commands that elevate their privileges and gain higher levels of access to the system.
- Data exfiltration: A shell can be used to run commands that allow an attacker to search for and steal sensitive data, such as login credentials, personal information, or financial data.
In addition to shells, the marketplace also has sections for RDP and SSH access, but there are no listings by any seller on those sections yet.
SCAMPAGES
Attackers can exploit scampages to trick users into divulging their sensitive information, such as login credentials, personal details, or financial data.
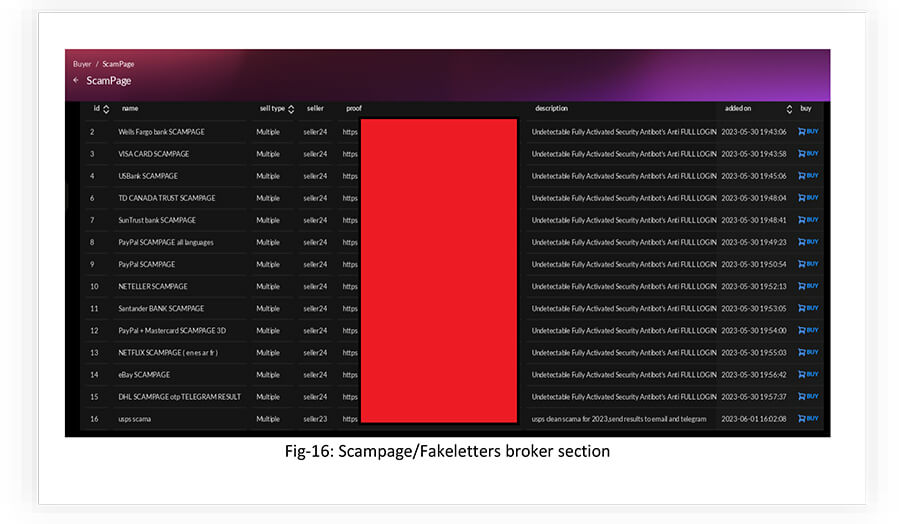
Here’s how attackers can utilize scampages to carry out their malicious activities:
- Phishing Attacks: Attackers can use scampages as part of phishing campaigns. They send out fraudulent emails or messages that appear to be from legitimate organizations, such as banks, payment gateways, or OTT platforms. These emails contain links to scampages designed to mimic the genuine login or payment pages of the targeted services. When victims unknowingly enter their credentials on these fake pages, the attackers capture the information, allowing them to gain unauthorized access to user accounts or conduct further fraudulent activities.
- Account Takeover: By obtaining users’ login credentials through scampages, attackers can hijack their accounts on banks, payment gateways, or OTT platforms. Once they gain unauthorized access, they can perform unauthorized transactions, steal funds, or manipulate account information for financial gain.
- Identity Theft: Scampages often request users to provide personal information beyond login credentials, such as full names, addresses, social security numbers, or date of birth. Attackers can collect this information through scampages and use it for identity theft, opening fraudulent accounts, or conducting other forms of financial fraud.
- Credential Harvesting: Scampages can be used to harvest a large number of login credentials and personal data. Attackers can sell these credentials on the dark web to other threat actors or use them for various malicious purposes, such as credential stuffing attacks, where they attempt to use the same username and password combinations on multiple services to gain unauthorized access.
- Financial Fraud: With the information obtained from scampages, attackers can carry out financial fraud, including unauthorized transactions, money transfers, or purchases using the victims’ compromised accounts or payment details. This can lead to financial losses for the victims and reputational damage for the targeted organizations.
ETLM INSIGHTS
- Threat Actor Profile: Based on the available information, there is suspicion that they are operating from Russia, however this is a low-confidence statement due to paucity of quality evidence.
- Threat Landscape: The marketplace offers a range of tools and services that can be used for various cybercriminal activities, such as phishing, malware, ransomware, and data theft. As a result, it is likely to attract a wide range of attackers with different motivations and capabilities, from script kiddies to advanced nation-state actors.
- Victimology: The targets are product-dependent, and as they accept sellers without a stringent process, they are evidently willing to work with anyone from anywhere.
- Impact Assessment: The ease of access to the tools and services along with the credibility of data offered by the marketplace is likely to lower the barrier to entry for cybercriminals, making it easier for threat actors with minimal expertise to launch effective cyber-attacks.
CONCLUSION
The Zero-day shop offers various products that can be used by threat actors to execute different types of cyber-attacks. The marketplace is currently in the initial stages but is set to attract a lot of small threat actor groups following the paid advertisements by the marketplace administrators on multiple forums. Security researchers and professionals should be aware of these products and how they can be used by threat actors, in order to develop effective defenses against them. To protect against these threats, organizations must implement a comprehensive cybersecurity strategy with a proactive approach that includes a combination of technical and organizational measures, such as implementing multi-factor authentication, patching and updating systems and software, using advanced threat intelligence tools, and providing regular security awareness training to employees.
RECOMMENDATIONS
- To protect against unauthorized access via shells, organizations should implement strict access controls, enforce strong passwords, and monitor for any suspicious activity or unusual system behavior.
- Organizations should secure their web hosting accounts with strong passwords, multi-factor authentication, and regular security updates to prevent attackers from gaining access to sensitive files and data.
- To defend against email-based attacks, organizations should implement email security protocols, such as SPF, DKIM, and DMARC, to verify the authenticity of incoming emails and filter out spam and phishing messages.
- Organizations should use email filtering technologies and firewalls to block outgoing spam and suspicious email traffic, while also educating employees on how to recognize and report phishing attacks.
- To secure RDP, organizations should use secure passwords, enforce two-factor authentication, and restrict access to authorized users only. It is also recommended to use VPNs to encrypt RDP traffic and prevent eavesdropping.
- Organizations should use secure key-based authentication instead of passwords, monitor SSH traffic for any unusual activity or suspicious logins, and implement strong access controls to limit the number of users with SSH access.
- To prevent social engineering attacks, organizations should implement strong security awareness training programs that educate employees on how to recognize and report phishing emails and other social engineering tactics.
- Organizations should use advanced threat intelligence tools that can identify and block botnet traffic, while also monitoring network traffic for any unusual patterns or suspicious activity.
- To secure cryptocurrency wallets, organizations should use strong passwords and two-factor authentication, store wallets on secure offline devices, and monitor transactions for any signs of fraud or unauthorized access.
- Organizations should use strong passwords and multi-factor authentication, monitor for any unusual login activity or account changes, and implement strict access controls to limit the number of users with administrative privileges.
- Organizations should regularly patch and update their software and systems to fix known vulnerabilities, use anti-malware and intrusion detection systems to detect and block exploits, and implement strict access controls to limit the number of users with administrative privileges.
















