


Pig-butchering scams long-con investment fraud schemes involving prolonged emotional grooming, impersonation, and fraudulent trading platforms have rapidly evolved into one of the most economically damaging global cybercrime models. These operations combine psychological manipulation, technologically fabricated financial ecosystems, and sophisticated cross-border money laundering pipelines. Taken together, these elements create a mature cybercriminal enterprise that is exceptionally challenging to detect and dismantle.
While pig-butchering scams begin with human-driven social engineering, their success depends on a broader criminal infrastructure that includes AI-assisted identity fabrication, coordinated scam compounds, domain and application development, stablecoin-based laundering systems, and transnational money mule networks. This infrastructure allows threat actors to scale their operations, handle large victim pools, and maintain operational continuity even when individual domains or accounts are blocked.
Economic losses from pig-butchering scams are now estimated in the tens of billions of dollars annually. Victims span all demographics from students to retirees and frequently lose life savings, retirement funds, assets, and borrowed money. Beyond the financial harm, the emotional consequences are severe: survivors often report depression, shame, and long-term trauma. These factors drive significant underreporting, enabling scam networks to proliferate unchecked.
This report provides a comprehensive, deeply analytical assessment of pig-butchering scams through a cybersecurity and threat-intelligence lens. It examines the threat landscape, actor ecosystem, operational lifecycle, technical infrastructure, attribution evidence, victimology, forensic methodologies, detection models, policy gaps, and actionable recommendations. The objective of this report is to equip CISOs, security architects, fraud investigators, law enforcement personnel, and threat-intelligence practitioners with a complete understanding of this growing cybercrime model and to support more effective detection, disruption, and response.
Pig-butchering scams represent a distinctive hybrid cyber threat one that merges psychological exploitation with technical fraud infrastructure. These scams are not purely cyber in nature, nor are they purely financial fraud; rather, they operate at the intersection of both domains, leveraging technology to amplify traditional social engineering to an industrial scale. The name “pig-butchering” reflects the long-term grooming process: victims are systematically “fattened” with trust, emotional intimacy, and staged financial success before being “slaughtered” through financial extraction.
Pig-butchering has evolved beyond the domain of opportunistic scammers. It is now a structured, globalized criminal economy supported by multilayered operational practices and specialized roles. The model enables sustained exploitation because it manipulates human psychology over long timeframes while simultaneously leveraging financial technologies like cryptocurrency, decentralized finance, and cross-border payments to obscure financial flows.
Pig-butchering scams emerged in East and Southeast Asia roughly a decade ago but expanded dramatically during the COVID-19 pandemic as digital isolation increased and global engagement shifted to online platforms. Criminal groups adapted rapidly, exploiting both technological advances such as AI-generated content and the rising popularity of cryptocurrency as an investment vehicle.
Initially, pig-butchering consisted of relatively small networks operating simple scripts via social media. Today, large compounds staffed by hundreds or thousands of individuals orchestrate operations with coordinating layers covering social engineering, engineering of fake platforms, financial operations, and even forced labour. These operations generate billions of dollars in illicit profit annually, creating significant geopolitical and law-enforcement pressure.
Pig-butchering is now a major cyber-financial crime risk because it tests the boundaries of multiple security domains simultaneously:
Because pig-butchering crosses several cybersecurity categories identity abuse, infrastructure exploitation, financial fraud, cryptographic laundering its mitigation requires cooperation across sectors that traditionally operated separately.
Environmental Conditions Enabling Growth
Several global conditions enabled pig-butchering to rise as a dominant cyber-fraud model.
Technological Conditions
Advances in AI-generated images, deepfake video synthesis, and automated message generation make it trivial to manufacture believable online personas. Additionally, low-cost VPS hosting and domain registration services enable quick deployment of fake trading platforms, while encrypted messaging tools hide scammer communication.
Social Conditions
Loneliness, digital dependency, and widespread online engagement have created psychological environments ripe for manipulation. Scammers exploit trust-seeking behaviours, cultural norms of politeness, and romantic aspirations to initiate and sustain long-term conversations.
Financial Conditions
The availability of cryptocurrency particularly stablecoins like USDT provides a near-perfect mechanism for laundering funds. Traditional financial controls struggle to detect scams where victims voluntarily initiate transfers, making AML detection significantly harder.
Pig-butchering scams now operate across a broad global landscape, shaped by regional criminal ecosystems, socio-economic vulnerabilities, and digital platform misuse. Understanding this landscape is essential for developing effective detection and mitigation strategies.
Global Operational Distribution
Pig-butchering operations follow a geographically distributed model. Scam compounds in Southeast Asia typically serve as central operational hubs where workforce labor, often trafficking victims are used to run large portions of the scam lifecycle. Coordination hubs in East Asia, the Middle East, and parts of Africa support logistics, money laundering, and operational planning.
Victims are distributed globally. Countries with large middle-class populations, high digital adoption, and strong investment cultures (e.g., U.S., India, UK, Canada, Singapore, Australia) are particularly targeted. This creates a phenomenon where operational activities occur in one part of the world while victims are in entirely different jurisdictions, complicating enforcement.
Victim Demographic Patterns
Victims are not confined to a specific demographic group. Instead, scammer scripts allow flexible adaptation to a wide range of target profiles. Younger victims often fall prey to romance-oriented approaches, while older or wealthier individuals may be targeted through investment-related conversations or job-related narratives. Scammers frequently research victims’ backgrounds through social media to craft tailored psychological hooks, creating a highly personalized manipulation strategy.
Scale and Severity of Impact
Economic impact is enormous. Many victims lose substantial portions of their net worth. Some liquidate property, borrow money, or use credit lines based on the scammer’s guidance. Many elderly victims lose retirement funds accumulated over decades. These losses have ripple effects across families, communities, and local economies. Institutions bear secondary impacts: banks handle fraud claims and compliance investigations; social platforms face brand trust erosion; and crypto exchanges must address illicit transaction flows.
Long-Term Societal Consequences
Beyond immediate financial losses, pig-butchering undermines digital trust. Individuals become hesitant to engage in online interactions, reducing legitimate social and economic activity. The scams contribute to negative perceptions of cryptocurrency, complicating adoption and regulatory acceptance. In regions where scam compounds operate, local economies and governance structures suffer due to criminal influence, corruption, and trafficking.
Pig-butchering scams are not opportunistic one-off frauds; they represent an entire cybercrime industry. This ecosystem includes layered operational roles, specialized support teams, logistical networks, and financial channels.
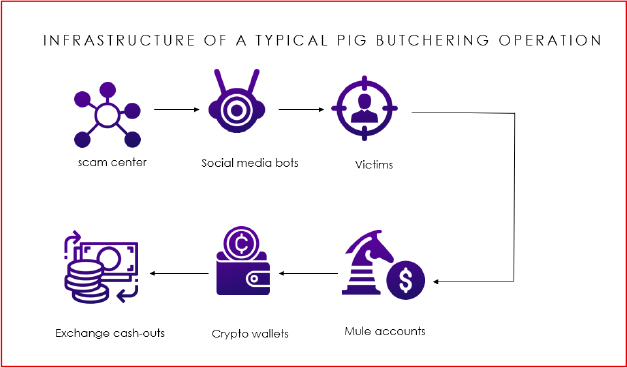
Scam Compounds
Scam compounds operate similarly to large-scale business process outsourcing (BPO) centres. These facilities often occupy high-rise office buildings or isolated compounds. Workers operate in shifts covering nearly 24 hours of activity. Supervisors and team leads manage productivity, track engagement metrics, and evaluate performance.
Workers are trained extensively. Their training includes psychological manipulation techniques, conversation pacing strategies, and detailed scripts designed to engage victims for weeks or months. Workers often operate multiple personas simultaneously across multiple platforms. Many individuals found in these scam centres are victims of trafficking, having been lured through false job advertisements and coerced into criminal activity.
Technical Infrastructure Teams
Dedicated technical teams handle website and app development, backend system maintenance, server updates, and operational resilience. These teams create, deploy, and maintain fraudulent trading platforms that mimic the behaviour of legitimate cryptocurrency or forex applications. Technical staff ensure that dashboards reflect real-time market data, create convincing user interfaces, and manage failover systems that allow rapid replacement of blocked domains.
These teams often possess legitimate professional experience in software development. Their involvement demonstrates the blending of cybercrime with professional technical labour markets.
Money Laundering and Financial Support Networks
Money laundering teams play a crucial role. Once victim funds are collected, they must be quickly moved through a network of mule accounts, cryptocurrency wallets, mixers, and exchanges. These teams leverage deep knowledge of AML evasion techniques, exploiting weaker regulatory regions, decentralized exchanges, privacy coins, or OTC brokers that permit high-volume trades without identity verification.
Their methods are highly adaptive. When regulators crack down on a specific laundering vector, new mechanisms emerge reflecting a dynamic and resilient financial ecosystem.
Fraud-as-a-Service Elements
Criminal groups also commoditize parts of the pig-butchering operation. Scammers can purchase fake identities, pre-built personas, investment scripts, fraudulent trading platforms, and money laundering services. This commoditization mirrors the evolution of ransomware-as-a-service and highlights the growing sophistication of cybercriminal markets.
The pig-butchering attack lifecycle involves distinct stages, each with specialized TTPs.
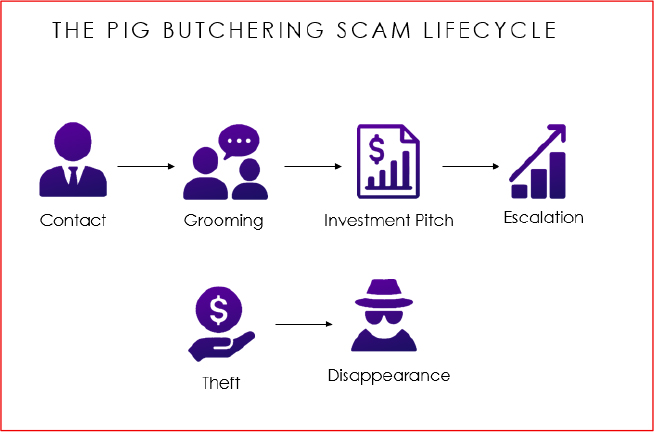
Initial Contact and Reconnaissance
Initial contact typically occurs on dating platforms, social networks, or messaging services. Scammers initiate conversations using compelling personas supported by AI-generated photos or curated images. Reconnaissance occurs as scammers analyse the victim’s digital footprint, identifying emotional vulnerabilities, financial background, and interests.
Grooming and Psychological Manipulation
Grooming is a methodical and structured process. Scammers engage victims in daily conversations, sharing fake personal experiences and gradually escalating emotional intimacy. This stage builds trust and emotional dependency, creating conditions where the victim becomes receptive to financial suggestions. The grooming process may last weeks or months, allowing scammers to extract personal details that can later be used to tailor persuasive pitches.
Investment Introduction and Manipulation
Once emotional trust is established, scammers introduce the investment narrative. This transition is subtle: they may mention recent profits or a friend’s trading success, gradually shifting the conversation toward financial topics. To reinforce credibility, scammers display screenshots, fake profit summaries, or fabricated account balances.
Fake Platform Interaction
Fake platforms are pivotal. They are designed to simulate legitimate financial ecosystems with realistic dashboards, market charts, and portfolio management features. Victims deposit funds through bank transfers or cryptocurrency payments. Initial returns displayed on the dashboard create a sense of authenticity. Victims are encouraged to reinvest earnings, increasingly committing more money.
Escalation and High-Pressure Manipulation
At this stage, victims are emotionally invested. Scammers escalate pressure subtly, emphasizing time-limited opportunities or encouraging victims to leverage personal loans or liquidate assets. The mixture of emotional manipulation and fabricated financial success traps the victim in a psychological loop where investing more appears to be a rational decision.
Withdrawal Blocking and Collapse
Eventually, the victim attempts to withdraw funds. Scammers implement artificial barriers such as verification fees, tax prepayments, or account freezes. Each barrier is designed to extract additional funds. When the victim refuses or asks too many questions, scammers disappear, delete accounts, or shut down platforms.
Laundering and Cash-Out
Post-extraction, funds are rapidly laundered. Cryptocurrency-based flows move quickly across multiple wallets, mixers, and decentralized exchanges. Fiat funds move through mule accounts and international wire transfers. The laundering stage ensures the criminal network retains access to funds while minimizing traceability.
Pig-butchering operations depend heavily on their technical ecosystem. The following components are instrumental to their success.
Domain and Web Infrastructure
Fake trading websites are typically hosted on low-cost VPS servers registrable without strict identity requirements. Domains are often newly registered, with WHOIS privacy features making attribution difficult. These websites use sleek interfaces with market data pulled through APIs from legitimate exchanges, creating a sense of authenticity. Multiple domains serve as backups in case primary domains are blocked or reported.
Mobile Application Infrastructure
Mobile applications are frequently distributed outside official app stores. These applications may include embedded wallets, fake dashboards, or server-controlled financial figures. APK signatures provide strong indicators of fraud, as scammers reuse certificates across multiple apps. Their permissions may include excessive access such as reading SMS or device identifiers raising further red flags.
Backend Financial and CRM Systems
The backend architecture supports both financial deception and operational management. Scammers use CRM systems to track victim behaviour and leverage analytics to identify high-value targets. Backend servers control “profits,” update dashboards, and manage deposit/withdrawal workflows. High-volume operations require automation for onboarding new victims, handling initial conversations, and generating convincing financial outputs.
Cryptocurrency and Payment Infrastructure
Stablecoins, especially USDT on the TRON network, are preferred due to low fees and high liquidity. Cross-chain bridges allow rapid movement across blockchain ecosystems, making traceability harder. Mixers further obscure transaction histories by mixing victim funds with other crypto pools. OTC brokers then support off-ramp conversions to fiat without formal KYC requirements.
Recent intelligence and research shed light on the actor ecosystem driving pig-butchering scams. While no confirmed nation-state APT groups are attributed to pig-butchering campaigns, several criminal and militia-linked organizations are directly implicated.
Confirmed Criminal Actor Evidence
Investigations conducted by OFAC, U.S. DOJ, and Chainalysis reveal involvement of the Democratic Karen Benevolent Army (DKBA), a Myanmar-based armed group. OFAC sanctions highlight DKBA’s control of scam centres that target victims globally. These findings reveal a disturbing overlap between cybercrime and paramilitary operations.
Another high-profile case involves the Prince Holding Group and its founder Chen Zhi, linked to extensive fraud operations in Cambodia. U.S. authorities seized billions in bitcoin connected to pig-butchering operations allegedly controlled by this network. This indicates that some scam compounds operate under corporate fronts with deep political connections.
Scam Compounds and Militia Connections
Locations such as KK Park in Myanmar and the Golden Triangle Special Economic Zone (GTSEZ) in Laos have emerged as major hotspots for pig-butchering operations. These compounds involve forced labour, human trafficking, and organized cyber fraud. Militia protection and local corruption in these zones provide operational shelter for scam networks.
Academic and Research Attribution
Recent academic studies analysing hundreds of thousands of social media posts have identified consistent patterns linking scam operator behaviour to specific geographic regions and organizational structures. Evidence suggests that many of these operations function like military or corporate hierarchies, with accountable supervisors and measurable performance metrics.
No Evidence of APT Involvement
Although pig-butchering shares some superficial TTPs with APT operations, such as infrastructure obfuscation and multi-stage operations, there is no publicly confirmed evidence that nation-state APTs conduct pig-butchering scams. Current intelligence strongly supports classification as financially motivated cybercrime groups with occasional militia protection not espionage actors.
One of the most striking illustrations of the destructive potential of pig-butchering scams emerged in the United States in 2023, when Heartland Tri-State Bank in Kansas collapsed after its CEO, Shan Hanes, became entangled in a long-form cryptocurrency investment fraud. According to public reporting, Hanes maintained extended contact with scammers who strategically manipulated him over time, eventually persuading him to initiate a series of escalating wire transfers from the bank’s accounts into cryptocurrency wallets controlled by the fraudsters. The total amount transferred exceeded $47 million, draining liquidity and destabilizing the institution’s financial position.
Once persuaded that he would recover and grow the bank’s funds through supposed high-yield crypto trading, Hanes continued to authorize transfers even as the amounts escalated rapidly. Scammers employed narratives commonly seen in such schemes claims that additional payments were required to “unlock” prior investments or to meet liquidity thresholds. As the losses mounted, the institution’s capital reserves collapsed, resulting in the failure of Heartland Tri-State Bank. Depositors were protected through federal insurance mechanisms, but shareholders incurred significant losses, and the bank ceased operations permanently. Hanes was later sentenced to more than two decades in federal prison for embezzlement tied to these transfers.
This case demonstrates that pig-butchering scams can transcend individual financial harm and escalate into full-scale institutional collapse. It underscores that even highly educated individuals in positions of trust and expertise can be manipulated through sustained psychological conditioning. The Kansas incident is now widely referenced by financial-crime investigators as the first publicly documented instance where a pig-butchering scam directly contributed to the operational failure of a regulated financial entity.
The Kansas bank case forces a reconsideration of pig-butchering scams not merely as consumer-level fraud, but as a potential vector for organizational destabilization. Although current evidence suggests these scams are driven primarily by financially motivated criminal syndicates rather than nation-state APTs, their demonstrated ability to compromise high-value individuals introduces a credible intelligence hypothesis: pig-butchering-style operations could be intentionally weaponized to target executives, financial officers, and privileged insiders in order to trigger cascading organizational harm.
From a strategic threat-modelling perspective, several dynamics support this hypothesis.
First, the success of pig-butchering relies on psychological exploitation rather than technical compromise. This creates a pathway for threat actors to bypass traditional cybersecurity defences entirely. Even with strong endpoint protection, multi-factor authentication, and hardened networks, an organization remains vulnerable if a senior decision-maker can be manipulated into initiating high-risk financial transfers or exposing sensitive operational data.
Second, executive-level targets possess disproportionately high financial and operational authority. A well-executed long-form grooming effort could persuade such individuals to approve unauthorized payments, alter investment portfolios, misallocate corporate funds, or engage in actions that jeopardize liquidity exactly as seen in the Heartland Tri-State Bank collapse. If a CEO or CFO can be deceived into transferring tens of millions in corporate assets, the damage may extend beyond immediate financial loss and into regulatory sanctions, insolvency, or reputational ruin.
Third, the structure of pig-butchering scams aligns with the patience and persistence commonly associated with advanced adversaries. The grooming period often spanning months mirrors the dwell-time seen in traditional APT operations, in which attackers embed themselves deeply within a target environment before executing an objective. It is not inconceivable that a sophisticated threat group could adopt these techniques to achieve strategic disruption instead of financial gain.
Finally, with the rise of geopolitical conflict and financially motivated proxy operations, the boundary between profit-driven cybercrime and state-aligned activity continues to blur. If criminal networks with documented militia connections already operate scam compounds, the potential exists for such techniques to be repurposed deliberately or opportunistically for broader disruptive objectives.
Taken together, these factors suggest a plausible and increasingly relevant hypothesis: pig-butchering scams represent an emerging pathway for targeted organizational compromise, where threat actors criminal or state-linked could deliberately manipulate executives or privileged employees into actions that destabilize corporate operations, weaken financial integrity, or precipitate institutional collapse. While empirical evidence of state-directed deployment of this technique is not yet confirmed, the Kansas case demonstrates that the mechanism is viable, the impact is real, and the risk is sufficiently credible to warrant inclusion in executive threat models.
The impact of pig-butchering scams extends far beyond financial loss.
Psychological Impact
Victims often develop emotional attachment to scammers, making financial loss emotionally devastating. Many victims experience deep shame, depression, anxiety, and PTSD-like symptoms. Some become socially isolated or quit online platforms altogether. The emotional trauma can exceed the financial loss.
Financial Impact
Long-term financial consequences are severe. Some victims lose their entire net worth. Others accumulate debt through loans taken to “invest” according to scammer advice. Several cases involve bankruptcy or retirement disruption. The compounded nature of financial and psychological damage makes recovery extremely difficult.
Reporting Behaviour
Because victims feel ashamed, many do not report the crime. Underreporting hinders law-enforcement efforts and allows networks to continue operating with little resistance. Financial institutions often struggle to classify transactions as fraud because victims willingly initiate transfers.
Forensic workflows must integrate digital, financial, and blockchain investigative approaches.
Digital Forensics
Digital investigations collect chat logs, browser histories, screenshots, metadata, and mobile applications. Analysts reconstruct communication sequences to identify manipulation patterns and platform abuse. APKs are analysed for malicious behaviour or embedded financial endpoints.
Blockchain Forensics
Blockchain forensics follows victim funds. Analysts map wallet clusters, identify mixer interactions, and track cross-chain transactions. Market-leading tools (e.g., Chainalysis, Elliptic, TRM Labs) assist investigators in identifying on-ramp and off-ramp points such as exchanges or OTC brokers. Rapid freeze requests can prevent total fund loss if submitted early.
Banking Forensics
Banks must analyse beneficiary names, transaction patterns, and mule indicators. Behavioural models detect rapid fund flows inconsistent with customer profiles. Collaboration with law enforcement supports the freezing of mule accounts and identification of laundering networks.
Platform Mitigation (Social Networks, Dating Apps)
Platforms require behavioural analytics capable of detecting unnatural messaging patterns, new accounts showing romantic behaviour immediately, and accounts promoting investment opportunities. Image hash clustering identifies AI-generated or reused profile photos. Platforms must implement warnings during off-platform migration attempts.
Financial Institution Mitigation
Banks and fintech firms should deploy behavioural AML models that evaluate unusual activity patterns. Transaction cooling-off periods can reduce high-value impulsive transfers. Banks should also monitor exchange transfers and integrate blockchain forensics into AML systems to identify high-risk patterns.
Crypto Exchange Mitigation
Exchanges must adopt wallet risk scoring, enforce strong KYC processes, and collaborate with law enforcement on freeze requests. Monitoring cross-chain flows and detecting interactions with known scam-affiliated wallets are critical defence measures.
Pig-butchering poses several governance and enforcement challenges.
Regulatory Fragmentation
Cryptocurrency regulation varies widely across jurisdictions, with many regions lacking robust AML controls. OTC brokers often operate in legal grey zones, enabling high-volume cash-outs.
Enforcement Challenges
Law enforcement agencies struggle with international cooperation, especially when scams originate from regions with limited governance or rampant corruption. MLAT processes are slow and often ineffective for time-sensitive financial crimes.
Need for Unified Policy Action
Effective mitigation requires harmonizing AML/KYC frameworks, establishing shared wallet blacklists, enforcing app vetting requirements, and enabling expedited cross-border freeze protocols.
| Tactic | Technique ID | Technique |
| Reconnaissance | T1593 | Search Websites |
| Reconnaissance | T1592 | Gather Victim Info |
| Resource Dev | T1585 | Establish Accounts |
| Resource Dev | T1583.001 | Acquire Domains |
| Initial Access | T1204 | User Execution |
| Initial Access | T1566.002 | Spearphishing via Messaging |
| Execution | T1646 | Social Engineering |
| Persistence | T1078 | Valid Accounts |
| Defense Evasion | T1562 | Impair Defenses |
| Collection | T1114 | Message Collection |
| Exfiltration | T1041 | C2 Exfiltration |
| Impact | T1657 | Financial Theft |
Strategic Recommendations
Tactical (for SOC / TI teams)
Operational Recommendations
Pig-butchering scams represent one of the most pervasive and damaging global cybercrime ecosystems. Their hybrid nature emotional manipulation, fake financial platform engineering, and sophisticated laundering makes them uniquely resilient and difficult to counter. Addressing this threat requires a multi-layered approach involving cybersecurity teams, financial regulators, law enforcement, platform operators, and international policy bodies.
This report provides a comprehensive analysis of pig-butchering scams, highlighting the complex threat landscape, operational structure, technical infrastructure, forensic methodologies, and mitigation strategies. Only through coordinated, intelligence-driven action can organizations and governments curb the growth of this escalating cybercrime model and safeguard individuals from its devastating impact.