


This report provides an additional overview of the destructive Remote Administration Tool, which has been developed by a user based in Syria. The latest enhancements to this tool have introduced new functionalities that enable threat actors to compromise Android users more effectively, providing them with powerful capabilities to obtain extensive data and information. As additional features continued to be incorporated, the security community was surprised that the threat actor introduced an additional module designed to generate the dropper payload.
This is our second report on the advanced Craxs Remote Administration tool: in the previous report, we exposed the developer of a destructive remote administration tool for Android devices and also reviewed the panel, including Android malware generated from the tool. EVLF’s old operator (from Syria) sold the channel to a new administration of unknown origin. Fortunately, before this transaction took place, we were able to find out the real identity of the original developer-operator of CraxsRAT and report it to the relevant authorities. In this report, we are reviewing the newly added feature that serves the role of a dropper, a novel technique added to the Android remote administration tool that has not been seen before in any other publicly available RAT.
The updated Craxs Remote Administration Tool now includes an additional build option. The primary build option is already available, offering a range of destructive features with a few new add-ons, however, the Android package in the primary build contains code similar to what was previously reported, i.e. the new add-on to the panel enables threat actors to create a dropper. When combined with well-planned social engineering, this feature can further ensnare Android users. In our further analysis, we delve into the dropper’s functionality and how the payload code serves as a dropper.
The panel’s main builder enables the threat actor to configure the connection between the compromised device and command & control.
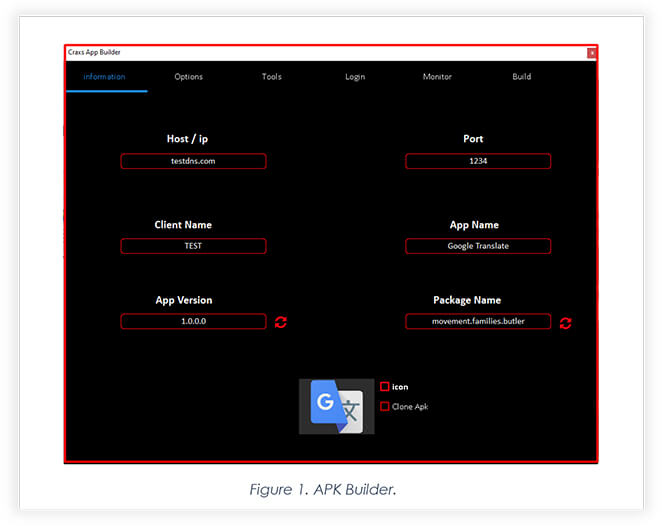
The panel also allows threat actors to customize the main payload by choosing icon, size, and website to add to the web view module.

Below snippet shows the destructive features the panel offers threat actors to inject into the main payload.
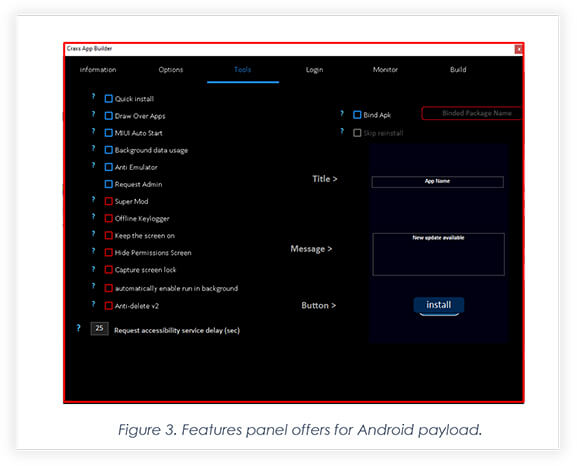
Threat actors can customize the credentials monitoring of any website they want to.

The final build page allows threat actors to choose permissions they want to exploit and then generate the main payload.

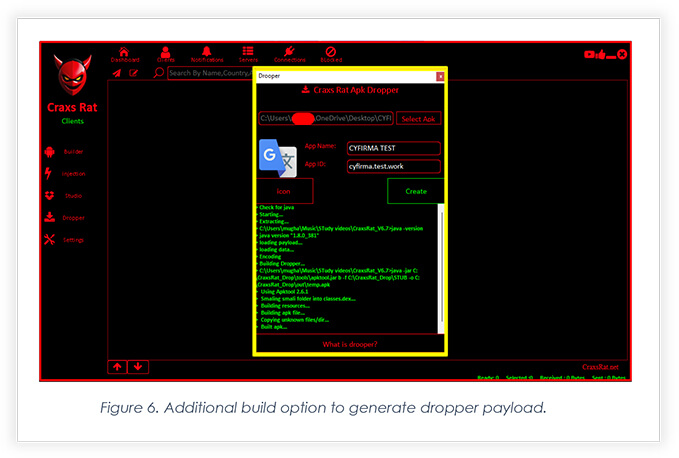
Figure 6 highlights a new add-on to the tool. This new build option allows threat actors to build an Android package that will help attackers to deliver the main payload to fully compromise the device.
When it is opened after installation, victims are taken to the page where the background dropper fetches the main payload. The user interface, meanwhile, displays ‘Downloading updates’ graphics.

Once the app is fetched in the background, the dropper app then asks the victim to click on the update button.
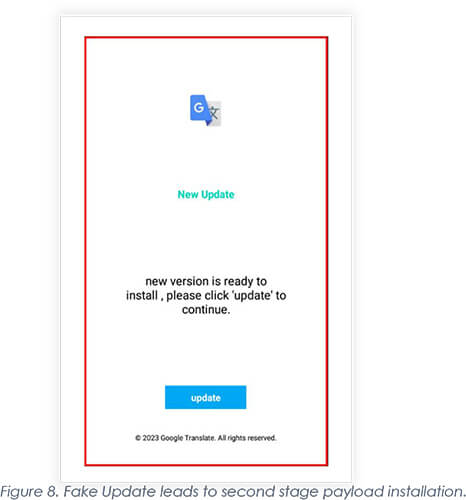
Upon clicking ‘update’ (Figure 8), the apps take victims to the next page where they interact with the main payload for its installation.

Once installed, the victim is asked to enable accessibility to exploit the permissions and fully compromise the android devices.

childapp.apk shown in the below screenshot is the actual main payload that was injected into dropper payload using dropper module shown in figure 6.

The snippet below shows MainActivity Class exploiting WRITE_PERSMISSION_STORAGE and READ_EXTERNAL_STORAGE permissions to access local storage and perform dropper process to deploy second-stage malware.

Part of the module ‘childapp’, which is the main payload injected while building the dropper android payload (Figure 6). With the use of “PackageInstaller’ class module, it initiates the installation of the main payload.
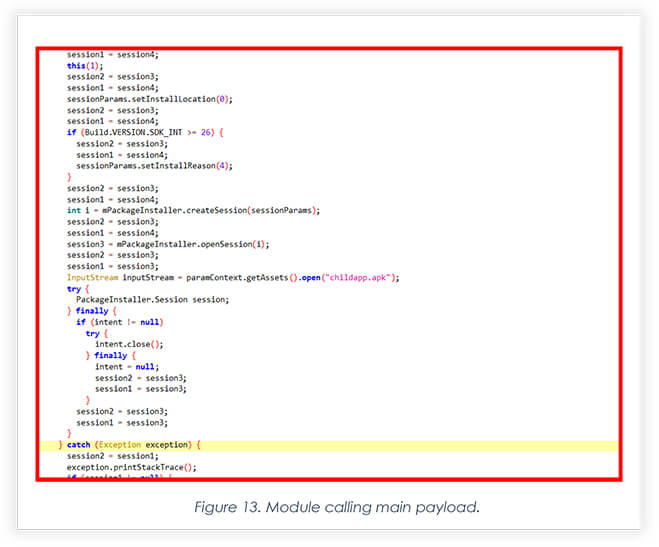
Below code is part of module that manipulates the victim into believing the update is in progress shown in figure.7.

OBSERVATION
We have included a few screenshots highlighting some of our observations regarding the demand for CraxsRat in underground forums and Telegram channels. These screenshots provide clear indications of the increasing demand for CraxsRat among cybercriminals pursuing various objectives.

New Owner for EVLF Dev from unknown origin.
Additionally, CYFIRMA research noted that recent posts and tutorials for the RAT are being released in Mandarin, increasing the likelihood of Chinese threat actors being interested in the malware.
Our team has observed, threat actors are increasingly utilizing various Android Remote Access Trojans (RATs) to exploit unsuspecting internet users. Among these RATs, CraxsRat has emerged as the preferred choice for a wide range of threat actors, particularly those with Android-based targets. The likelihood of Chinese threat actors adopting this tool is significant, given the increased interaction between the CraxsRat developer and Chinese users. This engagement includes the sharing of tutorials in Chinese on how to operate the RAT. This surge in demand has created a cause for concern. Although the RAT is not readily accessible to internet users, there have been instances of leaked files, often the result of the activities of rogue individuals operating within platforms such as Telegram. We have observed high demand for CraxsRat, which creates a potential higher risk threat environment for Android users. This powerful tool can be employed for various malicious activities, including financial scams and cyber espionage.


The tool has already become the preferred RAT for threat actors seeking to carry out illegal cyber activities by targeting Android-based users. With the addition of a dropper payload, threat actors are expected to use it even more frequently. Social engineering tactics will be adjusted according to the functionality of the dropper payload, which exploits the minimum of permissions and enables threat actors to evade antivirus software through an additional layer of obfuscation. The user interaction with the dropper payload requires multiple clicks, which leads to the installation of the main payload. Nevertheless, the delivery mechanism works in favor of threat actors, as it significantly reduces the chances of browsers detecting malware in the initial stages if threat actors choose to deliver it via the internet browser.