



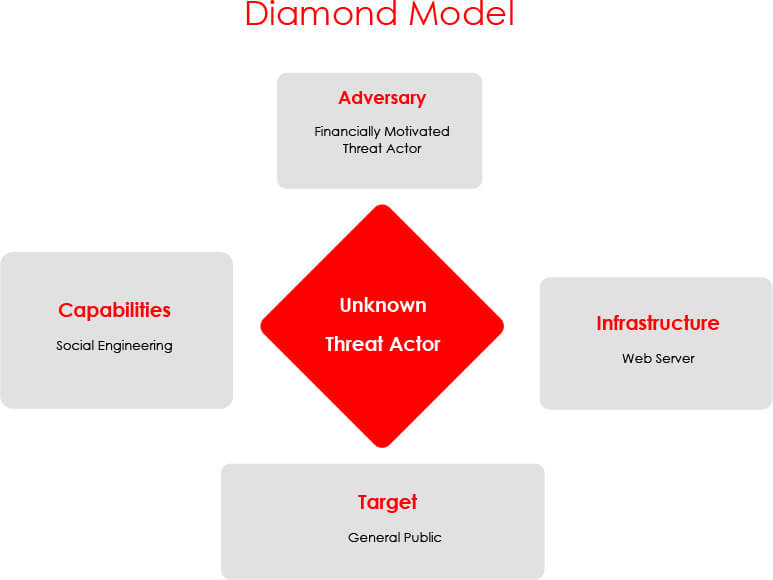
The team at CYFIRMA recently identified a pattern where unknown threat actors utilize Android malware to target individuals in urgent need of instant money. These unknown, financially motivated threat actors make enticing promises of quick loans with minimal formalities, deliver malware to compromise their devices, and employ threats to extort money.
The team at CYFIRMA obtained a malicious Android package used to target victims for extortion. The fake loan app claims to provide instant loans to its users: when the app is installed, the user is shown reasons for granting permissions. The app then asks victims to login and submit their details as part of KYC, which includes a selfie. Once this process is complete, the user is directed to a page where the victim is shown a few listed amounts in lakhs of rupees. Once the user selects an amount, they see a small sum that needs to be paid as a fee to get an instant loan of rupees in lakhs. At this point, the threat actor has the victim’s basic details required for KYC, including a government ID and a selfie, along with data such as a contact list and text messages obtained via a malicious app.
After this, the threat actor manipulates the selfie to create a nude image and attempts to extort money by threatening to distribute it to their contact list. The amount that the actor asks for is not significant, but they persistently message and call the victim to persuade them into making the transaction.
The team obtained the malicious Android package, while an incident was ongoing, and the team leveraged the opportunity to start social engineering to gather more details about the threat actor.
During our technical analysis, we found that the malicious app was utilizing minimum permissions to perform malicious activities, making the app undetectable by anti-viruses and online scanning platforms.
Process Overview
The team investigated the application and its functionality. Although the loan app appeared to be a legitimate instant loan service, the app is a fake loan service and also includes malicious behavior. Our exploration was limited to the sign-up page to avoid exposing our number. Nevertheless, we have outlined the steps following the sign-up process with the number in the executive summary.
Upon opening, the moneyfine.apk application displays a page for accessing permissions:

Upon agreeing to the terms, the app takes the user to sign up or sign in:

Clicking on the signup/ Sign-in shown in the previous screenshot the app then takes you to the sign-in and sign-up page where it asks the victim to log in with OTP.

Code review revealed that the app mainly exploits permissions for contacts, call logs, and camera access for selfie upload. The obfuscation level was minimal, and the app remained undetected by many antivirus programs, primarily because the exploited permissions were limited. The app functioned like a typical instant loan app and victims were made to complete the KYC process; however, KYC details were also utilized in the process of money extortion.
This snippet is extracted from the Android Manifest file associated with the malicious Moneyfine.apk Android app, revealing the permissions utilized to engage in malicious activities.
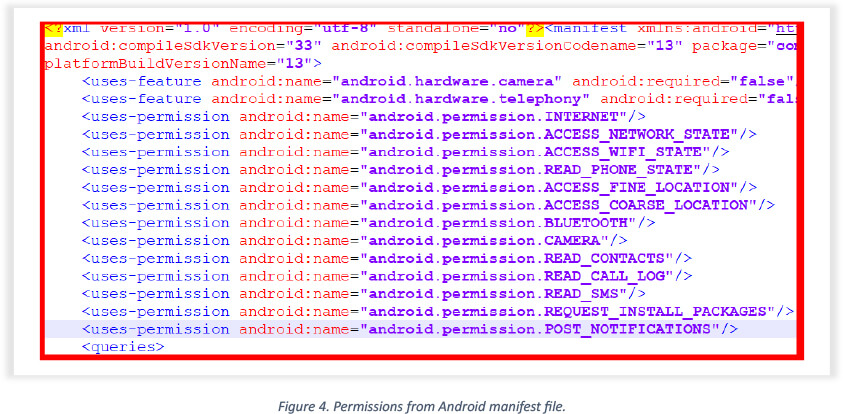
Two major permissions that were exploited are:
| Sr.no | Permissions | Descriptions |
| 1. | READ_CALL_LOG | This permission allows the threat actor to read call logs. |
| 2. | READ_CONTACTS | This permission allows the threat actor to read and fetch contacts. |
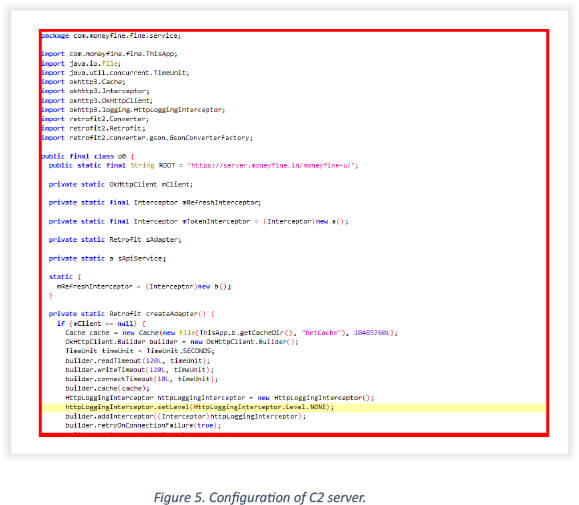
The below snippet shows configuring Retrofit with a command-and-control server for transferring data via HTTP requests:
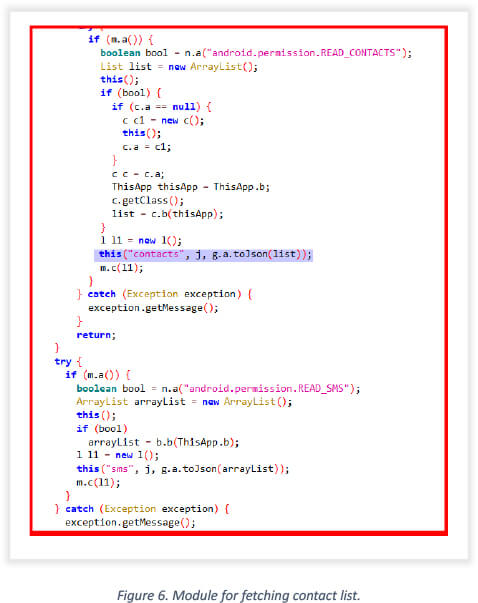
This snapshot displays a portion of the code, where the contact permission.READ_CONTACTS is exploited to retrieve contacts in a JSON file.
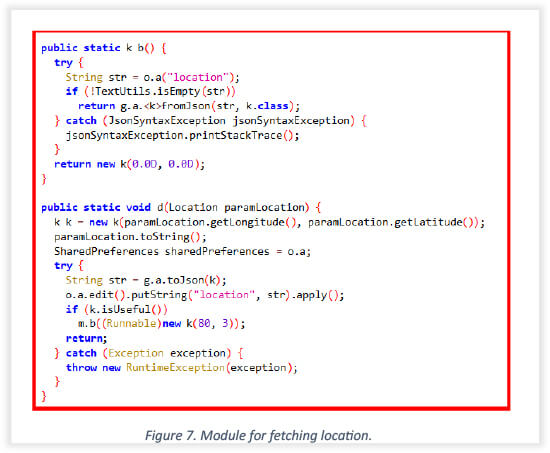
The below snapshot shows code that is responsible for obtaining the victim’s precise location.
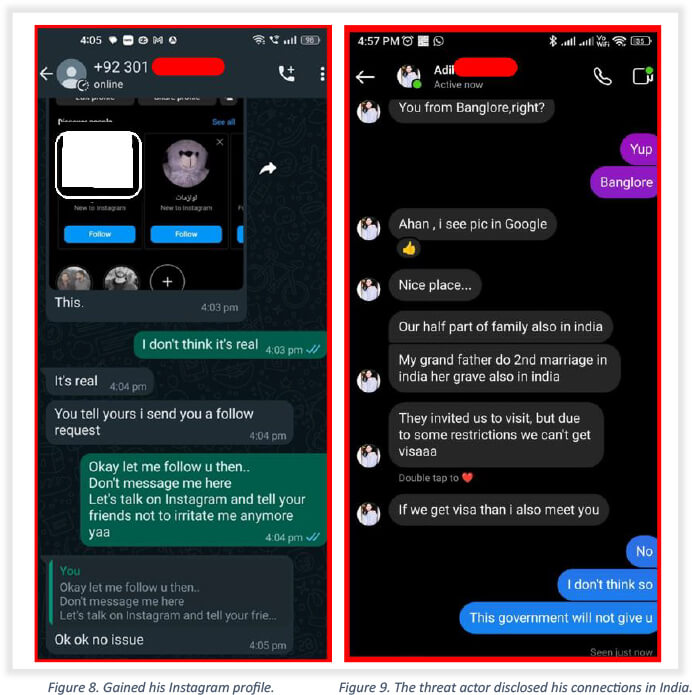
The team employed social engineering methods to gather more details about the threat actor, revealing an unknown company in Pakistan, recruiting individuals for specific job roles and providing them with resources to deliver malicious Android packages. These individuals then threaten compromised victims to extort money. Additionally, it was discovered that the threat actor has connections in India (see screengrab of chat on Instagram). Users from India were also found in his followers and following list. This arguably explains why the Pakistan-based threat actor utilized the Unified Payment Interface (UPI) payment method to receive money, which is typically used by Indian citizens. Despite UPI not being available in Pakistan, victims were directed to make payments through this system, indicating potential collaboration with individuals in India for fund redirection.
The act of extorting money after successfully compromising a victim is not a new phenomenon. In the past, we have observed victims being compromised, leading to the theft of private pictures, which are subsequently used to blackmail victims into sending larger amounts. Regrettably, in some cases, victims have taken their own lives. Currently, it appears to be a lucrative business for the threat actor, leveraging fear for financial gains. This trend will no doubt continue as hunger for money is equally found in innocent people who need easy money.
Extortion via malicious loan apps is on the rise, and the ever-evolving nature of cyber threats makes it challenging for individuals, especially those who may not be tech-savvy, to keep up with the latest tactics used by threat actors. Many vulnerable people tend to fall for these kinds of malicious offers, mostly those who need urgent financial support in less time.
| Tactics | Technique ID | Description |
| TA0101 – Command and Control | T0869-Standard Application Layer Protocol | The threat actor uses a web service as a command-and-control server. |
| TA0035 – Collection | T1430-Location Tracking | Fetches precise Location as a part of information gathering. |
| TA0035 – Collection | T1636.002 Call Log | The threat actor exploits Call log permission to access call logs |
| TA0035 – Collection | T1636.004 SMS Messages | The threat actor Access SMSs by exploiting gained SMS permission. |
| TA0035 – Collection | T1636.002 Contact List | The threat actor fetches an Updated contact list. |
| Indicator | Type | Remarks |
| 0E1E4E638195BD6EF2E55D74A7867931E7DD8AE34F5A3E30CD29AD7907F5DDE6 | Hash: SHA256 | moneyfine.apk |
| 6419F9BA5F52550D2324394D285E26CAFCC04B5C723F21DA4FF0E5B4E9CC8E59 | Hash: SHA256 | Moneyfine.apk |
| file[.]moneyfine[.]in/moneyfine[.]apk | URL | Payload Delivery |
| moneyfine[.]in | Domain | Website |
| server[.]moneyfine[.]in | Sub-domain | Command and Control |
The investigation revealed that the financially motivated threat actor strategically minimized the app permissions to avoid detection by antivirus programs, exploiting the contact list and selfie image to send threatening messages for extortion. This highlights the threat actor’s adept use of social engineering to orchestrate the campaign, as opposed to relying on a more dangerous malicious Android app that might fall foul of anti-virus software.